1, Introduction to firewall
Firewall definition: it is a technology that helps the computer network build a relatively isolated protection barrier between its internal and external networks by organically combining various software and hardware equipment for security management and screening, so as to protect the security of user data and information.
Development and application of firewall: ipfwadm and ipchains (RedHat 7.0) were the first, followed by iptables. Since the beginning of CentOS 7, friedwall has developed rapidly and improved iptables. At present, iptables are still used more.
Location of firewall:
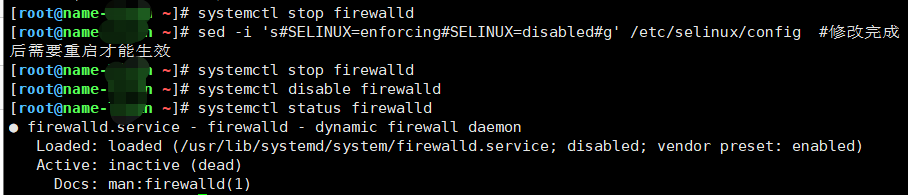
- Premise: the architecture is deployed in the part connected between the web and enterprise services (in front of the interface switch at the front end of the website).
- Tandem deployment: the best storage deployment with strong protection. However, if the firewall fails, the whole enterprise service will be affected.
- Bypass deployment: the best comprehensive storage deployment method will not affect the whole enterprise service due to firewall problems, but the protection is relatively weak compared with series deployment.
2, Introduction to IPtables
-
What are IPtables
Iptables is a user space command line program for configuring Linux 2.4 X and later. It is for system administrators. Since the network address translation is also configured from the packet filtering rule set, the packaging of iptables also includes IP6 tables. ip6tables is used to configure IPv6 packet filters.
Personal understanding: it is a free open source firewall tool based on packet filtering under Linux (before C7), which can finely control the data packets flowing in, out and through the server. At present, Iptables mainly works in layers 2, 3 and 4 of OSI layer 7 (without compilation). If the kernel is recompiled, Iptables can also support layer 7 control (squid agent + iptables) for layer 7 filtering.
III. iptables package filtering process
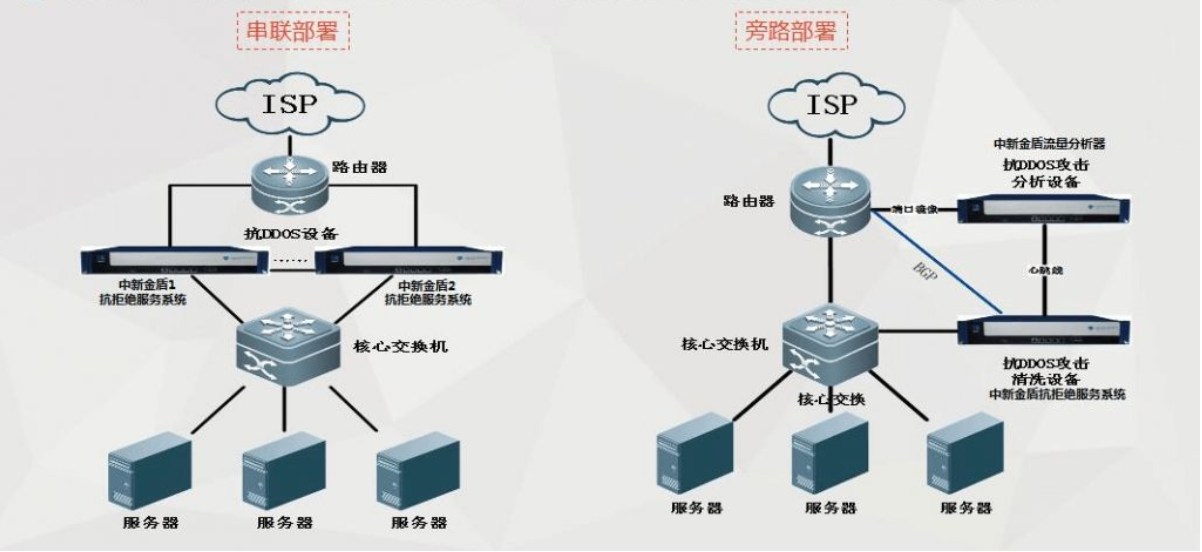
iptables uses the [packet] filtering mechanism, so it will analyze the [packet header data] of the requested packet and match it according to our preset rules to determine whether it can enter the host.
[packet header] refers to the transmission data flowing through the OSI seven layer model. When passing through each layer, each layer packs the data layer by layer according to the protocol followed, as shown in the following figure:
iptables workflow
- The firewall is filtered layer by layer. It is actually filtered from top to bottom and from front to back according to the order of configuration rules.
- If the firewall matches the rules according to the set rules, that is, it clearly indicates whether to block or pass, then the packet will not match the new rules downward.
- If the packet does not match the explicit rule of block or pass in all rules, it will be matched downward until the explicit default rule is obtained after matching the default rule, so as to confirm whether to block or pass.
- The default rules of the firewall will be executed only after all the rules in the corresponding chain are executed (the last executed rule).
As shown in the figure:

4, 4 Table 5 chain action relationship and working principle of iptables
According to the internal structure of IPtables, it can be subdivided into address tables distinguished by functions and address chains distinguished by IPtables actions; The relationships include: IPtables (user space) - > Netfilter (inner space) - > tables (4 tables) - > chains (5 chains) - > rule policy.
Note: the description of specific tables and chains in the system can be viewed through the man IPtables command
1. Functions of four tables
- filter (host firewall): controls the incoming and outgoing data packets of the host, mainly the default table of IPtables; The corresponding chains contained in the table: INPUT, OUTPUT and FORWARD
- nat: used for port or IP mapping or shared Internet access; Chains included in the table: POSTROUTING, preouting, and OUTPUT
- mangle: used to configure the routing mark ttl \ tos \ mark (disassemble the message, modify it, and reseal it); Chains included in the table: INPUT,OUTPUT,FORWARD, postrouting, preouting
- raw: turn off the connection tracking mechanism enabled on the nat table; Chains contained in the table: OUTPUT, preouting
2. Role of chains chain
- INPUT: data packet entering the host. The most critical chain of host firewall (INPUT chain of filter table)
- OUTPUT: the packet that flows out of the host
- FORWARD: packets flowing through the host
- Preouting: the chain, nat port or IP mapping (guidance) that the server first passes through. (preouting chain of nat table)
- POSTROUTING: the chain that passes through at the end of the outgoing server. nat shares the Internet. LAN shared Internet access (POSTROUTING chain of nat table)

5, iptables installation
1. Close selinux
If SELinux is not closed, iptables does not read the configuration file
Temporary shutdown command: getenforce0
Permanent shutdown command:
sed -i 's#SELINUX=enforcing#SELINUX=disabled#g' /etc/selinux/config #After the modification is completed, you need to restart to take effect
2. Turn off firewalld and turn off auto start
Turn off firewall
systemctl stop firewalld
Turn off startup and self startup
systemctl disable firewalld
View firewall status
systemctl status firewalld
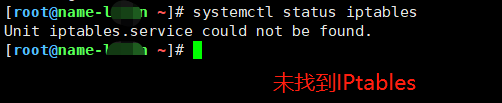
3. Check whether IPtables is installed
Command: systemctl status iptables
4. Install iptables
Installation command: Yum install iptables Services - y
Start and view iptables status
systemctl start iptables
systemctl enable iptables
View profile information
View configuration file command: cat /etc/sysconfig/iptables
1 filter <==surface table
2 :INPUT ACCEPT [0:0] Access control chains
3
4 :FORWARD ACCEPT [0:0] Flow control
5
6 :OUTPUT ACCEPT [0:0]Outflow control
7 -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT #<==rule rule
8 -A INPUT -p icmp -j ACCEPT
9 -A INPUT -i lo -j ACCEPT
10 -A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
11 -A INPUT -j REJECT --reject-with icmp-host-prohibited
12 -A FORWARD -j REJECT --reject-with icmp-host-prohibited

5. View startup status
- View startup status command: iptables - NL -- line number
- n # < = = display rules as numbers
- L # < = = all rules in the list chain
-- line number # < = = print rule serial number
- t specifies the table (default: `filter ')
- Check iptables kernel module lsmod |egrep "nat|filter
6, iptables common command parameters
- iptables -h# view iptables directory
- Usage analysis
1 iptables -[A] chain rule-specification [options] #Add rule to chain 2 iptables -I chain [rulenum] rule-specification [options] #Insert rule into chain 3 iptables -D chain rulenum [options] #Delete rule according to rule number 4 iptables -[FZ] [chain] [options] #Clear rule clear counter 5 iptables -[X] chain #Delete the user-defined chain. 6 iptables -P chain target [options] #Set default rules for chains 7 iptables -h #help
- Common syntax parameters:
1 --append -A chain #Add rule to chain 2 --delete -D chain #Delete rule from chain 3 --delete -D chain rulenum #Delete according to rule number 4 --insert -I chain [rulenum] #Insert rule defaults to the first rule 5 --list -L [chain [rulenum]] #List rule 6 --flush -F [chain] #Clear all rules 7 --zero -Z [chain [rulenum]] #Counter 8 --policy -P chain target #Change default rule 9 --protocol -p proto #Filtering for protocols, for example`tcp' 10 --source -s address[/mask][...] #Based on source address 11 --destination -d address[/mask][...] #Based on destination address 12 --in-interface -i input name[+] #Specify access interface 13 --jump -j target #Jump 14 --numeric -n #Digital output address and port 15 --out-interface -o output name[+] # Specify outgoing interface 16 --table -t table #Specify table(default: `filter') 17 --line-numbers #Display rule number - Processing actions of iptables according to rules
1 *ACCEPT: Allow packets to pass. 2 *DROP: Directly discard the data packet without giving any response information. At this time, the client will feel that its request is in the sea, and will respond after the timeout. 3 *REJECT: If the data packet is rejected, a response message will be sent to the data sender if necessary, and the client will receive the rejection message as soon as it requests. 4 *SNAT: Source address translation solves the problem that intranet users surf the Internet with the same public network address. 5 *MASQUERADE: yes SNAT A special form of, suitable for dynamic, temporary and variable ip Come on. 6 *DNAT: Destination address translation. 7 *REDIRECT: Do port mapping locally. 8 *LOG: stay/var/log/messages Log information is recorded in the file, and then the packet is passed to the next rule, that is, no other operation is done on the packet except recording, and the next rule is still allowed to match.
- Examples of common commands:
1 iptables -I INPUT -p tcp --dport 23:8809 -j DROP #Filtering from port 23 to port 8809 2 iptables -I INPUT -p tcp -s 192.168.56.1 -j DROP #Seal single IP 3 iptables -I INPUT -p tcp --dport 23:8809 -j DROP #Seal multiple ports at the same time: from port 23 to port 8809 4 iptables -A INPUT -P TCP --dport 80 -j ACCEPT #Develop 80 ports 5 iptables -I OUTPUT -p tcp --dport 80 -j DROP #Port 80 is not allowed to flow out 6 iptables -I INPUT -p tcp -m multiport --dport 21,23,24,80,3306 -j DROP #Matching port range 7 iptables -A INPUT -p icmp -s 192.168.56.0/24 --icmp-type 8 -j ACCEPT #Set the access within the same network segment (it can be accessed within the company, but not by other personnel) 8 iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT #Allow associated status packages( ftp Protocol, 21 connection ports, 20 data transmission ports)
7, Deploy host firewall
1. IPtables enterprise firewall application scenarios
- Scenario 1: host firewall function (INPUT chain of filter table).
- Scenario 2: the LAN shares the Internet and acts as a gateway (POSTROUTING chain of nat table).
- Scenario 3: port and IP mapping (preouting chain of NAT table), hard anti NAT function.
- Scenario 4: implement IP one-to-one mapping (DMZ).
- ·
2. Firewall deployment ideas
- Deployment host firewall default disable mode
- Deploy enterprise gateway. The default is allowed
3. Actual deployment
- Deletion strategy: various clearing
1 iptables -F 2 iptables -X 3 iptables -Z 4 iptables -F -t nat 5 iptables -X -t nat 6 iptables -Z -t nat - Allow your own network segment and port 22 to pass through
1 iptables -A INPUT -s 10.0.0.0/24 -j ACCEPT 2 iptables -A INPUT -s 203.81.18.0/24 -j ACCEPT 3 iptables -A INPUT -p tcp --dport 22 -j ACCEPT ##According to your own situation, you generally don't need to use it at work - Set default rule policy
iptables -P INPUT DROP iptables -P FORWARD DROP iptables -P OUTPUT ACCEPT - Set other permissions
1 iptables -A INPUT -i lo -j ACCEPT #Allow loopback address 2 iptables -A INPUT -p tcp -m multiport --dport 80,443 -j ACCEPT #Set 80 port forwarding 3 iptables -A INPUT -s 172.16.1.0/24 -j ACCEPT 4 iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT#Connection status settings4. Production scenario maintenance - block an IP and a port
- Daily change the / etc/sysconfig/iptables configuration and add it to the corresponding location for permanent effect
-A INPUT -p tcp -m tcp --dport 3306 -j DROP
The # seal off rule must be placed on the top of other allowed rules to take effect.
The # permission rule must be placed on top of other permission rules to take effect. Reload effective: systemctl reload iptables
2. Temporary IP (- I): the rule disappears after restarting for a special IP
iptables -I INPUT -s 203.71.78.10 -j DROP
3. Common rules take effect in front
8, The final idea of firewall layout:
- Try not to configure external IP for the server. It can be forwarded through proxy or mapped through firewall.
- If concurrency is not particularly serious, open iptables firewall in the external IP environment. If there is a large amount of concurrency and iptables cannot be opened, which will affect the performance, buy a hardware firewall.