system management
- preview contents
- 1.iptables rule backup and recovery
- 2. 9 zone s of firewalld
- 3.firewalld operation on zone
- 4. Operation on service in firewalld
- 5.linux task planning cron
- 6. System service management tool chkconfig before CentOS 7
- 7. CentOS service management tool systemd
- 7.1 list all service names
- 7.2 list all units with service type
- 7.3 several common service related commands
- 8. unit introduction
- 9.target introduction
- After class summary
- 3. System service startup sequence
preview contents
10.19 iptables rule backup and recovery 10.20 9 zone s of firewalld 10.21 firewalld operation on zone 10.22 firewalld operation on service 10.23 linux task planning cron 10.24 chkconfig tool 10.25 systemd management services 10.26 unit introduction 10.27 target introduction extend firewalld custom iptables rules https://blog.51cto.com/jevic/1785162 Provide a blog for iptables series articles https://www.zsythink.net/archives/tag/iptables/page/2/ anacron https://www.jianshu.com/p/3009a9b7d024?from=timeline systemd custom startup script http://www.jb51.net/article/100457.htm
1.iptables rule backup and recovery
Iptables backs up data to the configuration file / etc/sysconfig/iptables, using the following command
[root@linux-001 ~]# service iptables save
iptables backs up rules to another file instead of a configuration file
[root@linux-001 ~]# iptables-save > my.ipt [root@linux-001 ~]# cat my.tpt # Generated by iptables-save v1.4.21 on Wed Apr 17 03:35:23 2019 *nat :PREROUTING ACCEPT [267:82430] :INPUT ACCEPT [260:81921] :OUTPUT ACCEPT [25:8200] :POSTROUTING ACCEPT [26:8252] -A PREROUTING -d 192.168.141.128/32 -p tcp -m tcp --dport 1122 -j DNAT --to-destination 192.168.100.100:22 -A POSTROUTING -s 192.168.100.100/32 -j SNAT --to-source 192.168.141.128 COMMIT # Completed on Wed Apr 17 03:35:23 2019 # Generated by iptables-save v1.4.21 on Wed Apr 17 03:35:23 2019 *filter :INPUT ACCEPT [2610:326613] :FORWARD ACCEPT [827:68276] :OUTPUT ACCEPT [1817:173008] COMMIT # Completed on Wed Apr 17 03:35:23 2019 [root@linux-001 ~]#
iptables recover file data
[root@linux-001 ~]# iptables -t nat -F
[root@linux-001 ~]# iptables -t nat
iptables v1.4.21: no command specified
Try `iptables -h' or 'iptables --help' for more information.
[root@linux-001 ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
[root@linux-001 ~]#
[root@linux-001 ~]# iptables-restore < my.tpt
[root@linux-001 ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 DNAT tcp -- * * 0.0.0.0/0 192.168.141.128 tcp dpt:1122 to:192.168.100.100:22
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 SNAT all -- * * 192.168.100.100 0.0.0.0/0 to:192.168.141.128
[root@linux-001 ~]# 2. 9 zone s of firewalld
2.1 start firewalld
In the previous iptables, we turned off firewalld and set startup not to start, installed iptables service, turned on iptables, and set startup. This time we reverse the operation, turn off iptables and turn on firewalld.
[root@linux-001 ~]# systemctl stop iptables.service
[root@linux-001 ~]# systemctl disable iptables.service
Removed symlink /etc/systemd/system/basic.target.wants/iptables.service.
[root@linux-001 ~]#
[root@linux-001 ~]# systemctl enable firewalld.service
Created symlink from /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service to /usr/lib/systemd/system/firewalld.service.
Created symlink from /etc/systemd/system/multi-user.target.wants/firewalld.service to /usr/lib/systemd/system/firewalld.service.
[root@linux-001 ~]# systemctl start firewalld.service
[root@linux-001 ~]# iptables -nvL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
28 2056 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
1 92 INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0
1 92 INPUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0
1 92 INPUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED
0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_direct all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_IN_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_IN_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_OUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FORWARD_OUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID
0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT 20 packets, 1904 bytes)
pkts bytes target prot opt in out source destination
20 1904 OUTPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0
Chain FORWARD_IN_ZONES (1 references)
pkts bytes target prot opt in out source destination
0 0 FWDI_public all -- ens37 * 0.0.0.0/0 0.0.0.0/0 [goto]
0 0 FWDI_public all -- ens33 * 0.0.0.0/0 0.0.0.0/0 [goto]
0 0 FWDI_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto]
Chain FORWARD_IN_ZONES_SOURCE (1 references)
pkts bytes target prot opt in out source destination
Chain FORWARD_OUT_ZONES (1 references)
pkts bytes target prot opt in out source destination
0 0 FWDO_public all -- * ens37 0.0.0.0/0 0.0.0.0/0 [goto]
0 0 FWDO_public all -- * ens33 0.0.0.0/0 0.0.0.0/0 [goto]
0 0 FWDO_public all -- * + 0.0.0.0/0 0.0.0.0/0 [goto]
Chain FORWARD_OUT_ZONES_SOURCE (1 references)
pkts bytes target prot opt in out source destination
Chain FORWARD_direct (1 references)
pkts bytes target prot opt in out source destination
Chain FWDI_public (3 references)
pkts bytes target prot opt in out source destination
0 0 FWDI_public_log all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FWDI_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FWDI_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
Chain FWDI_public_allow (1 references)
pkts bytes target prot opt in out source destination
Chain FWDI_public_deny (1 references)
pkts bytes target prot opt in out source destination
Chain FWDI_public_log (1 references)
pkts bytes target prot opt in out source destination
Chain FWDO_public (3 references)
pkts bytes target prot opt in out source destination
0 0 FWDO_public_log all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FWDO_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 FWDO_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0
Chain FWDO_public_allow (1 references)
pkts bytes target prot opt in out source destination
Chain FWDO_public_deny (1 references)
pkts bytes target prot opt in out source destination
Chain FWDO_public_log (1 references)
pkts bytes target prot opt in out source destination
Chain INPUT_ZONES (1 references)
pkts bytes target prot opt in out source destination
0 0 IN_public all -- ens37 * 0.0.0.0/0 0.0.0.0/0 [goto]
1 92 IN_public all -- ens33 * 0.0.0.0/0 0.0.0.0/0 [goto]
0 0 IN_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto]
Chain INPUT_ZONES_SOURCE (1 references)
pkts bytes target prot opt in out source destination
Chain INPUT_direct (1 references)
pkts bytes target prot opt in out source destination
Chain IN_public (3 references)
pkts bytes target prot opt in out source destination
1 92 IN_public_log all -- * * 0.0.0.0/0 0.0.0.0/0
1 92 IN_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0
1 92 IN_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0
Chain IN_public_allow (1 references)
pkts bytes target prot opt in out source destination
1 92 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 ctstate NEW
Chain IN_public_deny (1 references)
pkts bytes target prot opt in out source destination
Chain IN_public_log (1 references)
pkts bytes target prot opt in out source destination
Chain OUTPUT_direct (1 references)
pkts bytes target prot opt in out source destination
[root@linux-001 ~]#
[root@linux-001 ~]# iptables -t nat -nvL
Chain PREROUTING (policy ACCEPT 1 packets, 328 bytes)
pkts bytes target prot opt in out source destination
1 328 PREROUTING_direct all -- * * 0.0.0.0/0 0.0.0.0/0
1 328 PREROUTING_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0
1 328 PREROUTING_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 OUTPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 POSTROUTING_direct all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 POSTROUTING_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 POSTROUTING_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0
Chain OUTPUT_direct (1 references)
pkts bytes target prot opt in out source destination
Chain POSTROUTING_ZONES (1 references)
pkts bytes target prot opt in out source destination
0 0 POST_public all -- * ens37 0.0.0.0/0 0.0.0.0/0 [goto]
0 0 POST_public all -- * ens33 0.0.0.0/0 0.0.0.0/0 [goto]
0 0 POST_public all -- * + 0.0.0.0/0 0.0.0.0/0 [goto]
Chain POSTROUTING_ZONES_SOURCE (1 references)
pkts bytes target prot opt in out source destination
Chain POSTROUTING_direct (1 references)
pkts bytes target prot opt in out source destination
Chain POST_public (3 references)
pkts bytes target prot opt in out source destination
0 0 POST_public_log all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 POST_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0
0 0 POST_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0
Chain POST_public_allow (1 references)
pkts bytes target prot opt in out source destination
Chain POST_public_deny (1 references)
pkts bytes target prot opt in out source destination
Chain POST_public_log (1 references)
pkts bytes target prot opt in out source destination
Chain PREROUTING_ZONES (1 references)
pkts bytes target prot opt in out source destination
0 0 PRE_public all -- ens37 * 0.0.0.0/0 0.0.0.0/0 [goto]
1 328 PRE_public all -- ens33 * 0.0.0.0/0 0.0.0.0/0 [goto]
0 0 PRE_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto]
Chain PREROUTING_ZONES_SOURCE (1 references)
pkts bytes target prot opt in out source destination
Chain PREROUTING_direct (1 references)
pkts bytes target prot opt in out source destination
Chain PRE_public (3 references)
pkts bytes target prot opt in out source destination
1 328 PRE_public_log all -- * * 0.0.0.0/0 0.0.0.0/0
1 328 PRE_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0
1 328 PRE_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0
Chain PRE_public_allow (1 references)
pkts bytes target prot opt in out source destination
Chain PRE_public_deny (1 references)
pkts bytes target prot opt in out source destination
Chain PRE_public_log (1 references)
pkts bytes target prot opt in out source destination
[root@linux-001 ~]# 2.2 zone in firewalld
Firewalld has 9 zones by default. The default zone is public, which can be understood as the unit of firewalld: rule set.
## see firewalld Planted zone ## [root@linux-02 ~]# firewall-cmd --get-zones block dmz drop external home internal public trusted work [root@linux-02 ~]# ## View default zone What is it? ## [root@linux-02 ~]# firewall-cmd --get-default-zone public [root@linux-02 ~]#
The differences between firewalld zone s are as follows:

3.firewalld operation on zone
Firewall CMD -- set default zone = work / / set default zone Firewall CMD -- get zone of interface = ens33 / / query the specified network card Firewall CMD -- zone = public -- add interface = Lo / / set the zone for the specified network card Firewall CMD -- zone = DMZ -- change interface = Lo / / change the zone for the network card Firewall CMD -- zone = DMZ -- remove interface = Lo / / delete zone for network card Firewall CMD -- get active zones / / view the zones of all network cards in the system
## Set default zone ## [root@linux-02 ~]# firewall-cmd --set-default-zone=work success [root@linux-02 ~]# firewall-cmd --get-default-zone work ## Check the of the specified network card zone ## [root@linux-02 ~]# firewall-cmd --get-zone-of-interface=ens33 work [root@linux-02 ~]# firewall-cmd --get-zone-of-interface=ens37 work [root@linux-02 ~]# firewall-cmd --get-zone-of-interface=lo no zone ## Settings for the specified network card zone ## [root@linux-02 ~]# firewall-cmd --zone=dmz --add-interface=ens37 The interface is under control of NetworkManager, setting zone to 'dmz'. success [root@linux-02 ~]# firewall-cmd --get-zone-of-interface=ens37 dmz ## Changes to the specified network card zone ## [root@linux-02 ~]# firewall-cmd --zone=public --change-interface=ens37 The interface is under control of NetworkManager, setting zone to 'public'. success [root@linux-02 ~]# firewall-cmd --get-zone-of-interface=ens37 public ## Delete the specified network card zone ## [root@linux-02 ~]# firewall-cmd --zone=public --remove-interface=ens37 The interface is under control of NetworkManager, setting zone to default. success [root@linux-02 ~]# firewall-cmd --get-zone-of-interface=ens37 work ## View the of all network cards zone ## [root@linux-02 ~]# firewall-cmd --get-active-zones work interfaces: ens33 ens37
4. Operation on service in firewalld
Firewall CMD -- get services / / view all series Firewall CMD -- List Services / / view the service s in the current zone Firewall CMD -- zone = public -- add service = http / / add HTTP to the public zone firewall-cmd --zone=public --remove-service=http Ls / usr / lib / firewalld / zones / / profile template for zone Firewall CMD -- zone = public -- add service = http -- permanent / / after changing the configuration file, the configuration file will be generated under the / etc/firewalld/zones directory
## View all service ## [root@linux-02 ~]# firewall-cmd --get-service RH-Satellite-6 amanda-client amanda-k5-client bacula bacula-client bgp bitcoin bitcoin-rpc bitcoin-testnet bitcoin-testnet-rpc ceph ceph-mon cfengine condor-collector ctdb dhcp dhcpv6 dhcpv6-client dns docker-registry docker-swarm dropbox-lansync elasticsearch freeipa-ldap freeipa-ldaps freeipa-replication freeipa-trust ftp ganglia-client ganglia-master git gre high-availability http https imap imaps ipp ipp-client ipsec irc ircs iscsi-target jenkins kadmin kerberos kibana klogin kpasswd kprop kshell ldap ldaps libvirt libvirt-tls managesieve mdns minidlna mongodb mosh mountd ms-wbt mssql murmur mysql nfs nfs3 nmea-0183 nrpe ntp openvpn ovirt-imageio ovirt-storageconsole ovirt-vmconsole pmcd pmproxy pmwebapi pmwebapis pop3 pop3s postgresql privoxy proxy-dhcp ptp pulseaudio puppetmaster quassel radius redis rpc-bind rsh rsyncd samba samba-client sane sip sips smtp smtp-submission smtps snmp snmptrap spideroak-lansync squid ssh syncthing syncthing-gui synergy syslog syslog-tls telnet tftp tftp-client tinc tor-socks transmission-client upnp-client vdsm vnc-server wbem-https xmpp-bosh xmpp-client xmpp-local xmpp-server zabbix-agent zabbix-server ## View current zone What are there in the next service ## [root@linux-02 ~]# firewall-cmd --list-services ssh dhcpv6-client ## see public of zone What are there in the next service ## [root@linux-02 ~]# firewall-cmd --zone=public --list-services ssh dhcpv6-client ## hold http increase to public of zone lower ## [root@linux-02 ~]# firewall-cmd --zone=public --add-service=http success [root@linux-02 ~]# firewall-cmd --zone=public --list-services ssh dhcpv6-client http ## hold public Where zone Lower http service delete ## [root@linux-02 ~]# firewall-cmd --zone=public --remove-service=http success [root@linux-02 ~]# firewall-cmd --zone=public --list-services ssh dhcpv6-client ## Add service Save to the configuration file. The configuration file is in the/etc/firewalld/zones/lower ## [root@linux-02 ~]# firewall-cmd --zone=public --add-service=http --permanent success [root@linux-02 ~]# ls /etc/firewalld/zones/ public.xml public.xml.old [root@linux-02 ~]# cat /etc/firewalld/zones/public.xml <?xml version="1.0" encoding="utf-8"?> <zone> <short>Public</short> <description>For use in public areas. You do not trust the other computers on networks to not harm your computer. Only selected incoming connections are accepted.</description> <service name="ssh"/> <service name="dhcpv6-client"/> <service name="http"/> </zone> ## firewalld in zones Template in/usr/bin/firewalld/zones/ ## [root@linux-02 ~]# ls /usr/lib/firewalld/zones/ block.xml dmz.xml drop.xml external.xml home.xml internal.xml public.xml trusted.xml work.xml [root@linux-02 ~]# ls /usr/lib/firewalld/services/ amanda-client.xml ftp.xml libvirt-tls.xml pop3.xml ssh.xml amanda-k5-client.xml ganglia-client.xml libvirt.xml postgresql.xml syncthing-gui.xml bacula-client.xml ganglia-master.xml managesieve.xml privoxy.xml syncthing.xml bacula.xml git.xml mdns.xml proxy-dhcp.xml synergy.xml bgp.xml gre.xml minidlna.xml ptp.xml syslog-tls.xml bitcoin-rpc.xml high-availability.xml mongodb.xml pulseaudio.xml syslog.xml bitcoin-testnet-rpc.xml https.xml mosh.xml puppetmaster.xml telnet.xml bitcoin-testnet.xml http.xml mountd.xml quassel.xml tftp-client.xml bitcoin.xml imaps.xml mssql.xml radius.xml tftp.xml ceph-mon.xml imap.xml ms-wbt.xml redis.xml tinc.xml ceph.xml ipp-client.xml murmur.xml RH-Satellite-6.xml tor-socks.xml cfengine.xml ipp.xml mysql.xml rpc-bind.xml transmission-client.xml condor-collector.xml ipsec.xml nfs3.xml rsh.xml upnp-client.xml ctdb.xml ircs.xml nfs.xml rsyncd.xml vdsm.xml dhcpv6-client.xml irc.xml nmea-0183.xml samba-client.xml vnc-server.xml dhcpv6.xml iscsi-target.xml nrpe.xml samba.xml wbem-https.xml dhcp.xml jenkins.xml ntp.xml sane.xml xmpp-bosh.xml dns.xml kadmin.xml openvpn.xml sips.xml xmpp-client.xml docker-registry.xml kerberos.xml ovirt-imageio.xml sip.xml xmpp-local.xml docker-swarm.xml kibana.xml ovirt-storageconsole.xml smtp-submission.xml xmpp-server.xml dropbox-lansync.xml klogin.xml ovirt-vmconsole.xml smtps.xml zabbix-agent.xml elasticsearch.xml kpasswd.xml pmcd.xml smtp.xml zabbix-server.xml freeipa-ldaps.xml kprop.xml pmproxy.xml snmptrap.xml freeipa-ldap.xml kshell.xml pmwebapis.xml snmp.xml freeipa-replication.xml ldaps.xml pmwebapi.xml spideroak-lansync.xml freeipa-trust.xml ldap.xml pop3s.xml squid.xml [root@linux-02 ~]#
Requirement: ftp service defines port 1121. ftp needs to be released under the work zone Solution:
- cp /usr/lib/firewalld/services/ftp.xml /etc/firewalld/services
- vi /etc/firewalld/services/ftp.xml / / change 21 to 1121
- cp /usr/lib/firewalld/zones/work.xml /etc/firewalld/zones/
- vi /etc/firewalld/zones/work.xml / / add a line < service name = "ftp" / >
- Firewall CMD -- reload / / reload
- firewall-cmd --zone=work --list-services
[root@linux-02 ~]# cp /usr/lib/firewalld/services/ftp.xml /etc/firewalld/services/ [root@linux-02 ~]# vim /etc/firewalld/services/ftp.xml <?xml version="1.0" encoding="utf-8"?> <service> <short>FTP</short> <description>FTP is a protocol used for remote file transfer. If you plan to make your FTP server publicly available, enable this option. You need the vsftpd package installed for this option to be useful.</description> <port protocol="tcp" port="1121"/> <module name="nf_conntrack_ftp"/> </service> [root@linux-02 ~]# cp /usr/lib/firewalld/zones/work.xml /etc/firewalld/zones/ [root@linux-02 ~]# vim /etc/firewalld/zones/work.xml <?xml version="1.0" encoding="utf-8"?> <zone> <short>Work</short> <description>For use in work areas. You mostly trust the other computers on networks to not harm your computer. Only selected incoming connections are accepted.</description> <service name="ssh"/> <service name="dhcpv6-client"/> <service name="ftp"/> </zone> [root@linux-02 ~]# firewall-cmd --reload success [root@linux-02 ~]# firewall-cmd --zone=work --list-services ssh dhcpv6-client ftp
5.linux task planning cron
5.1 crontab options:
option | meaning |
|---|---|
-u | user |
-e | Create scheduled task |
-l | View scheduled tasks |
-r | Delete scheduled task |
systemctl start crond.service
5.2 format of crontab
Field name | explain | Value range |
|---|---|---|
minute | The minute ordinal of each hour | 0-59 |
hour | The hour of the day | 0-24 |
day | The day of each month | 1-31 |
month | Which month of each year | 1-12 |
What day is today? | The day of the week | 0-6 (both 0 and 7 represent Sunday) |
Commands executed | Commands and parameters to be executed |
## crontab Format: minute hour date month day of the week execution command ## [root@linux-02 ~]# cat /etc/crontab SHELL=/bin/bash PATH=/sbin:/bin:/usr/sbin:/usr/bin MAILTO=root # For details see man 4 crontabs # Example of job definition: # .---------------- minute (0 - 59) # | .------------- hour (0 - 23) # | | .---------- day of month (1 - 31) # | | | .------- month (1 - 12) OR jan,feb,mar,apr ... # | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat # | | | | | # * * * * * user-name command to be executed ## Create a scheduled task ## [root@linux-02 ~]# crontab -e * * * * * command path // The first five fields can be rounded to specify when to start working. The sixth field is the string, that is, the command field, which includes the commands scheduled by crontab. The fields are separated by spaces and tabs. ## View scheduled tasks ## [root@linux-02 ~]# crontab -l 30 2 * * * sh /root/oss.sh
5.3 some common special symbols in crontab command:
Symbol | explain |
|---|---|
* | Represents any time |
, | Indicates segmentation. For example, 2 and 5 in the second paragraph represent 2 points and 5 points |
- | Indicates a paragraph. For example, in the second paragraph: 1-5, it means 1 to 5 points |
/n | It means that each n unit is executed once. For example, * / 1 in the second paragraph means that the command is executed every 1 hour. It can also be written as 1-23 / 1 |
5.4 crontab backup
The scheduled task created by each user is named with the user name in / var/spool/cron / directory. If backup is required, you can directly copy this file.
6. System service management tool chkconfig before CentOS 7
The chkconfig command is mainly used to update (start or stop) and query the run level information of system services. Remember that chkconfig does not automatically disable or activate a service immediately, it simply changes the symbolic connection.
6.1 display the operation status information of all operation level system services
[root@linux-02 ~]# chkconfig --list
Note: the output result is only displayed SysV Service, not included
Primordial systemd Service. SysV Configuration data
May be native systemd Configure overrides.
To list systemd Service, please execute 'systemctl list-unit-files'.
View in detail target Please execute
'systemctl list-dependencies [target]'.
netconsole 0:shut 1:shut 2:shut 3:shut 4:shut 5:shut 6:shut
network 0:shut 1:shut 2:open 3:open 4:open 5:open 6:shut6.2 parameter usage
– add adds the specified system service so that the chkconfig command can manage it, and adds relevant data in the description file of system startup. – del deletes the specified system service, which is no longer managed by the chkconfig command, and deletes the relevant data in the description file of system startup. – level < level code > specifies the execution level at which the read system service is to be turned on or off. Level 0 indicates shutdown Level 1 indicates single user mode Level 2 indicates multi-user command line mode without network connection Level 3 indicates multi-user command line mode with network connection Level 4 indicates: not available Level 5 indicates multi-user mode with graphical interface Level 6 means restart It should be noted that the level option can specify the run level to view, not necessarily the current run level. For each run level, there can only be one start script or stop script. When switching the run level, init will not restart the services that have been started or stop the services that have been stopped again.
6.3 service level shutdown
[root@linux-02 ~]# chkconfig --level 3 network off
[root@linux-02 ~]# chkconfig --list
Note: the output result is only displayed SysV Service, not included
Primordial systemd Service. SysV Configuration data
May be native systemd Configure overrides.
To list systemd Service, please execute 'systemctl list-unit-files'.
View in detail target Please execute
'systemctl list-dependencies [target]'.
netconsole 0:shut 1:shut 2:shut 3:shut 4:shut 5:shut 6:shut
network 0:shut 1:shut 2:open 3:shut 4:open 5:open 6:shut
[root@linux-02 ~]# chkconfig --level 345 network off
[root@linux-02 ~]# chkconfig --list
Note: the output result is only displayed SysV Service, not included
Primordial systemd Service. SysV Configuration data
May be native systemd Configure overrides.
To list systemd Service, please execute 'systemctl list-unit-files'.
View in detail target Please execute
'systemctl list-dependencies [target]'.
netconsole 0:shut 1:shut 2:shut 3:shut 4:shut 5:shut 6:shut
network 0:shut 1:shut 2:open 3:shut 4:shut 5:shut 6:shut
[root@linux-02 ~]# 6.4 deleting a service
[root@linux-02 ~]# chkconfig --del network
[root@linux-02 ~]# chkconfig --list
Note: the output result is only displayed SysV Service, not included
Primordial systemd Service. SysV Configuration data
May be native systemd Configure overrides.
To list systemd Service, please execute 'systemctl list-unit-files'.
View in detail target Please execute
'systemctl list-dependencies [target]'.
netconsole 0:shut 1:shut 2:shut 3:shut 4:shut 5:shut 6:shut
[root@linux-02 ~]# 6.5 add a service
[root@linux-02 ~]# chkconfig --add network
[root@linux-02 ~]# chkconfig --list
Note: the output result is only displayed SysV Service, not included
Primordial systemd Service. SysV Configuration data
May be native systemd Configure overrides.
To list systemd Service, please execute 'systemctl list-unit-files'.
View in detail target Please execute
'systemctl list-dependencies [target]'.
netconsole 0:shut 1:shut 2:shut 3:shut 4:shut 5:shut 6:shut
network 0:shut 1:shut 2:open 3:open 4:open 5:open 6:shut7. CentOS service management tool systemd
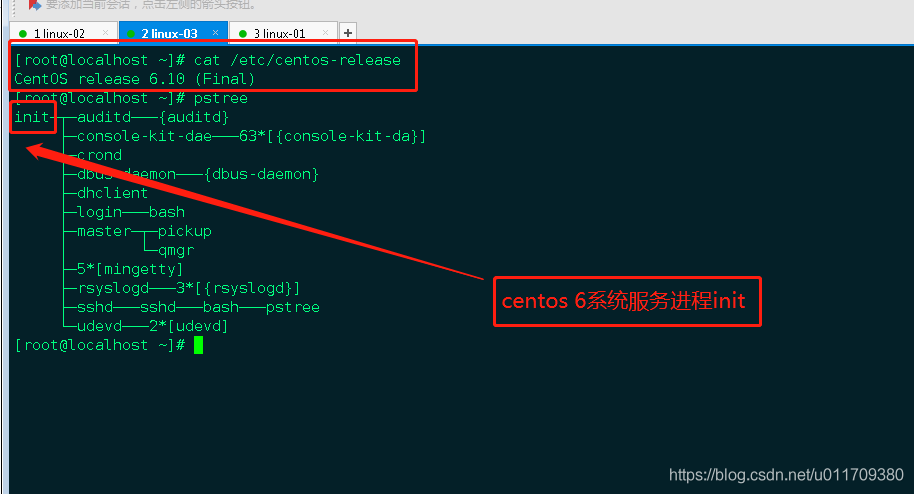
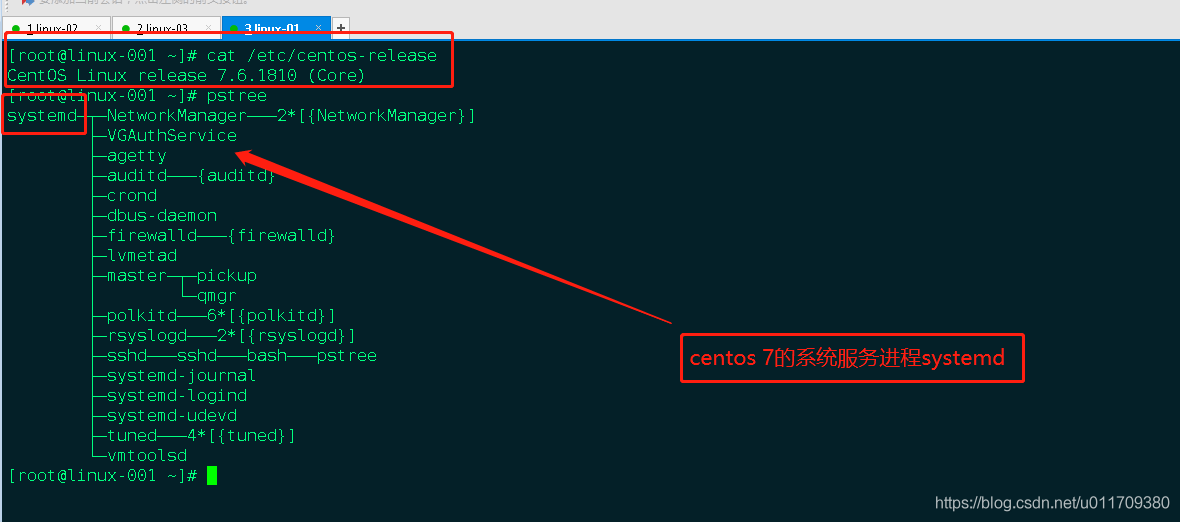
In RHEL7, the initial process becomes systemd. The initial process used by RHEL6 and previous versions is init. Init is a linear startup process, starting one by one, which is relatively slow; systemd can start multiple processes and improve the speed a lot. In addition, systemd also simplifies development and integrates logs.
7.1 list all service names
[root@linux-02 ~]# systemctl list-unit-files UNIT FILE STATE proc-sys-fs-binfmt_misc.automount static dev-hugepages.mount static dev-mqueue.mount static proc-sys-fs-binfmt_misc.mount static sys-fs-fuse-connections.mount static sys-kernel-config.mount static sys-kernel-debug.mount static tmp.mount disabled brandbot.path disabled systemd-ask-password-console.path static systemd-ask-password-plymouth.path static systemd-ask-password-wall.path static session-1.scope static session-32.scope static session-37.scope static arp-ethers.service disabled auditd.service enabled autovt@.service enabled blk-availability.service disabled brandbot.service static console-getty.service disabled console-shell.service disabled container-getty@.service static cpupower.service disabled crond.service enabled ...... runlevel0.target disabled runlevel1.target disabled runlevel2.target enabled runlevel3.target enabled runlevel4.target enabled runlevel5.target static runlevel6.target disabled shutdown.target static sigpwr.target static sleep.target static slices.target static smartcard.target static sockets.target static sound.target static suspend.target static swap.target static sysinit.target static system-update.target static time-sync.target static timers.target static umount.target static fstrim.timer disabled systemd-readahead-done.timer indirect systemd-tmpfiles-clean.timer static 226 unit files listed. lines 204-229/229 (END)
7.2 list all units with service type
[root@linux-02 ~]# systemctl list-units --all --type=service UNIT LOAD ACTIVE SUB DESCRIPTION auditd.service loaded active running Security Auditing Service cpupower.service loaded inactive dead Configure CPU power related settings crond.service loaded active running Command Scheduler dbus.service loaded active running D-Bus System Message Bus ● display-manager.service not-found inactive dead display-manager.service dracut-shutdown.service loaded inactive dead Restore /run/initramfs ebtables.service loaded inactive dead Ethernet Bridge Filtering tables emergency.service loaded inactive dead Emergency Shell ● exim.service not-found inactive dead exim.service firewalld.service loaded active running firewalld - dynamic firewall daemon getty@tty1.service loaded active running Getty on tty1 ● ip6tables.service not-found inactive dead ip6tables.service ● ipset.service not-found inactive dead ipset.service ● iptables.service not-found inactive dead iptables.service irqbalance.service loaded inactive dead irqbalance daemon kdump.service loaded active exited Crash recovery kernel arming kmod-static-nodes.service loaded active exited Create list of required static device nodes f microcode.service loaded inactive dead Load CPU microcode update network.service loaded active exited LSB: Bring up/down networking NetworkManager-wait-online.service loaded active exited Network Manager Wait Online NetworkManager.service loaded active running Network Manager plymouth-quit-wait.service loaded inactive dead Wait for Plymouth Boot Screen to Quit plymouth-quit.service loaded inactive dead Terminate Plymouth Boot Screen plymouth-read-write.service loaded inactive dead Tell Plymouth To Write Out Runtime Data plymouth-start.service loaded inactive dead Show Plymouth Boot Screen ...... LOAD = Reflects whether the unit definition was properly loaded. ACTIVE = The high-level unit activation state, i.e. generalization of SUB. SUB = The low-level unit activation state, values depend on unit type. 83 loaded units listed. To show all installed unit files use 'systemctl list-unit-files'.
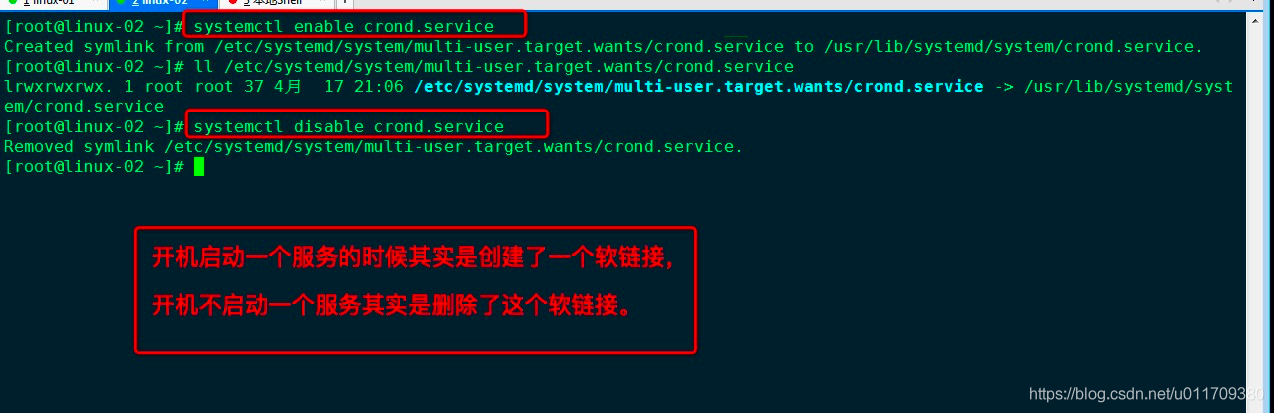
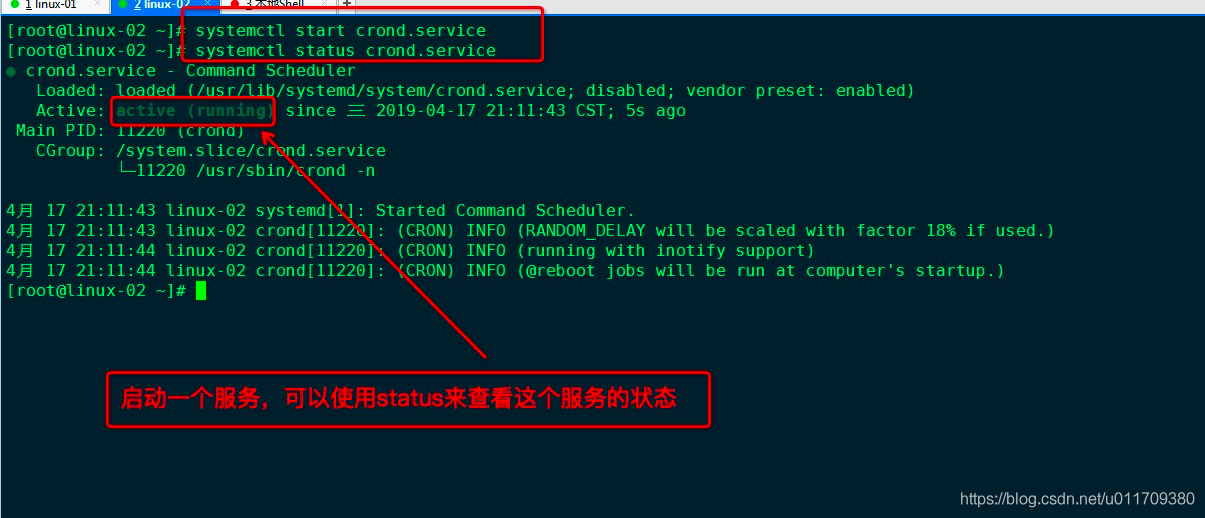
7.3 several common service related commands
systemctl enable crond.service / / start the service systemctl disable crond / / disable crond systemctl status crond / / view status systemctl stop crond / / stop the service systemctl start crond / / start the service systemctl restart crond / / restart the service Systemctl is enabled crond / / check whether the service is started
8. unit introduction
System D consists of a concept called Unit. It saves the configuration files of services, devices, mount points and other information of the operating system, and can handle the dependencies between different units. Most units are statically defined in the Unit file, and some are generated dynamically. The Unit has multiple states:
- Active is active and is currently running
- The stopped is (inactive), which has been stopped at present
- The one in startup is (activating), which is currently starting
- In stopping, it is (deactivating) and is currently stopping
- The failed state means that an error is encountered during the unit startup, such as the file or path cannot be found or the process crashes during operation.
The file locations of all units in the system / usr/lib/systemd/system have a total of 11 unit types: Service system service target is a group of multiple unit s Device hardware device Mount file system mount point automount auto mount point Path file or path scope is not an external process started by systemd slice process group snapshot systemd snapshot Socket interprocess communication socket swap swap file Timer timer
Unit type | explain |
|---|---|
service unit | It is used to encapsulate a background service process, such as starting a firewall through systemctl start firewalld. This belongs to the service unit. |
socket unit | It is used to encapsulate a background service process, such as starting a firewall through systemctl start firewalld. This belongs to the service unit. |
target unit | It is used to logically combine multiple units so that they can start at the same time. |
device unit | It is used to encapsulate a device file and can be used for device based startup. Not every device file needs a device unit, but every device marked by udev rules must appear as a device unit. |
mount unit | Used to encapsulate a file system mount point (backward compatible with / etc/fstab) |
automount unit | It is used to encapsulate an automatic mount point of a file system. It will be mounted only when the file system is accessed. It replaces the traditional autofs service. |
timer unit | It is used to encapsulate a time triggered action, which replaces scheduled tasks such as atd and crond. |
swap unit | It is used to encapsulate a swap partition or swap file. It is similar to mount. |
path unit | Used to start other services based on changes in specific objects on the file system. |
slice unit | It is used to control the overall resource occupation of all processes in a specific cggroup. |
scope unit | It is similar to the service unit, but it is automatically created by systemd according to the information received by the D-bus interface and can be used to manage externally created processes. |
9.target introduction
When learning systemctl earlier, you can perform start,stop,restart and other operations on the specific service at the end of the service; In addition, another kind of suffix ends with target. These target services can be regarded as a collection of services, which predefine which services run and which do not run. This concept is very similar to the runlevel concept before RHEL6.
View target in the system
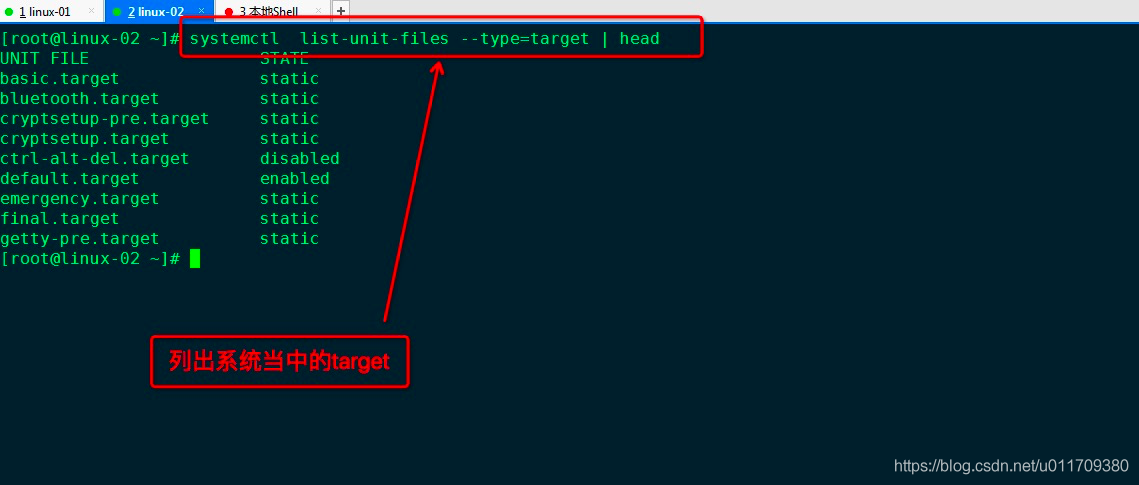
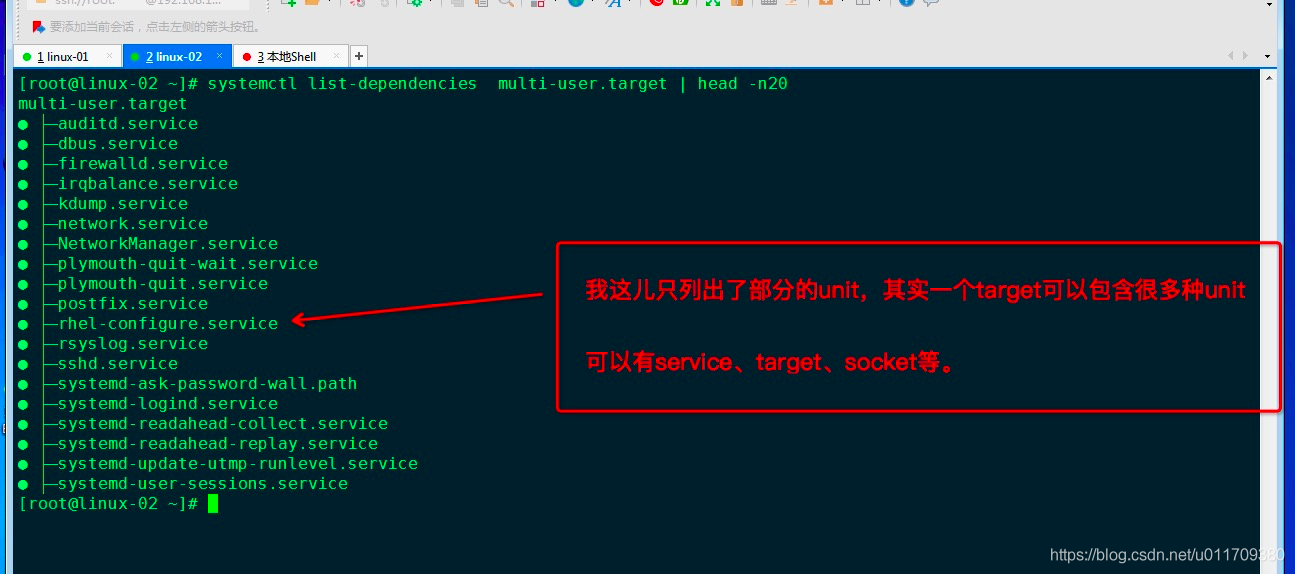
View which unit s are included in the specified target:
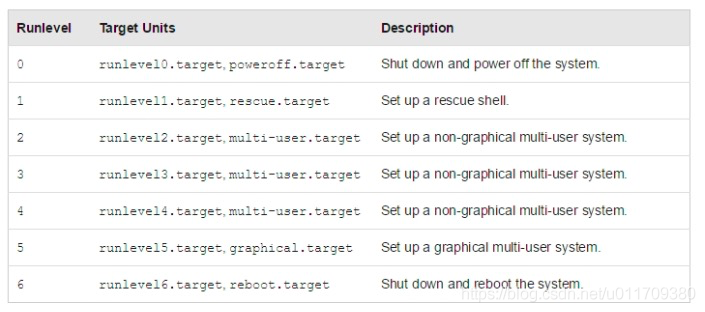
Versions before RHEL6 can be found in / etc / RC D view 7 operation levels. Each operation level corresponds to different functions. For example, 0 is shutdown, 1 is single user, 2 is multi-user (no network), 3 is multi-user, 4 is useless, 5 is graphical interface, and 6 is restart. You can use init 0 to shut down directly, and so on. In RHEL7, target has similar and equivalent definitions:
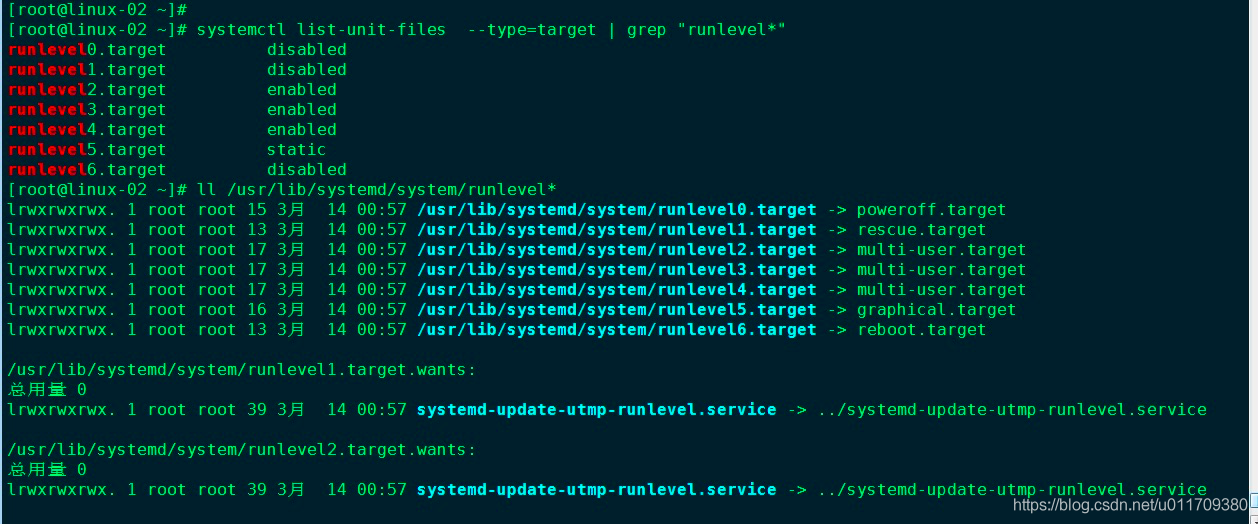
To view the default target:
[root@linux-02 ~]# systemctl get-default multi-user.target
Check which target a service belongs to
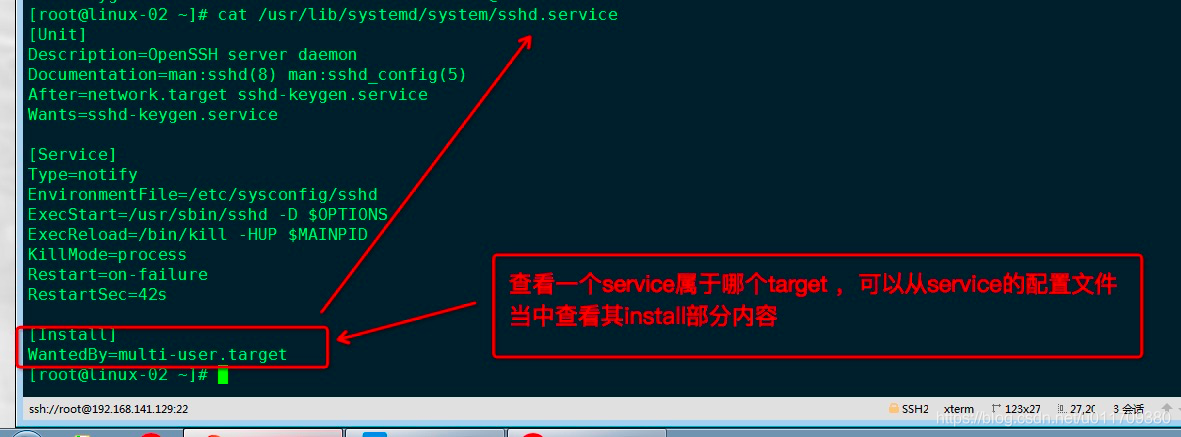
After class summary
1. The system releases a port 80
## use firewall Add 80 ports ##
[root@linux-001 ~]# firewall-cmd --add-port=80/tcp
## use iptables Add 80 ports ##
[root@linux-001 ~]# iptables -A INPUT -p tcp -dport 80 -j ACCEPT
## firewall The added port 80 is saved in the configuration file and reloaded to make its host restart take effect ##
[root@linux-001 ~]# firewall-cmd --permanent --add-port=80/tcp && firewall-cmd --reload
## firewall add to http The service is saved in the configuration file and reloaded to make its host restart take effect ##
[root@linux-001 ~]# firewall-cmd --permanent --add-service=http && firewall-cmd --reload2. How to add custom rules for firewall CMD
The following is just a brief description and example of user-defined rules, which is actually what is in the help document; For detailed instructions, please refer to firewall CMD -- help
The parameters passed are consistent with iptables, ip6tables and ebtables!
The Centos7 Firewall user interface still calls the iptables module of the system kernel to set rules!
Direct options
– direct needs to be the first parameter of the direct option.
Pass the command to the firewall. Parameters can be iptables, ip6tables and ebtables command line parameters.
firewall-cmd --direct --passthrough { ipv4 | ipv6 | eb }
For table Add a new chain.
firewall-cmd --direct --add-chain { ipv4 | ipv6 | eb }
From table Delete chain from.
firewall-cmd --direct --remove-chain { ipv4 | ipv6 | eb }
Query whether the chain exists and the table . if yes, return 0, otherwise return 1
firewall-cmd --direct --query-chain { ipv4 | ipv6 | eb }
If enabled, this command will have a return value. This command has no output information.
Gets a space delimited table List of chains in.
firewall-cmd --direct --get-chains { ipv4 | ipv6 | eb }
For table Add a chain with parameter, and set the priority to.
firewall-cmd --direct --add-rule { ipv4 | ipv6 | eb }
Reference example:
Method -: [reload takes effect. Restart after modification can take effect]
firewall-cmd --permanent --direct --add-rule ipv4 filter INPUT 1 -s 192.168.1.0/24 -p tcp --dport=22 -j ACCEPT
firewall-cmd --permanent --direct --add-rule ipv4 filter INPUT 2 -p tcp --dport=22 -j DROP
Mode 2: [failure after heavy load or restart]
iptables -t filter -I INPUT_direct -s 192.168.1.20 -p tcp --dport=22 -j ACCEPT
iptables -A INPUT_direct -p tcp --dport=22 -j DROP
From table Delete a chain with parameters from.
firewall-cmd --direct --remove-rule { ipv4 | ipv6 | eb }
firewall-cmd --direct --remove-rule ipv4 filter INPUT 2 -p tcp --dport=22 -j DROP
Query whether the chain with parameters exists in the table
firewall-cmd --direct --query-rule { ipv4 | ipv6 | eb }
Get table All rules added to the chain in are separated by a newline.
firewall-cmd --direct --get-rules { ipv4 | ipv6 | eb }
This section extends the link: https://blog.51cto.com/jevic/1785162
3. System service startup sequence
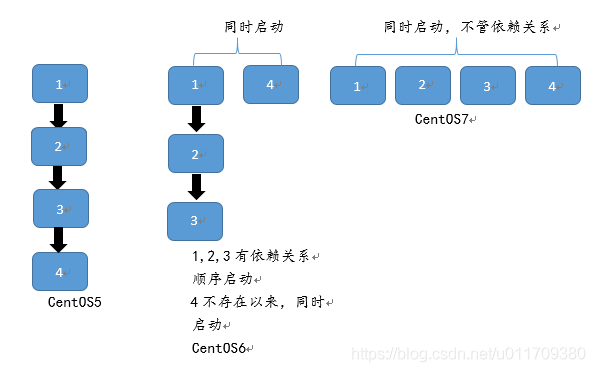
After the Linux kernel is loaded and started, the first process in user space is the initialization process. The physical file of this program is agreed to be located in / sbin/init. Of course, the kernel can also start the specified program by passing kernel parameters. This process is characterized by a process number of 1, which represents the first running user space process. Different distributions adopt different startup procedures, mainly including the following mainstream options:
Linux distributions represented by Ubuntu adopt upstart CentOS7. System V init before version 0 CentOS7.0 version of systemd