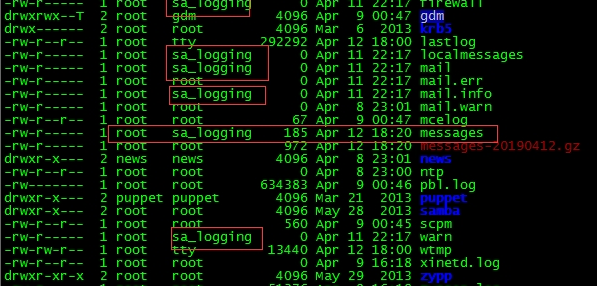
It was originally modified with chown / chmod, but it was restored to its original shape after a day
It is found that logrotate is the program that will modify the log every day when dumping it. Check the configuration file
/var/log/messages {
compress
dateext
maxage 365
rotate 99
missingok
notifempty
size +4096k
create 640 root root
sharedscripts
postrotate
/etc/init.d/syslog reload > /dev/null
endscript
}It is found that a create 640 root statement is very similar. Change to create 770 root logging.
Then, the command logrotate -vf /etc/logrotate.d/syslog was used to test and found that it was the same as before.
Later on
sharedscripts postrotate /etc/init.d/syslog reload > /dev/null endscript
These names can be commented out. It is concluded that the syslog program reloads the configuration file to make changes. Check the relevant processes
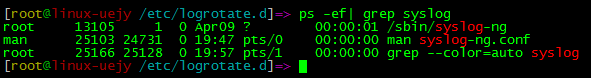
You can see the program / SBIN / syslog ng, which indicates that this program is used for log management under SUSE.
Find its configuration file / etc/syslog-ng/syslog-ng.conf for analysis. There is such a sentence in it:
#
# Global options.
#
options { long_hostnames(off); sync(0); perm(0640); group(1001); stats(3600); };Check to see that you can set related options. The details are as follows:
OPTIONS
You can specify several global options to syslog-ng in the options statement:
options { opt1; opt2; ... };
Where an option can be any of the following:
chain_hostnames(yes|no)
Enable or disable the chained hostname format.
long_hostnames(yes|no)
This is a deprecated alias for chain_hostnames().
keep_hostname(yes|no)
Specifies whether to trust hostname as it is included in the log message. If keep_hostname is yes and there is a hostname
in the message it is not touched, otherwise it is always rewritten based on the information where the message was received
from.
use_dns(yes|no)
Enable or disable DNS usage. syslog-ng blocks on DNS queries, so enabling DNS may lead to a Denial of Service attack. To
prevent DoS, protect your syslog-ng network endpoint with firewall rules, and make sure that all hosts, which may get to
syslog-ng is resolvable.
use_fqdn(yes|no)
Add Fully Qualified Domain Name instead of short hostname.
check_hostname(yes|no)
Enable or disable whether the hostname contains valid characters.
bad_hostname(regex)
A regexp which matches hostnames which should not be taken as such.
dns_cache(yes|no)
Enable or disable DNS cache usage.
dns_cache_expire(n)
Number of seconds while a successful lookup is cached.
dns_cache_expire_failed(n)
Number of seconds while a failed lookup is cached.
dns_cache_size(n)
Number of hostnames in the DNS cache.
create_dirs(yes|no)
Enable or disable directory creation for destination files.
dir_owner(uid)
User id.
dir_group(gid)
Group id.
dir_perm(perm)
Permission value (octal mask).
owner(uid)
User id for created files.
group(gid)
Group id for created files.
perm(perm)
Permission value for created files.
gc_busy_threshold(n)
Sets the threshold value for the garbage collector, when syslog-ng is busy. GC phase starts when the number of allocated
objects reach this number. Default: 3000.
gc_idle_threshold(n)
Sets the threshold value for the garbage collector, when syslog-ng is idle. GC phase starts when the number of allocated
objects reach this number. Default: 100.
log_fifo_size(n)
The number of lines fitting to the output queue. An output queue is present for all destinations.
log_msg_size(n)
Maximum length of message in bytes (NOTE: some syslogd implementations have a fixed limit of 1024 characters).
mark(n)
The number of seconds between two MARK lines. NOTE: not implemented yet.
stats(n)
The number of seconds between two STATS messages.
sync(n)
The number of lines buffered before written to file (can be overridden locally).
time_reap(n)
The time to wait before an idle destination file is closed.
time_reopen(n)
The time to wait before a died connection is reestablished.
use_time_recvd(yes|no)
This variable is used only for macro expansion where the meaning of the time specific macros depend on this setting, how-
ever as there are separate macros for referring to the received timestamp (R_ macros) and the log message timestamp (S_),
so using this value is not recommended.You can see that the three options of uid/gid/perm are exactly what we want.
Conclusion:
1. Modify the configuration file / etc/syslog-ng/syslog-ng.conf
hold
options { long_hostnames(off); sync(0); perm(0640); stats(3600); };
Modified to
options { long_hostnames(off); sync(0); perm(0640); group(1001); stats(3600); };
Note: in groupid is group logging:!:1001: corresponding ID number
2. Modify the configuration file / etc/logrotate.d/syslog
Put the line in / var/log/messages
create 640 root root
Modified to
create 640 root sa_logging
3. The results after restart are as follows: