Why use network programming
When you write two python Documents, such as a.py and b.py,Run separately and it will run well. However, if you want to transfer data between the two programs, you need to create a file and a.py Write what you want to pass to a file, and then b.py Just read from this file.
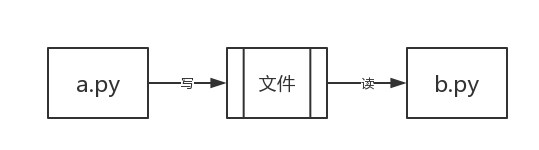
But when a.py and b.py What should I do on different computers? A similar mechanism is the computer network disk, qq wait. We can chat with others on our computer and upload and download content to the online disk on our computer. These are two programs communicating.
Software development architecture
We understand that the application of copper whiskers between the two procedures can be roughly divided into two types:
The first: QQ, wechat, online disk, Youku, etc. are desktop applications that need to be installed
The second web class: Baidu, Zhihu, blog Park and other applications that can be accessed directly by browser
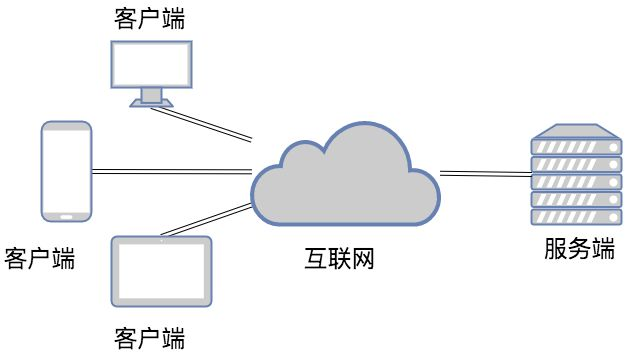
1.C/S architecture
c/s framework c:client Client architecture s:server Server architecture """ Treat the client as a customer who goes to the store to consume Regard the server as a storefront providing services eg:Various mobile phones app It is the client of major software Three characteristics of the server: 1.24 Service is provided 24 hours a day(monitor) 2.changeless IP address 3.Capable of serving multiple users(High concurrency),Number of users at the same time app """
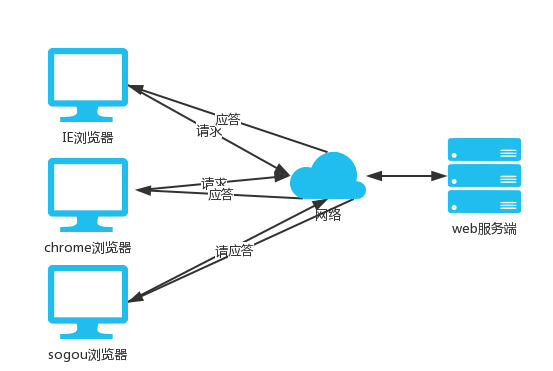
2.B/S architecture
b/s framework b:browser Browser side s:server Server side """ The browser acts as the client of each server Essence: bs Architecture is essentially the same cs framework """
In fact, Browser is also a kind of Client, but this Client does not need you to install many applications. It only needs to request the relevant resources (web resources) of the server through HTTP on the Browser, and the Client Browser can add, delete, modify and check
Network basis of theoretical knowledge
Network programming actually studies the data communication between programs History of remote data transmission(civil) 1.Wired telephone --> Telephone line interconnection 2.wireless telephone --> Signal transmitter 3.Big ass computer --> Network cable 4.Notebook computer --> network card ... summary: The premise of remote data interaction must be physical link media In addition to physical connection media, there should also be something that can ensure barrier free interaction with each other(standard) OSI Seven layer agreement
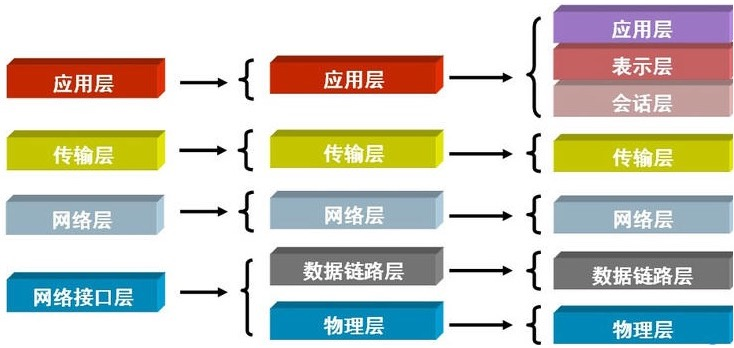
OSI layer 7 protocol
# All computers must have these seven layers application layer ^ Presentation layer | Session layer | Transport layer | network layer | data link layer | Physical connection layer |
# The development level can be summarized into five layers application layer Presentation layer Session layer Transport layer network layer data link layer Physical connection layer
Bottom up research: function Physical connection layer: provides a physical connection interface and physical devices(Network cable, network card...) Data link layer: binary data transmission 1.Specifies the grouping mode of electrical signals
Hardware
2.Ethernet protocol
It stipulates that the computer must have a network card, and there must be a fixed string of numbers on the network card
(12 Hexadecimal digits: the first six digits of the manufacturer's number and the last six digits of the assembly line number)
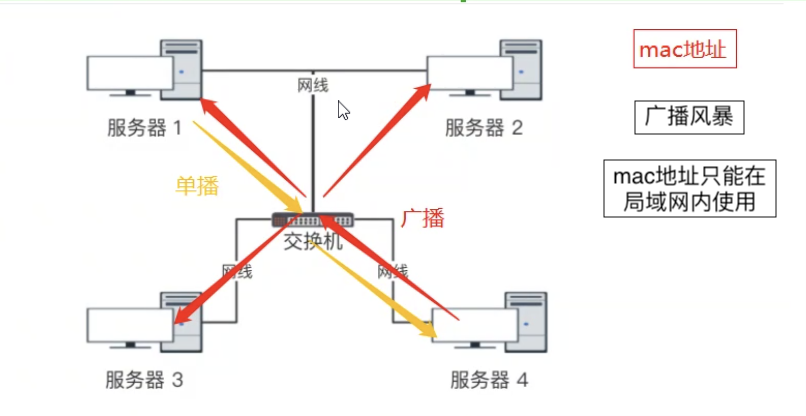
The above numbers are also called computer numbers mac address(Similar to ID number)
Common hardware
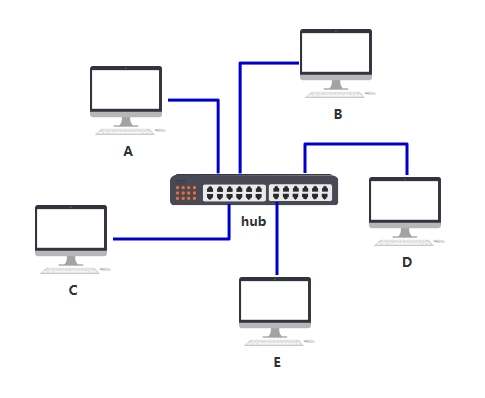
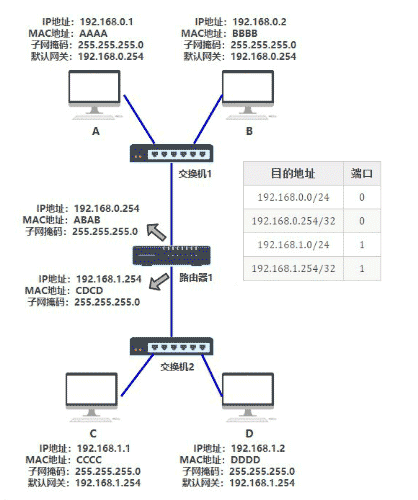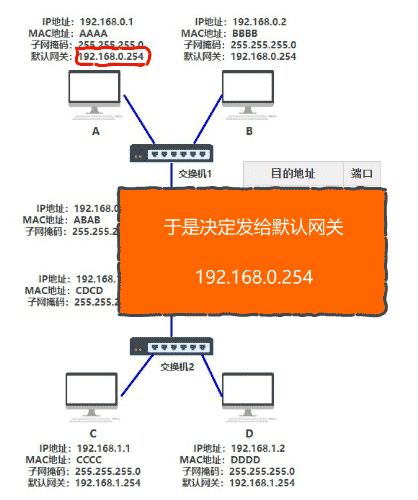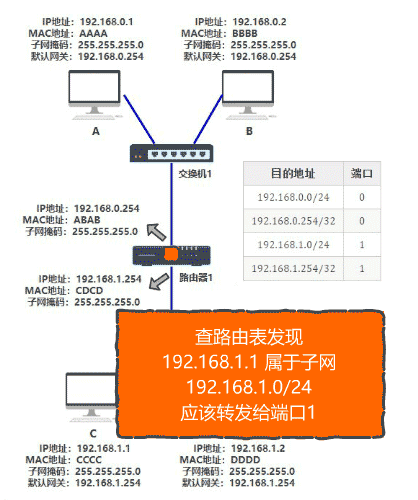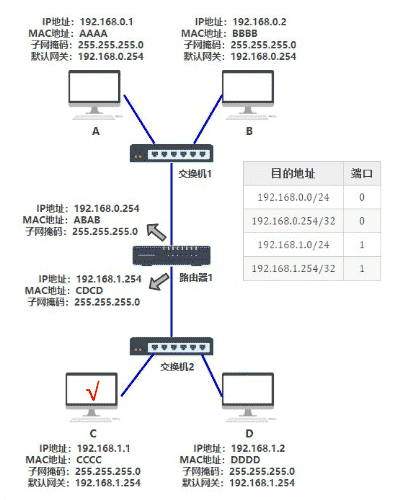
Switch: All computers connected to the machine can be interconnected with each other LAN: A network of switches in an area internet: It can be simply understood that multiple LANs are interconnected with each other """ be based on mac Address data transmission 1.Broadcast storm 2.mac Address cannot be transferred across LAN """
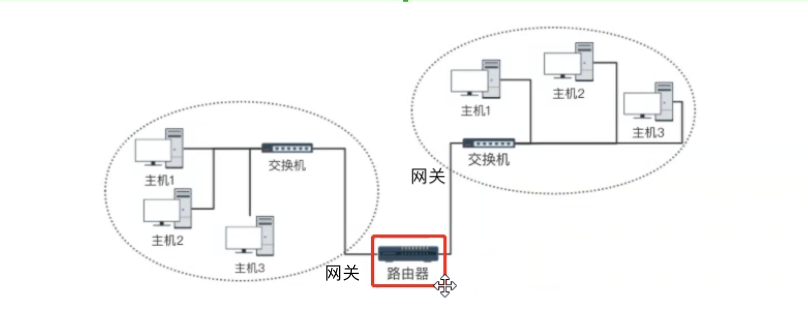
Router: it can link multiple LAN bin to realize data transmission between LANs
Go to OSI layer 7
network layer
IP Protocol: it stipulates that all computers connected to the Internet must have one IP Address for unique identification(internet) Two versions: IPV4: dotted decimal Minimum 0.0.0.0 Maximum 255.255.255.255 IPV6: Can represent every grain of sand on earth IP It is divided into two categories; IP The protocol enables a computer to have a unique identity Public network IP Private network IP Public network IP Need to spend money to buy and apply Private network IP Built in but not accessible over the Internet
ARP Protocol
Origin of arp protocol: computer communication basically depends on roar, that is, broadcast. All upper packets should be encapsulated with an Ethernet head at the end, and then sent through Ethernet protocol.
Communication is based on mac broadcasting. It is easy for a computer to obtain its own mac when contracting. How to obtain the mac of the target host needs to be through arp protocol
arp agreement Address resolution protocol; Network based request will IP Address translation to mac address
If you (A) don't know the MAC address of your partner B at this time
The answer is very simple. In the network layer, I need to find the MAC address corresponding to the IP address, that is, in some way, find the MAC address BBBB corresponding to 192.168.0.2.
This method is the arp protocol. At the same time, computers A and B will also have an arp cache table, which records the corresponding relationship between IP and MAC addresses.
| IP address | Mac address |
|---|---|
| 192.168.15.31 | BBBB |
At the beginning, this table is empty. In order to know the MAC address of computer B (192.168.15.31), computer A will broadcast an arp request. After receiving the request, B will bring its own MAC address to A. At this point, A updates its arp table.
In this way, by continuously broadcasting arp requests, all computers will update the arp cache table completely.
Transport layer
TCP agreement UDP agreement
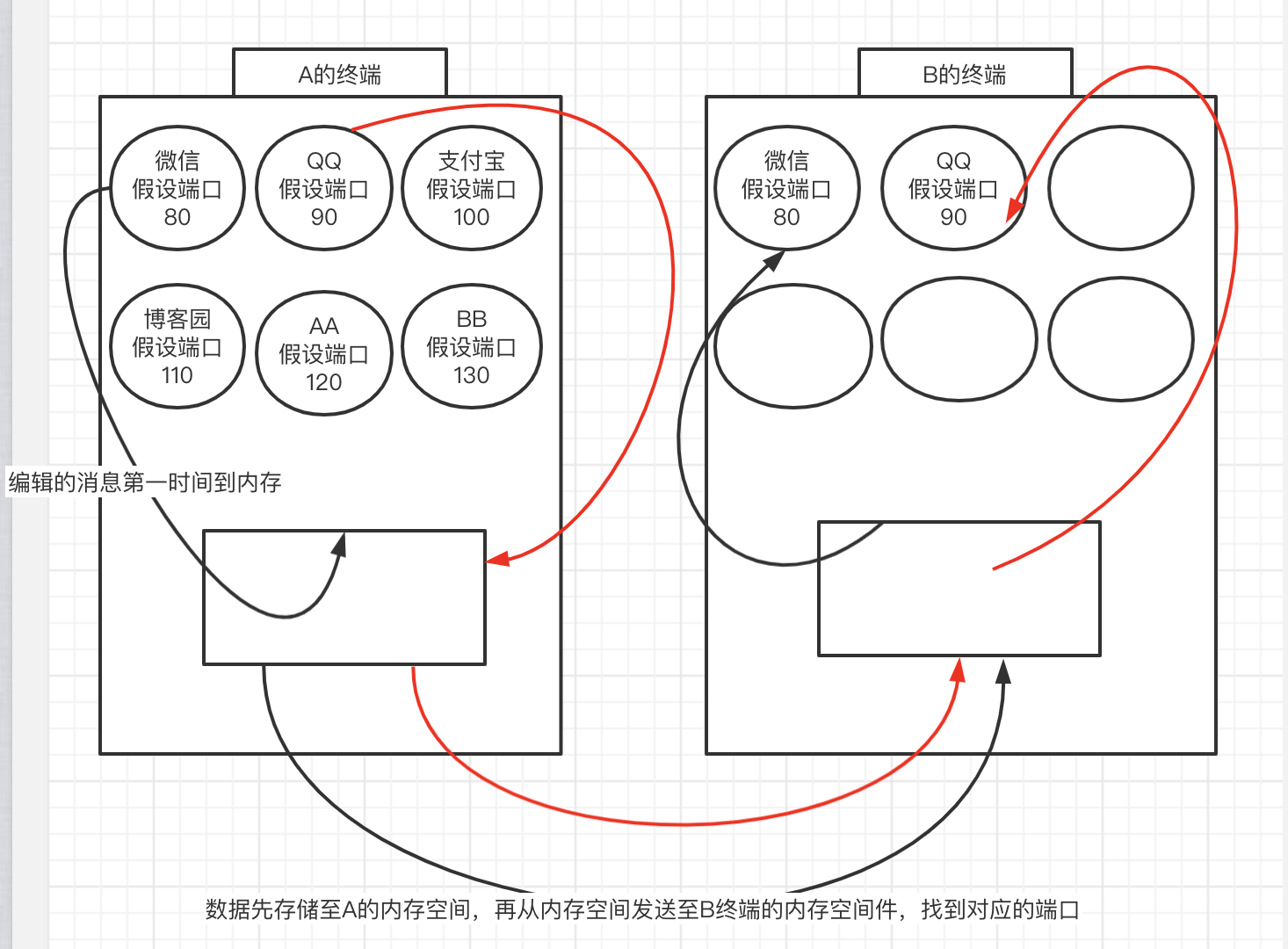
How does one program find another program on the network
Firstly, the program must be started. Secondly, there must be the address of the machine. For example, our address location is probably the country \ province \ city \ District \ street \ building \ house number.
Then, each networked machine also has its own address on the network. How should its address be expressed?
Port protocol: Range: 0~65535 Properties: dynamic assignment ' When running wechat for the first time, the system randomly sends a port number, such as 2022 Then close wechat and restart, and the system takes a random port number ' Basic usage principle of port number: 0-1024 The port number that the system needs to use by default 1024-8000 Common software port number(The implication is that those who develop their own software in the future should avoid the above two categories) # Port: an application that can uniquely identify the cloud running on a computer """ The port number cannot be repeated at the same time on the same computer """ Summary: ip + port It can uniquely identify a running application on a computer connected to the Internet in the world
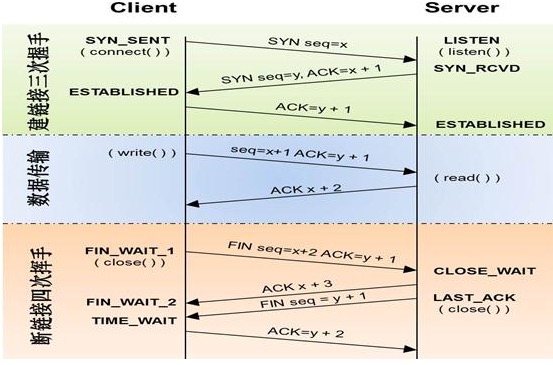
TCP protocol
Also known as streaming protocol and reliable protocol Three handshakes to establish connection Important state listen Listening station: wait for the other party to send a request sysn_rcv Status: busy replying to confirm establishment request # Flood attack: the server receives a large number of requests to establish links at the same time Four waves to disconnect Cannot be merged into three times During the vacuum period, both parties may transmit data to each other
Three handshakes and four waves
UDP protocol
Alias: unreliable protocol There is no channel concept for data transmission, and it doesn't matter if it is sent out """ TCP The agreement is equivalent to making a phone call, you and me UDP The protocol is equivalent to sending text messages, which can be viewed at any time """
application layer
They are all self-defined protocol standards, which can be followed or not followed HTPP agreement FTP agreement
Based on the boss blog > https://www.cnblogs.com/flashsun/p/14266148.html