We will use a series to explain the complete practice of microservices from requirements to online, from code to k8s deployment, from logging to monitoring.
The whole project uses the micro services developed by go zero, which basically includes go zero and some middleware developed by relevant go zero authors. The technology stack used is basically the self-developed component of the go zero project team, which is basically the go zero software.
Actual project address: github.com/Mikaelemmmm/go-zero-loo...
1. Authentication service
1.1 identity-api
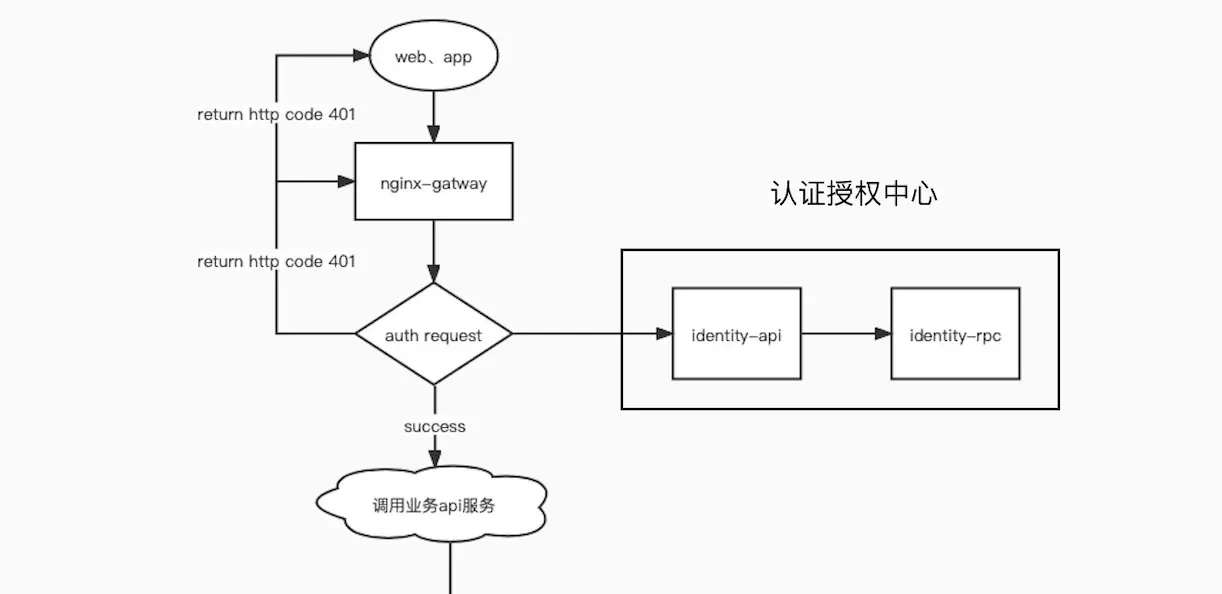
Identity is mainly used for authentication services, as mentioned earlier in nginx gateway. When accessing a resource, nginx will first parse the token in the identity API, and the identity API will request identity RPC. All authentication and issuance tokens are unified in identity RPC
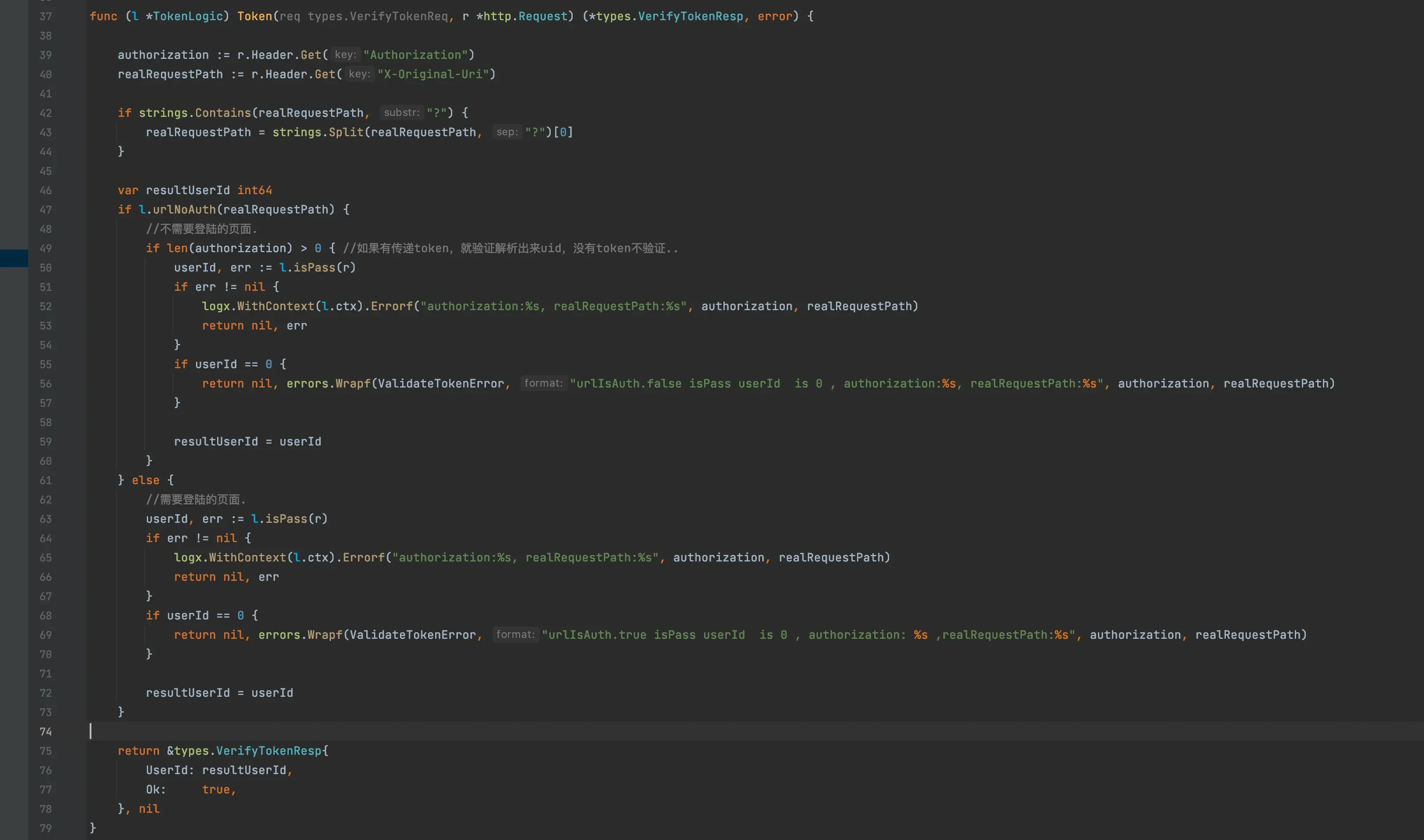
We will get the token from the Authorization of the header and the access resource path from x-Original-Uri
- If the currently accessed route requires login:
- token parsing failure: the http401 error code will be returned to the front end;
- Successful token parsing: the parsed userId will be put into the x-user of the header and returned to the auth module. The auth module will pass the header to the corresponding accessed service (usercenter), so that we can get the id of the logged in user directly in the usercenter
- If the currently accessed route does not require login:
- A token was passed in the front-end header
- If the token verification fails: http401 is returned;
- If the token verification is successful: the parsed userId will be put into the x-user of the header and returned to the auth module. The auth module will pass the header to the corresponding access service (usercenter), so that we can get the id of the login user directly in the usercenter
- token is not passed in the front-end header: userid will be passed 0 to the back-end service
- A token was passed in the front-end header
The urlNoAuth method determines whether the current resource is configured in yml and can not log in
//Does the current url require authorization verification
func (l *TokenLogic) urlNoAuth(path string) bool {
for _, val := range l.svcCtx.Config.NoAuthUrls {
if val == path {
return true
}
}
return false
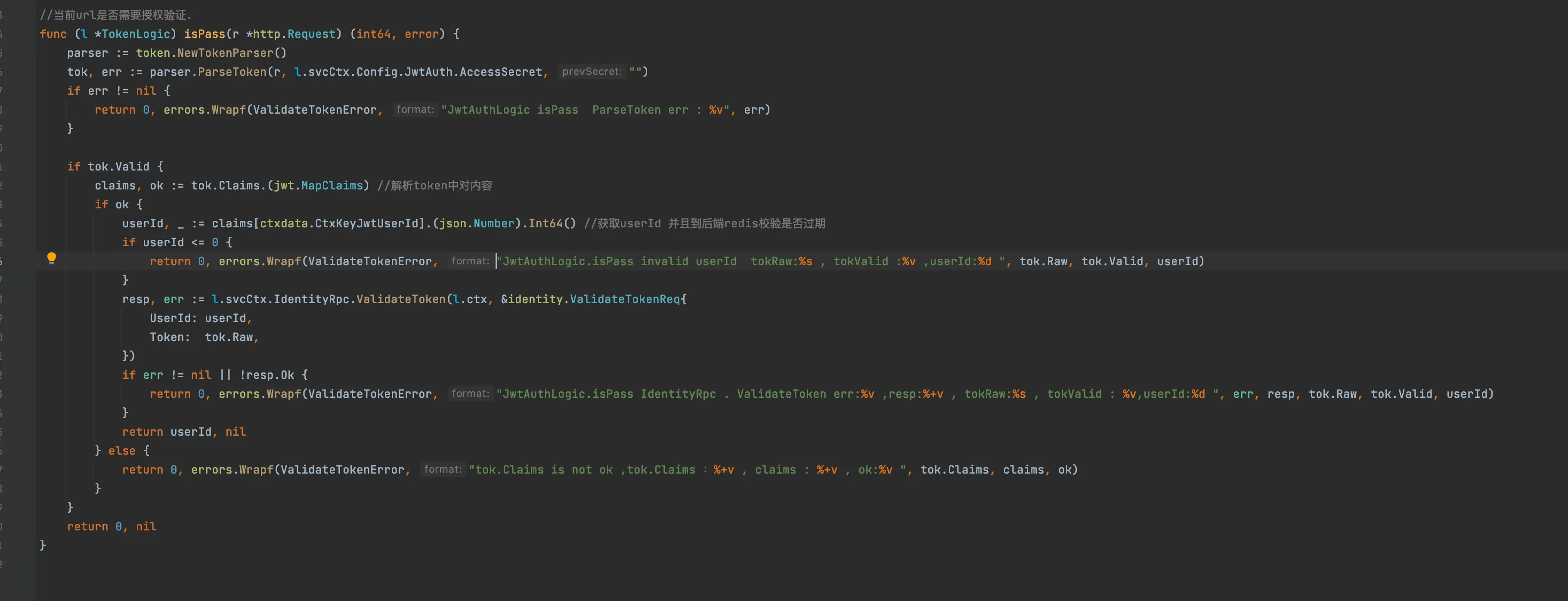
}isPass method is to verify the identity RPC token, which mainly uses the jwt method of go zero
1.2 identity-rpc
When we register and log in successfully, the user service will call identity RPC to generate a token, so we uniformly issue and verify the token in identity RPC, so we don't have to write a jwt for each service to maintain.
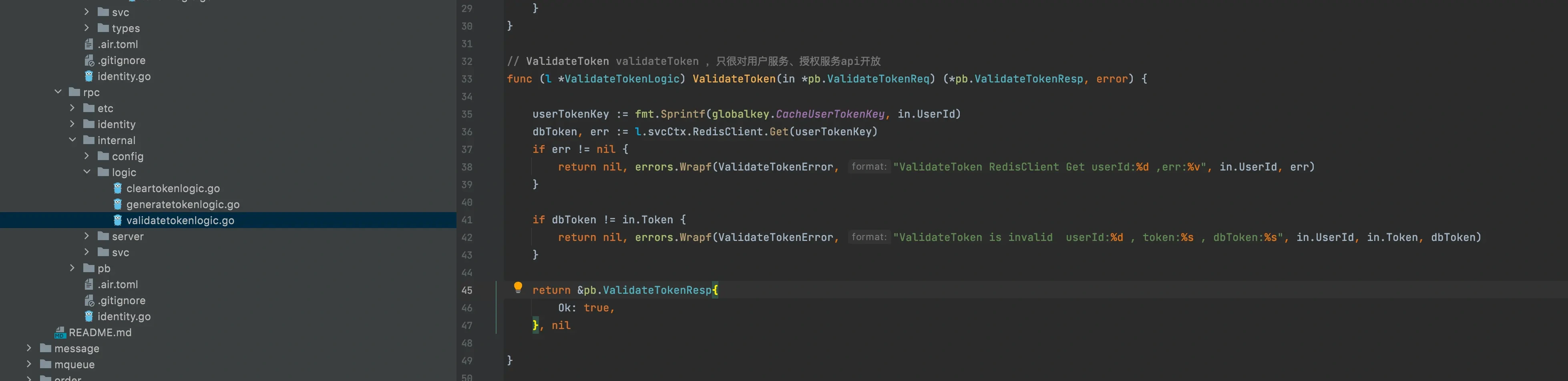
When the identity api request comes in, the identity api can parse the userid itself, but if we want to check whether the token is expired, we need to go to redis in the back-end rpc for secondary verification (of course, if you think there is one more request here, you can put this step into the api and directly request redis), which is verified by the validateToken method of rpc
message ValidateTokenReq {
int64 userId = 1;
string token = 2;
}
message ValidateTokenResp {
bool ok = 1;
}
rpc validateToken(ValidateTokenReq) returns(ValidateTokenResp);Verify whether the redis token issued during login, registration and other authorization is correct and expired.
In this way, the api can return whether the auth module of nginx fails. If it fails, the auth will directly return to the front-end http code 401 (so your front-end should first judge all the exceptions of http status code > = 400, and then judge the business error code). If you successfully access the back-end service directly, you will get the data and directly return it to the front-end display
2. Install goctl, protoc and protoc Gen go
[note] this has nothing to do with authentication. It's just for the code to be written later. It's best to install it here
2.1 installation goctl
# for Go 1.15 and earlier GO111MODULE=on GOPROXY=https://goproxy.cn/,direct go get -u github.com/zeromicro/go-zero/tools/goctl@latest # for Go 1.16 and later GOPROXY=https://goproxy.cn/,direct go install github.com/zeromicro/go-zero/tools/goctl@latest
Verify that the installation was successful
$ goctl --version
Goctl custom template: copy the contents of the data/goctl folder under the project directory to the HOME directory In goctl, when generating code, goctl will preferentially generate code according to the content under this template
$ cp -r data/goctl ~/.goctl
2.2 installing the protoc ol
Link: github.com/protocolbuffers/protobu...
Directly find the protocol of the corresponding platform. I'm a mac intel chip, so directly find protocol-3.19.3-osx-x86_ 64.zip, unzip it, enter the bin directory under this directory, and copy the protocol directly to your gopath/bin directory.
Verify that the installation was successful
$ protoc --version
2.3 installing the protocol Gen go
$ GOPROXY=https://goproxy.cn/,direct go install google.golang.org/protobuf/cmd/protoc-gen-go@latest
Check whether there is protocol Gen go under $GOPATH/bin
[note]: if you encounter the following problems when using goctl to generate code later
protoc --proto_path=/Users/seven/Developer/goenv/go-zero-looklook/app/usercenter/cmd/rpc/pb usercenter.proto --go_out=plugins=grpc:/Users/seven/Developer/goenv/go-zero-looklook/app/usercenter/cmd/rpc --go_opt=Musercenter.proto=././pb goctl: generation error: unsupported plugin protoc-gen-go which installed from the following source: google.golang.org/protobuf/cmd/protoc-gen-go, github.com/protocolbuffers/protobuf-go/cmd/protoc-gen-go; Please replace it by the following command, we recommend to use version before v1.3.5: go get -u github.com/golang/protobuf/protoc-gen-go goctl version: 1.3.0 darwin/amd64
Direct execution
$ GOPROXY=https://goproxy.cn/,direct go get -u github.com/golang/protobuf/protoc-gen-go
2.4 install the protocol Gen go grpc
$ GOPROXY=https://goproxy.cn/,direct go install google.golang.org/grpc/cmd/protoc-gen-go-grpc@latest
3. Summary
In general, identity is relatively simple. The whole process is as follows:
User initiated resource request - > nginx Gateway - > match to corresponding service module - > auth module - > identity API - > identity RPC - > user requested resource
Project address
Welcome to go zero and star support us!
Wechat communication group
Focus on the "micro service practice" official account and click on the exchange group to get the community community's two-dimensional code.