1. Create a private CA and apply for a certificate.
1.1 create CA related directories and files
[22:05:51 root@centos8 data]#mkdir -pv /etc/pki/CA/{certs,crl,newcerts,private}
mkdir: created directory '/etc/pki/CA'
mkdir: created directory '/etc/pki/CA/certs'
mkdir: created directory '/etc/pki/CA/crl'
mkdir: created directory '/etc/pki/CA/newcerts'
mkdir: created directory '/etc/pki/CA/private'
[22:06:09 root@centos8 data]#tree /etc/pki/CA
/etc/pki/CA
├── certs
├── crl
├── newcerts
└── private
4 directories, 0 files
vim /etc/pki/tls/openssl.cnf
[ CA_default ]
dir = /etc/pki/CA # Where everything is kept
certs = $dir/certs # Where the issued certs are kept
crl_dir = $dir/crl # Where the issued crl are kept
database = $dir/index.txt # database index file.
#unique_subject = no # Set to 'no' to allow creation of
# several certs with same subject.
new_certs_dir = $dir/newcerts # default place for new certs.
certificate = $dir/cacert.pem # The CA certificate
serial = $dir/serial # The current serial number
crlnumber = $dir/crlnumber # the current crl number
# must be commented out to leave a V1 CRL
crl = $dir/crl.pem # The current CRL
private_key = $dir/private/cakey.pem# The private key
According to the definition in the configuration file, create index.txt and serial file
[22:09:05 root@centos8 CA]#touch /etc/pki/CA/index.txt
[22:09:30 root@centos8 CA]#echo 01 > /etc/pki/CA/serial
1.2 create private key of CA
[22:14:10 root@centos8 CA]#tree . ├── certs ├── crl ├── index.txt ├── newcerts ├── private │ └── cakey.pem └── serial 4 directories, 3 files [22:14:17 root@centos8 CA]#cat private/cakey.pem -----BEGIN RSA PRIVATE KEY----- MIIEowIBAAKCAQEA16BJ4fmgqUUKJTJyQ927j+p+IEJ+oQXNLCHf+/QZtHP5sPCF X+KWjK4p621Jv9hEZ6GUaRxfmB52tLmXpbm9lYssPXPdMa4C7faST9mQjPn7riKF FIKZqiN4uJJdCBSG+rUSB/w3LEAGlHgTAQw1Zy4MaZApE8Oko1PSzqG1CuGMn1BI mIWjy1kxCckWWTwHpPp7fb0ai7EJnaiEgyjcA3UKWR9ze7Qhr4ZI9jXo/+8URQHr 35J+gs1YCSEnIOyEQECsZk4mIFpTQgqBgDh5U2QRZDuuFvmx2Ev7DOJ8mlv5NRni YE5G1Rk9SLcP0puyZqWnZKfr6OgqPd2+tImDMwIDAQABAoIBAG4f1/wIYMxyjTbo J8GPeh6LVXUmYMPeUaYretiUF5i47po2jPemotsgjBpIC7VmP7FprYFtU0k+rcOp UdD7Jt88YBDWnu6jf62HE7yiUhgeCDMsQCl0dgSV7y7c2ZSp3zIlzhqz7n20CWhE VvhfAts6gm5biQ8mCWy8/9o2bl8qWFuH6N2IffioO8V0cbYDSj/11e1sH757V5yH jaQrCNEvUBOZ1wHOWWqhXNJ0zSTPf8xCaVQ+kGMdCwygex5HXbA6f/NRg0p2Mjmi +2VC2lbgzU4HgHWqvfyC3jlfvrZ2hmBPovWWaXcHTAqL0mQMsrPpo5KhE3ah+kUB kTol2NkCgYEA9DhEx2rSJZaI33hJVZWhEP4IsXY1Vck/+jmqhrH12jNzOx5yhjGP RzFkH5YBAN+ftZDLK5i6byKRYUPY6RXaeD046UcB5xnfonPLXRcCQjb4vMH6z6RI LDVOpLwP0/GeT9UQLCTaZZsNLKfKax3aS8eOd2kKFACzrAtig4rEta0CgYEA4gbu 1dfScTfZPbUzPqFoxcjVfaxgTS/xe+BsQ9U3lq32hq1RdHR/hhHXXUWMFCk9DB5F 1j7gCkjXk8mTmLGuB2UyPXe3s6QORtxyuwOV3o9MHbRGR8AEcOw/SKdfX6dJLXL9 mD24rUZ+L7aEU8Gap+lJA1woUyfh4hnS+sQFeF8CgYBpWpzRKlPdw0LopIt+UD5b hjtZ0xTPHTJsT9QwpzTYHLnpFwlwupCEtdnrhlqIde//86ax+AD1UIRG4W4Bn1vP 4xlaCTfY6mB/RFTGo9ZlmjFTvJrmWIiKCbUTe82YMPOKnO+NG5jbnDfiu7+m1goG BuB+wuGGH4djAMZO2N5jQQKBgBNNnkYbCXjr2RzBBeBabpU9oqX5+7t71bbLotNk OTwgHUbBNIyqil2L1oW7s8vg/bq0Nyil9AJM2ERh2b4XppIxHUpMmB66axG4MAAy vTDlsg1zYPEtv/NY6cqtqKKFqeU8xdWjp8r8kzhF8SUqCqg+byLfUv5PEKZ7qB4M cZ8nAoGBAMje3kjW+U6mq5gTMRNdfVlRjdz++kQ6Z35dC81AyAVbihpW7gK/tf0A nI9xJZ8t3PB6A6RGEmtrjsO9eORcuoLeWwAnjBHiNgdW2YkUTzwsvvENvKogDQkD uO80GYxeGLaIQo1VT+EvW970bVHiDEWgVDSGmo0rvSUHWRf/2m4p -----END RSA PRIVATE KEY----- [22:14:40 root@centos8 CA]#ll private/cakey.pem -rw-------. 1 root root 1675 Dec 13 22:14 private/cakey.pem
1.3 issue self signed certificate to CA
[22:17:19 root@centos8 CA]#openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 3650 -out /etc/pki/CA/cacert.pem
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:cn
State or Province Name (full name) []:shandong
Locality Name (eg, city) [Default City]:jn
Organization Name (eg, company) [Default Company Ltd]:magedu
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) []:ca.magedu.org
Email Address []:
[22:17:44 root@centos8 CA]#
[22:17:45 root@centos8 CA]#
[22:17:45 root@centos8 CA]#tree
.
├── cacert.pem
├── certs
├── crl
├── index.txt
├── newcerts
├── private
│ └── cakey.pem
└── serial
4 directories, 4 files
[22:21:02 root@centos8 CA]#cat cacert.pem
-----BEGIN CERTIFICATE-----
MIIDUzCCAjugAwIBAgIUKc/T12l1ZX85q3Nj3U4KTTBYdkowDQYJKoZIhvcNAQEL
BQAwOTELMAkGA1UEBhMCY24xFTATBgNVBAcMDERlZmF1bHQgQ2l0eTETMBEGA1UE
CgwKbWFnZWR1Lm9yZzAeFw0yMTEyMTMxNDE3NDRaFw0zMTEyMTExNDE3NDRaMDkx
CzAJBgNVBAYTAmNuMRUwEwYDVQQHDAxEZWZhdWx0IENpdHkxEzARBgNVBAoMCm1h
Z2VkdS5vcmcwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDXoEnh+aCp
RQolMnJD3buP6n4gQn6hBc0sId/79Bm0c/mw8IVf4paMrinrbUm/2ERnoZRpHF+Y
Hna0uZelub2Viyw9c90xrgLt9pJP2ZCM+fuuIoUUgpmqI3i4kl0IFIb6tRIH/Dcs
QAaUeBMBDDVnLgxpkCkTw6SjU9LOobUK4YyfUEiYhaPLWTEJyRZZPAek+nt9vRqL
sQmdqISDKNwDdQpZH3N7tCGvhkj2Nej/7xRFAevfkn6CzVgJIScg7IRAQKxmTiYg
WlNCCoGAOHlTZBFkO64W+bHYS/sM4nyaW/k1GeJgTkbVGT1Itw/Sm7Jmpadkp+vo
6Co93b60iYMzAgMBAAGjUzBRMB0GA1UdDgQWBBSRQDe5X23JWC4iSqPwDQX4PzZd
azAfBgNVHSMEGDAWgBSRQDe5X23JWC4iSqPwDQX4PzZdazAPBgNVHRMBAf8EBTAD
AQH/MA0GCSqGSIb3DQEBCwUAA4IBAQDSvO5+s5RdPavqgCxcoLrqYi2k1HZDmv6b
fs6Y50i8X2etlw2AlR8lAFVg147ueHMC8vdFbe5i5c9X/KMJYnJ9a4KEOyByUEiu
okhK/XMKZBO4afg6LjTh9pCHt83kHrMPkWyd8vYBTyefWG9ODRylbpnAHAg24e8H
ggr9L81HD49VVE6BU1gEsNjC6VIFWk/JCr5gWScSVd1sgkRer3uhx857mR4nfueT
AR5HkoAnMmpeSHKytw4Lm9cZp826Yjyv1sY011k6nRVQWLmiAftwaLEWO0ytecng
pjLgcEL76hra8RZDv9Lb1SrUTebb0GMoTEKpIEGy4w2/G7Dtl9ht
-----END CERTIFICATE-----
[22:21:11 root@centos8 CA]#openssl x509 -in /etc/pki/CA/cacert.pem -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
4e:34:73:46:cc:a8:f4:8a:26:b3:a7:71:d0:97:d3:b4:e4:8a:2c:49
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = cn, ST = shandong, L = jn, O = magedu, CN = ca.magedu.org
Validity
Not Before: Dec 13 14:55:45 2021 GMT
Not After : Dec 11 14:55:45 2031 GMT
Subject: C = cn, ST = shandong, L = jn, O = magedu, CN = ca.magedu.org
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:d7:a0:49:e1:f9:a0:a9:45:0a:25:32:72:43:dd:
bb:8f:ea:7e:20:42:7e:a1:05:cd:2c:21:df:fb:f4:
19:b4:73:f9:b0:f0:85:5f:e2:96:8c:ae:29:eb:6d:
49:bf:d8:44:67:a1:94:69:1c:5f:98:1e:76:b4:b9:
97:a5:b9:bd:95:8b:2c:3d:73:dd:31:ae:02:ed:f6:
92:4f:d9:90:8c:f9:fb:ae:22:85:14:82:99:aa:23:
78:b8:92:5d:08:14:86:fa:b5:12:07:fc:37:2c:40:
06:94:78:13:01:0c:35:67:2e:0c:69:90:29:13:c3:
a4:a3:53:d2:ce:a1:b5:0a:e1:8c:9f:50:48:98:85:
a3:cb:59:31:09:c9:16:59:3c:07:a4:fa:7b:7d:bd:
1a:8b:b1:09:9d:a8:84:83:28:dc:03:75:0a:59:1f:
73:7b:b4:21:af:86:48:f6:35:e8:ff:ef:14:45:01:
eb:df:92:7e:82:cd:58:09:21:27:20:ec:84:40:40:
ac:66:4e:26:20:5a:53:42:0a:81:80:38:79:53:64:
11:64:3b:ae:16:f9:b1:d8:4b:fb:0c:e2:7c:9a:5b:
f9:35:19:e2:60:4e:46:d5:19:3d:48:b7:0f:d2:9b:
b2:66:a5:a7:64:a7:eb:e8:e8:2a:3d:dd:be:b4:89:
83:33
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
91:40:37:B9:5F:6D:C9:58:2E:22:4A:A3:F0:0D:05:F8:3F:36:5D:6B
X509v3 Authority Key Identifier:
keyid:91:40:37:B9:5F:6D:C9:58:2E:22:4A:A3:F0:0D:05:F8:3F:36:5D:6B
X509v3 Basic Constraints: critical
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
b7:bc:60:0b:7d:2a:fe:30:13:fd:c8:37:db:1f:00:70:ad:d4:
b5:00:1b:b0:47:ff:77:97:2c:be:2d:9a:34:09:24:b6:83:df:
97:56:82:e4:26:13:bd:58:ac:3c:41:cb:4e:db:33:46:ec:ee:
1c:15:53:bc:8f:4b:e4:c2:07:a5:9c:dd:9f:10:35:5a:2f:b4:
71:88:b4:d3:db:c4:99:b1:e1:8d:63:84:d2:b4:66:1a:90:69:
8b:c2:90:5c:86:49:2d:4f:66:57:21:2e:95:fe:47:23:f4:92:
43:61:4f:6c:1f:08:21:bb:21:e7:c5:1e:25:42:91:48:be:eb:
9f:60:51:a2:30:44:3a:8b:ea:15:59:b5:9f:1c:e4:5f:cf:73:
59:8f:e1:b7:0f:79:2c:28:38:ac:bf:8e:bb:2a:22:0e:19:a0:
ae:f3:c0:7b:71:e8:63:06:d9:e2:49:63:e0:a9:f5:c3:09:e5:
da:f7:95:3e:e7:96:ba:b5:90:51:98:5e:35:27:9b:1b:6b:86:
d3:a9:1c:b1:d5:dd:0f:6e:35:fc:16:11:21:f6:b8:8a:e1:19:
7f:00:0b:87:14:b0:f5:ad:80:c7:ef:3d:04:c8:ef:50:1a:a7:
dc:fe:99:07:04:90:24:fe:60:d9:b0:e5:ff:e6:5f:9f:c8:f1:
1f:ce:7c:82
1.4 user generated private key and certificate application file
[22:24:38 root@centos8 CA]mkdir /data/app1 [22:25:41 root@centos8 data]#(umask 066;openssl genrsa -out /data/app1/app1.key 2048) Generating RSA private key, 2048 bit long modulus (2 primes) ...............................................................................................................................+++++ .................................+++++ e is 65537 (0x010001) [22:25:52 root@centos8 data]#cat /data/app1/app1.key -----BEGIN RSA PRIVATE KEY----- MIIEpAIBAAKCAQEAruak7Dcnct+OSGCkPglfukSZw9HPlIiqV3TaTfUlazE6U77c Z5lXWJL3USjus+a8Lm7DKJj3aCR6p0wsLM+0G6LT8MZzMzpykBM1cMKQU/2W00RO JgMf6S7Sja9xmeLhQwN/McjcZI9TIxoqlUlGeg4GnwiS2FT5sBPs0cbzhO3CwonY AiglyAkFNJbvVCR7YRvdbp70x0nxL8PYMwd7sUDLH85DVpzajJfXwBuQjtP5pseo pKs/17bLY7j01kGbeSl3z3W3HIu9MuJecUVvo9mYRtFzMnNqbcOhGi5Iw2ZGlRsu 6CL3ugCeKIkWjj4KQ3sE5FITcmbKzgKjqpKaQwIDAQABAoIBADHT9eJyKCP6+r82 ATTHWOVpS+FU8e2gLd9ypAsXr0xlnvdi5coCDrdmT11o6vCH6M7VsXXsdnfOBL+K 3P77QZWqAvWSpBlRKnhPcKcqVxIGqiSQTi9YLowxUb0Z4aR01bZQ1bjqP5fKmWXj u4QCdziorEw8lhFZzDTUyGBPbOtOlNKLOj8Q6+dOW+YIr82mRISy1WQDLIcTm87u w1KCnlSlylLqKAxNUnnWruaGcfw1Bg5l14UsanXbt51XU47uZPbfkaiB1Kskky2Q HdPGFCjdD14MVayY1N+dRd+dwG/OPEoTSW+Ns3OhO1vGIGo1mhRFmmY6eGorgNtV qE7SbYkCgYEA2c3uagN5ZPhNc04J9IWq5VgUZRzoimme1hx9gBNDnd66Buv4/x34 FG0s1Ndy+QV2eZjVZyn6Hfy3qG5yyz5Ybar8andK0sF6d6ROWLadsCtKSqpTwNoR cj3C7qf6JY1/VsxlqYCkEjVVwfyF0slKzlbU70hiU9AWcDA/3+J3YXUCgYEAzZKc +12ywdmycwEL1koNWSwR5yXs3lu/OLYWF2PleX6c4gAwwt1LkpEYNq3YzpBinGA2 3gTKgLgEZSeNsdZMCZO0XBYSxZMdeF5Po8dMVkCynqt7OACD19nCBFSQvdm2kAV7 hCGfPbCWouaLsAcQmWwSBdD1ih/hm+kmrrb/ndcCgYEAt3DPFXDZpGXQ7YVTsyOF XOZDPyoK3NC6W4DhXqZa87LsIPpL26rFD4coFBdlmUC1mRJU4i+jnfAESxLDElTv K2awc4cHeNxFplC3P9aGlyLOznYIVkwUF5DXBiRp9YjoMBW0pf9XsJJFKT3jBDZP D9xoOSRQ1GBVFaY9lfXqMCUCgYBT2Fqiw4KnQg1gjqqvSiDLoAflSTilMLJ7hPjZ rWro9NUz8HPy5qNuMjO4CYwGJCm0MiHux/F4MpXIVCucvxTgSxgi/vXFE83PTFgb Kqxd+aFgyfxFyR/9J9nUPlGSvXuSnknUiIoUdTPbWUDcGOWSTdvD94hOP9aa6qtW U1lKnQKBgQChTAlPi4Q4r/SO0cTAAFQLfa+jXEg9kRdjN9I/3idorhG7Ynj0Cq1i DFZg/X90YgzHeIyAYm+5HzXm5r+yNlyiXRZmb/TyZnthXtV5+Swn2NixLSKhGDlg hzIMNxCAz/4pRCTHTvRs3eZur3syoKj+jAmejrlm6h+fvtwJO3wRsg== -----END RSA PRIVATE KEY----- [22:57:07 root@centos8 app1]#openssl req -new -key /data/app1/app1.key -out /data/app1/app1.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:cn State or Province Name (full name) []:shandong Locality Name (eg, city) [Default City]:jn Organization Name (eg, company) [Default Company Ltd]:magedu Organizational Unit Name (eg, section) []: Common Name (eg, your name or your server's hostname) []:app1.magedu.org Email Address []: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []:
1.5 certificate issued by Ca
[23:35:00 root@centos8 app1]#openssl ca -in /data/app1/app1.csr -out /etc/pki/CA/certs/app1.crt -days 1000
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Dec 13 15:35:30 2021 GMT
Not After : Sep 8 15:35:30 2024 GMT
Subject:
countryName = cn
stateOrProvinceName = shandong
organizationName = magedu
commonName = app1.magedu.org
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
0D:AD:83:06:DE:DE:39:F9:ED:C8:43:0D:6A:44:25:C1:6E:CB:A4:AF
X509v3 Authority Key Identifier:
keyid:91:40:37:B9:5F:6D:C9:58:2E:22:4A:A3:F0:0D:05:F8:3F:36:5D:6B
Certificate is to be certified until Sep 8 15:35:30 2024 GMT (1000 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
1.6 viewing certificates
[23:58:21 root@centos8 app1]#tree /etc/pki/CA /etc/pki/CA ├── cacert.pem ├── certs │ └── app1.crt ├── crl ├── index.txt ├── index.txt.attr ├── index.txt.old ├── newcerts │ └── 01.pem ├── private │ └── cakey.pem ├── serial └── serial.old 4 directories, 9 files [23:59:13 root@centos8 app1]#openssl ca -status 01 Using configuration from /etc/pki/tls/openssl.cnf 01=Valid (V) [23:59:37 root@centos8 app1]#cat /etc/pki/CA/index.txt V 240908153530Z 01 unknown /C=cn/ST=shandong/O=magedu/CN=app1.magedu.org [00:00:05 root@centos8 app1]#cat /etc/pki/CA/serial.old 01 [00:00:27 root@centos8 app1]#cat /etc/pki/CA/serial 02 [00:01:38 root@centos8 app1]#cp /etc/pki/CA/certs/app1.crt /data/app1/ [00:01:55 root@centos8 app1]#ls /data/app1/ app1.crt app1.csr app1.key
1.7 trust certificate
CA certificate
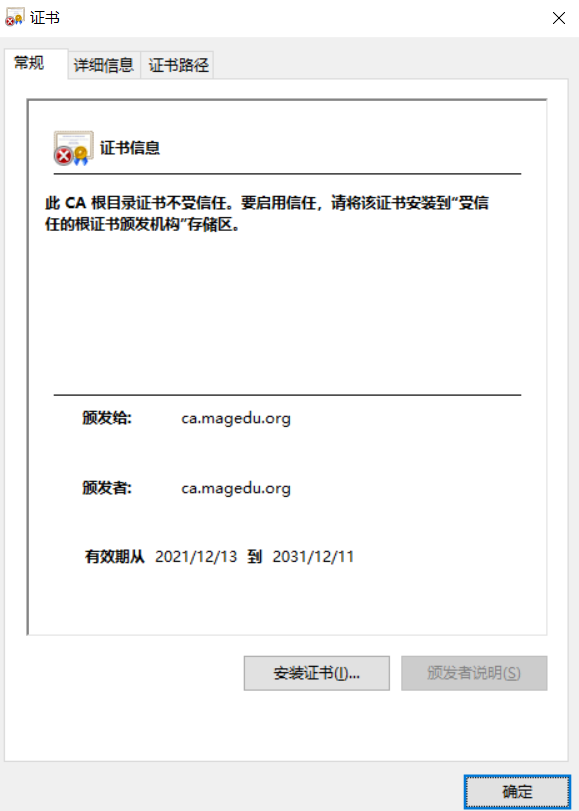
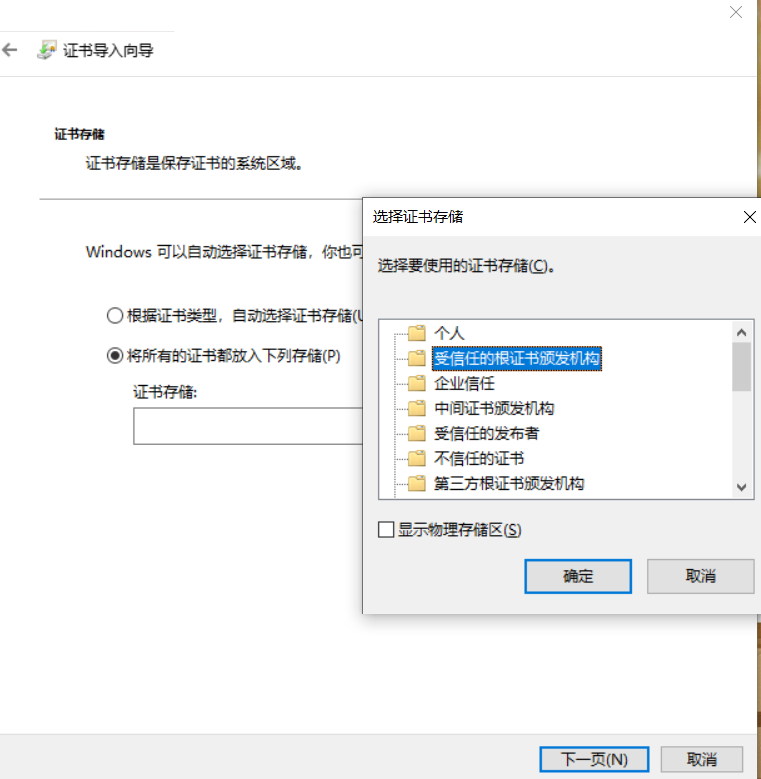
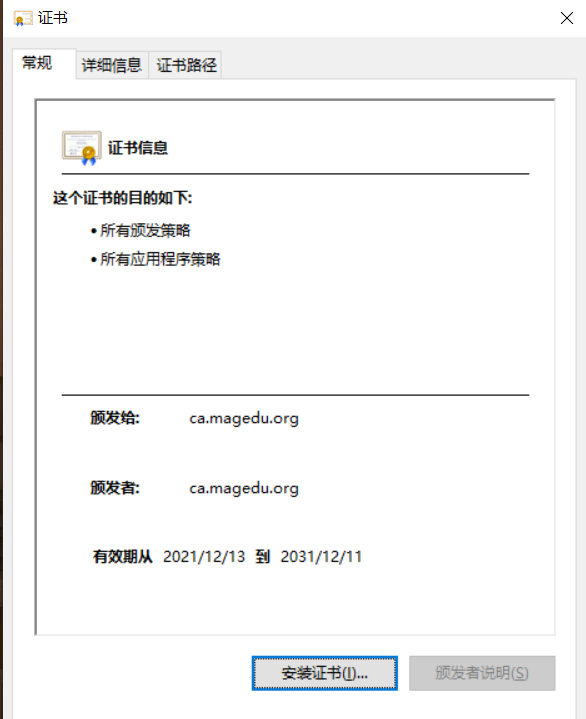
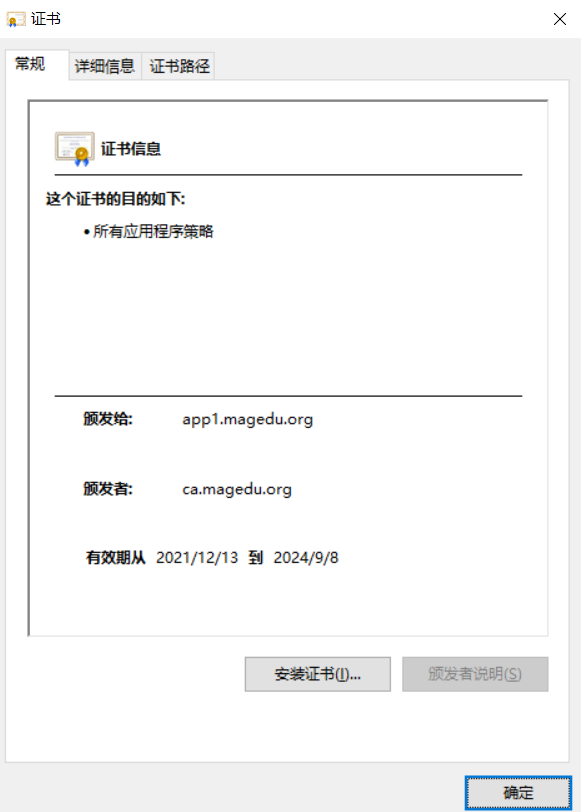
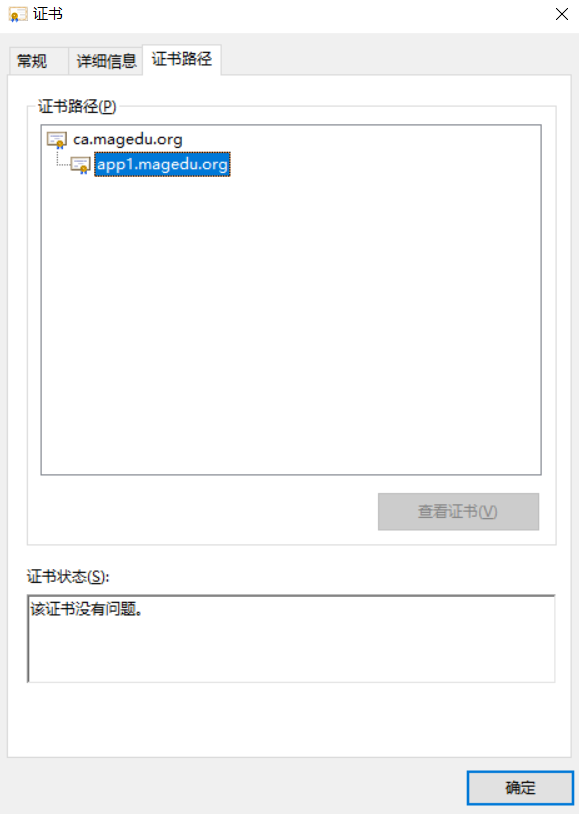
1.8 revocation of certificates
[11:33:39 root@centos8 app1]#openssl ca -status 01 Using configuration from /etc/pki/tls/openssl.cnf 01=Valid (V) [11:33:53 root@centos8 app1]#openssl ca -revoke /etc/pki/CA/newcerts/01.pem Using configuration from /etc/pki/tls/openssl.cnf Revoking Certificate 01. Data Base Updated [11:34:22 root@centos8 app1]#openssl ca -status 01 Using configuration from /etc/pki/tls/openssl.cnf 01=Revoked (R) [11:34:25 root@centos8 app1]#cat /etc/pki/CA/index.txt R 240908153530Z 211214033422Z 01 unknown /C=cn/ST=shandong/O=magedu/CN=app1.magedu.org
1.9 generate certificate revocation list file
[11:37:42 root@centos8 app1]#openssl ca -gencrl -out /etc/pki/CA/crl.pem
Using configuration from /etc/pki/tls/openssl.cnf
/etc/pki/CA/crlnumber: No such file or directory
error while loading CRL number
140616407349056:error:02001002:system library:fopen:No such file or directory:crypto/bio/bss_file.c:69:fopen('/etc/pki/CA/crlnumber','r')
140616407349056:error:2006D080:BIO routines:BIO_new_file:no such file:crypto/bio/bss_file.c:76:
[11:38:10 root@centos8 app1]#echo 01 > /etc/pki/CA/crlnumber
[11:38:45 root@centos8 app1]#openssl ca -gencrl -out /etc/pki/CA/crl.pem
Using configuration from /etc/pki/tls/openssl.cnf
[11:38:48 root@centos8 app1]#
[11:38:49 root@centos8 app1]#cat /etc/pki/CA/crlnumber
02
[11:39:04 root@centos8 app1]#cat /etc/pki/CA/crl.pem
-----BEGIN X509 CRL-----
MIIBxTCBrgIBATANBgkqhkiG9w0BAQsFADBWMQswCQYDVQQGEwJjbjERMA8GA1UE
CAwIc2hhbmRvbmcxCzAJBgNVBAcMAmpuMQ8wDQYDVQQKDAZtYWdlZHUxFjAUBgNV
BAMMDWNhLm1hZ2VkdS5vcmcXDTIxMTIxNDAzMzg0OFoXDTIyMDExMzAzMzg0OFow
FDASAgEBFw0yMTEyMTQwMzM0MjJaoA4wDDAKBgNVHRQEAwIBATANBgkqhkiG9w0B
AQsFAAOCAQEAckP2aDYPGlIh4/Ea9tTvCNTbilG/IZfov6DBMkAwDickZIUIRt9o
xMAKITIwMxtN7RgVPg/r3GTtNc6FWO/6LvGacYopfwtzg1BGFMDUpM2A4TI6OF44
KXbVkXU98uven3PDvT0srnCjnaAesY/A8f9y6XaHcReDCCRSz6ery6EmwSKXXbXn
QRhnf9jxFHvV3VGTJ0IC9wJtD68DwFg0qdz8kJXLNuTEKTH6W/WP3SQG0YTANNiy
GEhW5Mxp+ZIoEllEQRm+qau+2GosmIwlzoq8vmBQX16QfkCS2H0e7C02QNmz1WwJ
Ih4x82l8079MT51aFZOTIPI0iCr6/d1w5w==
-----END X509 CRL-----
[11:40:28 root@centos8 app1]#
[11:40:29 root@centos8 app1]#openssl crl -in /etc/pki/CA/crl.pem -noout -text
Certificate Revocation List (CRL):
Version 2 (0x1)
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = cn, ST = shandong, L = jn, O = magedu, CN = ca.magedu.org
Last Update: Dec 14 03:38:48 2021 GMT
Next Update: Jan 13 03:38:48 2022 GMT
CRL extensions:
X509v3 CRL Number:
1
Revoked Certificates:
Serial Number: 01
Revocation Date: Dec 14 03:34:22 2021 GMT
Signature Algorithm: sha256WithRSAEncryption
72:43:f6:68:36:0f:1a:52:21:e3:f1:1a:f6:d4:ef:08:d4:db:
8a:51:bf:21:97:e8:bf:a0:c1:32:40:30:0e:27:24:64:85:08:
46:df:68:c4:c0:0a:21:32:30:33:1b:4d:ed:18:15:3e:0f:eb:
dc:64:ed:35:ce:85:58:ef:fa:2e:f1:9a:71:8a:29:7f:0b:73:
83:50:46:14:c0:d4:a4:cd:80:e1:32:3a:38:5e:38:29:76:d5:
91:75:3d:f2:eb:de:9f:73:c3:bd:3d:2c:ae:70:a3:9d:a0:1e:
b1:8f:c0:f1:ff:72:e9:76:87:71:17:83:08:24:52:cf:a7:ab:
cb:a1:26:c1:22:97:5d:b5:e7:41:18:67:7f:d8:f1:14:7b:d5:
dd:51:93:27:42:02:f7:02:6d:0f:af:03:c0:58:34:a9:dc:fc:
90:95:cb:36:e4:c4:29:31:fa:5b:f5:8f:dd:24:06:d1:84:c0:
34:d8:b2:18:48:56:e4:cc:69:f9:92:28:12:59:44:41:19:be:
a9:ab:be:d8:6a:2c:98:8c:25:ce:8a:bc:be:60:50:5f:5e:90:
7e:40:92:d8:7d:1e:ec:2d:36:40:d9:b3:d5:6c:09:22:1e:31:
f3:69:7c:d3:bf:4c:4f:9d:5a:15:93:93:20:f2:34:88:2a:fa:
fd:dd:70:e7
[11:40:57 root@centos8 app1]#sz /etc/pki/CA/crl.pem
[11:41:32 root@centos8 app1]#
Modify suffix to crl.pem.crl
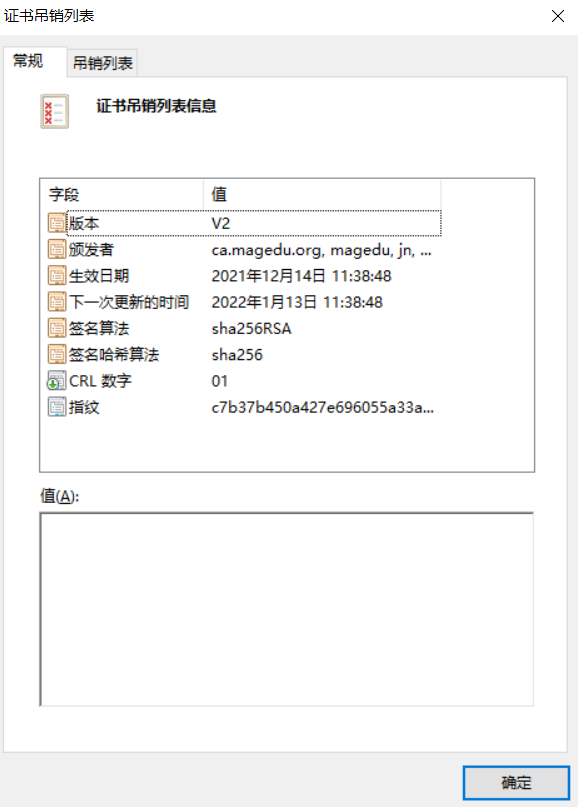
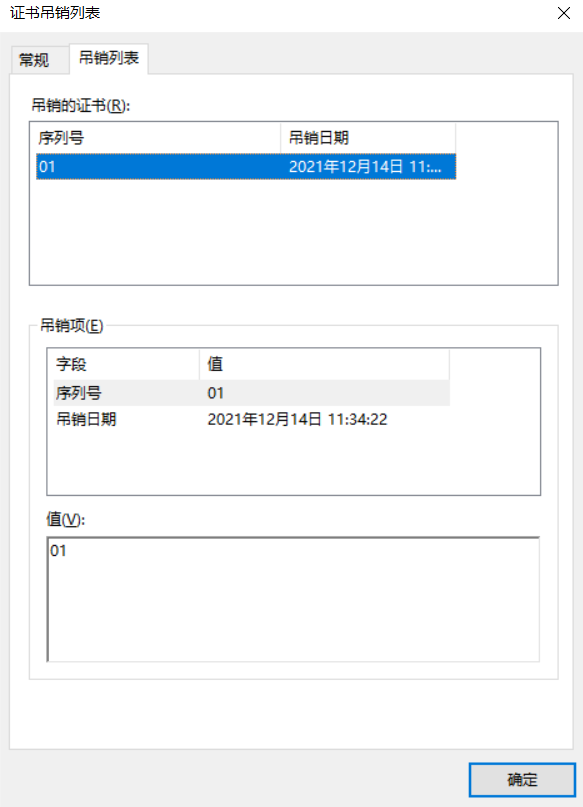
2. Summarize the common parameters and usage of ssh
ssh: secure shell protocol, 22/tcp, Secure remote login to realize encrypted communication and replace the traditional telnet agreement Specific software implementation: OpenSSH: ssh Open source implementation of the protocol, CentOS Default installation dropbear: the other one ssh Implementation of open source project based on Protocol
Public key exchange principle
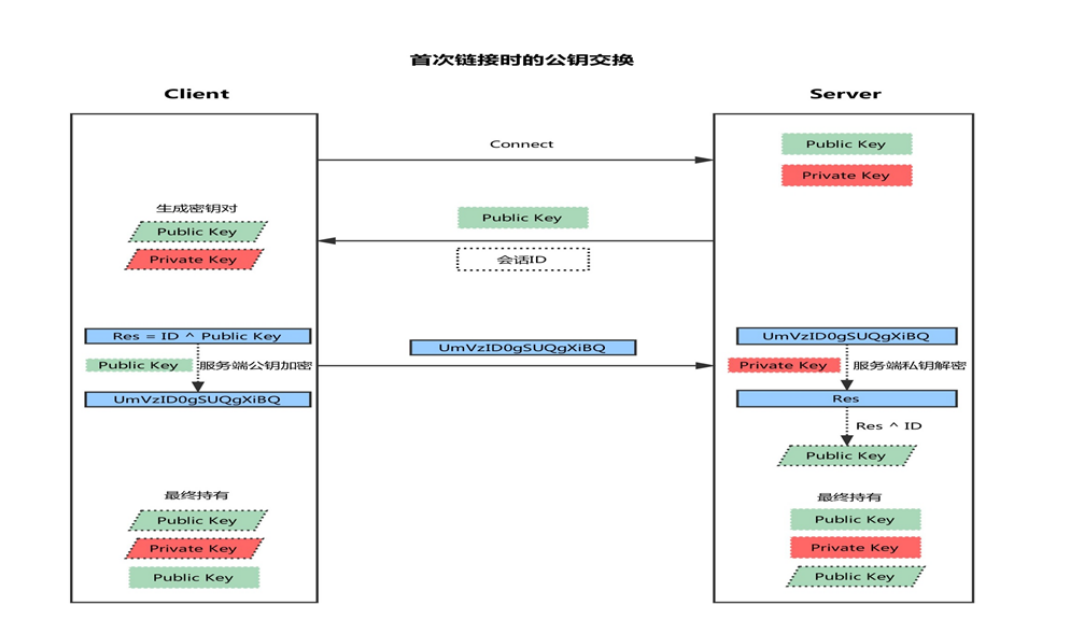
(1) Client initiated link request
(2) The server returns its own public key and a session ID (in this step, the client gets the server's public key)
(3) Client generated key pair
(4) The client calculates a value Res with its own public key XOR session ID, and encrypts it with the public key of the server
(5) The client sends the encrypted value to the server, and the server decrypts it with the private key to obtain Res
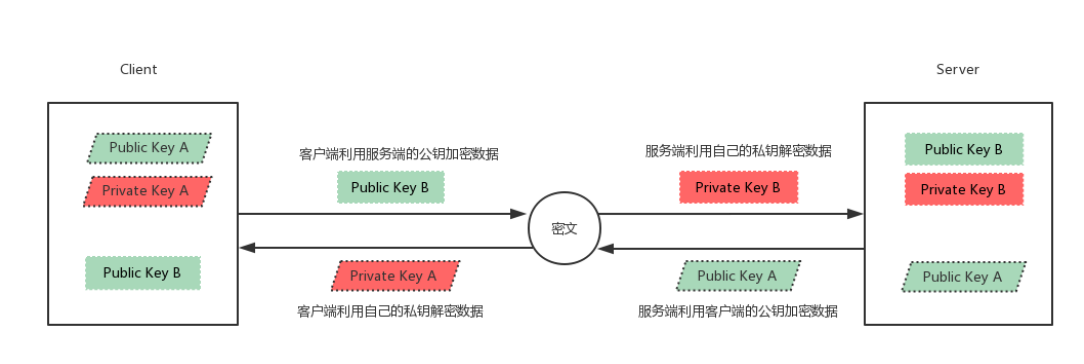
(6) The server uses the decrypted value Res XOR session ID to calculate the client's public key (in this step, the server obtains the client's public key)
(7) Finally: each party holds three secret keys, namely its own pair of public and private keys, and the other party's public key. All subsequent communications are secure
Will be encrypted
ssh encryption communication principle
Format:
ssh [user@]host [COMMAND] ssh [-l user] host [COMMAND] -p port #Port on which the remote server listens -b #Specify the source IP of the connection -v #Debug mode -C #Compression mode -X #Support x11 forwarding -t #Force pseudo tty allocation, such as SSH - t remoteserver1 SSH - t remoteserver2 SSH remoteserver3 -o option For example:-o StrictHostKeyChecking=no -i <file> #Specify the path of the private key file to implement key based authentication. The default file is ~ / ssh/id_dsa, ~/.ssh/id_ecdsa, ~/.ssh/id_ed25519,~/.ssh/id_rsa etc.
give an example:
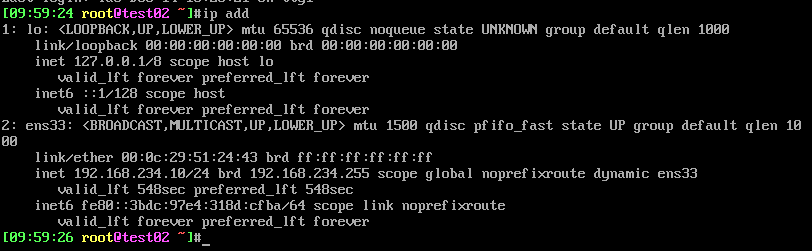
[14:21:26 root@centos8 ~]#ssh -t 192.168.234.100 ssh 192.168.234.101 Warning: Permanently added '192.168.234.100' (ECDSA) to the list of known hosts. root@192.168.234.100's password: root@192.168.234.101's password: Last login: Tue Dec 14 14:19:10 2021 from 192.168.234.1 [14:22:41 root@test02 ~]# [14:22:50 root@centos8 ~]#ssh 192.168.234.101 "touch 1.txt" Warning: Permanently added '192.168.234.101' (ECDSA) to the list of known hosts. root@192.168.234.101,s password: [14:23:53 root@centos8 ~]#echo "hostname -I " > test.sh [14:24:45 root@centos8 ~]# [14:24:46 root@centos8 ~]# [14:24:46 root@centos8 ~]#ssh 192.168.234.101 /bin/bash < test.sh root@192.168.234.101's password: 192.168.234.101
Common authentication methods for ssh service login
User / password
Key based
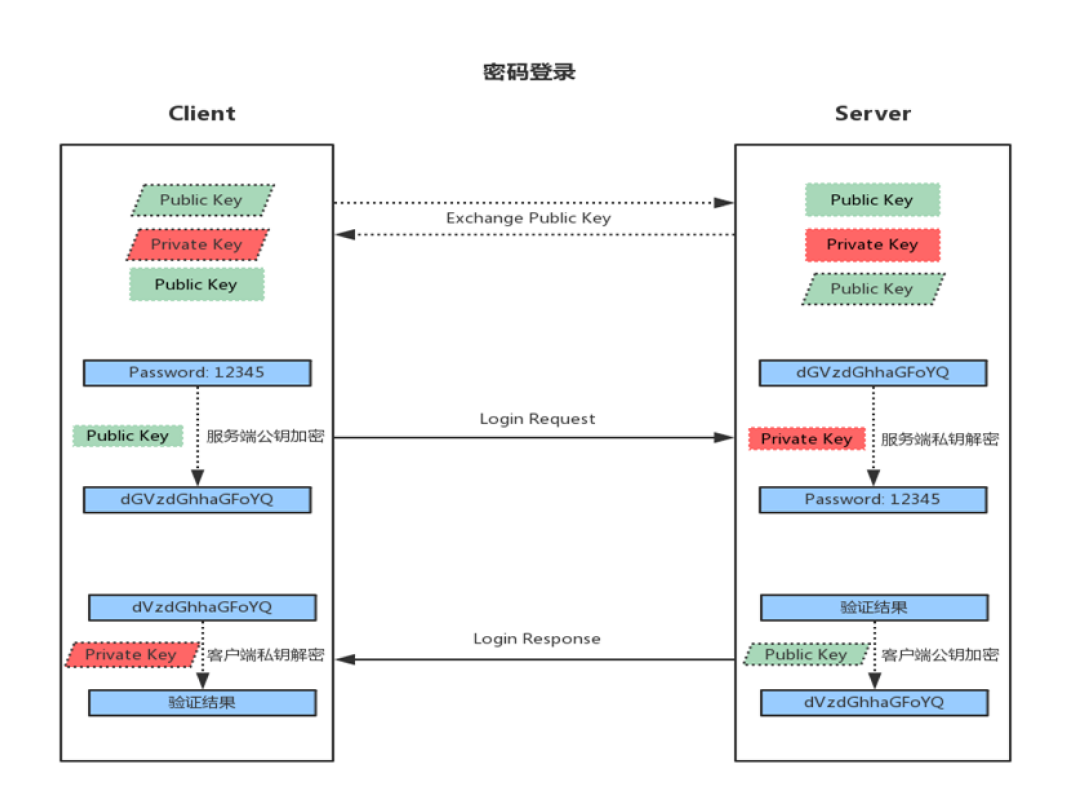
(1) When the client initiates an ssh request, the server will send its public key to the user
(2) The user will encrypt the password according to the public key sent by the server
(3) The encrypted information is sent back to the server, which decrypts it with its own private key. If the password is correct, the user logs in successfully
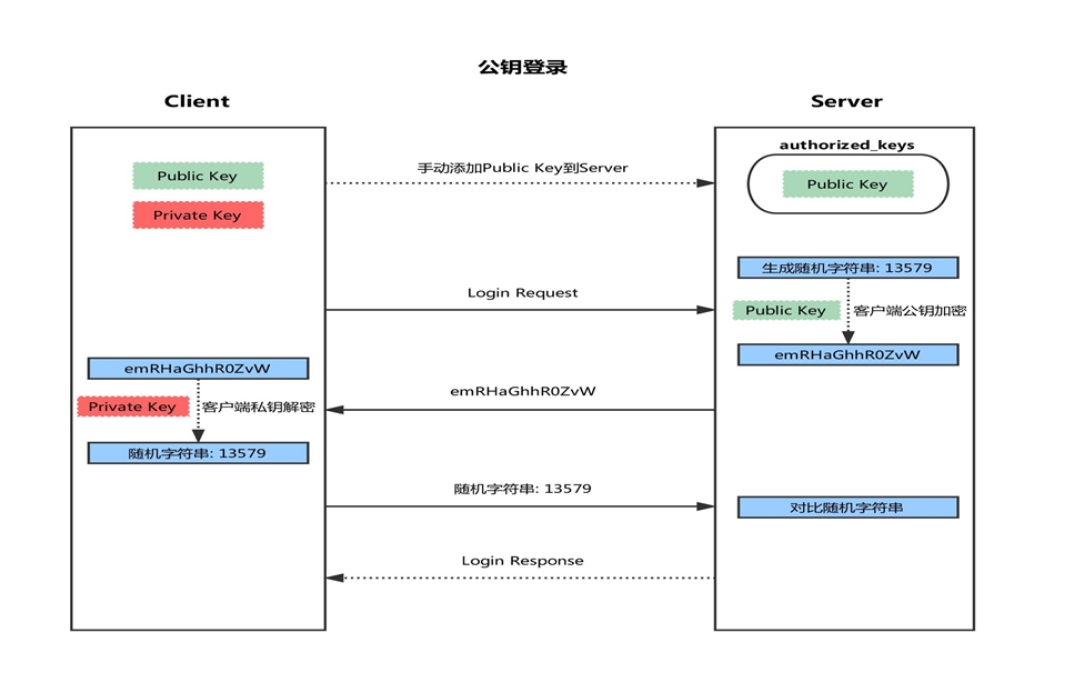
- First, a pair of keys (SSH keygen) is generated on the client
- And copy the client's public key SSH copy ID to the server
- When the client sends a connection request again, including ip and user name
- After receiving the request from the client, the server will go to authorized_keys. If there are responding IP addresses and users, they will be generated randomly
Into a string, for example: magedu - The server will use the public key copied from the client for encryption, and then send it to the client
- After getting the message from the server, the client will decrypt it with the private key, and then send the decrypted string to the server
- After receiving the string sent by the client, the server compares it with the previous string. If it is consistent, it is allowed to log in without password
[15:18:51 root@test02 ~]#ssh-agent bash [15:18:59 root@test02 ~]#ps -ef | grep agent root 1440 1439 0 15:18 ? 00:00:00 ssh-agent bash root 1473 1439 0 15:19 pts/0 00:00:00 grep --color=auto agent [15:19:05 root@test02 ~]# [15:19:06 root@test02 ~]# [15:19:06 root@test02 ~]#ssh-add Enter passphrase for /root/.ssh/id_rsa: Identity added: /root/.ssh/id_rsa (/root/.ssh/id_rsa) [15:19:28 root@test02 ~]#ssh 192.168.234.129 Activate the web console with: systemctl enable --now cockpit.socket Last login: Tue Dec 14 15:18:48 2021 from 192.168.234.101
3. Summarize the common parameters of sshd service.
Server side: sshd
Server side configuration file: / etc/ssh/sshd_config
Server side profile help: man 5 sshd_config
Port 22 #Production suggestion modification ListenAddress ip LoginGraceTime 2m PermitRootLogin yes #The default ubuntu does not allow root remote ssh login StrictModes yes #Check ssh / file owner, permissions, etc MaxAuthTries 6 #Maximum number of attempts MaxSessions 10 #Maximum sessions for the same connection PubkeyAuthentication yes #key based authentication PermitEmptyPasswords no #Empty password connection PasswordAuthentication yes #Connect based on user name and password GatewayPorts no ClientAliveInterval 10 #Unit: Second ClientAliveCountMax 3 #Default 3 UseDNS yes #Increase speed can be changed to no GSSAPIAuthentication yes #Increase speed can be changed to no MaxStartups #Maximum unauthenticated connection, default 10 Banner /path/file
Best practices for ssh services
A non default port is recommended Prohibited use protocol version 1 Restrict logged in users Set idle session timeout length Use firewall settings ssh Access policy Listen only for specific IP address For password based authentication, strong password policies are used, such as: tr -dc A-Za-z0-9_ < /dev/urandom | head -c 12| xargs Use key based authentication Do not use empty passwords prohibit root User login directly limit ssh Access frequency and concurrent online number Analyze logs frequently
4. Build dhcp service to realize ip address application distribution
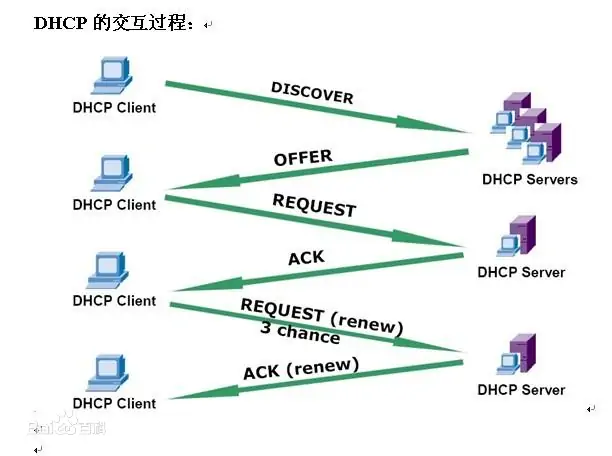
1,DHCP Client Broadcast DHCP Discover Message. 2,be-all DHCP Server Can receive DHCP Client Sent DHCP Discover Message, all DHCP Server Will give a response to DHCP Client Send a DHCP Offer Message. DHCP Offer In message“ Your(Client) IP Address"Field is DHCP Server Can be provided to DHCP Client Used IP Address, and DHCP Server Will be their own IP Address on“ option"Field so that DHCP Client Distinguish between different DHCP Server. DHCP Server After sending this message, there will be an allocated IP A record of the address. 3,DHCP Client Only one of them can be processed DHCP Offer Message, the general principle is DHCP Client Process first received DHCP Offer Message. DHCP Client There will be a broadcast DHCP Request Message, the selected message will be added in the option field DHCP Server of IP Address and required IP Address. 4,DHCP Server received DHCP Request After the message, judge the value in the option field IP Whether the address is the same as your own address. If not, DHCP Server Do not do any processing, only clear the corresponding IP Address assignment record; If the same, DHCP Server Will go to DHCP Client Respond to a DHCP ACK Message and add in the option field IP Lease term information for the address. 5,DHCP Client Received DHCP ACK After the message, check DHCP Server Allocated IP Whether the address can be used. If available, then DHCP Client Successfully obtained IP Address and according to IP The address usage lease term automatically starts the renewal process; If DHCP Client Found assigned IP The address is already in use, then DHCP Client towards DHCPServer issue DHCP Decline Message, notification DHCP Server Disable this IP Address, then DHCP Client Start the new address application process. 6,DHCP Client Successfully obtained at IP The address can be sent at any time DHCP Release The message releases its own IP Address, DHCP Server received DHCP Release After the message, the corresponding message will be recovered IP Address and reassign. In use, the lease term exceeds 50 years%At the moment, DHCP Client Will be unicast to DHCP Server send out DHCPRequest To renew the lease IP Address. If DHCP Client Successfully received DHCP Server Sent DHCP ACK Message, it shall be extended according to the corresponding time IP Address lease term; If not received DHCP Server Sent DHCP ACK Message, then DHCP Client Continue using this IP Address. In use lease term over 87.5%At the moment, DHCP Client Will be broadcast to DHCP Server send out DHCPRequest To renew the lease IP Address. If DHCP Client Successfully received DHCP Server Sent DHCP ACK Message, it shall be extended according to the corresponding time IP Address lease term; If not received DHCP Server Sent DHCP ACK Message, then DHCP Client Continue using this IP Address until IP When the lease term for the use of the address expires, DHCP Client Will to DHCP Server send out DHCP Release Message to release this IP Address and start a new one IP Address application process.
/etc/dhcp/dhcpd.conf
option domain-name "magedu.org";
option domain-name-servers 180.76.76.76, 223.6.6.6;
default-lease-time 600;
max-lease-time 7200;
log-facility local7;
subnet 192.168.234.0 netmask 255.255.255.0 {
range 192.168.234.10 192.168.234.100;
option routers 192.168.234.2;
}
#Specify the assigned ip address according to the mac
host testclient {
hardware ethernet 00:0c:29:33:b4:1a;
fixed-address 192.168.234.12;
default-lease-time 86400;
max-lease-time 864000;
option routers 192.168.234.2;
option domain-name-servers 114.114.114.114,8.8.8.8 ;
option domain-name "magedu.net";
}