What is a container?In life, our common containers are all kinds of bottles, jars and jars, all kinds of things that can hold other materials are called containers. The characteristics of containers are that they have a good isolation function, which makes different materials isolated from each other. In addition, containers are convenient to transport and store. This is what we call containers in life and their characteristics. In the field of computers, containers are nothing more than containers.It is characterized by containers in the same life, which are isolated and easy to "transport" (transportation in computers is called porting, from system A to system B) and convenient to "store" (in this case, packages of library files on which programs and operations depend, i.e., packages of programs and runtime environments); LXC is the abbreviation of Linux containers, meaning LinuxContainer; Linux container technology is really about integrating the functionality of the kernel so that it can support multiple containers running in isolation from each other; we know that the functional users of the kernel cannot directly operate, they must have a user-space software to manipulate the kernel functionality through system calls; so LxC is the tool used to manipulate the containerization of the Linux kernel; this logic is somewhat similar to iptables Iptables do not check the user's message, it is the kernel netfilter that really works.
Key technical points of LXC:
1. chroot: Root switch, an operation that changes the root directory of the currently running process and its children.A program running in this environment cannot access files and commands outside the root directory.
2. namespaces: Namespaces, LXC relies on the namespace feature of the Linux kernel in terms of isolation control, specifically by adding flag s to clone s;
3. CGroups: Control group, LXC depends on the cgroups subsystem of the Linux kernel in resource management. The cgroups subsystem is a process group-based resource management framework provided by the Linux kernel, which can limit available resources for a specific process group.
LXC is simple to use:
1. Install LXC tools
[root@lxc ~]# yum install lxc-* libcgroup* bridge-utils Loaded plugins: fastestmirror base | 3.6 kB 00:00:00 epel | 4.7 kB 00:00:00 extras | 2.9 kB 00:00:00 updates | 2.9 kB 00:00:00 (1/7): base/7/x86_64/group_gz | 153 kB 00:00:00 (2/7): epel/x86_64/group_gz | 95 kB 00:00:00 (3/7): epel/x86_64/updateinfo | 1.0 MB 00:00:00 (4/7): updates/7/x86_64/primary_db | 1.3 MB 00:00:00 (5/7): extras/7/x86_64/primary_db | 190 kB 00:00:00 (6/7): base/7/x86_64/primary_db | 6.1 MB 00:00:01 (7/7): epel/x86_64/primary_db | 6.8 MB 00:00:02 Determining fastest mirrors * base: mirrors.aliyun.com * extras: mirrors.aliyun.com * updates: mirrors.aliyun.com Resolving Dependencies --> Running transaction check ---> Package bridge-utils.x86_64 0:1.5-9.el7 will be installed ---> Package libcgroup.x86_64 0:0.41-21.el7 will be installed ---> Package libcgroup-devel.x86_64 0:0.41-21.el7 will be installed ---> Package libcgroup-pam.x86_64 0:0.41-21.el7 will be installed ......Omit some information Installed: bridge-utils.x86_64 0:1.5-9.el7 libcgroup.x86_64 0:0.41-21.el7 libcgroup-devel.x86_64 0:0.41-21.el7 libcgroup-pam.x86_64 0:0.41-21.el7 libcgroup-tools.x86_64 0:0.41-21.el7 lxc.x86_64 0:1.0.11-2.el7 lxc-devel.x86_64 0:1.0.11-2.el7 lxc-doc.noarch 0:1.0.11-2.el7 lxc-extra.x86_64 0:1.0.11-2.el7 lxc-libs.x86_64 0:1.0.11-2.el7 lxc-templates.x86_64 0:1.0.11-2.el7 Dependency Installed: libtirpc.x86_64 0:0.2.4-0.16.el7 lua-alt-getopt.noarch 0:0.7.0-4.el7 lua-filesystem.x86_64 0:1.6.2-2.el7 lua-lxc.x86_64 0:1.0.11-2.el7 python3.x86_64 0:3.6.8-13.el7 python3-libs.x86_64 0:3.6.8-13.el7 python3-pip.noarch 0:9.0.3-7.el7_7 python3-setuptools.noarch 0:39.2.0-10.el7 python36-lxc.x86_64 0:1.0.11-2.el7 Complete! [root@lxc ~]#
Tip: Please configure epel source and base source before installation;
2. Add Network Bridge
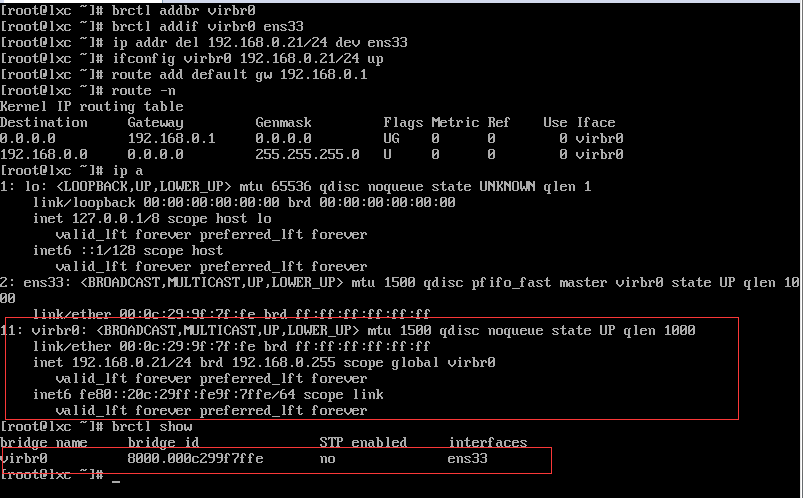
3. Check if the current system meets the requirements for creating containers
[root@lxc ~]# lxc-checkconfig Kernel configuration not found at /proc/config.gz; searching... Kernel configuration found at /boot/config-3.10.0-693.el7.x86_64 --- Namespaces --- Namespaces: enabled Utsname namespace: enabled Ipc namespace: enabled Pid namespace: enabled User namespace: enabled newuidmap is not installed newgidmap is not installed Network namespace: enabled Multiple /dev/pts instances: enabled --- Control groups --- Cgroup: enabled Cgroup clone_children flag: enabled Cgroup device: enabled Cgroup sched: enabled Cgroup cpu account: enabled Cgroup memory controller: enabled Cgroup cpuset: enabled --- Misc --- Veth pair device: enabled Macvlan: enabled Vlan: enabled Bridges: enabled Advanced netfilter: enabled CONFIG_NF_NAT_IPV4: enabled CONFIG_NF_NAT_IPV6: enabled CONFIG_IP_NF_TARGET_MASQUERADE: enabled CONFIG_IP6_NF_TARGET_MASQUERADE: enabled CONFIG_NETFILTER_XT_TARGET_CHECKSUM: enabled --- Checkpoint/Restore --- checkpoint restore: enabled CONFIG_FHANDLE: enabled CONFIG_EVENTFD: enabled CONFIG_EPOLL: enabled CONFIG_UNIX_DIAG: enabled CONFIG_INET_DIAG: enabled CONFIG_PACKET_DIAG: enabled CONFIG_NETLINK_DIAG: enabled File capabilities: enabled Note : Before booting a new kernel, you can check its configuration usage : CONFIG=/path/to/config /usr/bin/lxc-checkconfig [root@lxc ~]#
Tip: If error is not reported, the current environment meets the criteria for creating containers
4. Specify template to create container
[root@lxc ~]# lxc-create -n test -t /usr/share/lxc/templates/lxc-centos
Host CPE ID from /etc/os-release: cpe:/o:centos:centos:7
Checking cache download in /var/cache/lxc/centos/x86_64/7/rootfs ...
Downloading CentOS minimal ...
Loaded plugins: fastestmirror
base | 3.6 kB 00:00:00
updates | 2.9 kB 00:00:00
Determining fastest mirrors
* base: mirrors.aliyun.com
* updates: mirrors.aliyun.com
Resolving Dependencies
--> Running transaction check
---> Package chkconfig.x86_64 0:1.7.4-1.el7 will be installed
--> Processing Dependency: rtld(GNU_HASH) for package: chkconfig-1.7.4-1.el7.x86_64
--> Processing Dependency: libpopt.so.0(LIBPOPT_0)(64bit) for package: chkconfig-1.7.4-1.el7.x86_64
--> Processing Dependency: libc.so.6(GLIBC_2.14)(64bit) for package: chkconfig-1.7.4-1.el7.x86_64
......Omit some content
Container rootfs and config have been created.
Edit the config file to check/enable networking setup.
The temporary root password is stored in:
'/var/lib/lxc/test/tmp_root_pass'
The root password is set up as expired and will require it to be changed
at first login, which you should do as soon as possible. If you lose the
root password or wish to change it without starting the container, you
can change it from the host by running the following command (which will
also reset the expired flag):
chroot /var/lib/lxc/test/rootfs passwd
[root@lxc ~]#
Tip: -t denotes the specified template, which is actually a shell script. After installing the lxc-templates package, there are several templates below by default/usr/share/lxc/templates/If you see the above tip indicating that the container has been successfully created, we can use lxc-ls to view all containers created by the current system;
[root@lxc ~]# lxc-ls test [root@lxc ~]#
Tip: You can see that the current system only has a container named test
5. Modify the root password of the current test container
[root@lxc ~]# chroot /var/lib/lxc/test/rootfs passwd Changing password for user root. New password: BAD PASSWORD: The password is shorter than 8 characters Retype new password: passwd: all authentication tokens updated successfully. [root@lxc ~]#
Tip: Actually, you don't need to change it. The default password is stored in the file / var/lib/lxc/test/tmp_root_passwd; it prompts us to change the password after you log in to the container without changing it
6. Start the container and log in to it
[root@lxc ~]# lxc-start -n test
systemd 219 running in system mode. (+PAM +AUDIT +SELINUX +IMA -APPARMOR +SMACK +SYSVINIT +UTMP +LIBCRYPTSETUP +GCRYPT +GNUTLS +ACL +XZ +LZ4 -SECCOMP +BLKID +ELFUTILS +KMOD +IDN)
Detected virtualization lxc.
Detected architecture x86-64.
Welcome to CentOS Linux 7 (Core)!
Running in a container, ignoring fstab device entry for /dev/root.
Cannot add dependency job for unit display-manager.service, ignoring: Unit not found.
[ OK ] Reached target Local Encrypted Volumes.
[ OK ] Reached target Swap.
[ OK ] Started Dispatch Password Requests to Console Directory Watch.
[ OK ] Started Forward Password Requests to Wall Directory Watch.
[ OK ] Reached target Paths.
[ OK ] Reached target Remote File Systems.
[ OK ] Created slice Root Slice.
[ OK ] Listening on Journal Socket.
[ OK ] Created slice User and Session Slice.
[ OK ] Listening on /dev/initctl Compatibility Named Pipe.
[ OK ] Listening on Delayed Shutdown Socket.
[ OK ] Created slice System Slice.
Mounting Huge Pages File System...
Starting Read and set NIS domainname from /etc/sysconfig/network...
Starting Journal Service...
Starting Remount Root and Kernel File Systems...
[ OK ] Reached target Slices.
[ OK ] Created slice system-getty.slice.
Mounting POSIX Message Queue File System...
[ OK ] Mounted Huge Pages File System.
[ OK ] Started Journal Service.
[ OK ] Started Read and set NIS domainname from /etc/sysconfig/network.
[ OK ] Mounted POSIX Message Queue File System.
[ OK ] Started Remount Root and Kernel File Systems.
Starting Configure read-only root support...
Starting Flush Journal to Persistent Storage...
Starting Rebuild Hardware Database...
[ OK ] Reached target Local File Systems (Pre).
<46>systemd-journald[16]: Received request to flush runtime journal from PID 1
[ OK ] Started Flush Journal to Persistent Storage.
[ OK ] Started Configure read-only root support.
Starting Load/Save Random Seed...
[ OK ] Reached target Local File Systems.
Starting Rebuild Journal Catalog...
Starting Create Volatile Files and Directories...
Starting Mark the need to relabel after reboot...
[ OK ] Started Load/Save Random Seed.
[ OK ] Started Rebuild Journal Catalog.
[ OK ] Started Create Volatile Files and Directories.
[ OK ] Started Mark the need to relabel after reboot.
Starting Update UTMP about System Boot/Shutdown...
[ OK ] Started Update UTMP about System Boot/Shutdown.
[ OK ] Started Rebuild Hardware Database.
Starting Update is Completed...
[ OK ] Started Update is Completed.
[ OK ] Reached target System Initialization.
[ OK ] Listening on D-Bus System Message Bus Socket.
[ OK ] Reached target Sockets.
[ OK ] Reached target Basic System.
Starting Permit User Sessions...
Starting OpenSSH Server Key Generation...
Starting LSB: Bring up/down networking...
[ OK ] Started D-Bus System Message Bus.
Starting Login Service...
[ OK ] Started Daily Cleanup of Temporary Directories.
[ OK ] Reached target Timers.
[ OK ] Started Permit User Sessions.
Starting Cleanup of Temporary Directories...
[ OK ] Started Console Getty.
[ OK ] Reached target Login Prompts.
[ OK ] Started Command Scheduler.
[ OK ] Started Cleanup of Temporary Directories.
[ OK ] Started Login Service.
[ OK ] Started OpenSSH Server Key Generation.
CentOS Linux 7 (Core)
Kernel 3.10.0-693.el7.x86_64 on an x86_64
test login: root
Password:
You are required to change your password immediately (root enforced)
Changing password for root.
(current) UNIX password:
New password:
Retype new password:
[root@test ~]# hostname
test
[root@test ~]#
Tip: After starting the container, log in to the container with the default password, which prompts us to change the password; if you want the container to run in the background (not occupying the current shell terminal), you can use the -d option to specify it;
View information about the test container
[root@lxc ~]# lxc-info -n test Name: test State: RUNNING PID: 5896 IP: 192.168.0.216 CPU use: 0.16 seconds BlkIO use: 0 bytes Memory use: 1.34 MiB KMem use: 0 bytes Link: veth6WQY6V TX bytes: 1.67 KiB RX bytes: 17.50 KiB Total bytes: 19.17 KiB [root@lxc ~]#
Stop the test container
[root@lxc ~]# lxc-stop -n test [root@lxc ~]# lxc-info -n test Name: test State: STOPPED [root@lxc ~]#
Destroy Containers
[root@lxc ~]# lxc-destroy -n test [root@lxc ~]# lxc-ls [root@lxc ~]#
Tip: Destroy the container. The container must be in a stopped state, otherwise it cannot be destroyed
The above is about simple management of lxc containers;