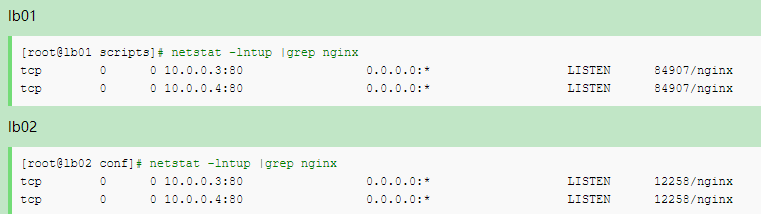
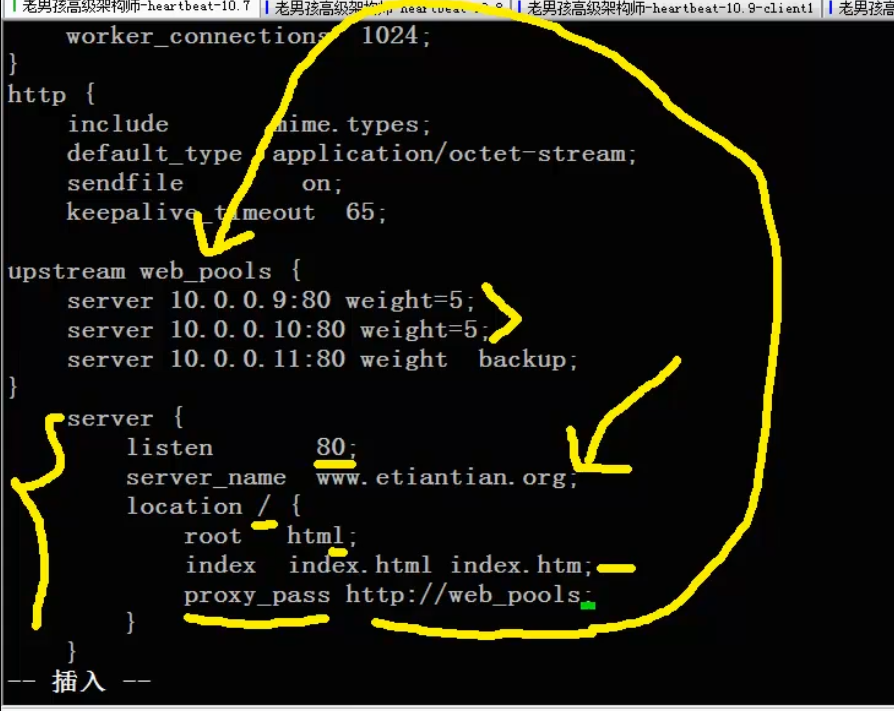
Load balancing, there is a place where = 5 is not written. Pay attention to the following figure
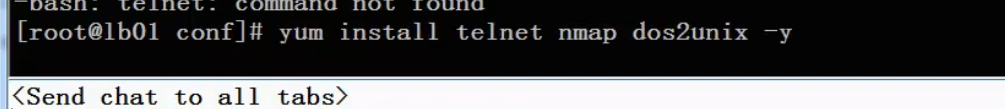
Installing telnet
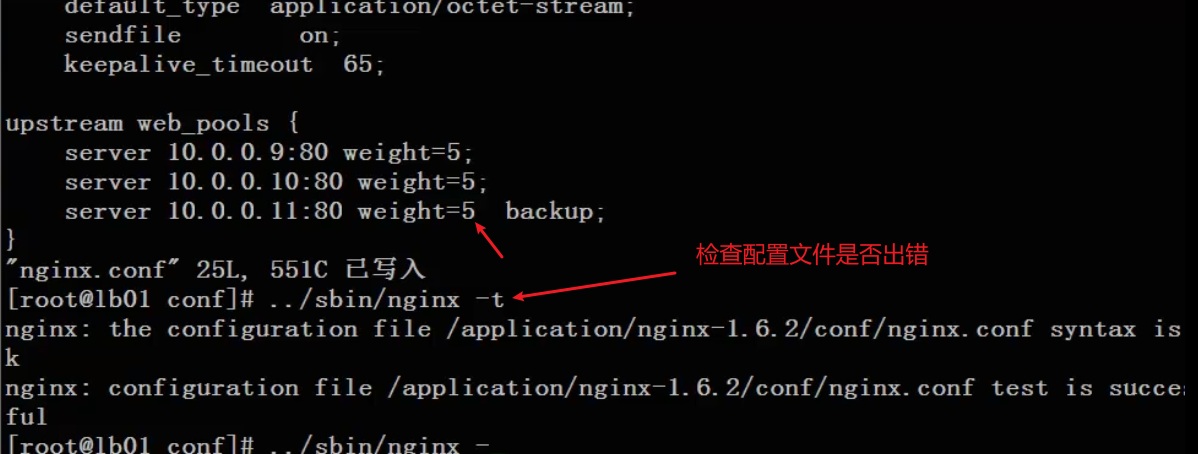
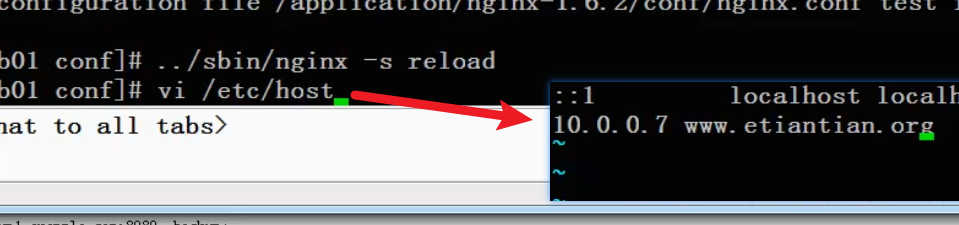
Restart ng and configure ip
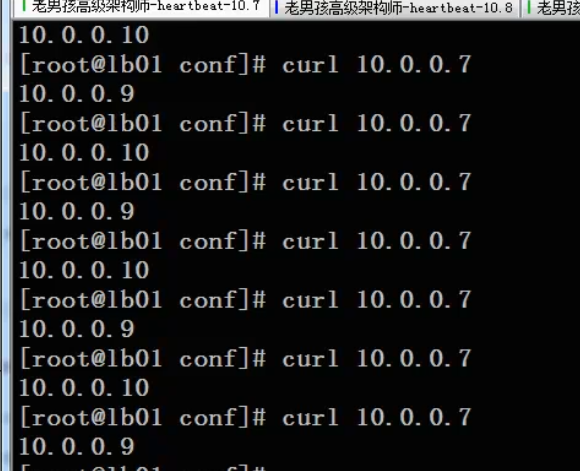
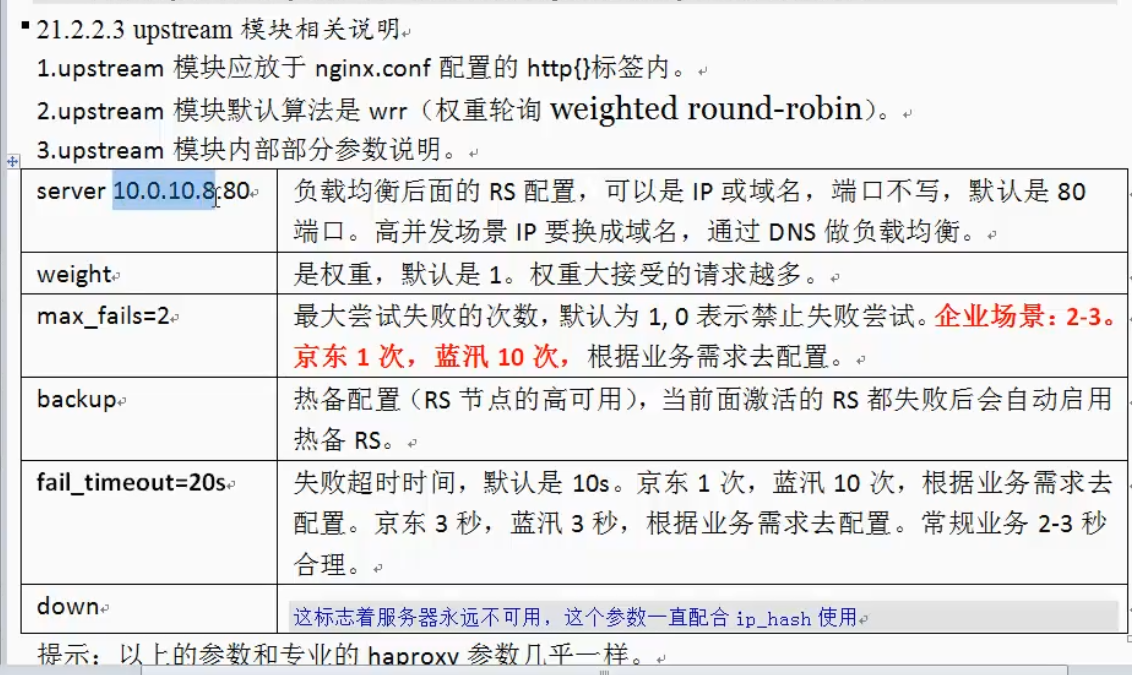
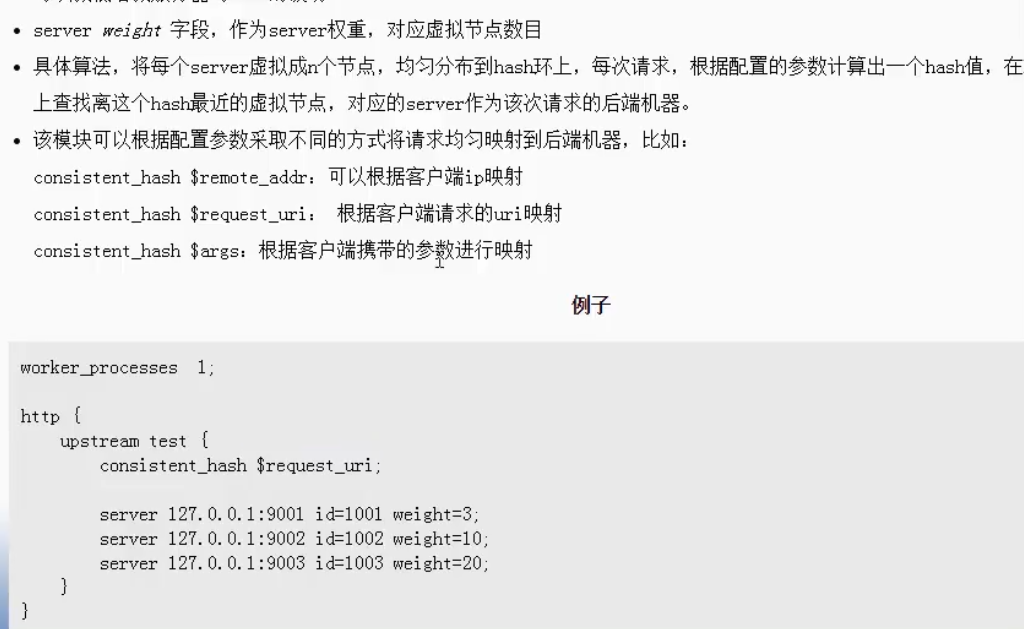
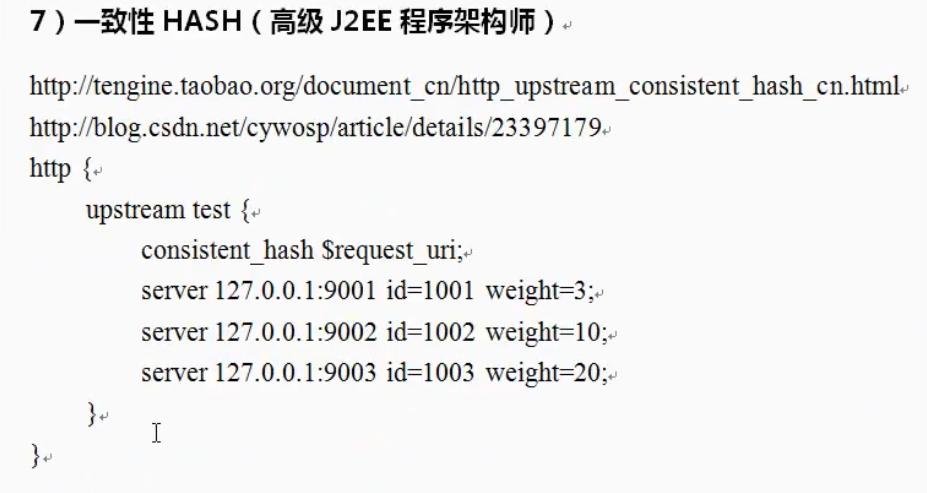
Address hash
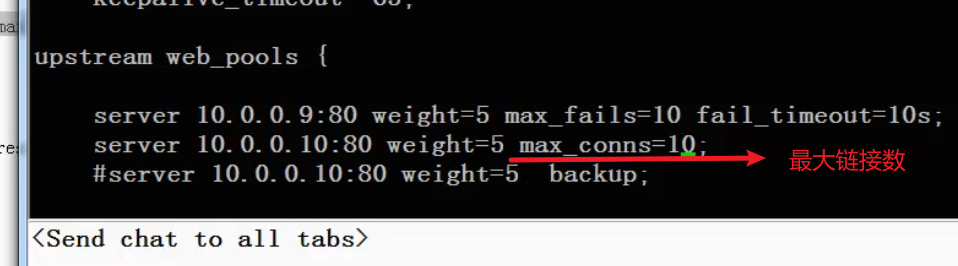
Maximum number of links
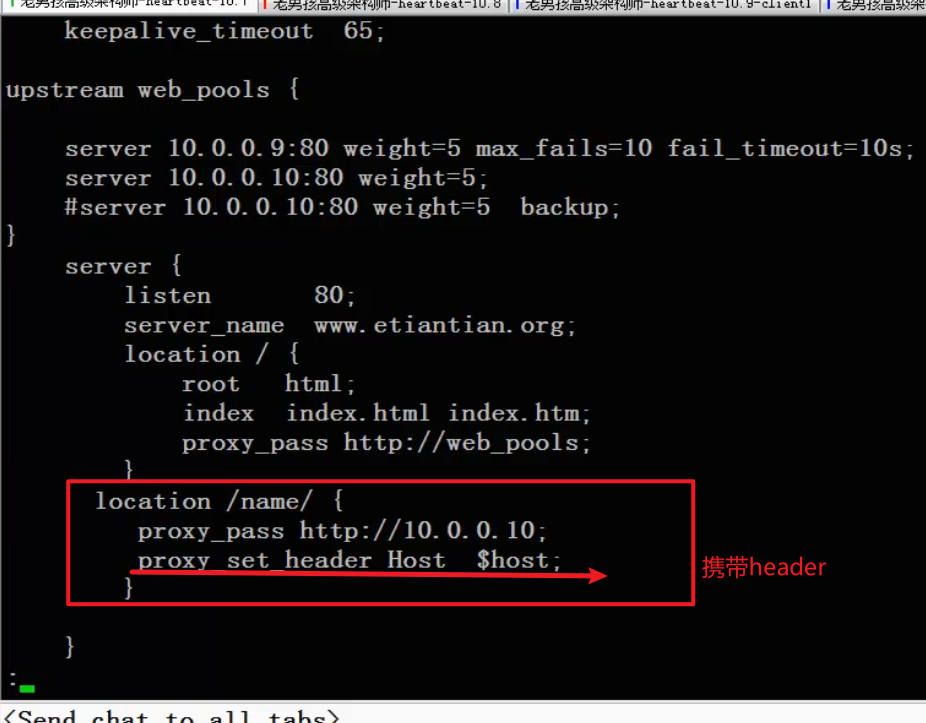
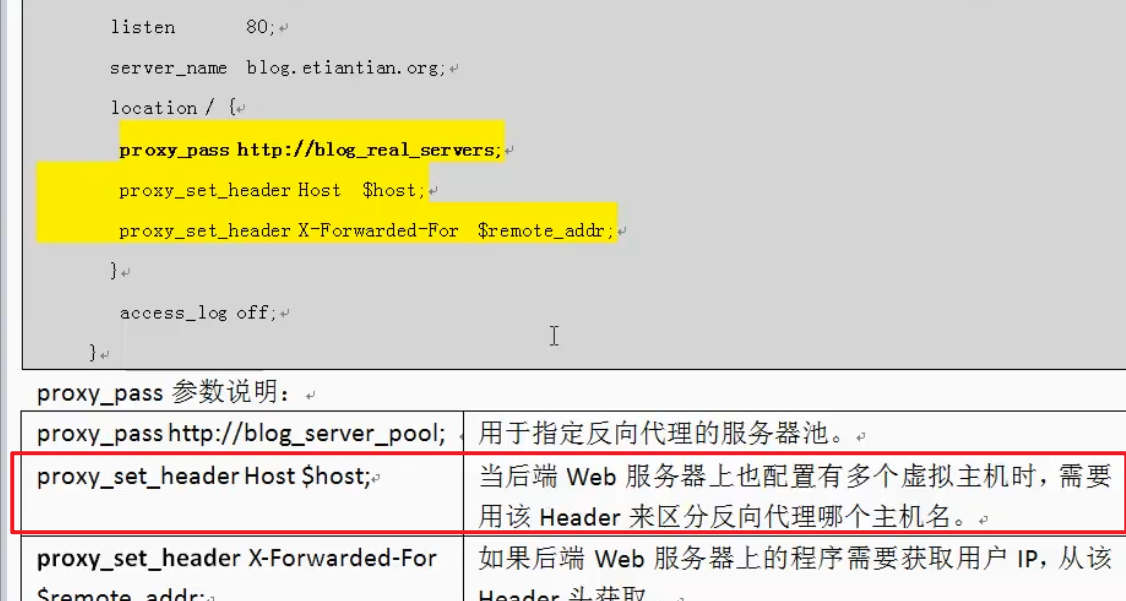
Carry header
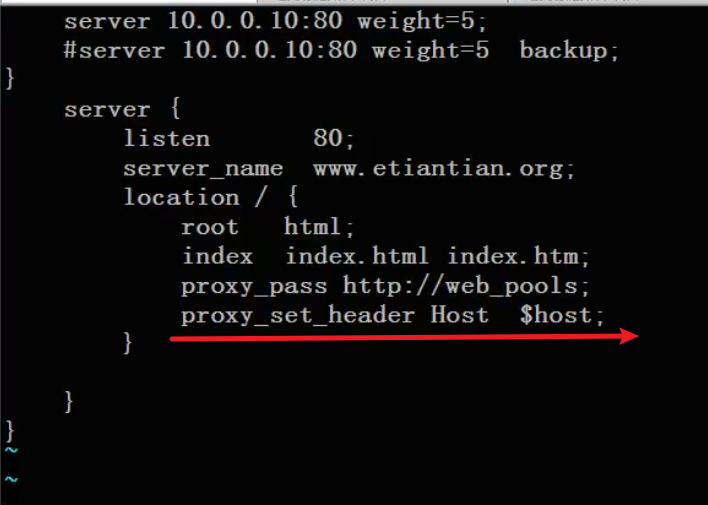
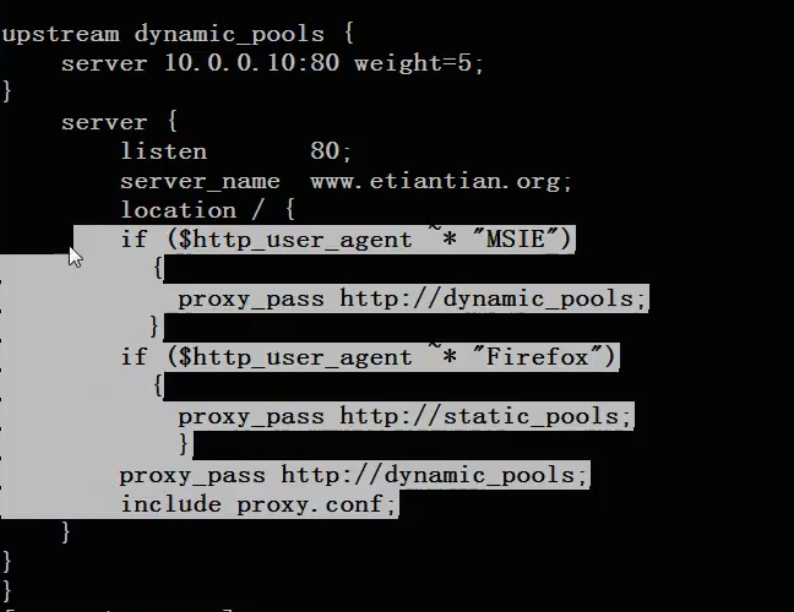
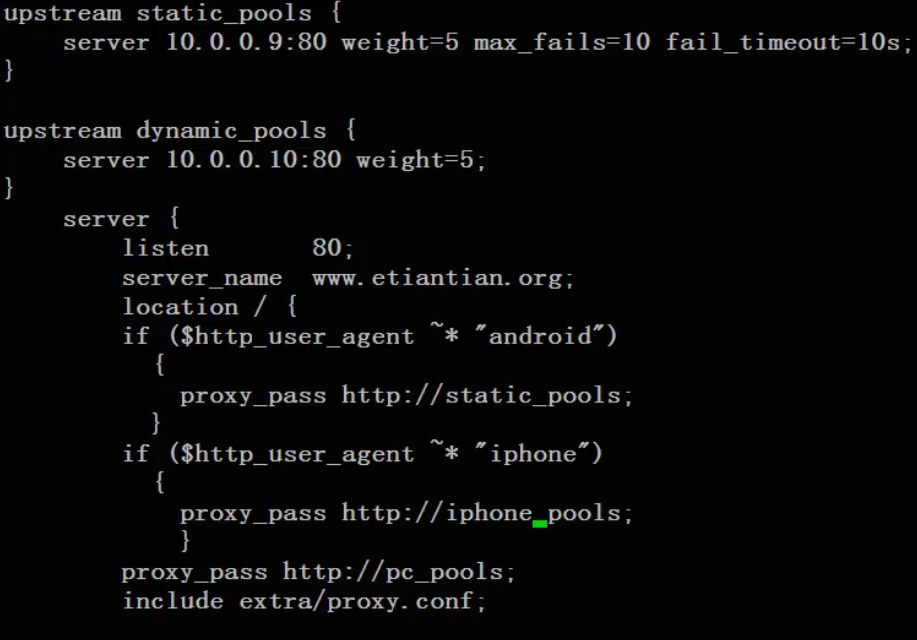
With host name and ip
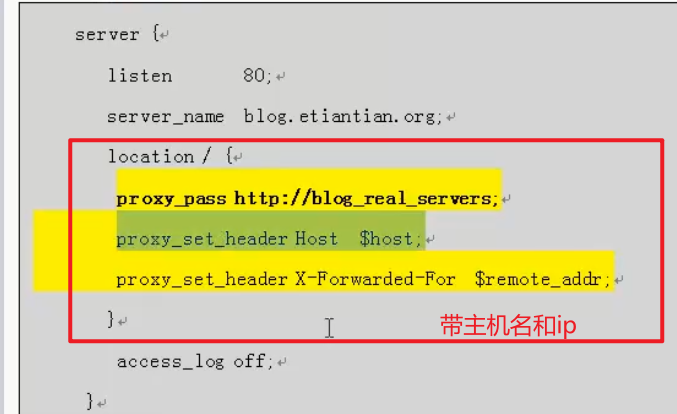
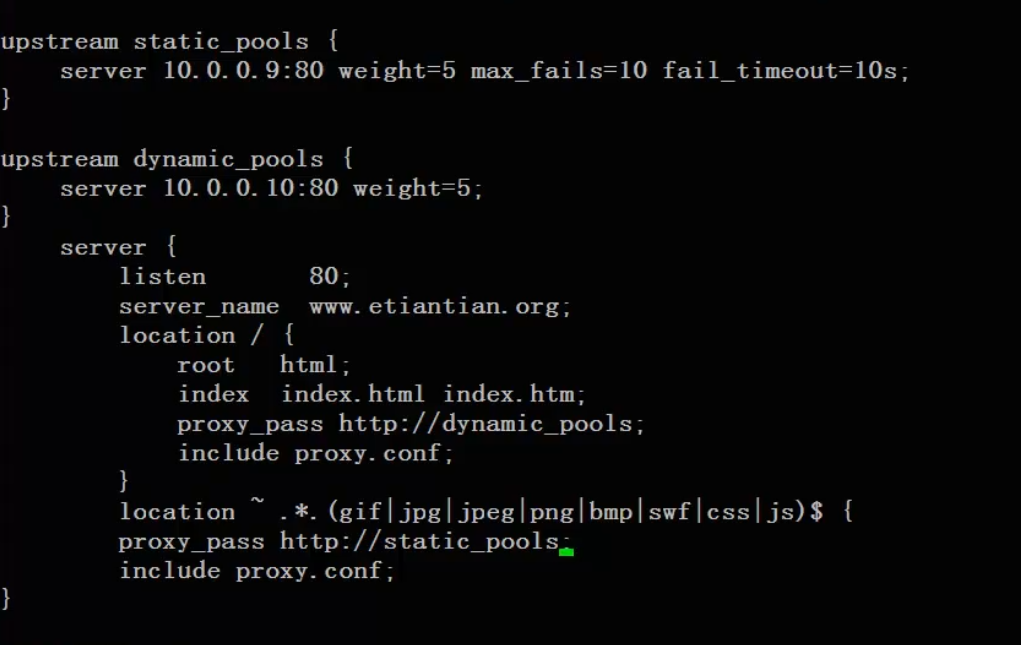
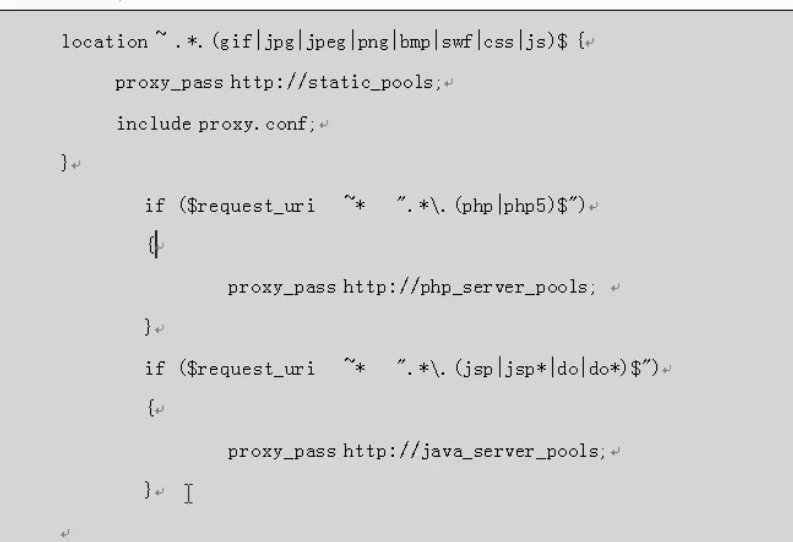
Domain name splitting
Include include files
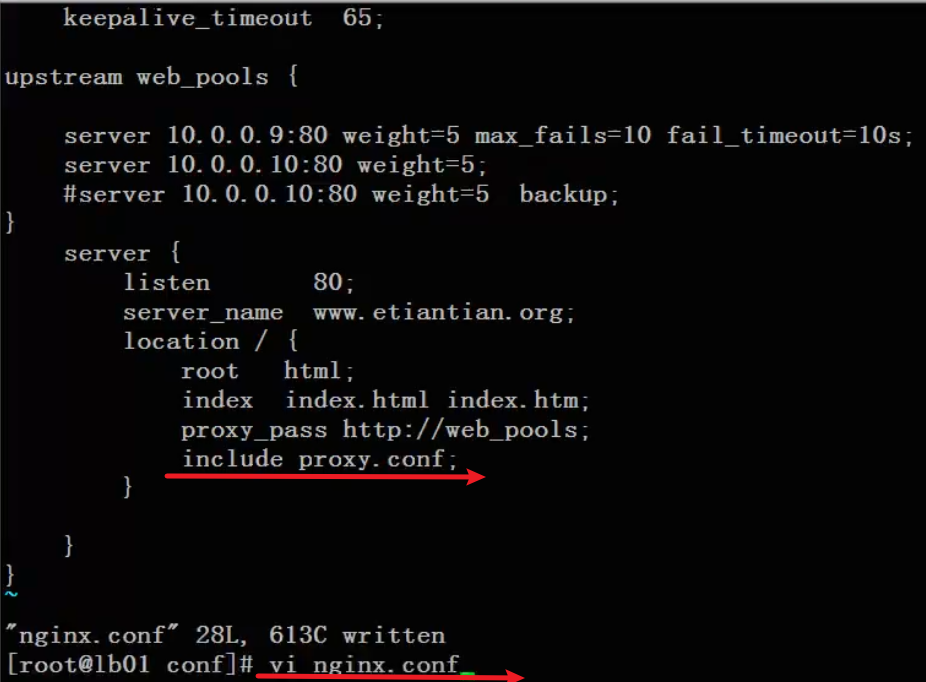
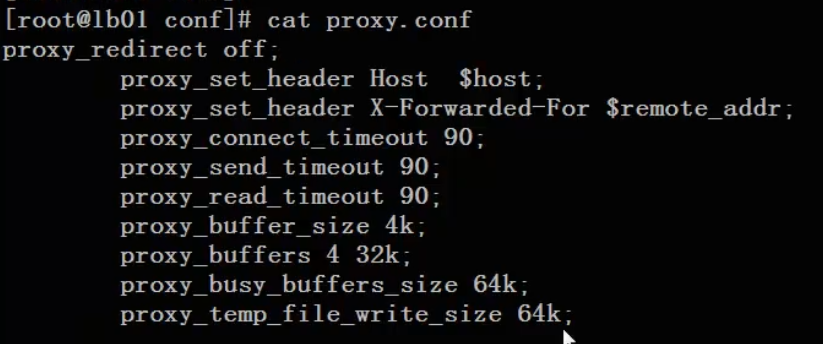
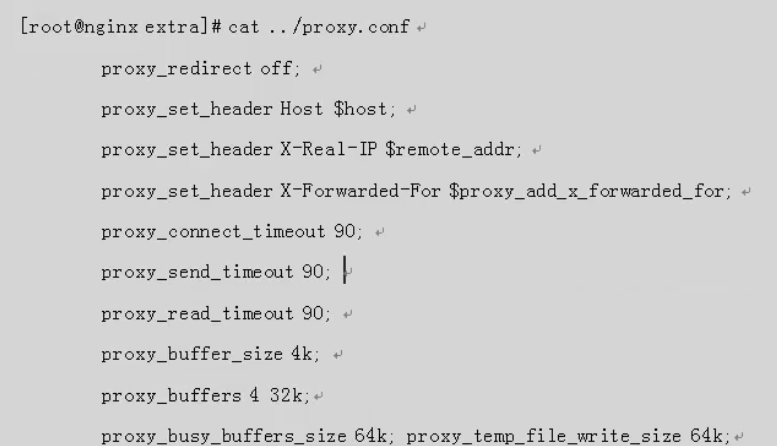
proxy.conf proxy settings
Dynamic and static separation
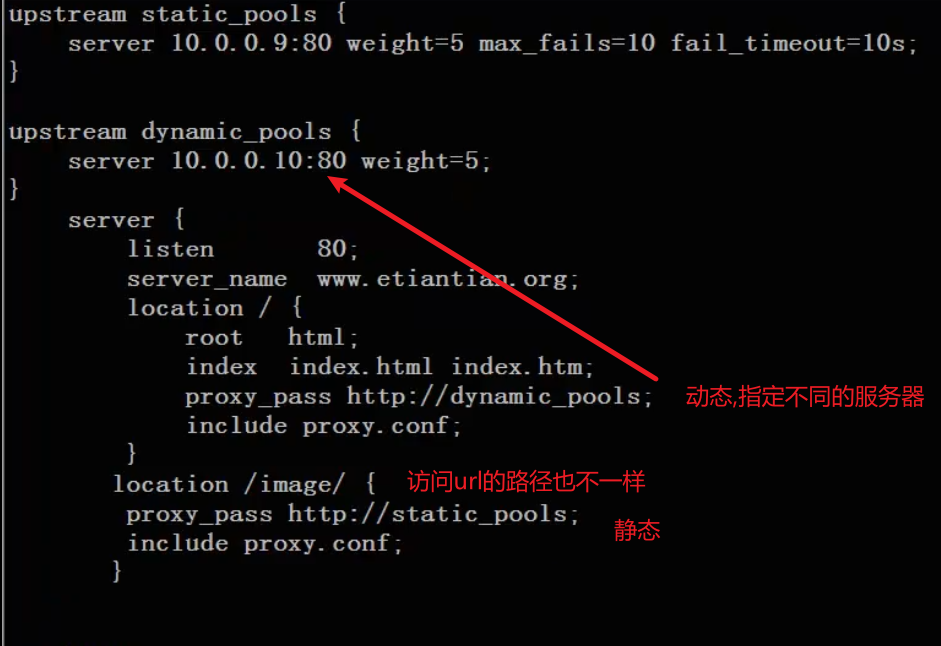
The dynamic and static separation is realized through the extension, which can also be judged through if
Judge through useragent
health examination
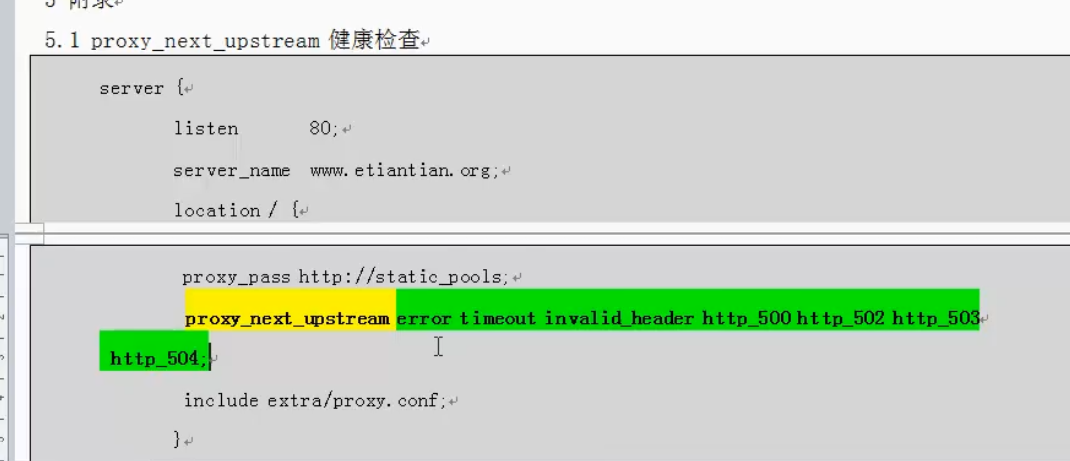
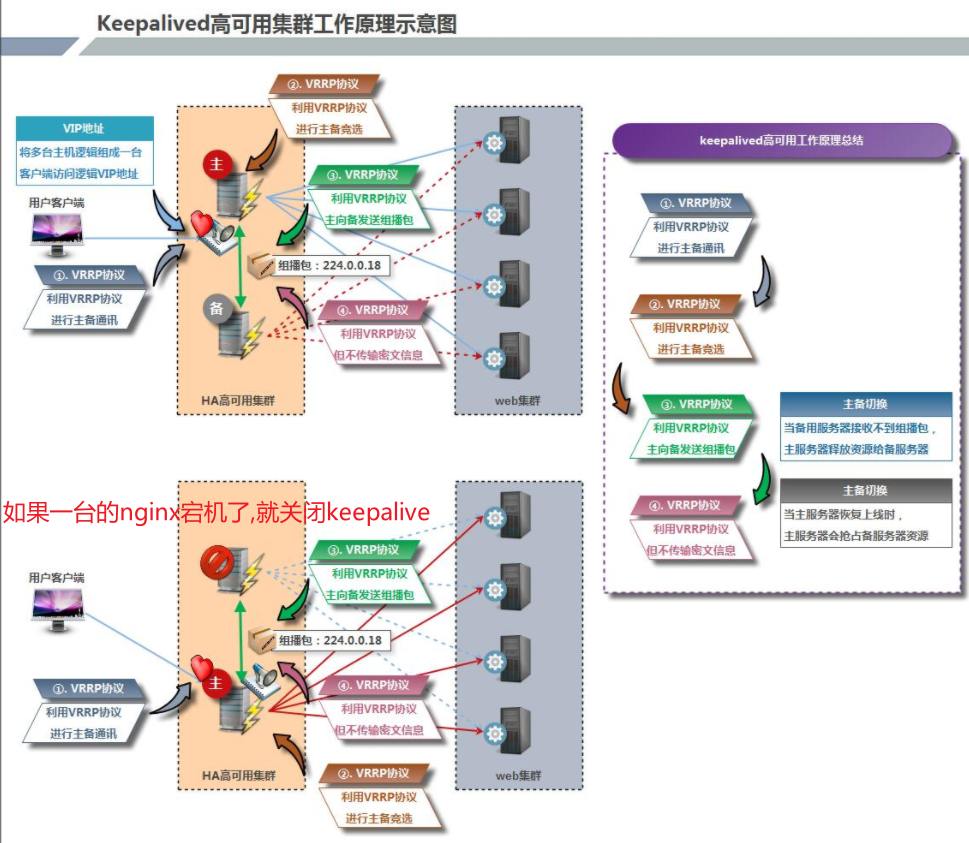
Highly available Keepalived
High availability: two business systems start the same service. If one fails and the other takes over automatically, we will call this high availability;
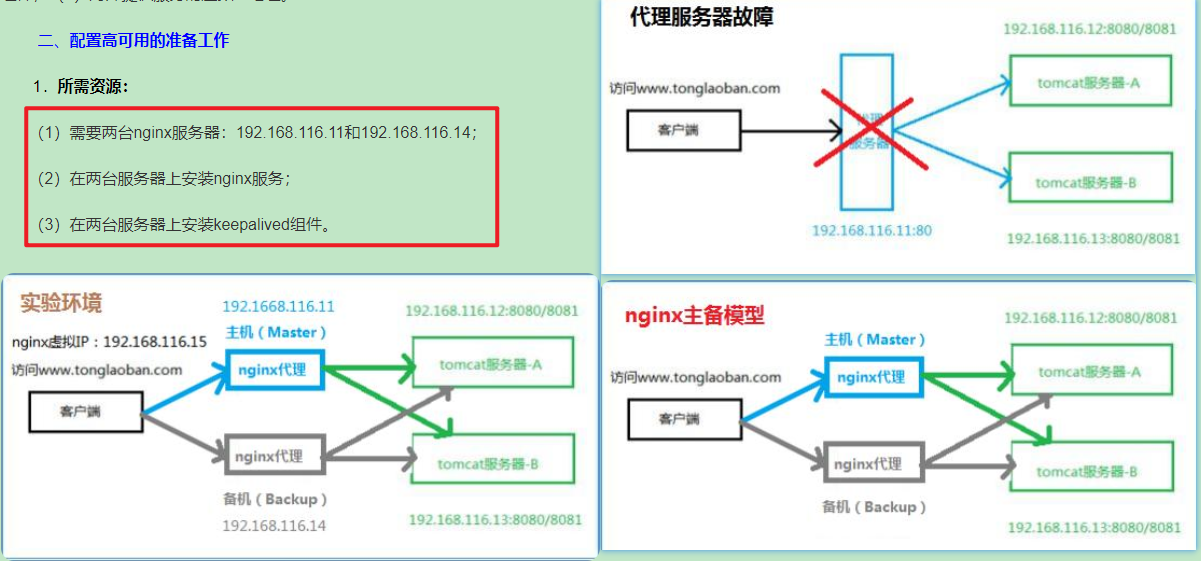
Keepalived will generate a virtual IP, which is bound to the IP of multiple real servers. When the user sends a request to the virtual IP, the request will be routed to the primary server first. When the primary server goes down, the request will be routed to the standby server to achieve the purpose of high availability.
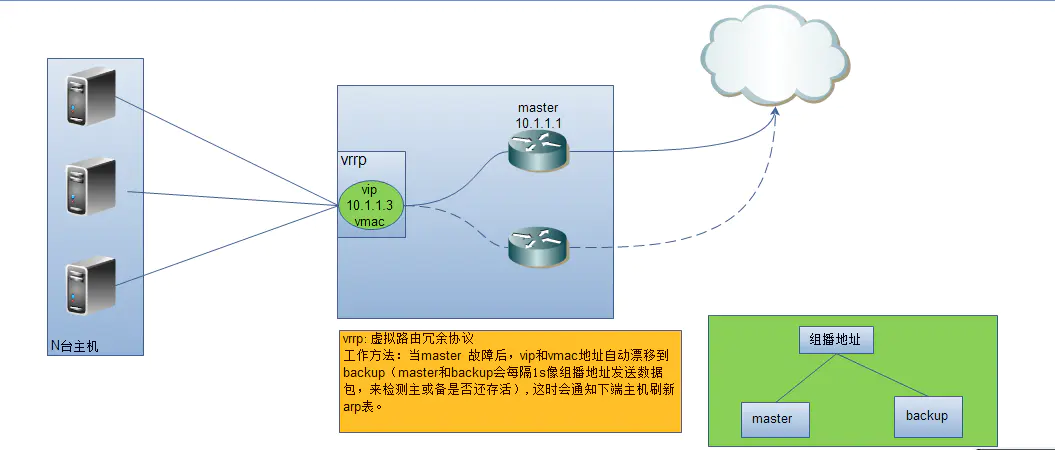
Keepalived working mode: preemptive and non preemptive
@1. yum installation:
yum install keepalived -y Log storage location:/var/log/messages
@2. Official website
You can go to the Keepalived official website( https://www.keepalived.org )Download
tar -zxvf keepalived-2.2.4.tar.gz @1. Install dependent packages yum -y install libnl libnl-devel yum install -y openssl openssl-devel @2. Execute configuration command,Enter the directory to execute ./configure --prefix=/usr/local/keepalived --sysconf=/etc @3. Execute the compile and install command make && make install @4. After successful installation, in /etc/keepalived Under the directory, you will see keepalived.conf Documents.
II Configuration of mode 1
Enter the / etc/keepalived directory and modify keepalived Conf file.
A The server configuration is as follows:
! Configuration File for keepalived
global_defs {
# Globally unique host ID
router_id server_a
}
vrrp_instance VI_1 {
# Identify whether it is the primary node or the standby node. The value is MASTER or BACKUP
state MASTER
# Bound network card
interface ens33
# Virtual routing id to ensure that the primary and standby nodes are consistent
virtual_router_id 51
# weight
priority 100
# Synchronization check time. The default interval is 1 second
advert_int 1
# All active and standby users need the same password for authentication and authorization
authentication {
auth_type PASS
auth_pass 1111
}
# Virtual IP
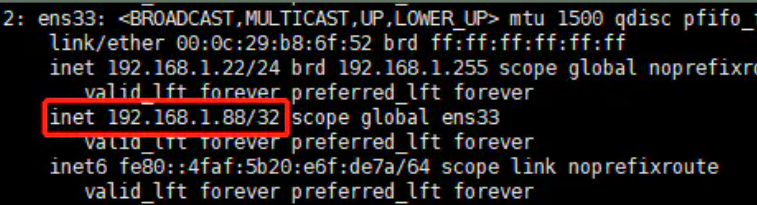
virtual_ipaddress {
192.168.1.88
}
}
B The server configuration is as follows:
! Configuration File for keepalived
global_defs {
router_id server_b
}
vrrp_instance VI_1 {
# Set as standby
state BACKUP
interface ens33
virtual_router_id 51
# The weight setting is lower than that of the host
priority 90
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
# The virtual IP needs to be set as the same as the active and standby IP
virtual_ipaddress {
192.168.1.88
}
}
- Give the virtual ip and establish the shell script. You must give permission and permission
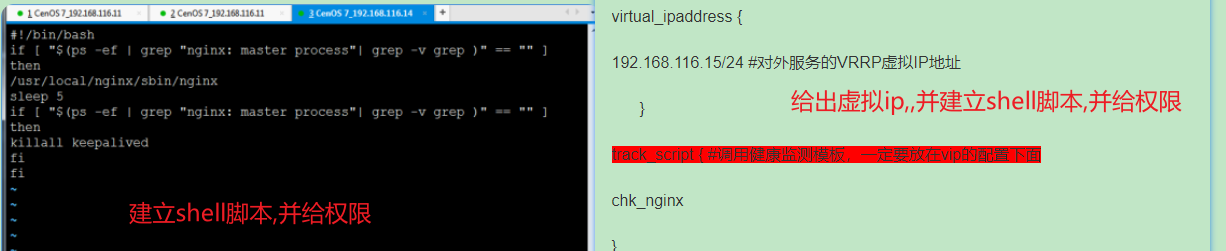
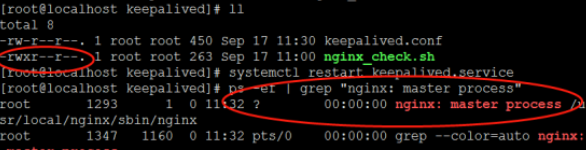
5. Start Keepalived
get into /usr/local/keepalived/sbin catalogue ./keepalived perhaps Start with script nginx as well as keepalived: systemctl start keepalived.service
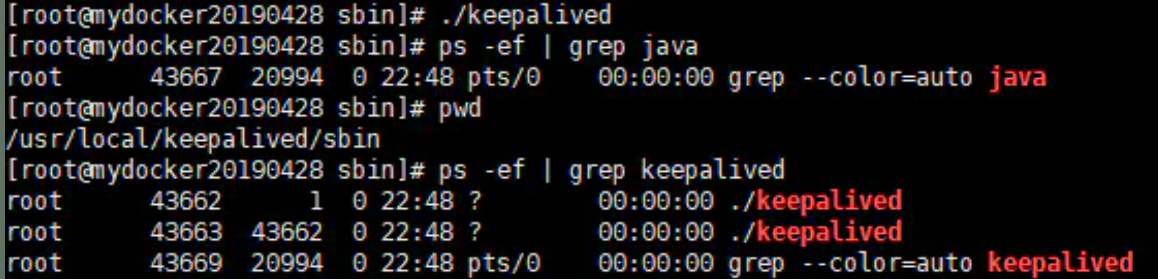
View log:
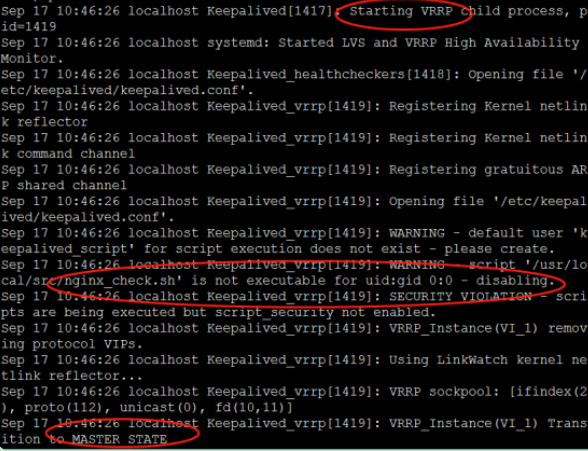
The startup script has helped me start nginx. View the virtual ip address generated by the network card: 192.168.116.15:
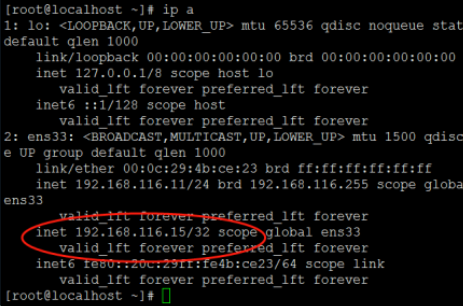
Authentication service
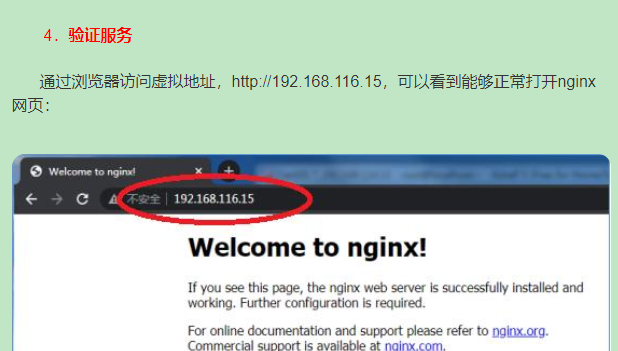
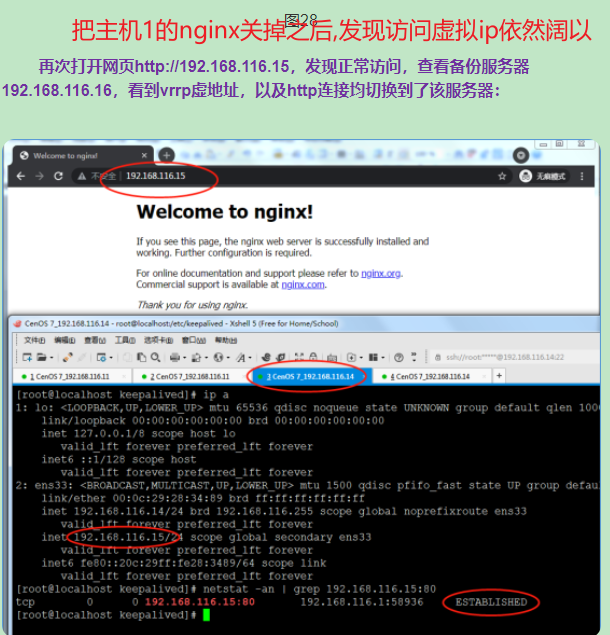
6. Stop server A and see if the virtual IP is routed to server B
The test shows that after server A is closed, the virtual IP is routed to server B.
Finally, modify the proxy of nginx to point to the virtual IP
worker_processes 1;
events {
worker_connections 1024;
}
http {
include mime.types;
default_type application/octet-stream;
sendfile on;
keepalive_timeout 65;
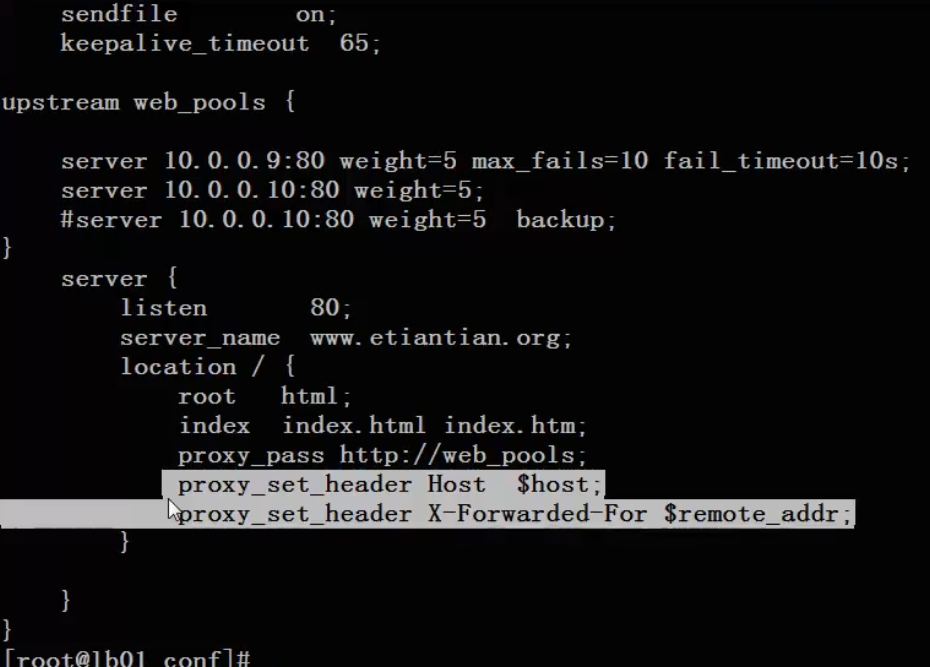
upstream server_pools {
server 10.0.0.7:80;
server 10.0.0.8:80;
}
server {
listen 192.168.1.15:80;
server_name www.etiantian.org;
location / {
proxy_pass http://server_pools;
proxy_set_header Host $host;
proxy_set_header X-Forwarded-For $remote_addr;
}
}
II Configuration of mode 2
1. keepaliaved preemptive configuration
master configuration
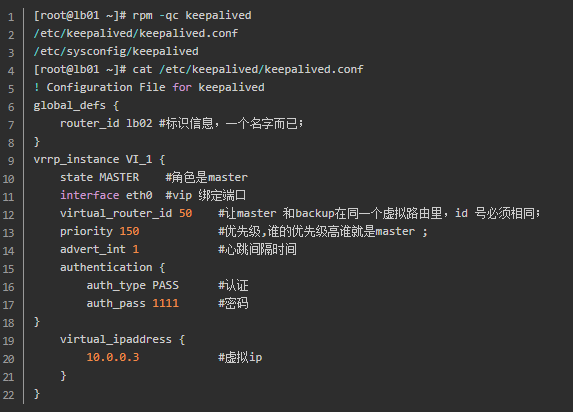
backup configuration
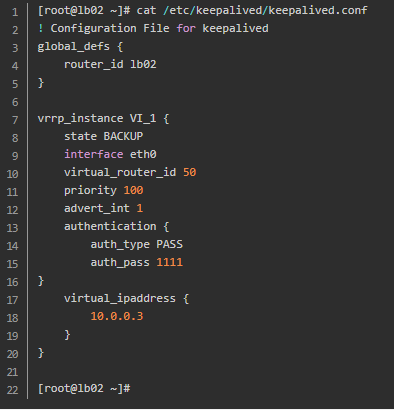
2. Keepalived non preemptive configuration:
Non preemptive mode is no longer divided into master and slave mode. All of them are BACKUP, and nopreempt is added to the configuration file to identify it as non preemptive mode;
First profile settings
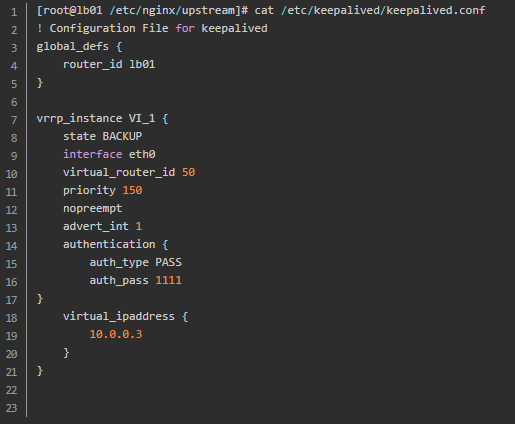
Second profile settings
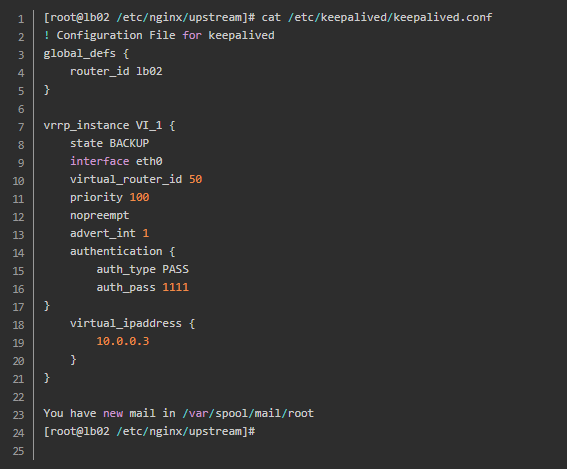
3,nginx+keepalived
Implementation idea: take vip in Keepalived as the listening address of Nginx load balancing, and the domain name is also bound with the address of vip. Note: to realize high availability of Nginx load balancing, the function of Keepalived address drift is required.
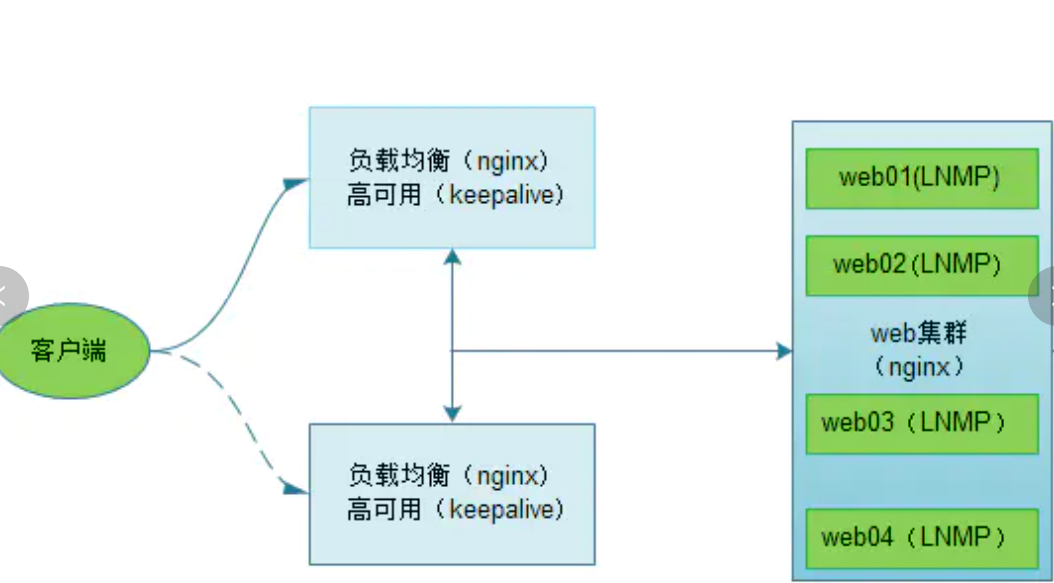
Two load balancing configurations:
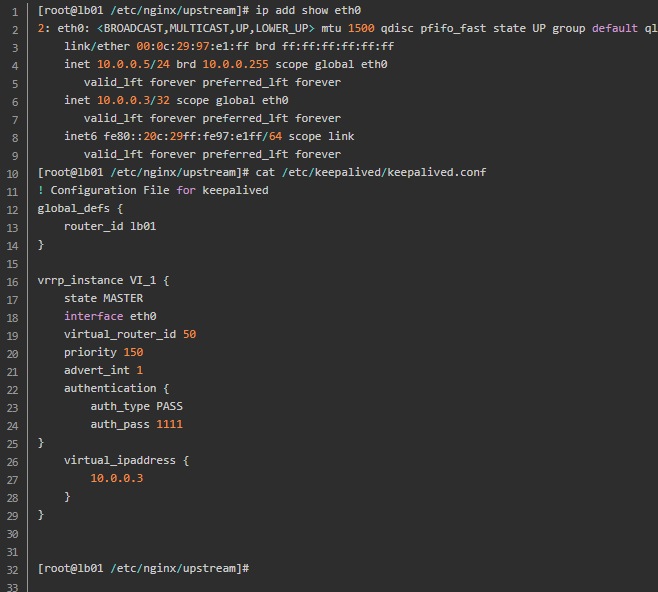
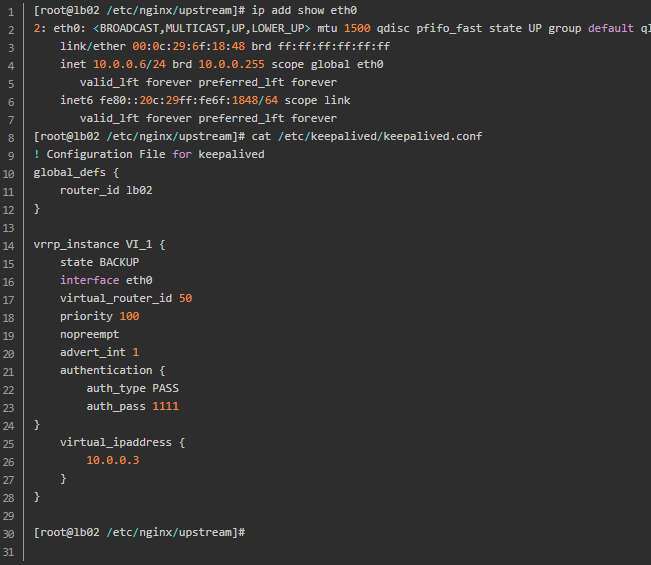
4. Kept cleft brain phenomenon
For some reasons, the two keepalived highly available servers cannot detect the heartbeat information of each other within the specified time, resulting in each other seizing the ownership of each other's resources and services. However, at this time, both highly available servers are still alive.
Possible causes:
- 1. Network faults such as loose server network cable;
- 2. The server hardware breaks down due to damage;
- 3. Both active and standby firewalld firewalls are enabled.
- 4. In the Keepalived+nginx architecture, when Nginx goes down, the user request will fail, but keepalived will not switch,
! Therefore, you need to write a script to detect the survival status of nginx. If nginx does not survive, kill the keepalived on the down nginx host. (all keepalived must be configured)
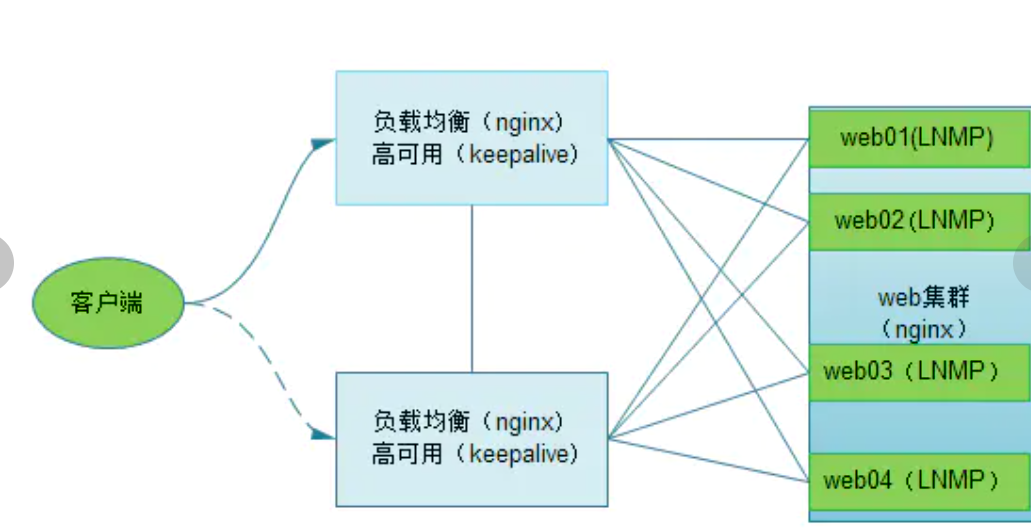
The script is as follows:
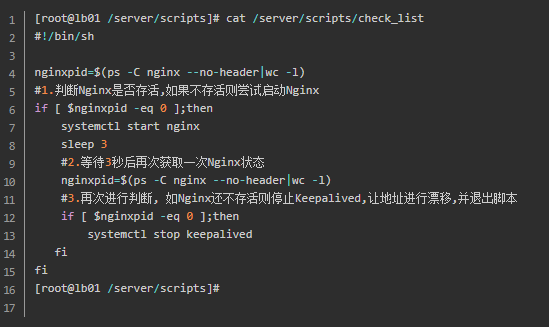
The configuration file is as follows:
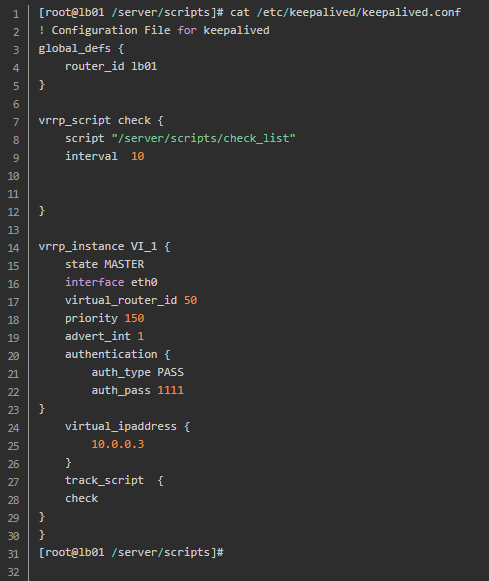
Multi instance configuration
Write monitoring script and check_www.sh
vim check_www.sh #!/bin/bash while true do if [ `ps -ef |grep nginx |grep -v grep |wc -l` -lt 2 ] then /etc/init.d/keepalived stop exit fi done chomod +x check_www.sh
2.7.1 keepalived configuration file of LB01
[root@lb01 scripts]# cat /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
router_id lb01
}
vrrp_script check {
script "/server/scripts/check_www.sh"
interval 2
weight 2
}
vrrp_instance VI_1 {
state MASTER
interface eth0
virtual_router_id 51
priority 150
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
10.0.0.3/24 dev eth0 label eth0:1
}
track_script {
check
}
}
vrrp_instance VI_2 {
state BACKUP
interface eth0
virtual_router_id 52
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
10.0.0.4/24 dev eth0 label eth0:2
}
}
2.7.2 modify the keepalived configuration file of lb02
[root@lb02 conf]# cat /etc/keepalived/keepalived.conf
! Configuration File for keepalived
global_defs {
router_id lb02
}
vrrp_instance VI_1 {
state BACKUP
interface eth0
virtual_router_id 51
priority 100
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
10.0.0.3 dev eth0 label eth0:1
}
}
vrrp_instance VI_2 {
state MASTER
interface eth0
virtual_router_id 52
priority 150
advert_int 1
authentication {
auth_type PASS
auth_pass 1111
}
virtual_ipaddress {
10.0.0.4 dev eth0 label eth0:2
}
}
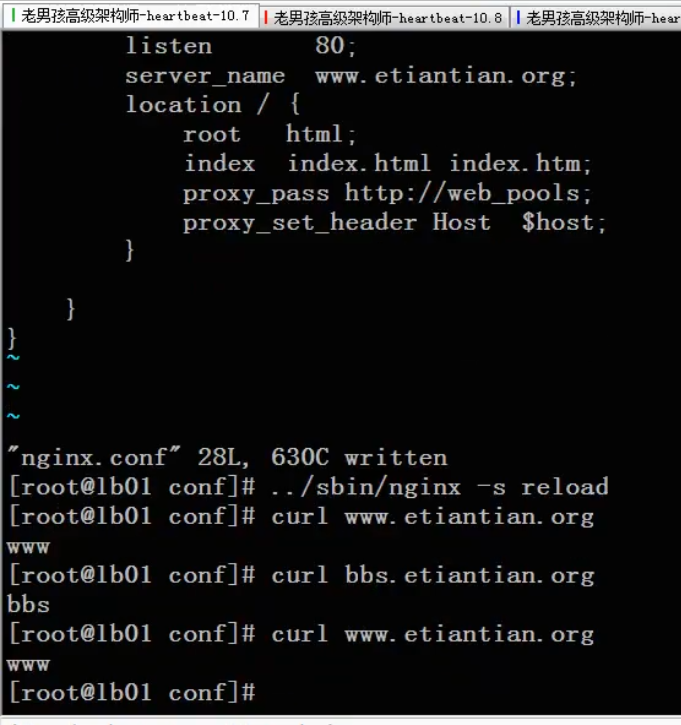
Modify the nginx configuration file to let bbs and www listen to different ip addresses respectively
worker_processes 1;
events {
worker_connections 1024;
}
http {
include mime.types;
default_type application/octet-stream;
sendfile on;
keepalive_timeout 65;
upstream server_pools {
server 10.0.0.7:80;
server 10.0.0.8:80;
server 10.0.0.9:80;
}
server {
listen 10.0.0.3:80;
server_name www.etiantian.org;
location / {
proxy_pass http://server_pools;
proxy_set_header Host $host;
proxy_set_header X-Forwarded-For $remote_addr;
}
}
server {
listen 10.0.0.4:80;
server_name bbs.etiantian.org;
location / {
proxy_pass http://server_pools;
proxy_set_header Host $host;
proxy_set_header X-Forwarded-For $remote_addr;
}
}
}