podman accelerator & & Harbor
podman acceleration configuration
Configure the accelerator. It takes effect immediately without restarting centos8: [root@localhost ~]# vi /etc/containers/registries.conf [[registry]] prefix="docker.io" location="pvurwzu6.mirror.aliyuncs.com" centos7: [root@localhost ~]# vi /etc/containers/registries.conf [[docker.io]] location="pvurwzu6.mirror.aliyuncs.com" [root@localhost ~]# cd /etc/containers/ [root@localhost containers]# ls certs.d oci policy.json registries.conf registries.conf.d registries.d storage.conf [root@localhost containers]# vi registries.conf ·············· [registries.search] registries = ["docker.io"] ·············· //Pull image [root@localhost ~]# podman pull nginx Trying to pull docker.io/library/nginx:latest... //The default is to find docker io Getting image source signatures Copying blob 21e0df283cd6 done Copying blob e5ae68f74026 done Copying blob ed835de16acd done Copying blob 77700c52c969 done Copying blob 881ff011f1c9 done Copying blob 44be98c0fab6 done Copying config f652ca386e done Writing manifest to image destination Storing signatures f652ca386ed135a4cbe356333e08ef0816f81b2ac8d0619af01e2b256837ed3e
Harbor
Whether you use docker distribution to build your own warehouse or run the container through the official image, we can find that it is very simple through the previous demonstration. It is not as convenient as directly using the official Docker Hub to manage the image. At least the official Docker Hub can manage the image through the web interface and perform search on the web interface, You can also use Webhooks and Automated Builds to automatically build images based on Dockerfile. Instead of executing docker build locally, users push all build context files to github as a warehouse, so that Docker Hub can pull these files from github to complete automatic construction.
However, no matter how powerful the official Docker Hub is, it is abroad after all, so the speed is the biggest bottleneck. It is impossible for us to consider using the official warehouse many times. However, the two self built warehouse methods mentioned above are very simple and inconvenient to manage, so a project favored by CNCF organization, named Harbor, emerged later.
Introduction to Harbor
Harbor is secondary encapsulated by VMWare on the basis of Docker Registry, with many additional programs added, and provides a very beautiful web interface.
Harbor It is an open source trusted cloud native warehouse project for storage, user management and image discovery. Harbor Extends open source by adding features that users typically need, such as security, identity, and management Docker Distribution version. Harbor Support advanced features such as user management, access control, activity monitoring, and replication between instances.
Harbor features
-
Multi tenant content signing and validation
-
Security and vulnerability analysis
-
Audit log record
-
Identity integration and role-based access control
-
Image replication between instances
-
Extensible API and graphical UI
-
Internationalization (currently Chinese and English Culture)
Docker compose
It is very difficult to deploy Harbor on physical machines. In order to simplify Harbor applications, Harbor officials directly make Harbor into applications running in containers. Moreover, this container relies on many storage systems such as redis, mysql and pgsql in Harbor, so it needs to arrange many containers to work together. Therefore, when deploying and using VMWare Harbor, It needs the help of Docker for stand-alone scheduling
Compose is a tool for defining and running multi container Docker applications. With compose, you can use YAML files to configure the services of your application. Then, use a single command to create and start all services from the configuration.
Docker Compose official document
Harbor deployment
[root@node3 bin]# curl -L "https://github.com/docker/compose/releases/download/1.29.2/docker-compose-$(uname -s)-$(uname -m)" -o /usr/local/bin/docker-compose
[root@node3 bin]# pwd
/usr/local/bin
[root@node3 bin]# ls
docker-compose
Apply executable permissions to binaries:
[root@localhost ~]# chmod +x /usr/local/bin/docker-compose
[root@node3 ~]# wget https://github.com/goharbor/harbor/releases/tag/v2.3.5 .
[root@node3 ~]# ls
anaconda-ks.cfg grafana-enterprise-8.2.5-1.x86_64.rpm
harbor-offline-installer-v2.3.5.tgz
[root@node3 ~]# tar xf harbor-offline-installer-v2.3.5.tgz -C /usr/local/
[root@node3 ~]# cd /usr/local/
[root@node3 local]# ls
bin etc games harbor include lib lib64 libexec sbin share src
[root@node3 local]# cd harbor/
[root@node3 harbor]# ls
common.sh harbor.yml.tmpl LICENSE
harbor.v2.3.5.tar.gz install.sh prepare
[root@node3 harbor]# hostnamectl set-hostname registry.example.com
[root@node3 harbor]# bash
[root@registry harbor]# vim /etc/hosts
[root@registry harbor]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
192.168.136.142 registry.example.com
//Add domain name resolution on another host to view
[root@node2 ~]# vim /etc/hosts
[root@node2 ~]# cat /etc/hosts
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
192.168.136.142 registry.example.com
[root@node2 ~]# ping registry.example.com
PING registry.example.com (192.168.136.142) 56(84) bytes of data.
64 bytes from registry.example.com (192.168.136.142): icmp_seq=1 ttl=64 time=0.552 ms
64 bytes from registry.example.com (192.168.136.142): icmp_seq=2 ttl=64 time=0.254 ms
64 bytes from registry.example.com (192.168.136.142): icmp_seq=3 ttl=64 time=0.336 ms
//On server
[root@registry harbor]# cp harbor.yml.tmpl harbor.yml
[root@registry harbor]# ls
common.sh harbor.yml install.sh prepare
harbor.v2.3.5.tar.gz harbor.yml.tmpl LICENSE
[root@registry harbor]# vim harbor.yml
hostname: registry.example.com
# http related config
http:
# port for http, default is 80. If https enabled, this port will redirect to https port
port: 80
# https related config
#https:
# https port for harbor, default is 443
# port: 443
# The path of cert and key files for nginx
# certificate: /your/certificate/path
# private_key: /your/private/key/path
//Note out those not noted above
# Remember Change the admin password from UI after launching Harbor.
harbor_admin_password: Harbor12345 #Administrator password
# Harbor DB configuration
database:
# The password for the root user of Harbor DB. Change this before any production use.
password: root123 #Database password
# The maximum number of connections in the idle connection pool. If it <=0, no idle connections are retained.
max_idle_conns: 100 #Maximum number of idle connections 100
..............................................
of harbor.
max_open_conns: 900 #Maximum connections 900
# The default data volume
data_volume: /data #Data stored in data
······················
//install
** matters needing attention
[root@registry harbor]# systemctl start docker
[root@registry harbor]# systemctl enable docker
Created symlink /etc/systemd/system/multi-user.target.wants/docker.service → /usr/lib/systemd/system/docker.service.
[root@registry harbor]# systemctl status firewall
Unit firewall.service could not be found.
[root@registry harbor]# systemctl status firewalld
● firewalld.service - firewalld - dynamic firewall daemon
Loaded: loaded (/usr/lib/systemd/system/firewalld.service; disabled; vend>
Active: inactive (dead)
Docs: man:firewalld(1)
[root@registry harbor]# setenforce 0
setenforce: SELinux is disabled
[root@registry harbor]# ./install.sh
[Step 5]: starting Harbor ...
Creating network "harbor_harbor" with the default driver
Creating harbor-log ... done
Creating harbor-db ... done
Creating harbor-portal ... done
Creating registry ... done
Creating redis ... done
Creating registryctl ... done
Creating harbor-core ... done
Creating harbor-jobservice ... done
Creating nginx ... done
✔ ----Harbor has been installed and started successfully.----
//Generated image
[root@registry harbor]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
goharbor/harbor-exporter v2.3.5 1730c6f650e2 5 days ago 81.9MB
goharbor/chartmuseum-photon v2.3.5 47004f032938 5 days ago 179MB
goharbor/redis-photon v2.3.5 3d0cedc89a0d 5 days ago 156MB
goharbor/trivy-adapter-photon v2.3.5 5c0212e98070 5 days ago 133MB
goharbor/notary-server-photon v2.3.5 f20a76c65359 5 days ago 111MB
goharbor/notary-signer-photon v2.3.5 b9fa38eef4d7 5 days ago 108MB
goharbor/harbor-registryctl v2.3.5 7a52567a76ca 5 days ago 133MB
goharbor/registry-photon v2.3.5 cf22d3e386b8 5 days ago 82.6MB
goharbor/nginx-photon v2.3.5 5e3b6d9ce11a 5 days ago 45.7MB
goharbor/harbor-log v2.3.5 a03e4bc963d6 5 days ago 160MB
goharbor/harbor-jobservice v2.3.5 2ac32df5a2e0 5 days ago 211MB
goharbor/harbor-core v2.3.5 23baee01156f 5 days ago 193MB
goharbor/harbor-portal v2.3.5 bb545cdedf5a 5 days ago 58.9MB
goharbor/harbor-db v2.3.5 9826c57a5749 5 days ago 221MB
goharbor/prepare v2.3.5 a1ceaabe47b2 5 days ago 255MB
[root@registry harbor]# ss -antl
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 128 127.0.0.1:1514 0.0.0.0:*
LISTEN 0 128 0.0.0.0:111 0.0.0.0:*
LISTEN 0 128 0.0.0.0:80 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 128 [::]:111 [::]:*
LISTEN 0 128 [::]:80 [::]:*
LISTEN 0 128 [::]:22 [::]:*
LISTEN 0 128 *:3000 *:*
Manage harbor using ip login
The account password is the account password in the previous file
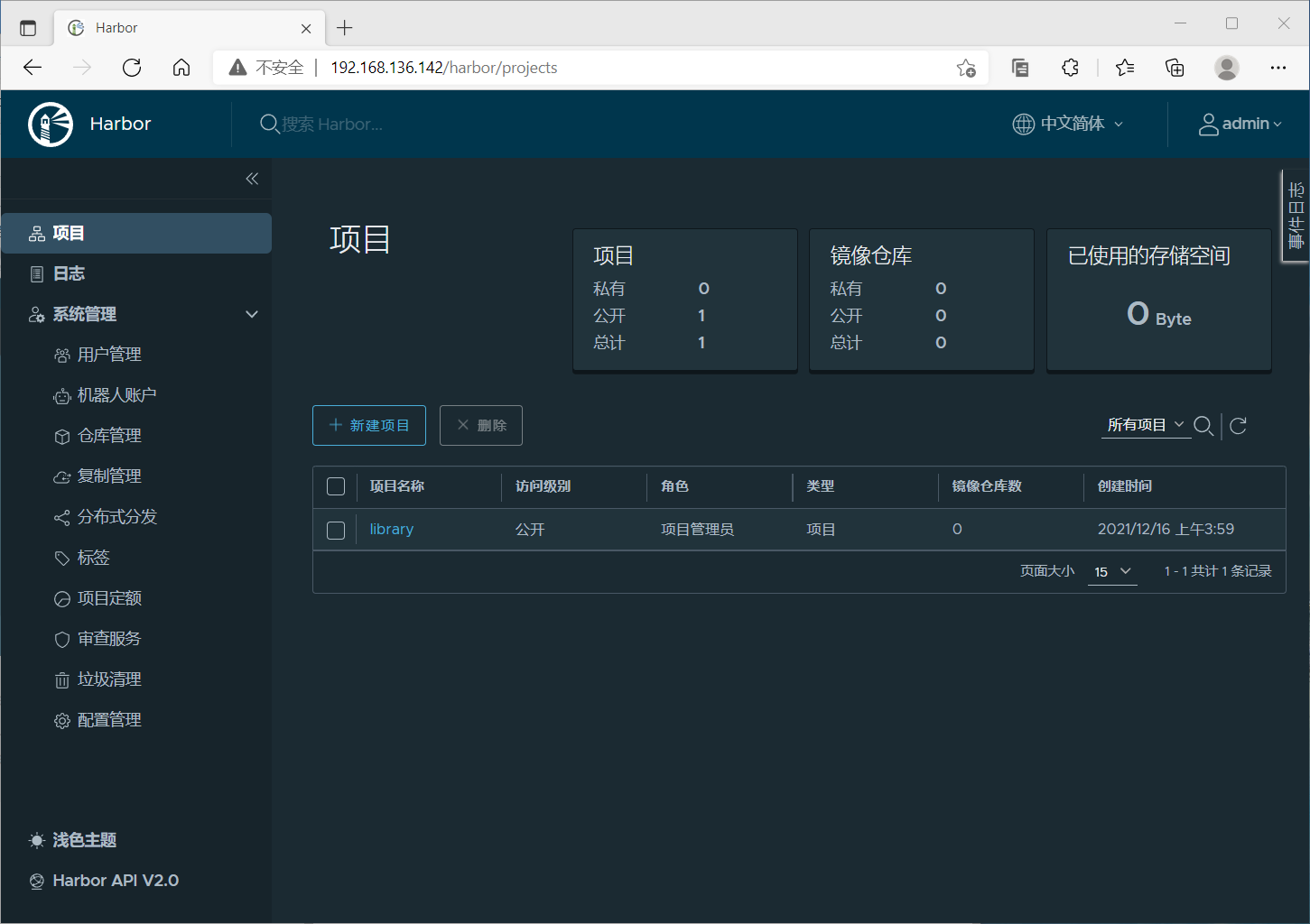
Install the docke service on the client
//Install docker
[root@node2 ~]# cd /etc/yum.repos.d/
[root@node2 yum.repos.d]# curl -o docker-ce.repo https://mirrors.tuna.tsinghua.edu.cn/docker-ce/linux/centos/docker-ce.repo
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 100 1919 100 1919 0 0 3360 0 --:--:-- --:--:-- --:--:-- 3360
[root@node2 yum.repos.d]# ls
CentOS-Linux-AppStream.repo CentOS-Linux-HighAvailability.repo
CentOS-Linux-BaseOS.repo CentOS-Linux-Media.repo
CentOS-Linux-ContinuousRelease.repo CentOS-Linux-Plus.repo
CentOS-Linux-Debuginfo.repo CentOS-Linux-PowerTools.repo
CentOS-Linux-Devel.repo CentOS-Linux-Sources.repo
CentOS-Linux-Extras.repo docker-ce.repo
CentOS-Linux-FastTrack.repo salt.repo
[root@node2 yum.repos.d]# sed -i 's@https://download.docker.com@https://mirrors.tuna.tsinghua.edu.cn/docker-ce@g' docker-ce.repo
[root@node2 yum.repos.d]# yum -y install docker-ce
[root@node2 yum.repos.d]# sudo mkdir -p /etc/docker
[root@node2 yum.repos.d]# cd
[root@node2 ~]# sudo tee /etc/docker/daemon.json <<-'EOF'
> {
> "registry-mirrors": ["https://pvurwzu6.mirror.aliyuncs.com"]
> }
> EOF
{
"registry-mirrors": ["https://pvurwzu6.mirror.aliyuncs.com"]
}
[root@node2 ~]# systemctl daemon-reload
[root@node2 ~]# systemctl restart docker
//Modify the daemon JSON file
[root@node2 ~]# vim /etc/docker/daemon.json
[root@node2 ~]# cat /etc/docker/daemon.json
{
"insecure-registries": ["registry.example.com"]
}
[root@node2 ~]# systemctl restart docker
//Log in to private warehouse
[root@node2 ~]# docker login registry.example.com
Username: admin
Password:
WARNING! Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
//Pull image the image pulled here is pulled from the official
[root@node2 ~]# docker pull busybox
Using default tag: latest
latest: Pulling from library/busybox
3cb635b06aa2: Pull complete
Digest: sha256:b5cfd4befc119a590ca1a81d6bb0fa1fb19f1fbebd0397f25fae164abe1e8a6a
Status: Downloaded newer image for busybox:latest
docker.io/library/busybox:latest
//Modify name
[root@node2 ~]# docker tag busybox:latest registry.example.com/library/busybox:0.1
[root@node2 ~]# docker images
REPOSITORY TAG IMAGE ID CREATED SIZE
busybox latest ffe9d497c324 7 days ago 1.24MB
registry.example.com/library/busybox 0.1 ffe9d497c324 7 days ago 1.24MB
//Upload image
[root@node2 ~]# docker push registry.example.com/library/busybox:0.1
The push refers to repository [registry.example.com/library/busybox]
64cac9eaf0da: Pushed
0.1: digest: sha256:50e44504ea4f19f141118a8a8868e6c5bb9856efa33f2183f5ccea7ac62aacc9 size: 527
View in the server web interface
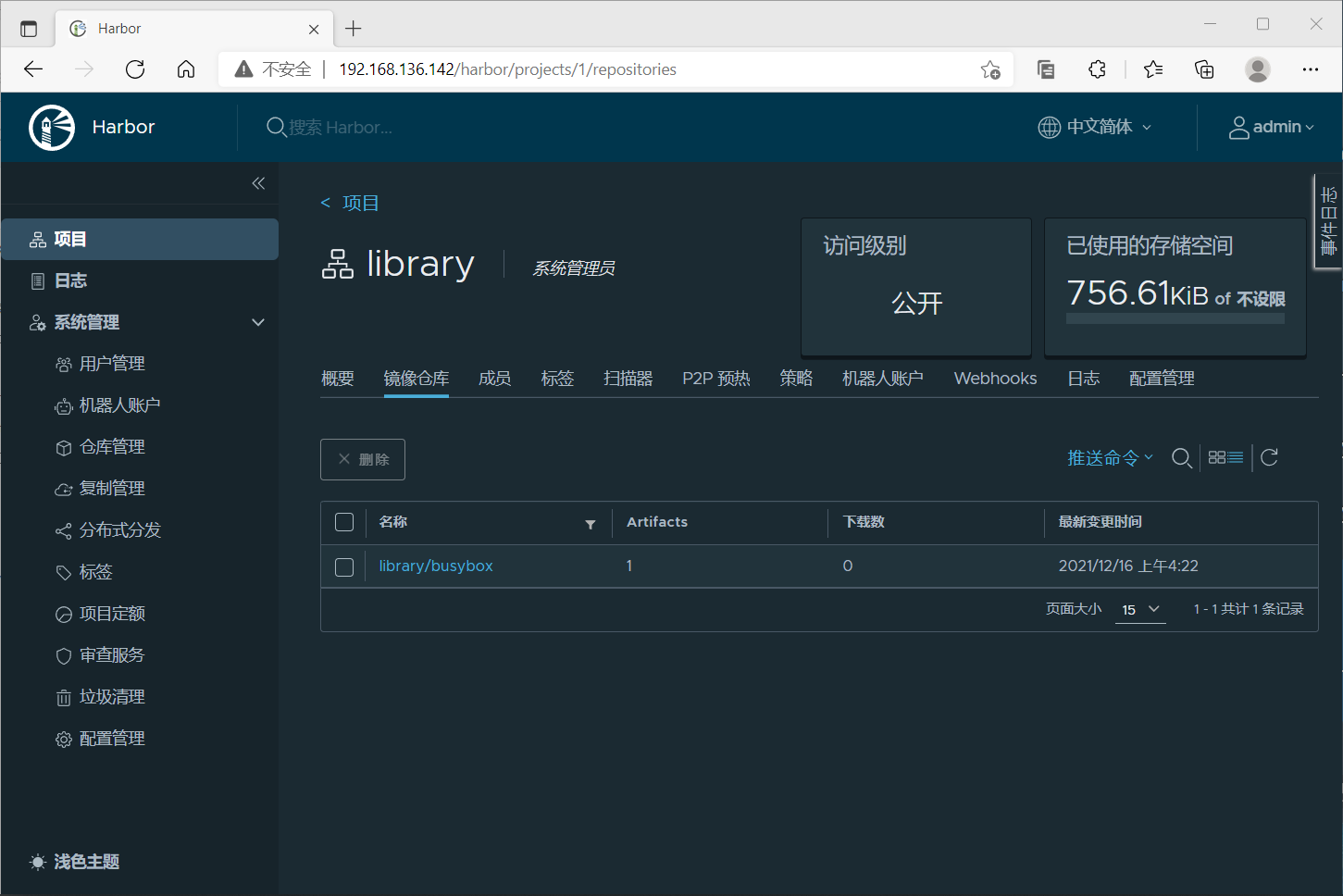
After deleting the image, try to pull in the private warehouse
[root@node2 ~]# docker rmi registry.example.com/library/busybox:0.1 Untagged: registry.example.com/library/busybox:0.1 Untagged: registry.example.com/library/busybox@sha256:50e44504ea4f19f141118a8a8868e6c5bb9856efa33f2183f5ccea7ac62aacc9 [root@node2 ~]# docker images REPOSITORY TAG IMAGE ID CREATED SIZE busybox latest ffe9d497c324 7 days ago 1.24MB [root@node2 ~]# docker pull registry.example.com/library/busybox:0.1 0.1: Pulling from library/busybox Digest: sha256:50e44504ea4f19f141118a8a8868e6c5bb9856efa33f2183f5ccea7ac62aacc9 Status: Downloaded newer image for registry.example.com/library/busybox:0.1 registry.example.com/library/busybox:0.1 [root@node2 ~]# docker images REPOSITORY TAG IMAGE ID CREATED SIZE busybox latest ffe9d497c324 7 days ago 1.24MB registry.example.com/library/busybox 0.1 ffe9d497c324 7 days ago 1.24MB //Very fast
Precautions for using Harbor:
- When uploading an image on the client, you must remember to execute docker login for user authentication, otherwise you cannot directly push
- If https is not used on the client, it must be in / etc / docker / daemon Configure the insert registers parameter in the JSON configuration file
- The data storage path shall be configured into a shared storage with sufficient capacity in the configuration file
- Harbor is managed by using the docker compose command. If you need to stop harbor, you can also use docker compose stop. For other parameters, please – help