1, Introduction theory overview
1.1 introduction and theoretical overview of virtualization technology
- Because there was a set of statistical data in the early EPA report: when EPA studied the energy efficiency of servers and data centers, it found that in fact, only 5% of the time of servers are working, and the rest of the time has been dormant. However, software resources have no high performance (stability and efficiency) as hardware resources (the same function), so virtualization technology appears
- Virtualization Technology
- One computer is virtualized into multiple logical computers through virtualization technology, and multiple logical computers are run on one computer at the same time,
At the same time, each logical computer can run different operating systems, and applications can run in independent spaces without affecting each other,
So as to improve the working efficiency of the computer
- One computer is virtualized into multiple logical computers through virtualization technology, and multiple logical computers are run on one computer at the same time,
- Virtualization technology functions
- 1. Simulate multiple operating systems (centos, win10, suse) in one operating system (win10), and each operating system can run different services (nginx+tomcat), so as to build a cluster with one host (from the whole)
- 2. Realize the function of physical hardware through software / application.
- Development of virtualization technology
- In 1961, the IBM 709 machine realized the time-sharing system, which divided the CPU occupation into several extremely short time slices (1/100sec), and each time slice performed different work. By polling these time slices, a CPU was disguised as multiple CPUs
- In 1972, IBM officially named the time-sharing system of system370 as virtual machine
- In 1990, IBM launched system 390, which supports logical partition (dividing a CPU into multiple parts, which are independent of each other, that is, logical partition)
- Xen: it came out in 2003. It is an external hypervisor/VMM program (virtual machine management program), which can control the host and allocate resources to multiple clients (virtualization technology supported by Xen: full virtualization, semi virtualization)
- KVM: it came out in 2007 and is now built into the kernel (KVM: supported virtualization technology: full virtualization)
- Virtualization type
- 1. Full Virtualization: all physical hardware resources are abstracted through software, and finally called
- Usage: use the hypervisor(VMM) software. Its principle is to establish an abstraction layer between the underlying hardware and the server. The core based virtual machine is an open source product for Linux system. The hypervisor(VMM) can capture the instructions of the CPU and act as an intermediary for the instructions to access the hardware controller and peripherals.
- 2. Semi Virtualization: the operating system needs to be modified
- 3. Direct access: direct use of physical hardware resources (need support, not perfect for the time being)
- 1. Full Virtualization: all physical hardware resources are abstracted through software, and finally called
- Virtualization technology features (advantages and disadvantages)
| advantage | inferiority |
|---|---|
| Centralized management (remote management and maintenance) | High initial expenses (initial hardware support) |
| Improve hardware utilization (low utilization of physical resources. For example, peak, virtualization solves the "idle" capacity) | Reduce hardware utilization (specific scenarios, such as applications that eat too much resources are not necessarily suitable for virtualization) |
| Dynamically adjust the machine / resource configuration (virtualization separates the application and service hardware of the system, so as to improve the flexibility) | Larger error impact area (local physical downtime may lead to unavailability of virtual machines and damage to all files in virtual machines) |
| High reliability (additional functions and schemes can be deployed to improve transparent application environments such as load balancing, migration, recovery and replication) | Complex implementation configuration and management (management personnel have difficulty in operation and maintenance and troubleshooting) |
| Certain restrictions (virtualization technology involves various restrictions and must be used in combination with servers, applications and suppliers supporting / compatible virtualization) | |
| Security (security risks of virtualization technology) |
1.2 virtualization technology (VMware Workstation)
- workstation supports the virtualization technology of intel and AMD
- Hardware assisted virtualization technology Intel-VT-x, AMD-V
- Intel VT-x technology mainly includes virtualization technology in three aspects: CPU, memory and I/O, and provides optimization processing (to make up for the defects of X86 architecture virtualization in the early stage)
- AMD-V: it is a set of hardware extension and hardware assisted virtualization technology for x86 processor system architecture, which can simplify the virtualization solution of pure software
- Improve the design of VMM (virtual machine monitor), make full use of hardware resources and improve the virtualization efficiency of server and data center
- VMM is a system software, which can maintain multiple efficient and isolated program environments (virtual machines), manage the real resources of the computer system and provide interfaces for virtual machines
- VMM features
- 1. Logical division of physical resources (conversion to virtual resources)
- 2. It is the intermediary between the host and the application or virtual machine
1.3 virtualization technology (KVM)
1.3.1 preface overview
- KVM (kernel based virtual machine) is one of virtualization technologies. It is a kernel based virtual machine
- KVM is a native full virtualization solution of open source Linux based on X86 hardware of virtualization extension (the cpu is required to support Intel-VT-x or AMD-V)
- KVM is embedded in the kernel module to simulate the processor and memory to support the operation of virtual machines
- The virtual machine is implemented as a conventional Linux process, which is scheduled by the standard Linux scheduler;
- Each virtual CPU of the virtual machine is implemented as a regular Linux process. This enables KMV to use the existing functions of the Linux kernel, but KVM itself does not perform any simulation. The client space program (virtual machine) is required to set the address space of a client virtual server through the / dev/kvm interface (this virtual device can be seen only when hardware assisted virtualization is turned on), and Qemu simulates I/O (ioctl) for resource scheduling and maintenance management
- Libvirt
- KVM management tools can manage VMS such as KVM, Xen, VirtualBox and even OpenStack
- Libvirt consists of three components: background daemon libvirtd, API library and command line tool virsh
1.3.2 KVM architecture mode
- KVM virtualization architecture has three modes
- 1. Guest OS: the OS in VM is guest OS. The mode in which the client runs in the operating system. The client is divided into kernel mode and user mode.
- 2. User mode: provide users with user space tools for virtual machine management and I/O on behalf of users. Qemu works in this mode (the main function of Qemu)
- 3.linux kernel mode: simulate CPU and memory to realize customer mode switching. When processing is launched from customer mode, KVM runs in this mode
1.3.3 KVM principle
- 1.Guest: the client system, including CPU (vCPU), memory and driver (Console, network card, I/O device driver, etc.), is operated in a restricted CPU mode by KVM.
- 2.KVM: kernel module simulates processor and memory to support virtual machine operation
- 3.Qemu: mainly deals with I/O and provides a user space / dev/kvm for customers.
- libvirt tool for virtual machine management.
- ioctl: a system call dedicated to device I / O operations.
- libvirt: KVM management tool
- The above constitutes a complete virtualization platform
- Simple understanding:
- KVM driver provides virtualization of processor and memory, and interception of client I/O (intercepting sensitive instructions). After I/O of guest is intercepted, it is handed over to Qemu for processing
- Qemu uses interface libkvm to call (ioctl) virtual machine device interface / dev/kvm to allocate resources, manage and maintain virtual machines
1.3.4 core functions of KVM virtualization technology (principle)
- QEMU (works in the user layer and controls the libkvm tool (function of the tool: control the KVM in the kernel) to call the physical virtualization resources (the way to call the physical virtualization resources is ioctl, which is supplied to the virtual machine)
- KVM (works in the kernel layer, virtualizes / abstracts physical hardware resources, and provides Qemu component calls)
1.3.5 KVM workflow
- Qemu in user mode uses the interface libkvm to enter the kernel mode through ioctl system call. The KVM driver creates a virtual CPU and virtual memory for the virtual machine, then executes the VMLAU · NCH instruction to enter the client mode, loads the Guest OS and runs it. If exceptions occur during the operation of Guest OS, pause the operation of Guest OS and exit to kernel mode while saving the current state to deal with these exceptions.
- When processing these exceptions in kernel mode, if I/O is not required, re-enter client mode after processing. If I/O is required, enter the user mode, and Qemu will process the I/O. after processing, enter the kernel mode, and then enter the customer mode
1.3.6 functions of KVM core components
- QEMU function: control I/O virtualization and call hardware resources
- KVM function: provide virtualization of CPU and memory (hardware resources) for virtual machines
1.3.7 comparison between before and after virtualization
- Before virtualization
- ① Each host has an operating system
- ② Close combination of software and hardware
- ③ Running multiple applications on the same host often creates conflicts
- ④ Low utilization of system resources (e.g. 5%)
- ⑤ Hardware is expensive and inflexible
- After virtualization
- ① It breaks the interdependence between operating system and hardware
- ② By encapsulating the technology into virtual machines, the operating system and applications are managed as a single individual
- ③ Strong safety and fault isolation
- ④ Virtual machines are hardware independent and can run on any hardware
- Operating system
- LINUX + Apache + MySQL + PHP in LAMP architecture (implemented by one host). Apache and MySQL resources are shared. If the architecture requires high security isolation between services, Apache pages and MySQL database directories must not meet each other. If Apache vulnerabilities are exposed, attackers can access MySQL data directories through Apache processes, So as to obtain the data in mysql, which is a serious security risk. So if we want to solve this potential danger, we can achieve kernel level isolation (using virtualization technology)
- Combination of software and hardware
- Because the hardware and operating system are incompatible or unsupported, some software and hardware functions cannot be used normally (which is also the most difficult problem). At this time, we can use virtualization technology, because the software and hardware will be isolated (deployed) through the virtualization layer driver. As long as the virtualization layer can identify software / hardware applications, we can combine the software and hardware
- Application aspect
- Running multiple applications on the same host will usually lead to conflicts. For example, Apache and Nginx have the same location (port 80), and can only be separated by using reverse proxy. At the same time, if this method is used on the same machine, important data files in Apache and Nginx will be leaked at the same time. So we can isolate services through virtualization
1.3.7 KVM network mode (two types)
- NAT (default)
- The data packet is transmitted through the interface of the host in NAT mode. It can access the external network, but it cannot access the virtual machine network from the outside
- bridge
- This mode allows the virtual machine to have a network like an independent host. External machines can directly access the inside of the virtual machine, but they need the support of network card (generally supported by wired network card)
2, KVM virtualization platform deployment
2.1 start the virtualization engine
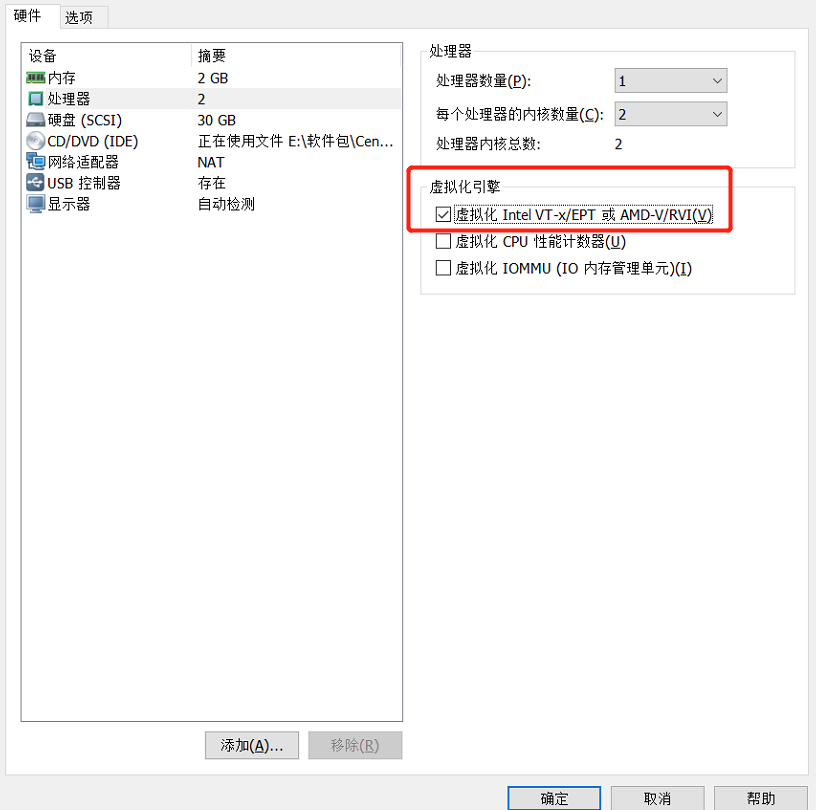
2.2 modify the host name, close the firewall and permanently mount the image disc
[root@localhost ~]# hostnamectl set-hostname kvm [root@localhost ~]# su [root@kvm ~]# systemctl stop firewalld.service [root@kvm ~]# setenforce 0 [root@kvm ~]# systemctl disable firewalld.service [root@kvm ~]# vim /etc/fstab # # /etc/fstab # Created by anaconda on Thu May 6 21:55:59 2021 # # Accessible filesystems, by reference, are maintained under '/dev/disk' # See man pages fstab(5), findfs(8), mount(8) and/or blkid(8) for more info # UUID=0fb43f15-0bd0-4297-b86d-6902413b5773 / xfs defaults 0 0 UUID=a0011c7a-97c2-408a-affa-062bc3473b3d /boot xfs defaults 0 0 UUID=24836570-11f5-406d-9620-6df4d5c96c1e swap swap defaults 0 0 /dev/cdrom /mnt iso9660 defaults 0 0 [root@kvm ~]# mount -a mount: /dev/sr0 Write protected, will mount as read-only [root@kvm ~]# df -hT file system type Capacity used available used% Mount point /dev/sda3 xfs 26G 3.6G 22G 14% / devtmpfs devtmpfs 978M 0 978M 0% /dev tmpfs tmpfs 993M 0 993M 0% /dev/shm tmpfs tmpfs 993M 9.0M 984M 1% /run tmpfs tmpfs 993M 0 993M 0% /sys/fs/cgroup /dev/sda1 xfs 497M 151M 346M 31% /boot tmpfs tmpfs 199M 0 199M 0% /run/user/0 tmpfs tmpfs 199M 12K 199M 1% /run/user/42 /dev/sr0 iso9660 4.3G 4.3G 0 100% /mnt
2.3 environmental optimization
- Set DNS reverse resolution
[root@kvm ~]# vim /etc/ssh/sshd_config 115 UseDNS no [Uncomment and change to no(Set to NO Can let the client SSH Connect to server (faster)]
- Make local warehouse
[root@kvm ~]# cd /etc/yum.repos.d/ [root@kvm yum.repos.d]# ls CentOS-Base.repo CentOS-CR.repo CentOS-Debuginfo.repo CentOS-fasttrack.repo CentOS-Media.repo CentOS-Sources.repo CentOS-Vault.repo [root@kvm yum.repos.d]# mkdir bak [root@kvm yum.repos.d]# mv *.repo bak [root@kvm yum.repos.d]# ls bak [root@kvm yum.repos.d]# vim local.repo [local] name=kvm baseurl=file:///mnt gpgcheck=0 enabled=1 [root@kvm yum.repos.d]# yum clean all [root@kvm yum.repos.d]# yum repolist
2.4 installing KVM
- Install KVM basic components
[System image installation for minimized installation GNOME Desktop environment, if the graphical interface is installed, it is not necessary to install] [root@kvm yum.repos.d]# yum groupinstall -y "GNOME Desktop" [root@kvm yum.repos.d]# yum -y install qemu-kvm-tools.x86_64 virt-install qemu-img bridge-utils libvirt virt-manager [qemu-kvm : KVM [module] [qemu-kvm-tools : KVM Debugging tools,[optional] [virt-install : [command line tool for building virtual machine] [qemu-img : qemu assembly,Create disk, start virtual machine, etc.] [bridge-utils : [network support tools] [libvirt : Virtual machine management tool] [virt-manager : GUI management virtual machine]
- Check whether the CPU supports virtualization
[See there VMX Support virtualization] [root@kvm yum.repos.d]# cat /proc/cpuinfo | grep vmx flags : fpu vme de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush mmx fxsr sse sse2 ss ht syscall nx pdpe1gb rdtscp lm constant_tsc arch_perfmon nopl xtopology tsc_reliable nonstop_tsc eagerfpu pni pclmulqdq vmx ssse3 fma cx16 pcid sse4_1 sse4_2 x2apic movbe popcnt tsc_deadline_timer aes xsave avx f16c rdrand hypervisor lahf_lm abm 3dnowprefetch tpr_shadow vnmi ept vpid fsgsbase tsc_adjust bmi1 avx2 smep bmi2 invpcid mpx rdseed adx smap clflushopt xsaveopt xsavec arat flags : fpu vme de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush mmx fxsr sse sse2 ss ht syscall nx pdpe1gb rdtscp lm constant_tsc arch_perfmon nopl xtopology tsc_reliable nonstop_tsc eagerfpu pni pclmulqdq vmx ssse3 fma cx16 pcid sse4_1 sse4_2 x2apic movbe popcnt tsc_deadline_timer aes xsave avx f16c rdrand hypervisor lahf_lm abm 3dnowprefetch tpr_shadow vnmi ept vpid fsgsbase tsc_adjust bmi1 avx2 smep bmi2 invpcid mpx rdseed adx smap clflushopt xsaveopt xsavec arat
- Check whether KVM module is installed
[root@kvm yum.repos.d]# lsmod | grep kvm [lsmod: display loaded system modules] kvm_intel 170086 0 kvm 566340 1 kvm_intel irqbypass 13503 1 kvm
- Set the display mode of the startup interface
[root@kvm yum.repos.d]# ln -sf /lib/systemd/system/graphical.target /etc/systemd/system/default.target
2.5 setting up KVM network
- Nat: by default, data packets are transmitted through the host interface in NAT mode. You can access the external network, but you cannot access the virtual machine network from the outside
- Bridge: this mode allows the virtual machine to have a network like an independent host. External machines can directly access the inside of the virtual machine, but it needs the support of network card (generally supported by wired network card)
- Here, the Bridge mode is used for deployment
[root@kvm yum.repos.d]# vim /etc/sysconfig/network-scripts/ifcfg-ens33 #IPADDR=192.168.131.10 [note original IP address] #NETMASK=255.255.255.0 [note original subnet mask] #GATEWAY=192.168.131.2 [note] #DNS1=192.168.131.2 [note] BRIDGE=br0 [Set to bridge mode, Associate br0 [network card]
- Create and edit bridge network card
[root@kvm ~]# vim /etc/sysconfig/network-scripts/ifcfg-br0
TYPE=Bridge
BOOTPROTO=static
DEFROUTE=yes
PEERDNS=yes
PEERROUTES=yes
IPV4_FAILURE_FATAL=no
IPV6INIT=yes
IPV6_AUTOCONF=yes
IPV6_DEFROUTE=yes
IPV6_PEERDNS=yes
IPV6_PEERROUTES=yes
IPV6_FAILURE_FATAL=no
IPV6_ADDR_GEN_MODE=stable-privacy
NAME=br0
DEVICE=br0
ONBOOT=yes
IPADDR=192.168.131.200
NETMASK=255.255.255.0
GATEWAY=192.168.131.2
[root@kvm yum.repos.d]# systemctl restart network
[root@kvm ~]# ifconfig
br0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.131.200 netmask 255.255.255.0 broadcast 192.168.131.255
inet6 fe80::3e8a:5ed5:d2e5:855c prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:49:74:c2 txqueuelen 1000 (Ethernet)
RX packets 135 bytes 12961 (12.6 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 134 bytes 18041 (17.6 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
ether 00:0c:29:49:74:c2 txqueuelen 1000 (Ethernet)
RX packets 2927 bytes 235755 (230.2 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 2183 bytes 344622 (336.5 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1 (Local Loopback)
RX packets 76 bytes 6508 (6.3 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 76 bytes 6508 (6.3 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
virbr0: flags=4099<UP,BROADCAST,MULTICAST> mtu 1500
inet 192.168.122.1 netmask 255.255.255.0 broadcast 192.168.122.255
ether 52:54:00:34:1e:2d txqueuelen 1000 (Ethernet)
RX packets 0 bytes 0 (0.0 B)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 0 bytes 0 (0.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
- For ease of operation, you can create a new connection on the Xshell
2.6 KVM deployment and management
2.6.1 create the directory of KVM storage and image data and upload Centos7 image
[root@kvm ~]# mkdir -p /data_kvm/iso [image directory] [root@kvm ~]# mkdir -p /data_kvm/store [storage directory] [root@kvm ~]# mkdir -p /qz [root@kvm ~]# mount.cifs //192.168.1.50/linux package / qz/ Password for root@//192.168.1.50/linux package: [root@kvm ~]# cp -p /qz/CentOS-7-x86_64-DVD-1708.iso /data_kvm/iso / [copy the image file to the image directory (the process is long)]
- View mirror
[root@kvm ~]# ll /data_kvm/iso/ Total consumption 4415488 -rwxr-xr-x. 1 root root 4521459712 10 September 29, 2017 CentOS-7-x86_64-DVD-1708.iso
2.6.2 managing virtual machines using virtual system manager
- Creating ideas
- ① Create storage pool (ISO, STORE)
- ② Add storage volume
- ③ Create virtual machine
[root@kvm yum.repos.d]# Virt Manager [open the graphical interface, and the following operations are operated in the graphical interface]
2.6.3 step 1: create ISO and STORE storage pools (ISO and STORE steps are the same, just note the pool name and path)
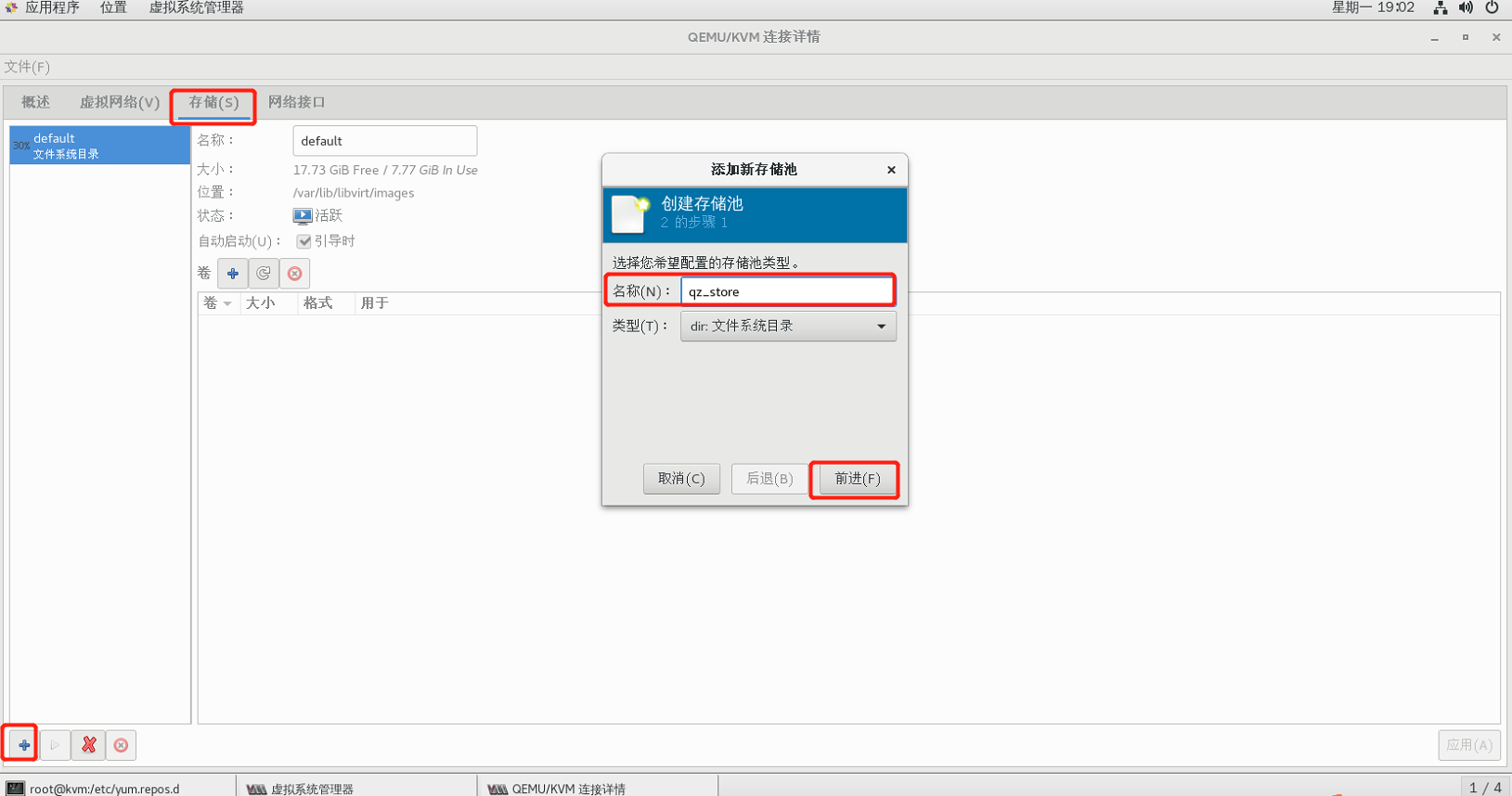
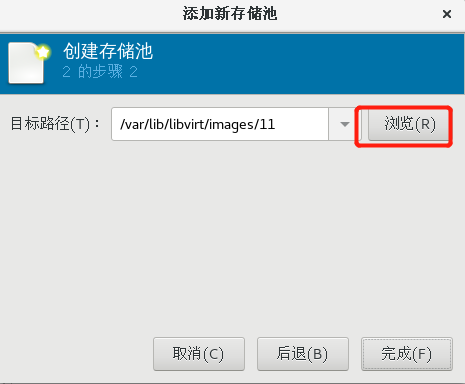
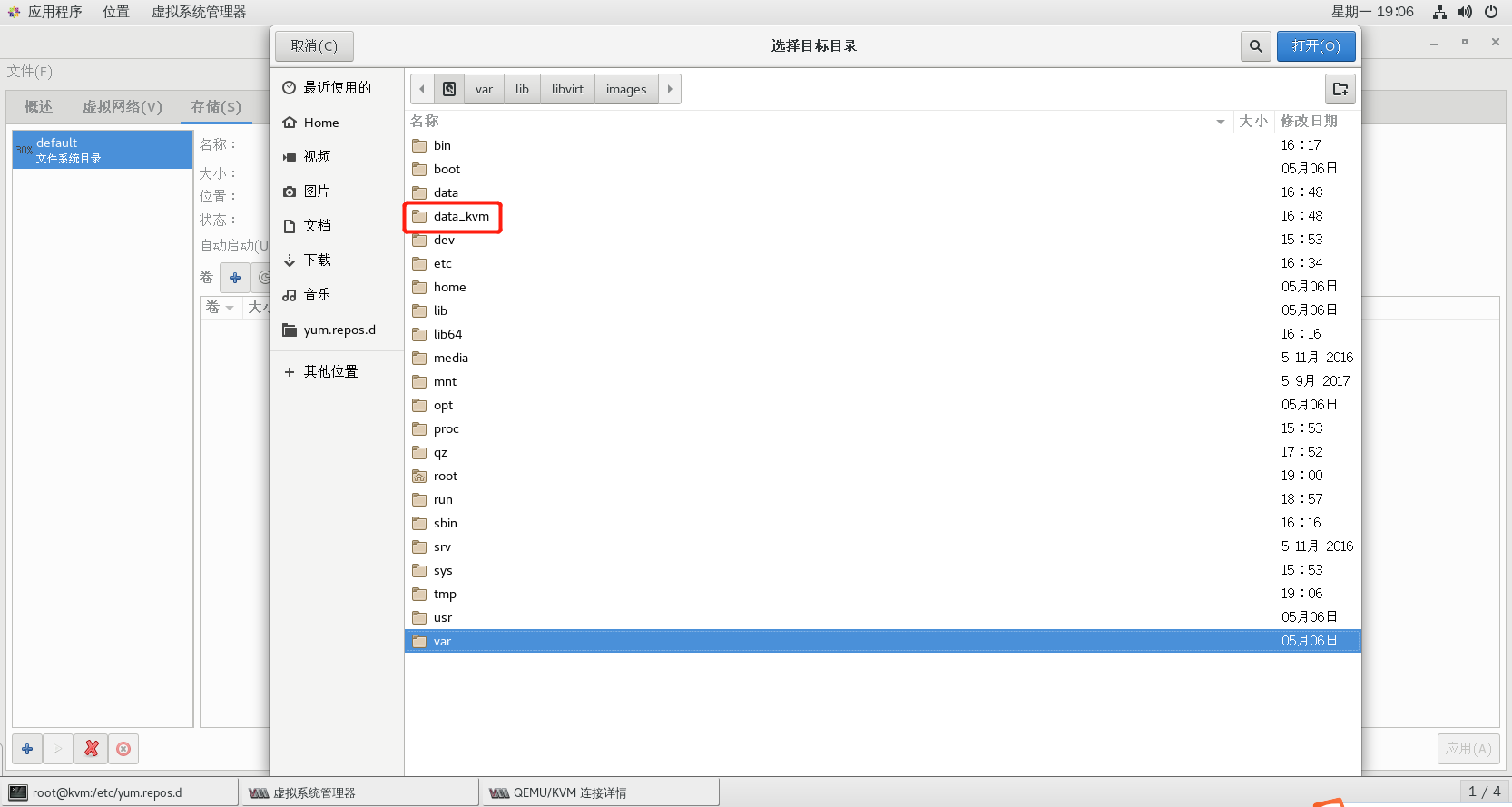
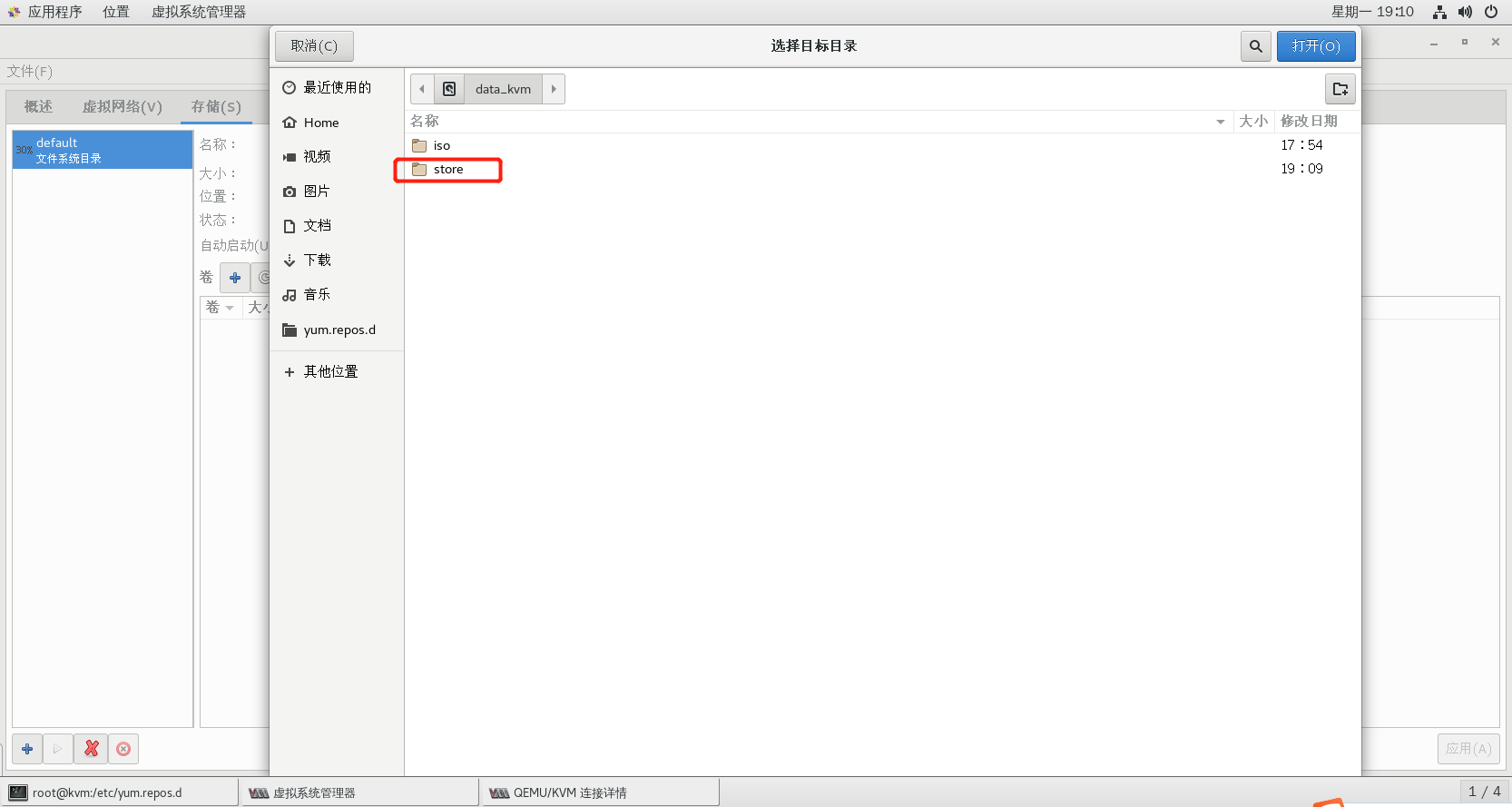
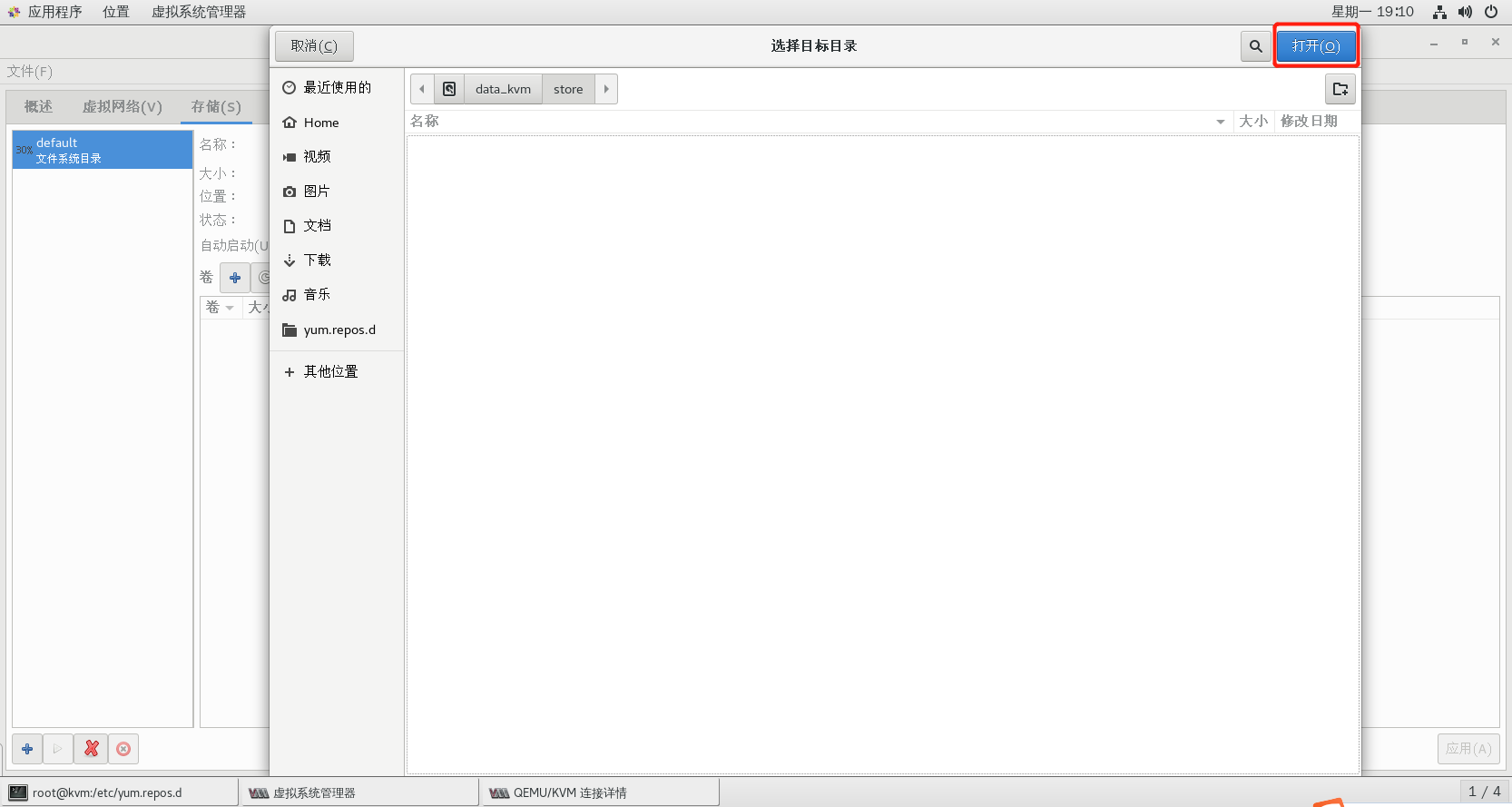
2.6.4 step 2: create storage volume
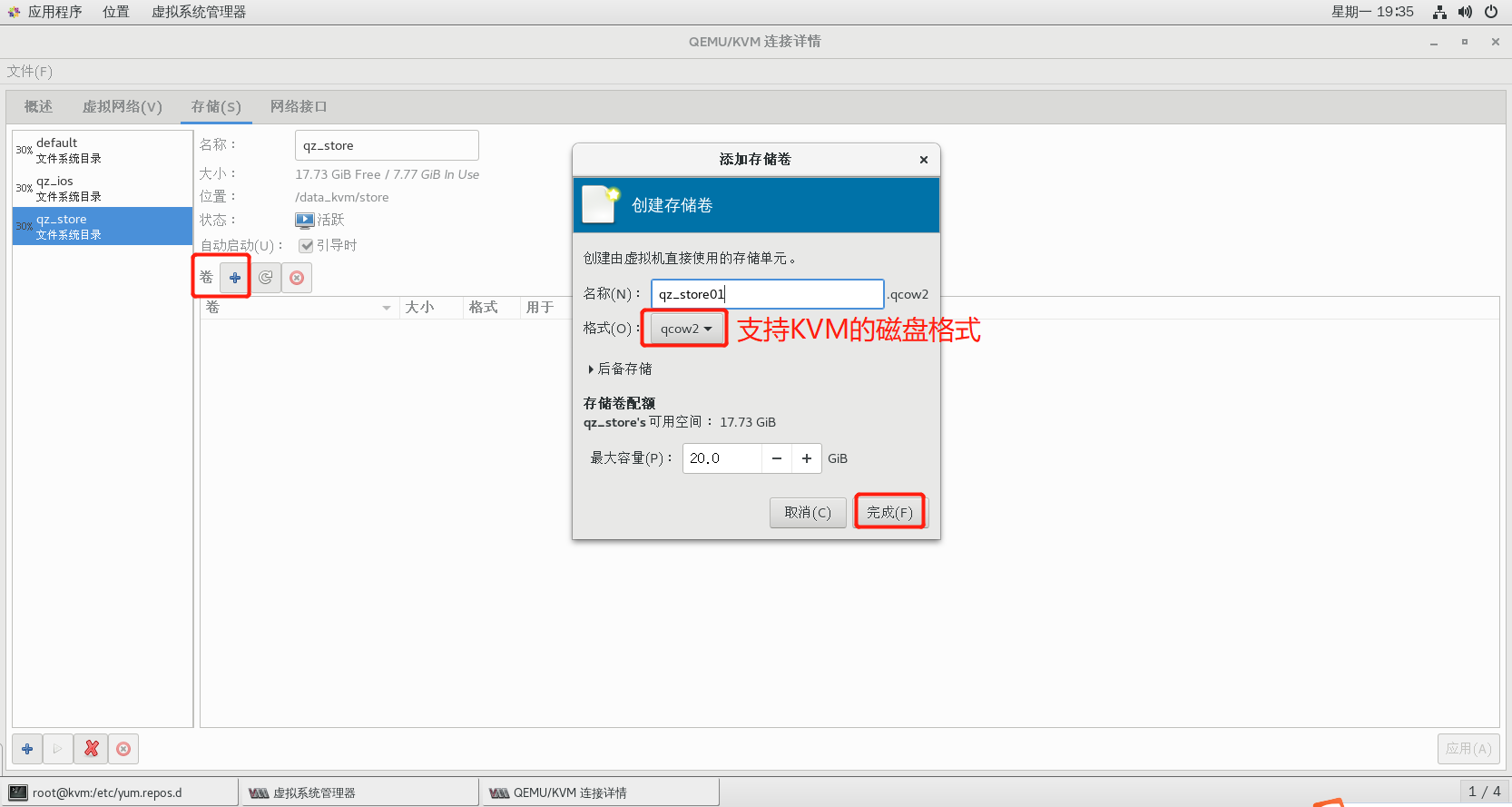
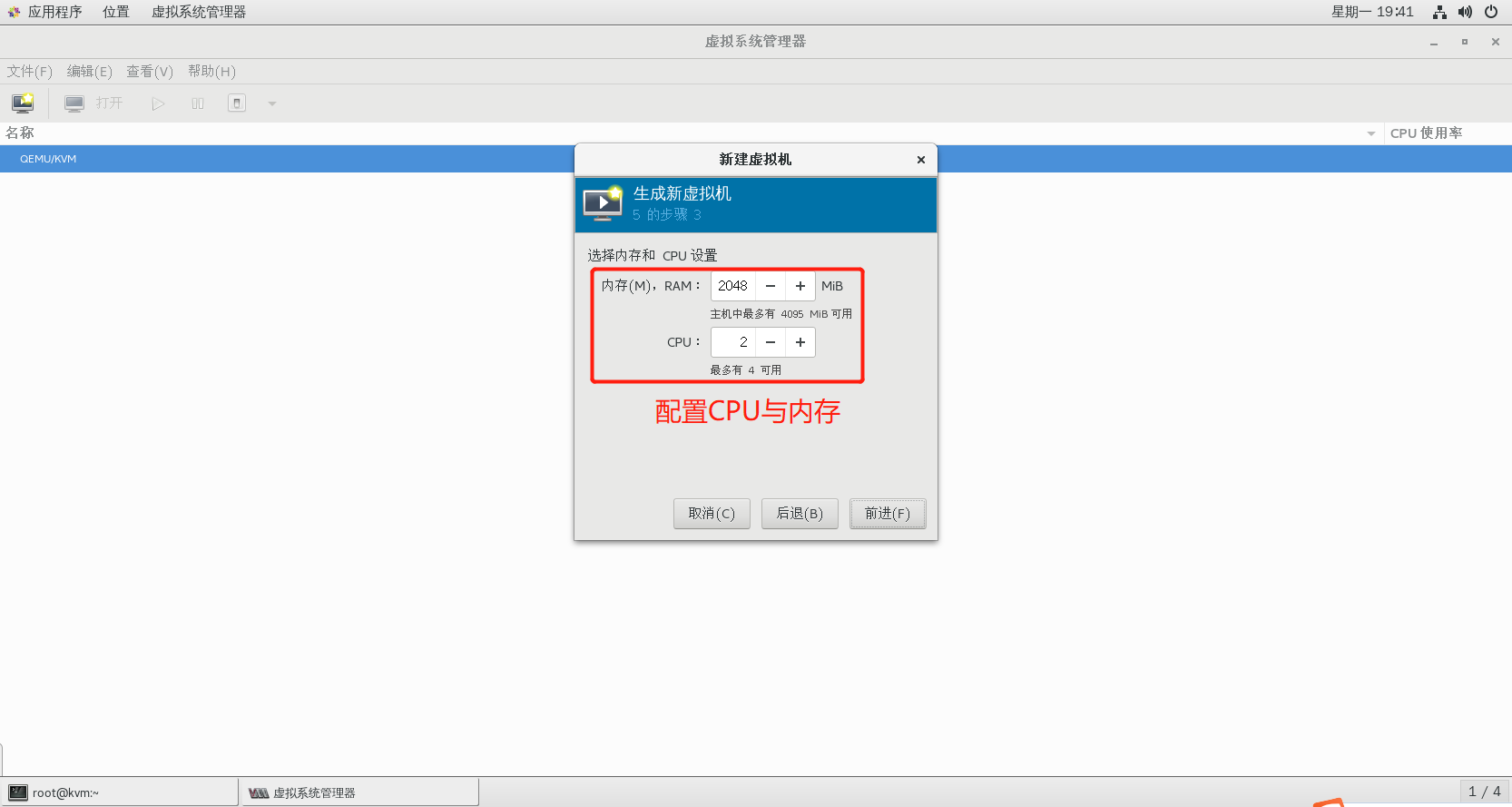
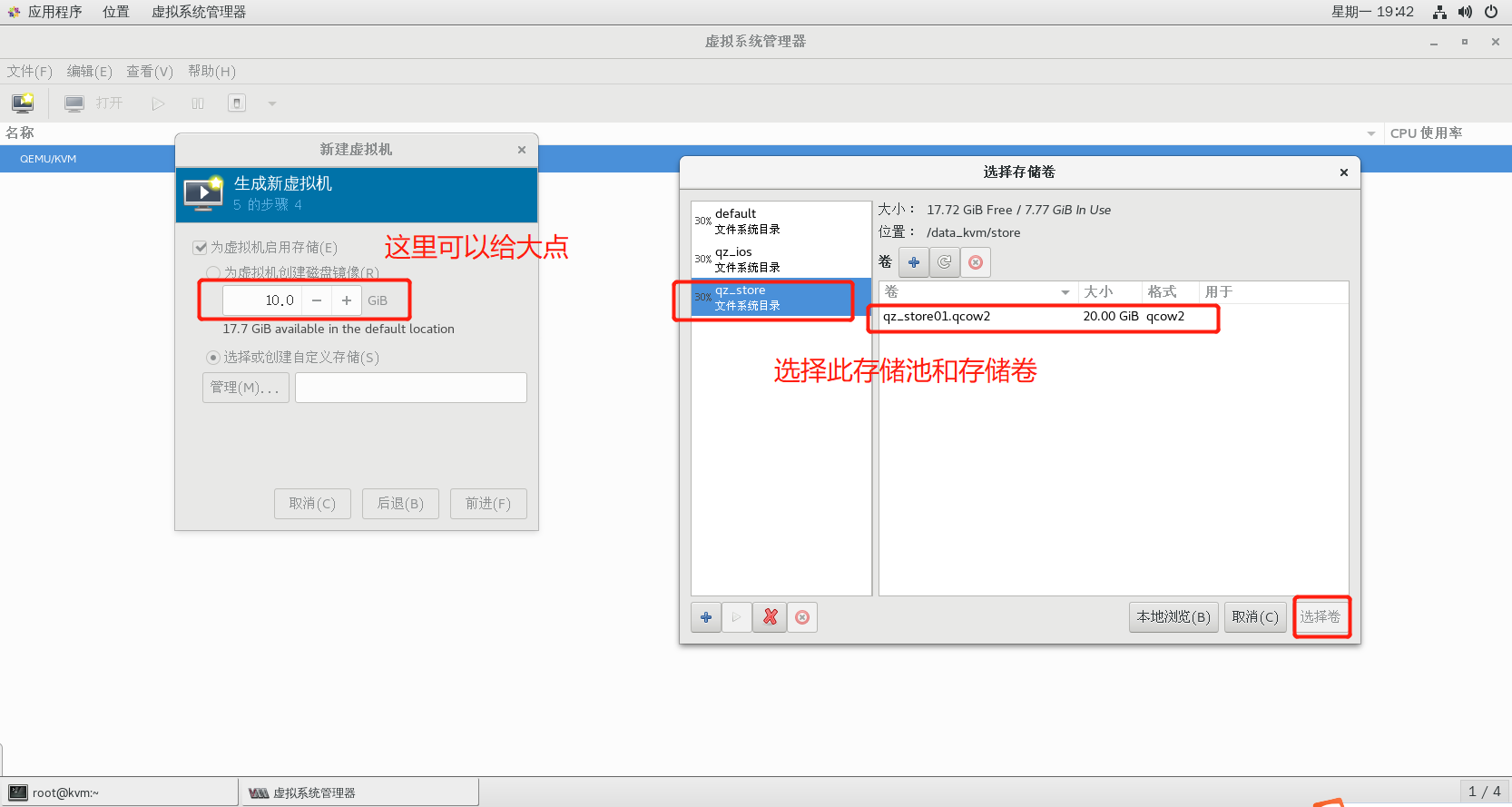
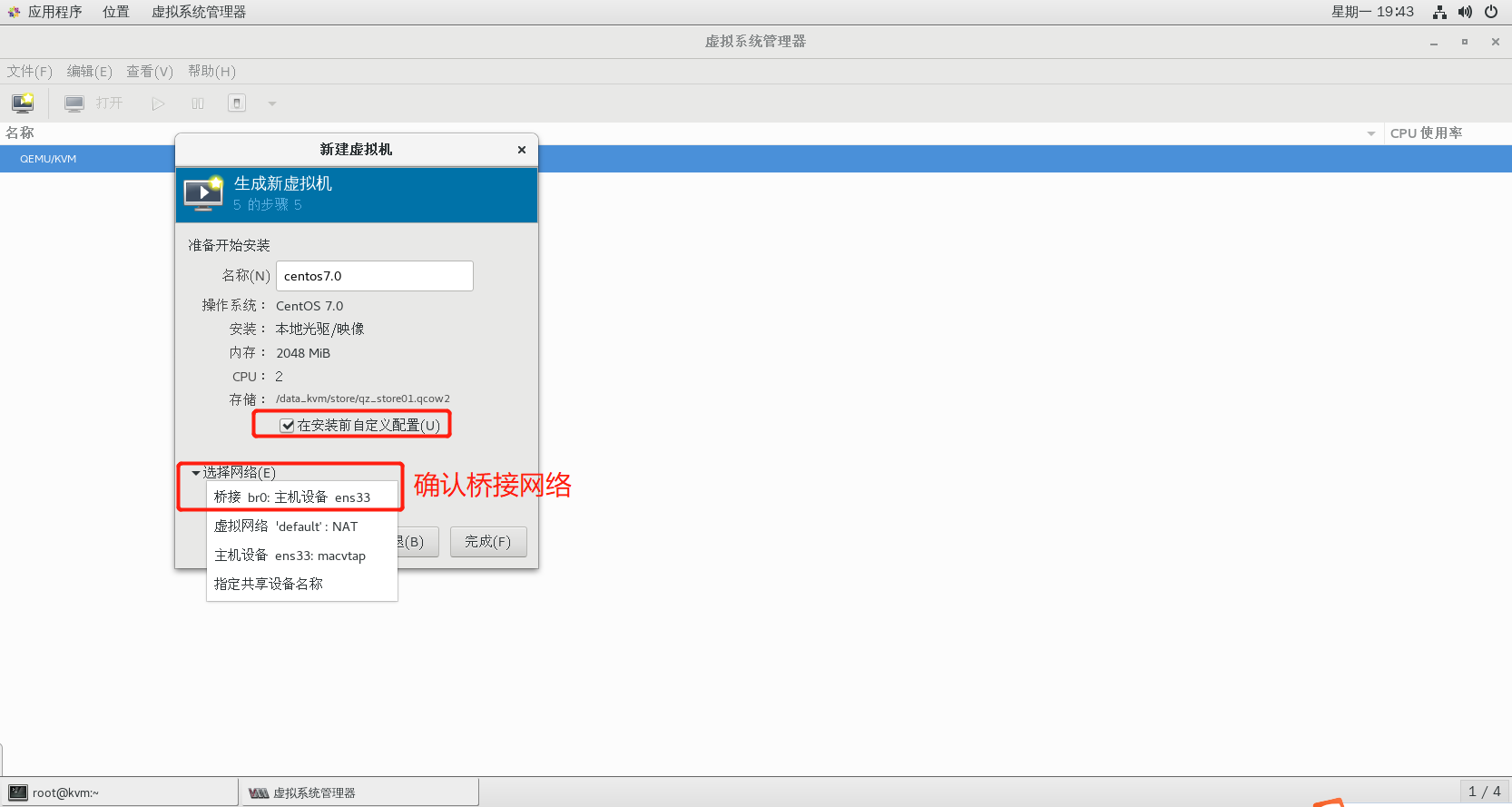
2.6.5 step 3: create virtual machine
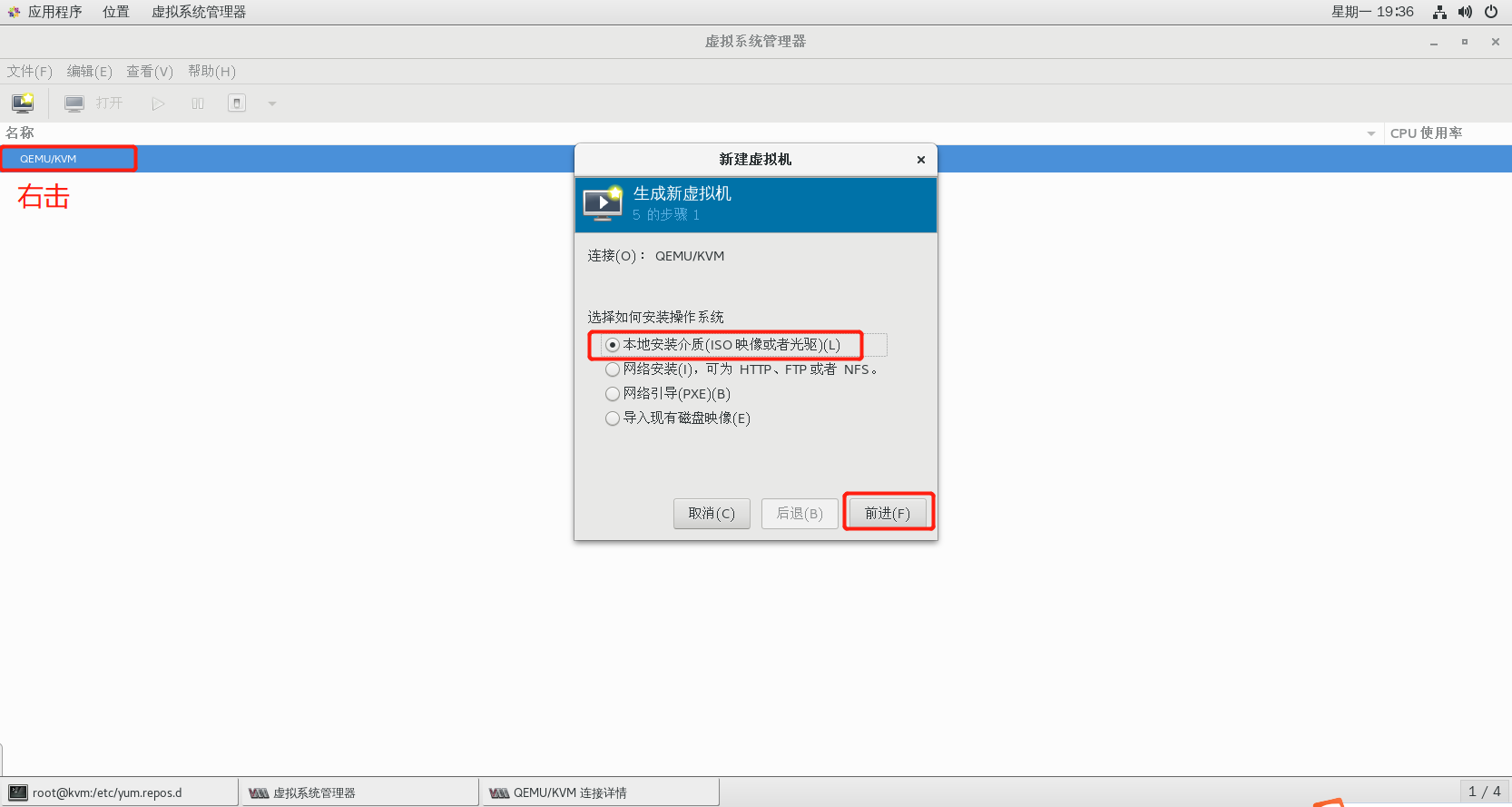
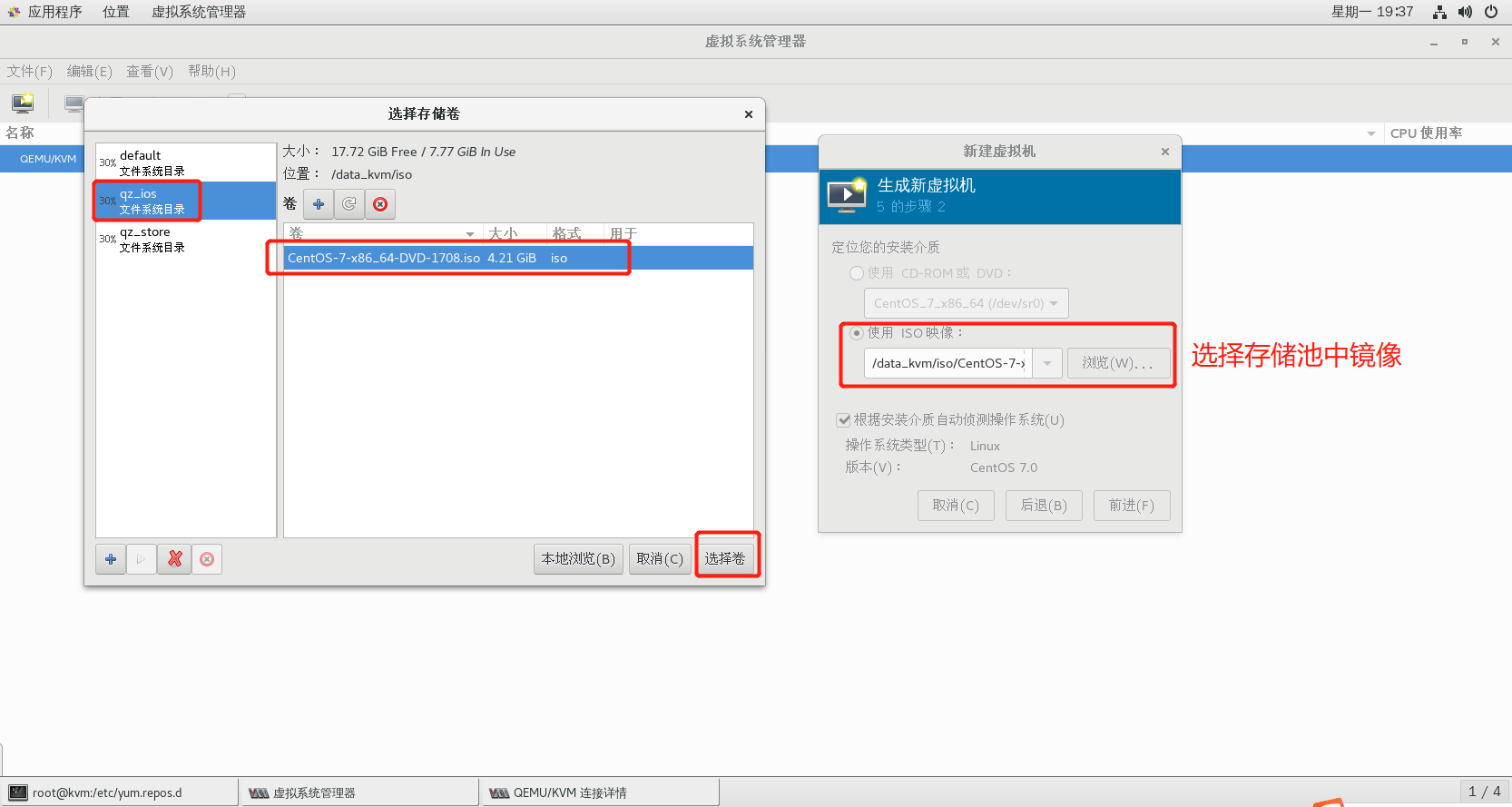
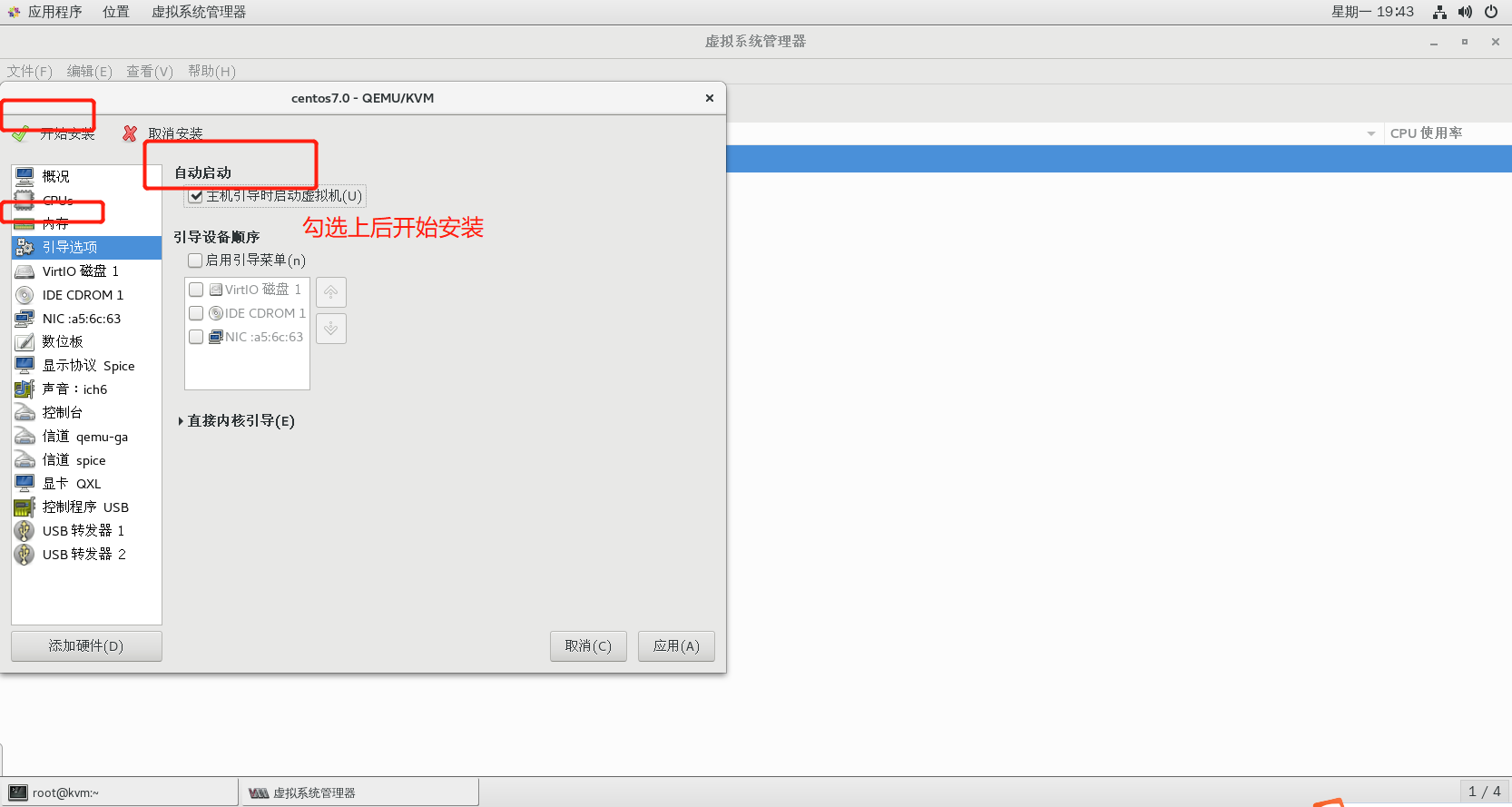
2.6.6 success