Shared server
Provide file sharing services through the network, and provide file download and upload
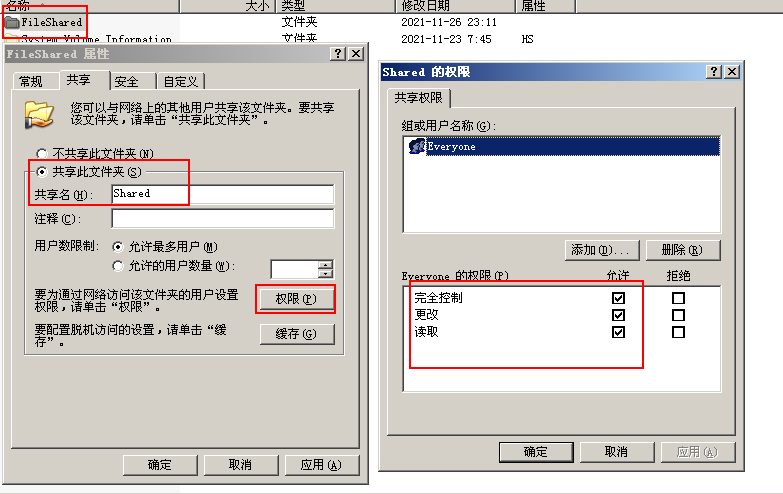
- Set up a shared folder on Win2003
- Enter the win2003IP address in Win+R on the Win7 virtual machine
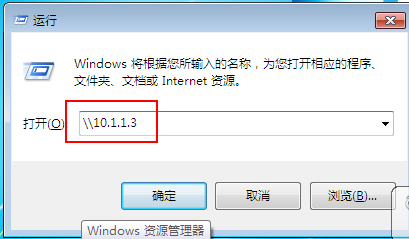
- Click OK and enter the user name and password. After successful verification, the shared folder will be displayed
Permissions for shared folders
- Local login, only affected by NTFS permissions
- Remote login will be affected by sharing and NTFS permissions, and the intersection will be taken
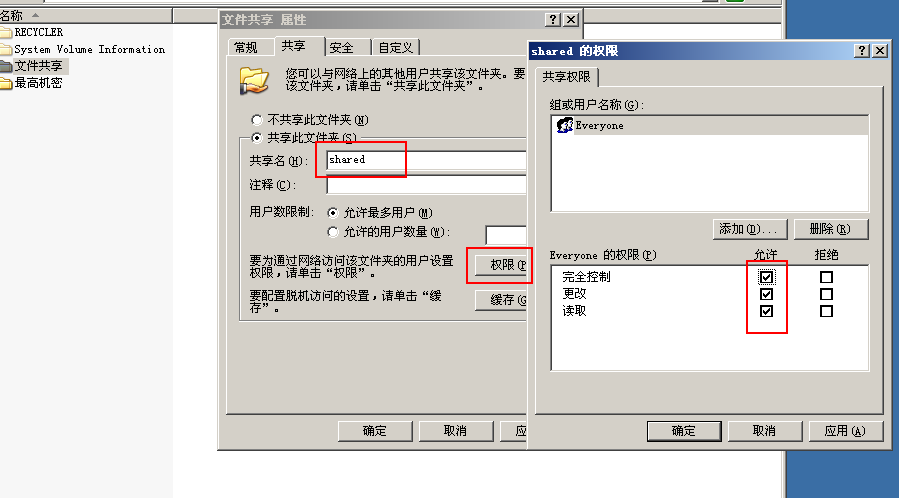
- Set the sharing permission, which is fully controlled by Everyone, and then set the specific permission requirements in NTFS permission
Case:
Create a shared folder and set two users edison and dizzy. edison has UpLoad permission to the UpLoad folder under the shared folder, Download permission to the software folder, and dizzy has all control permissions to the folder.
realization
-
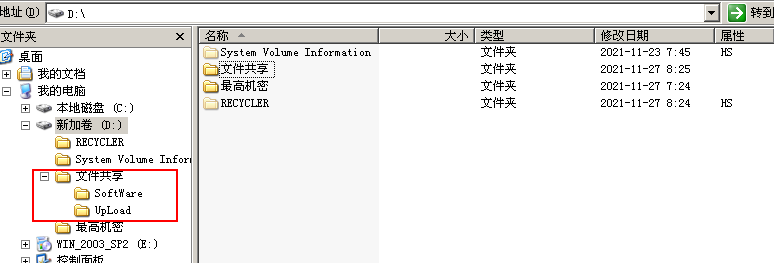
Create a "file share" folder on the win2003 virtual machine, and create SoftWare and UpLoad folders under the "file share" folder
-
Set the file share folder as a shared folder
-
Modify SoftWare and UpLoad folder permissions
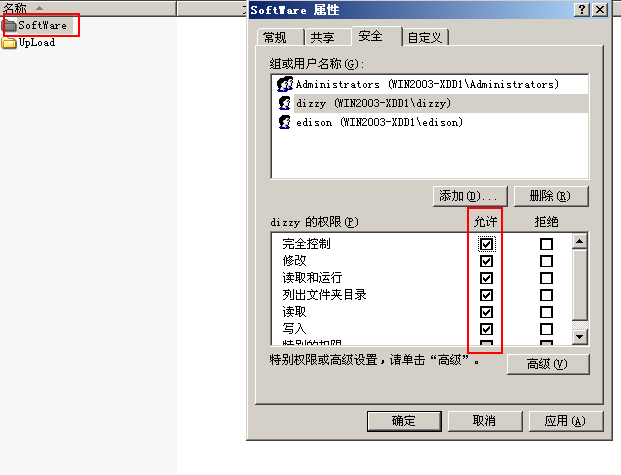
Set the permission of edison user to read and run the folder, list the folder directory and read the permission
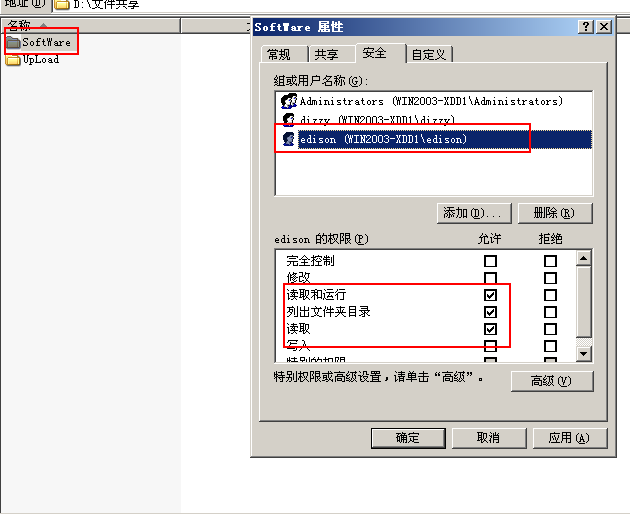
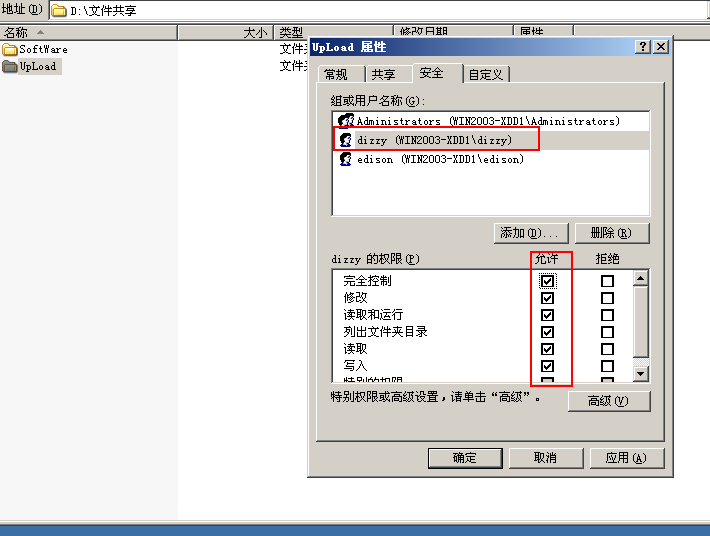
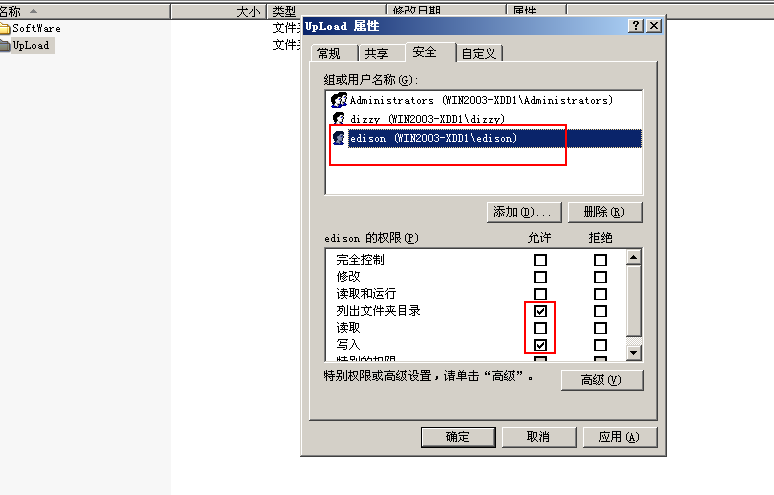
Set the edison user's permissions on folders to list folder directories and write
Hide sharing
- Create a hidden shared folder on the win2003 virtual machine, that is, add it after the share name$
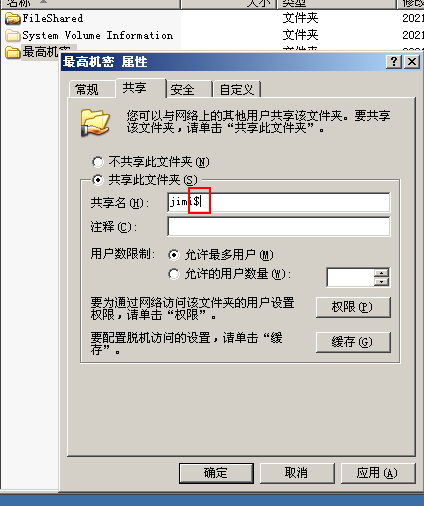
- Enter win2003IP on the win7 virtual machine, and then enter the share name $
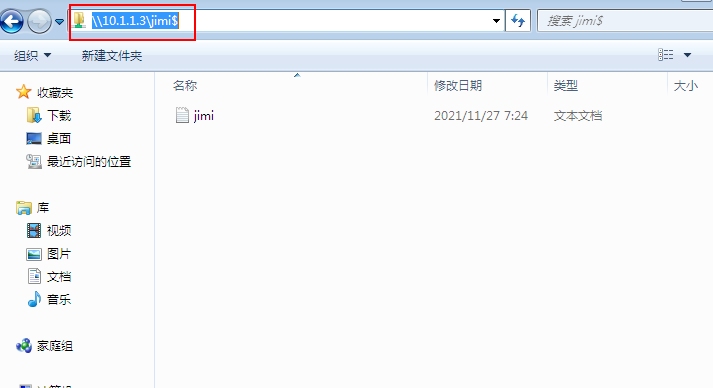
Share command
C:\Documents and Settings\Administrator>net share Share name resources notes ------------------------------------------------------------------------------- jimi$ D:\Top secret #Empty connection IPC$ long-range IPC ADMIN$ C:\WINDOWS Remote management D$ D:\ Default share C$ C:\ Default share Shared D:\FileShared Command completed successfully. C:\Documents and Settings\Administrator>net share Shared /del Shared Has been deleted. C:\Documents and Settings\Administrator>net share jimi$ /del User opened jimi$ Continue this operation will force the file to close. Do you want to continue this operation? (Y/N) [N]: y jimi$ Has been deleted. C:\Documents and Settings\Administrator>net share Share name resources notes ------------------------------------------------------------------------------- IPC$ long-range IPC ADMIN$ C:\WINDOWS Remote management D$ D:\ Default share C$ C:\ Default share Command completed successfully. #To delete a share, C $and D $cannot be deleted by using the command. The deletion is temporary and will become invalid after restart C:\Documents and Settings\Administrator>net share c$ /del c$ Has been deleted. C:\Documents and Settings\Administrator>net share d$ /del d$ Has been deleted. C:\Documents and Settings\Administrator>net share ipc$ /del A system error occurred 5. Access denied. #Create share C:\Documents and Settings\Administrator>net share c$=c: c$ Sharing succeeded. C:\Documents and Settings\Administrator>net share Share name resources notes ------------------------------------------------------------------------------ IPC$ long-range IPC ADMIN$ C:\WINDOWS Remote management c$ c:\ Default share
Automatic generation of hidden sharing in shielding system
- Win+R opens the run dialog box, and enter regedit to open the registry editor
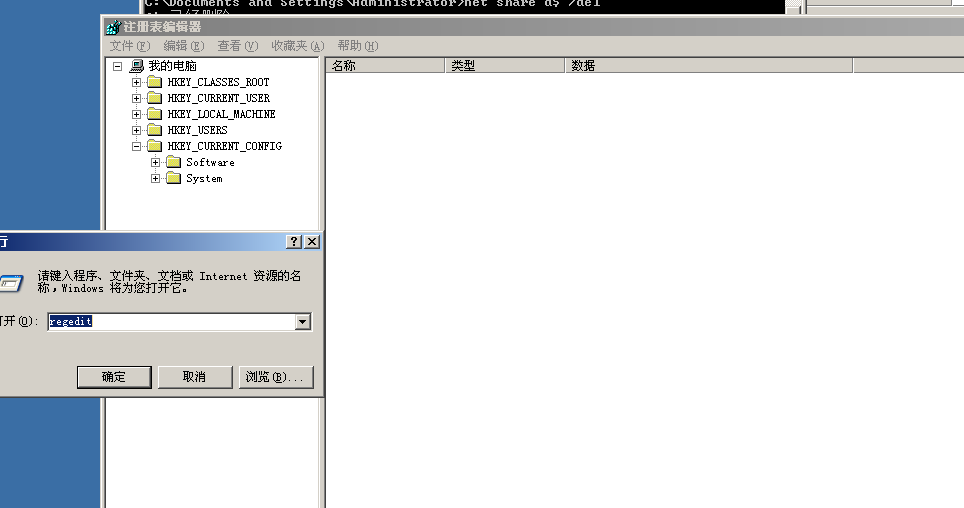
- Locate shared registry location
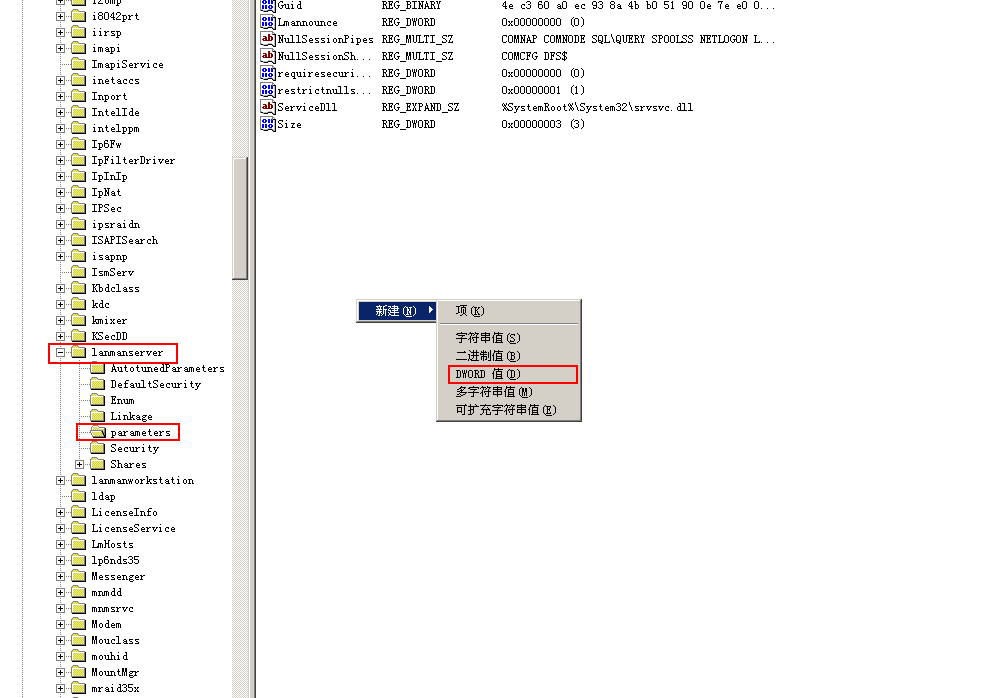
HEKY_LOCAL_MACHINE\System\CurrentControlSet\Services\LanmanServer\Parameters
Right click to create a new DWORD value. The name is AutoShareServer and the value is 0

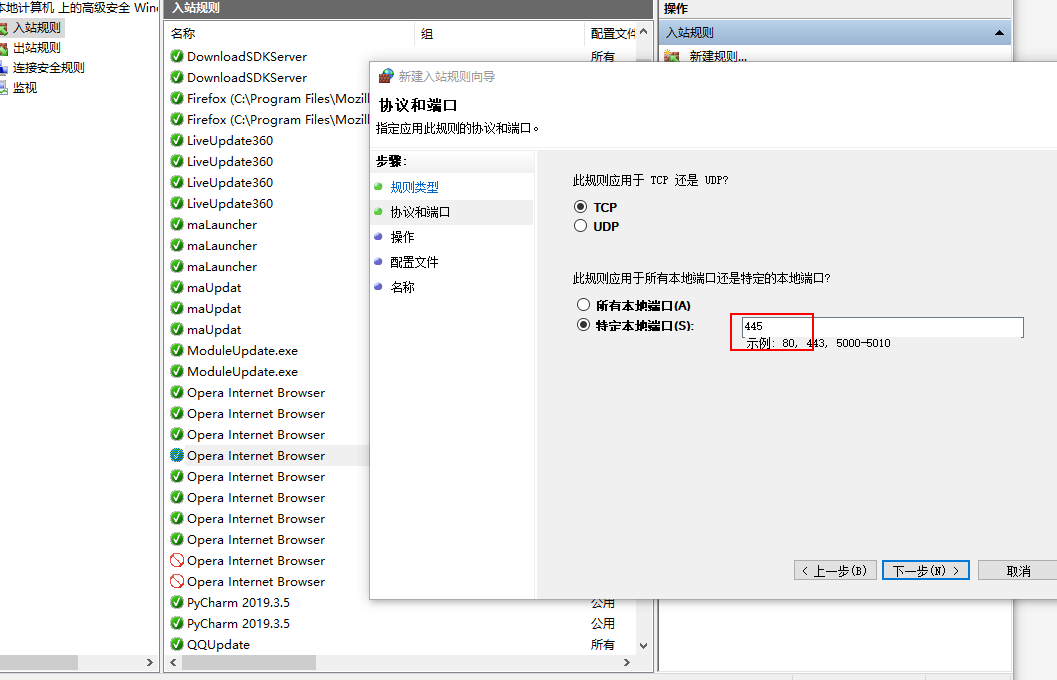
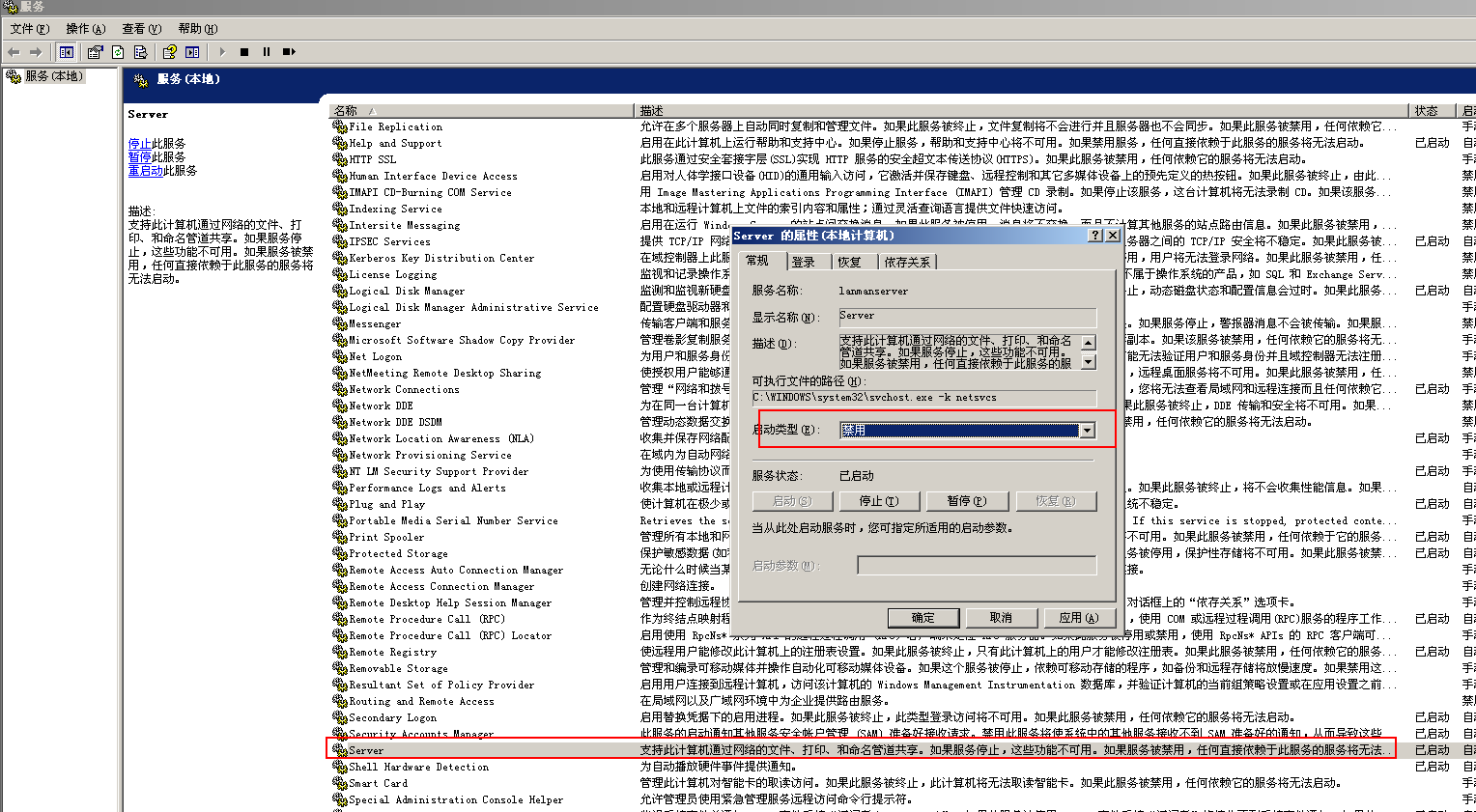
Turn off shared services (Port 445)
Close port 445 to shield the incoming virus (such as blackmail virus)
- win+r opens the run dialog box, and enter services.msc to open the service window
- Locate the Server and disable the service
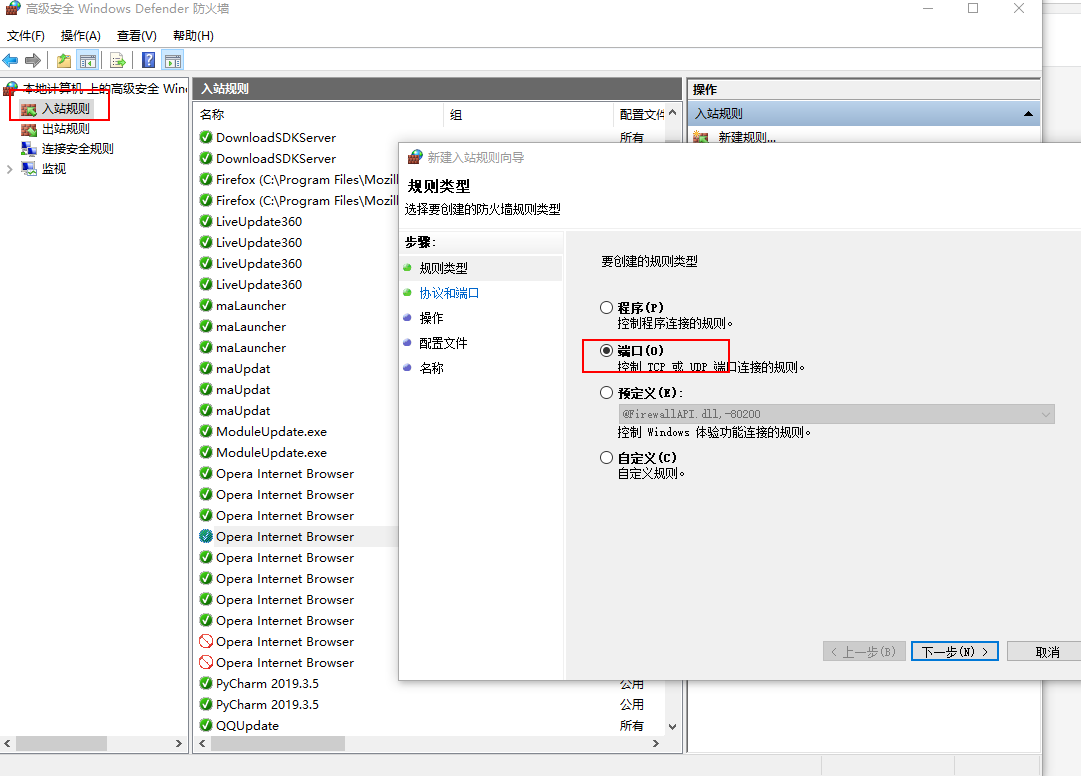
- Configure firewall - inbound rules (only available for win7, win2008 and above systems)
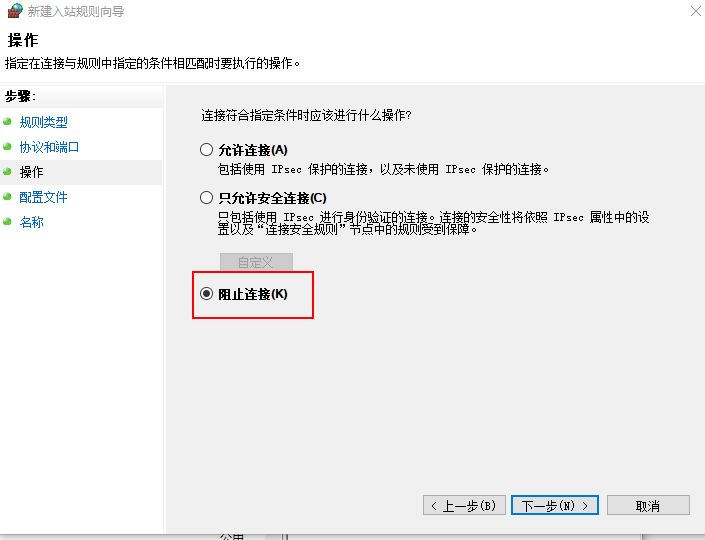
Disable 445 access by changing firewall inbound rules
- Take win10 as an example, open the control panel, control panel \ all control panel items \ Windows Defender firewall
- Click Advanced settings on the left
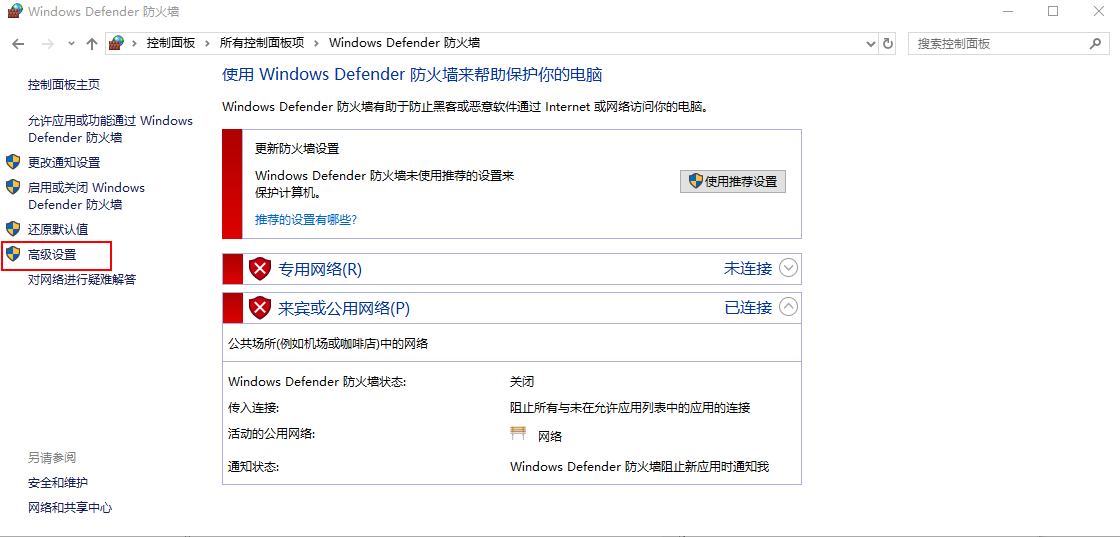
- Right click the inbound rule to create a new inbound rule