kali - Introduction to information collection
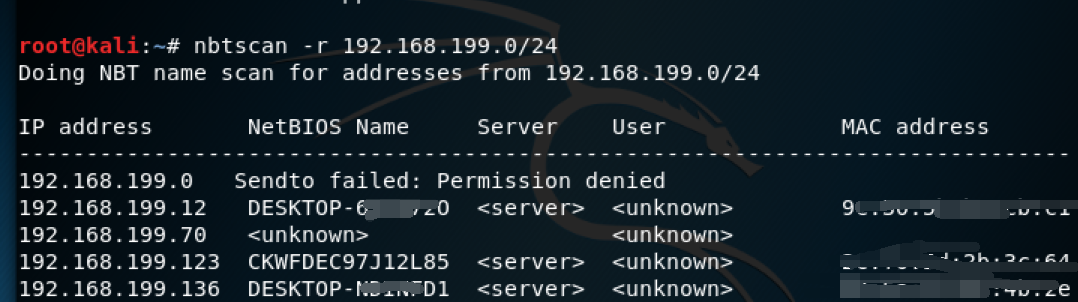
nbtscan
This is a program for scanning NetBIOS name information on Windows network. The program sends NetBIOS status query to each address within the given range, and lists the received information in an easy to read table. For each responding host, NBTSCAN lists its IP address, NetBIOS computer name, login user name and MAC address. But it can only be used in LAN. NBTSCAN can get the real IP address and MAC address of PC. if there is "ARP attack", you can find the IP / and MAC address of PC equipped with ARP attack. But it can only be used in LAN. NBTSCAN can get the real IP address and MAC address of PC. if there is "ARP attack", you can find the IP / and MAC address of PC equipped with ARP attack. NBTSCAN can get the real IP address and MAC address of the PC. if there is "ARP attack", you can find the IP / MAC address of the PC equipped with ARP attack. In short, NBTSCAN can get the real IP address and MAC address of the PC.
nbtscan needs to download and install by itself.
Use command
nbtscan -r 192.168.1.0/24
Netdiscover installation
Network scanning tool provided by Kali Linux
GitHub address: https://github.com/alexxy/netdiscover
ubuntu:
$ sudo apt install netdiscover
View help information after installation:
$ netdiscover -h Netdiscover 0.5.1 [Active/passive ARP reconnaissance tool] Written by: Jaime Penalba <jpenalbae@gmail.com> Usage: netdiscover [-i device] [-r range | -l file | -p] [-m file] [-F filter] [-s time] [-c count] [-n node] [-dfPLNS] -i device: your network device -r range: scan a given range instead of auto scan. 192.168.6.0/24,/16,/8 -l file: scan the list of ranges contained into the given file -p passive mode: do not send anything, only sniff -m file: scan a list of known MACs and host names -F filter: customize pcap filter expression (default: "arp") -s time: time to sleep between each ARP request (milliseconds) -c count: number of times to send each ARP request (for nets with packet loss) -n node: last source IP octet used for scanning (from 2 to 253) -d ignore home config files for autoscan and fast mode -f enable fastmode scan, saves a lot of time, recommended for auto -P print results in a format suitable for parsing by another program and stop after active scan -L similar to -P but continue listening after the active scan is completed -N Do not print header. Only valid when -P or -L is enabled. -S enable sleep time suppression between each request (hardcore mode) If -r, -l or -p are not enabled, netdiscover will scan for common LAN addresses
netdiscover
netdiscover -i eth0 192.168.0.1/24 -i adapter name -r ip paragraph
Passive scanning
utilize netdiscover Scanning tool for passive information scanning netdiscover -p -p:It means passive
Netdiscover is a network scanning tool, which can discover active hosts through ARP scanning, and can perform ARP scanning in both active and passive modes. Check the network ARP traffic by actively sending ARP request, and scan the network address through automatic scanning mode. This article introduces the installation and use of netdiscover.
Netdiscover option
| option | explain |
|---|---|
| -i device | network interface |
| -r range | Scanning range, such as 192.168.0.0/24, only supports / 8, / 16 and / 24 |
| -l file | Scan range list file, one range per line |
| -p | Passive mode: no message occurs, only sniffing |
| -m file | Scan list files for known Mac addresses and host names |
| -F filter | Custom pcap filter expression (default "arp") |
| -s time | Sleep time between each ARP request (MS, default 1ms) |
| -c count | The number of times each ARP request is sent. It is used for networks that lose packets. The default is 1 time |
| -n node | Scan the last source IP. The default is 67(x.x.x.67), and the allowable range is 2-253 |
| -d | Ignore the main profile of automatic scanning and quick mode, and scan the default range and IP |
| -f | Enable fast mode scanning to scan. 1,. 100 and. 254 of each network segment |
| -P | Generate output to file or other parsing program, and exit after scanning, for example: ` netdiscover -P -r 192.168.20.0/16 |
| -L | Similar to - P, but continues to capture ARP packets after active scanning |
| -N | Do not print header, only valid when - P or - L is enabled |
| -S | Deprecated |
Netdiscover uses
usage
If the passive mode (- p), scan list (- l), or scan range (- r) options are not enabled, netdiscover scans LAN addresses (192.168.0.0/16, 172.16.0.0/12, and 10.0.0.0/8).
Scan result control key:
h: Display help information
$ netdiscover -i ens38 -p
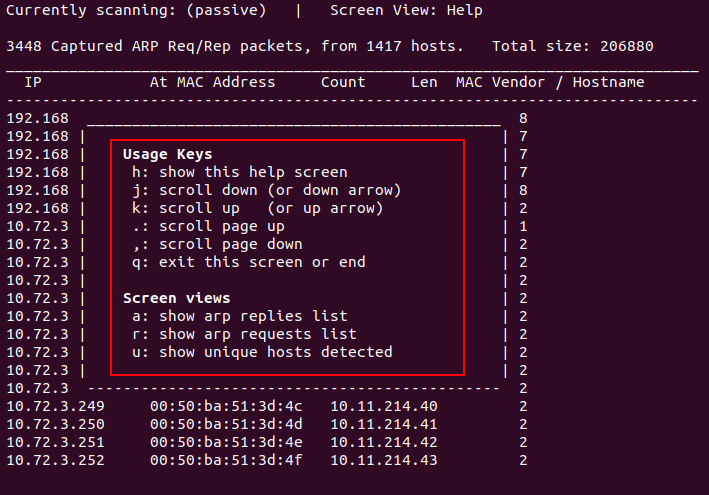
q: Exit the help information interface, or exit the scan (or Ctrl+c (exit)
j: Scroll down (or use the down arrow)
k: Scroll up (or use the up arrow)
.: Page up
,: Page down
Scan results view:
a: Display ARP response list
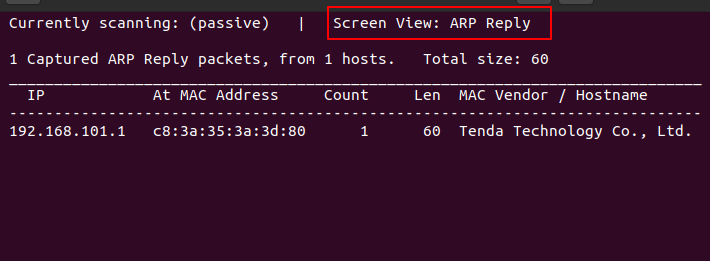
r: Displays the list of ARP requests

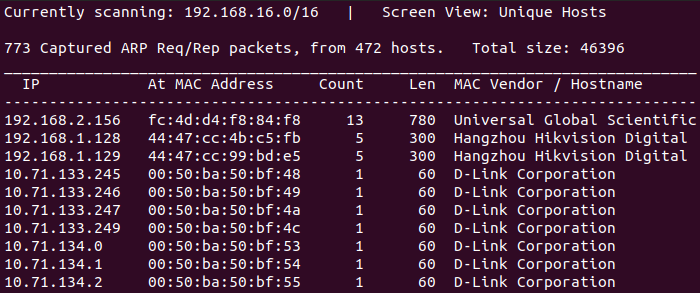
u: Displays the unique host detected
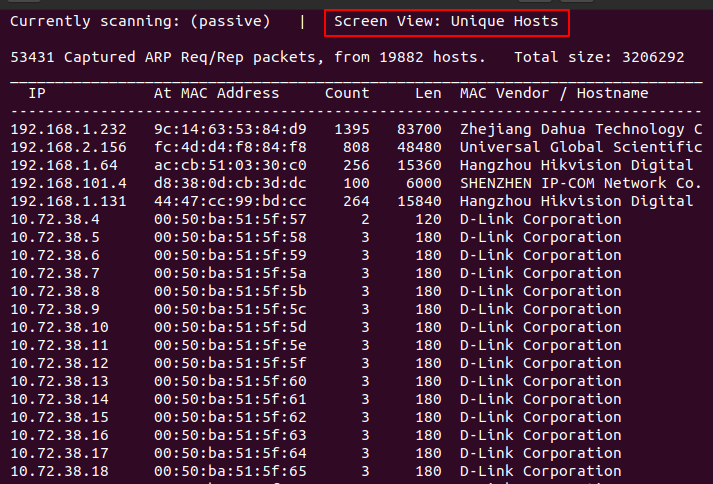
Use example
Scan specified interface:
$ netdiscover -i ens38
Quick scan:
$ netdiscover -i ens38 -f
Scan specified range:
$ netdiscover -i ens38 -r 192.168.0.0/16
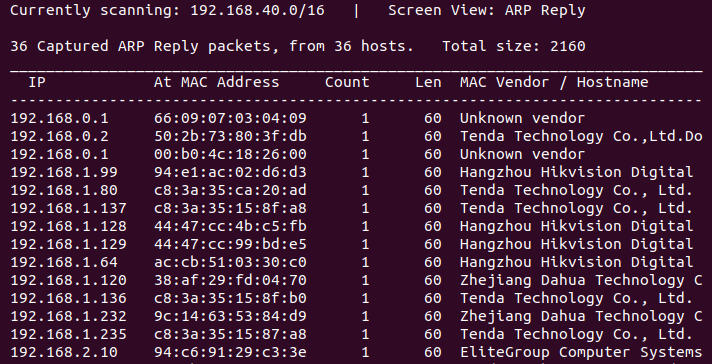
Passive scan, sniff only:
$ netdiscover -i ens38 -r 192.168.0.0/16 -p