professional knowledge
Principle of computer composition
Q: because CPU The internal operation speed is faster, and CPU It takes a long time to access main memory once, so the machine cycle is usually used_______To specify. A: The shortest time to read an instruction word from main memory
Q: Among the following register groups, the register group that can provide offset address during intra segment addressing is( ). A: BX,BP,SI,DI
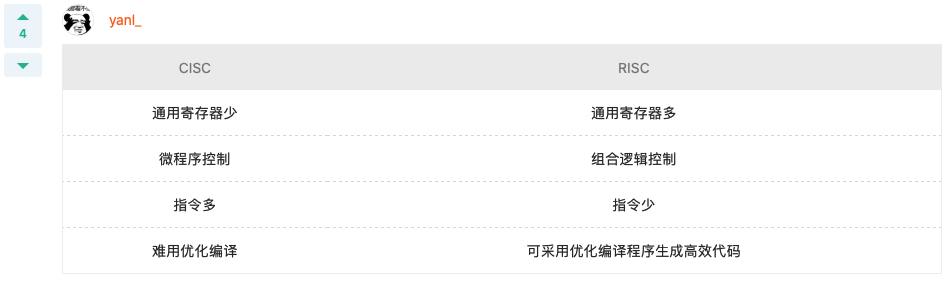
Q: The title comes from kingcraft forum About RISC In the narration of, the error is (). RISC Microprogrammed controllers are widely used // Hardwired controller RISC Most instructions are completed in one clock cycle RISC Relative number of internal general registers CISC many RISC The number of instructions, addressing mode and type of instruction format are relative CISC less A: RISC Microprogrammed controllers are widely used

Q: At the beginning of the pulse, whether there is a jump indicates "0" and "1". The code that always jumps in the middle of the pulse is () A: Differential Manchester code
Distinguishing method: Manchester code / differential Manchester code
data structure
Q: The prefix form of an expression is"+-*^ABCD/E/F+GH",Its infix form is() A: A^B*C-D+E/(F/(G+H))
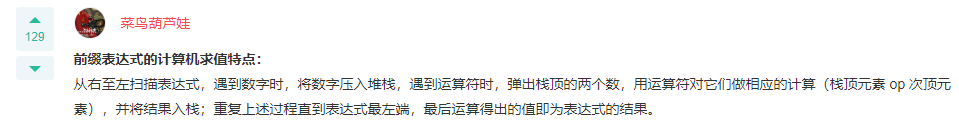
Q: Quick sort is a sort with the best average performance among comparison based sorting algorithms. ( ) A: correct
Q: In a 4-order tree with 15 keywords B In the tree, the maximum number of nodes containing keywords is () A: 15

Q: On the premise that the sequence of elements to be sorted is basically orderly, the most efficient sorting method is______ . Insert sort Select sort Quick sort Merge sort A: Select sort

Q: The time complexity of the algorithm is O(nlogn),The space complexity is O( 1)The sorting algorithm is( ). Quick sort Merge sort Heap sort Select sort A: Heap sort
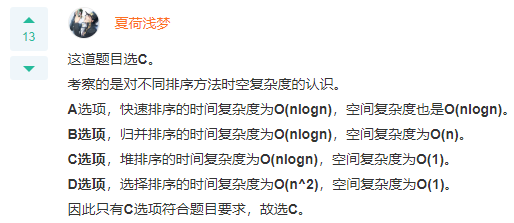
Q: In a student information table, set up a set of keyword sequences representing grades(24,15,32,28,19,10,40)When direct insertion sorting is adopted, when inserting record 19 into the ordered table, the number of comparisons required to find the insertion position is( ) A: 4
Q: The general means of optimizing recursive programs are () Tail recursive optimization Cycle optimization Stack optimization Stop value optimization A: Tail recursive optimization

Q: There is a set of initial keyword sequence (30),20,10,25,15,28),The result of the 4th direct insertion sorting is () A: 10,15,20,25,30,28
The result before the k + 1st keyword processing

Q: Known trigeminal tree T The weights of the six leaf nodes in are 2, 3, 4, 5, 6 and 7 respectively, T The minimum weighted (external) path length is () A: 46


Q: Which of the following lookup methods has an average lookup length independent of the number of data elements in the lookup table? Hash lookup Sequential search Half search B+Tree lookup A: Hash lookup // I think there are still problems with the problem. After all, if there is a conflict, it will affect the search efficiency
Detailed explanation of B-tree and B + tree
m-order B-tree:
- Each node has at most m − 1 m-1 m − 1 keyword
- The root node has at least 2 2 2 sub trees, up to m m m sub trees
- All leaf nodes are on the same layer
- All non leaf nodes except the root node have at least ceil(m/2) sub trees
- There is no need to use pointer links between leaf nodes (the B + tree needs to be connected)
When inserting, if the number of keywords of the node is equal to m − 1 m-1 m − 1, it must be split into two nodes
When deleting a node, if the number of keywords of the node is equal to ceil(m/2) -1 (it cannot be less than ceil(m/2) -1. Once it is less, the merge operation must be performed). Then it needs to merge with its sibling node to borrow a node to form a node:
- When the number of sibling nodes is greater than ceil(m/2), the corresponding keyword of the parent node moves down to the end of the node, and the keyword at the beginning of the sibling node runs to the position of the parent node
- When the number of sibling nodes is equal to ceil(m/2), the two nodes are merged together with the keyword of the parent node, and a keyword of the merge and endpoint runs to the parent node
Note: when deleting the leaf node with only one element in the third-order B tree, it's not just to delete the node. You also need to perform the merging operation to supplement the required 1 subtree
m-order B-tree with n keywords should
n
+
1
n+1
n+1 nodes
(the leaf node of the B tree corresponds to the failure of search. Yes
n
n
The probability of failure is
n
+
1
n+1
n+1 species
Q: Suppose a file gets 100 initial merging segments (initial sequence) after internal sorting. If multi-channel merging sorting algorithm is used and three times of merging are required to complete the sorting, the minimum number of merging paths is A: 5
Q: A binary tree has four nodes in total. The preorder (first root order) traverses the four nodes of the binary tree and records the values of each node. The result is“ abcd". So, how many possible topologies are there for the binary tree? () A: 14
Cartland number of "Introduction notes to algorithm"
Q: The binary tree is represented by a binary linked list. If you want to exchange the positions of the left and right subtrees of all its nodes, the following () convenient method is more appropriate A: Post order // The preamble can also be implemented
Q: Adjacency multiple list is a chain storage structure of undirected graph and directed graph. ( ) A: error
Adjacency multiple table storage method of graph (super detail)

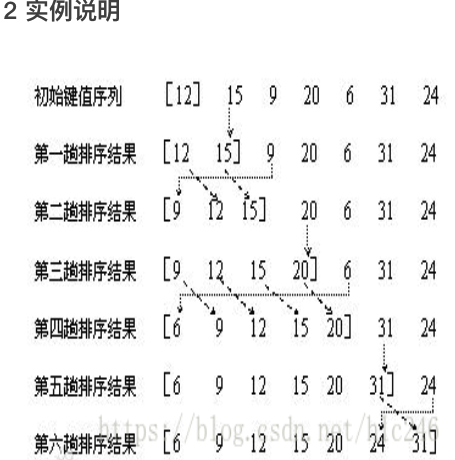
Q: Using the idea of direct insertion sorting method, the time complexity of establishing an ordered linear table is () A: O(n^2)
Specific implementation: Direct insertion sorting of sorting algorithm series
C/C++
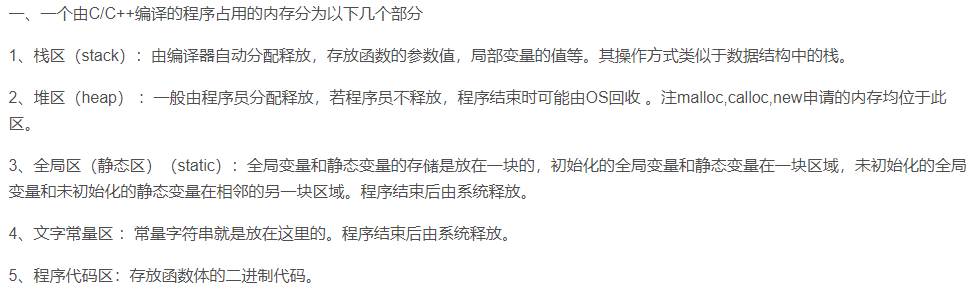
Q: About operating system heap And stack In the statement, the correct one is (). stack Automatically allocated and released by the compiler,Store the parameter values of the function, local variables and global variables heap It is generally allocated and released by the programmer. If the programmer does not release it, it may cause memory leakage of the operating system stack Automatically assigned by the system without programmer intervention, heap Manual application required heap And stack When the initial size space is full, the system will automatically increase its size A: heap It is generally allocated and released by the programmer. If the programmer does not release it, it may cause memory leakage of the operating system stack Automatically assigned by the system without programmer intervention, heap Manual application required
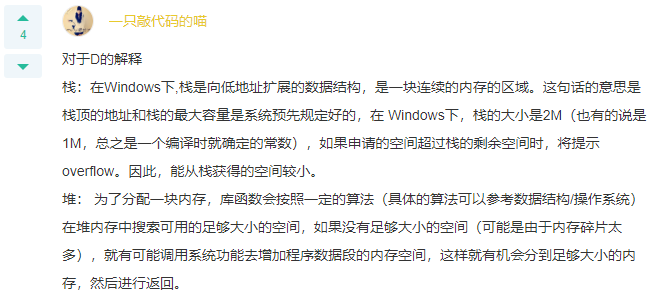
Q: There are the following class definitions:
class A
{
public:
int fun1();
virtual void fun2();
private:
int _a;
};
A: 8

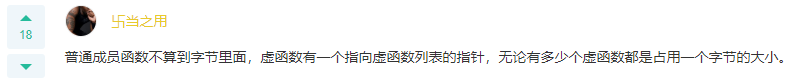
Q: The following description of the storage class that allocates memory for this type of variable only when used is (). A: auto and register
Q: The following description of the type of error is in (). Any form of constructor can implement data type conversion. Constructors with non default parameters can convert basic type data into class type objects. The type conversion function can convert a class type object to another specified type object. Type conversion functions can only be defined as member functions of a class, not as friend functions of a class. A: Any form of constructor can implement data type conversion.
Q: 64 Bit system, defined variables int*a[2][3]How many bytes does it occupy? A: 48
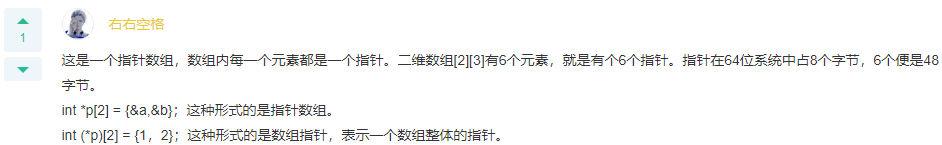
Q: If there are the following descriptions and statements, int c[4][5],(*p)[5];p=c;Can quote correctly c The of array elements is( ). A: *(p[0]+2)
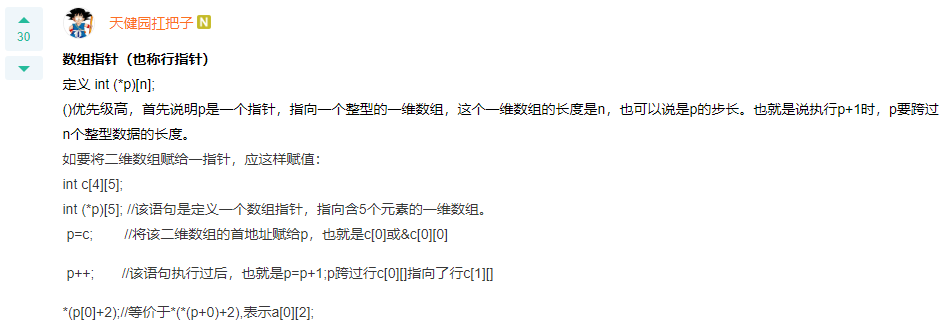
Q: [[single choice] in 32-bit system, for the following structure A and B,sizeof(A),sizeof(B)The results are ()
#include <stdio.h>
#pragma pack(2)
struct A
{
int a;
char b;
short c;
};
#pragma pack()
#pragma pack(4)
struct B
{
char b;
int a;
short c;
};
#pragma pack()
int main()
{
printf("sizeof(A)=%d,sizeof(B)=%d\n",sizeof(A),sizeof(B));
return 0;
}
A: 8,12

Q: Here's about const Right? A: To prevent a variable from being changed, you can use const keyword. In a function declaration, const The formal parameter can be modified to indicate that it is an input parameter and its value cannot be changed inside the function For a member function of a class, it is sometimes necessary to specify that its return value is const Type so that its return value is not lvalue
Q: Escape characters are as follows: '\0X41','\0x41','\X41','\x41','\a','\b','\c','\r' The number of wrong escape characters is A: 4 individual
Baidu Encyclopedia - escape characters
Q: There is the following code:
class A
{
public:
A() {}
~A() {}
};
class B : public A
{
public:
B() {}
~B() {}
public:
int a;
};
If: x=sizeof(A),y=sizeof(B),Excuse me? x,y What are the values of?
A: x=1,y=4
Q: stay C++In, a container is a (). A: Standard class template
Q: hypothesis C Used in language programs malloc Requested memory, but not free Drop, then when the process is kill After that, the operating system will generate Memory leak segmentation fault core dump None of the above is true A: None of the above is true

Q: In the following expression, can be used as C The legal expression is (). [3,2,1,0] (3,2,1,0) 3=2=1=0 3/2/1/0 A: (3,2,1,0)

Q: In C++, what does "explicit" mean? what does "protected" mean? // What does "explicit" mean in C + +? What does "protected" mean? explicit-keyword enforces only explicit casts to be valid // Explicit keyword only enforces explicit cast Protected members are accessible in the class that defines them and in classes that inherit from that class.// Protected members can be accessed in the class that defines them and in classes that inherit from that class. Protected members only accessible within the class defining them. All the above are wrong // Protected members can only be accessed in the class that defines them. A: explicit-keyword enforces only explicit casts to be valid Protected members are accessible in the class that defines them and in classes that inherit from that class.
Q: What is true about the following code
extern "C" {
void foo(int) { }
}
"C" representative c language
This code should be in c++In language code
This code tells c++Caller, this is a paragraph C code
use nm see, foo Actually named similar style `__Z4fooi`
A: Answer questions and learn new knowledge

Q: Please find out which errors are in the following program:
int main() {
/* const The content cannot be changed before
* const The pointer cannot change after
* const* Pointer to constant
* *const The pointer itself is a constant
*/
int i = 10;
int j = 1;
const int *p1; // (1)
// const modifier int *p1 indicates that the value of the content pointed to by p1 cannot be changed
// The object can be changed by p1, but the value of the object cannot be modified by p1
int const *p2 = &i; // (2)
// const modifier * p2 indicates that the value of the content pointed to by p1 cannot be changed (it also indicates that int can be in front and behind)
p2 = &j; // (3)
int *const p3 = &i; // (4)
// const modifier p3 indicates that the p3 pointer itself cannot change or p3 can no longer point to other objects
// You cannot change the object pointed to by p3, but you can modify the value of the object pointed to by p3
*p3 = 20; // (5)
*p2 = 30; // (6) Error reporting
p3 = &j; // (7) Error reporting
}
A: 6,7
Q: An application passes dual buffer Dynamically load the data configuration file, and the process is as follows
function reload(){
if(Check that the file exists){
if(Time since last configuration update < threshold){
log(); Ignore updates
return;
}
if(File is not empty && The content of the file has changed){
ret = new_buffer.loadconfig(); // Allocate new buffer memory and load configuration
if(ret != SUCCESS){
log();//Print error log
}
}
switch(old_buffer, new_buffer) // Switch to dual buffer
clear(old_buffer) // Free old buffer memory
}
}
The following situations may occur:
The configuration file is updated frequently, resulting in cpu The load is too high
repeatedly reaload Memory leak after application
Configuration file format error, new_buffer Loading error, service configuration invalid
Due to misoperation, the configuration file is deleted and the service configuration is invalid
A: Configuration file format error, new_buffer Loading error, service configuration invalid

Q: The following description of references and pointers is correct A: A reference can represent a pointer References and pointers are both means to achieve polymorphic effects The reference itself is the alias of the target variable, and the operation on the reference is the operation on the target variable
A reference is not an object. On the contrary, it is just another name for an existing object (that is, it has no own address, or the address we see is the address of the object to which the reference refers)
The reference itself is not an object, so a pointer to the reference cannot be defined. But the pointer is an object, so there is a reference to the pointer
Q: There are the following expressions: int const c = 21; // The value of variable c cannot be changed const int *d = &a; // The value of the content pointed to by the pointer variable d cannot be changed, but the direction of d can be changed int *const e = &b; // The pointing of the pointer cannot be changed. E always points to b, but the value of b can be changed through * e int const *const f = &a; // The pointer cannot be changed, and the direction of the pointer cannot be changed Which of the following expressions will be prohibited by the compiler? *c = 32; // × *d = 43; // × e = &a; // × f = 0x321f; // × d = &b; *e = 34; A: slightly
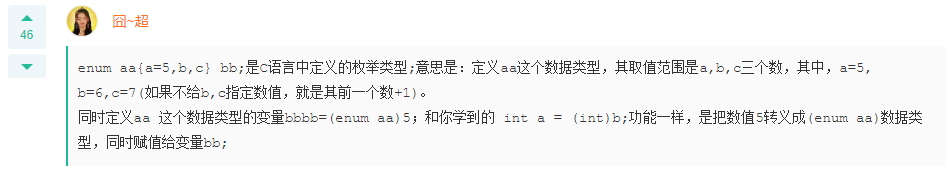
Q: stay C In language, this definition and statement are legal: enum aa { a=5,b,c} bb; bb = (enum aa) 5;Is this statement correct?
A: correct
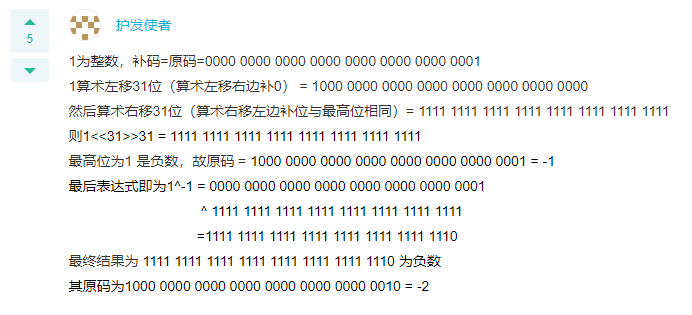
Q: What is the output of the following function:
void func() {
int k = 1^(1 << 31 >> 31);
printf("%d\n", k);
}
A: -2
Signed arithmetic shift right
Unsigned - logical shift right
Q: Among the following functions, which do not belong to the same class as other functions are_____. fread gets getchar pread getline scanf A: pread
Q: c/c++In, the incorrect description of a static member of a class is (). Static members do not belong to objects, but are shared members of classes c++11 Before, non const Static data members of should be defined and initialized outside the class Static member function does not have this Pointer, you need to access object members through class parameters Only static member functions can manipulate static data members A: Only static member functions can manipulate static data members
Q: About shared_ptr What is true is: A: Containers can be used as share_ptr Managed objects
Q: Among the following options, the operators that cannot operate on pointer variables with the same basic type are + - = == A: +

Q: The correct one in the following statement is () Variables can only be defined in the function body, and variables are not allowed to be defined elsewhere The type of constant cannot be distinguished from literal form. It needs to be determined according to the type name The predefined identifier is C A kind of language keyword, which cannot be used for other purposes Both integer and real constants are numeric constants A: Both integer and real constants are numeric constants
Q: An algorithm should have five characteristics such as "certainty". The error in the description of the other four characteristics is (). There are zero or more inputs There are zero or more outputs Poverty feasibility A: There are zero or more outputs
The algorithm has zero or more inputs and at least one or more outputs
The algorithm has no meaning without output
Q: There is such a class:
class Eye
{
public:
void Look(void);
};
Now I want to define a Head Class, also want to implement Look Functions that should be used()Method to realize code reuse.
A: combination
Namely:
class Head {
Eye eye;
};
// but how to implement the Look code?


operating system
Q: Which of the following methods cannot implement the client-Server( Client-Server)Interprocess communication in mode( ) Remote method call( Remote Method Invocation) Remote procedure call( Remote Procedure Calls) Socket programming( Sockets) Messaging system( Message Passing Systems) A: Messaging system( Message Passing Systems)
Q: In a file system, FCB Account for 64 B,The size of a disk block is 1 KB,The primary directory is adopted. It is assumed that there are 3200 files in the file directory If there are multiple directory entries, the average time required to find a file______Access disk A: 100

Q: In the following statement about the unit of computer storage capacity, the error is () 1KB<1MB<1GB The basic unit is bytes( Byte) A Chinese character needs a byte of storage space One byte can hold one English character A: A Chinese character needs a byte of storage space
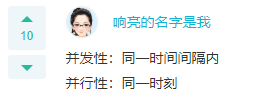
Q: Concurrency refers to multiple events in ()_____simultaneous A: At the same time interval
Q: The title comes from kingcraft forum Assumed variable i,f and d The data types are int,float and double(int Expressed by complement, float and double Use separately IEEE754 Single precision and double precision floating-point format representation), known i=785,f=1.5678e3,d=1.5e100. If the following relational expression is executed in a 32-bit machine, the result is true (). Ⅰ.i==(int)(float)i Ⅱ.f==(float)(int)f Ⅲ.f==(float)(double)f Ⅳ.(d+f)-d==f A: onlyⅠandⅢ
Explain the storage of floating-point numbers in memory
Detailed analysis of addition and subtraction operation at the bottom of floating point number

Q: In the following description of pipe pass, the correct one is( ) Management is a mechanism of mutual exclusion between processes. It ensures that processes can access shared variables mutually exclusive, and it is convenient to block and wake up processes. // ❌ Should be a synchronization mechanism Guan Chenghe P.V Similarly, synchronization operations are scattered among processes. // ❌ Only one process in the management process uses shared resources at a time, so there is no need for synchronous operation Guan Chenghe P.V Similarly, improper use can lead to process deadlock. A management process defines a data structure and a set of operations that can be performed concurrently on the data structure. This set of operations can synchronize the process and change the data in the management process. A: A management process defines a data structure and a set of operations that can be performed concurrently on the data structure. This set of operations can synchronize the process and change the data in the management process.
The function of the pipe process is similar to that of semaphore and PV operation. It belongs to a process synchronization and mutual exclusion tool, but it has different properties from semaphore and PV operation.



Q: Even in a multiprogramming environment, ordinary users can design programs that directly access memory with the physical address of memory. A: error

Q: Under which of the following conditions, computer jitter and oscillation will not occur:( ) cpu The speed is greatly improved, very fast IO Efficiency improvement The memory page of the working area of the program, which is maintained in main memory A single process runs without multi process scheduling Computer CPU Enough cores The memory is large enough not to use swap space A: The memory page of the working area of the program, which is maintained in main memory A single process runs without multi process scheduling The memory is large enough not to use swap space
Q: What are the forms of interprocess communication() A: Socket Pipe Shared memory Signal

Q: In the page storage management system, some page replacement algorithms will appear Belady Abnormal phenomenon, that is, the number of missing pages of a process will increase with the increase of the number of page boxes allocated to the process. In the following algorithms, there may be Belady The of the anomaly is () Ⅰ.LRU algorithm Ⅱ.FIFO algorithm Ⅲ.OPT algorithm A: onlyⅡ
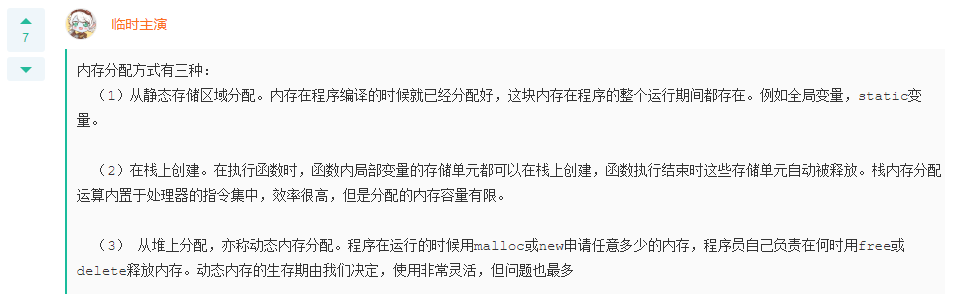
Q: The following description of memory allocation methods and their differences is correct? Allocate from a static storage area. When the function is executed, the storage units of local variables in the function can be created on the stack, and these storage units are automatically released at the end of function execution. The stack memory allocation operation is built into the instruction set of the processor. Create on the stack. Memory has been allocated when the program is compiled, and it exists throughout the running period of the program. For example, global variables, static Variable. Allocation from the heap, also known as dynamic memory allocation. The program is used when running malloc or new The programmer is responsible for when to use any amount of memory free or delete Free memory. The lifetime of dynamic memory is determined by the programmer. It is very flexible to use, but it also has the most problems. None of the above is correct A: Allocation from the heap, also known as dynamic memory allocation. The program is used when running malloc or new The programmer is responsible for when to use any amount of memory free or delete Free memory. The lifetime of dynamic memory is determined by the programmer. It is very flexible to use, but it also has the most problems.
Q: Sequential files are suitable to be built on sequential storage devices, but not on disks. A: error
Q: The following about interrupts I/O Mode and DMA In the narration of mode comparison, the error is (). interrupt I/O The method requested is CPU Processing time, DMA The way to request the right to use the bus is The interrupt response occurs after the execution of an instruction, DMA The response occurs after a bus transaction is completed interrupt I/O In this mode, data transmission is completed by software, DMA In this mode, data transmission is completed by hardware interrupt I/O The method is applicable to all external equipment, DMA This method is only applicable to fast external devices A: interrupt I/O The method is applicable to all external equipment, DMA Fast mode only for external devices
Q: In the following disk scheduling algorithms, what happens to disk adhesion? First come, first served Shortest seek time first All of them Scanning algorithm A: All of them
Q: The title comes from kingcraft forum The following options do not improve the disk device I/O The performance is (). rearrangement I/O Request order Set up multiple partitions on one disk Read ahead and write behind Optimize the distribution of physical blocks of files A: Set up multiple partitions on one disk
Q: When a printout required by a process ends, the process is () and its status will change from () A: Wake up blocked to ready
Blocking, wake-up, suspension and activation of processes
Q: One of the main features of time-sharing operating system is to improve (). A: Interaction of computer system

Q: Variable partition method can effectively eliminate external fragments, but it can not eliminate internal fragments. A: wrong
Fixed partition allocation will generate internal fragments, while dynamic partition allocation will generate external fragments
Paging generates internal fragments and segmentation generates external fragments
Q: In order to prevent users from damaging files when using shared files, you can usually use () method to protect files. A: Specified access
Q: For time-sharing operating systems, CPU The algorithm often used for process scheduling is () A: Time slice rotation
The difference between real-time operating system and time-sharing operating system
Q: When a process is recording a semaphore S Upper execution V(S)After the operation causes another process to wake up, S The value of is ().
A: ≤0
typedef struct {
int value;
struct process *L;
} semaphore;
void wait(semaphore S) { // P operation
S.value--;
if (S.value < 0) {
//add this process to S.L;
block(S.L);
}
}
void signal(semaphore S) { // V operation
S.value++;
if (S.value <= 0) {
//remove a process P from S.L;
wakeup(P);
}
}
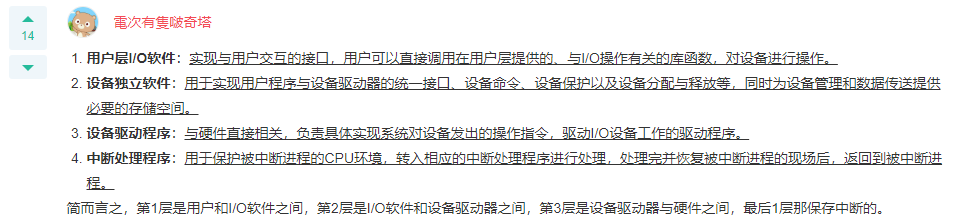
Q: Operating system I/O The subsystem is usually composed of four levels. Each level clearly defines the interface with adjacent levels, and its reasonable hierarchical organization order is (). A: User level I/O Software, device independent software, device driver, interrupt handler

Q: CPU Performance is affected by () factors. I.Word length; II.Master clock cycle; III Size of instruction set A: l,II,and III

Q: Changing the logical address in the job address space into the physical address in memory is called () A: Relocation
Q: Two cooperation processes cannot use () to transfer information database file system High level language global variables Shared memory A: High level language global variables
Q: stay Windows Of the following statements about fast formatting disks, the correct one is ( ) . A: Quick format can only be used for disks that have been formatted

computer network
Q: Twisted pair cables generally use () connectors and interfaces. A: RJ-45
RJ-45 interface is a network cable interface
9-pin debugging interface in COM port
COM port cannot form a network
Q: Requirements for interconnection of various networks at physical layer () A: The data transmission rate and link protocol are the same
Q: Relationship between baud rate and bit rate Baud rate Bit rate throughput Channel bandwidth A: Channel bandwidth
Rate, also known as data rate, refers to the data transmission rate, which represents the amount of data transmitted per unit time. It can be expressed in two ways: symbol transmission rate and information transmission rate
Symbol transmission rate, also known as Baud rate, indicates the number of symbols transmitted by the digital communication system in unit time. The unit is Baud. 1 Baud indicates that the digital communication system transmits one symbol per second. The symbol can be multi base or binary, and the symbol rate is independent of the base number
Information transmission rate, also known as bit rate, represents the number of binary symbols transmitted by digital communication system in unit time (i.e. the number of bits), and the unit is bit / second
Baud and bit are two different concept names, but there is a certain relationship between symbol transmission rate and information transmission rate in quantity: if a symbol carries an amount of information of N bits, the symbol transmission rate of M baud rate corresponds to the information transmission rate of M n bit s / second
Bandwidth, the "highest data rate" that can pass from one point of the network to another in unit time. The unit is b/s
Relationship between baud rate and bit rate
Q: about HTTP,Which of the following descriptions are accurate ( ) A: HTTP Is based on TCP Application layer protocol above protocol HTTP Is request based/Protocol for response model design HTTP The protocol is a clear text protocol, which is not safe enough HTTP The protocol supports a variety of methods, such as HEAD, DELETE, PUT, TRACE, GET,POST
Q: Which of the following statements describes the role of default routing ( ) A: When there is no other route to the destination host, the host uses the default route to transmit data to a host outside the local network
Default route is the route selected by the router when no other route exists for the destination address in the IP packet. The default router will not use all packets in the routing table.

Q: Some port numbers are reserved for commonly used server applications, also known as well-known ports, and their range is (). A: 0~1023 // 1024 in total
Q: In“ HTTP In the sentence "port 80 is used by default in the protocol", port 80 refers to () A: Web The transport layer port number of the server
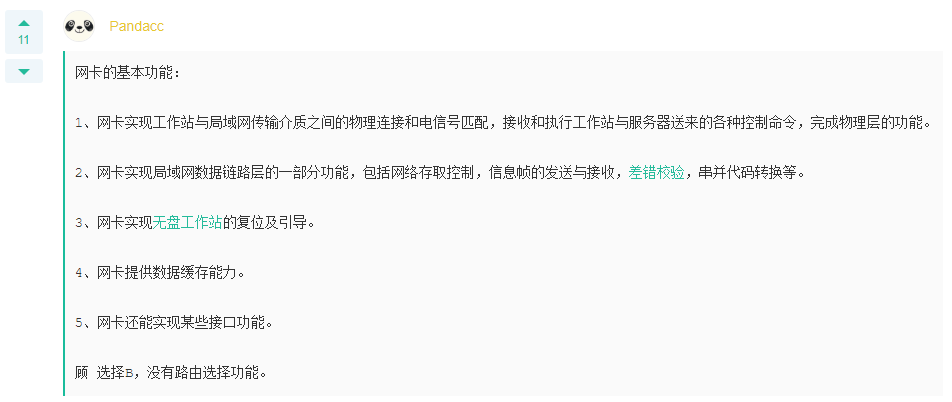
Q: Which of the following is not the basic function of the network card (). data conversion Routing Network access control Data cache A: Routing
Q: Internet The four storey structures of are () A: Network interface layer, network layer, transport layer and application layer
The four layer protocol of TCP/IP: network interface layer (physical layer + data link layer), Internet layer, transportation layer and application layer
Q: about DHCP What is correct is that__________ A: DHCP One can be obtained dynamically IP Address, and its subnet mask, default gateway, and DNS server address
DHCP Dynamic Host Configuration Protocol
- When the host is just started, you need to get an ip address from the DHCP server (you can surf the Internet with an ip address), and broadcast from port 68 to find the DHCP server
- There may be more than one DHCP in the network segment where the host is located. All DHCP receiving broadcast information from port 67 will respond and broadcast the DHCP provided message containing the DHCP configuration information (including an ip address, subnet mask, default gateway, DNS server address, etc.)
- The host will select one of these messages and send DHCP request message to the selected DHCP
- The selected DHCP server sends a confirmation message DHCPACK, and the host can use this ip address
Q: Forwarding and routing are the same concept. Both refer to that when the switching node receives a packet, it looks up the forwarding table according to its destination address and sends the packet. ( ) A: error

Q: about HTTP Which of the following statements is not true ()? There is a status, and there is an association between the previous and subsequent requests // HTTP is stateless. When the same client accesses the page on the same server for the second time, the response of the server is the same as that of the page accessed for the first time FTP You can also use HTTP agreement // TCP protocol is used, and there is no case of who uses who on the same layer of HTTP and FTP HTTP The response includes a digital status code, and 200 represents the correct return of the request HTTP and TCP,UDP In the network hierarchy, there are protocols at the same level // TCP and UDP are of transport layer A: slightly
Q: One SNMP What are the components of the message? ( ) A: edition Head security parameter SNMP Data part of message
SNMP simple network management protocol
Use connectionless UDP, server port 161 and client port 162
Q: The following are computer network protocols TCP/IP MAP IPX/SPX V.24 A: TCP/IP IPX/SPX
Q: Socket,Socket is a pair of TCP / IP Programming call interface encapsulated by protocol. socket The main types of use are: A: be based on TCP Protocol, which provides reliable byte stream service in the way of stream be based on UDP Protocol, using data message to provide data packaging and sending service
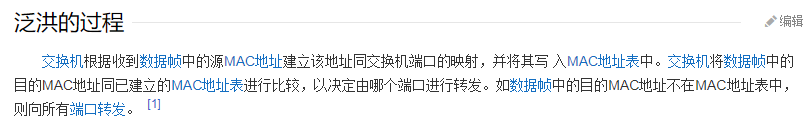
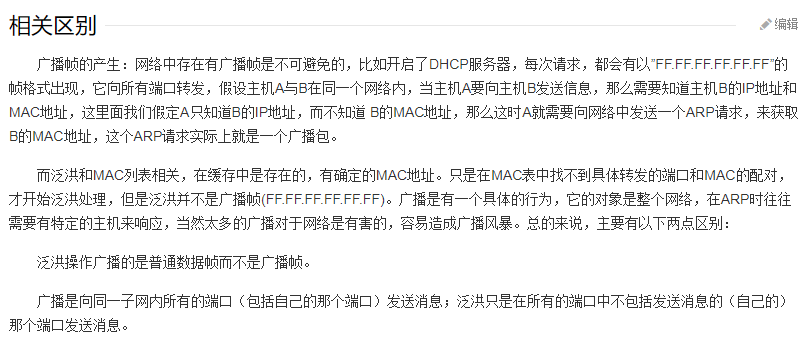
Q: When the switch receives a frame, but the target of the frame MAC At the of the switch MAC The address table cannot be found. Will the switch? ( ) A: flooding
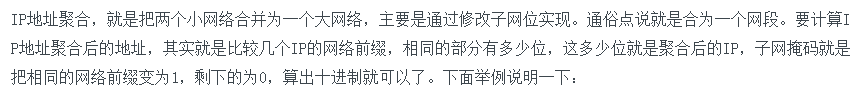
Q: IP The address block is 211.168.15.192/26,211.168.15.160/27 And 211.168.15.128/27 The number of available addresses of the three address blocks after aggregation is ()? A: 126
address aggregation: all hosts connected to the same network correspond to an entry in the forwarding table, that is, prefixes are allowed to represent a group of addresses.
Q: Office computer of a company DHCP obtain IP Address. One day, all computers failed to obtain the address. Access is denied internet,Network administrator view IP Address, possibly () 172.16.2.1 169.254.2.1 169.254.2.255 169.254.255.255 A: 169.254.2.1
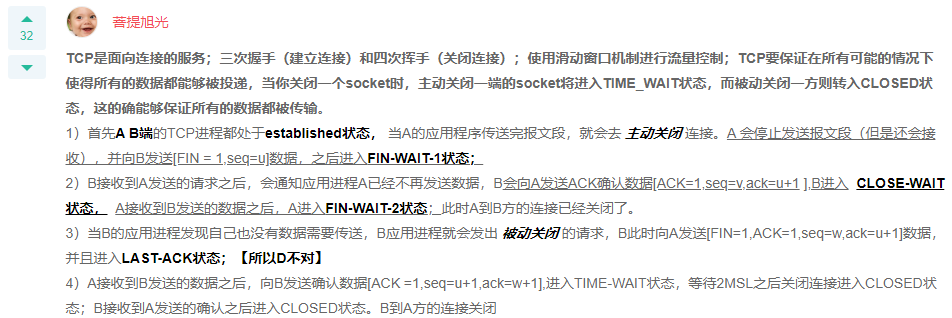
Q: Related below TCP What's wrong with the description of the agreement? TCP Use window mechanism for flow control because TCP The connection is full duplex, so each direction must be closed separately, requiring four handshakes TCP Connection establishment requires three handshakes Passive shutdown socket After that, you will enter TIME_WAIT state A: Passive shutdown socket After that, you will enter TIME_WAIT state
Q: Limited broadcasting is to limit broadcasting to a minimum.The range is: () A: Within this network
Limited broadcast address and direct broadcast address
Broadcast address: all destination mac addresses are 1
Limited broadcast address: the destination IP address is all 1, and the source address is all 0
Function: when the computer starts up, because it doesn't know its subnet, ask the network IP address server DHCP to obtain an IP address
Direct broadcast address: destination IP address: network number + host number are all 1
Function: find neighbors or notify everyone else in the network
DHCP Dynamic Host Configuration Protocol
Q: The following is about 100 BASE-T The error in the description of is (). The data transmission rate is 100 Mbit/S The signal type is baseband signal Use category 5 UTP,Its maximum transmission distance is 185 M It supports two networking modes: sharing and switching A: Use category 5 UTP,Its maximum transmission distance is 185 M
Q: Dynamic routing protocol compared to static routing protocol (multiple choice) () Less bandwidth // x simple // x Routers can automatically detect network changes // √ The router can automatically calculate new routes // √ A: slightly
Q: The following description of the Internet routing protocol is wrong (). The Internet adopts static and hierarchical routing protocol. RIP It is a routing protocol based on distance vector, RIP Select a route (shortest route) with the least routers to the destination network. OSPF The most important feature is that using distributed link state protocol, all routers can finally establish a link state database (topology diagram of the whole network). BGP-4 Path vector routing protocol is adopted. BGP The network accessibility information exchanged is the sequence of autonomous systems to reach a network. A: The Internet adopts static and hierarchical routing protocol.
Internal gateway protocol:
RIP routing information protocol
Using distance vector protocol
RIP allows a path to contain up to 15 routers
Features: only exchange information with adjacent routers; The information exchanged is all the information known to the router at present, that is, its current routing table; Exchange information at regular intervals
UDP is used for transmission, and the port number is 520
A RIP message includes up to 25 routers, and the maximum length of the message is 504 bytes
Disadvantages: when the network fails, it takes a long time to transmit this information to all routes (good news spreads fast and bad news spreads slowly)
Advantages: simple implementation and low overhead
OSPF open shortest path priority 159
Using distributed link state protocol
Features: send information to all routers in the system (this method is called flooding method); The information sent is the link status of all routers adjacent to the link; The flooding method is used to send this information only when the link changes
The update process converges faster
The use of hierarchical regional division greatly reduces the traffic of information
The IP datagram is directly used for transmission, and the protocol field value in the header of the IP datagram is 89
External gateway protocol:
BGP border gateway protocol 163
Using path vector routing protocol
The purpose is to find a better route (at the boundary of autonomous system) that can reach the destination network, not the best route
Use TCP port number 179
The information exchanged is a series of autonomous systems to reach a network
The message size is 19 ~ 4096 bytes
database
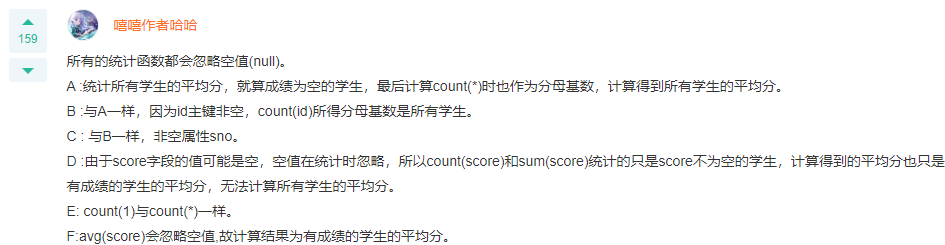
Q: The structure of the table is as follows: CREATE TABLE `score` ( `id` int(11) NOT NULL AUTO_INCREMENT, `sno` int(11) NOT NULL, `cno` tinyint(4) NOT NULL, `score` tinyint(4) DEFAULT NULL, PRIMARY KEY (`id`) ) ; The results of the following query statements must be equal () A.SELECT sum(score) / count(*) FROM score WHERE cno = 2; B.SELECT sum(score) / count(id) FROM score WHERE cno = 2; C.SELECT sum(score) / count(sno) FROM score WHERE cno = 2; D.SELECT sum(score) / count(score) FROM score WHERE cno = 2; E.SELECT sum(score) / count(1) FROM score WHERE cno = 2; F.SELECT avg(score) FROM score WHERE cno = 2; A: D,F A,B,C,E
About the value represented by tinyint- What is the difference between tinyint (4) and tinyint (80)
Q: If you want to delete a trigger from the database, you should use SQL Language commands () DELETE TRIGGER DROP TRIGGER DISABLE TRIGGER REMOVE TRIGGER A: DROP TRIGGER

Q: The database system achieves data independence because it adopts (). A: Three level mode structure
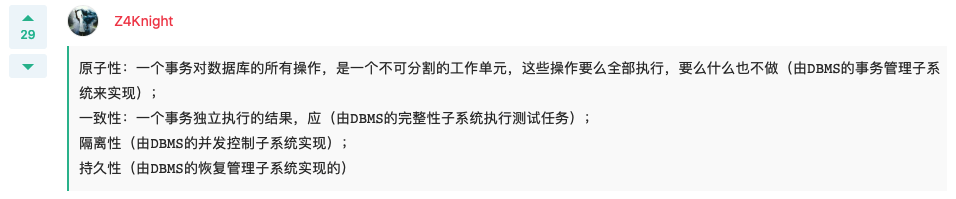
Q: There are two transactions T1,T2,The concurrent operation is shown in Figure 2. The following evaluation is correct( ).
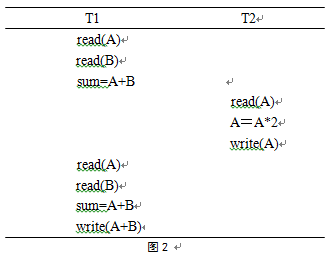
There is no problem with this operation The operation is missing modifications This operation cannot be read repeatedly This operation reads "dirty" data A: This operation cannot be read repeatedly
Q: Transaction isolation is determined by DBMS Yes (). A: Implementation of concurrency control subsystem
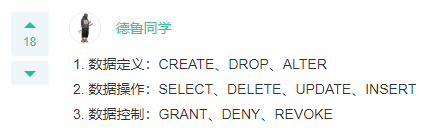
Q: SQL Language has the function of (). A: Data definition, data manipulation and data control
Q: In the transaction dependency graph, if the dependencies of two transactions form a cycle, then( ). A: System deadlock

Q: SQL Language is the language of (). A: Non process

Q: Blocking can avoid data inconsistency, but it may cause( ). A: Several transactions wait for each other to release the blockade

Q: The cloud computing service type that takes the platform as a service is SaaS A: error
Q: In a relationship R If each data item is indivisible, then R Must belong to () A: First paradigm

software test
Q: Which of the following test methods does not belong to the white box coverage standard () Basic path Boundary value analysis Cyclic coverage Logical coverage A: Boundary value analysis
Q: Bottom up integration requires testers to write drivers. Please judge whether this sentence is correct or not. A: T

software engineering
Q: ISO The software quality evaluation model consists of three layers, in which the criterion for evaluating design quality is () A: SQDC // software qualtity design comment. Software quality design evaluation
Q: Judge the relationship between the following classes and fill in the corresponding numbers in brackets. student – Freshmen () A: commonly-special // emmm doesn't understand why it's not a whole - part
Q: One of the commonly defined methods in software engineering is the structured life cycle method( SLC Method), which of the following statements does not have SLC Main features of the method () Strictly define requirements Division of development stages Standardize document format Analysis control process A: Analysis control process
Knowledge blind spot
Operation and maintenance
Q: The following are not database optimization techniques Separate data, log and index to different high-performance I/O equipment Aggregate tables vertically and horizontally to reduce the number of tables use OR Can be decomposed into multiple queries, and UNION Multiple queries Put the data processing on the server,For example, you can use multiple storage processes A: Aggregate tables vertically and horizontally to reduce the number of tables
JAVA
Q: Which statement declares a variable a which is suitable for referring to an array of 50 string objects?(Java) A: String a[]; String[] a; Object a[];
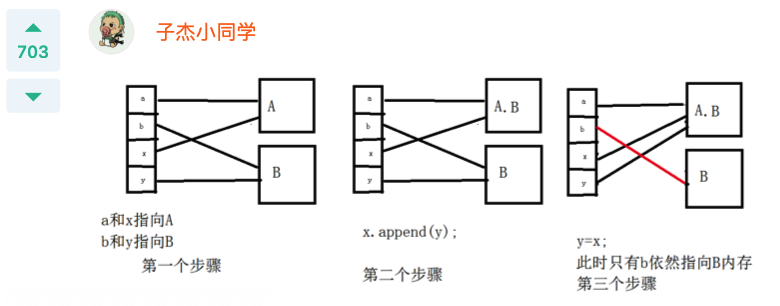
Q: What is the result of the following code?
public class foo {
public static void main(String sgf[]) {
StringBuffer a=new StringBuffer("A");
StringBuffer b=new StringBuffer("B");
operate(a,b);
System.out.println(a+"."+b);
}
static void operate(StringBuffer x,StringBuffer y) {
x.append(y);
y=x;
}
}
A: The code can be compiled, run and output“ AB.B".
Q: Java Collection classes in include ArrayList,LinkedList,HashMap The following description of collection classes is correct () ArrayList and LinkedList All realized List Interface // √ ArrayList Access speed ratio LinkedList fast // √ When adding and deleting elements, ArrayList Better performance // x costs a lot HashMap realization Map Interface, which allows any type of key and value object, and allows null Used as a key or value // √ the object is OK, but not if it is changed to basic type A: slightly
Fundamentals of programming
Q: In the following about SPOOLing In the narration of, what is not correct is () SPOOLing The system makes use of the ability of processor and channel to work in parallel. SPOOLing The system speeds up the execution of the process. SPOOLing The system turns an exclusive device into a shared device. SPOOLing The main purpose of the system is to improve I/O Equipment efficiency. A: SPOOLing The system speeds up the execution of the process.
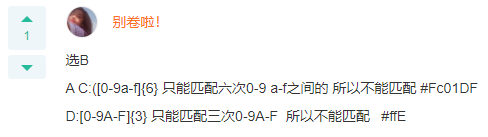
Q: It is required to match the following hexadecimal color values. The regular expression can be: #ffbbad #Fc01DF #FFF #ffE
A: /#([0-9a-fA-F]{6}|[0-9a-fA-F]{3})/g
Q: display C Under the root directory B5.PRG Document content DOS The command is( ) A: TYPE C: \B5.PRG
emm DOS is not commonly used, so I don't remember
Q: There are many technical indicators of computers, and the most important one should be ______ . A: Main frequency, word length and memory capacity
Q: Implicit instruction refers to_____. A: There are no instructions in the system

Linux
Q: You through editing/etc/group The file has changed sales group of GID,All team members can successfully make the conversion, except Jack,He can't even log in. What's the reason? A: stay/etc/passwd It's indicated in the Jack of GID
Q: Exiting unix If a process needs to continue running after the system account, it can be used () awk sed crontab nohup A: nohup
Q: file exer1 Your access rights are rw-r--r-- ,To increase the execution permission of all users and the write permission of users in the same group, the following commands are correct chmod a+x,g+w exer1 chmod 775 exer1 chmodo+x exer1 chmodg+w exer1 A: chmod a+x,g+w exer1 chmod 775 exer1

Q: linux tcpdump Monitor network card eth0,Opposite host IP For 10.1.1.180,tcp For data with port 80, the corresponding command is? A: tcpdump -i eth0 -nn 'tcp and port 80 and host 10.1.1.180'
Q: What command is used to query, not really to find the file system on the hard disk, but to retrieve the file name database, and wildcards can be used? and*? whereis find locate type A: locate

Q: stay Linux Built in the system DHCP If it is necessary to specify the default gateway address for the client when using the server, it is 192.168.1.1,Can be in dhcpd.conf Set () in the configuration file A: option routers 192.168.1.1;
Q: In order to view the constantly updated log files, the command you can use is () cat -n vi more tail -f A: tail -f
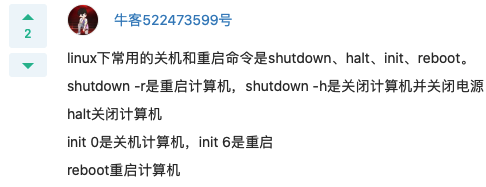
Q: close linux The system (without restarting) can use the command. Ctrl+Alt+Del // restart halt shutdown -r now // Restart now reboot A: halt

Network foundation
Q: HTTP CODE What does 403 mean? A: The server received the request but refused to provide service
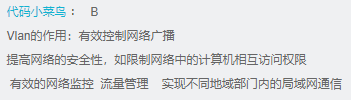
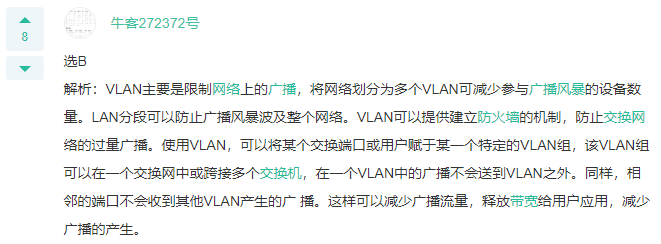
Q: VLAN What are the main functions of? Ensure network security Suppress broadcast storm Simplify network management Improve network design flexibility A: Suppress broadcast storm
Q: The method of representing digital signals "1" and "0" by changing the frequency of carrier signal is called ( ) AM // amplitude modulation FM // frequency modulation PM // Phase modulation A: FM
Q: The following belong to DDOS The attack methods are () A: SYN Flood NTP Amplification attack CC attack
Q: Internet computers must follow unified rules when communicating with each other, which is called security specification. ( ) A: error
Q: Twisted pair is composed of two mutually insulated and uniformly twisted threaded wires. The following description of twisted pair is incorrect () Its transmission rate is up to 10 Mbit/s~100Mbit/s,Even higher, the transmission distance can reach tens of kilometers or even more It can transmit both analog and digital signals Compared with coaxial cable, twisted pair cable is easy to be disturbed by external electromagnetic wave, and the line itself also produces noise, with high bit error rate Usually only used as LAN communication medium A: Usually only used as LAN communication medium
Q: Asynchronous transfer mode ATM A () packet called a cell is used and transmitted using a () channel. A: Fixed length, optical fiber
Q: Theoretically, the maximum transmission distance of thin coaxial cable is? A: 185 rice
Q: ISDN Full duplex data channel for network voice and data transmission( B Channel) rate is (). A: 128 kbps

Q: The error detection code adopts redundant coding technology, that is, enough redundant information is added to each transmitted data block, so that the transmission error can be found and corrected automatically at the receiving end. Is this statement correct? A: error

Q: Related below Cookie What's wrong is Cookie Not just one Cookie It is always saved in the client. According to the storage location in the client, it can be divided into memory Cookie And hard disk Cookie stay HTTP In request Cookie It's ciphertext somewhat Cookie It is deleted when the user exits the session, which can effectively protect personal privacy A: stay HTTP In request Cookie It's ciphertext
Compilation and architecture
Q: For the segmentation of memory by a series of microcomputers, if the maximum word storage unit (16 bit binary) of each segment is 32 K,Then the binary digits representing the byte unit offset address in the segment should be (). A: 16 position
Q: Implement task level, instruction level and program level parallelism is () SIMD MIMD SISD MISD A: MIMD

Q: The content of computer system structure research does not include () Definition of instruction system Definition of software and hardware interface Structure of adder Evaluation of computer system performance A: Structure of adder
Q: Power carrier technology is the use of 220 V The power line transmits the low-frequency signal sent by the transmitter to the receiver, so as to realize intelligent control. A: error
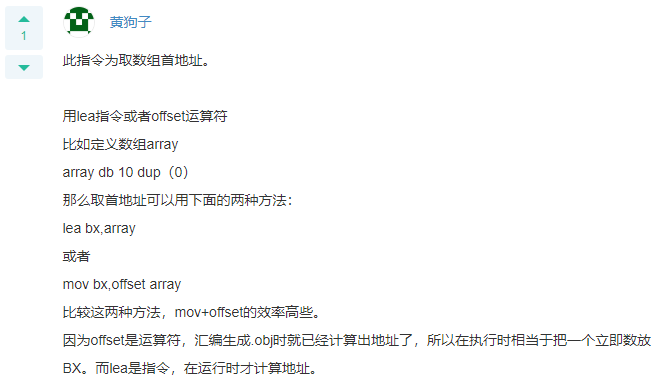
Q: And LEA BX, ARRAY The instructions with the same function are( ) A: MOV BX,OFFSET ARRAY
Q: The expression expressed by inverse Polish method is also called prefix expression. ( ) A: error // Polish is the prefix expression
Q: ZigBee Network equipment( ), can only send messages to FFD Or from FFD Receive information. A: Reduced function equipment( RFD)
ZigBee communication technology all know
Q: ZigBee (): When a node is added or deleted, the node location changes, the node fails, etc., the network can repair itself, and adjust the network topology accordingly without manual intervention to ensure that the whole system can still work normally. A: Self healing function
Q: Of the following options, in I/O The information transmitted on the data line of the bus includes (). Ⅰ. I/O Command word in interface Ⅱ. I/O Status word in interface Ⅲ. Interrupt type number A: Ⅰ, Ⅱ, Ⅲ
Q: Wireless sensor network related standards (). A: Technical standard for interface between sensor and communication module Technical standards of node equipment, etc
Q: The code that generates Boolean expressions and control flow statements by single pass scanning must use backfill technology. Is this statement correct? A: yes
Q: The machine oriented language that uses mnemonics instead of opcodes and address symbols instead of operands is () A: assembly language
Q: The "data width" of byte multichannel is (). A: Single byte

Q: Conditional transfer instruction JB The conditions for program transfer are () A: CF=1
front end
Q: Which of the following are block level elements () input // Inline wrap element ul hr li div form A:
https://www.nowcoder.com/test/question/done?tid=43233547&qid=55058#summary
Q: stay HTML5 In, you can directly SVG Element embedding HTML Page. A: correct
SVG means Scalable Vector Graphics.
SVG uses XML format to define images.
SVG tutorial - rookie tutorial
Q: When using the map for image search, you can drag and drop a picture from the computer desktop to the input box of the map page, which is used HTML5 Yes () API Implemented. ( ) history File system images A: File
https://developer.mozilla.org/zh-CN/docs/Web/API/History_API
https://developer.mozilla.org/zh-TW/docs/Web/API/File/Using_files_from_web_applications