I. ingress
1 ingress
Ingress is an API object that manages the external access of services in the cluster. The typical access method is HTTP.
Ingress provides load balancing, SSL finalization, and name based virtual hosting
1.1 description
Node( Node): Kubernetes One of the working machines in the cluster is a part of the cluster. Cluster( Cluster): A set of operations by Kubernetes Managed container application node. In this example and in most common Kubernetes In the deployment environment, the nodes in the cluster are not in the public network. Edge router( Edge router): A router that enforces firewall policies in a cluster( router). It can be a gateway managed by a cloud provider or physical hardware. Cluster network( Cluster network): A set of logical or physical connections according to Kubernetes The network model realizes communication within the cluster. Service( Service): Kubernetes The service uses the tag selection operator( selectors)Set of identifiers Pod. Unless otherwise stated, it is assumed that the service has only virtual nodes that can be routed in the cluster network IP.
1.2 what is ingress?
Ingress exposes HTTP and HTTPS routes from outside the cluster to services within the cluster. Traffic routing is controlled by rules defined on the ingress resource.
The following is a simple progress example that sends all traffic to the same Service:
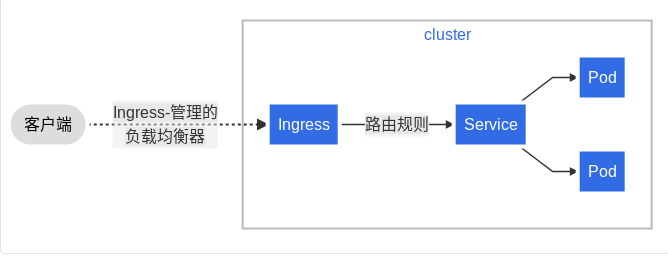
The Ingress service can be configured to provide externally accessible URL s, load balancing traffic, terminate SSL/TLS, and provide name based virtual hosts.
The Ingress controller is usually responsible for achieving Ingress through the load balancer, although it can also configure edge routers or other front ends to help handle traffic.
Ingress does not expose any ports or protocols. When exposing services other than HTTP and HTTPS to the Internet, you usually use
Service.Type=NodePort or service Type = service of type loadbalancer.
1.3 environmental preparation
You must have an Ingress controller to meet the requirements of Ingress. Creating only the progress resource itself has no effect.
You may need to deploy an Ingress controller, such as Ingress nginx. You can choose from many Ingress controllers.
Ideally, all Ingress controllers should comply with the reference specifications. But in fact, different Ingress controllers operate slightly differently.
1.4 progress rules
Each HTTP rule contains the following information:
Optional host. In this example, no host,Therefore, the rule applies by specifying IP All inbound addresses HTTP signal communication. If provided host(for example foo.bar.com),be rules Applicable to this host. Path list paths(For example,/testpath),Each path has a serviceName and servicePort Defined Association backend. Before the load balancer directs traffic to the referenced service, both the host and the path must match the content of the incoming request. backend(Back end) yes Service The combination of service and port names described in the document. With rules host and path Matching pair Ingress of HTTP(and HTTPS )The request will be sent to the listed backend.
Usually, the default backend is configured in the Ingress controller to serve any request that does not conform to the path in the protocol.
1.5 DefaultBackend
Ingress without rules sends all traffic to the same default backend. defaultBackend is usually a configuration option for the ingress controller, not specified in the ingress resource.
If neither hosts nor paths matches the HTTP request in the progress object, the traffic will be routed to the default backend.
1.6 resource backend
The resource backend is an ObjectRef that points to another Kubernetes in the same namespace as an Ingress object. Resource and Service configurations are mutually exclusive. When both are set, they will fail to pass the legitimacy check. A common use of a resource backend is to direct all inbound data to an object storage backend with static assets.
1.7 path type
Each path in progress needs a corresponding Path Type. The path with pathType not explicitly set cannot pass the legitimacy check. There are currently three supported path types:
ImplementationSpecific: for this path type, the matching method depends on the IngressClass. The specific implementation can treat it as a separate pathType or the same as the Prefix or Exact type.
Exact: exactly matches the URL path and is case sensitive.
Prefix: matches based on the URL path prefix separated by /. Matching is case sensitive and is done one by one for the elements in the path. The path element refers to the list of labels in the path separated by the / separator. If each p is the element prefix of the request path p, the request matches the path p.
Note: if the last element of the path is a substring of the last element in the request path, it will not match (for example: / foo/bar matches / foo/bar/baz, but does not match / foo/barbaz).
1.8 simple fan out
A fan out configuration routes traffic from the same IP address to multiple services according to the requested HTTP URI. Ingress allows you to minimize the number of load balancers. For example, this setting:

1.9 name based virtual hosting
Name based virtual hosts support routing HTTP traffic for multiple host names to the same IP address.

1.9 TLS
You can protect progress by setting a Secret containing TLS private key and certificate. Ingress only supports a single TLS port 443 and assumes that the TLS connection terminates at the ingress node (the traffic with the Service and its Pod is transmitted in clear text). If different hosts are specified in the TLS configuration section of ingress, they will be multiplexed on the same port according to the host name specified through the SNI TLS extension (if the ingress controller supports SNI). TLS Secret must contain a file named TLS CRT and TLS Key name of the key. This data contains the certificate and private key for TLS
explain: Note that cannot be used on default rules TLS,Because you need to issue certificates for all possible subdomains. So, tls Nodal hosts The value of requires a field rules Nodal host Exactly.
Note: there are differences in TLS functions supported by various Ingress controllers.
1.10 load balancing
When the Ingress controller starts booting, it uses some load balancing policy settings applicable to all Ingress, such as load balancing algorithm, back-end weight scheme and others. More advanced load balancing concepts (such as persistent sessions, dynamic weights) have not been exposed through Ingress. You can get these functions through the load balancer for services.
It is worth noting that although the health check is not directly exposed through Ingress, there are parallel concepts in Kubernetes, such as readiness check, which allow you to achieve the same purpose.
II. Ingress controller
1 Ingress controller
In order for the Ingress resource to work, the cluster must have an Ingress controller running.
Unlike other types of controllers that run as part of the Kube controller manager executable, the progress controller does not start automatically with the cluster. Based on this page, you can select the best implementation of the ingress controller for your cluster.
As a project, Kubernetes currently supports and maintains AWS, GCE and nginx Ingress controllers.
2 using multiple Ingress controllers
You can deploy any number of ingress controllers in the cluster. When creating an ingress, you should use the appropriate ingress Class annotates each ingress to indicate which ingress controller should be used if there are multiple ingress controllers in the cluster.
If you do not define Ingress Class, the cloud provider may use the default Ingress controller.
Ideally, all Ingress controllers should meet this specification, but the operation of various Ingress controllers is slightly different.
Note: make sure you check the documentation for the ingress controller to see the considerations for selecting it.
3. Inress nginx controller
3.1 importing images
[root@server1 ~]# docker load -i ingress-nginx-v0.48.1.tar 5a02fda3e930: Loading layer 118.5MB/118.5MB 1f8bcc0f3b79: Loading layer 4.096kB/4.096kB d5e4519c2dc5: Loading layer 37.93MB/37.93MB feb9e468234b: Loading layer 20.85MB/20.85MB 0588019ee2b1: Loading layer 3.538MB/3.538MB f40af979a380: Loading layer 294.9kB/294.9kB d54a23db80e8: Loading layer 6.543MB/6.543MB 376dfd7f7c2e: Loading layer 36.15MB/36.15MB 00a7fcfa3488: Loading layer 3.074MB/3.074MB a6b8ae1d26a4: Loading layer 4.096kB/4.096kB f51616668e99: Loading layer 49.39MB/49.39MB 6d051c91466c: Loading layer 3.584kB/3.584kB Loaded image: reg.westos.org/ingress-nginx/controller:v0.48.1 7a5b9c0b4b14: Loading layer 3.031MB/3.031MB 87c9f1582ca0: Loading layer 15.44MB/15.44MB dd7be1bf03ab: Loading layer 27.83MB/27.83MB Loaded image: reg.westos.org/ingress-nginx/kube-webhook-certgen:v1.5.1
3.2 labeling images
[root@server1 ~]# docker tag reg.westos.org/ingress-nginx/controller:v0.48.1 reg.westos.org/ingress-nginx/controller:v0.48.1 [root@server1 ~]# docker tag reg.westos.org/ingress-nginx/kube-webhook-certgen:v1.5.1 reg.westos.org/ingress-nginx/kube-webhook-certgen:v1.5.1
3.3 uploading images
[root@server1 ~]# docker push reg.westos.org/ingress-nginx/controller:v0.48.1 The push refers to repository [reg.westos.org/ingress-nginx/controller] 6d051c91466c: Pushed f51616668e99: Pushed a6b8ae1d26a4: Pushed 00a7fcfa3488: Pushed 376dfd7f7c2e: Pushed d54a23db80e8: Pushed f40af979a380: Pushed 0588019ee2b1: Pushed feb9e468234b: Pushed d5e4519c2dc5: Pushed 1f8bcc0f3b79: Pushed 5a02fda3e930: Pushed b2d5eeeaba3a: Mounted from metallb/controller v0.48.1: digest: sha256:6fb617a01cf858d3908bdbabba2de63d9e4f46b26a18a7fc40f49a9b3cc825ad size: 3050 [root@server1 ~]# docker push reg.westos.org/ingress-nginx/kube-webhook-certgen:v1.5.1 The push refers to repository [reg.westos.org/ingress-nginx/kube-webhook-certgen] dd7be1bf03ab: Pushed 87c9f1582ca0: Pushed 7a5b9c0b4b14: Pushed v1.5.1: digest: sha256:784853e84a0223f34ea58fe36766c2dbeb129b125d25f16b8468c903262b77f6 size: 949
3.4 warehouse view image
3.5 using ingress nginx controller
Edit depoly Yaml file
[root@server1 ingress]# cat deploy.yaml
apiVersion: v1
kind: Namespace
metadata:
name: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
---
# Source: ingress-nginx/templates/controller-serviceaccount.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
helm.sh/chart: ingress-nginx-3.34.0
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/version: 0.48.1
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/component: controller
name: ingress-nginx
namespace: ingress-nginx
automountServiceAccountToken: true
---
# Source: ingress-nginx/templates/controller-configmap.yaml
apiVersion: v1
kind: ConfigMap
metadata:
labels:
helm.sh/chart: ingress-nginx-3.34.0
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/version: 0.48.1
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/component: controller
name: ingress-nginx-controller
namespace: ingress-nginx
data:
---
# Source: ingress-nginx/templates/clusterrole.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
helm.sh/chart: ingress-nginx-3.34.0
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/version: 0.48.1
app.kubernetes.io/managed-by: Helm
name: ingress-nginx
rules:
- apiGroups:
- ''
resources:
- configmaps
- endpoints
- nodes
- pods
- secrets
verbs:
- list
- watch
- apiGroups:
- ''
resources:
- nodes
verbs:
- get
- apiGroups:
- ''
resources:
- services
verbs:
- get
- list
- watch
- apiGroups:
- extensions
- networking.k8s.io # k8s 1.14+
resources:
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- ''
resources:
- events
verbs:
- create
- patch
- apiGroups:
- extensions
- networking.k8s.io # k8s 1.14+
resources:
- ingresses/status
verbs:
- update
- apiGroups:
- networking.k8s.io # k8s 1.14+
resources:
- ingressclasses
verbs:
- get
- list
- watch
---
# Source: ingress-nginx/templates/clusterrolebinding.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
helm.sh/chart: ingress-nginx-3.34.0
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/version: 0.48.1
app.kubernetes.io/managed-by: Helm
name: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: ingress-nginx
subjects:
- kind: ServiceAccount
name: ingress-nginx
namespace: ingress-nginx
---
# Source: ingress-nginx/templates/controller-role.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
labels:
helm.sh/chart: ingress-nginx-3.34.0
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/version: 0.48.1
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/component: controller
name: ingress-nginx
namespace: ingress-nginx
rules:
- apiGroups:
- ''
resources:
- namespaces
verbs:
- get
- apiGroups:
- ''
resources:
- configmaps
- pods
- secrets
- endpoints
verbs:
- get
- list
- watch
- apiGroups:
- ''
resources:
- services
verbs:
- get
- list
- watch
- apiGroups:
- extensions
- networking.k8s.io # k8s 1.14+
resources:
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- extensions
- networking.k8s.io # k8s 1.14+
resources:
- ingresses/status
verbs:
- update
- apiGroups:
- networking.k8s.io # k8s 1.14+
resources:
- ingressclasses
verbs:
- get
- list
- watch
- apiGroups:
- ''
resources:
- configmaps
resourceNames:
- ingress-controller-leader-nginx
verbs:
- get
- update
- apiGroups:
- ''
resources:
- configmaps
verbs:
- create
- apiGroups:
- ''
resources:
- events
verbs:
- create
- patch
---
# Source: ingress-nginx/templates/controller-rolebinding.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
helm.sh/chart: ingress-nginx-3.34.0
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/version: 0.48.1
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/component: controller
name: ingress-nginx
namespace: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: ingress-nginx
subjects:
- kind: ServiceAccount
name: ingress-nginx
namespace: ingress-nginx
---
# Source: ingress-nginx/templates/controller-service-webhook.yaml
apiVersion: v1
kind: Service
metadata:
labels:
helm.sh/chart: ingress-nginx-3.34.0
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/version: 0.48.1
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/component: controller
name: ingress-nginx-controller-admission
namespace: ingress-nginx
spec:
type: ClusterIP
ports:
- name: https-webhook
port: 443
targetPort: webhook
selector:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/component: controller
---
# Source: ingress-nginx/templates/controller-service.yaml
apiVersion: v1
kind: Service
metadata:
annotations:
labels:
helm.sh/chart: ingress-nginx-3.34.0
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/version: 0.48.1
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/component: controller
name: ingress-nginx-controller
namespace: ingress-nginx
spec:
type: NodePort
ports:
- name: http
port: 80
protocol: TCP
targetPort: http
- name: https
port: 443
protocol: TCP
targetPort: https
selector:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/component: controller
---
# Source: ingress-nginx/templates/controller-deployment.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
helm.sh/chart: ingress-nginx-3.34.0
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/version: 0.48.1
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/component: controller
name: ingress-nginx-controller
namespace: ingress-nginx
spec:
selector:
matchLabels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/component: controller
revisionHistoryLimit: 10
minReadySeconds: 0
template:
metadata:
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/component: controller
spec:
dnsPolicy: ClusterFirst
containers:
- name: controller
image: ingress-nginx/controller:v0.48.1
imagePullPolicy: IfNotPresent
lifecycle:
preStop:
exec:
command:
- /wait-shutdown
args:
- /nginx-ingress-controller
- --election-id=ingress-controller-leader
- --ingress-class=nginx
- --configmap=$(POD_NAMESPACE)/ingress-nginx-controller
- --validating-webhook=:8443
- --validating-webhook-certificate=/usr/local/certificates/cert
- --validating-webhook-key=/usr/local/certificates/key
securityContext:
capabilities:
drop:
- ALL
add:
- NET_BIND_SERVICE
runAsUser: 101
allowPrivilegeEscalation: true
env:
- name: POD_NAME
valueFrom:
fieldRef:
fieldPath: metadata.name
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
- name: LD_PRELOAD
value: /usr/local/lib/libmimalloc.so
livenessProbe:
failureThreshold: 5
httpGet:
path: /healthz
port: 10254
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 1
readinessProbe:
failureThreshold: 3
httpGet:
path: /healthz
port: 10254
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 1
ports:
- name: http
containerPort: 80
protocol: TCP
- name: https
containerPort: 443
protocol: TCP
- name: webhook
containerPort: 8443
protocol: TCP
volumeMounts:
- name: webhook-cert
mountPath: /usr/local/certificates/
readOnly: true
resources:
requests:
cpu: 100m
memory: 90Mi
nodeSelector:
kubernetes.io/os: linux
serviceAccountName: ingress-nginx
terminationGracePeriodSeconds: 300
volumes:
- name: webhook-cert
secret:
secretName: ingress-nginx-admission
---
# Source: ingress-nginx/templates/admission-webhooks/validating-webhook.yaml
# before changing this value, check the required kubernetes version
# https://kubernetes.io/docs/reference/access-authn-authz/extensible-admission-controllers/#prerequisites
apiVersion: admissionregistration.k8s.io/v1
kind: ValidatingWebhookConfiguration
metadata:
labels:
helm.sh/chart: ingress-nginx-3.34.0
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/version: 0.48.1
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/component: admission-webhook
name: ingress-nginx-admission
webhooks:
- name: validate.nginx.ingress.kubernetes.io
matchPolicy: Equivalent
rules:
- apiGroups:
- networking.k8s.io
apiVersions:
- v1beta1
operations:
- CREATE
- UPDATE
resources:
- ingresses
failurePolicy: Fail
sideEffects: None
admissionReviewVersions:
- v1
- v1beta1
clientConfig:
service:
namespace: ingress-nginx
name: ingress-nginx-controller-admission
path: /networking/v1beta1/ingresses
---
# Source: ingress-nginx/templates/admission-webhooks/job-patch/serviceaccount.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: ingress-nginx-admission
namespace: ingress-nginx
annotations:
helm.sh/hook: pre-install,pre-upgrade,post-install,post-upgrade
helm.sh/hook-delete-policy: before-hook-creation,hook-succeeded
labels:
helm.sh/chart: ingress-nginx-3.34.0
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/version: 0.48.1
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/component: admission-webhook
---
# Source: ingress-nginx/templates/admission-webhooks/job-patch/clusterrole.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: ingress-nginx-admission
annotations:
helm.sh/hook: pre-install,pre-upgrade,post-install,post-upgrade
helm.sh/hook-delete-policy: before-hook-creation,hook-succeeded
labels:
helm.sh/chart: ingress-nginx-3.34.0
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/version: 0.48.1
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/component: admission-webhook
rules:
- apiGroups:
- admissionregistration.k8s.io
resources:
- validatingwebhookconfigurations
verbs:
- get
- update
---
# Source: ingress-nginx/templates/admission-webhooks/job-patch/clusterrolebinding.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: ingress-nginx-admission
annotations:
helm.sh/hook: pre-install,pre-upgrade,post-install,post-upgrade
helm.sh/hook-delete-policy: before-hook-creation,hook-succeeded
labels:
helm.sh/chart: ingress-nginx-3.34.0
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/version: 0.48.1
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/component: admission-webhook
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: ingress-nginx-admission
subjects:
- kind: ServiceAccount
name: ingress-nginx-admission
namespace: ingress-nginx
---
# Source: ingress-nginx/templates/admission-webhooks/job-patch/role.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
name: ingress-nginx-admission
namespace: ingress-nginx
annotations:
helm.sh/hook: pre-install,pre-upgrade,post-install,post-upgrade
helm.sh/hook-delete-policy: before-hook-creation,hook-succeeded
labels:
helm.sh/chart: ingress-nginx-3.34.0
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/version: 0.48.1
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/component: admission-webhook
rules:
- apiGroups:
- ''
resources:
- secrets
verbs:
- get
- create
---
# Source: ingress-nginx/templates/admission-webhooks/job-patch/rolebinding.yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: ingress-nginx-admission
namespace: ingress-nginx
annotations:
helm.sh/hook: pre-install,pre-upgrade,post-install,post-upgrade
helm.sh/hook-delete-policy: before-hook-creation,hook-succeeded
labels:
helm.sh/chart: ingress-nginx-3.34.0
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/version: 0.48.1
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/component: admission-webhook
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: ingress-nginx-admission
subjects:
- kind: ServiceAccount
name: ingress-nginx-admission
namespace: ingress-nginx
---
# Source: ingress-nginx/templates/admission-webhooks/job-patch/job-createSecret.yaml
apiVersion: batch/v1
kind: Job
metadata:
name: ingress-nginx-admission-create
namespace: ingress-nginx
annotations:
helm.sh/hook: pre-install,pre-upgrade
helm.sh/hook-delete-policy: before-hook-creation,hook-succeeded
labels:
helm.sh/chart: ingress-nginx-3.34.0
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/version: 0.48.1
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/component: admission-webhook
spec:
template:
metadata:
name: ingress-nginx-admission-create
labels:
helm.sh/chart: ingress-nginx-3.34.0
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/version: 0.48.1
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/component: admission-webhook
spec:
containers:
- name: create
image: ingress-nginx/kube-webhook-certgen:v1.5.1
imagePullPolicy: IfNotPresent
args:
- create
- --host=ingress-nginx-controller-admission,ingress-nginx-controller-admission.$(POD_NAMESPACE).svc
- --namespace=$(POD_NAMESPACE)
- --secret-name=ingress-nginx-admission
env:
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
restartPolicy: OnFailure
serviceAccountName: ingress-nginx-admission
securityContext:
runAsNonRoot: true
runAsUser: 2000
---
# Source: ingress-nginx/templates/admission-webhooks/job-patch/job-patchWebhook.yaml
apiVersion: batch/v1
kind: Job
metadata:
name: ingress-nginx-admission-patch
namespace: ingress-nginx
annotations:
helm.sh/hook: post-install,post-upgrade
helm.sh/hook-delete-policy: before-hook-creation,hook-succeeded
labels:
helm.sh/chart: ingress-nginx-3.34.0
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/version: 0.48.1
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/component: admission-webhook
spec:
template:
metadata:
name: ingress-nginx-admission-patch
labels:
helm.sh/chart: ingress-nginx-3.34.0
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/instance: ingress-nginx
app.kubernetes.io/version: 0.48.1
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/component: admission-webhook
spec:
containers:
- name: patch
image: ingress-nginx/kube-webhook-certgen:v1.5.1
imagePullPolicy: IfNotPresent
args:
- patch
- --webhook-name=ingress-nginx-admission
- --namespace=$(POD_NAMESPACE)
- --patch-mutating=false
- --secret-name=ingress-nginx-admission
- --patch-failure-policy=Fail
env:
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
restartPolicy: OnFailure
serviceAccountName: ingress-nginx-admission
securityContext:
runAsNonRoot: true
runAsUser: 2000
Pull up the pod node
[root@server1 ingress]# kubectl apply -f deploy.yaml namespace/ingress-nginx created serviceaccount/ingress-nginx created configmap/ingress-nginx-controller created clusterrole.rbac.authorization.k8s.io/ingress-nginx created clusterrolebinding.rbac.authorization.k8s.io/ingress-nginx created role.rbac.authorization.k8s.io/ingress-nginx created rolebinding.rbac.authorization.k8s.io/ingress-nginx created service/ingress-nginx-controller-admission created service/ingress-nginx-controller created deployment.apps/ingress-nginx-controller created validatingwebhookconfiguration.admissionregistration.k8s.io/ingress-nginx-admission created serviceaccount/ingress-nginx-admission created clusterrole.rbac.authorization.k8s.io/ingress-nginx-admission created clusterrolebinding.rbac.authorization.k8s.io/ingress-nginx-admission created role.rbac.authorization.k8s.io/ingress-nginx-admission created rolebinding.rbac.authorization.k8s.io/ingress-nginx-admission created job.batch/ingress-nginx-admission-create created job.batch/ingress-nginx-admission-patch created
View the generated namespace status
[root@server1 ingress]# kubectl get ns NAME STATUS AGE default Active 4d15h ingress-nginx Active 3m43s kube-node-lease Active 4d15h kube-public Active 4d15h kube-system Active 4d15h metallb-system Active 46h
View information about ingress nainx
[root@server1 ingress]# kubectl -n ingress-nginx get all NAME READY STATUS RESTARTS AGE pod/ingress-nginx-admission-create-h5km9 0/1 Completed 0 4m26s pod/ingress-nginx-admission-patch-n892n 0/1 Completed 0 4m26s pod/ingress-nginx-controller-5f476b6d87-plm4l 1/1 Running 0 4m26s NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service/ingress-nginx-controller NodePort 10.108.124.3 <none> 80:31673/TCP,443:31585/TCP 4m27s service/ingress-nginx-controller-admission ClusterIP 10.105.9.88 <none> 443/TCP 4m27s NAME READY UP-TO-DATE AVAILABLE AGE deployment.apps/ingress-nginx-controller 1/1 1 1 4m27s NAME DESIRED CURRENT READY AGE replicaset.apps/ingress-nginx-controller-5f476b6d87 1 1 1 4m27s NAME COMPLETIONS DURATION AGE job.batch/ingress-nginx-admission-create 1/1 7s 4m26s job.batch/ingress-nginx-admission-patch 1/1 7s 4m26s
View svc exposed ports
[root@server1 ingress]# kubectl -n ingress-nginx get svc NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE ingress-nginx-controller NodePort 10.108.124.3 <none> 80:31673/TCP,443:31585/TCP 5m16s ingress-nginx-controller-admission ClusterIP 10.105.9.88 <none> 443/TCP 5m16s
Modify the ingress nginx controller configuration
type: LoadBalancer
[root@server1 ingress]# kubectl -n ingress-nginx edit svc ingress-nginx-controller service/ingress-nginx-controller edited
You can see that the loadbalancer allocates ip 172.25.7.100
[root@server1 ingress]# kubectl -n ingress-nginx get svc NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE ingress-nginx-controller LoadBalancer 10.108.124.3 172.25.7.100 80:31673/TCP,443:31585/TCP 76m ingress-nginx-controller-admission ClusterIP 10.105.9.88 <none> 443/TCP 76m
Create pod: nginx myapp
[root@server1 ingress]# cat deployment.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
labels:
app: nginx
spec:
replicas: 3
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: myapp:v1
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: myapp-deployment
labels:
app: myapp
spec:
replicas: 3
selector:
matchLabels:
app: myapp
template:
metadata:
labels:
app: myapp
spec:
containers:
- name: myapp
image: myapp:v2
View pod
[root@server1 ingress]# kubectl apply -f deployment.yaml deployment.apps/nginx-deployment created deployment.apps/myapp-deployment created [root@server1 ingress]# kubectl get pod NAME READY STATUS RESTARTS AGE demo-5b4fc8bb88-5lt6g 1/1 Running 3 2d20h demo-5b4fc8bb88-whjwj 1/1 Running 3 2d20h myapp-deployment-67f8c948cf-dqjjh 0/1 ContainerCreating 0 3s myapp-deployment-67f8c948cf-l85vw 0/1 ContainerCreating 0 3s myapp-deployment-67f8c948cf-rbgth 0/1 ContainerCreating 0 3s nginx-deployment-6456d7c676-6zjx2 0/1 ContainerCreating 0 3s nginx-deployment-6456d7c676-7j7hb 0/1 ContainerCreating 0 3s nginx-deployment-6456d7c676-ql5qn 0/1 ContainerCreating 0 3s replicaset-example-kgkh5 1/1 Running 3 2d19h
Create service
[root@server1 ingress]# cat svc.yaml
apiVersion: v1
kind: Service
metadata:
name: nginx-svc
spec:
ports:
- protocol: TCP
port: 80
targetPort: 80
selector:
app: nginx
---
apiVersion: v1
kind: Service
metadata:
name: myapp-svc
spec:
ports:
- protocol: TCP
port: 80
targetPort: 80
selector:
app: myapp
View service
[root@server1 ingress]# kubectl apply -f svc.yaml service/nginx-svc created service/myapp-svc created [root@server1 ingress]# kubectl get svc NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 4d17h myapp-svc ClusterIP 10.101.91.109 <none> 80/TCP 4s nginx-svc ClusterIP 10.97.120.247 <none> 80/TCP 4s
ingress. Domain name matching is given under YML to match the service
[root@server1 ingress]# cat ingress.yaml
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-nginx
spec:
# tls:
rules:
- host: www1.westos.org
http:
paths:
- path: /
backend:
serviceName: nginx-svc
servicePort: 80
---
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-myapp
spec:
rules:
- host: www2.westos.org
http:
paths:
- path: /
backend:
serviceName: myapp-svc
servicePort: 80
View ingress information
[root@server1 ingress]# kubectl get ingress NAME CLASS HOSTS ADDRESS PORTS AGE ingress-myapp <none> www2.westos.org 172.25.7.1 80 117m ingress-nginx <none> www1.westos.org 172.25.7.1 80 117m
Set local resolution
root@server1 ingress]# cat /etc/hosts 127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4 ::1 localhost localhost.localdomain localhost6 localhost6.localdomain6 172.25.7.1 server1 reg.westos.org www1.westos.org www2.westos.org 172.25.7.2 server2 172.25.7.3 server3 172.25.7.4 server4
Domain name access test to access the corresponding service`
[root@server1 ingress]# curl www2.westos.org Hello MyApp | Version: v2 | <a href="hostname.html">Pod Name</a> [root@server1 ingress]# curl www1.westos.org Hello MyApp | Version: v1 | <a href="hostname.html">Pod Name</a>
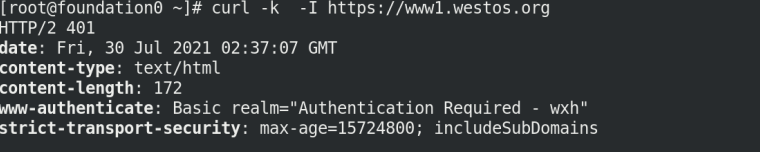
Load balancing test, successful myapp SVC
[root@server1 ingress]# curl www1.westos.org/hostname.html nginx-deployment-6456d7c676-8jsrd [root@server1 ingress]# curl www1.westos.org/hostname.html nginx-deployment-6456d7c676-8jsrd [root@server1 ingress]# curl www1.westos.org/hostname.html nginx-deployment-6456d7c676-bcx9b [root@server1 ingress]# curl www1.westos.org/hostname.html nginx-deployment-6456d7c676-kwqfr [root@server1 ingress]# curl www1.westos.org/hostname.html nginx-deployment-6456d7c676-bcx9b
To view the details, you can see www2 westos. Org corresponds to nginx SVC: 80. The ip addresses of three pod s under nginx SVC are used for balanced access
[root@server1 ingress]# kubectl describe ingress ingress-nginx
Name: ingress-nginx
Namespace: default
Address: 172.25.7.1
Default backend: default-http-backend:80 (<error: endpoints "default-http-backend" not found>)
Rules:
Host Path Backends
---- ---- --------
www1.westos.org
/ nginx-svc:80 (10.244.179.71:80,10.244.179.72:80,10.244.22.6:80)
Annotations: <none>
Events: <none>
4 TLS certification
4.1 create certification
[root@server1 ingress]# openssl req -x509 -sha256 -nodes -days 365 -newkey rsa:2048 -keyout tls.key -out tls.crt -subj "/CN=nginxsvc/O=nginxsvc" Generating a 2048 bit RSA private key ..................................................+++ ...........................+++ writing new private key to 'tls.key' ----- [root@server1 ingress]# kubectl create secret tls tls-secret --key tls.key --cert tls.crt secret/tls-secret created [root@server1 ingress]# kubectl get secrets NAME TYPE DATA AGE default-token-75rf9 kubernetes.io/service-account-token 3 4d16h tls-secret kubernetes.io/tls 2 17s
4.2 in ingress Yaml join certification
[root@server1 ingress]# cat ingress.yaml
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-nginx
annotations:
nginx.ingress.kubernetes.io/auth-type: basic
nginx.ingress.kubernetes.io/auth-secret: basic-auth
nginx.ingress.kubernetes.io/auth-realm: 'Authentication Required - lz'
spec:
tls:
- hosts:
- www1.westos.org
secretName: tls-secret
rules:
- host: www1.westos.org
http:
paths:
- path: /
backend:
serviceName: nginx-svc
servicePort: 80
[root@server1 ingress]# yum install -y httpd-tools
Loaded plugins: product-id, search-disabled-repos, subscription-manager
This system is not registered with an entitlement server. You can use subscription-manager to register.
docker | 3.0 kB 00:00:00
dvd | 4.3 kB 00:00:00
kubernetes | 1.4 kB 00:00:00
Package httpd-tools-2.4.6-88.el7.x86_64 already installed and latest version
Nothing to do
4.3 setting up accounts
[root@server1 ingress]# htpasswd -c auth lz New password: Re-type new password: Adding password for user lz [root@server1 ingress]# kubectl create secret generic basic-auth --from-file=auth secret/basic-auth created [root@server1 ingress]# kubectl get secrets NAME TYPE DATA AGE basic-auth Opaque 1 40s default-token-75rf9 kubernetes.io/service-account-token 3 4d18h tls-secret kubernetes.io/tls 2 121m
4.4 execute ingress yaml
[root@server1 ingress]# kubectl apply -f ingress.yaml Warning: networking.k8s.io/v1beta1 Ingress is deprecated in v1.19+, unavailable in v1.22+; use networking.k8s.io/v1 Ingress ingress.networking.k8s.io/ingress-nginx created ingress.networking.k8s.io/ingress-myapp created
4.5 address rewriting
[root@server1 ingress]# cat ingress.yaml
apiVersion: networking.k8s.io/v1beta1
kind: Ingress
metadata:
name: ingress-nginx
annotations:
#nginx.ingress.kubernetes.io/app-root: /hostname.html
nginx.ingress.kubernetes.io/rewrite-target: /$2
nginx.ingress.kubernetes.io/auth-type: basic
nginx.ingress.kubernetes.io/auth-secret: basic-auth
nginx.ingress.kubernetes.io/auth-realm: 'Authentication Required - lz'
spec:
tls:
- hosts:
- www1.westos.org
secretName: tls-secret
rules:
- host: www1.westos.org
http:
paths:
- path: /something(/|$)(.*)
backend:
serviceName: nginx-svc
servicePort: 80
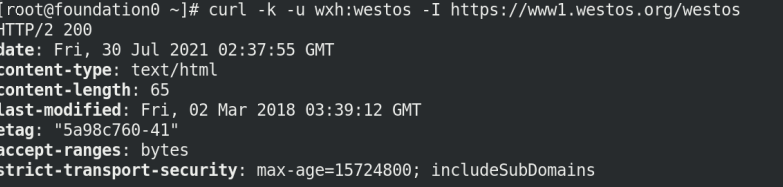
4.6 testing
load balancing