General Introduction
Single sign-on system (SSO) is one of the most popular solutions for business integration in enterprises.SSO is defined as multiple applications in which users only need to log in once to access all mutually trusted applications.Any SSO framework needs to create a unified certification center!
Solve the problem
When we have multiple systems and each system needs to do login operation, we will encounter very tedious problems (frequent login), inaccessible and authorization problems when other services are invoked, so how to solve this problem?We used the SSO framework.
Framework introduction
We use the MaJiaSSO framework to solve the single sign-on problem.This framework uses a very simple, five-minute integrated framework, uses JWT as a Token, does not rely on any storage, users can carry custom information, and can customize Token encrypted salt.We just need to create a unified authentication service that we use to authenticate user logins and to authenticate acquisition of Tokens.When accessing other services, you only need to bring Token with you to access them.We can use the @NoToken annotation to control the release of request mappings that do not require annotations.
Contrast Advantages
- Not dependent on any storage (most SSO s rely on caching/Redis/Mysql, etc.)
- Plug and play, five-minute integration
- Token is based on JWT, so users can carry their own information
- User-defined encrypted salt, safe and convenient
- Simple and convenient to control requests based on annotations
- Interceptor-based dynamic control of interception requests (recommended to intercept all/** using @NoToken control)
- Authentication server restart has no effect, no cache
Use SSO framework
Establish Unified Certification Center
Introduction of pom
<parent> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-parent</artifactId> <version>1.5.10.RELEASE</version> <relativePath /> </parent> <dependencies> <dependency> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-web</artifactId> </dependency> <!-- sso core --> <dependency> <groupId>com.majiaxueyuan</groupId> <artifactId>sso-core</artifactId> <version>1.2.2</version> </dependency> </dependencies>
Logon Request Controller
Here, for convenience, Sql services are not written, provided that the user name and password are admin/123456, respectively, indicating that the authentication has passed.
When the authentication passes, call the method loginSuccess, pass in the parameter (unique ID, user name, other information, custom encrypted salt), determine if the return status code is 200, and if so, get the data directly is the TOKEN value.
@RestController
public class LoginController {
@RequestMapping("/login")
public String login(String username, String password) {
if (username.equals("admin") && password.equals("123456")) {
// Indicates successful login
JSONObject json = new JSONObject();
json.put("username", username);
json.put("role", new ArrayList<String>(Arrays.asList("admin", "normal")));
Result loginSuccess = TokenLoginHelper.loginSuccess(1L, username, json.toJSONString(), "token-salt");
if (loginSuccess.getCode().equals(200)) {
String token = loginSuccess.getData().toString();
System.out.println(token);
return "token:" + token;
}
return "Logon Failure";
}
return "failed";
}
}
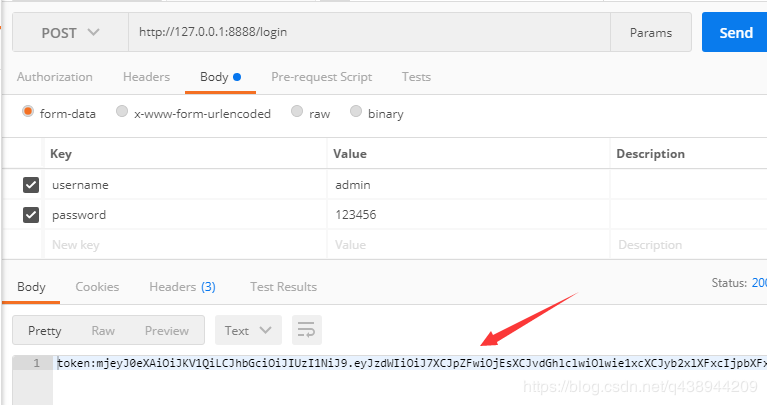
The certification service is integrated here
General Service Integration MaJiaSSO
For normal services, the same is true for one service and the same is true for two services...The same is true for 100 services.
IMPORTANT: When integrating, we need to be aware that the setting of encrypted salt should be consistent with the authorization center (a lock must correspond to its key to unlock it).
Integration steps:
- Create a normal SpringBoot service
- Reference to Jar Package
- Add Interceptor
- Release requests that do not require authentication
Integration is over!!!
pom.xml
<parent> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-parent</artifactId> <version>1.5.10.RELEASE</version> <relativePath /> </parent> <dependencies> <dependency> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-web</artifactId> </dependency> <dependency> <groupId>com.majiaxueyuan</groupId> <artifactId>sso-core</artifactId> <version>1.2.2</version> </dependency> </dependencies>
Add the MaJiaSSO interceptor and set the encrypted salt
@Configuration
public class MaJiaSsoConfig extends WebMvcConfigurerAdapter {
@Override
public void addInterceptors(InterceptorRegistry registry) {
registry.addInterceptor(ssoIntercepter()).addPathPatterns("/**");
}
@Bean
public MaJiaSSOIntercepter ssoIntercepter() {
return new MaJiaSSOIntercepter().setTokenSalt("token-salt");
}
}
Release some requests and get the information we keep in Token
The / hello request requires us to take Token with us for access, while the / hi request uses annotations to free up verification, coded as follows
@RestController
public class ClientController {
@RequestMapping("/hello")
public String hello(HttpServletRequest req) {
SSOUser user = (SSOUser) req.getAttribute("ssoUser");
System.out.println(user.toString());
return "hello";
}
@RequestMapping("/hi")
@NoToken(notNeedToken = true)
public String wei() {
return "hi,no token!";
}
}
Access diagram (no Token required, annotated by NoToken)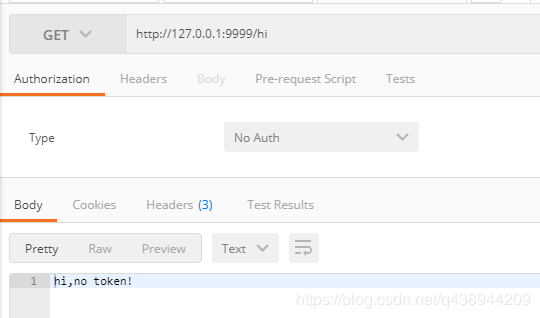
Requires Token to be accessed when it is not carried (returns Code401) and prompts illegal requests when Token is illegal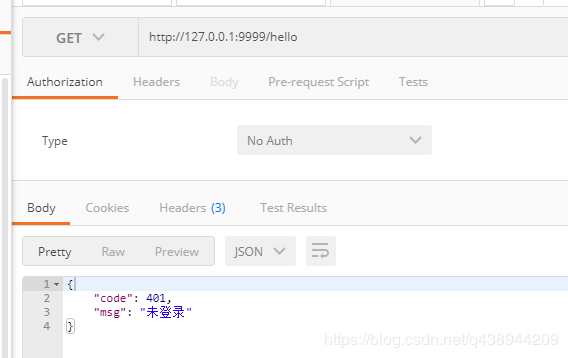
Access when carrying Token normally, and the console prints out all the information we carry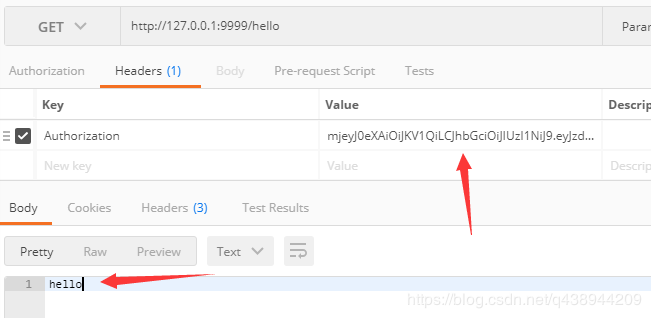
Console Prints Carried Information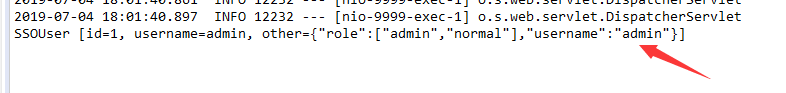
When accessing with a wrong Token, we can understand that someone maliciously attacked our system and gave us a hint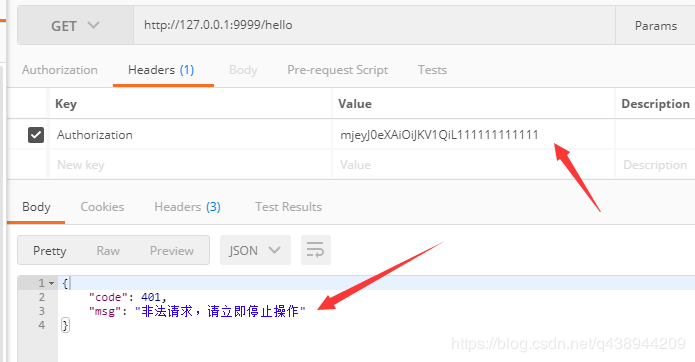
Here we've integrated MaJiaSSO successfully, adding many services, adding interceptors for each service is OK!SSO is that simple.
Link: http://www.imooc.com/article/288908
Author: LLL Lei Yi Sheep