It's a pity that the day of the competition is the day when I have the most things this month. I have less than 30 minutes to do the question. The picture question almost came out
In the final analysis, I'm too delicious. I'll work hard next time
I packed a copy of the title attachment:
Link: https://pan.baidu.com/s/1txp06OAZL9Ce-qN_VQhLtg
Extraction code: v9j7
Winter Olympics_ is_coming
The previous operation is the basic operation. binwalk separates a compressed package and finds a prompt at the comment information
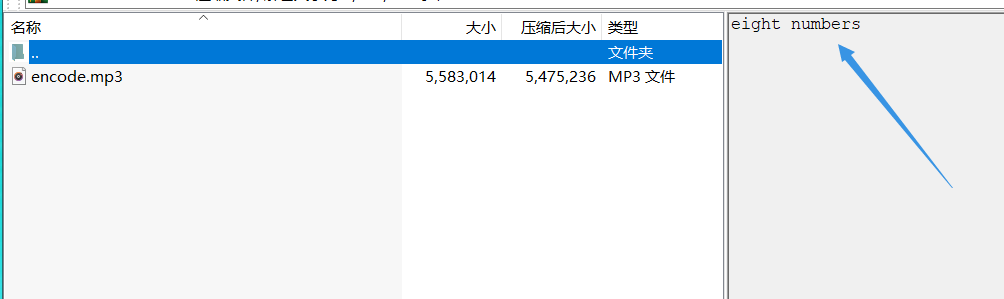
First look at the spectrum and waveform of the obtained mp3 file with Audacity. If there is no abnormality, it should be mp3 steganography. The eight numbers prompted here should be the hint of password. The theme of the Winter Olympic Games + 8 digits. It is easy to think of the date of the Winter Olympic Games: 20204
Using MP3Stego, the command is as follows, and the decryption is successful
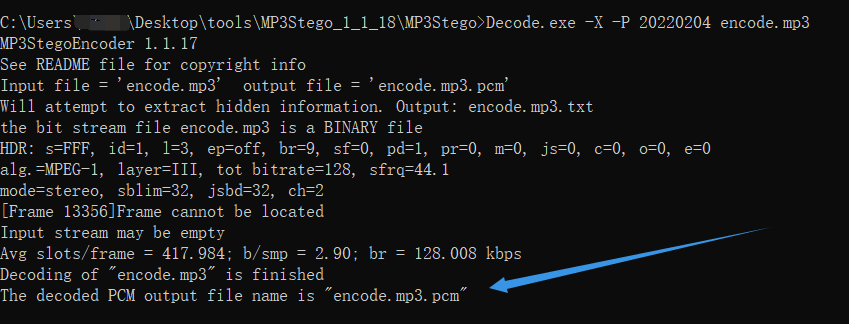
Decoded text encode mp3. Txt is as follows. If you observe carefully, you will find that there are some spaces in the middle for segmentation
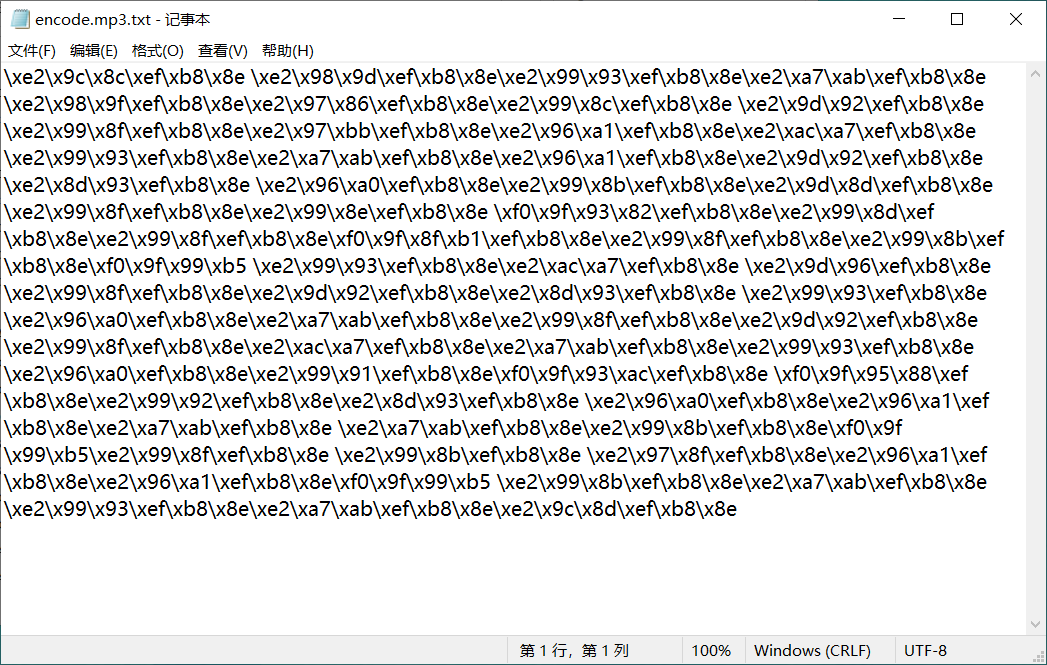
So write a script to remove \ x, and then convert the hexadecimal to characters to get
It was stuck here at that time. Unfortunately, I didn't recognize the character at that time. After the game, I found that I had done this test site before... It was wingdings, bugku's misc title, drunkenness and carnival. That's the character I got. Go Online website decrypt
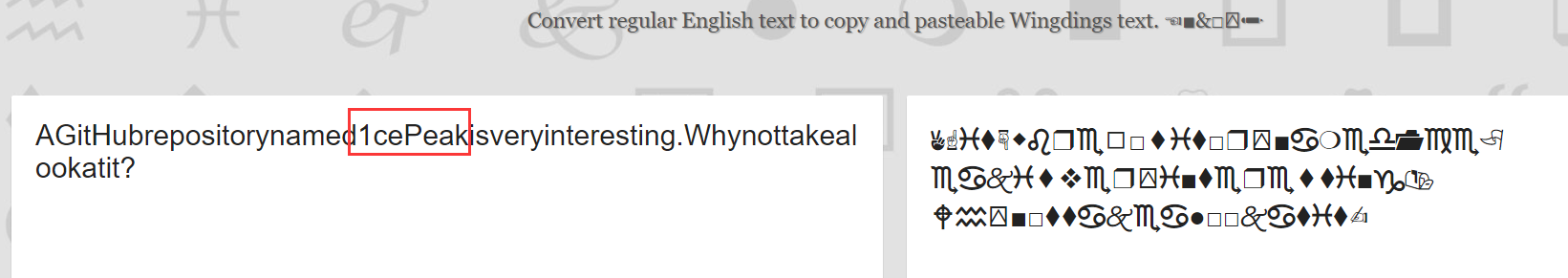
It should have been separated by spaces. The spaces were ignored in the previous decoding process, but a little attention can be found. Let's go to github to find a project named 1cePeak. Project address: https://github.com/Tr0jAnV1rU4/1cePeak/blob/main/A/post-checkout
Click here to download the file
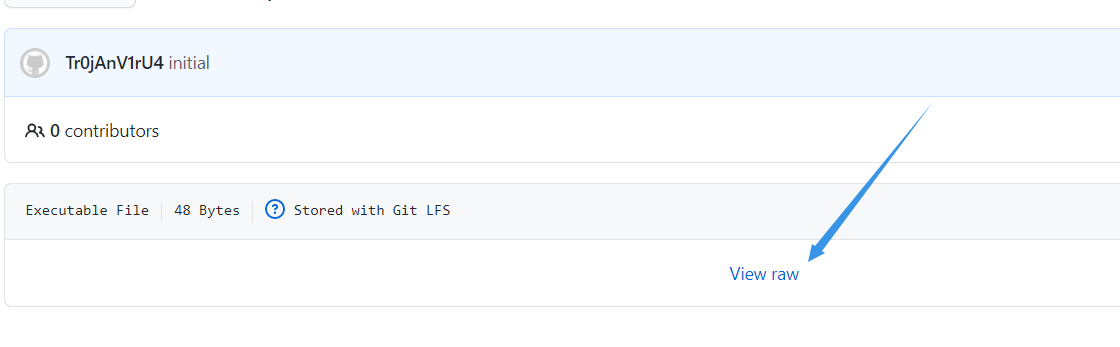 Open with notepad and find the following contents
Open with notepad and find the following contents
#!/bin/sh
echo How_6ad_c0uld_a_1cePeak_be? >&2
How_6ad_c0uld_a_1cePeak_be? I don't know what's the use for the moment. I turn around and look at the pictures and mp3 files. I find a cipher at the end of the mp3 file
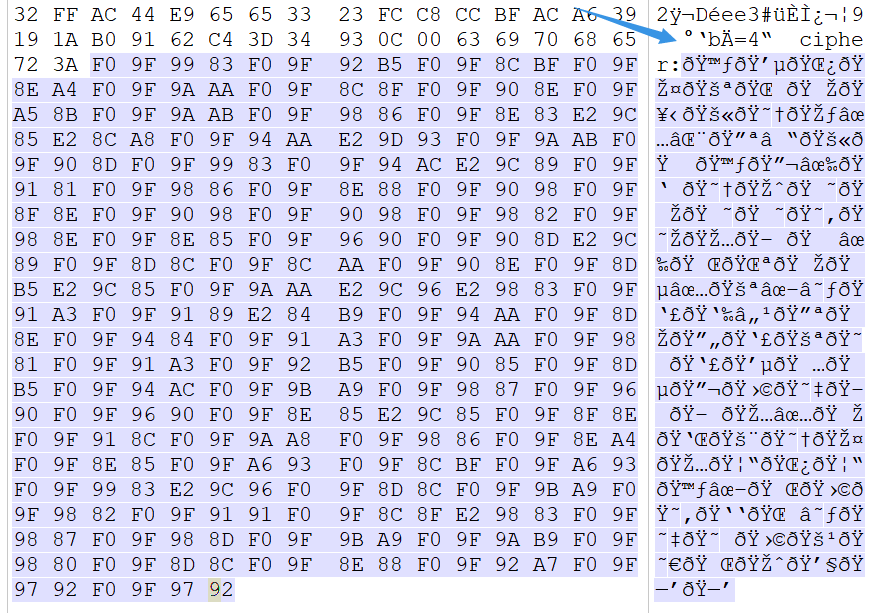
So copy the hexadecimal value of the following content, take it to convert characters, and solve a pile of emoji
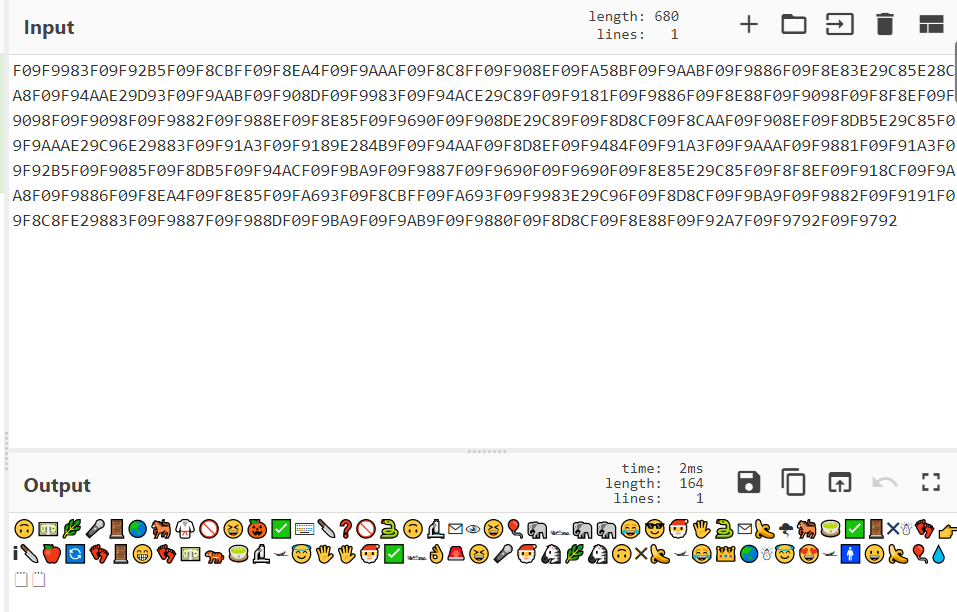
So use emoji-aes Decryption. The key here is the character just solved. The flag is successfully solved
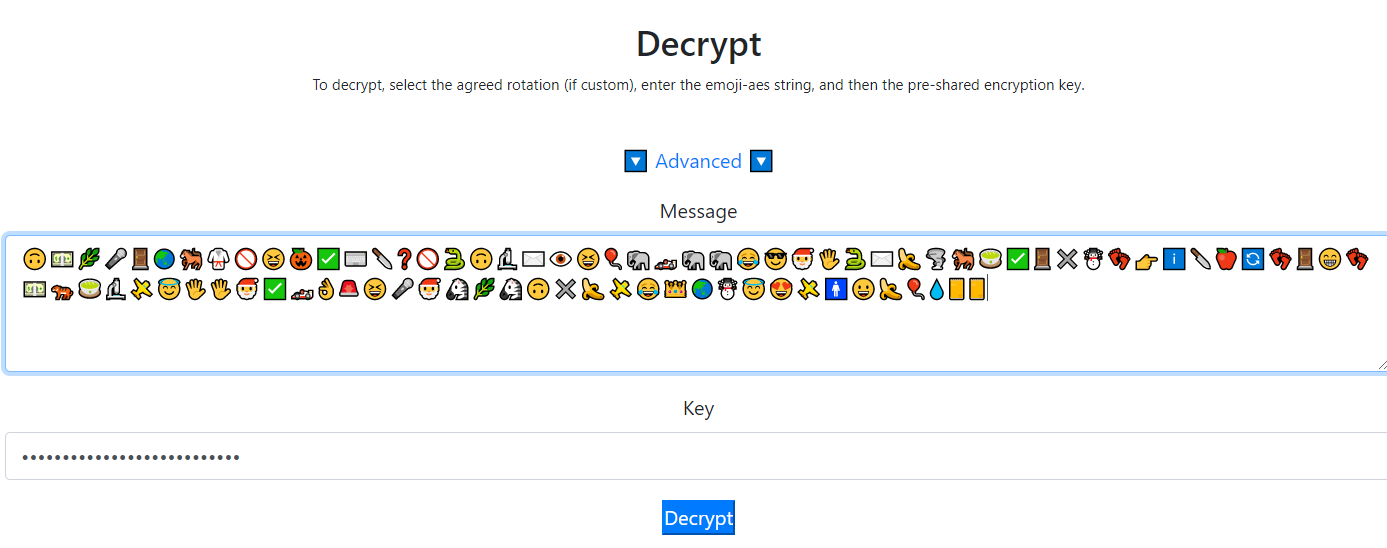
I_will_but_not_quite
Gave an encrypted py script and twin Vmem, it is obvious that we need memory forensics, get the key information, and then come back to write the decryption script.
First analyze the image: Python vol.py - f twin vmem imageinfo
Know that the system version is Win7SP1x64
Then analyze the process: Python vol.py - f twin vmem --profile=Win7SP1x64 pslist
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit ------------------ -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------ 0xfffffa8000cbfb30 System 4 0 84 515 ------ 0 2021-03-29 09:44:08 UTC+0000 0xfffffa80012734f0 smss.exe 256 4 2 29 ------ 0 2021-03-29 09:44:08 UTC+0000 0xfffffa8001e1c3d0 csrss.exe 332 324 9 416 0 0 2021-03-29 09:44:15 UTC+0000 0xfffffa80019e5b30 csrss.exe 384 376 11 310 1 0 2021-03-29 09:44:16 UTC+0000 0xfffffa8001ef3920 wininit.exe 392 324 3 77 0 0 2021-03-29 09:44:16 UTC+0000 0xfffffa8001ebe910 winlogon.exe 424 376 3 113 1 0 2021-03-29 09:44:16 UTC+0000 0xfffffa8001efeb30 services.exe 488 392 7 194 0 0 2021-03-29 09:44:17 UTC+0000 0xfffffa8001f35330 lsass.exe 496 392 7 592 0 0 2021-03-29 09:44:18 UTC+0000 0xfffffa8001f42b30 lsm.exe 508 392 10 141 0 0 2021-03-29 09:44:18 UTC+0000 0xfffffa80022bf6f0 svchost.exe 600 488 11 347 0 0 2021-03-29 09:44:23 UTC+0000 0xfffffa80022ddb30 svchost.exe 672 488 8 275 0 0 2021-03-29 09:44:24 UTC+0000 0xfffffa800231a700 svchost.exe 764 488 20 459 0 0 2021-03-29 09:44:24 UTC+0000 0xfffffa8002328210 svchost.exe 800 488 16 368 0 0 2021-03-29 09:44:25 UTC+0000 0xfffffa8002357660 svchost.exe 824 488 33 948 0 0 2021-03-29 09:44:25 UTC+0000 0xfffffa800237fb30 svchost.exe 992 488 10 520 0 0 2021-03-29 09:44:26 UTC+0000 0xfffffa80023da390 svchost.exe 344 488 15 483 0 0 2021-03-29 09:44:27 UTC+0000 0xfffffa80024197d0 spoolsv.exe 1032 488 12 315 0 0 2021-03-29 09:44:29 UTC+0000 0xfffffa800242cb30 svchost.exe 1072 488 19 307 0 0 2021-03-29 09:44:29 UTC+0000 0xfffffa800228ab30 vmtoolsd.exe 1244 488 9 281 0 0 2021-03-29 09:44:31 UTC+0000 0xfffffa8002601b30 taskhost.exe 1508 488 9 206 1 0 2021-03-29 09:44:35 UTC+0000 0xfffffa8002610b30 dwm.exe 1724 800 3 68 1 0 2021-03-29 09:44:36 UTC+0000 0xfffffa800101bb30 TPAutoConnSvc. 1760 488 10 140 0 0 2021-03-29 09:44:36 UTC+0000 0xfffffa8002674b30 explorer.exe 1792 1636 44 879 1 0 2021-03-29 09:44:37 UTC+0000 0xfffffa80025c5b30 dllhost.exe 2024 488 13 186 0 0 2021-03-29 09:44:38 UTC+0000 0xfffffa8002526b30 TPAutoConnect. 1356 1760 5 118 1 0 2021-03-29 09:44:39 UTC+0000 0xfffffa8002713060 conhost.exe 1428 384 1 32 1 0 2021-03-29 09:44:39 UTC+0000 0xfffffa8002537b30 msdtc.exe 1744 488 12 144 0 0 2021-03-29 09:44:40 UTC+0000 0xfffffa8002840b30 vmtoolsd.exe 2160 1792 7 297 1 0 2021-03-29 09:44:45 UTC+0000 0xfffffa80028a6b30 SearchIndexer. 2416 488 11 656 0 0 2021-03-29 09:44:53 UTC+0000 0xfffffa80028c1b30 jusched.exe 2496 2200 6 377 1 1 2021-03-29 09:44:55 UTC+0000 0xfffffa80029d6680 svchost.exe 2748 488 7 110 0 0 2021-03-29 09:45:05 UTC+0000 0xfffffa80023ef990 svchost.exe 860 488 13 333 0 0 2021-03-29 09:46:36 UTC+0000 0xfffffa80019dfb30 WmiPrvSE.exe 1440 600 7 109 0 0 2021-03-29 09:48:34 UTC+0000 0xfffffa8002749b30 jucheck.exe 2960 2496 7 368 1 1 2021-03-29 09:50:24 UTC+0000 0xfffffa8001e38b30 javaws.exe 400 2960 0 -------- 1 0 2021-03-29 09:50:24 UTC+0000 2021-03-29 09:50:24 UTC+0000 0xfffffa8001d0d200 jp2launcher.ex 1932 400 27 439 1 0 2021-03-29 09:50:24 UTC+0000 0xfffffa8001fc9060 taskeng.exe 3044 824 4 83 1 0 2021-03-30 07:52:37 UTC+0000 0xfffffa800282eb30 SearchProtocol 2020 2416 8 321 0 0 2021-03-30 07:55:59 UTC+0000 0xfffffa8001fb22b0 SearchFilterHo 3024 2416 5 98 0 0 2021-03-30 07:55:59 UTC+0000 0xfffffa8001fbb990 WinRAR.exe 1696 1792 18 564 1 0 2021-03-30 07:56:21 UTC+0000
Found WinRAR Exe is a little suspicious. It may have been compressed or decompressed. Use filescan with grep command to check rar and zip files
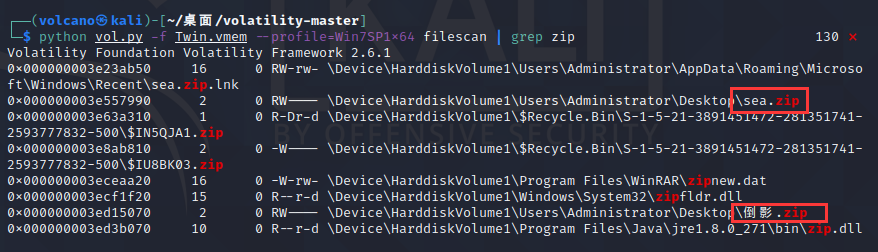
dump these two
python vol.py -f Twin.vmem --profile=Win7SP1x64 dumpfiles -Q 0x000000003ed15070 --dump-dir=./ python vol.py -f Twin.vmem --profile=Win7SP1x64 dumpfiles -Q 0x000000003e557990 --dump-dir=./
Get these two files, pull win10 back from kali, change the suffix, and then analyze
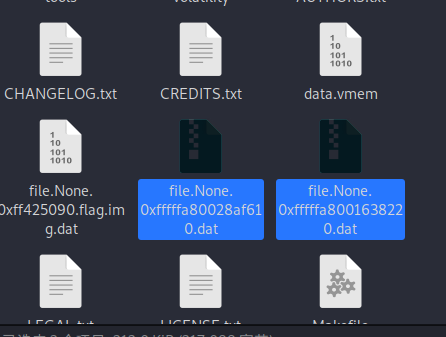
inverted reflection in water. After opening zip, change the suffix inside to jpg and drag it into winhex. After analysis, it is found that there is a string of base64 at the end
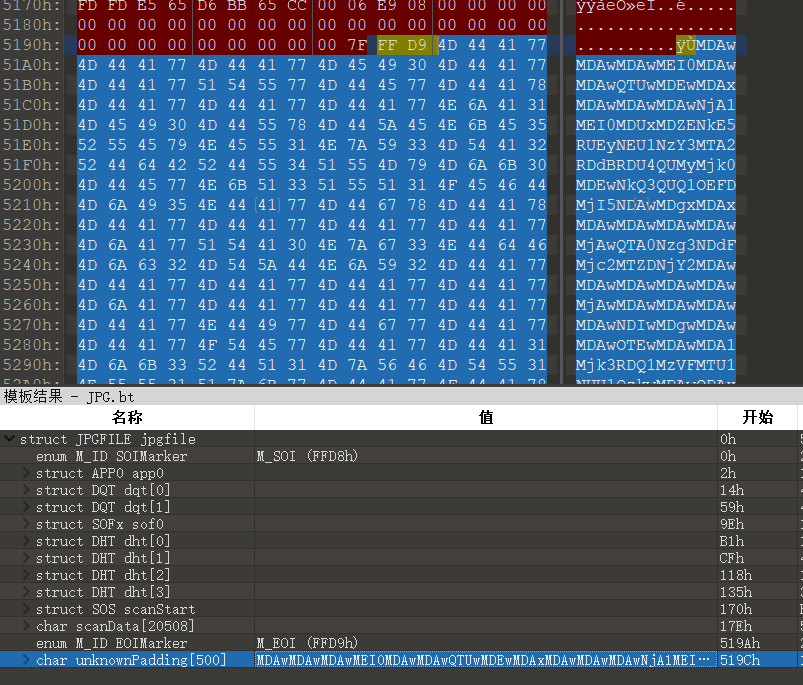
After decoding, look at the last few numbers, combine the reflection of the file name, turn the data upside down and save it as a 1 zip
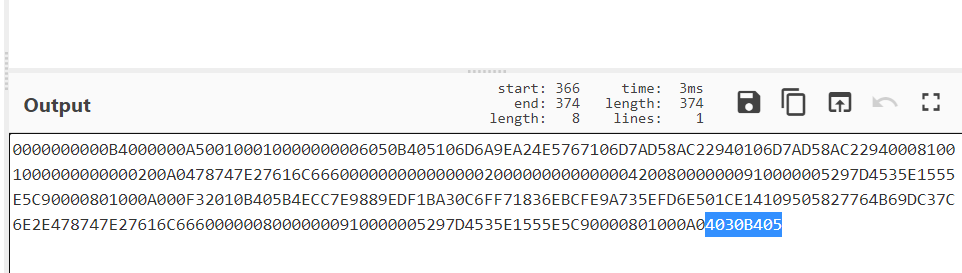
There's a flag in it Txt, but it can't be opened after encryption. I don't know if the person who made the question deliberately made a person's mentality
Another compressed package, sea There is a prompt in the comment information of zip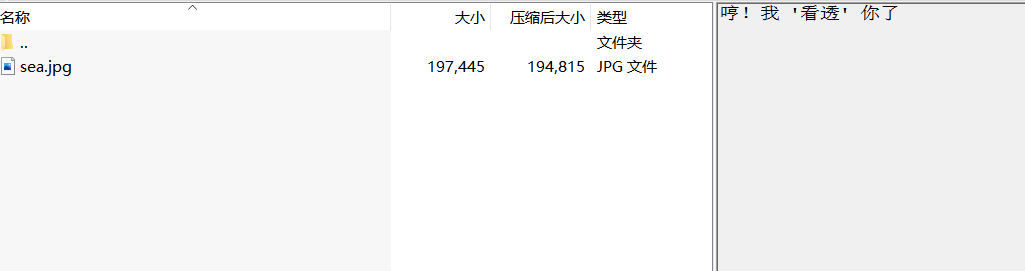
Seeing through here actually implies that the password is 123456 after the test
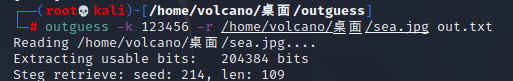
The solution is as follows:
4266gj2zn17b2jo5b62k73g22xg6j658350r5771vd40h4bd2ns33q30651y57s6752su3q05881hs3h53nb3603co2mv40l58n3da3f61i5
Direct hexadecimal to character, found that the solution is garbled. In fact, this is a double hex code. I haven't encountered it before, but there is a hint in the title. The file of memory forensics analysis just now shows that it is twin Online website Solution
Vnw3HC07BDgbBWNRGTx2fSckf399V1Z9CxIvHVd6fHsaEnR8fX40NyQ7JhM8CWV5fgMNN24=
The last step is to write the decryption script. Here we directly use taoshen mumuzi's taoshen blog: https://blog.csdn.net/qq_42880719
import base64
import random
secret = "Vnw3HC07BDgbBWNRGTx2fSckf399V1Z9CxIvHVd6fHsaEnR8fX40NyQ7JhM8CWV5fgMNN24="
dec = base64.b64decode(secret).decode("utf-8")
# for i in range(len(dec)):
# print(ord(dec[i]))
def r(s, num): #Caesar
l=""
for i in s:
if(ord(i) in range(97,97+26)):
l+=chr((ord(i)-97+num)%26+97)
else:
l+=i
return l
for i in range(86,128):
j = 1
tmp = [""]*len(dec)
tmp[-1] = chr(i)#Restore the last bit of blasting to restore all
while j != len(dec):
tmp[-j-1] = chr(ord(dec[-j])^ord(tmp[-j])) #Reverse XOR
j += 1
s = tmp[-1] #Because the last one is the last and the first XOR, the first XOR is actually the last one
for i in range(len(tmp)-1):
s += tmp[i]#Here is to splice the second to the last bit and add it after the first bit
try:
s = base64.b64decode(s).decode("utf-8")
for i in range(1,26):#Traverse Caesar
flag = r(s,i)
print(flag)
except:
pass
Suspect x's hard drive
I'm too delicious. I haven't reproduced the wp according to the bosses. I won't write it first