1, Brief description
Syzkaller is a kernel fuzzy testing tool developed by Google. In short, it automatically inputs various effective, invalid and completely randomized parameter data to the kernel, and observes the operation status of the kernel, whether there are panic, memory leakage and other problems, so as to discover the vulnerabilities hidden in the kernel. In recent years, many kernel CVE discoveries come from this, and the development and maintenance of this tool is also relatively active. It supports not only x86, but also ARM, Power, MIPS and other processors. It also supports not only Linux, but also windows, FreeBSD, Fuchsia and other systems. At the same time, it can also support the testing of remote physical machines and local virtual machines. In addition, it can also support distributed multi machine testing.
This article focuses on the use without much principle and code analysis. It only needs a little basic linux use. It is suitable for the introduction of syzkaller. There are many holes in the whole environment construction and use process, many of which are not mentioned on the Internet.
2, Basic environment
[1 > all resources acquisition < 1]
1. Network Security Learning Route
2. E-book (white hat)
3. Safety factory internal video
4. 100 src documents
5. Common safety interview questions
6. Analysis of classic topics in ctf competition
7. Complete kit
8. Emergency response notes
3, Environment construction
3.1 Ubuntu virtual machine configuration
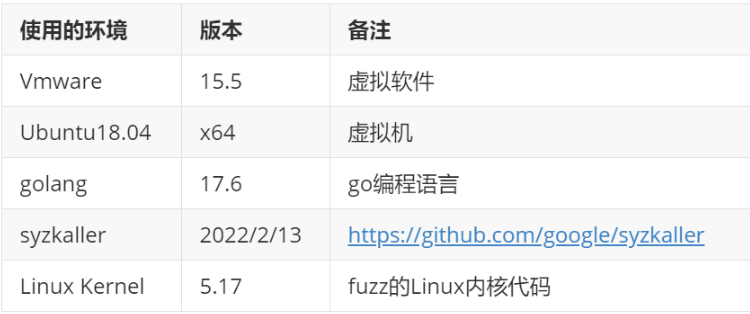
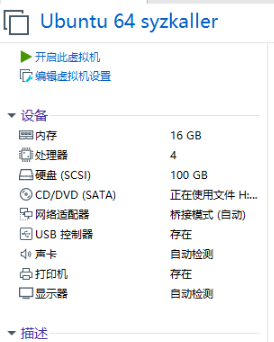
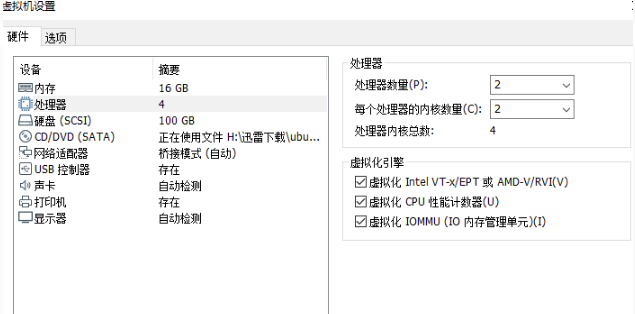
The configuration of Ubuntu virtual machine is shown in the figure below. Because the Linux kernel and syzkaller need to be compiled, the memory should be set as large as possible.
Vmware's own vmtools are installed on Ubuntu 1804 and cannot copy files with physical machines. You can try the following command:
sudo apt update sudo apt install open-vm-tools-desktop fuse
3.2 installing basic software
sudo apt-get install debootstrap sudo apt install qemu-kvm sudo apt-get install subversion sudo apt-get install git sudo apt-get install make sudo apt-get install qemu sudo apt install libssl-dev libelf-dev sudo apt-get install flex bison libc6-dev libc6-dev-i386 linux-libc-dev linux-libc-dev:i386 libgmp3-dev libmpfr-dev libmpc-dev sudo apt-get install g++ sudo apt-get install build-essential sudo apt install gcc sudo apt install openssh-server
Apt install golang go is not used to install go programming language. The version of go programming language installed by apt is 1.10. Using this version of go will report errors when compiling syzkaller, so choose to download and install version 1.17 of go here.
wget https://dl.google.com/go/go1.17.6.linux-amd64.tar.gz tar -zxvf go1.17.6.linux-amd64.tar.gz export GOPATH=/home/test/git/go/go //Replace the path with the path in your own virtual machine export GOROOT=/home/test/git/go/go export PATH=$GOPATH/bin:$PATH export PATH=$GOROOT/bin:$PATH
Run the go command and the installation is successful.
3.3 compiling syzkaller
Use the following command to pull and compile syzkaller code.
git clone https://github.com/google/syzkaller.git cd syzkaller make //Errors may be reported in this step
In case of jamming or killed process, use dmesg | egrep -i -B100 'killed process' to check. If it is Out of memory, it means that the memory is insufficient. At this time, you can use the following command to compile the first file separately:
GOOS=linux GOARCH=amd64 go build "-ldflags=-s -w -X github.com/google/syzkaller/prog.GitRevision= -X 'github.com/google/syzkaller/prog.gitRevisionDate='" -o ./bin/syz-manager github.com/google/syzkaller/syz-manager
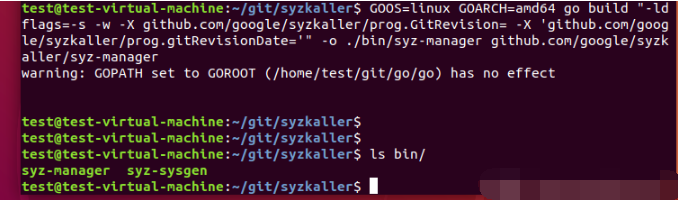
Check whether there is a compiled SYZ manager file in the bin directory:
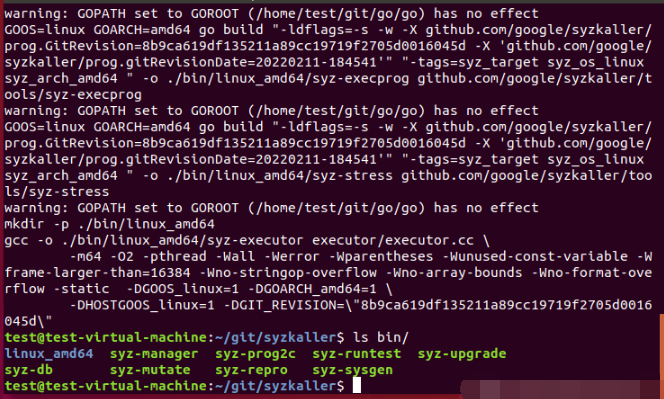
Continue to use the make command to complete the compilation, as shown in the following figure:
If the problem of insufficient memory still exists after compiling the first file separately, it can be solved by adding swap partition.
dd if=/dev/zero of=/root/swapfile bs=1M count=1024 //Create a file to be a swap partition: add a 1GB swap partition, and the command is written as follows, where count is equal to the number of blocks you want (bs*count = file size). mkswap /root/swapfile #Establish the file system of swap swapon /root/swapfile #Enable swap file /root/swapfile swap swap defaults 0 0 //Enable the system to start automatically when it is powered on, and add it in the file / etc/fstab
3.4 compiling Linux kernel
git pull linux code:
git clone https://mirrors.tuna.tsinghua.edu.cn/git/linux.git cd linux
If a certificate verification error is reported when pulling the code, as shown in the figure below:
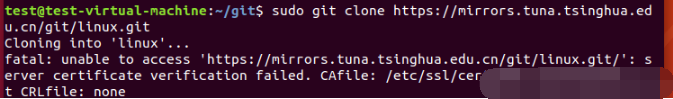
Solve the problem with the following command:
sudo apt update sudo apt install -y libgnutls30
After entering the linux directory, use the following commands to configure:
make CC="/usr/bin/gcc" defconfig make CC="/usr/bin/gcc" kvm_guest.config
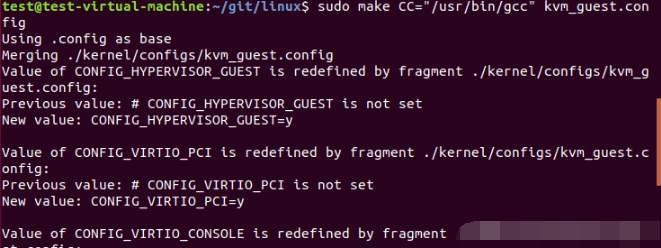
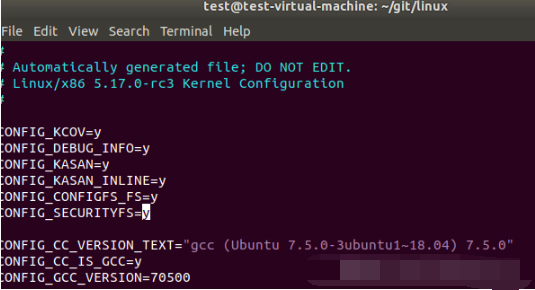
After configuration, open the in the current directory config file for manual configuration. The added contents are as follows:
CONFIG_KCOV=y CONFIG_DEBUG_INFO=y CONFIG_KASAN=y CONFIG_KASAN_INLINE=y CONFIG_CONFIGFS_FS=y CONFIG_SECURITYFS=y
Then execute the following command:
make CC="/usr/bin/gcc" olddefconfig
As shown in the figure below:
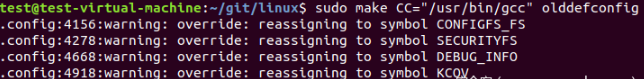
Open it again The config file found that the configuration just added has been deleted because there are in the configuration file, as shown in the following figure:
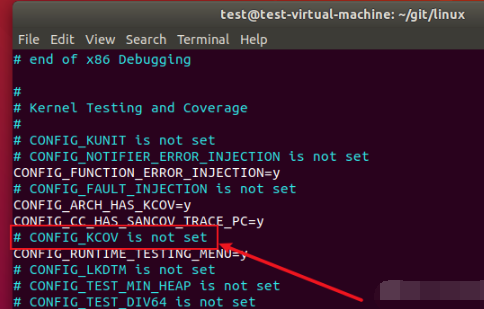
Re execute all configuration commands before olddefconfig, and then In the config file, delete the comment line where we want to add the configuration, such as: # CONFIG_KCOV is not set. Finally, re add the configuration above, and then execute the make CC = "/ usr/bin/gcc" olddefconfig command to find that there will be no warning.
If it is not deleted, the error "Failed to start Remount Root and Kernel File Systems" will appear during qemu virtualization later.
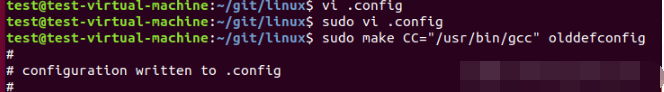
Finally, execute the following command to complete the compilation.
make CC="/usr/bin/gcc" -j64
3.5 making document system
Use the following command:
wget https://raw.githubusercontent.com/google/syzkaller/master/tools/create-image.sh -O create-image.sh chmod +x create-image.sh ./create-image.sh
If the wget command fails to download the file, you can directly access the browser and copy one without affecting the use.
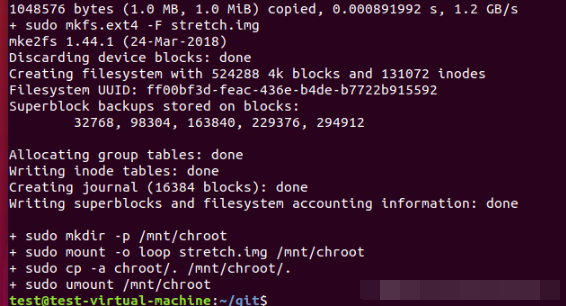
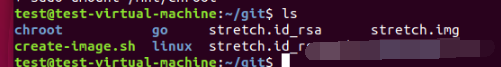
You can see stretch. Net under the directory id_ rsa,stretch.id_rsa.pub,stretch. The IMG file is successful.
3.6 operation syzkall
Here, you need to open the virtualization of Vmware virtual machine.
Install qemu virtual tools.
sudo apt-get install qemu-system-x86
Create boot. In the current directory SH file, the contents of which are as follows:
qemu-system-x86_64 \ -kernel linux/arch/x86/boot/bzImage \ -append "console=ttyS0 root=/dev/sda debug earlyprintk=serial slub_debug=QUZ"\ -hda ./stretch.img \ -net user,hostfwd=tcp::10021-:22 -net nic \ -enable-kvm \ -nographic \ -m 2560M \ -smp 2 \ -pidfile vm.pid \ 2>&1 | tee vm.log
Run boot SH, Failed to start Remount Root and Kernel File Systems is that the above configuration file is not well configured, and the KVM cannot be accessed to set the virtual machine.
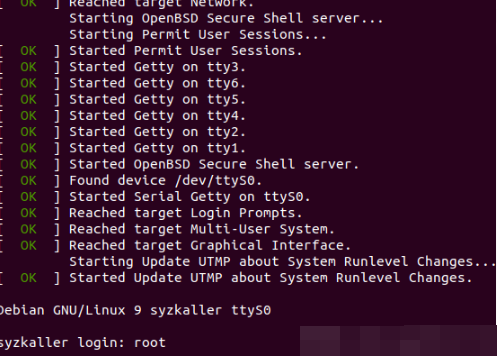
When running qemu virtual machine, there is a login prompt. Enter root as shown in the figure below. Log in without password.
Use the following command in the Vmware virtual machine to determine whether the ssh service of the qemu virtual machine is started successfully (syzkaller needs ssh) by logging in to the qemu virtual machine.
ssh -i stretch.id_rsa -p 10021 -o "StrictHostKeyChecking no" root[@localhost](https://github.com/localhost "@localhost")
Enter the syzkaller directory downloaded before and create my CFG configuration file, the contents of which are as follows:
{
"target": "linux/amd64",
"http": "127.0.0.1:56741",
"workdir": "/home/test/git/syzkaller/workdir",
"kernel_obj": "/home/test/git/linux",
"image": "/home/test/git/stretch.img",
"sshkey": "/home/test/git/stretch.id_rsa",
"syzkaller": "/home/test/git/syzkaller",
"procs": 8,
"type": "qemu",
"vm": {
"count": 4,
"kernel": "/home/test/git/linux/arch/x86/boot/bzImage",
"cpu": 2,
"mem": 2048
}
}
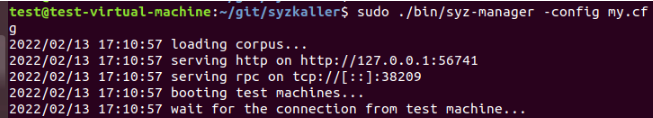
Use/ bin/syz-manager -config my. The CFG command runs. It runs a little slow and needs to wait.
4, Resolve the Failed to start Raise network interfaces error
The error "Failed to start Raise network interfaces" often occurs when running SYZ manager or qemu simulation.
Execute boot SH script, run the virtual machine, execute ifconfig command, and find that this command does not exist.
At present, the qemu virtual machine cannot be ping ed to the external network and cannot be installed with apt command, so here you choose to download the net tools offline package, compile it and copy it into the qemu virtual machine.
The qemu virtual machine initially has a default ip of 10.0.2.15, and also initializes the physical machine with an ip of 10.0.2.2.
You can use the following commands to copy files:
ip link set enp0s3 up scp -r [test@10.0.2](mailto:test@10.0.2).2:/home/test/Desktop/net-tools-2.10 ./
After copying, you can execute the ifconfig command, as shown in the following figure:
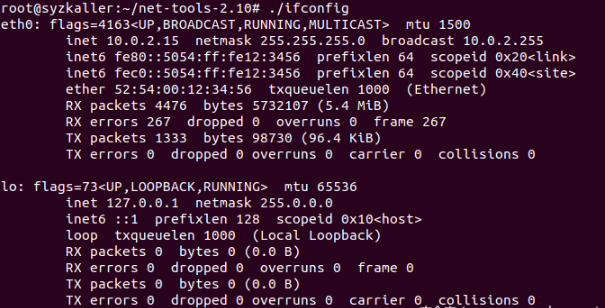
When using boot When the SH script runs qemu virtual machine and reports the error Failed to start Raise network interfaces, it executes the ifconfig command again and finds that only lo network card and enp0s3 network card are not started or ip address is not assigned. Delete the / etc/network/interfaces file in qemu virtual machine and create a new interface file. The contents of the file are as follows and copy it to the / etc/network/interfaces path of qemu virtual machine.
auto eth0 iface eth0 inet dhcp auto enp0s3 iface enp0s3 inet dhcp
Use boot.exe multiple times SH starts the qemu virtual machine and sometimes reports the error Failed to start Raise network interfaces. Then use the ifconfig command to check that the ip address still exists.
The local network card name is not eth0. You can use the following command to change it:
ip link set ens33 down ip link set ens33 name eth0 ip link set eth0 up
If you use syzkaller again for fuzz y, the effect will be much better. As for the root cause, the author has not analyzed the source code at present, and it may be updated in the future.
5, Fuzzy linux driver
5.1 compilation driver
In test There is a heap overflow demo in C:
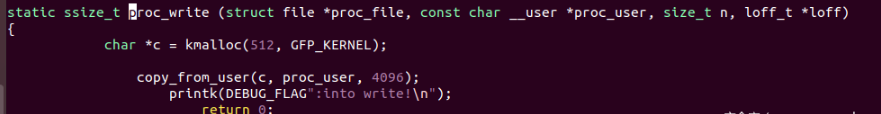
When compiling kernel modules, a linux header is involved. (for example, I compiled the driver of 5.17 under the system of 5.4.0) so the Makefile here is as follows:
CONFIG_MODULE_SIG=n obj-m += test.o EXTRA_CFLAGS += -fno-stack-protector -no-pie all: make -C /lib/modules/5.17.0-rc3-00316-gb81b1829e7e3/build M=$(PWD) modules
Create the directory test and set test Copy C and Makefile to the directory and run the make command.
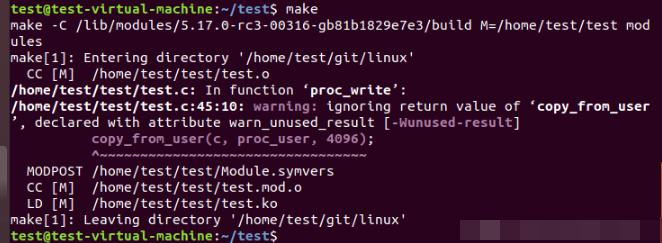
If not found
/lib/modules/5.17.0-rc3-00316-gb81b1829e7e3 path, execute make modules under the linux source code directory_ Install / lib / module.
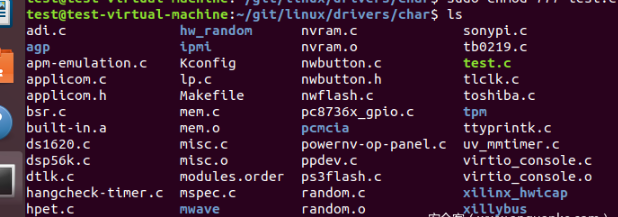
Test C copy to linux/drivers/char Directory:
Add the following configuration to the Kconfig file under the char Directory:
config TEST_MODULE tristate "Heap Overflow Test" default y help This file is to test a buffer overflow.
Add obj - $(config_test_module) + = test in Makefile under char directory o.
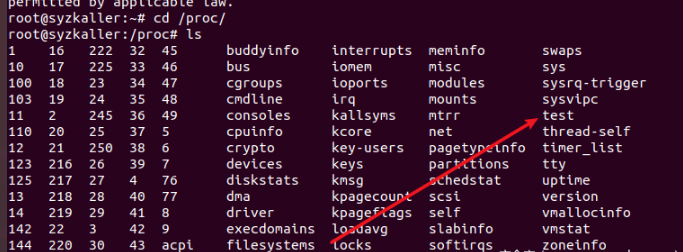
Enter the linux source code directory and make again. After compiling, use boot SH starts the virtual machine, enters the proc directory, and you can see test, indicating that the code has been successfully compiled and loaded.
5.2 adding syzkaller rules
Enter the syzkaller/sys/linux / directory and create a new proc_operation.txt, the contents of the file are as follows:
include <linux/fs.h> open$proc(file ptr[in, string["/proc/test"]], flags flags[proc_open_flags], mode flags[proc_open_mode]) fd read$proc(fd fd, buf buffer[out], count len[buf]) write$proc(fd fd, buf buffer[in], count len[buf]) close$proc(fd fd) proc_open_flags = O_RDONLY, O_WRONLY, O_RDWR, O_APPEND, FASYNC, O_CLOEXEC, O_CREAT, O_DIRECT, O_DIRECTORY, O_EXCL, O_LARGEFILE, O_NOATIME, O_NOCTTY, O_NOFOLLOW, O_NONBLOCK, O_PATH, O_SYNC, O_TRUNC, __O_TMPFILE proc_open_mode = S_IRUSR, S_IWUSR, S_IXUSR, S_IRGRP, S_IWGRP, S_IXGRP, S_IROTH, S_IWOTH, S_IXOTH
Go back to the syzkaller directory and compile SYZ extract and SYZ SYSGEN:
make bin/syz-extract make bin/syz-sysgen
Generate using SYZ extract const file:
bin/syz-extract -os linux -sourcedir "/home/test/git/linux" -arch amd64 proc_operation.txt
Generated proc_operation.txt.const is as follows:
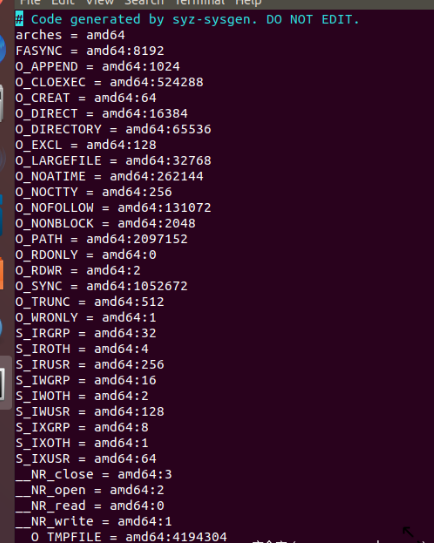
Next, execute the following command:
bin/syz-sysgen make clean make //Here refer to the above` modify my.cfg File, add the following fields: `"enable_syscalls": [ "open$proc", "read$proc", "write$proc", "close$proc" ],
5.3 fuzzy linux driver
Use bin / SYZ Manager - config my CFG command:
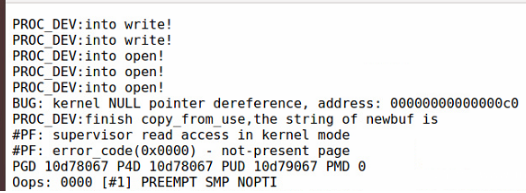
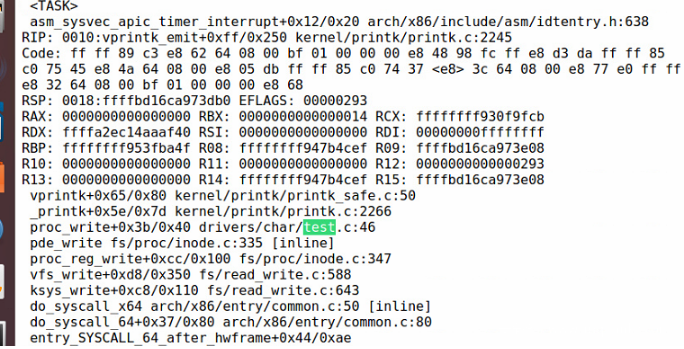
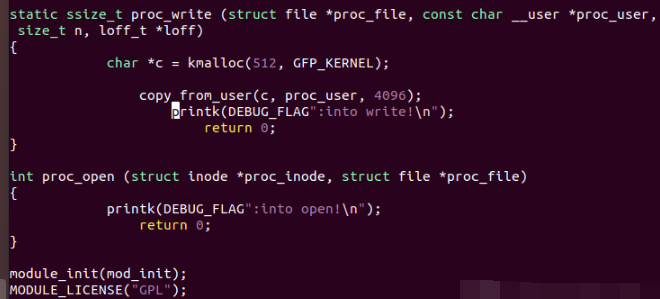
syzkaller recognizes it as a null pointer dereference error.
6, Summary
From the perspective of user experience, it is still difficult for this framework to explore vulnerabilities, especially for some kernel modules with complex interfaces, and it is written with go, which increases the learning cost, but it does dig out many vulnerabilities and is worth learning.