Hello everyone, I'm the researcher of Microsoft MVP Lab - Qian. Today, I will share with you how to use GitHub Actions to deploy Terraform Code to Azure in an automated manner through code examples.
Microsoft MVP lab researcher

Dry
Microsoft's most valuable expert, Microsoft Azure direction, currently engaged in NET technology stack product back-end development. Keen to learn Microsoft Azure related technologies and share their learning experience. At the same time, they are improving their design ability of Azure cloud infrastructure solutions and their training ability in Azure cloud technology
Thinking analysis
Deploying Azure infrastructure resources using Terraform Code is particularly popular. I once wrote an article to share the automatic deployment of Azure infrastructure resources described by Terraform Code using Azure DevOps. However, some people may be unfamiliar with Azure DevOps, plus the Parallel jobs paid jobs of Azure DevOps. So as an alternative, today I'd like to share with you how to deploy terrain code using GitHub Actions.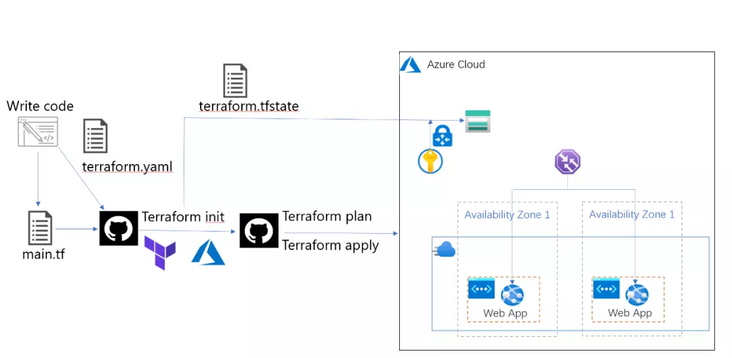
Configure the credentials of Azure Service Principal to GitHub Secret Library
Terraform Code and Azure CLI will use Azure Service Principle to authenticate the identity of Azure. For the creation of Azure Service Principle, please refer to Blog.
Blog: https://www.cnblogs.com/Allen...
Next, you need to add the following confidential information
1)AZURE_AD_CLIENT_ID
2)AZURE_AD_CLIENT_SECRET
3)AZURE_AD_TENANT_ID
4)AZURE_SUBSCRIPTION_ID
5)AZURE_CREDENTIALS
Including azure_ The format of credits is as follows:
"clientId": "XXXX", "clientSecret": "XXXX", "subscriptionId": "XXXX", "tenantId": "XXXX"
Store the above information in GitHub Secrets with the corresponding name.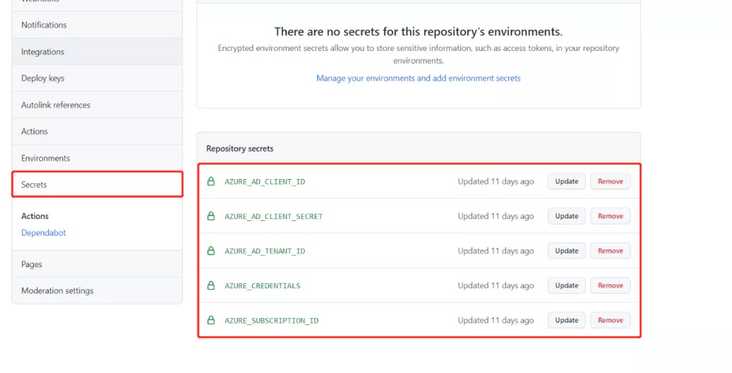
Configure the yaml of workflow run
Create a terrain. In the root directory of the terrain project Yaml and save it in the following directory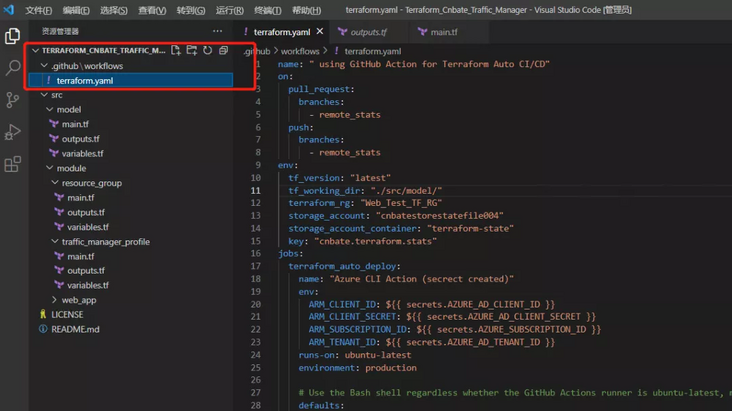
terraform.yaml is as follows
name: " using GitHub Action for Terraform Auto CI/CD"
on:
pull_request:
branches:
- remote_stats
push:
branches:
- remote_stats
env:
tf_version: "latest"
tf_working_dir: "./src/model/"
terraform_rg: "Web_Test_TF_RG"
storage_account: "cnbatestorestatefile004"
storage_account_container: "terraform-state"
key: "cnbate.terraform.stats"
jobs:
terraform_auto_deploy:
name: "Azure CLI Action (secrect created)"
env:
ARM_CLIENT_ID: ${{ secrets.AZURE_AD_CLIENT_ID }}
ARM_CLIENT_SECRET: ${{ secrets.AZURE_AD_CLIENT_SECRET }}
ARM_SUBSCRIPTION_ID: ${{ secrets.AZURE_SUBSCRIPTION_ID }}
ARM_TENANT_ID: ${{ secrets.AZURE_AD_TENANT_ID }}
runs-on: ubuntu-latest
environment: production
# Use the Bash shell regardless whether the GitHub Actions runner is ubuntu-latest, macos-latest, or windows-latest
defaults:
run:
shell: bash
steps:
- name: "Checkout"
uses: actions/checkout@master
- name: Azure Login
uses: azure/login@v1
with:
creds: ${{ secrets.AZURE_CREDENTIALS }}
enable-AzPSSession: false
environment: azurecloud
allow-no-subscriptions: false
- name: Azure CLI script
uses: azure/CLI@v1
with:
creds: ${{ secrets.AZURE_CREDENTIALS }}
enable-AzPSSession: false
environment: azurecloud
allow-no-subscriptions: false
azcliversion: 2.30.0
inlineScript: |
# create azure resource group
az group create --location eastasia --name ${{ env.terraform_rg }}
# create azure storage account
az storage account create --name ${{ env.storage_account }} --resource-group ${{ env.terraform_rg }} --location eastasia --sku Standard_LRS
# create storage account container for tf state
az storage container create --name ${{ env.storage_account_container }} --account-name ${{ env.storage_account }}
# query storage key and set variable
export ARM_ACCESS_KEY=$(az storage account keys list --resource-group ${{env.terraform_rg}} --account-name ${{ env.storage_account }} --query "[?keyName == 'key1'][value]" --output tsv)
echo $ARM_ACCESS_KEY
- name: "Terraform init azurerm backend"
uses: ahmedig/terraform-azurerm-backend@v1
with:
azure_credentials: ${{ secrets.AZURE_CREDENTIALS }}
resource_group_name: ${{ env.terraform_rg }}
container_name: ${{ env.storage_account_container }}
storage_account_name: ${{ env.storage_account }}
file_name: ${{ env.key }}
subscription_id: ${{ secrets.AZURE_SUBSCRIPTION_ID }}
tf_working_directory: ${{ env.tf_working_dir }}
- name: "Terraform Validate"
uses: hashicorp/terraform-github-actions@master
with:
tf_actions_version: ${{ env.tf_version }}
tf_actions_subcommand: 'validate'
tf_actions_working_dir: ${{ env.tf_working_dir }}
env:
GITHUB_TOKEN: ${{ secrets.AZURE_CREDENTIALS }}
- name: "Terraform Plan"
uses: hashicorp/terraform-github-actions@master
with:
tf_actions_version: ${{ env.tf_version }}
tf_actions_subcommand: 'plan'
tf_actions_working_dir: ${{ env.tf_working_dir }}
env:
GITHUB_TOKEN: ${{ secrets.AZURE_CREDENTIALS }}
- name: "Terraform Deploy"
uses: hashicorp/terraform-github-actions@master
with:
tf_actions_version: ${{ env.tf_version }}
tf_actions_subcommand: 'apply'
tf_actions_working_dir: ${{ env.tf_working_dir }}
env:
GITHUB_TOKEN: ${{ secrets.AZURE_CREDENTIALS }}
- name: "Terraform Destroy"
uses: hashicorp/terraform-github-actions@master
with:
tf_actions_version: ${{ env.tf_version }}
tf_actions_subcommand: 'destroy'
tf_actions_working_dir: ${{ env.tf_working_dir }}
env:
GITHUB_TOKEN: ${{ secrets.AZURE_CREDENTIALS }}Run workflows run
Since we specify the working branch "remote_stats" in "terrain. Yaml", when the "push" or "pull_request" operation occurs in the "remote" branch, the workflow of GitHub Actions will be triggered. So we directly push the currently edited "terrain. Yaml" file to the "remote_stats" branch, and view the workflow running results on GitHub.
If you need to know more about what operations are performed in each step, you can select the current workflow runs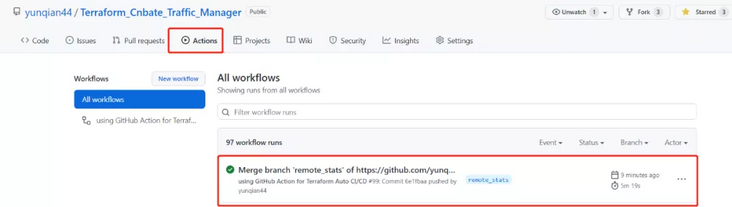
View each step and its output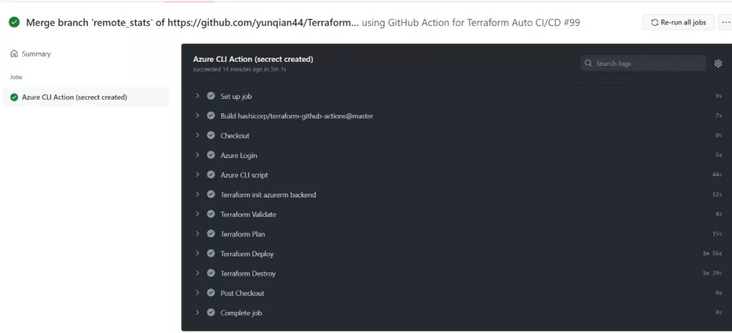
View the content of Terraform execution deployment plan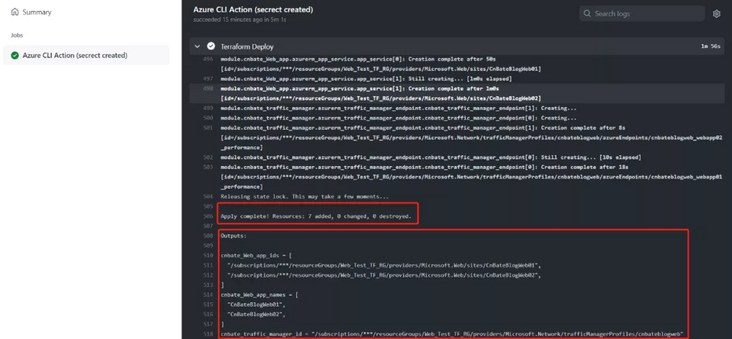
To refer to the detailed output information, copy the following link to the browser https://github.com/yunqian44/...
summary
In this experiment, we learn how to use GitHub Actions to automatically verify the syntax of terrain code, generate deployment plans, execute deployment plans, and destroy deployment plans. It also adds a new solution for us to choose the solution of automatically deploying Azure infrastructure, that is, code.
Set Secrets in GitHub Action workflow:
https://github.com/Azure/acti...
Azure service principal:
https://www.cnblogs.com/Allen...
GitHub:
https://github.com/yunqian44/...

Scan code attention to the official account, get more technical knowledge points