JAVA Creates MS AD Account and Sets Password through SSL Certificate
Recently, due to the need for work to sort out automation things, because the company launched OA last year, so the company's entry system will submit user information to the IT department, the earliest way is to enter, the IT department collects user information in AD to create corresponding user information, so in order to improve the efficiency of administrators, it is ready to implement the automatic creation of AD accounts, when the OA process. After the IT personnel approval node, the IT personnel automatically create AD accounts according to the personnel information after approval, so we sorted out some JAVA information to create AD personnel information, but we need to pay attention to the fact that some common operations of operating MS AD in JAVA language do not require SSL, but for the user password reset operation, we must use SSL, of course, we can skip before looking at the Internet. However, the experiment was not successful, so we still operate the user's AD password through SSL according to the standard configuration. It's no more nonsense. Today, we mainly introduce how to create MS AD account by using JAVA through SSL. Because we need to set the password for the created user, we need to use the SSL certificate. Since we need the SSL certificate, the purpose is to make JAVA trust LDAP, so we need to use the SSL certificate. To export trusted certificates from AD, import them into the cacert certificate file under JRE in the JAVA runtime environment. Now that we have talked about OA, in fact, we can apply for certificates and import certificates through the system's own functions, which is relatively simple; of course, if there is no OA environment, we can import certificates through the keytool of JDK in JAVA running environment, which we will introduce below;
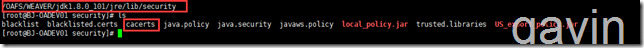
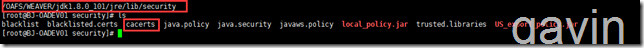
First, we use the functions in OA to import certificates; our certificate strength in OA is / OAFS/WEAVER/jdk1.8.0_101/jre/lib/security/cacerts.
After confirming the strength of JDK in the OA environment, we will then apply for certificates and import them.
We visit the address of OA, and then add / integration/ldapcert.jsp to it; if there is no JAVA file in the back, we can find the OA supplier to ask for it; or download it in the attachment.
First, we download the files in the attachment. After downloading, there are three files in the attachment.
First, we enter the classbean folder and copy the content to the corresponding directory of the corresponding OA server.
ecology\classbean\weaver\ldap
2. Then copy the following files from the folder integration file in the decompressed file to the corresponding server directory of OA:
ecology\integration
3. Because there are three folders after decompression, and the third folder src is the source code, we don't need to care about it.
Following the above approach, we can configure it through the following links
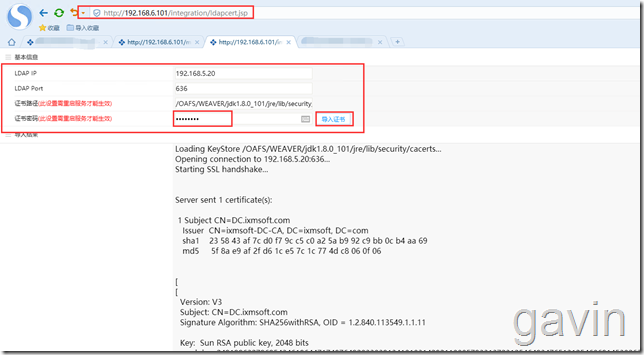
http://192.168.6.101/integration/ldapcert.jsp
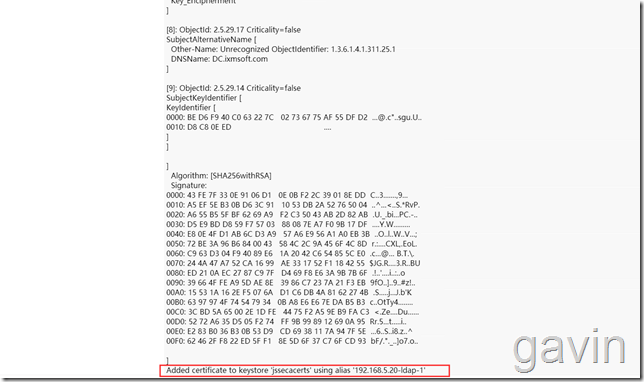
After visiting, we input the AD DC server address of LDAP IP input environment, the system will default to fill in LDAP port 636, and certificate strength, these information systems will automatically complete; we need to set the certificate password manually, generally we will set it as changeit, after setting these information, we import the certificate, will prompt the following import information;
Import complete
Then we need to download the certificate to the local JRE environment for testing.
Next, let's look at the second way of applying for certificates.
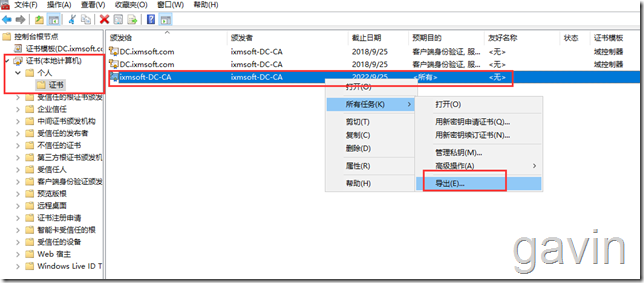
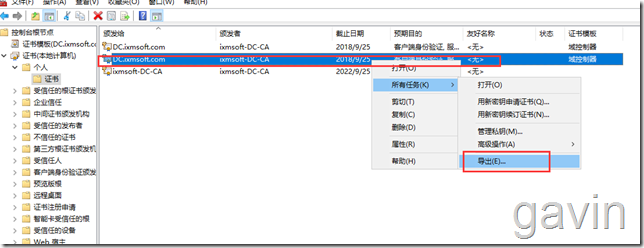
We need to import the root certificate of the domain from the DC
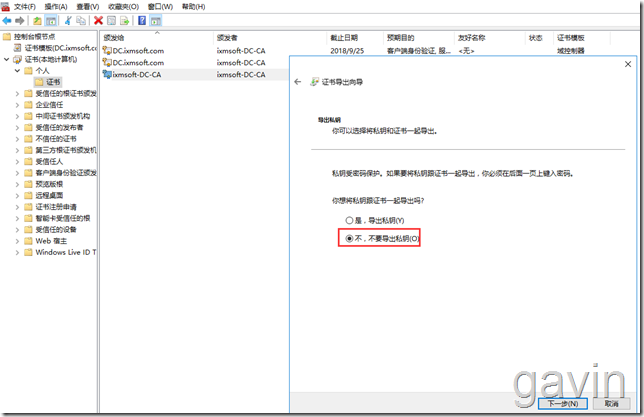
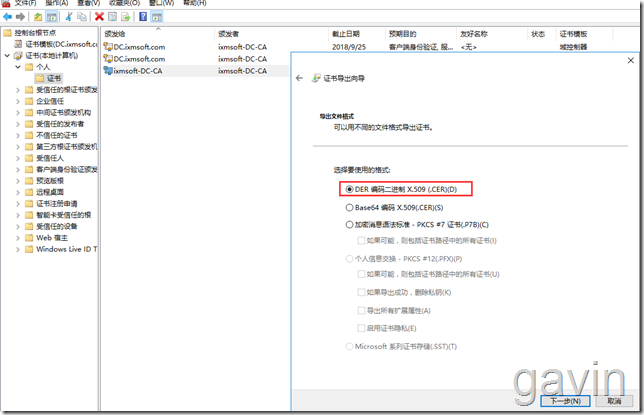
mmc - - add - - Certificate - - Computer - - Personal - - select root certificate - - export
No need to export private key
Use default DRE encoding
Preservation
We export another one in the same way.
Then we need to import the root certificate into the certificate in the local JDK environment.
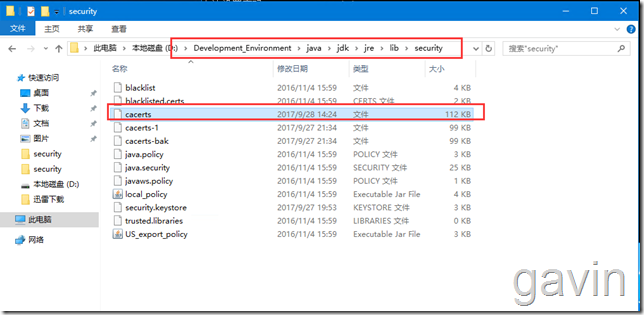
My local JDK environment roadside D: Development_Environment java jdk jre lib security
Then run the command to import the root certificate just exported into the cacert certificate file of Lujin.
We need cd to jdk first
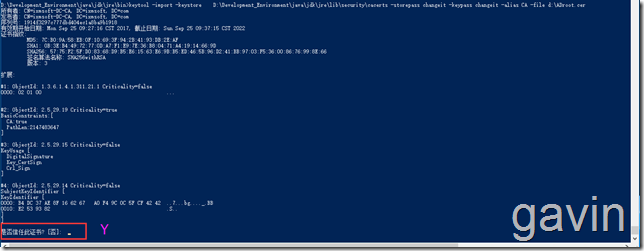
cd D:\Development_Environment\java\jdk\jre\bin
Then save the root certificate you just exported to disk D and import it through the following command
keytool keytool -import -keystore D:\Development_Environment\java\jdk\jre\lib\security\cacerts -storepass changeit -keypass changeit -alias CA -file d:\ADroot.cer
Enter Y trusted
Then we can go through it.
Then look at the ADDS environment.
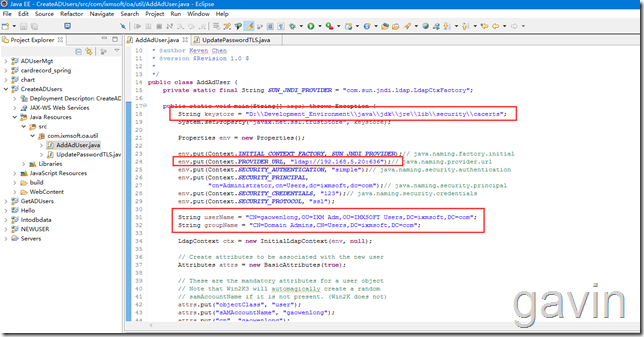
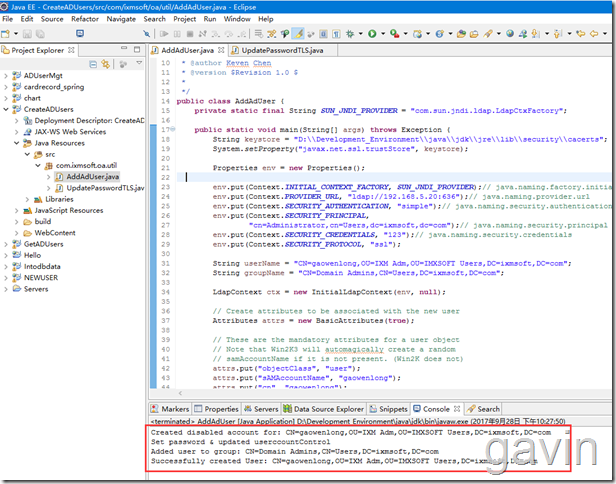
If we get ready, we can put in the code.
We set up the certificate roadmap, LDAP authentication information, and the user name that needs to be registered.
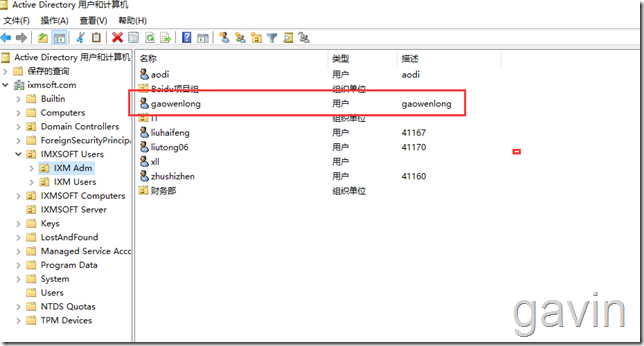
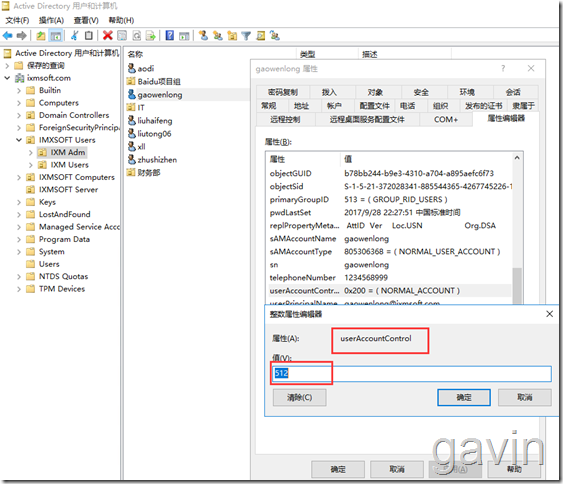
Successful account registration
Upper Code:
package com.ixmsoft.oa.util;
import java.util.Properties;
import javax.naming.*;
import javax.naming.ldap.*;
import javax.naming.directory.*;
/**
* @author Keven Chen
* @version $Revision 1.0 $
*
*/
public class AddAdUser {
private static final String SUN_JNDI_PROVIDER = "com.sun.jndi.ldap.LdapCtxFactory";
public static void main(String[] args) throws Exception {
String keystore = "D:\\Development_Environment\\java\\jdk\\jre\\lib\\security\\cacerts";
System.setProperty("javax.net.ssl.trustStore", keystore);
Properties env = new Properties();
env.put(Context.INITIAL_CONTEXT_FACTORY, SUN_JNDI_PROVIDER);// java.naming.factory.initial
env.put(Context.PROVIDER_URL, "ldap://192.168.5.20:636");// java.naming.provider.url
env.put(Context.SECURITY_AUTHENTICATION, "simple");// java.naming.security.authentication
env.put(Context.SECURITY_PRINCIPAL,
"cn=Administrator,cn=Users,dc=ixmsoft,dc=com");// java.naming.security.principal
env.put(Context.SECURITY_CREDENTIALS, "123");// java.naming.security.credentials
env.put(Context.SECURITY_PROTOCOL, "ssl");
String userName = "CN=gaowenlong,OU=IXM Adm,OU=IMXSOFT Users,DC=ixmsoft,DC=com";
String groupName = "CN=Domain Admins,CN=Users,DC=ixmsoft,DC=com";
LdapContext ctx = new InitialLdapContext(env, null);
// Create attributes to be associated with the new user
Attributes attrs = new BasicAttributes(true);
// These are the mandatory attributes for a user object
// Note that Win2K3 will automagically create a random
// samAccountName if it is not present. (Win2K does not)
attrs.put("objectClass", "user");
attrs.put("sAMAccountName", "gaowenlong");
attrs.put("cn", "gaowenlong");
// These are some optional (but useful) attributes
attrs.put("sn", "gaowenlong");
attrs.put("displayName", "gaowenlong");
attrs.put("description", "gaowenlong");
attrs.put("userPrincipalName", "gaowenlong@ixmsoft.com");
attrs.put("mail", "gaowenlong@ixmsoft.com");
attrs.put("telephoneNumber", "1234568999");
// some useful constants from lmaccess.h
int UF_ACCOUNTDISABLE = 0x0002; //Disable account
int UF_PASSWD_NOTREQD = 0x0020; //Users cannot change passwords
int UF_PASSWD_CANT_CHANGE = 0x0040;
int UF_NORMAL_ACCOUNT = 0x0200; //Normal user
int UF_DONT_EXPIRE_PASSWD = 0x10000; //password never expires
int UF_PASSWORD_EXPIRED = 0x800000; //Password has expired
// Note that you need to create the user object before you can
// set the password. Therefore as the user is created with no
// password, user AccountControl must be set to the following
// otherwise the Win2K3 password filter will return error 53
// unwilling to perform.
attrs.put("userAccountControl", Integer.toString(UF_NORMAL_ACCOUNT
+ UF_PASSWD_NOTREQD + UF_PASSWORD_EXPIRED + UF_ACCOUNTDISABLE));
// Create the context
Context result = ctx.createSubcontext(userName, attrs);
System.out.println("Created disabled account for: " + userName);
ModificationItem[] mods = new ModificationItem[2];
// Replace the "unicdodePwd" attribute with a new value
// Password must be both Unicode and a quoted string
String newQuotedPassword = "\"Password2000\"";
byte[] newUnicodePassword = newQuotedPassword.getBytes("UTF-16LE");
mods[0] = new ModificationItem(DirContext.REPLACE_ATTRIBUTE,
new BasicAttribute("unicodePwd", newUnicodePassword));
mods[1] = new ModificationItem(DirContext.REPLACE_ATTRIBUTE,
new BasicAttribute("userAccountControl", Integer
.toString(UF_NORMAL_ACCOUNT + UF_PASSWORD_EXPIRED)));
// Perform the update
ctx.modifyAttributes(userName, mods);
System.out.println("Set password & updated userccountControl");
// now add the user to a group.
try {
ModificationItem member[] = new ModificationItem[1];
member[0] = new ModificationItem(DirContext.ADD_ATTRIBUTE,
new BasicAttribute("member", userName));
ctx.modifyAttributes(groupName, member);
System.out.println("Added user to group: " + groupName);
} catch (NamingException e) {
System.err.println("Problem adding user to group: " + e);
}
// Could have put tls.close() prior to the group modification
// but it seems to screw up the connection or context ?
ctx.close();
System.out.println("Successfully created User: " + userName);
}
}Let's check.
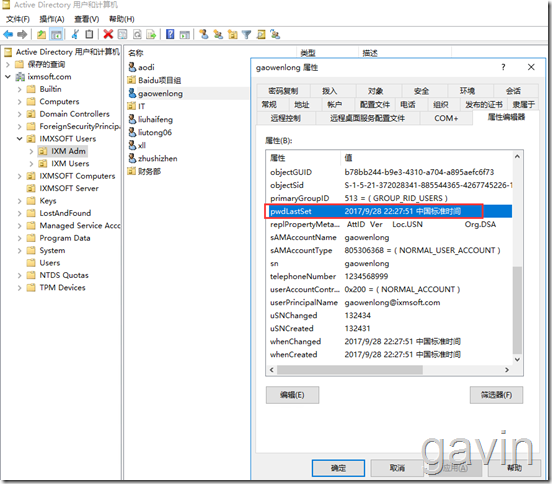
View Account Properties
Then look at the properties
We upload the java file to the attachment. If there is an error in eclipse, according to the error prompt, right-click to import the package related to ldap.