01... Getting started with redis caching
brief introduction
background
In our current project architecture, the Web server (Tomcat) and database are basically deployed independently and monopolize the server resources. With the growth of the number of users, concurrent reading and writing to the database will increase the pressure on database access and lead to performance degradation. In serious cases, it will directly lead to system downtime, for example:
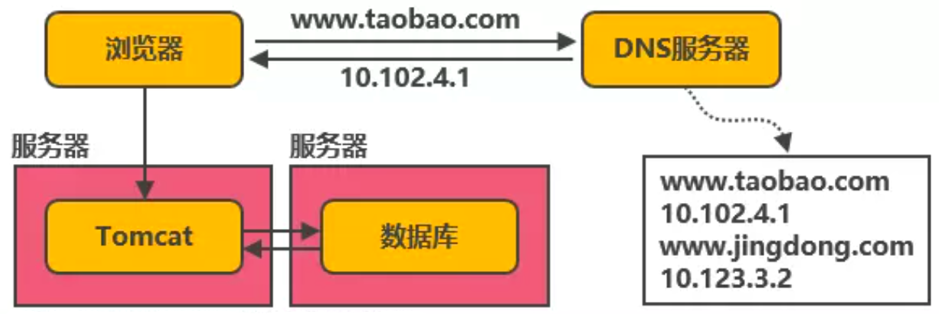
At this time, we can add local cache on the same Tomcat server and external distributed cache to cache popular data. That is, the cache can intercept most requests before reading and writing to the database, greatly reducing the pressure on the database. For example:
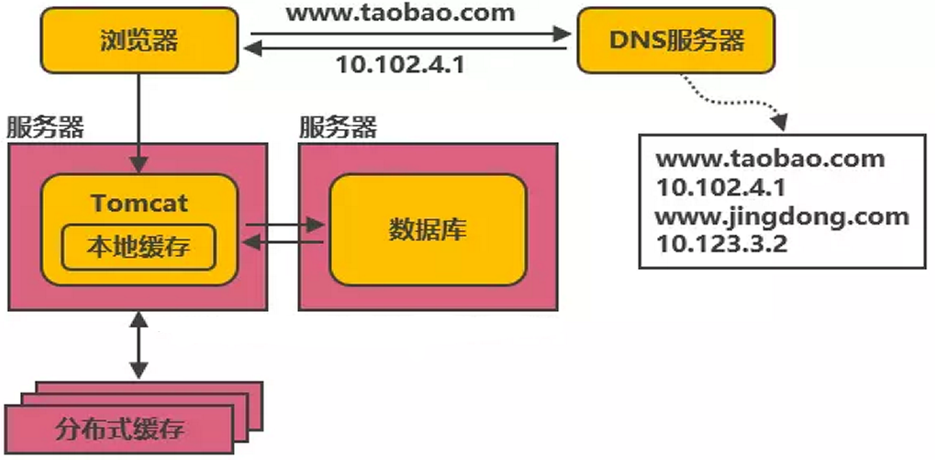
Based on such an architecture design, some distributed databases like redis were born.
Redis overview
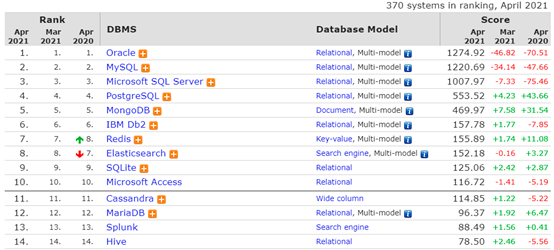
Redis is a key value storage system (official website: http://redis.io ), is a distributed cache database. In DB engines Redis ranks seventh in the database ranking of COM, as shown in the figure:
Version and reference description
Redis versions with even minor version numbers (numbers after the first decimal point) are stable versions (2.4, 2.6, etc.), and odd versions are unstable versions (2.5, 2.7), it is generally recommended to use a stable version in the production environment. The latest version 6.2.2 adds a stream processing method with higher performance. The official redis does not support the windows platform. The Windows version is a branch established by Microsoft and is compiled, released and maintained based on the official redis source code, so the redis version of the windows platform is slightly lower than the official version .
Redis related reference websites are as follows:
Bootnb relevant: https://www.runoob.com/redis/redis-tutorial.html Redis Official website: https://redis.io/ Source address: https://github.com/redis/redis Redis Online test: http://try.redis.io/ Redis Command Reference: http://doc.redisfans.com/
Redis initial operation
Start redis service
Startup in docker environment (multiple containers need to be run to start docker environment):
docker start redis01 #The bottom layer is also started through redis server. redis01 after the word start is the container name
View redis service in docker
docker ps
View the started redis process information
ps -ef|grep redis root 3511 1 0 16:29 ? 00:00:01 redis-server *:6379 root 3515 1 0 16:29 ? 00:00:01 redis-server 127.0.0.1:6380
Enter redis container
docker exec -it redis01 bash #redis01 container name
Log in to redis service
Log in to local redis
redis-cli perhaps redis-cli -p 6379 perhaps redis-cli -p 6379 -a password #-a is followed by password. Redis.com needs to be enabled for this operation requirepass option in conf file
Log in to remote redis
redis-cli -h ip -p6379 -a password
Enter the container directly and log in to the redis service
docker exec -it redis01 redis-cli
View redis information
First log in to redis, and then enter the info command, such as
127.0.0.1:6379> info #View the detailed configuration information of the current redis node
Clear redis screen
Clear redis screen content
127.0.0.1:6379> clear
Exit redis service
Exit the redis service, for example
127.0.0.1:6379> exit
Turn off redis service
Close the redis service, for example:
127.0.0.1:6379> shutdown
System help
You can view related instruction help based on the help instruction, for example:
127.0.0.1:6379> help
redis-cli 2.8.19
Type: "help @<group>" to get a list of commands in <group>
"help <command>" for help on <command>
"help <tab>" to get a list of possible help topics
"quit" to exit
127.0.0.1:6379> help type TYPE key summary: Determine the type stored at key since: 1.0.0 group: generic
Redis data storage operation
View key s in redis based on
127.0.0.1:6379> keys * (empty list or set)
Store data in the form of key/value
127.0.0.1:6379> set test1 666 ok 127.0.0.1:6379> set test2 888 ok 127.0.0.1:6379> keys * 1) "test1" 2) "test2"
Obtain data stored in redis based on key
127.0.0.1:6379> get test1 "666" 127.0.0.1:6379> get test2 "888" 127.0.0.1:6379> get test3 (nil) 127.0.0.1:6379>
Clear data in redis
Clear current database data
127.0.0.1:6379> flushdb ok
Clear all database data
127.0.0.1:6379> flushall ok
Key effective time design
In practice, we often need to control the effective duration of key s in redis, such as the timing of second kill operations, the effective duration of cached data, etc.
Expire (setting effective time - unit: seconds)
Syntax: exit key seconds
127.0.0.1:6379> set bomb tnt OK 127.0.0.1:6379> expire bomb 10 (integer) 1 127.0.0.1:6379> ttl bomb (integer) 5 127.0.0.1:6379> ttl bomb (integer) 3 127.0.0.1:6379> ttl bomb (integer) 3 127.0.0.1:6379> ttl bomb (integer) 2 127.0.0.1:6379> ttl bomb (integer) 1 127.0.0.1:6379> ttl bomb (integer) -2 127.0.0.1:6379> ttl bomb (integer) -2 127.0.0.1:6379>
Where, TTL views the remaining time of the key,
When the return value is - 2, the identification key is deleted.
When the key does not exist, - 2
When the key exists but the remaining lifetime is not set, - 1 is returned
Persist (cancel duration setting)
Use persist to invalidate the effective duration of specific key settings.
Syntax: PERSIST key
127.0.0.1:6379> set bomb tnt ok 127.0.0.1:6379> expire bomb 60 (integer) 1 127.0.0.1:6379> ttl bomb (integer) 49 127.0.0.1:6379> persist bomb (integer) 1 127.0.0.1:6379> ttl bomb (integer) -1 127.0.0.1:6379>
When setting new data, you need to reset the lifetime of the key, and resetting the value will also clear the lifetime.
pexpire (in milliseconds)
pexpire allows the effective duration of the key to be measured in milliseconds, which can achieve more accurate time control. For example, it can be applied to a scene.
Syntax: PEXPIRE key milliseconds
127.0.0.1:6379> set bomb tnt ok 127.0.0.1:6379> pexpire bomb 10000 (integer) 1 127.0.0.1:6379> ttl bomb (integer) 7 127.0.0.1:6379> ttl bomb (integer) 3 127.0.0.1:6379> ttl bomb (integer) -2 127.0.0.1:6379>
02... Redis common data types
brief introduction
summary
As a key/value data storage system, Redis provides a variety of data types to facilitate data management. Then, the data generated in our project is stored based on the specified type, such as user login information, shopping cart information, commodity details, etc.
Common data types
The basic data structure in Redis includes string, hash, set and ordered set. The specific type used in the work should be combined with the specific scene.
String type operation practice
String type is the simplest data type in redis. Its stored value can be string, and its maximum string length can be up to 512M. Based on this type, you can count the number of blog words, continuously append the log to the specified key, realize a distributed self increasing id, and realize the like operation of a blog.
incr/incrby
When the stored string is an integer, redis provides a practical command INCR to increment the current key value and return the incremented value.
Syntax: INCR key
127.0.0.1:6379> set num 1 (integer) 1 127.0.0.1:6379> incr num (integer 2 127.0.0.1:6379> keys * "num" 127.0.0.1:6379> incr num 127.0.0.1:6379>
Note: if num does not exist, it will be created automatically. If num exists, it will be automatically + 1
Specify growth factor
Syntax: INCRBY key increment
127.0.0.1:6379> incrby num 2 (integer) 5 127.0.0.1:6379> incrby num 3 (integer) 8 127.0.0.1:6379> incrby num 2 (integer) 10 127.0.0.1:6379>
decr/decrby
Decrements the specified integer
DECR key is decremented according to the default step size (1 by default)
Decrby key increment decrements according to the specified step size
127.0.0.1:6379> incr num (integer) 11 127.0.0.1:6379> decr num (integer) 10 127.0.0.1:6379> decrby num 3 (integer) 7
append
Add a value to the tail. If the key does not exist, create the key, and its value is the written value, that is, it is equivalent to SET key value. The return value is the total length of the appended string.
Syntax: AOOEND key value
127.0.0.1:6379> keys * "num" "test1" "test2" "test3" 127.0.0.1:6379> get test "666" 127.0.0.1:6379> append test "666" (integer) 6 127.0.0.1:6379> get test "666666" 127.0.0.1:6379>
strlen
String length, returns the length of the data. If the key does not exist, it returns 0. Note that if the key value is an empty string, 0 is also returned.
Syntax: STRLEN key
127.0.0.1:6379> get test "666666" 127.0.0.1:6379> strlen test (integer) 6 127.0.0.1:6379> strlen tnt (integer) 0 127.0.0.1:6379> set tnt "" ok 127.0.0.1:6379> strlen tnt (integer) 0 127.0.0.1:6379> exists tnt (integer) 1 127.0.0.1:6379>
mset/mget
Set / get multiple key values at the same time
Syntax: Mset key value
MGET key key ...
127.0.0.1:6379> flushall ok 127.0.0.1:6379> keys * (empty list or set) 127.0.0.1:6379> mset a 1 b 2 c 3 ok 127.0.0.1:6379> mget a b c 1) "1" 2) "2" 3) "3" 127.0.0.1:6379>
Section interview analysis
- How to realize the word count of blog? (strlen)
- How to continuously append the audit log to the specified key? (appen)
- How do you implement a distributed self incrementing id? (incr - snowflake algorithm)
- How to implement a blog like operation? (incr ,decr)
Application practice of Hash type
Redis hash type is equivalent to HashMap in Java. Its implementation principle is consistent with HashMap. It is generally used to store object information and store the mapping of fields and field values. A hash type can contain up to 232-1 fields.
hse/hget
Grammatical structure
HSET key field value HGET key field HMSET key field value file value HMGET key field field HGETALL key
HSET and HGET assignment and value
127.0.0.1:6379> hset user username lihua (integer)1 127.0.0.1:6379> hget user username "lihua" 127.0.0.1:6379> hset user username lili (integer)0 127.0.0.1:6379> keys user 1)"user" 127.0.0.1:6379> hgetall user 1)"username" 2)"lili" 127.0.0.1:6379> 127.0.0.1:6379> hset user age 18 (integer) 1 127.0.0.1:6379> hset user address "xi'an" (integer) 1 127.0.0.1:6379> hgetall user 1)"username" 2)"chen" 3)"age" 4)"18" 5)"address" 6)"xi'an" 127.0.0.1:6379>
The HSET command does not distinguish between insert and update operations. When the insert operation is executed, the HSET command returns 1 and when the update operation is executed, it returns 0.
hincrby
127.0.0.1:6379> hdecrby article total 1 #Error during execution 127.0.0.1:6379> hincrby article total -1 #There is no hdecrby subtraction command 127.0.0.1:6379> hget article total
hmset/hget
HMSET and HMGET set and get object properties
127.0.0.1:6379> hmset person username tony age 18 ok 127.0.0.1:6379> hmget person age username 1)"18" 2)"tony" 127.0.0.1:6379> hgetall person 1)"username" 2)"tony" 3)"age" 4)"18" 127.0.0.1:6379>
Note: the above HMGET field order can be customized
hexists
Check whether the attribute exists 127.0.0.1:6379> hexists killer (error) ERR wrong number of arguments for 'hexists' command 127.0.0.1:6379> hexists killer a (integer)0 127.0.0.1:6379> hexists user username (integer)1 127.0.0.1:6379> hexists user age (integer)1 127.0.0.1:6379>
hdel
Delete attribute
127.0.0.1:6379> hdel user age (integer)1 127.0.0.1:6379> hgetall user 1)"lihua" 2)"lili" 127.0.0.1:6379> hgetall person 1)"username" 2)"tony" 3)"age" 4)"18" 127.0.0.1:6379>
hkeys/hvals
Only get the field name HKEYS or field value HVALS
127.0.0.1:6379> hkeys person 1)"username" 2)"age" 127.0.0.1:6379> hvals person 1)"tony" 2)"18"
hlen
View the number of elements
127.0.0.1:6379> hlen user (integer)1 127.0.0.1:6379> hlen person (integer)2 127.0.0.1:6379>
Section interview analysis
Do you need to write memory to publish a blog? (required, hmset)
What do you do when browsing blog content? (hmget)
How to determine whether a blog exists? (hexists)
How to delete a blog? (hdel)
How do you store user information in a distributed system after you log in successfully? (hmset)
List type application practice
lpush
Add a string element in the header of the list corresponding to the key
redis 127.0.0.1:6379> lpush mylist "world" (integer) 1 redis 127.0.0.1:6379> lpush mylist "hello" (integer) 2 redis 127.0.0.1:6379> lrange mylist 0 -1 1)"hello" 2)"world" redis 127.0.0.1:6379>
Redis Lrange returns the elements within the specified interval in the list, and the interval is specified by offset START and END. Where 0 represents the first element, 1 represents the second element of the list, and so on. You can also use negative subscripts, with * * - 1 representing the last element of the list and - 2 * * representing the penultimate element of the list
rpush
Add a string element at the end of the list corresponding to the key
redis 127.0.0.1:6379> rpush wolist "NiHAO" (integer) 1 redis 127.0.0.1:6379> rpush wolist "SHiJIe" (integer) 2 redis 127.0.0.1:6379> lrange wolist 0 -1 1)"NiHao" 2)"SHiJIe" redis 127.0.0.1:6379>
del
Empty collection elements, for example
redis 127.0.0.1:6379> del mylist
linsert
Add a string element before or after the specific position of the list corresponding to the key
redis 127.0.0.1:6379> rpush wolist2 "HI" (integer) 1 redis 127.0.0.1:6379> rpush wolist2 "HAO" (integer) 2 redis 127.0.0.1:6379> linsert wolist2 before "HAO" "NI" (integer) 3 redis 127.0.0.1:6379> lrange wolist3 0 -1 1) "HI" 2) "NI" 3) "HAO" redis 127.0.0.1:6379>
lset
Set the element value of the specified subscript in the list (generally used for modification)
redis 127.0.0.1:6379> rpush wolist3 "YI" (integer) 1 redis 127.0.0.1:6379> rpush wolist3 "ER" (integer) 2 redis 127.0.0.1:6379> rpush wolist3 "SAN" (integer) 3 redis 127.0.0.1:6379> rpush wolist3 "SI" (integer) 4 redis 127.0.0.1:6379> lset wolist3 0 "LING" OK redis 127.0.0.1:6379> lset wolist3 -1 "WU" OK redis 127.0.0.1:6379> lrange wolist3 0 -1 1) "LING" 2) "ER" 3) "SAN" 4) "WU" redis 127.0.0.1:6379>
lrem
Delete count elements with the same value from the list corresponding to the key. When count > 0, delete them from beginning to end
redis 127.0.0.1:6379> rpush wolist4 "NI" (integer) 1 redis 127.0.0.1:6379> rpush wolist4 "HAO" (integer) 2 redis 127.0.0.1:6379> rpush wolist4 "HAO" (integer) 3 redis 127.0.0.1:6379> rpush wolist4 "HAO" (integer) 4 redis 127.0.0.1:6379> rpush wolist4 "MA" (integer) 5 redis 127.0.0.1:6379> lrem wolist4 2 "HAO" (integer) 2 redis 127.0.0.1:6379> lrange wolist4 0 -1 1) "NI" 2) "HAO" 3) "MA" redis 127.0.0.1:6379> rpush wolist4 "MA"
When count < 0, it is deleted from end to end
redis 127.0.0.1:6379> rpush wolist5 "NI" (integer) 1 redis 127.0.0.1:6379> rpush wolist5 "NI" (integer) 2 redis 127.0.0.1:6379> rpush wolist5 "HAO" (integer) 3 redis 127.0.0.1:6379> rpush wolist5 "MA" (integer) 4 redis 127.0.0.1:6379> rpush wolist5 "NI" (integer) 5 redis 127.0.0.1:6379> rpush wolist5 "NI" (integer) 6 redis 127.0.0.1:6379> lrem wolist5 -2 "NI" (integer) 2 redis 127.0.0.1:6379> lrange wolist 0 -1 1) "NI" 2) "NI" 3) "HAO" 4) "MA" count =0 Delete all when redis 127.0.0.1:6379> lrem wolist5 0 "NI" (integer) 2 redis 127.0.0.1:6379> lrange wolist 0 -1 1) "HAO" 2) "MA" redis 127.0.0.1:6379>