Authoritative Name Server
Store and provide the actual data of an area (whole DNS domain or part of DNS domain).
The types of authoritative name servers include:
Master: Contains raw area data. Sometimes referred to as the "main" name server
Slave: Backup server that transfers area data from Master server through area
Copy. Sometimes referred to as a "secondary" name server
Non-authoritative/Recursive Name Server
The client finds the data from the authoritative name server through it. The types of recursive name servers include
Cache Name Server Only: Used only for lookup, not authoritative for anything other than non-critical data
DNS lookup
The Stub parser on the client sends the query to the name server in/etc/resolv.conf. If the name server has authority over the requested information, it sends the authoritative answer to the client. Otherwise, if the name server has requested information in its cache, it sends the non-authoritative answer to the client. If there is no information in the cache, the name server will search. Authoritative name servers are used to find information. They search downward according to the DNS hierarchy from the root region until they have authoritative name servers for information, so as to get answers for clients. In this case, the name server passes the information to the client and keeps a copy in its cache for later searching.
DNS Resource Recording
DNS area stores information in the form of resource records. Each resource record has a type indicating the type of data it retains.
A: Name to IPv4 address
AAAA: Name to IPv6 address
CNAME: Name to Specification Name (another name containing A/A A AAAA records)
PTR: IPv4/IPv6 address to name
MX: Mail exchanger for name (where to send its e-mail)
NS: Name Server for Domain Names
SOA: Authorization Start, DNS Region Information (Management Information)
DNS debug
It displays detailed information from the DNS lookup, including why the query failed:
NOERROR: Successful query
NXDOMAIN: DNS server prompt does not have such a name
SERVFAIL: DNS server downtime or DNSSEC response validation failed
REFUSED: DNS server refuses to answer (perhaps for access control reasons)
Part of the output of dig
The title indicates information about queries and answers, including response status and any special markers set (aa for authoritative answers, etc.)
QUESTION: Propose actual DNS queries
ANSWER: Response (if any)
AUTHORITY: Name server responsible for domain/region
ADDITIONAL: Other information provided, usually about name servers
The comment at the bottom indicates the recursive name server that sends the query and the time it takes to get the response
Caching DNS Server
BIND is the most widely used open source name server. In RHEL, the firewall open ports 53/TCP and 53/UDP are provided through the bind package. The main configuration file for BIND is / etc/named.conf. / The var/name directory contains other data files used by the name server
/ Grammar of etc/named.conf
The text between /* and */ (can span multiple lines)
The instruction ends with a semicolon (;)
Many instructions assume that the address matching list is placed in braces, in the IP address or subnet list represented by CIDR, or in the named ACL (e.g., any; [all hosts] and none; [no hosts]).
The file begins with the options block, which contains instructions to control how named works.
The zone block controls how named looks up its authoritative root name server and region.
First install the bind package
Configuring Cache dns Server
systemctl start named
systemctl stop firewall #Close the firewall
vim /etc/named.conf #Modify in the configuration file
options {
listen-on port 53 { any; }; Modify all users
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
allow-query { any; }; modify
forwarders {192.158.122.1; }; Add to
[root@dns-server ~]# systemctl restart named
[root@dns-server ~]# Netstat-antlpe | grep name to see if the port is open
[root@dns-server ~]# dig www.taobao.com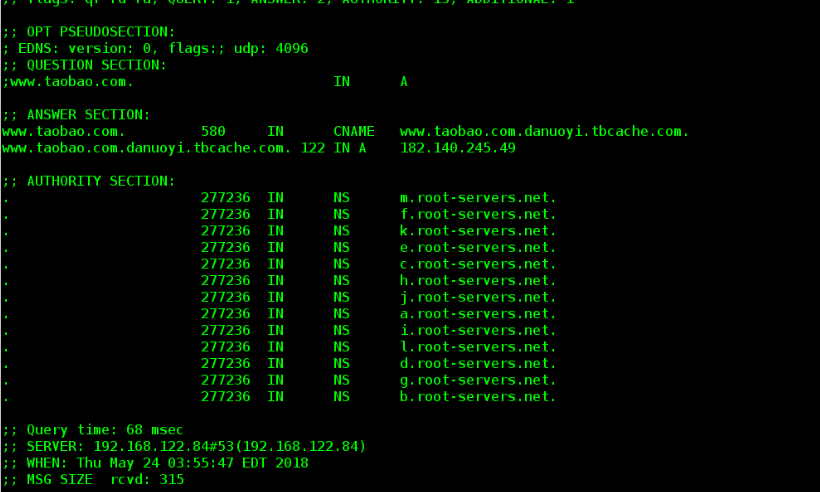
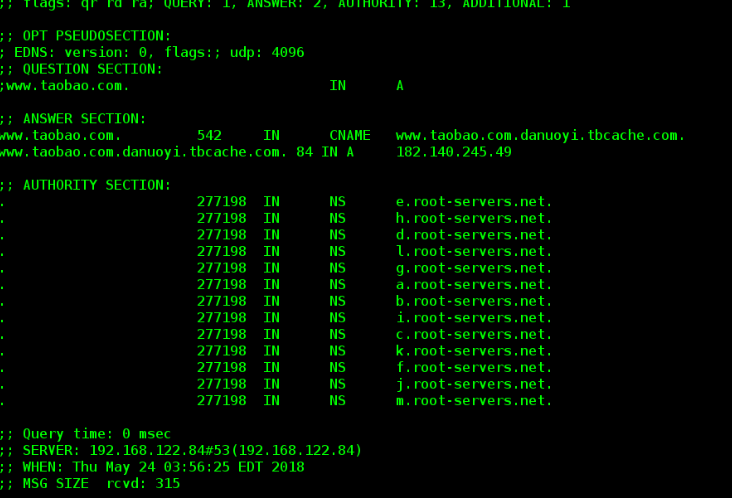
Comparing the two pictures, we can see that the time needed is greatly reduced, but the first time is longer.
[root@dns-desktop ~]# vim /etc/resolv.conf #Object-only additions to DNS
# Generated by NetworkManager
search westos.com
nameserver 172.25.254.220 Add this line,point dns cacheNext, configure the forward parsing of dns
root@server ~]# vim /etc/named.conf
options {
listen-on port 53 { any; };
listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
allow-query { any; };
[root@server ~]# systemctl restart named
[root@server ~]# vim /etc/named.rfc1912.zones
zone "westos.com" IN { ##Add this paragraph
type master;
file "westos.com.zone";
allow-update { none; };
};
[root@server ~]# cd /var/named
[root@server named]# cp -p named.localhost westos.com.zone
[root@server named]# vim westos.com.zone 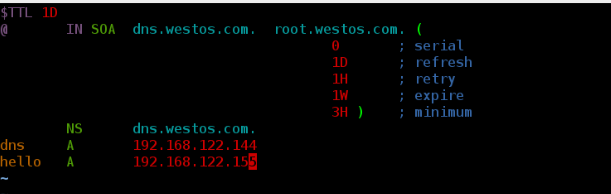
[root@server named]# systemctl restart named
[root@server named]# dig hello.westos.com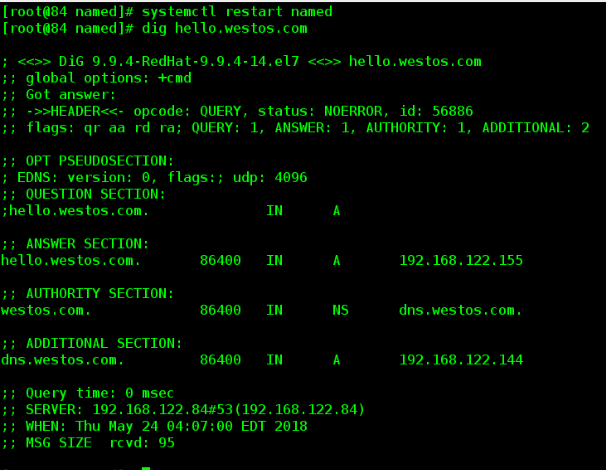
Wheel call
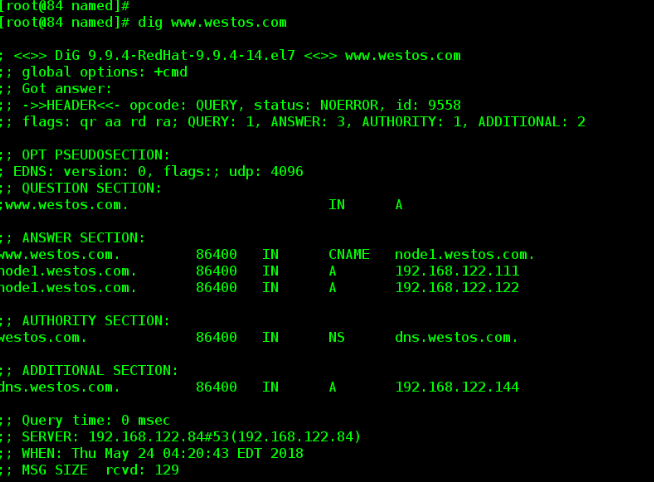
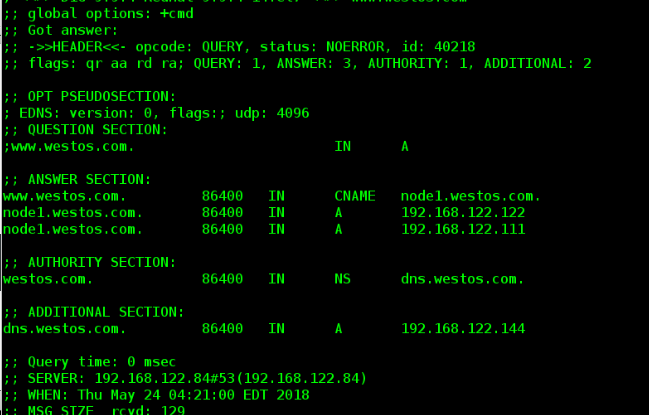
vim westos.com.zone Add the following www CNAME node1.westos.com node1 A 192.168.122.122 node1 A 192.168.122.111
Backward analysis
31 zone "1.0.0.127.in-addr.arpa" IN { #Write ip here.
32 type master;
33 file "named.loopback"; #I'm westos.com.ptr and remember to create this file.
34 allow-update { none; };
35 };
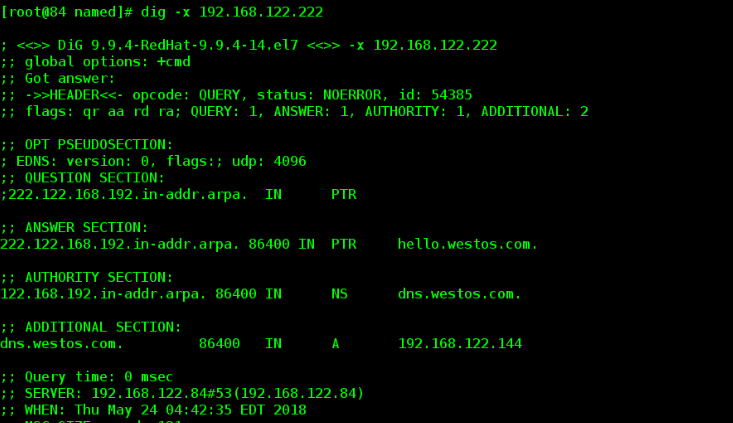
This is the content of my document. 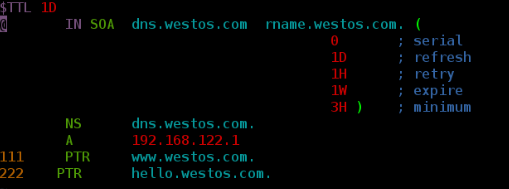
Multiway analysis
[root@server ~]# cd /var/named/
[root@server named]# cp -p westos.com.zone westos.com.inter
[root@server named]# vim westos.com.inter
[root@server named]# cp -p /etc/named.rfc1912.zones /etc/named.rfc1912.inter
[root@server named]# vim /etc/named.rfc1912.inter
zone "westos.com" IN { ##Delete this paragraph
type master;
file "westos.com.zone";
allow-update { none; };
};
zone "westos.com" IN { ##Add this paragraph
type master;
file "westos.com.inter";
allow-update { none; };
};
[root@server named]# vim /etc/named.conf
/*
zone "." IN {
type hint; Note this paragraph
file "named.ca";
};
include "/etc/named.rfc1912.zones";
include "/etc/named.root.key";
*/
view localnet{
match-clients { 192.168.122.84/24; }; ##Add view
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones";
};
view internet{
match-clients { 192.168.122.84/24; };
zone "." IN {
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.inter";
};
[root@server named]# systemctl restart named
//Testing:
//Add a wireless network card to server and set it up84 Network segment
[root@server ~]# vim /etc/sysconfig/network-scripts/ifcfg-eth1
DEVICE=eth1
BOOTPROTO=none
IPADDR= 192.168.122.84
NETMASK=255.255.255.0
ONBOOT=yes
[root@server ~]# systemctl restart network
[root@server ~]# ifconfig
eth1: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.122.84 netmask 255.255.255.0 broadcast 172.25.20.255
inet6 fe80::5054:ff:fe5f:4e96 prefixlen 64 scopeid 0x20<link>
ether 52:54:00:5f:4e:96 txqueuelen 1000 (Ethernet)
RX packets 7681 bytes 945721 (923.5 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 33 bytes 4387 (4.2 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@server ~]# vim /etc/resolv.conf
# Generated by NetworkManager
search example.com
nameserver 192.168.122.84 ##Setting dns pointing
# No nameservers found; try putting DNS servers into your
# ifcfg files in /etc/sysconfig/network-scripts like so:
#
# DNS1=xxx.xxx.xxx.xxx
# DNS2=xxx.xxx.xxx.xxx
# DOMAIN=lab.foo.com bar.foo.com
//Detection on server
[root@server ~]# dig www.westos.com ##
; <<>> DiG 9.9.4-RedHat-9.9.4-14.el7 <<>> www.westos.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 21593
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 2
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.westos.com. IN A
;; ANSWER SECTION:
www.westos.com. 86400 IN A 192.168.122.83
;; AUTHORITY SECTION:
westos.com. 86400 IN NS dns.westos.com.
;; ADDITIONAL SECTION:
dns.westos.com. 86400 IN A 192.168.122.84
;; Query time: 0 msec
;; SERVER: 192.168.122.84#53( 192.168.122.84)
;; WHEN: Tue May 09 03:18:41 EDT 2017
;; MSG SIZE rcvd: 93
//Detection on client
[root@client ~]# dig www.westos.com
; <<>> DiG 9.9.4-RedHat-9.9.4-14.el7 <<>> www.westos.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 27016
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 2
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;www.westos.com. IN A
;; ANSWER SECTION:
www.westos.com. 86400 IN A 192.168.122.83
;; AUTHORITY SECTION:
westos.com. 86400 IN NS dns.westos.com.
;; ADDITIONAL SECTION:
dns.westos.com. 86400 IN A 192.168.122.84
;; Query time: 1 msec
;; SERVER: 192.168.122.84#53( 192.168.122.84)
;; WHEN: Tue May 09 03:16:54 EDT 2017
;; MSG SIZE rcvd: 93
dns update
[root@server ~]# cp -p /var/named/westos.com.zone /mnt/
[root@server ~]# vim /etc/named.rfc1912.zones
zone "westos.com" IN {
type master;
file "westos.com.zone";
allow-update { 192.168.122.83; };
};
[root@server ~]# chmod 770 /var/named/
[root@server ~]# setsebool -P named_write_master_zones 1
[root@server ~]# systemctl restart named
//Detection in client
[root@client ~]# nsupdate ##Update data
> server 192.168.122.84
> update add hello.westos.com 86400 A 192.168.122.88 ##Add to
> send
> quit
[root@client ~]# dig hello.westos.com
; <<>> DiG 9.9.4-RedHat-9.9.4-14.el7 <<>> hello.westos.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 34366
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 2
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;hello.westos.com. IN A
;; ANSWER SECTION:
hello.westos.com. 86400 IN A 192.168.122.88
;; AUTHORITY SECTION:
westos.com. 86400 IN NS dns.westos.com.
;; ADDITIONAL SECTION:
dns.westos.com. 86400 IN A 192.168.122.84
;; Query time: 0 msec
;; SERVER: 192.168.122.84#53( 192.168.122.84)
;; WHEN: Tue May 09 03:46:17 EDT 2017
;; MSG SIZE rcvd: 95
[root@client ~]# nsupdate
> server 192.168.122.84
> update delete hello.westos.com ##Deleting
> send
> quit
[root@client ~]# dig hello.westos.com
; <<>> DiG 9.9.4-RedHat-9.9.4-14.el7 <<>> hello.westos.com
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 23712
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;hello.westos.com. IN A
;; AUTHORITY SECTION:
westos.com. 10800 IN SOA dns.westos.com. root.westos.com. 2 86400 3600 604800 10800
;; Query time: 0 msec
;; SERVER: 192.168.122.84#53( 192.168.122.84)
;; WHEN: Tue May 09 03:50:11 EDT 2017
;; MSG SIZE rcvd: 90
//Because updating dns results in a new file / var/named/westos.com.zone.jnl When you finish the experiment, you need to delete the generated files, and then copy the previously copied files. Otherwise, it will have an impact on the later experiments.
[root@server named]# rm -fr /var/named/westos.com.zone.jnl /var/named/westos.com.zone
[root@server named]# cp -p /mnt/westos.com.zone /var/named/Based on key
cp -p /etc/rndc.key /etc/westos.key
dnssec-keygen -a HMAC-MD5 -b 512 -n HOST westos
Kwestos.+157+24252.key
cat Kwestos.+157+24252.key
vim /etc/westos.key
key "westos" {
algorithm hmac-md5;
secret "hNSjcO3w/ZXSJo9TYoiIdFnzrOETFq74Smy9dlD3QhI09uj7tvtJdBSAV84L2KLhvDaM1wrI0leV5ti+VFByfQ==";
};
vim /etc/named.conf
include "/etc/westos.key";
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
vim /etc/named.rfc1912.zones.inter
zone "westos.com" IN {
type master;
file "westos.com.inter";
allow-update { key westos; };
also-notify { 192.168.122.84; };
//test
scp Kwestos.+157+24252* root@192.168.122.84:/mnt/
//Execution in the host with key
nsupdate -k Kwestos.+157+24252.private