Experiment 7 PKI/CA
1, Experimental purpose
- Understand CA certification process
- Master the use of openssl command, including public-private key generation, random number generation, certificate application and certificate issuance
2, Experimental content
- Use openssl to generate ca certificate and issue certificate
- Use PKI in the website to configure the secure connection access of the website: https
3, Experimental environment
Experiment with openssl.exe command
4, Experimental requirements
Complete the experiment according to the experimental content requirements
5, Experimental steps
1. Steps and running results of using openssl to generate ca certificate and issue certificate
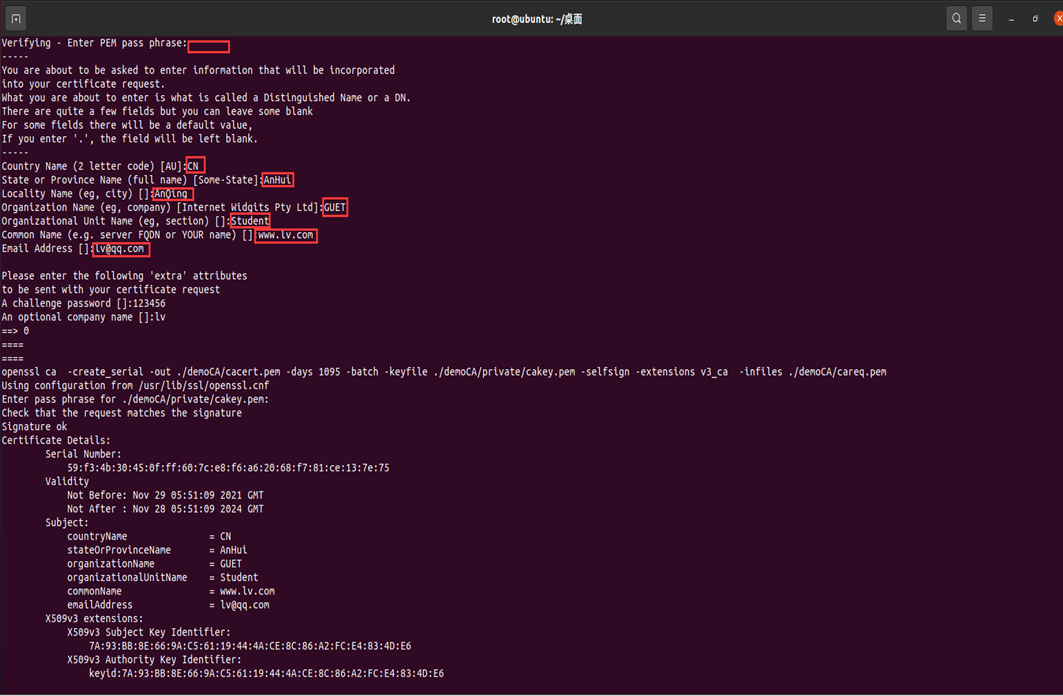
1. Intermediate CA self signing
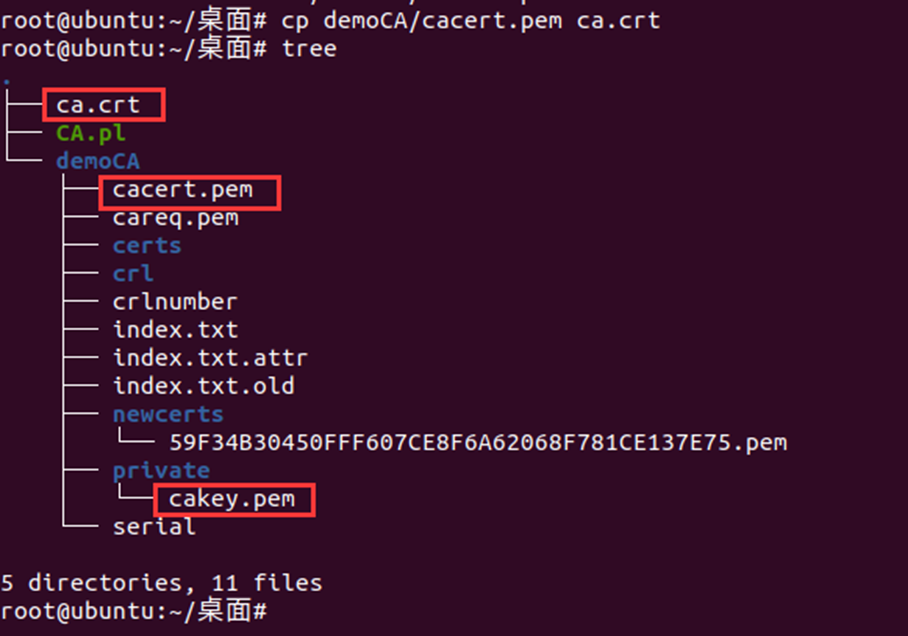
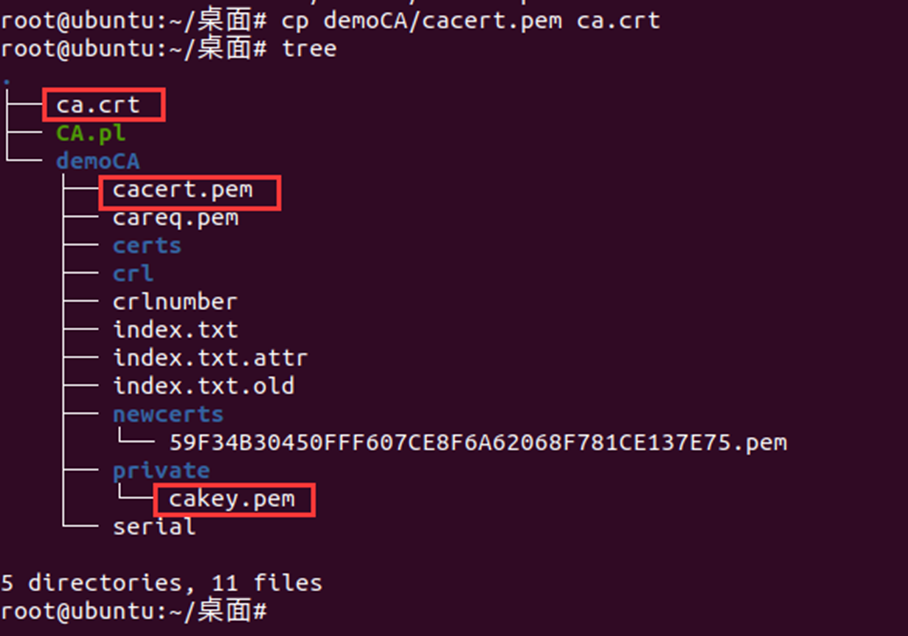
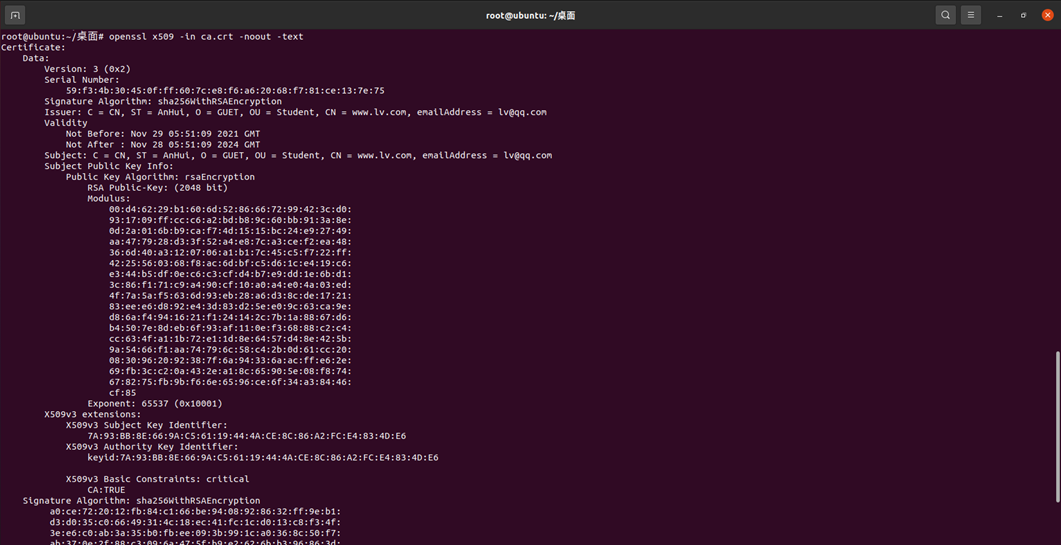
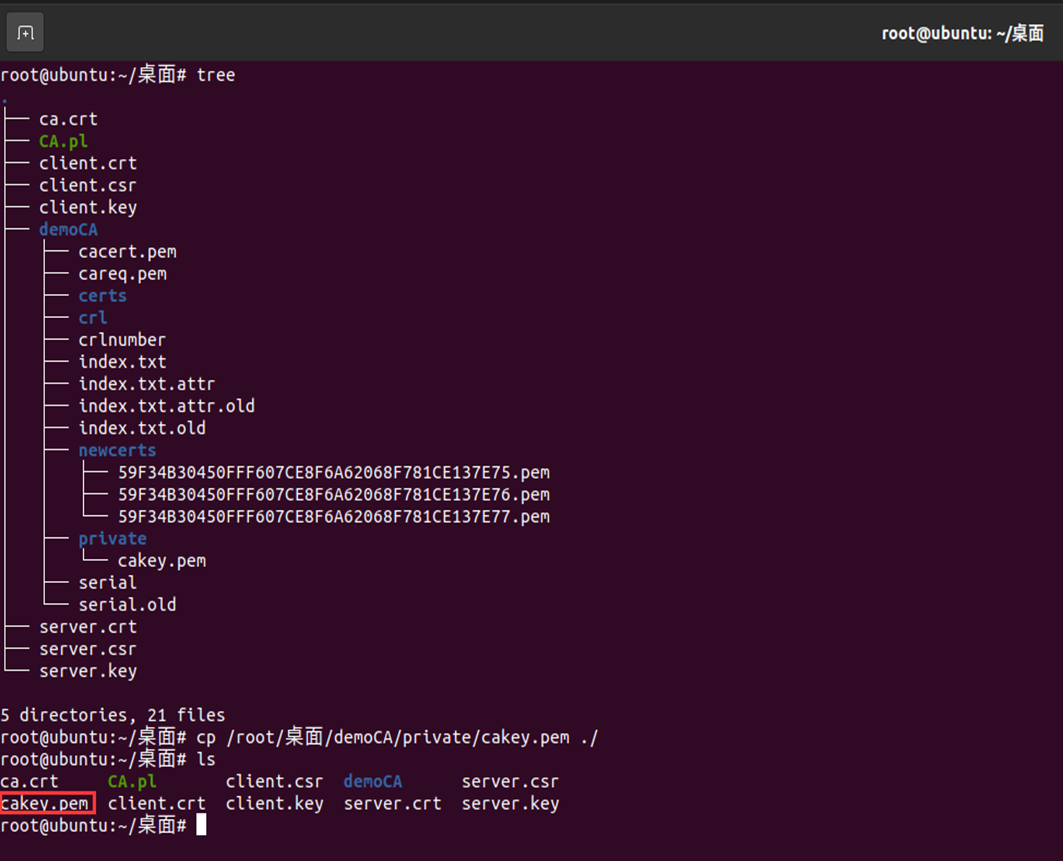
##Copy ssl/misc/CA.sh in the original openssl directory to the test directory you created: cp /usr/lib/ssl/misc/CA.pl ./ ##Create master certificate: ./CA.pl -newca ##Complete the information to be filled in according to the prompt. If the generation is successful, a certificate file will be generated in the demoCA directory under the current directory. demoCA/private/cakey.pem is the ca certificate private key and demoCA/cacert.pem is the ca root certificate. ##Copy cacert.pem to ca.crt cp demoCA/cacert.pem ca.crt ##View ca certificate content openssl x509 -in ca.crt -noout -text ##View ca certificate serial number openssl x509 -in ca.crt -noout -serial


2. Generate server certificate
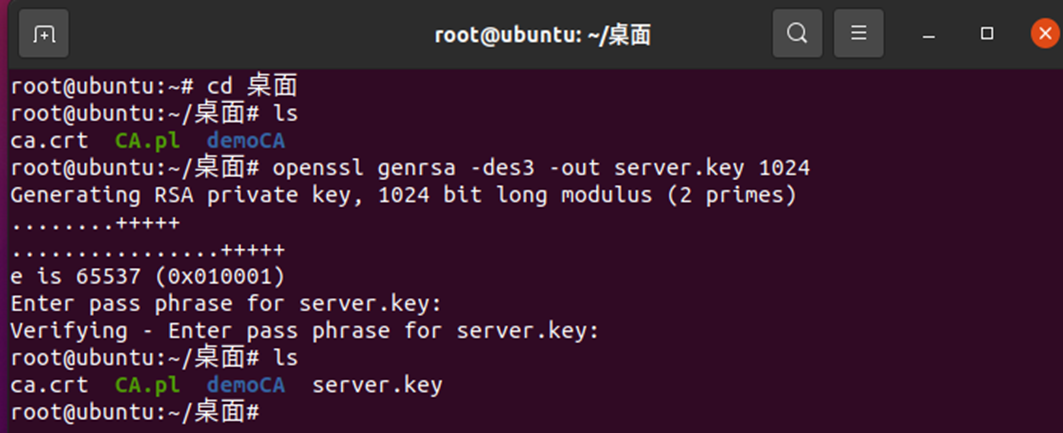
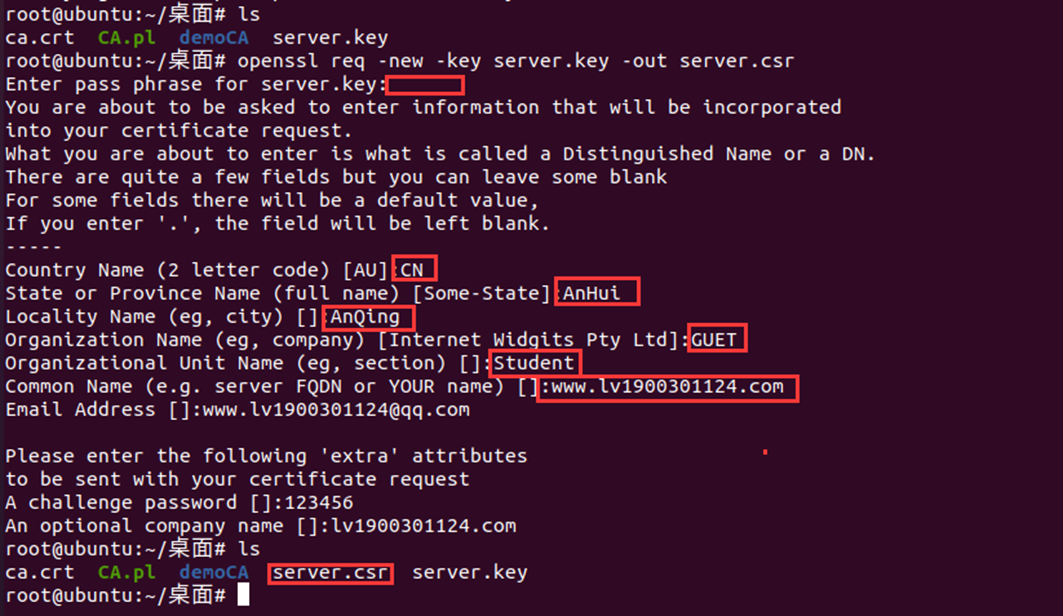
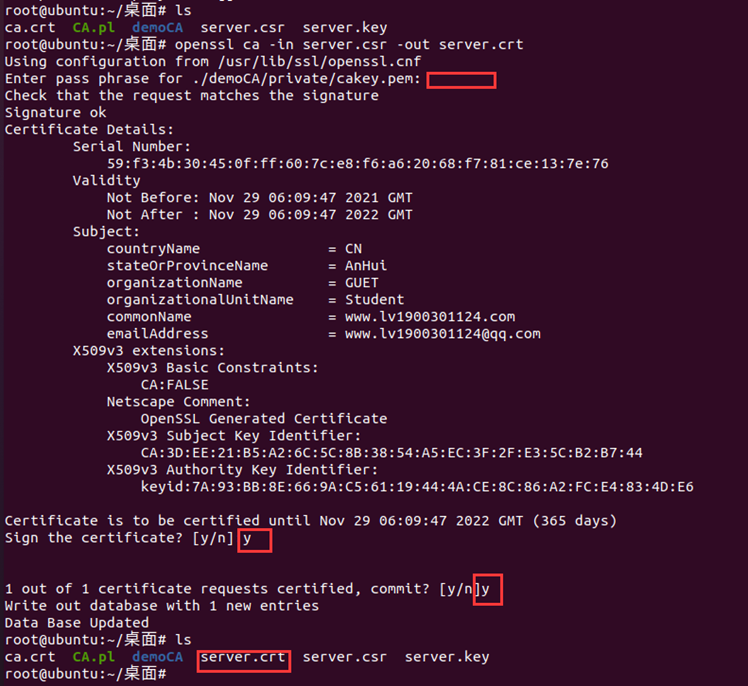
##Generate server private key: openssl genrsa -des3 -out server.key 1024 ##Generate csr file: openssl req -new -key server.key -out server.csr ##Sign and generate certificate: openssl ca -in server.csr -out server.crt
3. Generate client certificate
##Generate client private key: openssl genrsa -des3 -out client.key 1024 ##Generate csr file: openssl req -new -key client.key -out client.csr ##Sign and generate certificate: openssl ca -in client.csr -out client.crt
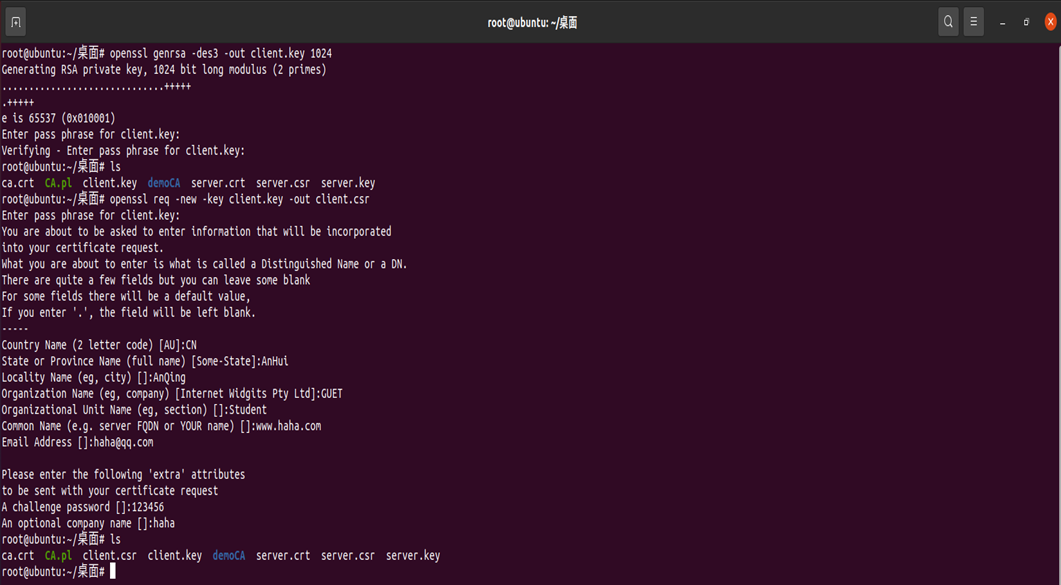
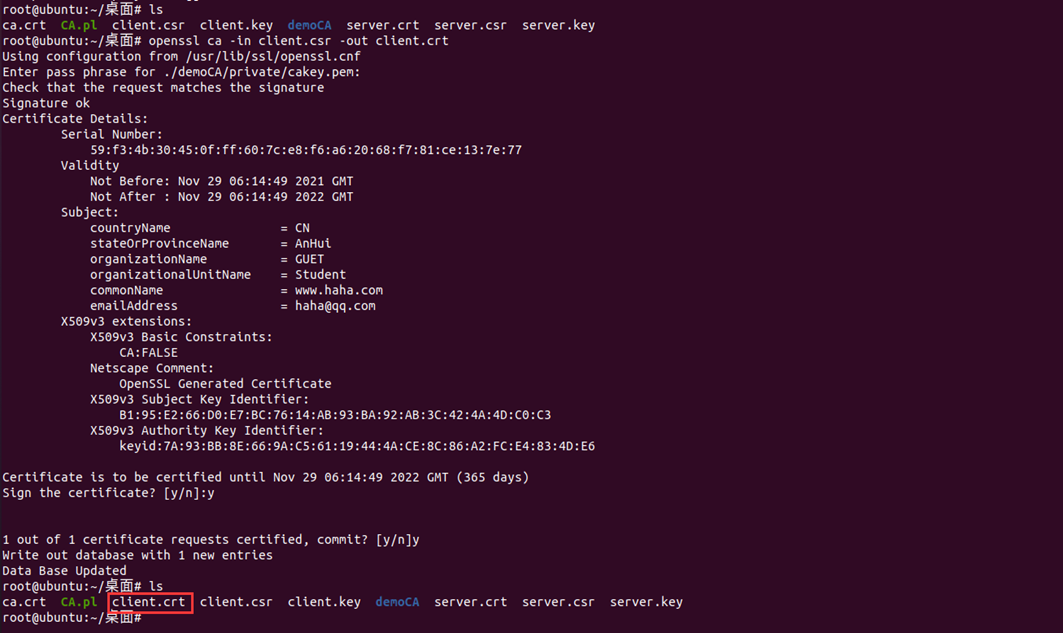
4. View the generated key and certificate information
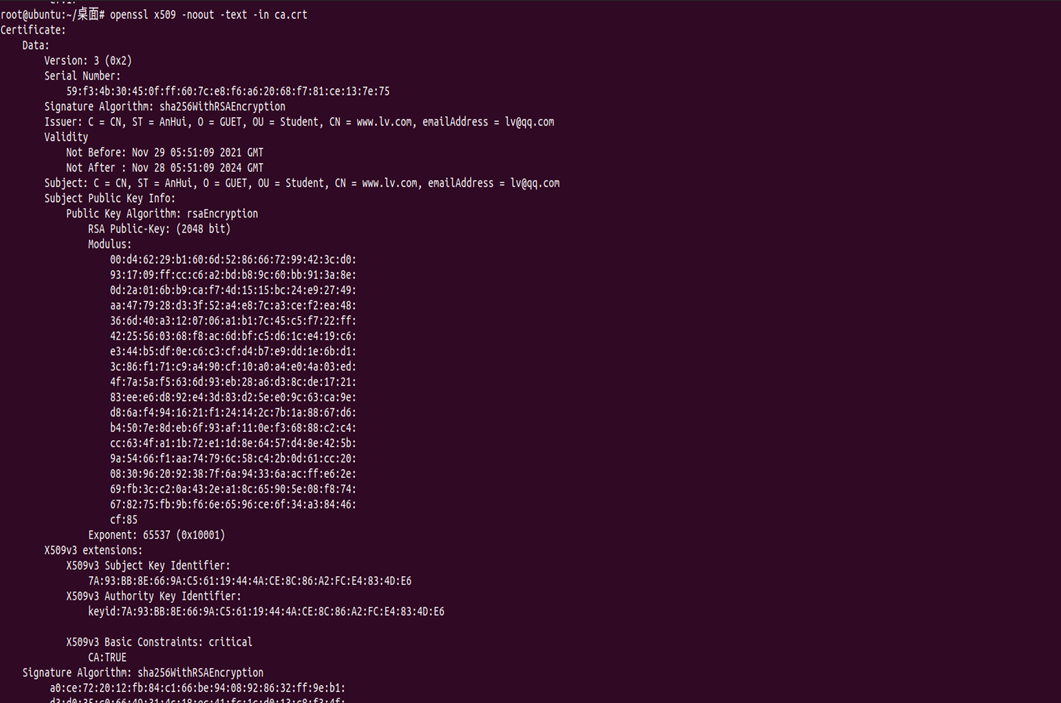
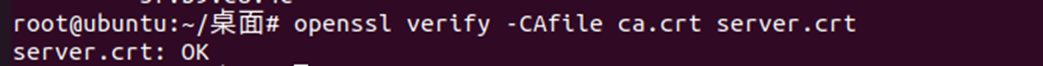
##view key info openssl rsa -noout -text -in server.key ##view CSR info openssl req -noout -text -in server.csr ##view cert info openssl x509 -noout -text -in ca.crt ##verify cert openssl verify -CAfile ca.crt server.crt
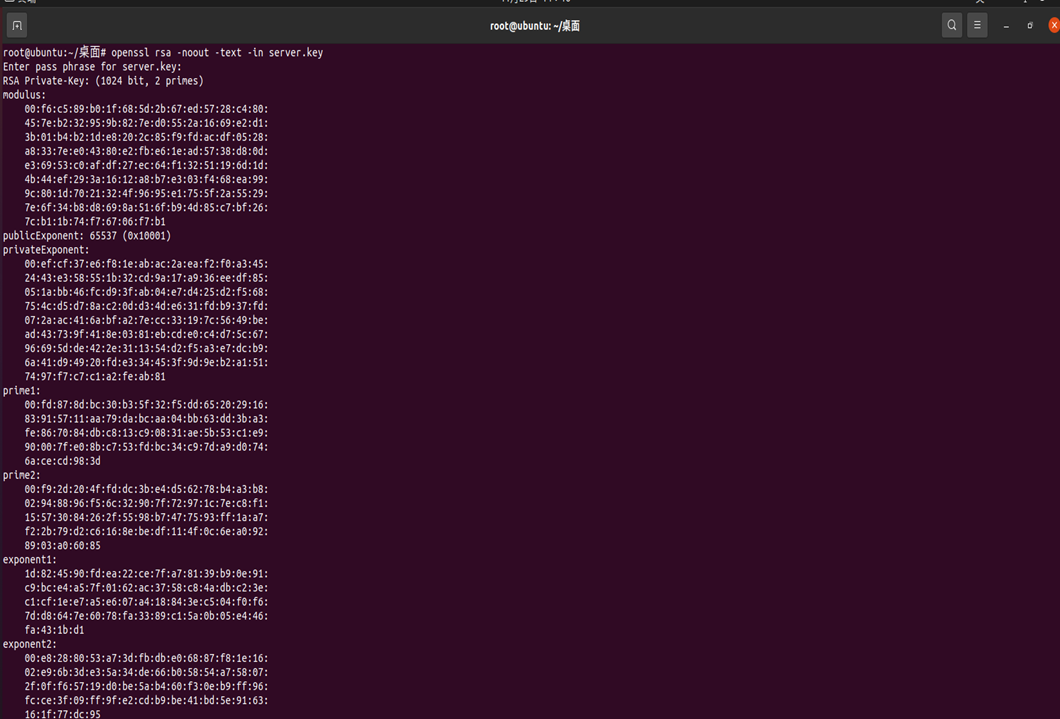
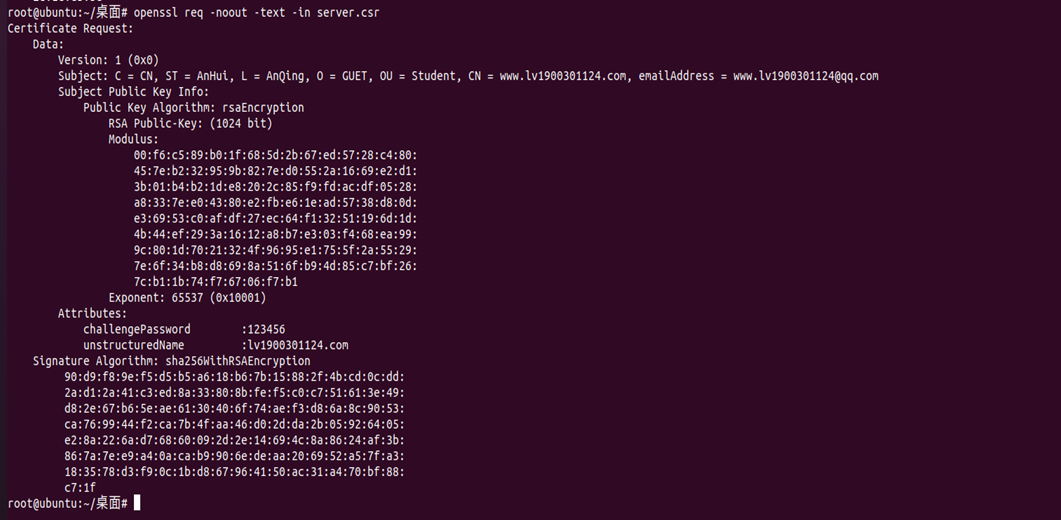
2. Steps and effect screenshots of using PKI in the website and configuring the secure connection https access of the website
Experiment preparation: lv1900301124.html, ca.pfx(ca.p12), server.pfx(server.p12)
Experimental steps:
lv1900301124.html
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>lv.com</title>
</head>
<body>
<p>Test successful!</p>
</body>
</html>
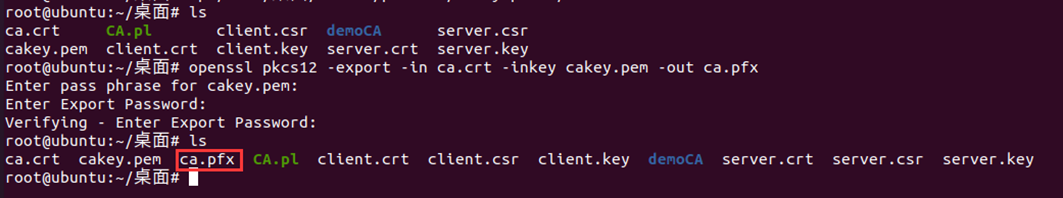
cp /root/desktop/demoCA/private/cakey.pem ./ openssl pkcs12 -export -in ca.crt -inkey cakey.pem -out ca.pfx openssl pkcs12 -export -in server.crt -inkey server.key -out server.pfx
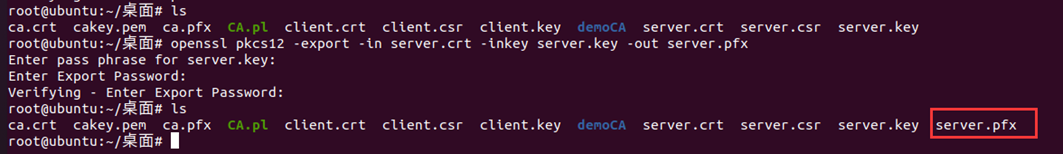
Environment configuration:
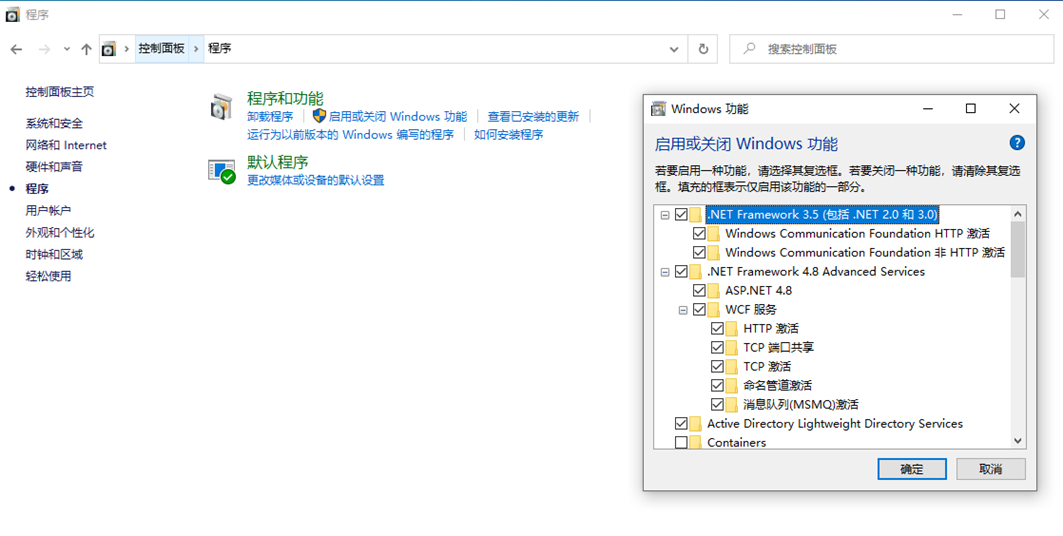
First: install. NET (because the NET framework is required in many cases, it is best to install the NET framework).
Open the control panel, enable or turn off Windows functions, find Net Framework 3.5 and. Net framework 4.7, check all the default checkboxes of 3.5 and 4.7, and then check ASP. Net 4.7 together. Then: install IIS (Internet Information Services), find Internet Information Services and check the check box. For details, see the figure below: (mainly the options related to application development functions). Wait until the installation is completed (this process requires networking support to download files)
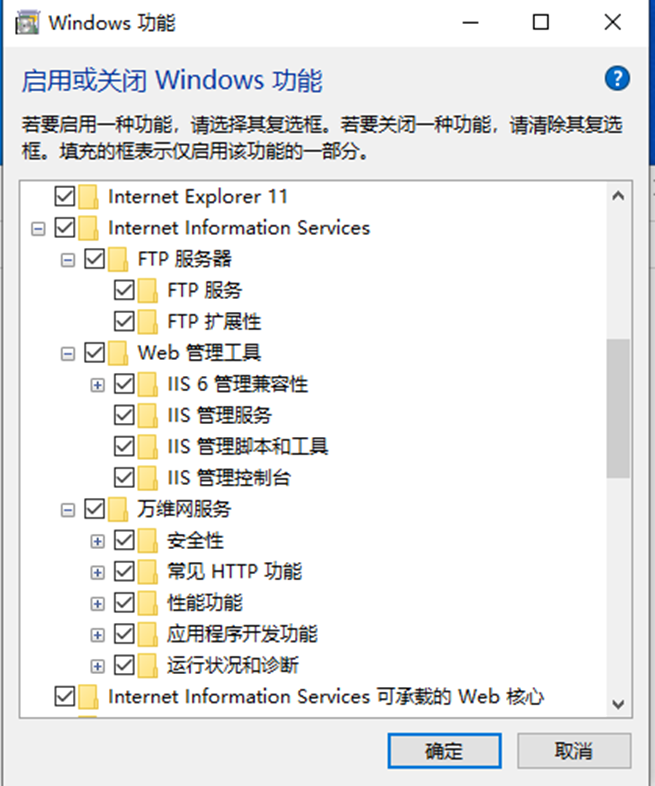
Enter in the browser after installation http://127.0.0.1 If you can open the IIS start page, the installation is successful.
Build a domain name website (intranet access only)
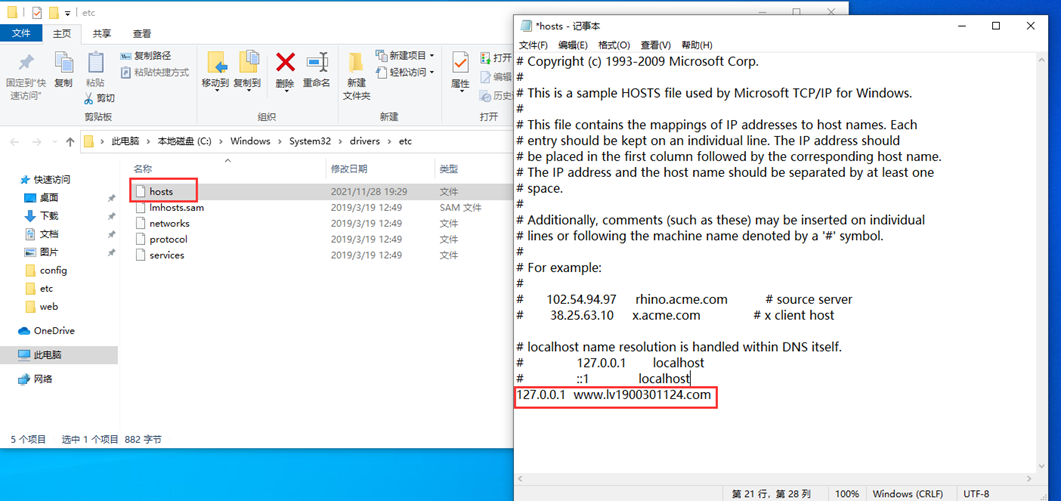
1. Open the hosts file (path: C:\Windows\System32\drivers\etc),
Add 127.0.0.1 www.lv1900301124.com at the end of the hosts file
2. Create web site
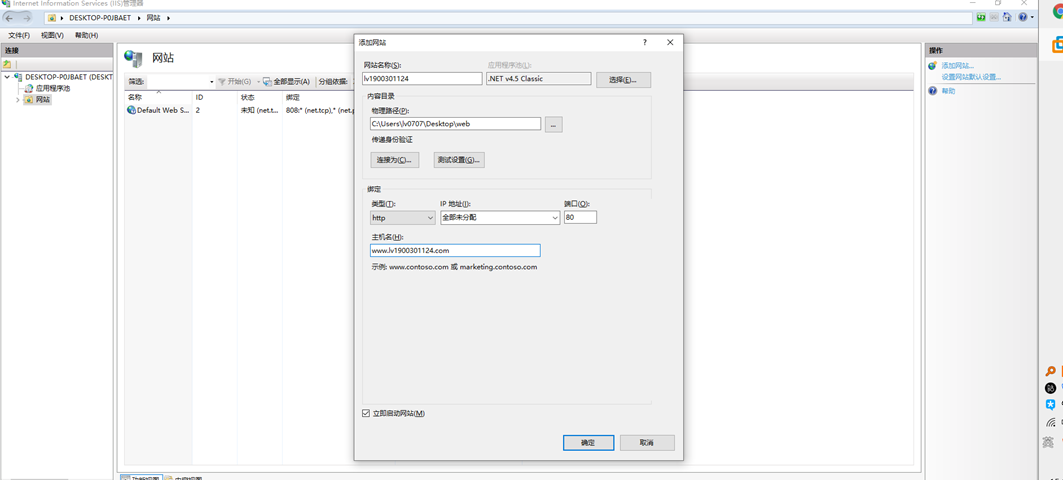
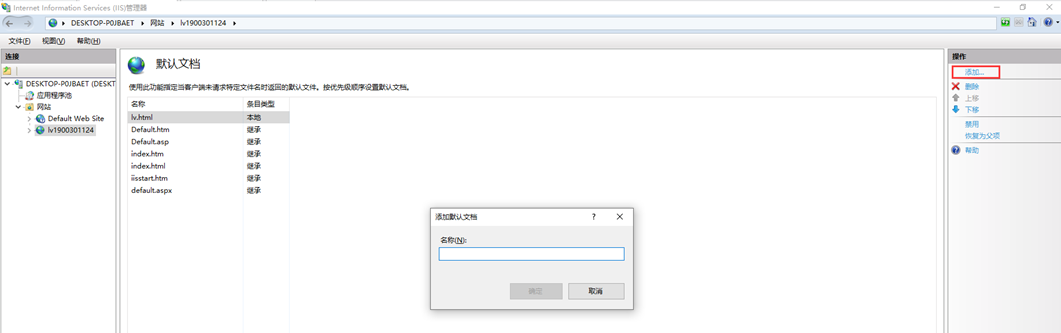
3. Modify home page
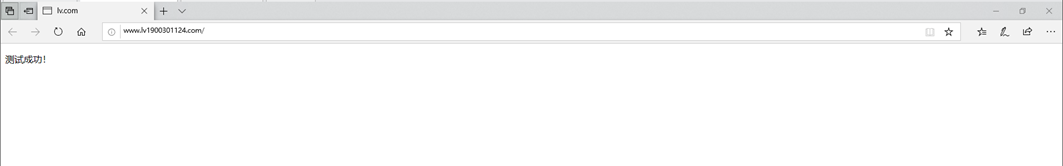
4. Browsing effect (http)
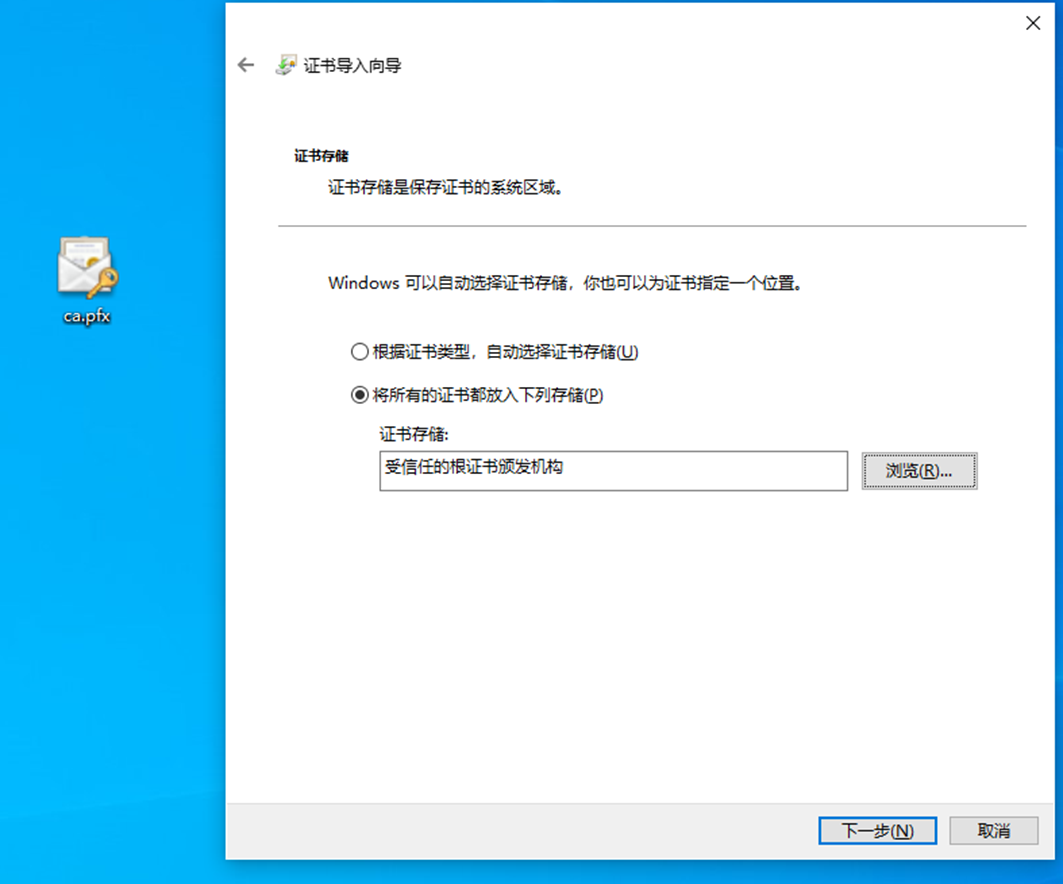
5. Installation certificate
Double click Install CA certificate (ca.pfx)
Install server certificate (server.pfx)
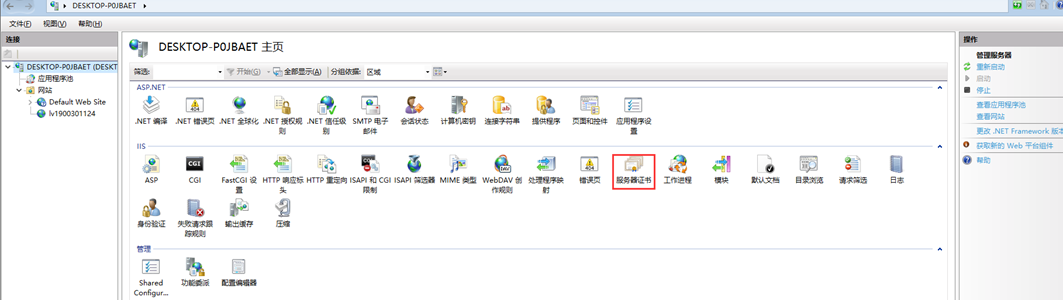
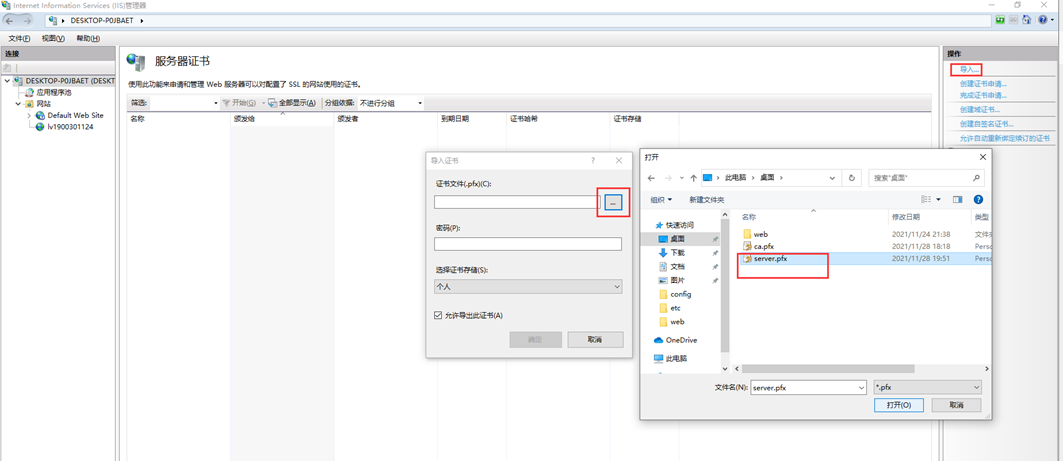
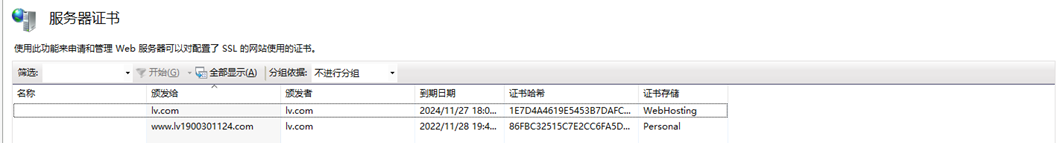
Selected certificate binding https website:
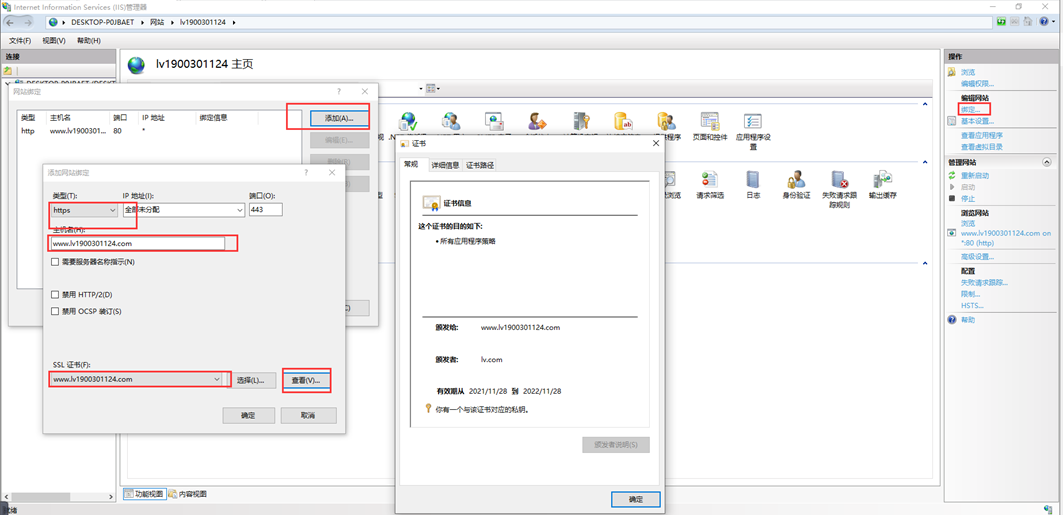
View effect:
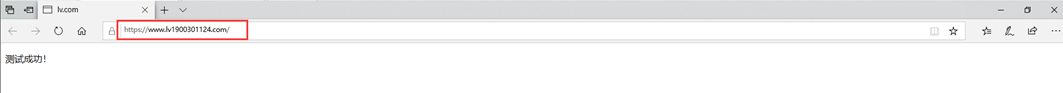
6, Problem record and experiment summary (required)
This experiment makes me feel the power of openssl, which is an open source software library package: applications can use this package to conduct secure communication, avoid eavesdropping, and confirm the identity of the connector at the other end. At present, this package is widely used in web page servers on the Internet. At the same time, I understand the process of CA issuing certificates and master the use of openssl commands Including public private key generation, random number generation, certificate application and certificate issuance. 2. Use PKI in the website and configure the secure connection access of the website: https, which makes me understand how the guarantee of our internet security website works at present.