explain
POM
When using Hutool encryption and decryption tool, the following dependencies are introduced
Copy code behind code <dependency> <groupId>cn.hutool</groupId> <artifactId>hutool-crypto</artifactId> <version>5.7.15</version> </dependency>
Symmetric encryption and asymmetric encryption
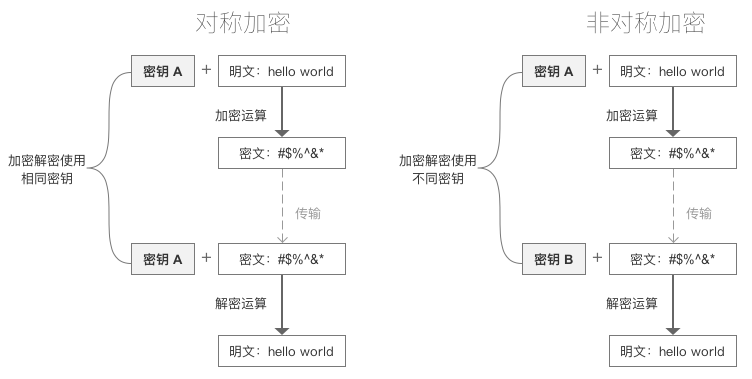
Symmetric encryption
Scan VX for Java data, front-end, test, python and so on
encryption algorithm
- Using the encryption method of single key cryptosystem, the same key can be used for information encryption and decryption at the same time. This encryption method is called symmetric encryption, also known as single key encryption.
- Common encryption algorithms
- DES(Data Encryption Standard): that is, data encryption standard. It is a block algorithm using key encryption. In 1977, it was determined as the federal data processing standard (FIPS) by the National Bureau of standards of the federal government of the United States and authorized to be used in unclassified government communications. Subsequently, the algorithm was widely spread internationally.
- AES(Advanced Encryption Standard): Advanced Encryption Standard, also known as Rijndael encryption method in cryptography, is a block encryption standard adopted by the federal government of the United States. This standard is used to replace the original DES, which has been analyzed by many parties and widely used all over the world.
- characteristic
- The encryption speed is fast, and large files can be encrypted
- The ciphertext is reversible. Once the key file is leaked, it will lead to data exposure
- After encryption, the corresponding character cannot be found in the coding table, resulting in garbled code. It is generally used in combination with Base64
Encryption mode
- ECB(Electronic codebook): electronic codebook. The message to be encrypted is divided into several blocks according to the block size of the block password, and each block is encrypted independently < br >
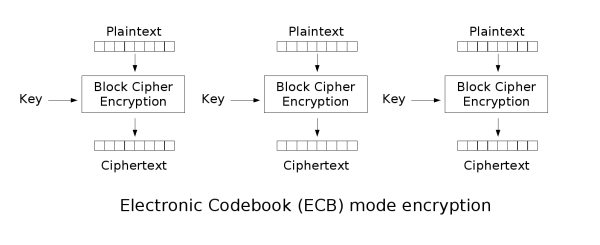
- Advantages: data can be processed in parallel
- Disadvantages: the same original text generates the same ciphertext, which can not protect the data well
- At the same time, the original text is the same, and the encrypted ciphertext is the same
- CBC (cipher block chaining): cipher block chaining. Each plaintext block is XORed with the previous ciphertext block before encryption. Each ciphertext block depends on all plaintext blocks in front of it < br >
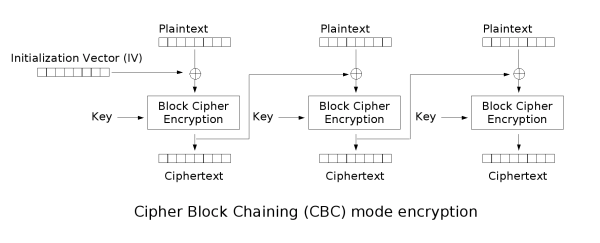
- Advantages: the ciphertext generated by the same original text is different
- Disadvantages: serial data processing
Fill mode
When the length of data to be processed by block does not meet the requirements of block processing, fill the rule of full block length according to a certain method
- NoPadding does not fill
- Under DES encryption algorithm, the length of the original text must be an integer multiple of 8byte
- Under AES encryption algorithm, the length of the original text must be an integer multiple of 16byte
- PKCS5Padding
- The size of the data block is 8 bits. If it is not enough, it will be supplemented
Tips: by default, the encryption mode and filling mode are ECB/PKCS5Padding. If CBC mode is used, parameter initialization vector IV needs to be added
DES and AES example code
Copy code behind code
public class SymmetricCryptoTest {
@Test
public void des() {
String text = "HelloWorld";
// Key: in DES mode, the key must be 8 bits
String key = "12345678";
// iv: offset. It is not required in ECB mode. It must be 8 bits in CBC mode
String iv = "12345678";
// DES des = new DES(Mode.ECB, Padding.PKCS5Padding, key.getBytes());
DES des = new DES(Mode.CBC, Padding.PKCS5Padding, key.getBytes(), iv.getBytes());
String encrypt = des.encryptBase64(text);
System.out.println(encrypt);
String decrypt = des.decryptStr(encrypt);
System.out.println(decrypt);
}
@Test
public void aes() {
String text = "HelloWorld";
// Key: in AES mode, the key must be 16 bits
String key = "1234567812345678";
// iv: offset. It is not required in ECB mode. It must be 16 bits in CBC mode
String iv = "1234567812345678";
// AES aes = new AES(Mode.ECB, Padding.PKCS5Padding, key.getBytes());
AES aes = new AES(Mode.CBC, Padding.PKCS5Padding, key.getBytes(), iv.getBytes());
// Encryption and Base transcoding
String encrypt = aes.encryptBase64(text);
System.out.println(encrypt);
// Decrypt to string
String decrypt = aes.decryptStr(encrypt);
System.out.println(decrypt);
}
}Asymmetric encryption
Scan VX for Java data, front-end, test, python and so on

brief introduction
- Asymmetric encryption algorithm is also called modern encryption algorithm.
- Asymmetric encryption is the cornerstone of computer communication security, which ensures that the encrypted data will not be cracked.
- Unlike symmetric encryption algorithms, asymmetric encryption algorithms require two keys: public key and private key
- Public and private keys are a pair
- If the data is encrypted with a public key, it can only be decrypted with the corresponding private key.
- If the data is encrypted with a private key, it can only be decrypted with the corresponding public key.
- Because encryption and decryption use two different keys, this algorithm is called asymmetric encryption algorithm.
- characteristic
- Encryption and decryption use different keys
- Processing data is slower because of the high level of security
- Common algorithms
- RSA
- ECC
RSA example
Copy code behind code
public class AsymmetricCryptoTest {
/**
* Private and public keys
*/
private static String privateKey;
private static String publicKey;
private static String encryptByPublic;
/**
* Generate public-private key
*/
@BeforeAll
public static void genKey() {
KeyPair pair = SecureUtil.generateKeyPair("RSA");
privateKey = Base64.encode(pair.getPrivate().getEncoded());
System.out.println("Private key\t" + privateKey);
publicKey = Base64.encode(pair.getPublic().getEncoded());
System.out.println("Public key\t" + publicKey);
}
@Test
public void test() {
String text = "HelloWorld";
// Initialize object
// The first parameter is the encryption algorithm, which is not transmitted. The default is RSA/ECB/PKCS1Padding
// The second parameter is the private key (Base64 string)
// The third parameter is the public key (Base64 string)
RSA rsa = new RSA(AsymmetricAlgorithm.RSA_ECB_PKCS1.getValue(), privateKey, publicKey);
// Public key encryption, private key decryption
String encryptByPublic = rsa.encryptBase64(text, KeyType.PublicKey);
System.out.println("Public key encryption\t" + encryptByPublic);
String decryptByPrivate = rsa.decryptStr(encryptByPublic, KeyType.PrivateKey);
System.out.println("Private key decryption\t" + decryptByPrivate);
// Private key encryption
String encryptByPrivate = rsa.encryptBase64(text, KeyType.PrivateKey);
System.out.println("Private key encryption\t" + encryptByPrivate);
String decryptByPublic = rsa.decryptStr(encryptByPrivate, KeyType.PublicKey);
System.out.println("Public key decryption\t" + decryptByPublic);
// The assignment here is for the next test
AsymmetricCryptoTest.encryptByPublic = encryptByPublic;
}
/**
* Decrypt the ciphertext encrypted by the public key using only the private key
*/
@Test
public void test2() {
// Pass in the private key and the corresponding algorithm
RSA rsa = new RSA(AsymmetricAlgorithm.RSA_ECB_PKCS1.getValue(), privateKey, null);
// Private key decrypts the ciphertext encrypted by the public key
String decrypt = rsa.decryptStr(encryptByPublic, KeyType.PrivateKey);
System.out.println(decrypt);
}
}Abstract encryption
brief introduction
- Message Digest is also called Digital Digest
- It is a fixed length value that uniquely corresponds to a message or text. It is generated by a one-way Hash encryption function acting on the message
- The value generated by digital digest cannot be tampered with in order to ensure the security of files or values
- characteristic:
- No matter how long the input message is, the length of the calculated message summary is always fixed. for example
- The message summarized with MD5 algorithm has 128 bits
- The message summarized with SHA-1 algorithm finally has 160 bits
- As long as the input messages are different, the summary messages generated after summarizing them must also be different; But the same input must produce the same output
- Message digest is unidirectional and irreversible
- No matter how long the input message is, the length of the calculated message summary is always fixed. for example
- Common algorithms
- MD5
- SHA1
- SHA256
- SHA512
MD5 and SHA-1 examples
Copy code behind code
public class DigesterTest {
@Test
public void md5() {
String text = "HelloWorld";
// The first is to create a Digester object and perform encryption
Digester md5 = new Digester(DigestAlgorithm.MD5);
String digestHex = md5.digestHex(text);
System.out.println(digestHex);
// The second is to use DigestUtil for execution
String md5Hex = DigestUtil.md5Hex(text);
System.out.println(md5Hex);
}
@Test
public void sha1() {
String text = "HelloWorld";
// The first is to create a Digester object and perform encryption
Digester md5 = new Digester(DigestAlgorithm.SHA1);
String digestHex = md5.digestHex(text);
System.out.println(digestHex);
// The second is to use DigestUtil for execution
String md5Hex = DigestUtil.sha1Hex(text);
System.out.println(md5Hex);
}
}Scan VX for Java data, front-end, test, python and so on
