Hello, guys. The last article - "look at my one code pass [series] from a technical perspective" simply analyzed the website information contained in the two-dimensional code after scanning one code pass. Today we continue.
This article is mainly to pave the way for the in-depth explanation of cache in the next issue and prepare the basic environment required for cache.
Two core entrances
The author saves "one code pass" on the mobile phone desktop, so it is very convenient to open one code pass. Generally, the steps to open one code pass are:
Alipay: Alipay home page -> One code pass (added to the home page) or: home page-> Search one code pass-> get into
Wechat: wechat -> find -> Applet ->Search one code pass
The above description: for programs with a large number of users, which are needed by almost everyone, [it should be very convenient to use]. From children to adults, they should be able to easily find their own "one code pass" and borrow the existing software(Huge user base),It can be popularized "overnight", which should be a very basic "product" thinking. So: Alipay and WeChat can enter one yard through the "small program".,For developers, these two applets need to be docked.
1) Applet
The essence of the "one code" entrance is: small program, that is, Alipay's small program (as for small programs, the author introduced it more, please Baidu). WeChat just provided an entrance, and finally jumped to my code interface or Alipay's small program interface.
In fact, if we are more careful, we can find this information as soon as the "code" goes online:
Payment applet portal

This shows that this is a small program for Alipay. Other information is basically understood through the news. It can be seen that the latest update is January 8, which is Saturday. It can be guessed that colleagues are working overtime.
Wechat applet portal

This figure is the information that can be viewed after entering the wechat applet portal, indicating that the source is: [wechat applet]. The author visited all the websites listed in [services provided by the following websites] and found the introduction of the previous blog: https://data.xa.gov.cn This website, as well as: Tencent maps, etc., others are test websites. The use of maps may need to collect action tracks, whether time and space intersect, etc., but the specific user interface has not been found in the small program.
Conclusion: the above information is obtained by us independently and spontaneously, not through "hindsight" of the news. We can feel some design ideas from it:
What form is the product developed? Is developing an App? Or a Web side? Or applet? Based on Alipay or WeChat? Based on one of them, what about the other?
"One code" is developed based on Alipay small program, WeChat small program made an entrance directly "chain" in the past. The development of small programs is very convenient. The development of APP is too heavy, and the development of Web side is not conducive to user access.
2) Entry mode
Click the applet icon, pull up the applet home page, click [my electronic code], and you can find that you enter a [H5 page]. We know that if it is a page in a native APP or applet, the page loading is very smooth, and we basically can't feel this "loading" process. From the second long loading progress bar, we can see that this interface is H5.

Of course, the most straightforward way is to grab the package and look at the interface. Because of the epidemic situation, the Type-C USB converter I bought is still on the way, so I can't brush the machine and install the system certificate to grab the package. However, I also saw some netizens grab the package and briefly share the interface information.
This will continue below.
Core interface
Although I can not catch a bag recently, I benefit from the official account of C and CPP programming.
Lu Xingmin knew that the connection of the last article would not be pasted. The author sent pictures
The interface for obtaining QR code data mentioned in the article is:
/person/app/refreshQRCode Specifically GET,still POST,The article did not mention that the author can grab the bag in the later stage.
That article is analyzed from the loaded static pictures. The author wants to make some guesses about the story behind some parameters of this interface:
{
"msg": "Operation succeeded",
"code": "0",
"data": {
"personName": "",
"code": "",
"logoFlag": "0",
"showTreeReason": "",
"healthStatus": "1",
"idCard": "",
"iconFlag": "",
"codeReason": ""
}
}
This is the information contained in the QR code returned from the back end. There are some familiar fields:
healthStatus This field naturally represents the "one code pass" color. Hypothesis 1-Green, 2-Yellow 3-Red. This field "has a big source", which is what "rules" the back end uses to determine what color the code is? It is learned from the news that the general rule is: "code according to the risk level and control measures of personnel: High risk personnel and personnel requiring centralized isolation are marked with red code, medium risk personnel and personnel requiring home isolation are marked with yellow code, and low risk personnel and personnel without control requirements are marked with green code " In short, there are two main factors: 1-Risk level of personnel 2-Control measures Risk level of personnel:For example, if a person's nucleic acid test is positive, its "code" should automatically turn red after the test results are obtained; If a person comes from a "high-risk" area, his code should also automatically turn red; Control measures: if A Upgrade the urban area to a high-risk area, or B If a case is found in the community and the whole community needs centralized isolation, all the "codes" of the personnel in the region or the community should turn red in time; If C The district was originally normal, but later the control strength was adjusted and upgraded to "medium risk", then C The "code" of personnel in the area should turn yellow in time. From this point of view, "code" is too important. Once the epidemic occurs, if the "code" can change color accurately and in time, it is very important to block the transmission chain. So let's imagine the logic behind "code discoloration": [1 The risk level of personnel] shall be related to the nucleic acid test results. Suppose that 10 million people, each nucleic acid 7 times, produce at least 70 million nucleic acid data records, Count the previous records(Although not displayed, the data shall be retained in the background),It's easy to exceed 100 million. Suppose the database is MySQL,If there are no warehouses or tables, the worst case is single table storage, It will be very difficult to query single table data at the "100 million" level. This is only the data of nucleic acid, not including personnel information, travel information, regional control information, etc; Suppose a person travels to Shanghai, goes to Zhejiang on the way, then returns to Xi'an, and finally returns to XX village. When I went to Shanghai, everything was normal there; During his stay in Zhejiang, the location was upgraded to a "medium risk" area, Then the person's "code" should be "yellow", which should be based on his geographical location information. Therefore, the background should record everyone's geographical location and moving track, so that when the person enters a place, he can calculate the color of the person's "code" in real time or asynchronously according to these "code assignment" rules. We often hear "intersection of time and space", which refers to people who intersect with cases in time and space. How to judge whether "I" intersects with others in time and space? It is absolutely impossible to rely on your own head to recall. Individuals may hide out of concern, so you need to collect everyone's travel data. This data may come from "12306", from "Ctrip" and from major ticket buying websites, that is, there will be a whole "travel network" to record all your tracks; Then, whether the time and space are crossed or not, it is necessary to associate all the data of relevant personnel together. It is simply understood as operations such as intersection, union and collection between sets, and finally "calculate" whether it is possible for you to "connect" with virus carriers, and then: call the SMS interface of the three operators to send you prompt SMS; The background asynchronous task refreshes your one yard pass. When you enter the village, the villagers ask you to display the code. You find that it was still yellow when you were in Zhejiang. Why is it red now? So you need isolation. Therefore, this "code" timely blocks the possibility that you may spread to a village. That's not enough [2]-Control measures] impact on the "code" color. Once the epidemic situation in a certain area tends to rise, a village, community or province is constantly adjusting the control measures. After each policy adjustment, the background should be able to calculate the "code" color of people in the corresponding area in time according to the control policy, The timing and frequency of calculation should be able to quickly respond to the requirements of the policy; For the background algorithm, the requirements for real-time calculation and data volume are very high. The author really hopes to describe an algorithm from the code level. This will be inspired later. Let's talk about it in detail. Imagine that there are a lot of data in a province. The state also needs to macro control all the data. The amount of data is really "massive".
code
This field is likely to be https://data.xa.gov.cn/ptrace/view/login.html?code=634588JFDAJFAKFAJF the code carried by this connection. As for the specific meaning of this code, we will not delve into it.
codeReason
showTreeReason
this codeReason It may be the explanation of "code" color. For example, if a person's code is "red", this field may briefly and clearly explain why the person is "red". Because all calculations are completed in the background, is the calculation result correct? What data are used in the calculation? Only programmers can make it clear that the calculation logic cannot be checked in a short time. Therefore, the basis of each "decision" should be recorded in the calculation process, and then the cached calculation process data should be returned when necessary.
showTreeReason ,It literally means a "tree" cause, and it is speculated that it may be a cause "chain". It is the display data of such a process of layer by layer analysis and layer by layer calculation.
The above can show that:
1. There are many things to do behind the interface, and big data is needed
2. The amount of data is beyond imagination
3. The algorithm is complex and requires high and low real-time performance
4. This query interface is called frequently
Examples of scenarios with frequent calls:
1) Frequent calls during rush hours.
From 8 to 9.30 every day, all office workers need to show one yard pass, which means that the back-end calculation results should be out before 8 o'clock, and then cache the calculation results. Only when people arrive at the company to show the code to the guard uncle can they be very smooth.
2) Call frequently when centralizing
Use cache
The above "conjecture" is more "false empty". I have also seen some videos analyzing the technology behind one code pass these days. The author wants to start from one point and express it intuitively and concisely. After thinking about it, I still start with [cache].
The author has built a set of environment:
front end Vue,back-end SpringBoot,Front and rear end separation. Simulate and write an interface to obtain "one code communication", and then simply add a cache to this interface and deploy it in Alibaba ECS upper. Front end Nginx,use Docker deploy Nginx Back end pass jar Deployment mode, jdk1.8 Redis The deployment is a single machine, using Docker Deployment.
The effects are as follows:
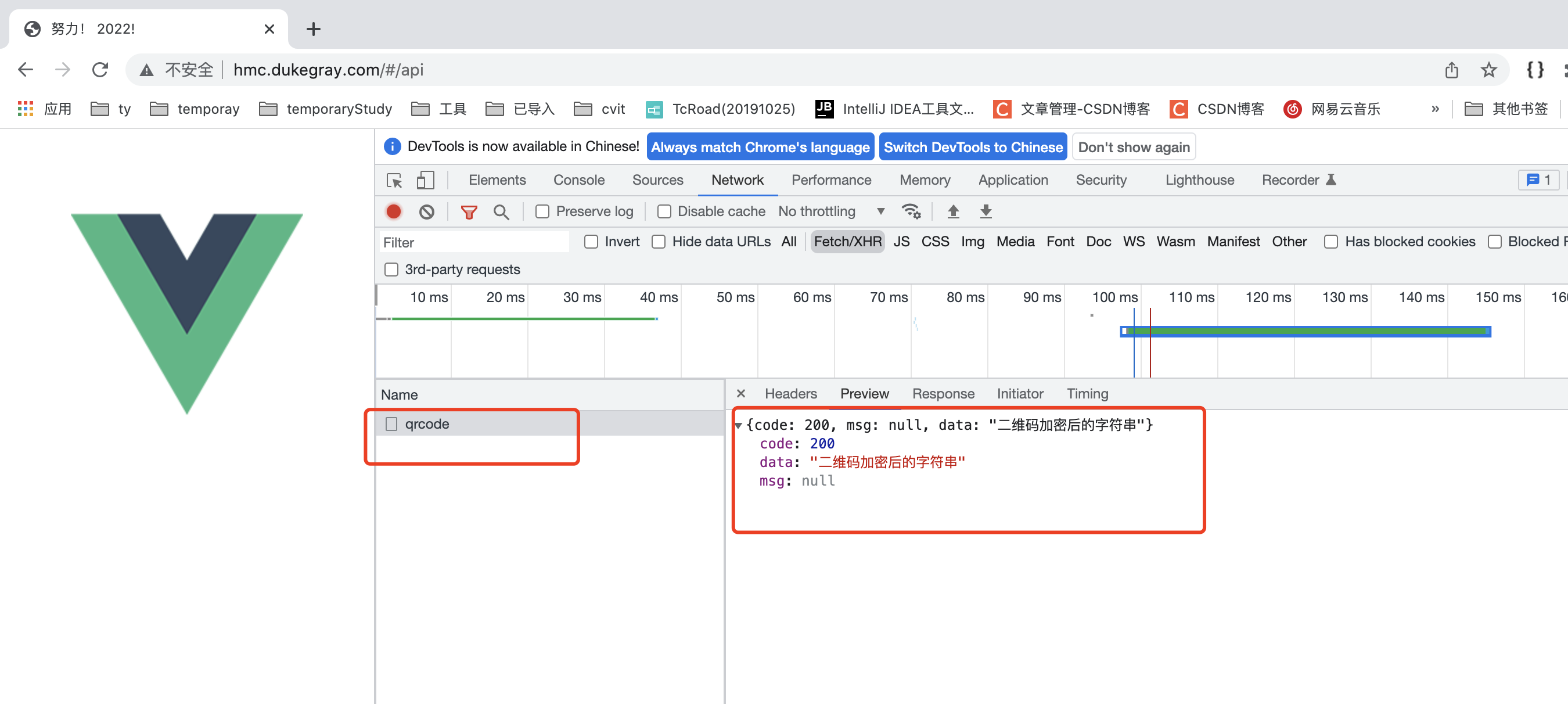
Backend Controller layer code:
/**
* Load QR code
*
* @return
*/
@GetMapping("")
@Cacheable(value = {"qr_code"})
public String getMyQrCode() {
return qrcodeService.getQrcode();
}

The effect after caching is as follows:

With such an environment, it is very convenient to add anything in the later stage, and the "stage" has been set up.
Well, that's all for today. Here I would like to thank the readers for their comments. Your comments have inspired me a little.
In the next issue, we intend to formally start from the perspective of caching, and explore and analyze how to deal with high concurrency step by step.
Goodbye!