1. Implementing https encryption
We know that now is the age of https, and almost every excellent website has launched https. After opening the HTTPS encrypted access, login to your website, browser address bar will appear a green lock, which is the use of hypertext transfer security protocol (HTTPS), HTTP channel for security purposes, in short, HTTP security version.
https is composed of two parts: HTTP+SSL/TLS. On the basis of http, a layer of encryption information module is added. The information insertion of the server and client will be encrypted by TLS, and the data transmitted are encrypted data.
In order to solve these shortcomings of HTTP protocol, we need to use another protocol: HTTPS. In order to ensure the security of data transmission, HTTPS adds the SSL protocol on the basis of http, which authenticates by certificate and encrypts the communication between browser and server.
SSL certificate is a kind of digital certificate, which uses Secure Socket Layer protocol to establish a secure channel between browser and web server, so as to realize the encrypted transmission of data information between client and server, ensure the security of information transmitted by both sides, and can not be eavesdropped by third parties, and users can use server certificate. The Book verifies whether the website visited is authentic and reliable.
The difference between encrypted HTTPS and HTTP:
- HTTP protocol is used to transfer information between web browser and web server. HTTP protocol sends content in plaintext without providing encrypted data in any way. If an attacker intercepts the transmission message between web browser and web server, he can read the information directly. Therefore, htt P protocol is not suitable for transmitting sensitive information.
The experiment is as follows:
Step 1: 1. Close the nginx service and recompile it (mainly to add ssl modules)
[root@nodel1 conf]# systemctl stop nginx [root@nodel1 conf]# cd /mnt [root@nodel1 mnt]# ls [root@nodel1 mnt]# cd nginx-1.17.1/ [root@nodel1 nginx-1.17.1]# make clean [root@nodel1 nginx-1.17.1]# yum install openssl-devel -y #When encrypting is used in the compilation process, you need to install this

[root@nodel1 nginx-1.17.1]# ./configure --prefix=/usr/local/nginx --with-http_realip_module --with-http_image_filter_module=dynamic --with-http_ssl_module [root@nodel1 nginx-1.17.1]# make

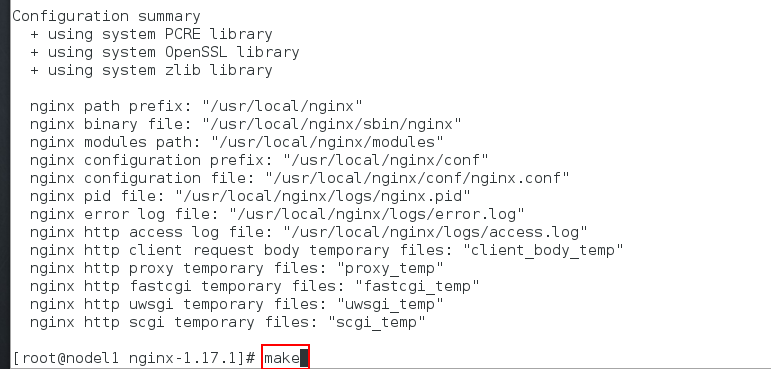
Replace the previous binary file and place the image module in the modules directory again
[root@nodel1 nginx-1.17.1]# cd objs/ [root@nodel1 objs]# cp nginx -f /usr/local/nginx/sbin/nginx [root@nodel1 objs]# ls [root@nodel1 objs]# cp ngx_http_image_filter_module.so /usr/local/nginx/modules
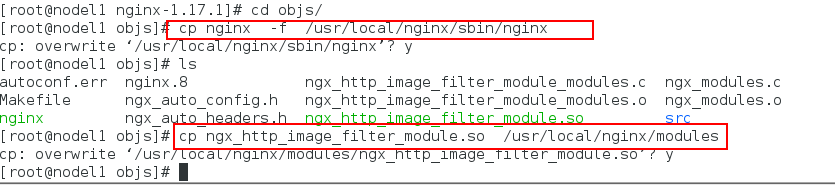
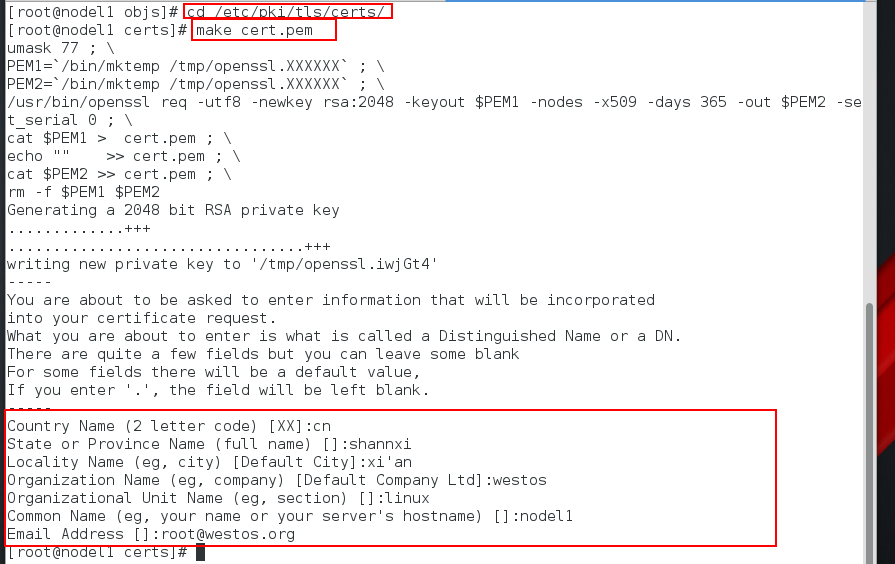
Step 2: Generate certificates under / etc/pki/tls/certs / and place them in the directory of nginx configuration files
[root@nodel1 objs]# cd /etc/pki/tls/certs/ [root@nodel1 certs]# make cert.pem #Generate certificates Country Name (2 letter code) [XX]:cn # Country Code, China Imports CN State or Province Name (full name) []:shannxi #province Locality Name (eg, city) [Default City]:xi'an #city Organization Name (eg, company) [Default Company Ltd]:westos #Company English Name Organizational Unit Name (eg, section) []:linux #Name of organization Common Name (eg, your name or your server's hostname) []:nodel1 #Host name or your name Email Address []:root@westos.org #E-mail address [root@nodel1 certs]# cp cert.pem /usr/local/nginx/conf/ # Place certificates in the directory of nginx configuration files

Step 3: Write the configuration file and open the nginx service (Note: https encryption is not set at this time, just ordinary http)
[root@nodel1 objs]# cd /usr/local/nginx/conf/
[root@nodel1 conf]# vim nginx.conf
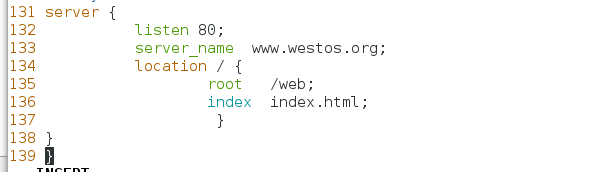
131 server {
132 listen 80;
133 server_name www.westos.org;
134 location / {
135 root /web;
136 index index.html;
137 }
138 }
139 }
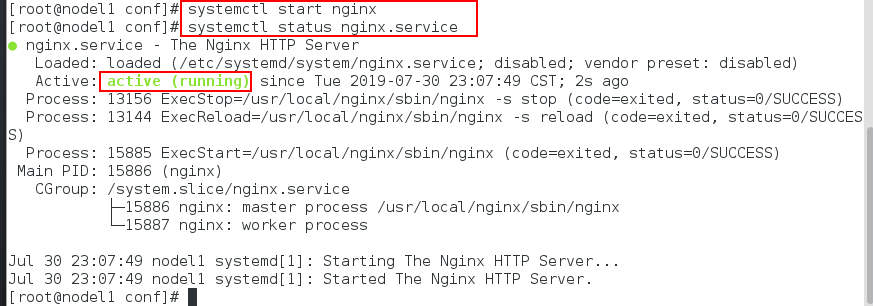
[root@nodel1 conf]# systemctl start nginx
[root@nodel1 conf]# systemctl status nginx.service
Step 4: Configure Resolve and Edit Default Publishing Files in nodel1
vim /etc/hosts 172.25.15.1 nodel1 www.westos.org
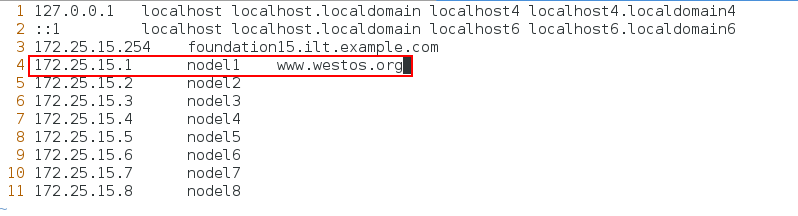
[root@nodel1 conf]# cd [root@nodel1 ~]# mkdir /web [root@nodel1 ~]# cd /web [root@nodel1 web]# vim index.html [root@nodel1 web]# cat index.html //The contents are as follows: www.westos.org
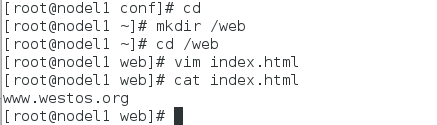
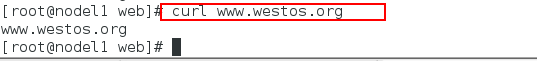
Step 5: Test and re-edit the nginx configuration file (https at this point)
Test: At this point, if you test the browser, there will be no green lock, because there is no https encryption set.
Write the nginx configuration file again, then check if there are any grammar errors and restart the service so that it can achieve HTTP - > HTTPS
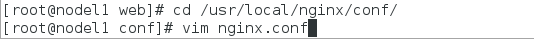
[root@nodel1 web]# cd /usr/local/nginx/conf/
[root@nodel1 conf]# vim nginx.conf
111 # HTTPS server
112
113 server {
114 listen 443 ssl; #ssl port
115 server_name www.westos.org;
116
117 ssl_certificate cert.pem;
118 ssl_certificate_key cert.pem;
119
120 ssl_session_cache shared:SSL:1m;
121 ssl_session_timeout 5m;
122
123 ssl_ciphers HIGH:!aNULL:!MD5;
124 ssl_prefer_server_ciphers on;
125
126 location / {
127 root /web;
128 index index.html index.htm;
129 }
130 }
131
132 server {
133 listen 80;
134 server_name www.westos.org;
135 rewrite ^/(.*)$ https://www.westos.org/;
136
137 location / {
138 root /web;
139 index index.html;
140 }
141 }
142 }
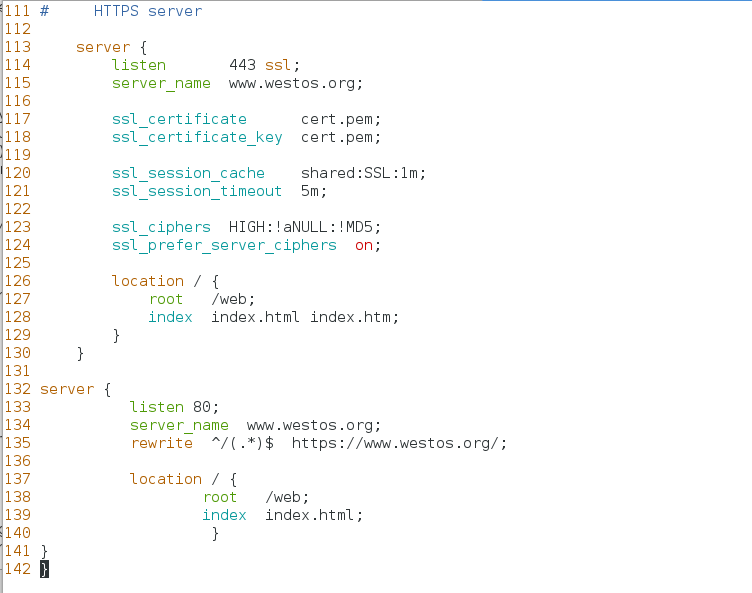
[root@nodel1 conf]# cd - /usr/local/nginx/sbin [root@nodel1 sbin]# ./nginx -t #Check for grammatical errors [root@nodel1 sbin]# systemctl reload nginx
Step 6: Add domain name resolution to the real machine and access it in the browser
[root@foundation15 ~]# vim /etc/hosts 172.25.15.1 nodel1 www.westos.org
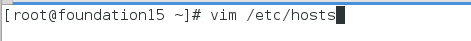

After entering www.westos.org in the browse, https: will be automatically completed and added certificates will be displayed.
Check the certificate information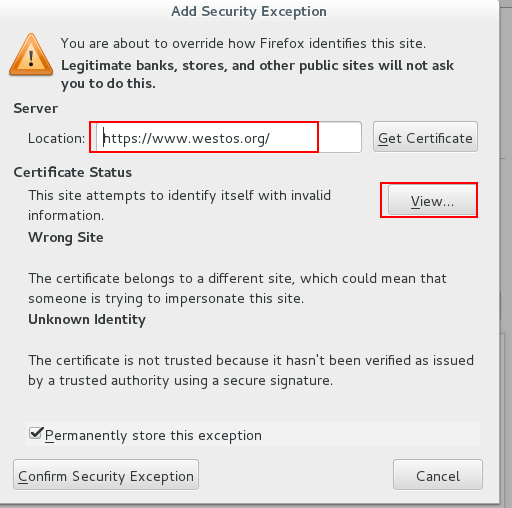

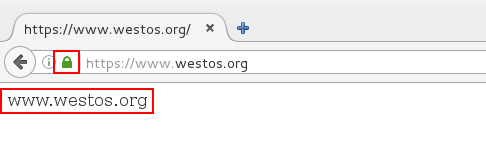
2. Redirection
First: redirect to specific files
Premises:
(1) redirect www.westos.org to https://www.westos.org (the above experiment has been completed and expanded here)
We want to redirect to specific documents. The questions are as follows:
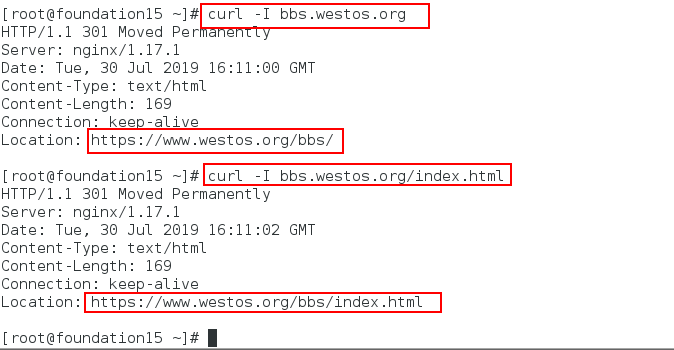
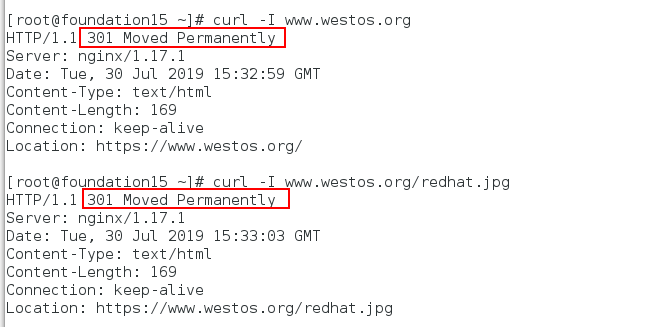
Visit www.westos.org on a physical machine The HTTP status code displayed is 302 (302 for temporary redirection and 301 for permanent redirection), and can be successfully redirected to https://www.westos.org.
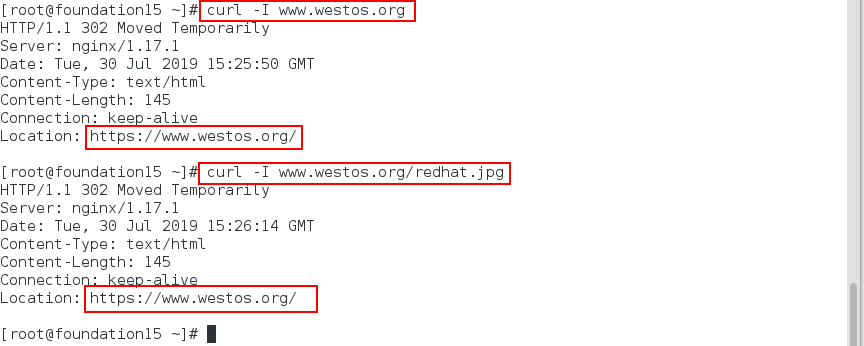
The experimental steps are as follows:
[root@nodel1 sbin]# cd -
/usr/local/nginx/conf
[root@nodel1 conf]# vim nginx.conf
132 server {
133 listen 80;
134 server_name www.westos.org;
135 rewrite ^/(.*)$ https://www.westos.org/$1;
[root@nodel1 conf]# systemctl reload nginx



At this point, we can see that the temporary redirection is 302. If we want to set the temporary redirection to permanent redirection, we need to do the following.
[root@nodel1 conf]# vim nginx.conf
132 server {
133 listen 80;
134 server_name www.westos.org;
135 rewrite ^/(.*)$ https://www.westos.org/$1 permanent;
[root@nodel1 conf]# systemctl reload nginx

At this point in the physical machine access:
Second: redirection between different websites
Step 1: Edit the nginx configuration file and configure the test page for bbs.westos.org
[root@nodel1 conf]# vim nginx.conf
143 server {
144 listen 80;
145 server_name bbs.westos.org;
146
147 location / {
148 root /bbs;
149 index index.html;
150 }
151 }
152 }
[root@nodel1 conf]# systemctl reload nginx


Check for errors:

[root@nodel1 conf]# cd [root@nodel1 ~]# mkdir /bbs [root@nodel1 ~]# cd /bbs [root@nodel1 bbs]# vim index.html [root@nodel1 bbs]# cat index.html bbs.westos.org #bbs test page

Add parsing to the machine:
[root@foundation15 ~]# vim /etc/hosts 172.25.15.1 nodel1 www.westos.org bbs.westos.org

Test:
Step 2: Modify the nginx configuration file and restart the nginx service
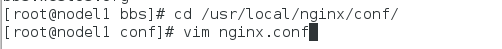
[root@nodel1 conf]# vim nginx.conf [root@nodel1 bbs]# cd /usr/local/nginx/conf/ [root@nodel1 conf]# vim nginx.conf 135 #rewrite ^/(.*)$ https://www.westos.org/$1 permanent; 136 rewrite ^/bbs/(.*)$ https://bbs.westos.org/$1 permanent; [root@nodel1 conf]# systemctl reload nginx
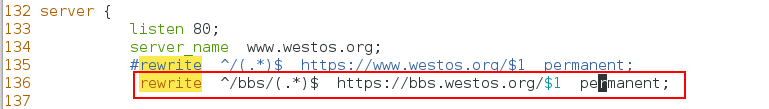

Test:
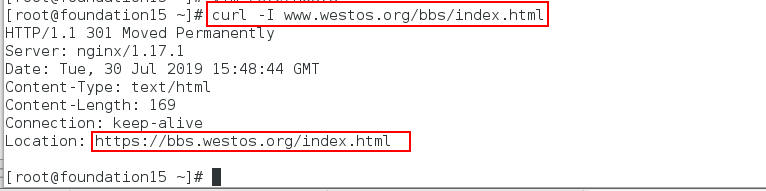
Although the above method realizes the redirection of different web pages, we find that in the test, we need to add a bbs, which is too inconvenient. To solve this problem, we do the following operations.
Step 3: Improvement
Copy the bbs directory / web Directory
[root@nodel1 conf]# cp -r /bbs /web/ [root@nodel1 conf]# cd /web/ [root@nodel1 web]# ls bbs index.html
[root@nodel1 conf]# vim nginx.conf
132 server {
133 listen 80;
134 server_name www.westos.org bbs.westos.org;
135 #rewrite ^/(.*)$ https://www.westos.org/$1 permanent;
136 #rewrite ^/bbs/(.*)$ https://bbs.westos.org/$1 permanent;
137 if ($host = "bbs.westos.org"){
138 rewrite ^/(.*)$ https://www.westos.org/bbs/$1 permanent;
139 }
140
141 location / {
142 root /web;
143 index index.html;
144 }
145 }
146 }

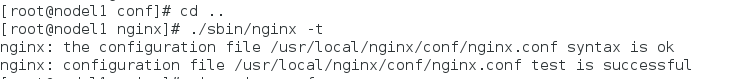
[root@nodel1 nginx]# ./sbin/nginx -t [root@nodel1 conf]# systemctl reload nginx

Step 4: Testing