
This is a basic operation example of Firewalld, using the Firewalld graphical operation interface for access control operation.
Experimental topology
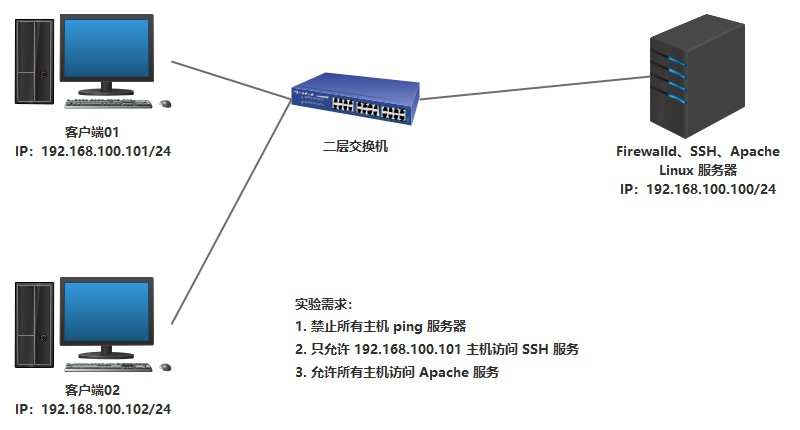
requirement analysis
First, the topology involves two regions. Here, work and public regions are used to make corresponding rules.
1. icmp is forbidden in the work area. 192.168.100.101 is allowed to access SSH service and Apache service.
2. icmp, SSH service and Apache service are forbidden in public area.
Analysis method: data processing flow based on firewall, please refer to Last blog.
Operation process
Basic preparation
- server installs Apache service. SSH service already exists by default.
[root@server ~]# yum install -y httpd [root@server ~]# echo "This is test page , all host can access" > /var/www/html/index.html [root@server ~]# systemctl start httpd.service
- By default, you can ping, ssh and access apache without turning off the firewall.
[root@host01 ~]# ping -c4 192.168.100.100 PING 192.168.100.100 (192.168.100.100) 56(84) bytes of data. 64 bytes from 192.168.100.100: icmp_seq=1 ttl=64 time=0.573 ms 64 bytes from 192.168.100.100: icmp_seq=2 ttl=64 time=0.575 ms 64 bytes from 192.168.100.100: icmp_seq=3 ttl=64 time=1.15 ms 64 bytes from 192.168.100.100: icmp_seq=4 ttl=64 time=0.441 ms --- 192.168.100.100 ping statistics --- 4 packets transmitted, 4 received, 0% packet loss, time 3003ms rtt min/avg/max/mdev = 0.441/0.686/1.156/0.277 ms
[root@host01 ~]# curl 192.168.100.100 curl: (7) Failed connect to 192.168.100.100:80; No route to host
[root@host01 ~]# ssh root@192.168.100.100 The authenticity of host '192.168.100.100 (192.168.100.100)' can't be established. ECDSA key fingerprint is SHA256:5GGc1rmzWwjF+ozz/PPTyLO2s6NmFHSxbzCNsLazXhY. ECDSA key fingerprint is MD5:0b:f5:62:d7:a4:1f:05:64:0b:7f:22:62:11:64:07:61. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '192.168.100.100' (ECDSA) to the list of known hosts. root@192.168.100.100's password: Last login: Wed Oct 23 09:55:12 2019 [root@server ~]# logout Connection to 192.168.100.100 closed.
Configure firewall
[root@server ~]# firewall-config
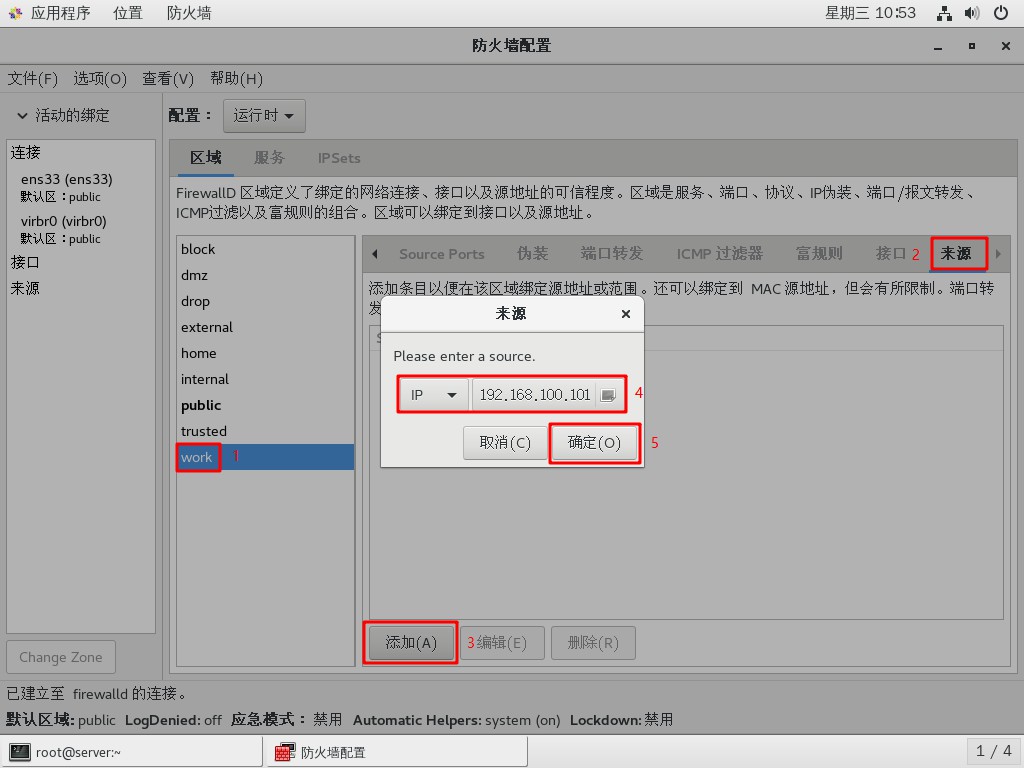
- Add source to work area: 192.168.100.101
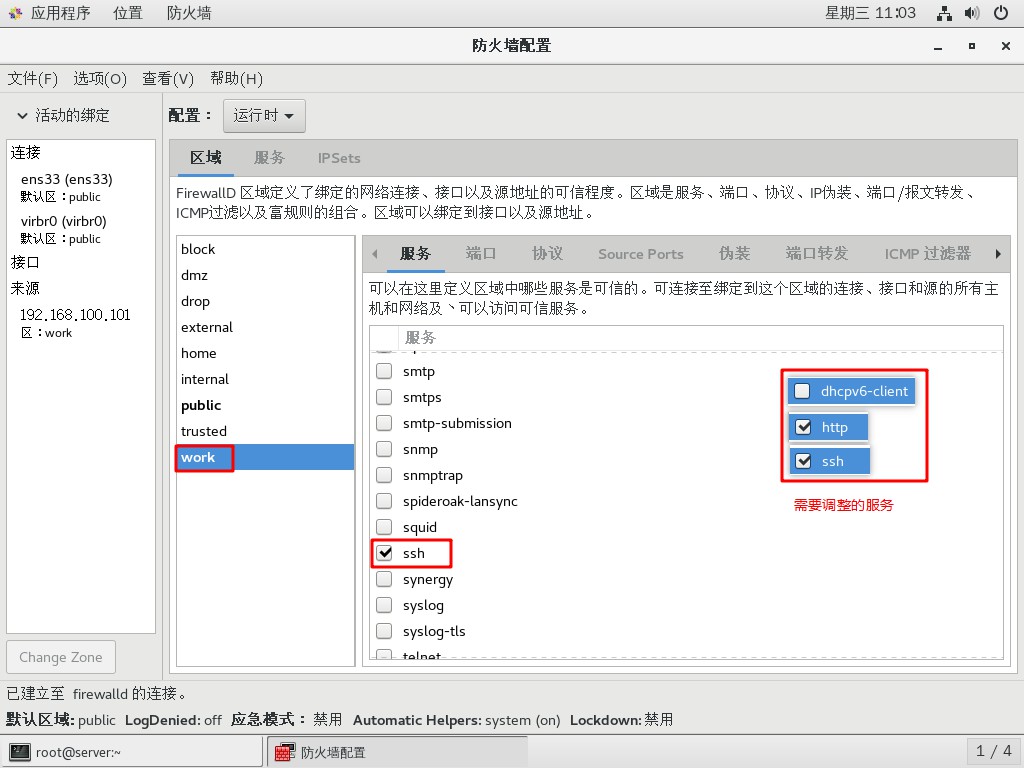
- Allow http and ssh services in the work area, and prohibit other existing services
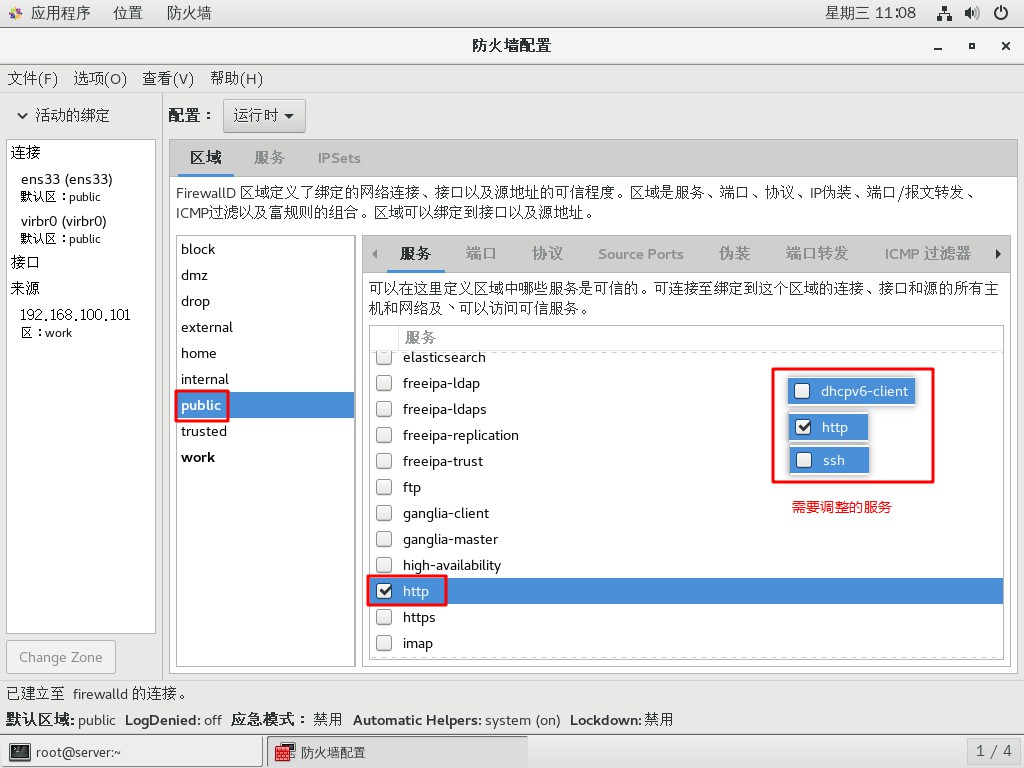
- Allow http services in the public area and prohibit other existing services
- Disable request request through ICMP filter, in both areas.
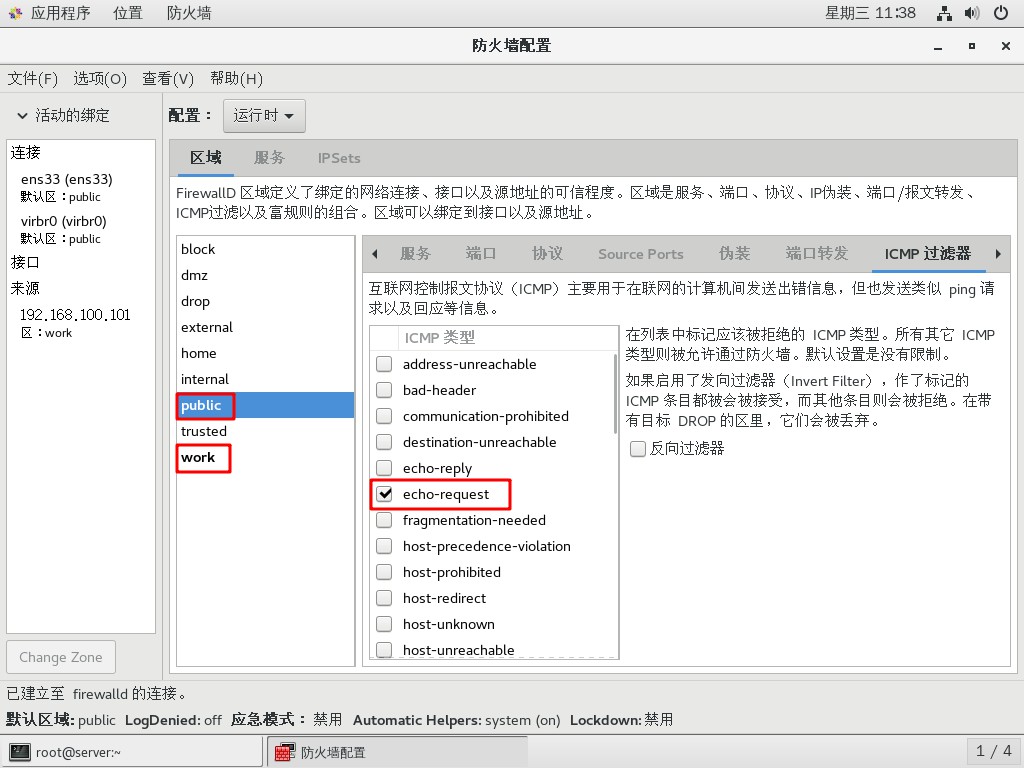
Result verification
- Website access
[root@host01 ~]# curl 192.168.100.100 This is test page , all host can access
[root@host02 ~]# curl 192.168.100.100 This is test page , all host can access
- SSH remote
[root@host01 ~]# ssh root@192.168.100.100 root@192.168.100.100's password: Last login: Wed Oct 23 10:47:15 2019 [root@server ~]# logout Connection to 192.168.100.100 closed.
[root@host02 ~]# ssh root@192.168.100.100 ssh: connect to host 192.168.100.100 port 22: No route to host
- ping test
[root@host01 ~]# ping -c4 192.168.100.100 PING 192.168.100.100 (192.168.100.100) 56(84) bytes of data. From 192.168.100.100 icmp_seq=1 Destination Host Prohibited From 192.168.100.100 icmp_seq=2 Destination Host Prohibited From 192.168.100.100 icmp_seq=3 Destination Host Prohibited From 192.168.100.100 icmp_seq=4 Destination Host Prohibited --- 192.168.100.100 ping statistics --- 4 packets transmitted, 0 received, +4 errors, 100% packet loss, time 3001ms
[root@host02 ~]# ping -c4 192.168.100.100 PING 192.168.100.100 (192.168.100.100) 56(84) bytes of data. From 192.168.100.100 icmp_seq=1 Destination Host Prohibited From 192.168.100.100 icmp_seq=2 Destination Host Prohibited From 192.168.100.100 icmp_seq=3 Destination Host Prohibited From 192.168.100.100 icmp_seq=4 Destination Host Prohibited --- 192.168.100.100 ping statistics --- 4 packets transmitted, 0 received, +4 errors, 100% packet loss, time 3002ms
Permanent configuration
- Set permanent configuration
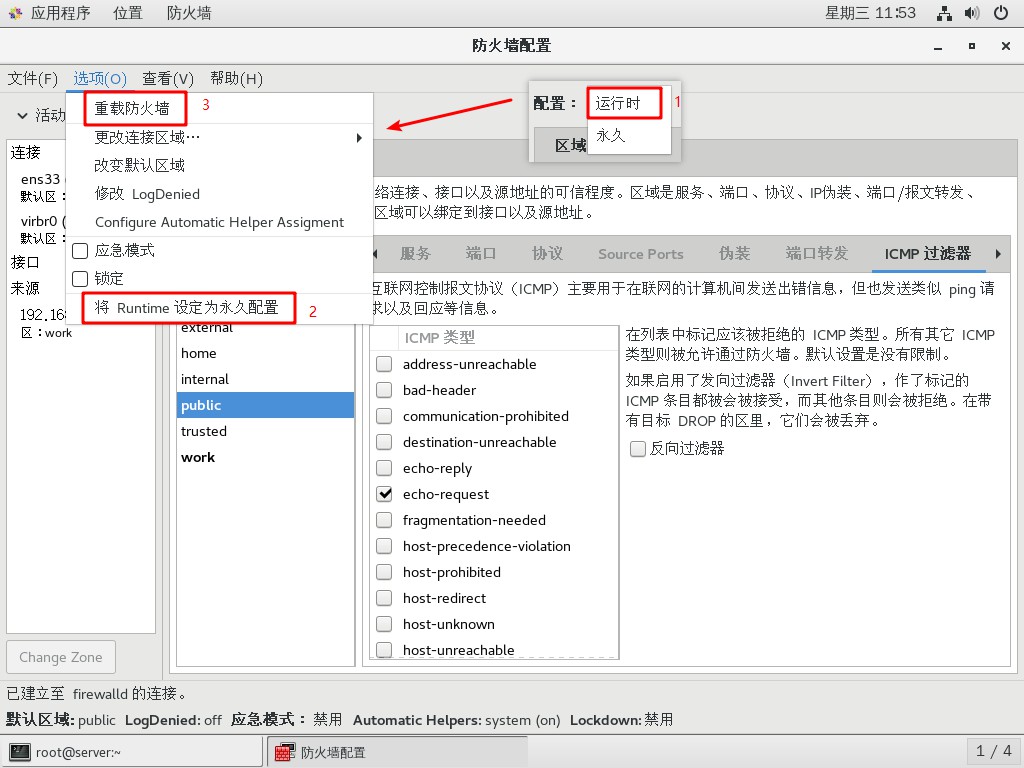
The configuration here is run-time configuration. To change the permanent configuration, you need to click options. First, set the Runtime to permanent configuration, and then reload the firewall. If you reload the firewall directly, the Runtime configuration will be lost.
If you choose permanent configuration from the beginning, you can directly overload the firewall to make the configuration effective.