What is selinux
selinux, kernel-level enhanced firewall
(File impact, security context) Label files and services, program labels and file labels are inconsistent (you can't see the file)
(Impact on Services) Remove unsafe functionality from services, restrict program functionality, and restrict (can't be removed) on the kernel.
selinux has three levels: disabled, permissive, enforcing
How to manage selinux levels
vim /etc/sysconfig/selinux reboot ##After changes to the configuration file, you need to restart it for it to take effect

selinux=disabled ##Closed state
selinux=Enforcing ##Turn on mandatory state - once the policy is violated, it cannot continue.
selinux=Permissive ##Opens a warning state - allows you to continue even if a policy has been violated, but records the violations.
getenforce ##View Status
This can be toggled on and off
setenforce 1 ## is set as mandatory
setenforce 0 ## set as warning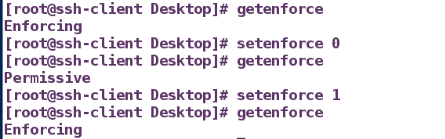
There is no security context when selinux is disabled.The functionality of files and services will not be limited.
[root@localhost ~]# touch /mnt/file1 #new file [root@localhost ~]# mv /mnt/file1 /var/ftp/ #Move it to the Public Home Directory [root@localhost ~]# ls /var/ftp/ file1 pub [root@localhost ~]# lftp 172.25.254.204 #Access using anonymous users lftp 172.25.254.204:~> ls #You can see all existing files without security context restrictions -rw-r--r-- 1 0 0 0 Apr 19 01:33 file1 drwxr-xr-x 2 0 0 31 Mar 07 2014 pub lftp 172.25.254.204:/> quit [root@localhost ~]# ls -Z /var/ftp/ #No security context is displayed in disabled state? -rw-r--r-- root root ? file1 drwxr-xr-x root root ? pub [root@localhost ~]# lftp 172.25.254.204 -u student #Access with local users Password: lftp student@172.25.254.204:~> ls -rw-r--r-- 1 1000 1000 2005 Apr 18 07:10 passwd lftp student@172.25.254.204:~> put /etc/group #A normal upload function was performed 850 bytes transferred lftp student@172.25.254.204:~> ls #Successfully uploaded file -rw-r--r-- 1 1000 1000 850 Apr 19 01:35 group -rw-r--r-- 1 1000 1000 2005 Apr 18 07:10 passwd lftp student@172.25.254.204:~> quit
When selinux is in Enforcing, there is a security context.The functionality of files and services is limited.
[root@localhost ~]# vim /etc/sysconfig/selinux [root@localhost ~]# reboot #Modify selinux status to Enforcing in configuration file [root@localhost ~]# getenforce # View selinux status Enforcing [root@localhost ~]# ls -Z /var/ftp/ #View the security context of content in the directory -rw-r--r--. root root system_u:object_r:public_content_t:s0 file1 drwxr-xr-x. root root system_u:object_r:public_content_t:s0 pub [root@localhost ~]# LFTP 172.25.254.204-u student accesses using local users Password: lftp student@172.25.254.204:~> ls -rw-r--r-- 1 1000 1000 2005 Apr 18 07:10 passwd lftp student@172.25.254.204:~> put /etc/group put: Access failed: 553 Could not create file. (group) #Unable to upload function, function is limited. lftp student@172.25.254.204:~> quit [root@localhost ~]# touch /mnt/file2 [root@localhost ~]# mv /mnt/file2 /var/ftp/ #Create a new file again and move it to the public home directory [root@localhost ~]# ls /var/ftp/ file1 file2 pub #The file does exist in the directory [root@localhost ~]# lftp 172.25.254.204 lftp 172.25.254.204:~> ls #However, the file 2 cannot be displayed for viewing after connection -rw-r--r-- 1 0 0 0 Apr 19 01:33 file1 drwxr-xr-x 2 0 0 31 Mar 07 2014 pub lftp 172.25.254.204:/> quit [root@localhost ~]# ls -Z /var/ftp/ #View the security context of the file -rw-r--r--. root root system_u:object_r:public_content_t:s0 file1 -rw-r--r--. root root unconfined_u:object_r:mnt_t:s0 file2 #Where file2's security context is not appropriate drwxr-xr-x. root root system_u:object_r:public_content_t:s0 pub
How to change the file security context
(1) Definition
The security context is a simple and consistent access control property, which is mainly reflected in the following two points:
A. For files: Restrict file access.The file must have a matching security context in order for being to recognize access.
b. For services: Restrict service functions considered unsafe to set switches.The switch is off by default and can be turned on when needed.
(2) View
Ls-Z ##Check the security context of files and directories;
Ps-Z ##Check the security context of the process;
mv: the security context does not change;
cp: The security context is regenerated.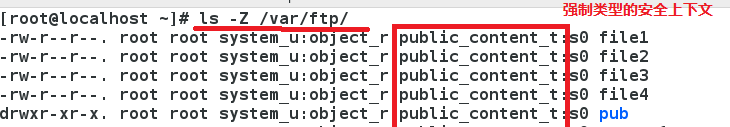
Temporary change
Chcon-t Security Context File
chcon -t public_content_t /publicftp -R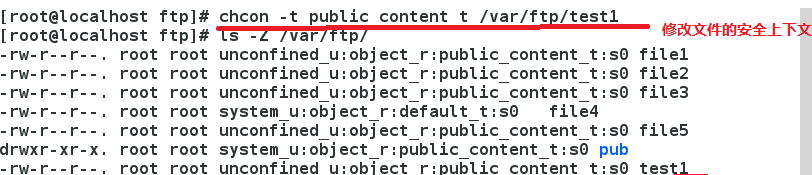
Turn off kernel firewall restart, turn on kernel firewall restart/publicftp security context restore
Semanage fcontext-l | grep / publicftp ##Kernel context security list
Nothing found so it will be restored
Permanent Change
Instant commands add directories to the kernel context security list
Semanage fcontext-l ##Lists the contents of the kernel security context list
semanage fcontext -a -t public_content_t '/publicftp(/.*)?'
Restorecon-R VV F/publicftp/ ##R VV Displays F Refresh
semanage fcontext -a -t public_content_t "/var/lala(/.*)?" #Permanently changes the security context of the directory; (/. *)? Indicates the directory itself, as well as existing and future new files. restorecon -R /var/lala/ # Scan after that to make the changes take effect. semanage fcontext -l |grep /var/ftp #View the security context settings for directory/var/ftp.
How can anonymous users upload when on (in the case of vstp's profile ok)
Change Security Context
ls -Zd /var/ftp/pub
Drwxr-x r-x. root system_u:object_r:public_content_t:s0/var/ftp/pub ## is not writable. SELINUX files are read-only and need to be added
Chcon-t public_content_rw_t/var/ftp/pub ##Add Write
How to control selinux switch on service function
Getsebool-a | grep service name
getsebool -a | grep ftp
Setsebool-P function bool value on|off ##P permanently open function
setsebool -P ftpd_anon_write on
[root@localhost ~]# setsebool -P ftp_home_dir 1 ##Set up bool Value is 1;-P ##Permanently open [root@localhost ~]# getsebool -a | grep ftp ##View bool value of ftp ftp_home_dir --> on ##bool value of 1 is set successfully, after modification, upload and delete functions of local users can be used normally ftpd_anon_write --> off ftpd_connect_all_unreserved --> off ftpd_connect_db --> off ftpd_full_access --> off ftpd_use_cifs --> off ftpd_use_fusefs --> off ftpd_use_nfs --> off ftpd_use_passive_mode --> off httpd_can_connect_ftp --> off httpd_enable_ftp_server --> off sftpd_anon_write --> off sftpd_enable_homedirs --> off sftpd_full_access --> off sftpd_write_ssh_home --> off tftp_anon_write --> off tftp_home_dir --> off [root@localhost ~]# lftp 172.25.4.104 -u student Password: lftp student@172.25.4.104:~> ls -rw-r--r-- 1 1000 1000 2005 Apr 21 16:11 passwd lftp student@172.25.4.104:~> put /etc/group 850 bytes transferred lftp student@172.25.4.104:~> ls -rw-r--r-- 1 1000 1000 850 Apr 21 16:22 group -rw-r--r-- 1 1000 1000 2005 Apr 21 16:11 passwd ##User uploaded successfully for this lftp student@172.25.4.104:~> rm group ##Local User Deleted Successfully rm ok, `group' removed lftp student@172.25.4.104:~> ls -rw-r--r-- 1 1000 1000 2005 Apr 21 16:11 passwd lftp student@172.25.4.104:~> exit
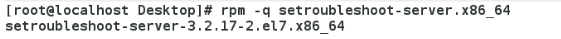
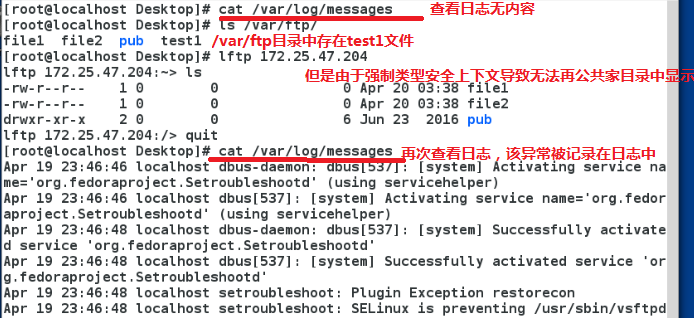
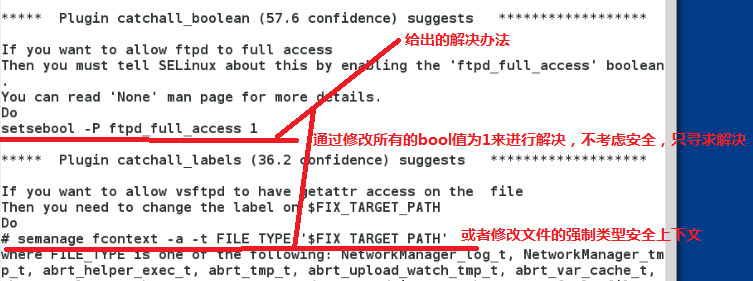
Monitor selinux error messages
setroubleshoot-server.x86_64 #This plug-in provides solutions to problems with selinux
/var/log/audit/audit.log Record the log of the problem
/var/log/messages provides problems and Solutions