Linux rights management
shell command operation principle
[yyx@VM-4-16-centos ~]$
Such a line of text is the command line, and the commands written later are called commands. Use which to view the directory where the commands we wrote are located. It can be seen that the commands under Linux are an executable file.
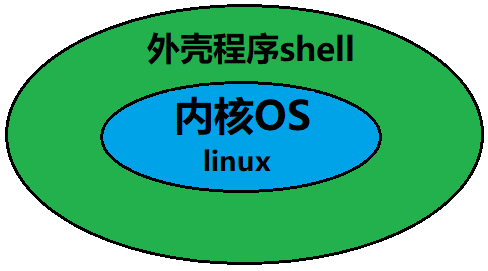
Generally, the operating system we call, including Linux, refers to the kernel and shell. Taking Windows as an example, the shell of Windows is the graphical interface of Windows, while the shell of Linux is the shell and the kernel is the Linux kernel.
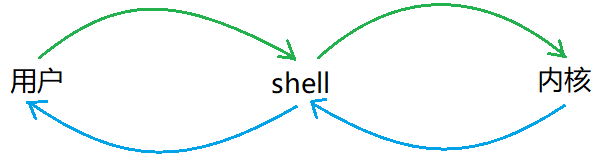
If users are allowed to communicate directly with the operating system kernel, they must be familiar with the operating system. In this way, the learning cost is too high and unsafe. Therefore, Linux sets up a shell as a media intermediary to convey users' instructions to the operating system. The definition of shell is the command line interpreter, which is used to translate the user's commands to the core processing of the operating system, and then translate the core processing results to the user.
Compared with Windows, we do not directly communicate with the kernel, but operate the system through a series of actions such as clicking through the graphical interface.
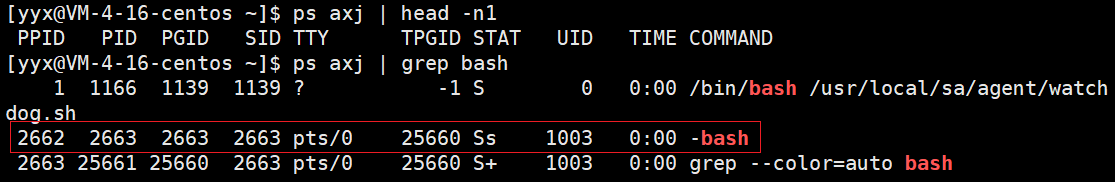
If shell is the command-line interpreter and the general name of all shell programs, bash is the command-line interpreter under Linux. bash is the most commonly used shell and the default shell under Linux. If the shell is compared to a programmer as a profession, bash is a specific person sitting between you and me.
1. Definition of authority
There are two types of users in Linux by default. One is root, that is, super administrator, with very high permissions, and the other is ordinary users with general permissions. You can use su to switch users:
[yyx@VM-4-16-centos ~]$ su - # Switch to root Password: Last failed login: Fri Jan 28 03:23:06 CST 2022 on pts/0 [root@VM-4-16-centos ~]#
The permissions of root user are very high, so the permission boundary between the two types of users must be clear.
#1. [root@VM-4-16-centos ~]# su yyx # Switch to normal user #2. [root@VM-4-16-centos ~]# exit # Switch to normal user logout [yyx@VM-4-16-centos root]$
Both methods can switch users, but it is not recommended to use the first one, because if you use su to switch users, the original user does not log out. In this way, the system will retain the bash of the original user and create the bash of other users. If the second method is used, that is, if you exit the original user, you will automatically switch back and destroy the bash of the original user, which will save more system resources.
The sudo command can be used to temporarily elevate user permissions, and the trusted user directory needs to be configured.
2. Design of authority
For example, if it's not a VIP, you can't watch member movies, and if it's not an employee, you can't enter the office. Therefore, permission is divided according to a specific attribute of a certain thing. Different people have different permissions. In system management, permission refers to that a specific user has a specific right to use system resources. Usually, the system administrator assigns different permissions to users for a specific resource, and the system automatically enforces these permissions.
Therefore, permission describes the relationship between the attributes of people and things. The next file visitor is the person, and the file type and access permission are the attributes of things.
2.1 classification of document visitors
There are three kinds of file visitors: owner, group and others.
- Owner: the user who created the file, which is not difficult to understand.
- Group: the group of the owner. If the file visitors are divided into the owner and others, it is not convenient for multi-user cooperation.
- Others: everyone except the owner and the group to which they belong.
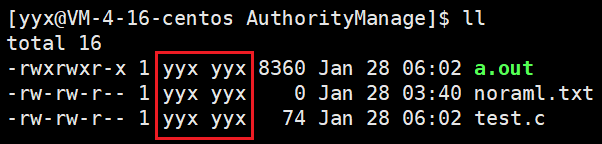
The first column in the red box in the above figure is the owner of the file, and the second column is the group to which it belongs. Because there are few users, they form a group by themselves.
Owner, group and others are all roles assigned to files, while root and ordinary users refer to specific users.
The next column is the size of the file, and the next column is the latest modification time of the file.
2.2 file type and access rights
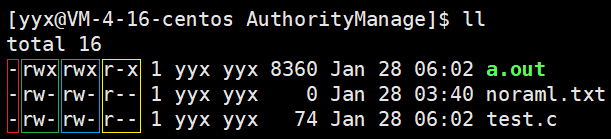
It can be clearly seen that the whole block in front has 10 columns and is divided into 4 groups. The first column forms a group, and then every three columns form a group, namely red, green, blue and yellow.
The first column of file attributes is used to distinguish file types. There are generally two types: - for ordinary files and d for directories. In Linux, file suffixes are not used as a way to distinguish files, but only the first column of attributes.
c stands for character device file, b block device file, p pipeline file and l link file. These are only for understanding at present.
2.3 expression of authority
The remaining nine columns of file attributes are divided into three groups, which represent the permissions of the file owner, the group and others. There are three kinds of file permissions: read r, write w and execute x.
Character representation
The character representation is the corresponding representation in the figure above.
- The first group represents the owner's permission to the file. The three columns represent read r, write w and execute x respectively. If you have permission, it is represented by characters. If you don't have permission, it is represented by -. The order should not be disordered.
- By analogy, the latter two groups are the permissions of the group and others, which are expressed in the same way.
| Linux representation | explain | Linux representation | explain |
|---|---|---|---|
| r-- | read-only | -w- | Write only |
| --x | implement | rw- | Readable and writable |
| r-x | Readable executable | -wx | Writable executable |
| rwx | Readable, writable and executable | --- | No permission |
Octal digit representation
Since there are only two states represented by each permission bit, either with or without, it can be represented by binary (with 1 and without 0). Conversion to octal is a total of eight numbers from 0 to 7, so it can also be expressed in octal.
| Authority symbol | Binary | octal number system |
|---|---|---|
| r-- | 100 | 4 |
| -w- | 010 | 2 |
| --x | 001 | 1 |
| rw- | 110 | 6 |
| r-x | 101 | 5 |
| rwx | 111 | 7 |
| -wx | 011 | 3 |
| --- | 000 | 0 |
The above two representations will be used in the subsequent permission setting commands.
3. Permission setting
There are two kinds of permissions to modify a file: one is to modify the read-write execution attribute of the file, and the other is to modify the owner and group of the file. Look at the first one first:
3.1 chmod
[yyx@VM-4-16-centos test]$ chmod u+r fileName
chmod can modify the read / write execution permissions of files for three types of visitors. The details are as follows:
# u means owner user [yyx@VM-4-16-centos test]$ chmod u+r file.txt # Add read permission to the owner [yyx@VM-4-16-centos test]$ chmod u-w file.txt # Cancel write permission to the owner [yyx@VM-4-16-centos test]$ chmod u-x file.txt # Cancel execution permission to the owner # g indicates the group to which it belongs [yyx@VM-4-16-centos test]$ chmod g+r file.txt # Add read permission to the group [yyx@VM-4-16-centos test]$ chmod g-w file.txt # Cancel write permission for the group [yyx@VM-4-16-centos test]$ chmod g-x file.txt # Cancel execution permission for the group # o means other s [yyx@VM-4-16-centos test]$ chmod o+r file.txt # Add read permissions to others [yyx@VM-4-16-centos test]$ chmod o-w file.txt # Cancel write permission to others [yyx@VM-4-16-centos test]$ chmod o-x file.txt # Cancel execution permission for others
- u. G and O respectively represent three kinds of visitors, +, - respectively represent addition and cancellation, and R, W and X respectively represent read-write execution. Then bring the file name.
[yyx@VM-4-16-centos test]$ ll ---------- 1 yyx yyx 74 Jan 29 05:50 file.txt [yyx@VM-4-16-centos test]$ chmod u+r file.txt # Modify individual permissions for an individual visitor [yyx@VM-4-16-centos test]$ ll -r-------- 1 yyx yyx 74 Jan 29 05:50 file.txt [yyx@VM-4-16-centos test]$ chmod u-r+wx file.txt # Modify multiple permissions for multiple visitors [yyx@VM-4-16-centos test]$ ll --wx------ 1 yyx yyx 74 Jan 29 05:50 file.txt [yyx@VM-4-16-centos test]$ chmod u+r,g+r file.txt # Modify a single permission for multiple accessors [yyx@VM-4-16-centos test]$ ll -rwxr----- 1 yyx yyx 74 Jan 29 05:50 file.txt [yyx@VM-4-16-centos test]$ chmod u+rwx,g+rwx,o+rwx file.txt # Modify multiple permissions for multiple visitors [yyx@VM-4-16-centos test]$ chmod a+rwx file.txt [yyx@VM-4-16-centos test]$ ll -rwxrwxrwx 1 yyx yyx 74 Jan 29 05:50 file.txt [yyx@VM-4-16-centos test]$ chmod u-r file.txt test.c # Continuous operation of multiple files
- chmod supports continuous modification of permissions of multiple visitors, multiple permissions of a single visitor, multiple permissions of multiple visitors, and continuous operation of multiple files.
[yyx@VM-4-16-centos test]$ chmod 777 file.txt # The permission value is 7, that is, rwx [yyx@VM-4-16-centos test]$ chmod u+rwx,g+rwx,o+rwx file.txt # The two are equivalent [yyx@VM-4-16-centos test]$ ll -rwxrwxrwx 1 yyx yyx 0 Jan 29 07:48 file.txt [yyx@VM-4-16-centos test]$ chmod 555 file.txt [yyx@VM-4-16-centos test]$ ll -r-xr-xr-x 1 yyx yyx 0 Jan 29 07:48 file.txt
- As mentioned earlier, the scheme of octal digits can also represent the permissions of visitors, so you can use the modification method in the above code. Both methods are equivalent.
[root@VM-4-16-centos test]# ll -rw-rw---- 1 yyx yyx 19 Jan 29 07:11 file.txt -rw-r--r-- 1 root root 0 Jan 29 06:11 root.txt [root@VM-4-16-centos test]# cat file.txt hello linux [root@VM-4-16-centos test]# echo "hello Linux" >> file.txt [root@VM-4-16-centos test]# ./file.txt
You can see that although file Other people in txt do not have any permissions, but in fact, the root user is not subject to any restrictions.
3.2 chown & chgrp
chown can be used to modify the owner of the file, and chgrp is the group to which the file belongs.
[yyx@VM-4-16-centos test]$ chown usrname fileName [yyx@VM-4-16-centos test]$ chgrp usrname fileName
[yyx@VM-4-16-centos test]$ chown root file.txt chown: changing ownership of 'file.txt': Operation not permitted
- It can be seen that the owner of a file cannot be changed to other users, even the owner of the file.
[yyx@VM-4-16-centos test]$ chmod u+rwx,g+rwx,o-rwx file.txt [yyx@VM-4-16-centos test]$ chgrp root file.txt [yyx@VM-4-16-centos test]$ ll total 12 -rwxrwx--- 1 yyx root 20 Jan 29 07:15 file.txt
Through the above setting method, you can only give the files to the members of the group for viewing and management.
[yyx@VM-4-16-centos test]$ chgrp root file.txt # Ordinary users are not allowed to change the file group to other users chgrp: changing group of 'file.txt': Operation not permitted [root@VM-4-16-centos test]# sudo chgrp root file.txt [yyx@VM-4-16-centos test]$ ll -rw-rw-r-x 1 yyx root 20 Jan 29 07:15 file.txt [yyx@VM-4-16-centos test]$ chgrp yyx file.txt # The file owner can change the group to which the file belongs back to himself [yyx@VM-4-16-centos test]$ ll -rwxrwx--- 1 yyx yyx 20 Jan 29 07:15 file.txt
Another small note is that ordinary users are not allowed to change the file group to other users, but the file owner can change the file group back to himself.
[yyx@VM-4-16-centos test]$ sudo chown root:root file.txt
- In this way, the owner of the file and the group to which it belongs can be modified together.
If the owner and group are specified, the scope of others is clear, so it does not need to be set separately.
3.3 directory permissions
It is very clear to us what the reading, writing and execution of ordinary files mean. But what does the reading, writing and execution of the directory mean? How is it different from ordinary documents?
[yyx@VM-4-16-centos test]$ ll total 4 d-wxrwxr-x 2 yyx yyx 4096 Jan 29 08:06 code [yyx@VM-4-16-centos test]$ ls code # Do not have read permission, unable to view the contents of the directory ls: cannot open directory code: Permission denied # [yyx@VM-4-16-centos test]$ ll total 4 dr-xrwxr-x 2 yyx yyx 4096 Jan 29 08:06 code [yyx@VM-4-16-centos test]$ touch code/file.txt # You do not have write permission to create or delete files touch: cannot touch 'code/file.txt': Permission denied # [yyx@VM-4-16-centos test]$ ll total 4 drw-rwxr-x 2 yyx yyx 4096 Jan 29 08:06 code [yyx@VM-4-16-centos test]$ cd code # Unable to enter the directory without execution permission -bash: cd: code: Permission denied
From the above code:
- With r read permission, the representative can view the contents in the directory;
- Having w write permission means being able to create or delete files under the directory;
- x represents the permission to enter the directory.
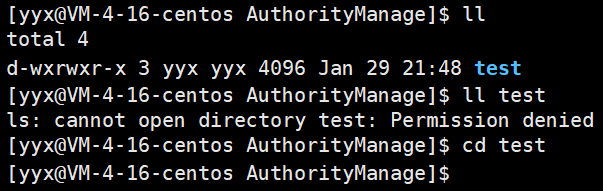
When a user has only executable but no read rights, he can only enter but cannot view the contents in the directory.
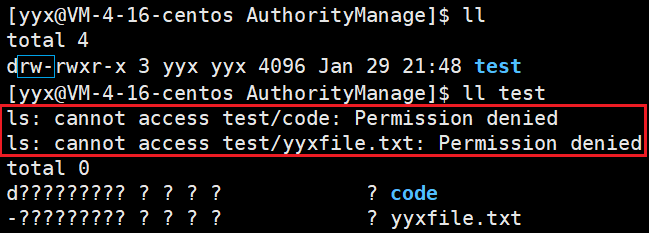
When a user has read but no executable permission to the directory, he can only view the name of the file in the directory, but cannot view other attribute information.
These are designed by Linux. There must be a reason for this design. Users only need to abide by it.
Viscous potential
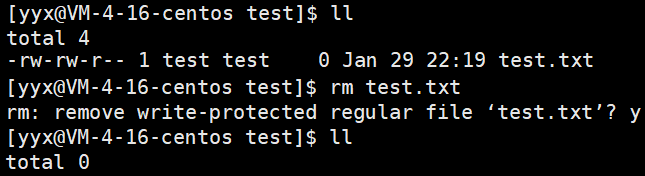
According to the permission provisions of the directory, as long as the user has write permission to the directory, the file created by others in the directory can be deleted without the consent of others. However, sometimes it is necessary to set the write permission for others, that is, to create files, but do not want others to have the permission to delete other user files. For this demand, the sticky bit can be used under Linux.
[yyx@VM-4-16-centos AuthorityManage]$ chmod o+t dirName
Note that the sticky bit modifies the directory and takes effect on all files in the directory.
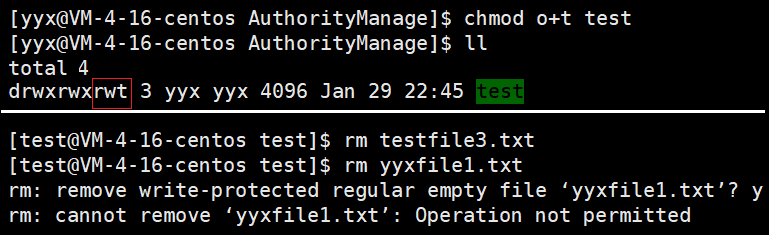
t is equivalent to a reduced version of x, so that other cannot delete other users' files.
Therefore, when a directory is set to the sticky bit, the files in the directory can only be deleted by the root super administrator, the directory owner and the file owner.
3.4 setting of default permissions
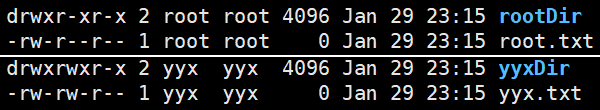
The above figure shows the default permissions of directories and ordinary files created by root and ordinary users respectively. A little analysis can be obtained:
- Ordinary files and directories created by ordinary users only limit the write permission of other, and ordinary files do not have execution permission.
- On this basis, the root user also limits the write permission of the group to which he belongs.
The ordinary file permission of ordinary users can be expressed as 0664 and the directory can be expressed as 0775. The following explains why the default permissions look like this.
File mask umask
In fact, the default permissions (starting permissions) of the created files and directories when they are created are represented by octal digits, which are 0666 and 0777 respectively. The initial permission is also affected by the permission mask umask before it becomes the default permission value.
In other words, the default permission of the file can be changed. Just change the value of the file mask umask. Umask can be set and viewed as follows:
[yyx@VM-4-16-centos test]$ umask # see 0002 [yyx@VM-4-16-centos test]$ umask 0002 # set up
After "subtracting" the file mask value from the starting permission value, the result is the default permission value generated by the file. The operation of "subtract" mask is as follows: the file permission values are represented in binary, and the starting permission value corresponds to the file mask value one by one. If a digit of the file mask is 1, the result of this bit must be 0.
110 110 110 # Start permission - 000 000 010 # File mask ---------------- 110 110 100 # Default permissions 111 111 111 # Start permission - 000 000 010 # File mask ---------------- 111 111 101 # Default permissions
This "subtraction" operation can reverse the file mask and then match it with the starting permission, that is, Mask & (~ mask). It can also be seen from the meaning of file mask, that is, the value of the corresponding bit is 1 when the permission of which bit is 0, that is, the bits appearing in umask should be removed from the result.
In fact, in actual development, the best default value of file mask is 0002. This is the natural choice of Linux for decades.