CDN

VO layer
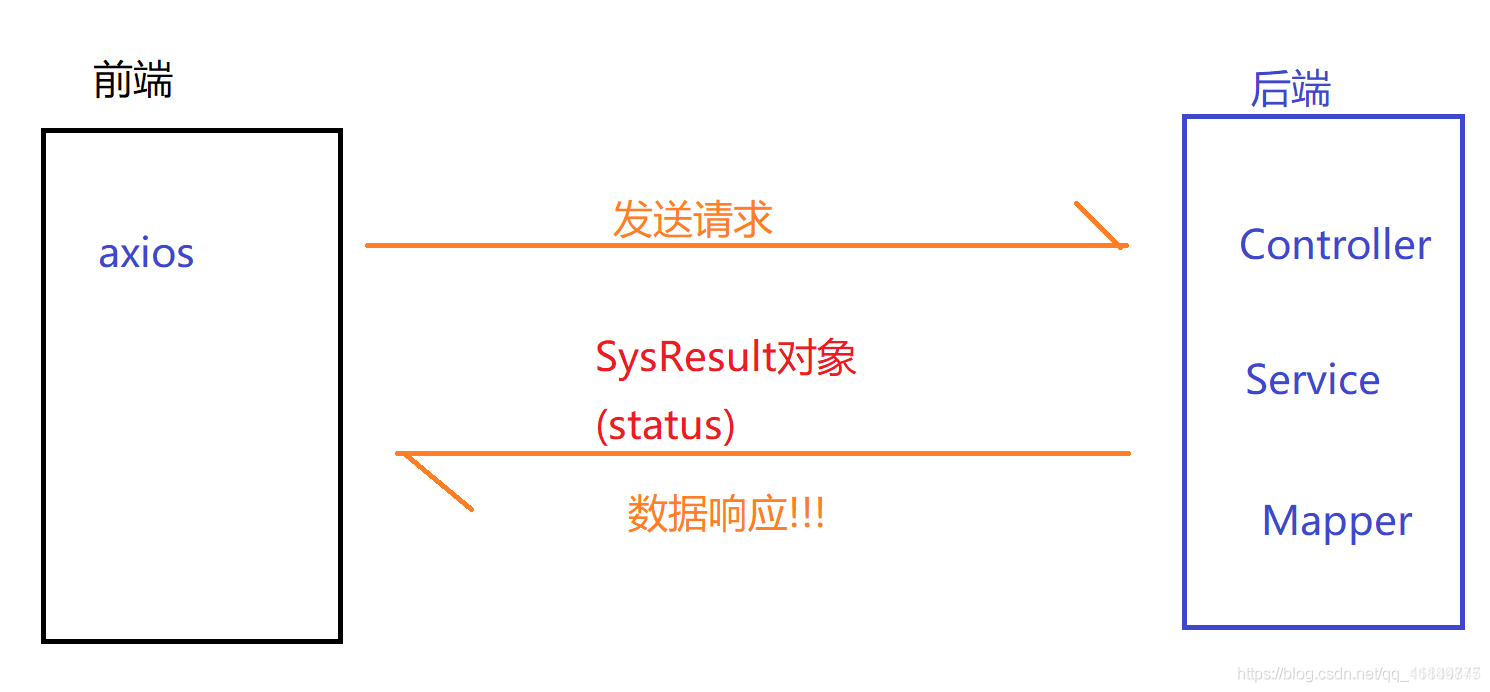
ToKen
Note: front end server: when the user logs in, enter the user name and password for verification!!!
Send the data information to the back-end server for verification and query the database
Assumption: user name and password are correct!!! The page should jump to the home page of the system "/ home"
Question: can I directly enter "/ home" in the browser? Theoretically, it is not allowed to access this page!
Solution:
The back-end server returns a unique token data. As long as the front-end carries the token, it is considered that the user has logged in You can jump to the page
Permission Operation prototype!!!
Summary: token is used to identify that the user has logged in!!!
MD5
MD5 message digest algorithm (English: MD5 message digest algorithm), a widely used cryptographic hash function, can generate a 128 bit (16 byte) hash value to ensure the integrity and consistency of information transmission. MD5 was developed by American Cryptologist Ronald levist (Ronald Linn Rivest) was designed and published in 1992 to replace MD4 algorithm. The program of this algorithm was standardized in RFC 1321 standard. After 1996, the algorithm was proved to have weaknesses and can be cracked. For data requiring high security, experts generally recommend to use other algorithms, such as SHA-2. In 2004, it was proved that MD5 algorithm can not prevent collision Therefore, it is not suitable for security authentication, such as SSL public key authentication or digital signature.
Summary:
1.MD5 information summary algorithm
2. Generally, the data can be MD5 encrypted to generate "digital fingerprint"
3. At this stage, md5 encryption algorithm is applied to major websites
4. After MD5 encryption, in theory, it cannot be transformed from ciphertext to plaintext and cannot be decompiled
5. Limit the number of password entries!!! Lock the account 3-5 times!!!
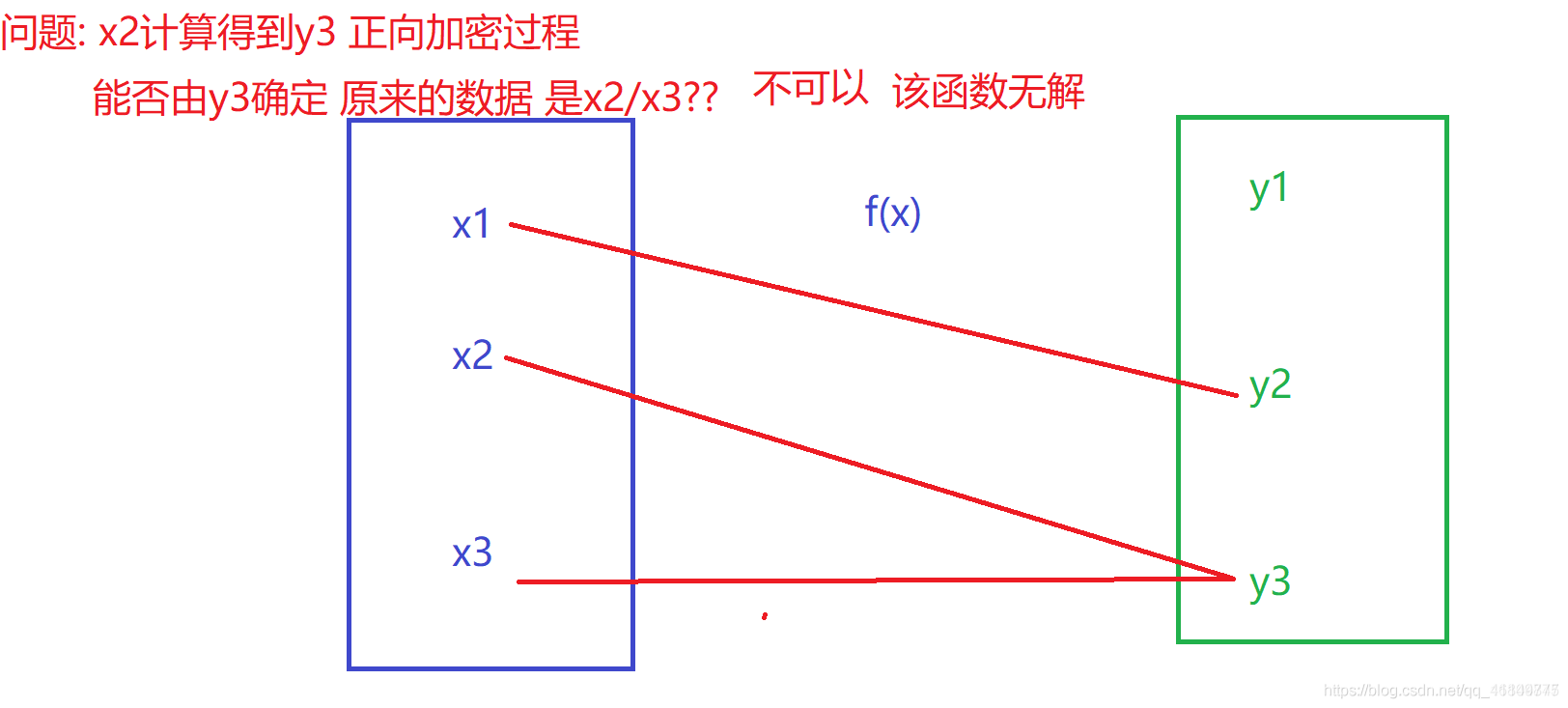
Core algorithm:
Knowledge review: high school function!!!
What is a function: given the unknown x, a unique result y is obtained through function calculation
Essence: the essence of MD5 is hash algorithm!!!
Session
Session: in computers, especially in network applications, it is called "session control". The session object stores the properties and configuration information required for a specific user session. In this way, when the user jumps between the Web pages of the application, the variables stored in the session object will not be lost, but will exist throughout the user session. When a user requests a Web page from an application, if the user does not have a session, the Web server will automatically create a session object. When a session expires or is abandoned, the server terminates the session. One of the most common uses of the session object is to store user preferences. For example, if you indicate that you don't like viewing drawings, you can store this information in the session object. For more information about using session objects, see "managing sessions" in the ASP applications section. Note that session state is reserved only in browsers that support cookie s.
Summary:
- Session is session control
- Session allows users to store data in the browser's Session Storage
- During the Session life cycle, the data of the whole Session is valid. If the Session window is closed, the data is cleared
- Session data is stored in the browser's memory (front-end)
Cookie
Cookie s, sometimes in the plural. The type is "small text file", which is the data (usually encrypted) stored on the user's local terminal by some websites in order to identify the user's identity and track the Session, and the information temporarily or permanently saved by the user's client computer [1].
Summary:
- A Cookie is a text file
- Cookie s store user information (encrypted data is more secure)
- Cookie s can be saved to the user's computer terminal to temporarily / permanently store information
Session and Cookie
User login information of mobile banking?? session requires high security
Shopping websites require users to log in without secret for seven days?? Use cookies for storage!!
Login information of the company's financial system? Session is recommended
Movie: there is no absolutely safe system
Summary: if you have high requirements for data security, use Session If a large number of queried data (unimportant) are stored, cookies are generally used for storage
Self management table design
Case: there is a business logic parent-child relationship with three levels. Q: how to design a table?
Business relationship: grandfather father son grandson great grandson
Idea 1: define three tables: grandfather table (ID) - father table (parent_id) - son table (parent_id - father)
Complex data structure!!! Not easy to expand!!!
Idea 2: define a table (ID ------ parent_id)
Requirement: each ID should have its own parent_id
Conclusion: if there is a parent-child relationship, the parent is used again_ ID Self correlation mode
Mybatis Puls paging
/**
* Paging query in MP mode
* Requirements:
* 1.Paging query list < user >
* 2.Gets the total number of records encapsulating the pageResult object
*
* @param pageResult
* @return
*/
@Override
public PageResult getUserList(PageResult pageResult) {
//The first part realizes data encapsulation!!!
int pageNum = pageResult.getPageNum(); //Get page
int pageSize = pageResult.getPageSize();//Acquisition conditions
//Parameter 1: page paging object
Page<User> page = new Page(pageNum,pageSize);
//Parameter 2: paged query criteria username fuzzy query
//Problem: if the user does not pass the query like keyword splicing parameter
//Dynamic splicing: pass parameter splicing like condition: true splicing like condition
// false do not splice the like keyword
QueryWrapper<User> queryWrapper = new QueryWrapper<>();
//Judge whether the user transfers parameters. If the parameter is transferred, it returns true; otherwise, it returns false
boolean flag = StringUtils.hasLength(pageResult.getQuery());
queryWrapper.like(flag,"username",pageResult.getQuery());
//Rule: page2 parameters: total / records after paging returned according to paging query 4 parameters
page = userMapper.selectPage(page,queryWrapper);
//Get the desired result according to the paging object
List<User> userList = page.getRecords();
long total = page.getTotal();
pageResult.setTotal(total).setRows(userList);
return pageResult;
}
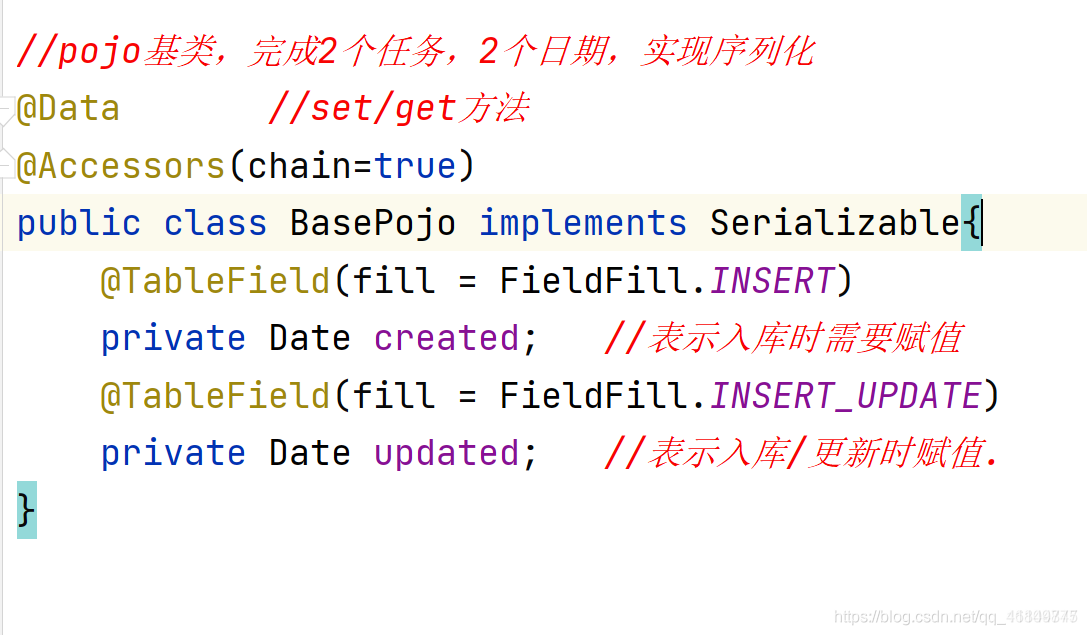
Data auto fill
- Automatic filling of data
1.1 description of business requirements
Requirement: each table in the database contains the field of creation time / modification time If you manually maintain the time information every time you operate the table Response development efficiency Can the strategy be optimized
Solution: MybatisPlus realizes automatic filling function
1.2 MPAPI description
1.2. 1 grammar rules
Implementation of meta object processor interface: com baomidou. mybatisplus. core. handlers. MetaObjectHandler
The annotation filling field @ TableField(... fill = FieldFill.INSERT) generator policy can also be configured!
1.2. 2 add notes
Note: the created/updated. Fields need to be automatically filled in for the new operation
The modified operation needs to be automatically populated with updated
@Component //Give the object to the Spring container for management
public class MyMetaObjectHandler implements MetaObjectHandler {
//When the database is added, the API call is automatically called without asking why
//The metaObject object is automatically populated by MP. The configuration has the default behavior
@Override
public void insertFill(MetaObject metaObject) {
//Get current time
Date date = new Date();
this.setFieldValByName("created", date, metaObject);
this.setFieldValByName("updated", date, metaObject);
}
//Automatically called when the database is modified
@Override
public void updateFill(MetaObject metaObject) {
//Get current time
Date date = new Date();
this.setFieldValByName("updated", date, metaObject);
}
}
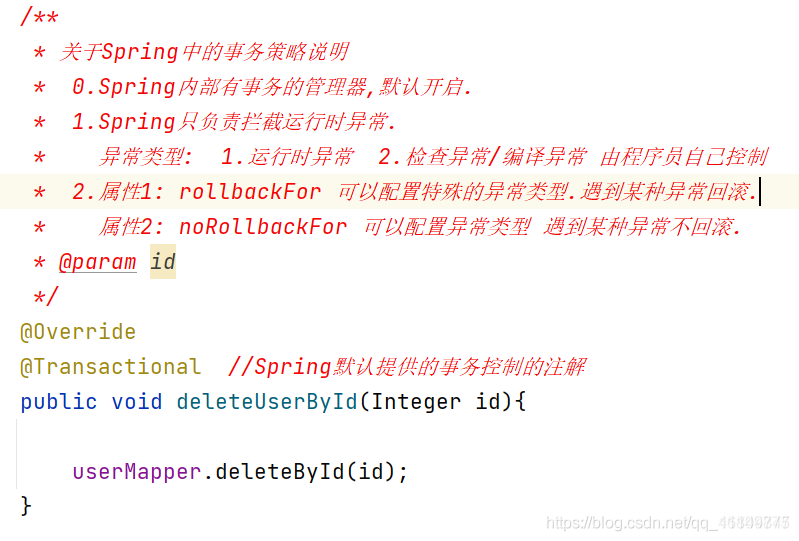
Thing control
3.1 what is a transaction
Note: if the background server performs normally, the business is correct and the transaction is committed If business execution fails The transaction should be rolled back
3.2 business test of existing code
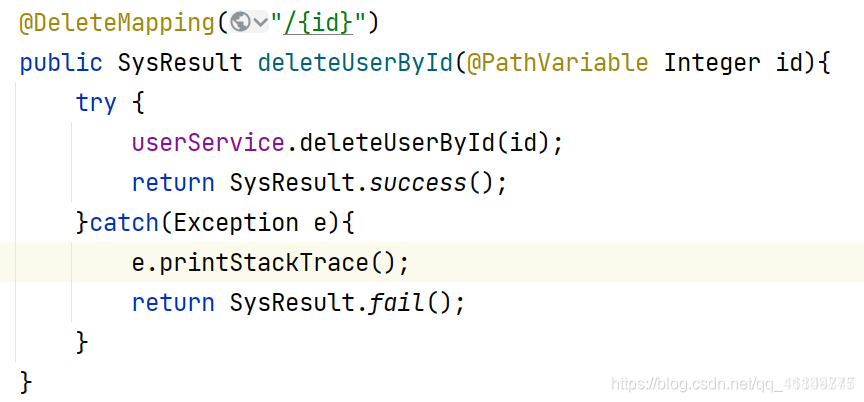
Note: as shown in the figure, if there is an error message during program execution Transaction rollback should be implemented However, two problems were found in the existing code
1: Nothing was added
2. After the background server reports an error, the user does not prompt
How to use
@Transactional annotation
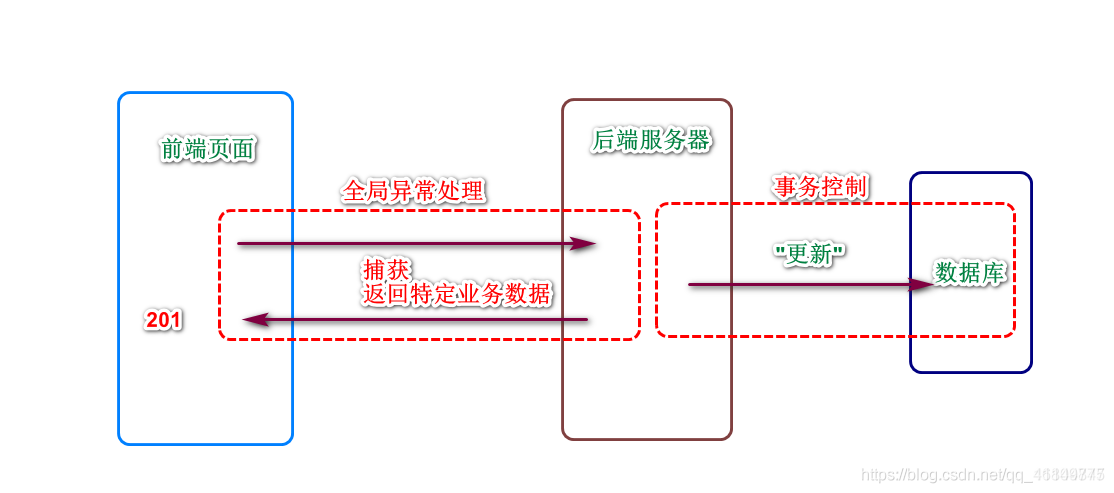
Global exception handling mechanism
Description: general control exception information In general, you need to add the try catch usage
Disadvantages: all methods require try catch control It will inevitably lead to the complex structure of the code
Solution: Spring provides a rule - based global exception handling mechanism
package com.jt.advice;
import com.jt.vo.SysResult;
import org.springframework.web.bind.annotation.ControllerAdvice;
import org.springframework.web.bind.annotation.ExceptionHandler;
import org.springframework.web.bind.annotation.RestControllerAdvice;
/**
* Spring In order to integrate the handling of global exceptions, the following annotations are developed
* 1.@RestControllerAdvice //Defines the JSON string of the return value of the global exception handling class
* 2.@ExceptionHandler Identifies the type of the intercepted exception. If the types match, the method is executed
*/
@RestControllerAdvice
public class MyExceptionAdvice {
//Writing method: 1 Runtime exception (general) 2 Custom exception information 3 Intercept all exceptions class
@ExceptionHandler(RuntimeException.class)
public Object exception(Exception e){
e.printStackTrace(); //Output exception information
//Requirement: if an exception is encountered, the user should be prompted with 201 / failure information
return SysResult.fail();
}
}
Data optimization
Idea 1: reduce the number of connections to the database
Idea 2: structure control from Java code - set correlation