1, Introduction to Linux Firewall
yum -y install iptables-services.x86_64 #install
Must be closed first firewalld firewall [root@localhost ~]# systemctl stop firewalld.service [root@localhost ~]# systemctl disable firewalld.service install iptables firewall [root@localhost ~]# yum -y install iptables-services.x86_64 #install [root@localhost ~]# systemctl start iptables.service [root@localhost ~]# systemctl enable iptables.service / / set iptables startup
1. Introduction to rule chain
Role of rules: filter or process data packets
The role of the chain: to accommodate various firewall rules
Classification basis of chain: different opportunities for processing data packets 2
2. There are five default rule chains:
(1) INPUT: Processing inbound packets
(2) OUTPUT: Processing outbound packets
(3) FORWARD: Processing forwarded packets
(4) POSTROUTING chain: process packets after routing
(5) Preouting chain: process packets before routing
Note that this is a capital letter (- A is added with the chain name)
3. Brief introduction to rule table
Function of rule table: to accommodate various rule chains
Table division basis: firewall rules have similar functions
4. Four default rule tables
(1) raw table: determines whether to track the status of the packet
(2) mangle table: setting tags for packets
(3) nat table: modify the source, destination lP address or port in the packet
(4) Filter table: determines whether to release the packet (filter)
-t indicates that it is filter by default when it is not written, which is most commonly used
5. Basic grammar

matters needing attention:
(1) When the table name is not specified, it refers to the filter table by default
(2) When the chain name is not specified, it refers to all chains in the table by default
(3) You must specify matching criteria unless you set the default policy for the chain
(4) Options, chain names and control types use uppercase letters, and the rest are lowercase
(5) The content modified by the current command line needs to be saved in the configuration file before it can be permanently saved
iptables-save > /etc/sysconfig/iptables //Iptables save can see the modified rules. The configuration file, etc/sysconfig/iptables,
6. Options
Management options
Example of management option usage
-A append an iptables -A INPUT at the end of the specified chain
-I inserts a new in the specified chain. If no serial number is specified, it will be the first iptables by default - I input
-P specifies the default rule iptables -POUTPUT ACCEPT
-D delete iptables -t nat -D INPUT
-R modify or replace a rule iptables -t nat -R INPUT
-L view iptables -t nat -L
-n all fields are displayed in digital form (for example! Any ip address is e.0.0.e instead of i anywhere, for example, protocol port number instead of service name) iptables -L -n,iptables -nL,iptables -vnL
-v displays more detailed information when viewing, which is often used with - L
– line number rule numbered iptables - t NAT - L - N -- line number / iptables - t NAT - L -- line number
-F clear all rules in the chain iptables -F
-X clear the rules of custom chains without affecting other chains iptables -X
-Z clear chain counter (size and sum of matched packets) iptables -Z
-S view all the rules of the chain or the rules of a chain / a specific rule followed by the numbers iptables -t nat -S, iptables -t nat -S POSTROUTING 1
Control options (uppercase required)
ACCEPT allows packets to pass
REJECT rejects the data packet. If necessary, a response message will be sent to the sender of the data packet
DROP directly discards the data packet without giving any response
LOG records the LOG information in the / var/log/messages file, and then sends the packet to the next rule. It does not process the packet itself
-j + control options
Add new rule
-A: add a rule at the end
-1: Add a rule at the beginning of the chain
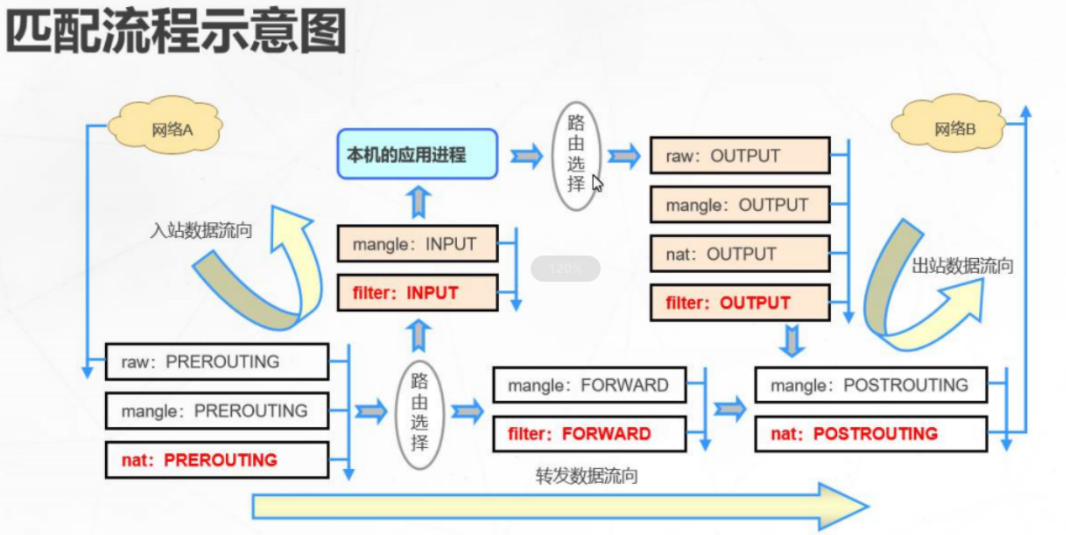
6. Sequential problem
1. Order between rule tables
raw→mangle→nat→filter
2. Order between rule chains
Inbound: preouting → INPUT
Outbound: output > postrouting
Forwarding: forwarding → FORWARD → POSTROUTING
3. Matching order within the rule chain
Check in sequence and stop when matching (except LOG Policy)
If no matching rule is found, it will be handled according to the default policy of the chain
Execute from top to bottom in each table
[root@localhost ~]# iptables -A INPUT -p icmp -s 192.168.100.6 -j ACCEPT [root@localhost ~]# iptables -A INPUT -p icmp -s 192.168.100.6 -J DROP [root@localhost ~]# iptables -vnL --line-number Chain INPUT (policy ACCEPT 67 packets, 4264 bytes) num pkts bytes target prot opt in out source destination 1 6 504 ACCEPT icmp -- * * 192.168.100.6 0.0.0.0/0 #At the same time, when there is rejection and consent, it depends on who is in front 2 2 168 DROP icmp -- * * 192.168.100.6 0.0.0.0/0
2, Operation part
1. View
iptables -vnL #Common collocation - vnL iptables -vnL --line-number #When viewing rules, mark the sequence number
[root@localhost ~]# iptables -vnL
Chain INPUT (policy ACCEPT 856 packets, 349K bytes)
pkts bytes target prot opt in out source destination
2 168 DROP icmp -- * * 192.168.100.6 0.0.0.0/0
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 all -- * * 192.168.150.0/24 192.168.160.0/24
Chain OUTPUT (policy ACCEPT 673 packets, 143K bytes)
pkts bytes target prot opt in out source destination
0 0 icmp -- * * 192.168.200.0/24 0.0.0.0/0
[root@localhost ~]# iptables -vnL --line-number
Chain INPUT (policy ACCEPT 889 packets, 351K bytes)
num pkts bytes target prot opt in out source destination
1 2 168 DROP icmp -- * * 192.168.100.6 0.0.0.0/0
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 0 0 all -- * * 192.168.150.0/24 192.168.160.0/24
Chain OUTPUT (policy ACCEPT 703 packets, 145K bytes)
num pkts bytes target prot opt in out source destination
1 0 0 icmp -- * * 192.168.200.0/24 0.0.0.0/0
2. Delete rule
iptables -D [table name] [serial number]
iptables -D INPUT 1 #Delete the rule with sequence number 1 in the INPUT table //If it is not indicated, all tables will be deleted. If only the table has no sequence number, the whole table will be deleted iptables -t filter -F #Clear all rules iptables -t filter -X #Empty custom chain iptables -t filter -Z #Clear counter #Generally, the three articles are implemented once to ensure that there is no residue
3. Add rules
-A append rule to last
-I insert the rule to the front
-R modification
-p specifies the protocol name, such as tcp, udp, icmp, all, etc
-s and source ip
-d and target ip
-i specify inbound network card
-o specify outbound network card
! Express the meaning of non
– sport specifies the source port
– specify the destination port
-m multiport --sport (or – dport) specifies multiple source ports or target ports, separated by: continuously, such as 20:80
-M MAC -- MAC source mak address matches mak address
-M star -- state uses the form of connection state
Common connection status NEW:Want to create a new online packet state ESTABLISHED:Online status of successfully Online RELATED:This indicates that this packet is related to the packet sent by our host, which may be a response packet or a transmission packet after successful connection!This state is often set INVALID:NULL packet ,for example I Packet status of data corruption
– ICMP type matches the type of ICMP
icmp type: Echo-Request:Code 8 Echo-Reply:The code is 0
-M iprange -- DST range ip range # matches multiple ip addresses
iptables -A INPUT -p icmp -j REJECT //No host is allowed to ping this host iptables -A INTPUT -p icmp -s 192.168.100.5 -j REJECT //The host of this ip is not allowed to ping this host iptables -A OUTPUT -p icmp -d 192.168.100.6 -j DROP //This host is not allowed to ping the host of this ip iptable -I OUTPUT ! -p icmp -j DROP .// Discard all inbound packets except icmp and set the rule to sequence 1 iptables -t filter -A INPUT -j REJECT //All incoming packages are rejected
Modify - R
[root@localhost ~]# iptables -I INPUT -p icmp -s 192.168.100.8 -j REJECT #First limit [root@localhost ~]# iptables -vnL --line-number Chain INPUT (policy ACCEPT 12 packets, 768 bytes) num pkts bytes target prot opt in out source destination 1 0 0 REJECT icmp -- * * 192.168.100.8 0.0.0.0/0 reject-w [root@localhost ~]# iptables -R INPUT 1 -j ACCEPT #Change the first item to ACCEPT, which is not commonly used. It is better to delete it and add it again [root@localhost ~]# iptables -vnL --line-number Chain INPUT (policy ACCEPT 0 packets, 0 bytes) num pkts bytes target prot opt in out source destination 1 10 640 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0
iptables -A OUTPUT -p tcp -d 192.168.100.211 -j CROP #The outbound packets of tcp protocol to the host of this ip are prohibited iptables -A FORWARDT -p tcp -s 192.168.100.6 -d 192.168.100.10 -j DROP #Prohibit ip forwarding from 0.6 to 0.10
iptables -A INPUT -i ens33 -j DROP #All packets coming in from the network card are prohibited iptables -A OUTPUT -o ens33 -j DROP #All data packets sent out by the network card are prohibited (it seems that they are used less) iptables -A INPUT -i ens33 -s 192.168.100.10 -j DROP #Data packets from the ip are prohibited from entering from the network card iptables -A INPUT ! -p icmp -j DROP #All non icmp packets are prohibited
iptables -A INPUT -p tcp --dport 80 -s 192.168.254.100 -j DROP #Disable the from this ip and take tcp80 port as the target port (the protocol - p should also be specified when the port) iptables -A INPUT -p tcp -m multiport --dport 80,20,100 -s 192.168.254.100 -j DROP #Specify multiple discontinuous ports iptables -A INPUT -p tcp -m multiport --dport 20:100 -s 192.168.254.100 -j DROP #Specify multiple consecutive ports, such as 20 to 80
iptables -A OUTPUT -p icmp -m iprange --dst-range 192.168.100.2-192.168.100.102 -j DROP #Specify multiple consecutive ip addresses -- DST range
[root@localhost ~]# iptables -A INPUT -p icmp --icmp-type echo-request -s 192.168.245.211 -j DROP #The request package is not allowed to pass [root@localhost ~]# iptables -vnL --line-number Chain INPUT (policy ACCEPT 19 packets, 1240 bytes) num pkts bytes target prot opt in out source destination 1 0 0 DROP icmp -- * * 192.168.245.211 0.0.0.0/0 icmptype 8
iptables -A INPUT -p icmp -m mac --mac-source 00:0c:26:f5:ac:58 -j DROP #Specify mak address
iptables -I INPUT -p tcp -m state --state ESTABLISHED -j ACCEPT iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT #Allow continuous release in response to requests
iptables -save #View modified configuration iptables -save > /etc/sysconfig/iptables #Save to the configuration file, then the shutdown and restart still exist