catalogue
1. Principle
Secondary injection can be understood as the injection caused by the malicious data constructed by the attacker being stored in the database and being read and entered into the SQL query statement. The defender may escape the special characters when the user enters malicious data; However, when the malicious data is inserted into the database, the processed data is restored and stored in the database. When the Web program calls the malicious data stored in the database and executes SQL query, SQL secondary injection occurs.
Secondary injection process
(1) Construct a statement first (this statement contains statements with escaped characters, such as mysql_escape_string, mysql_real_escape_string escape)
(2) Store the malicious statements we constructed into the database (escaped statements)
(3) The second construction statement (combined with the statements previously stored in the database. Because the system does not check the stored data, it is successfully injected)
2. Experimental process
Take sqli labs less 24 as an example
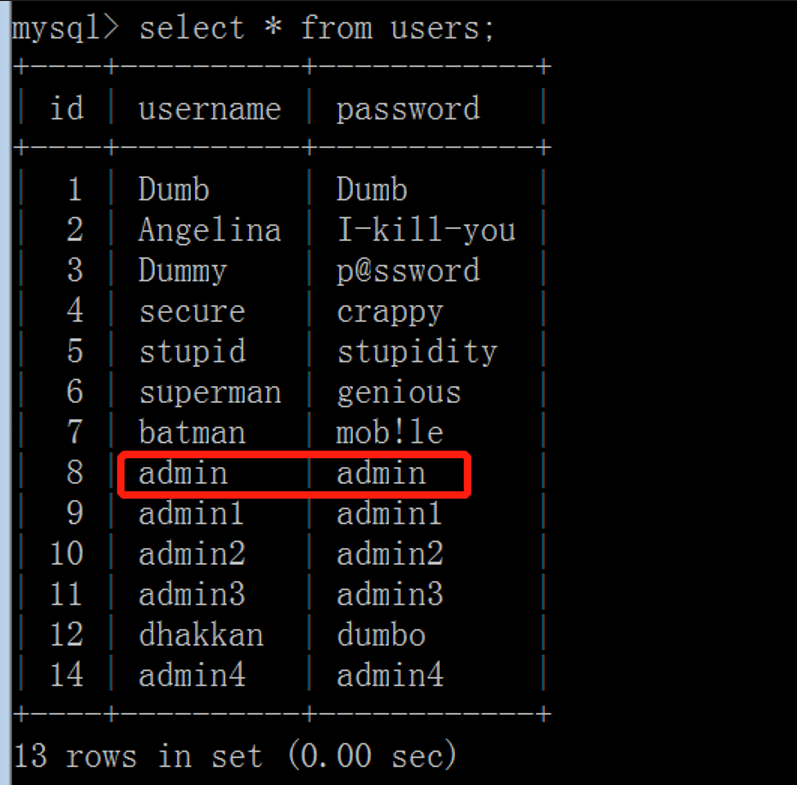
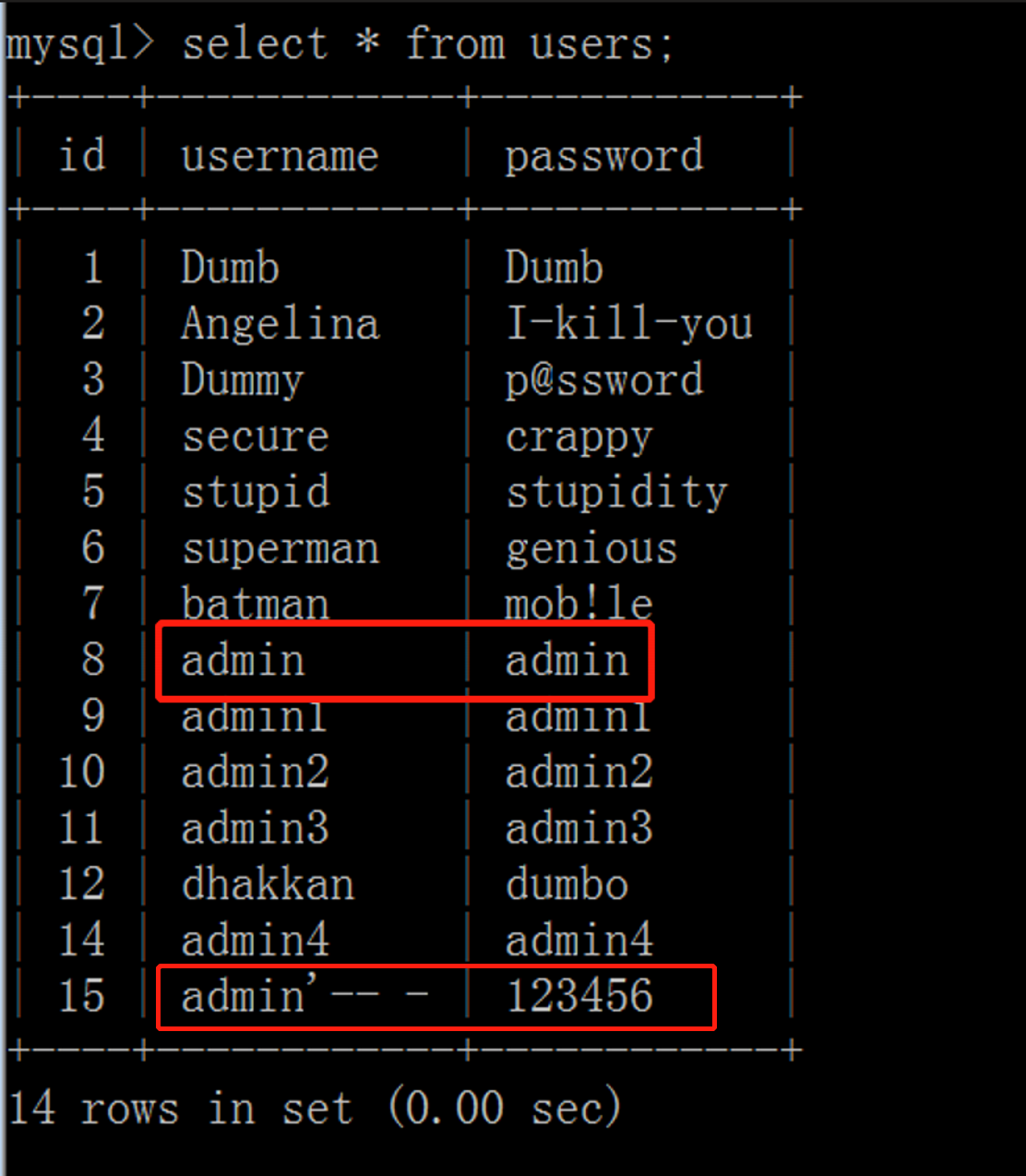
(1) View initial users table
It is found that the password of the account admin in the initial users table is admin
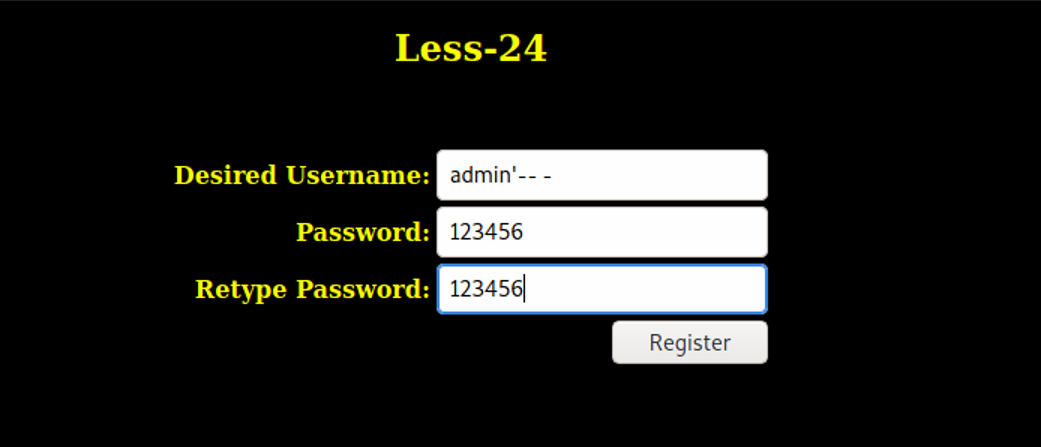
(2) Registered user
Register a user named admin '--- password 123456 on the website
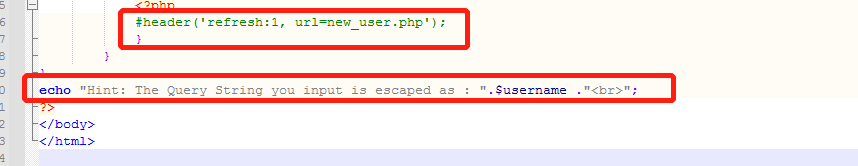
The main codes of registered users are as follows:
if (isset($_POST['submit']))
{
$username= mysql_escape_string($_POST['username']) ;
$pass= mysql_escape_string($_POST['password']);
$re_pass= mysql_escape_string($_POST['re_password']);
//Escape the data entered during account registration
echo "<font size='3' color='#FFFF00'>";
$sql = "select count(*) from users where username='$username'";
$res = mysql_query($sql) or die('You tried to be smart, Try harder!!!! :( ');
$row = mysql_fetch_row($res);
if (!$row[0]== 0)
{
?>
<script>alert("The username Already exists, Please choose a different username ")</script>;
<?php
header('refresh:1, url=new_user.php');
}
else
{
if ($pass==$re_pass)
{
$sql = "insert into users ( username, password) values(\"$username\", \"$pass\")";
//Code for creating account
mysql_query($sql) or die('Error Creating your user account, : '.mysql_error());
.........We can add a sentence of code at the end of the php file to print out the created user name in the web page. Automatically jump to the page code comments, easy to view the effect.
echo "Hint: The Query String you input is escaped as : ".$username ."<br>";
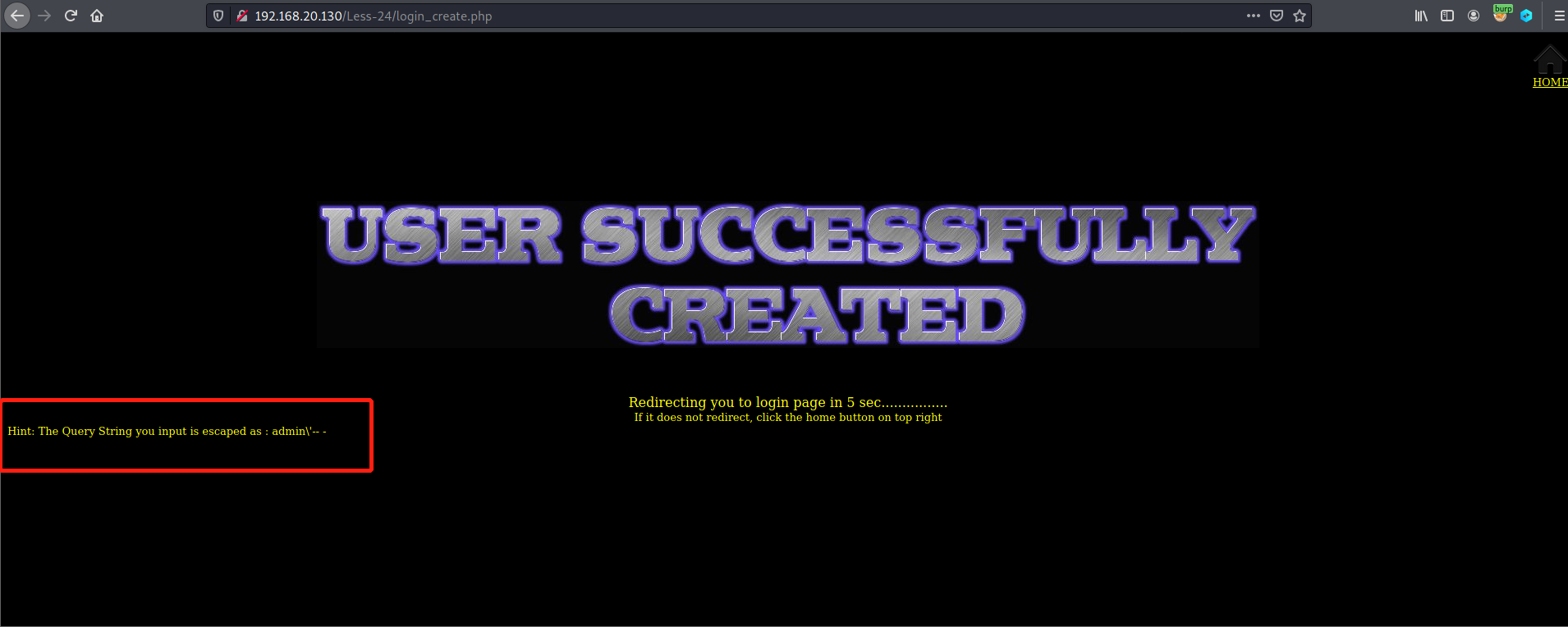
 It can be found that the single quotation mark of the user name admin '--- has been escaped. sql injection cannot be performed directly when registering a user. It can only be used twice to achieve sql injection and obtain data.
It can be found that the single quotation mark of the user name admin '--- has been escaped. sql injection cannot be performed directly when registering a user. It can only be used twice to achieve sql injection and obtain data.
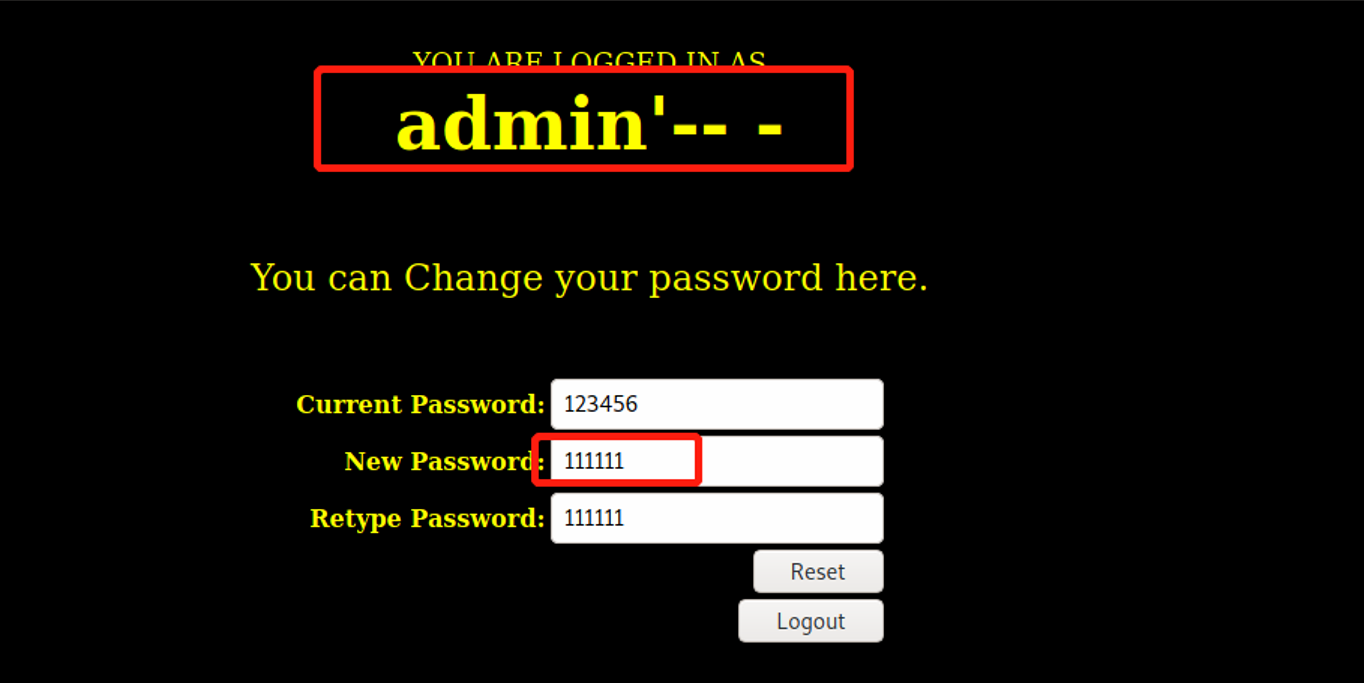
(3) Modify user password
Let's check the users table at this time and find that there is an additional user admin '--- instead of the admin \' --- just printed on the web page. This is because the code for creating the user only adds a \ 'before the single quotation mark, so that the single quotation mark is regarded as a character in the string rather than a single quotation mark in the sql statement.
Modify the password of user admin '---
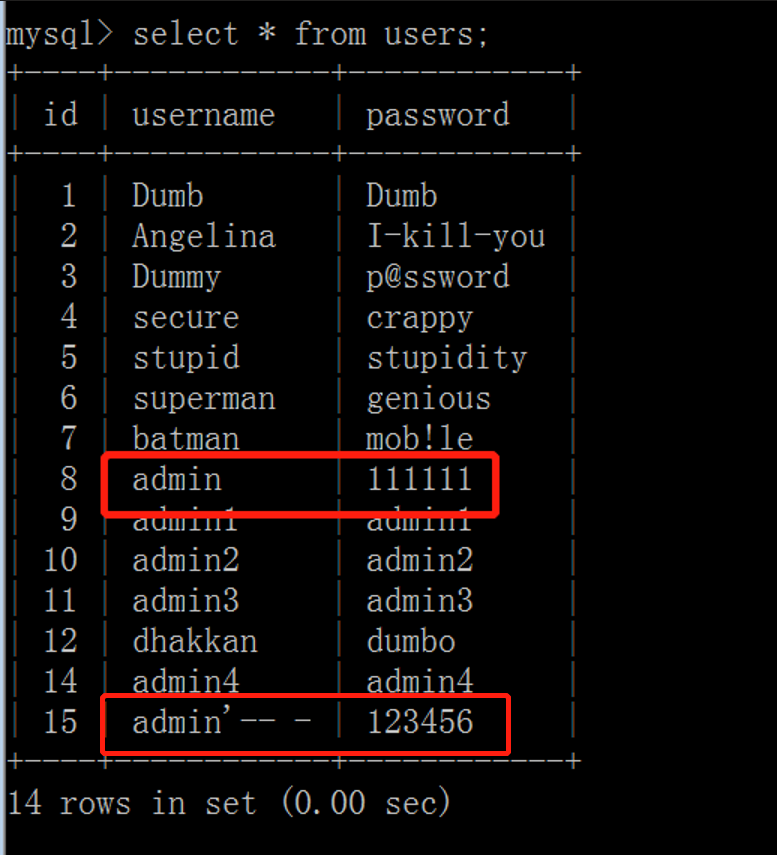
Check the users table again and find that the password of user admin '-- has not been changed, but the password of user admin has been changed. So we have the admin account password.
3. Cause
During the website design, although the registered information was filtered and the special characters were escaped, the data saved from the outside was not filtered when calling from the database, so that "admin '---" was substituted into the sql statement for execution, and the payload was executed, so as to achieve the purpose of modifying the user admin password
Specific code
#Original statement UPDATE users SET PASSWORD='$pass' where username='$username' and password='$curr_pass' #Statement after inserting payload UPDATE users SET PASSWORD='$pass' where username='admin'-- -' and password='$curr_pass' #At this time, the statement after 'admin' is annotated #Real effective statement UPDATE users SET PASSWORD='$pass' where username='admin' #Thus, the purpose of modifying the user admin password is achieved
4. Defensive measures
(1) Be cautious about externally submitted data
(2) When getting data from the database, you can't easily trust the queried data. You should do the same escape or screening
Reference link: SQL injection - secondary injection_ selecthch blog - CSDN blog_ Secondary injection