As a web and reverse server, nginx is widely used, especially for those who learn c/c + +. Today, I installed and configured nginx, which I've heard a lot of. It's mainly a personal experiment for the installation and guidance in the rookie tutorial. The main concern is that the installation of nginx depends on the upgrade of openssl.
1, Prepare for installation
Server configuration:
CentOS Linux release 7.9.2009 gcc version 4.8.5
My server accounts for the purchase of student benefits, but it is also available, so it is relatively new, so the next step is to install some dependencies required by nginx:
yum -y install make zlib zlib-devel gcc-c++ libtool openssl openssl-devel
(important points)
There is a different installation here, that is, the pcre dependency of nginx and the installation of nginx. I use the method of obtaining the installation package and then compiling the installation. Sometimes this is offline installation. When the host you need to install and configure is on the intranet and cannot connect to the Internet, obtain the compressed package from the Internet, transfer it to the intranet host, decompress and compile.
pcre installation package compressed package address
wget https://sourceforge.net/projects/pcre/files/pcre/8.45/pcre-8.45.tar.gz # Get compressed package tar -xzvf pcre-8.45.tar.gz #decompression cd pcre-8.45 ./configure make && make install #Compile and install pcre-config --version #View pcre version
I created a download directory in the current directory where I logged in to the ECS, and then saved all my installation packages and compressed packages required for compilation and installation in it (in linux system, I should force myself to do a good job in document classification management, because it is not as clear as windows).
After the installation, nginx will be installed. The address is as follows. Repeat the above operation:
Installation of nginx , I chose the newer version of nginx.
wget http://nginx.org/download/nginx-1.21.1.tar.gz tar -xzvf nginx-1.21.1.tar.gz cd nginx-1.21.1 #Generate a suitable makefile using the configure provided by nginx ./configure --prefix=/usr/local/webserver/nginx --with-http_stub_status_module --with-http_ssl_module --with-pcre=~/download/pcre-8.45 #Compile and install make && make install
Generally speaking, the process is finished, but it seems that things will not go on normally, so it gives me a moth again.
checking for OpenSSL library ... not found checking for OpenSSL library in /usr/local/ ... not found checking for OpenSSL library in /usr/pkg/ ... not found checking for OpenSSL library in /opt/local/ ... not found ./configure: error: SSL modules require the OpenSSL library. You can either do not enable the modules, or install the OpenSSL library into the system, or build the OpenSSL library statically from the source with nginx by using --with-openssl=<path> option.
Obviously, it says my openssl is wrong. Why? This is what I downloaded using yum. It's an older openssl version. We can check it and know the required openssl version.
[root@Jack download]# openssl version OpenSSL 1.0.2k-fips 26 Jan 2017
2, Upgrade openssl
The openssl installation here is based on yum, but the data I got from Baidu are basically upgraded without deleting the current version of openssl, but under my operation, um...... There's still a problem. The first is the practice I refer to:
stay here You can find the openssl package you need and choose what you need.
wget https://www.openssl.org/source/old/1.1.1/openssl-1.1.1j.tar.gz tar -xzvf openssl-1.1.1j.tar.gz cd openssl-1.1.1j #Generate appropriate makefile s ./config --prefix=/usr/local/openssl ./config –t #Compile and install make && make install
The next step is the key. Now we just compile and install the new version of openssl, but when you check the version, you still use the old version, as shown below:
[root@Jack download]# openssl version OpenSSL 1.0.2k-fips 26 Jan 2017
So here's some replacement work:
#Backup current openssl mv /usr/bin/openssl /usr/bin/openssl.bak mv /usr/include/openssl /usr/include/openssl.bak #Create soft links for compiled openssl ln -sf /usr/local/openssl/bin/openssl /usr/bin/openssl ln -sf /usr/local/openssl/include/openssl /usr/include/openssl #Check function library cd /usr/local ldd /usr/local/openssl/bin/openssl #Update function library echo "/usr/local/openssl/lib" >> /etc/ld.so.conf ldconfig -v
#Last view version [root@Jack local]# openssl version OpenSSL 1.1.1j 16 Feb 2021(Library: OpenSSL 1.0.2k-fips 26 Jan 2017)
It's interesting here. It's another inexplicable error. The result shows that although it's a new version of the library, the openssl execution file is an old version! (I wrote a blog after I finished the operation, and then I couldn't reproduce it, so the problem was typed according to my impression. Don't mind if there's something wrong.).
This is because the above only changes the openssl executable file, but the library directory is still the default path of the system, so we need to change it now:
mv /usr/lib64/libssl.so /usr/lib64/libssl.so.bak ln -sf /usr/local/openssl/lib/libssl.so /usr/lib64/libssl.so
Well, then I think it's ok, so I delete all the backup files of the old version, and then openssl can't be executed......
[root@Jack ~]# openssl version -bash: openssl: no such file or directory [root@Jack ~]# /usr/bin/openssl OpenSSL 1.1.1j 16 Feb 2021
In this way, the problem is obvious, that is, the soft link we created is not added to the environment variable path. Here, I choose to compile the environment variable file to make it effective:
#1 vim ~/.bashrc #2 add the following command at the end of the file export PATH=/usr/bin:$PATH #3 reset effective source ~/.bashrc
Then openssl can be used normally. Repeat the above steps of nginx installation:
./configure --prefix=/usr/local/webserver/nginx --with-http_stub_status_module --with-http_ssl_module --with-pcre=~/download/pcre-8.45 #Compile and install make && make install #View historical versions of nginx /usr/local/webserver/nginx/sbin/nginx -v
Trample pit
In order to record the previous pit, I uninstalled openssl and openssl devel previously installed with yum, then deleted and restored the previously installed nginx and the library compiled by the new version of openssl, reinstalled the previous environment, and then the following problems occurred:
objs/ngx_modules.o \ -ldl -lpthread -lcrypt ~/download/pcre-8.45/.libs/libpcre.a -lssl -lcrypto -ldl -lpthread -lz \ -Wl,-E /usr/bin/ld: warning: libcrypto.so.1.1, needed by /usr/lib/gcc/x86_64-redhat-linux/4.8.5/../../../../lib64/libssl.so, may conflict with libcrypto.so.10 /usr/bin/ld: objs/src/core/nginx.o: undefined reference to symbol 'OpenSSL_version@@OPENSSL_1_1_0' //usr/local/openssl/lib/libcrypto.so.1.1: error adding symbols: DSO missing from command line collect2: error: ld returned 1 exit status make[1]: *** [objs/nginx] Error 1 make[1]: Leaving directory `/root/download/nginx-1.21.5' make: *** [build] Error 2
The specific problem description is like this. The upgraded openssl version is the new version, but the linked library compiled in nginx is the old version. In order to ensure clean cleaning, I had to delete the previous backup file, write it into the environment variable file, restore it, and then push it over and start again. So I deleted libssl so. 1.0.2k, why? I owe you! Then I couldn't log in. It was always in the state of connection closed. I thought it was an accident in the computer room, so I went to bed. As a result, it was still the same the next day!
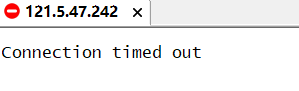
Try vnc login. Yes, and then try ssh login with local cmd. It fails:
PS C:\Users\Jack\Desktop> ssh root@121.5.47.242 kex_exchange_identification: read: Connection reset PS C:\Users\Jack\Desktop> ssh -v root@121.5.47.242 OpenSSH_for_Windows_8.1p1, LibreSSL 3.0.2 debug1: Connecting to 121.5.47.242 [121.5.47.242] port 22. debug1: Connection established. debug1: identity file C:\\Users\\samu/.ssh/id_rsa type -1 debug1: identity file C:\\Users\\samu/.ssh/id_rsa-cert type -1 debug1: identity file C:\\Users\\samu/.ssh/id_dsa type -1 debug1: identity file C:\\Users\\samu/.ssh/id_dsa-cert type -1 debug1: identity file C:\\Users\\samu/.ssh/id_ecdsa type -1 debug1: identity file C:\\Users\\samu/.ssh/id_ecdsa-cert type -1 debug1: identity file C:\\Users\\samu/.ssh/id_ed25519 type -1 debug1: identity file C:\\Users\\samu/.ssh/id_ed25519-cert type -1 debug1: identity file C:\\Users\\samu/.ssh/id_xmss type -1 debug1: identity file C:\\Users\\samu/.ssh/id_xmss-cert type -1 debug1: Local version string SSH-2.0-OpenSSH_for_Windows_8.1 kex_exchange_identification: Connection closed by remote host PS C:\Users\Jack\Desktop>
But it let me find the source of the problem, compared with kex_exchange_identification: Connection closed by remote host: when I went to Baidu, I found one that said it was a concurrent connection back pot, then changed MaxStartups and MaxSessions, and restarted the ssh service after the change, but my restart failed (operate at vnc login):
#Modify MaxStartups and MaxSessions vim /etc/ssh/sshd_config #Restart ssh service systemctl restart sshd
If it's a concurrent connection problem, that's fine, but the result shows that it can't be restarted. Let me check the ssh status:
#Check the ssh service status sshd.service #Report specific error sshd -t
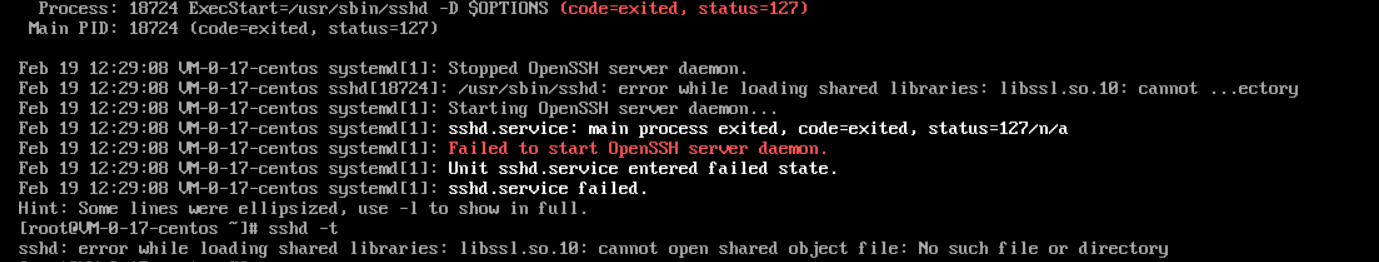
The error message here is very clear, that is, load libssl so. Error at 10:00. After confirmation, restore the previously changed file variables first, otherwise I don't know what's going on. For ECS login, vnc login is basically a configuration problem, so you can use ssh -v @ to check whether there is a problem with ssh login, and then you can solve it,
#Check ssh service service sshd status #Test mode view sshd -t
sshd is a daemon in openssh software suite, which can be used to view ssh problems. The next step is how to install libssl so. 10.
Let's see what's wrong with the library file. ll check libssl in the / usr/lib64 library The file information starting with so can be seen from the following: libssl so. 10 link to libssl so. 1.0.2k file is missing.
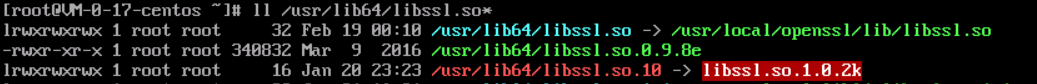
However, many methods do not correspond to the current version. I simply choose to reinstall the system. After all, it is a cloud server and has its own image, but you'd better save the image before doing the operation in the future.