AES encryption details
Introduction: the full name is advanced encryption standard (English Name: Advanced Encryption Standard), also known as Rijndael encryption method in cryptography, which is sponsored by the National Institute of standards and technology of the United States (NIST) was released in 2001 and became an effective standard in 2002. It is a block encryption standard adopted by the federal government of the United States. This standard is used to replace the original DES. It has been analyzed by many parties and widely used all over the world. It itself has only one key, which is used to realize encryption and decryption.
mode support
CBC, CFB, CTR, ctrgradman, ECB, OFB, etc.
padding support
ZeroPadding, noppadding, AnsiX923, Iso10126, Iso97971, Pkcs7, etc.
Basic parameters of encryption and decryption
In symmetric and asymmetric encryption algorithms, three parameters are often used: initial vector iv, encryption mode and padding. First, the meaning and function of the three parameters are introduced:
Initial vector iv
In cryptography, the initial vector, also known as the initial function, is used in combination with the key. As a means of encrypting data, it is a value of fixed length. The length of iv depends on the encryption method. It is usually equivalent to the length of the encryption key or password used. Generally, it is required to be a random number or quasi random number in the process of use, The initial vector generated by random number can achieve semantic security, which makes it difficult for attackers to crack the ciphertext that is consistent with the original text and generated with the same key.
Encryption mode
At present, the popular encryption and digital authentication algorithms adopt block encryption, which means that the encrypted plaintext is divided into fixed size data blocks, and then the cryptographic algorithm is executed., To get the ciphertext. Data blocks are usually of the same length as the key. The encryption mode is developed on the basis of the encryption algorithm, and can also exist independently of the encryption algorithm. The encryption mode defines how to convert plaintext larger than one data block size into ciphertext by reusing the encryption algorithm, and describes the process of encrypting each data block. At present, the more used encryption modes are CBC, ECB, PBC, CFB, OFB and CTR.
Filling method: padding
Block ciphers can only process data of a certain length, and the length of messages is usually variable. Therefore, the last piece of data in some modes needs to be filled before encryption. There are several filling methods, the simplest of which is to fill empty characters at the end of plaintext so that their length is an integer multiple of block data. The common filling methods are as follows: PKCS7, PKCSS, ZeroPadding, ISO10126 and ANSIX923.
JavaScript encryption
// Reference crypto JS encryption module
var CryptoJS = require('crypto-js')
function tripleAesEncrypt() {
var key = CryptoJS.enc.Utf8.parse(aesKey),
iv = CryptoJS.enc.Utf8.parse(aesIv),
srcs = CryptoJS.enc.Utf8.parse(text),
// CBC encryption mode, Pkcs7 filling mode
encrypted = CryptoJS.AES.encrypt(srcs, key, {
iv: iv,
mode: CryptoJS.mode.CBC,
padding: CryptoJS.pad.Pkcs7
});
return encrypted.toString();
}
function tripleAesDecrypt() {
var key = CryptoJS.enc.Utf8.parse(aesKey),
iv = CryptoJS.enc.Utf8.parse(aesIv),
srcs = encryptedData,
// CBC encryption mode, Pkcs7 filling mode
decrypted = CryptoJS.AES.decrypt(srcs, key, {
iv: iv,
mode: CryptoJS.mode.CBC,
padding: CryptoJS.pad.Pkcs7
});
return decrypted.toString(CryptoJS.enc.Utf8);
}
var text = "I love Python!" // Object to be encrypted
var aesKey = "6f726c64f2c2057c" // Key, 16 multiples
var aesIv = "0123456789ABCDEF" // Offset, 16 multiples
var encryptedData = tripleAesEncrypt()
var decryptedData = tripleAesDecrypt()
console.log("Encrypted string: ", encryptedData)
console.log("Decrypt string: ", decryptedData)
// Encrypted string: dZL7TLJR786VGvuUvqYGoQ==
// Decryption string: I love Python!
python implementation
import base64
from Cryptodome.Cipher import ARC4
def rc4_encrypt(key, t):
enc = ARC4.new(key.encode('utf8'))
res = enc.encrypt(t.encode('utf-8'))
res = base64.b64encode(res)
return res
def rc4_decrypt(key, t):
data = base64.b64decode(t)
enc = ARC4.new(key.encode('utf8'))
res = enc.decrypt(data)
return res
if __name__ == "__main__":
secret_key = '12345678' # secret key
text = 'I love Python!' # Encrypted object
encrypted_str = rc4_encrypt(secret_key, text)
print('Encrypted string:', encrypted_str)
decrypted_str = rc4_decrypt(secret_key, encrypted_str)
print('Decryption string:', decrypted_str)
# Encrypted string: b'8tNVu3/U/veJR2KgyBw = '
# Decryption string: b'I love Python! '
case analysis
Target website: aHR0cDovL2p6c2MubW9odXJkLmdvdi5jbi9kYXRhL2NvbXBhbnk=
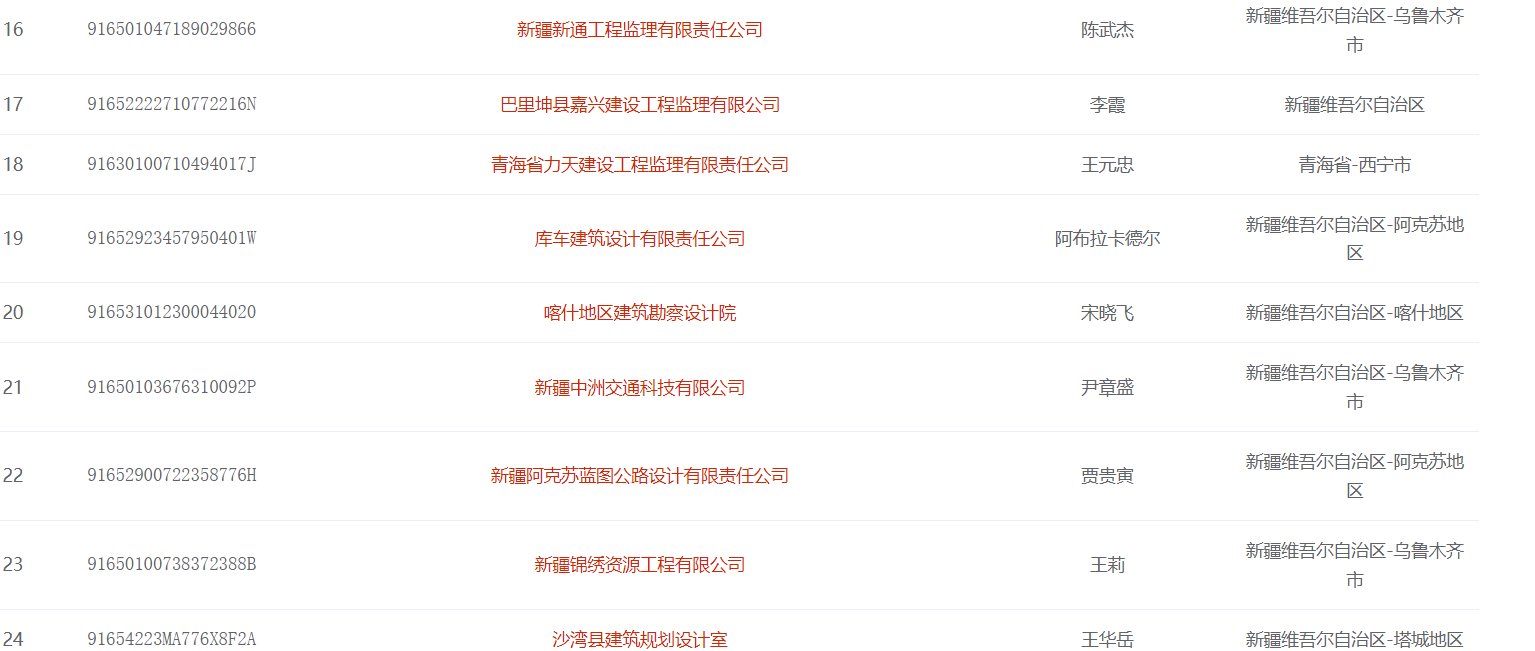
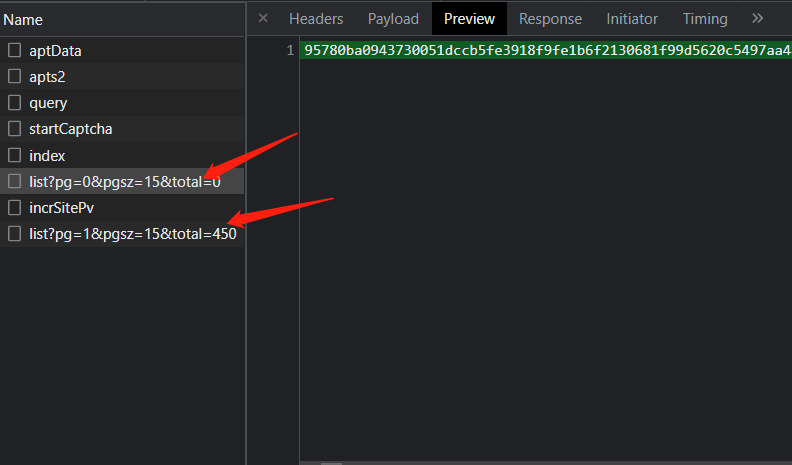
The analysis shows that the enterprise data is loaded through Ajax and encrypted. From past experience, the content before encryption should be json data, and the encryption method of data can not be seen. Therefore, general json data can search json Parse found the object code.
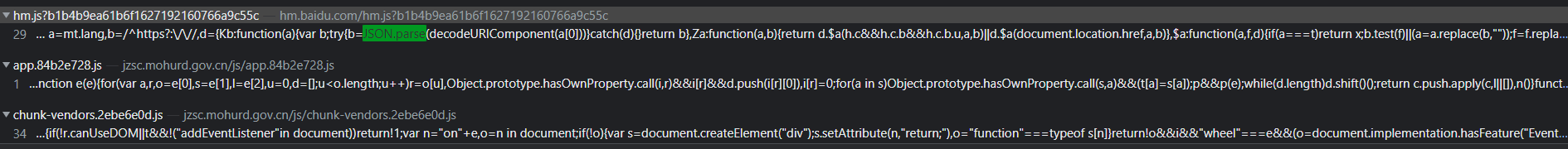
Through the global search, we found a total of three available codes. Through debugging and analysis, we found the app 84b2e728. JS is the target file.
Place a breakpoint at the suspicious code for debugging:
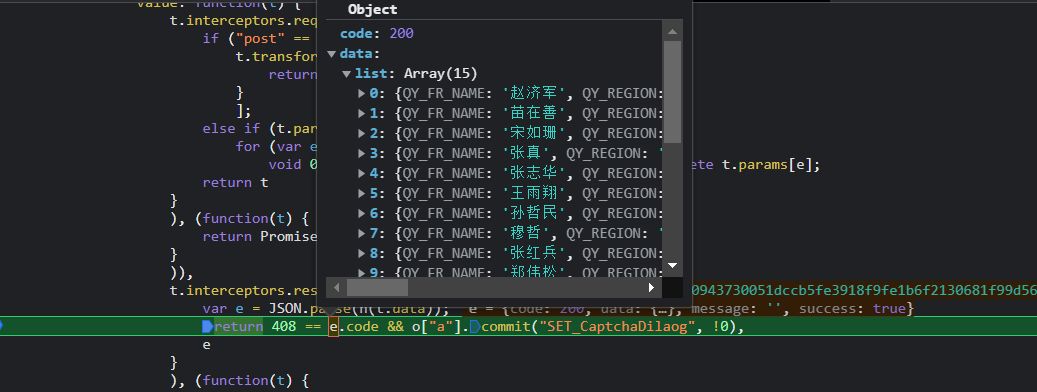
The variable E is the decrypted data, and the observation statement var e = JSON parse(h(t.data)); , Following the H function directly, you can see the obvious AES encryption:
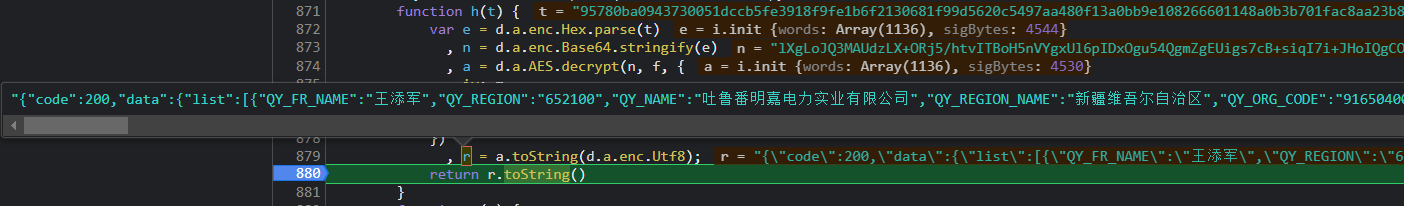
It can be seen from the above figure that variable r is the data before encryption and variable t is the data after encryption.
function h(t) {
var e = d.a.enc.Hex.parse(t)
, n = d.a.enc.Base64.stringify(e)
, a = d.a.AES.decrypt(n, f, {
iv: m,
mode: d.a.mode.CBC,
padding: d.a.pad.Pkcs7
})
, r = a.toString(d.a.enc.Utf8);
return r.toString()
}
The encryption mode is CBC, the filling mode is pkcs7, and the missing values of offset m and f can be found above.
f = d.a.enc.Utf8.parse("jo8j9wGw%6HbxfFn")
m = d.a.enc.Utf8.parse("0123456789ABCDEF")
In python, you need to introduce CryptoJS and rewrite this function.